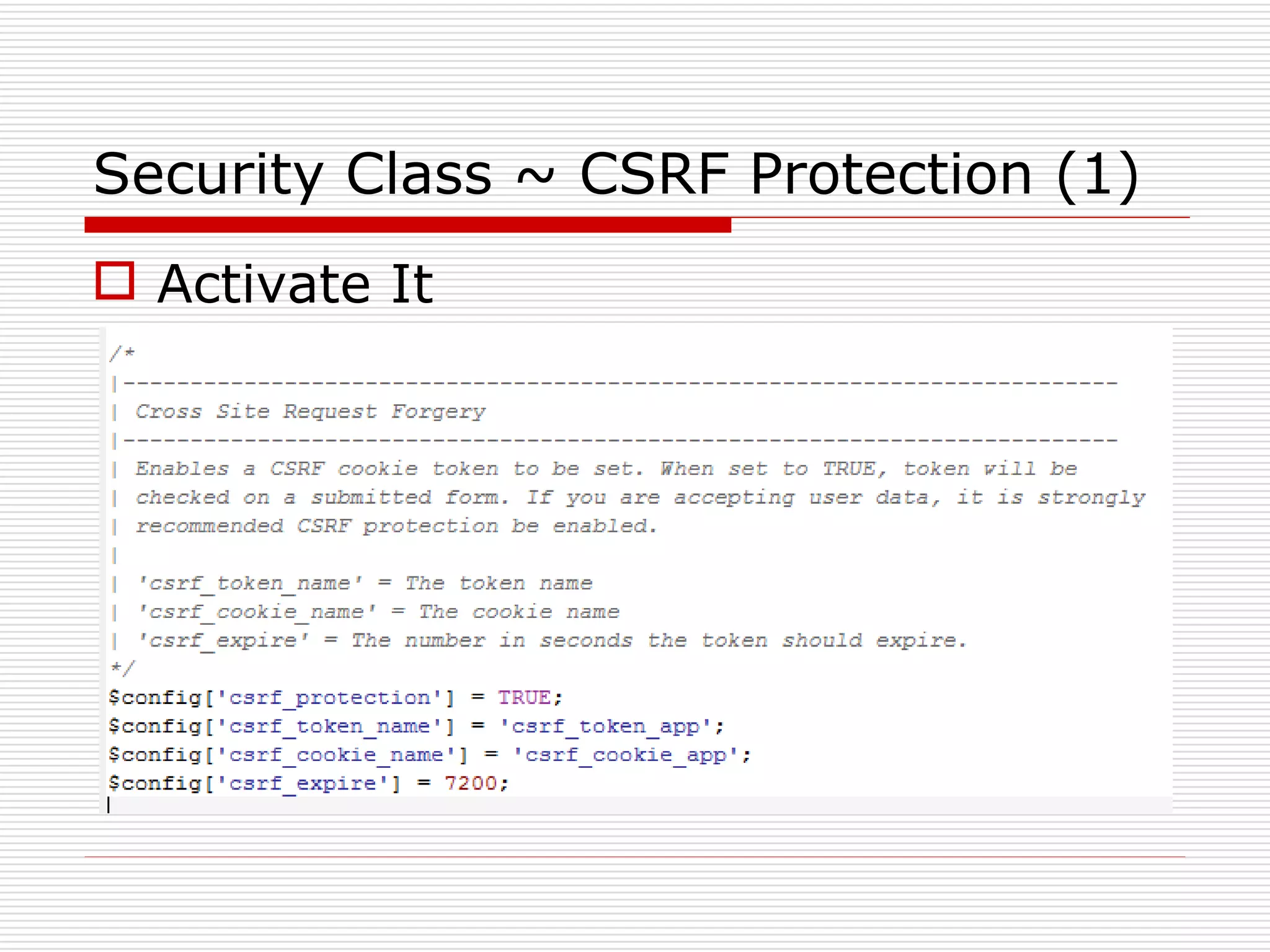
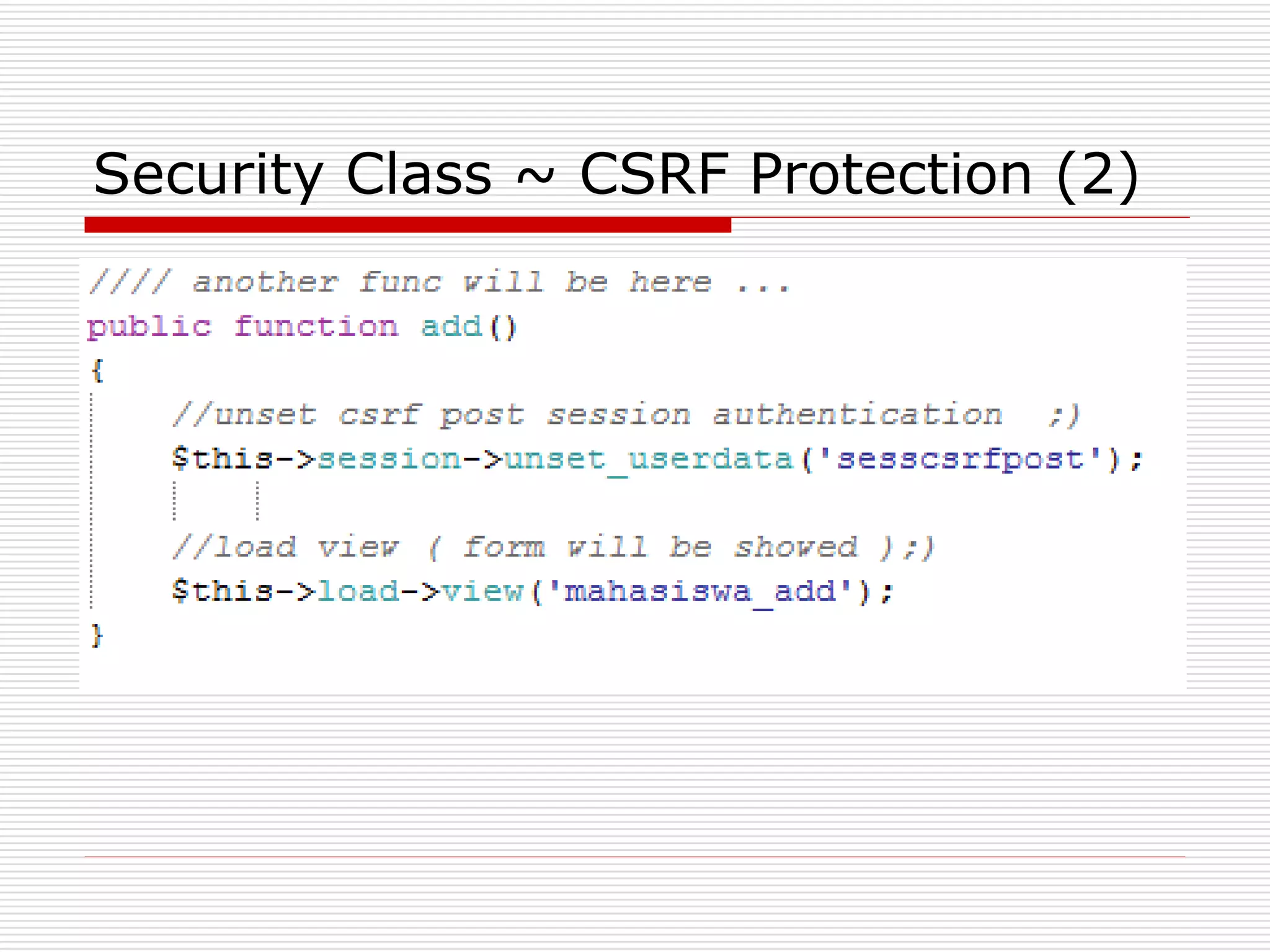
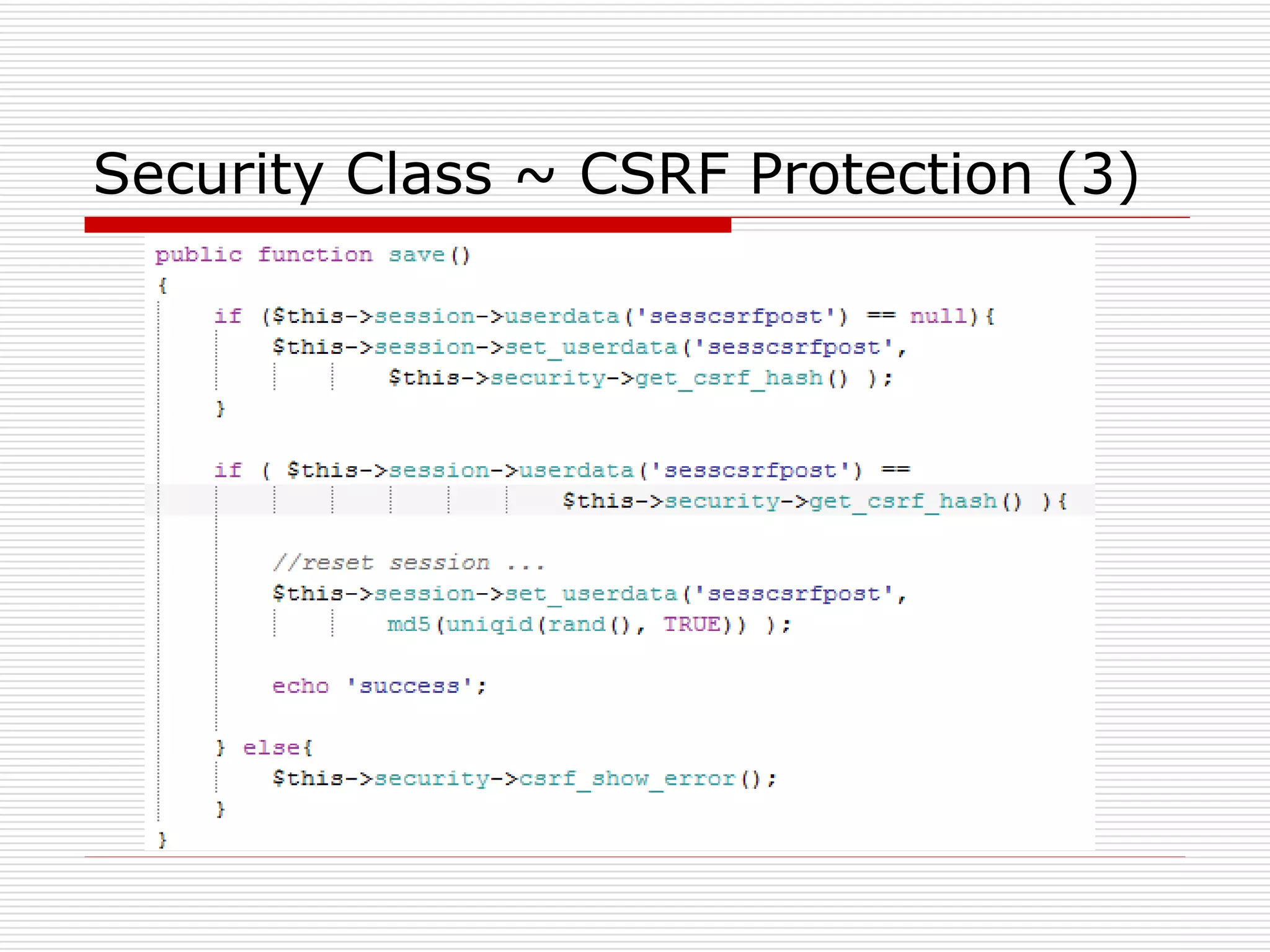
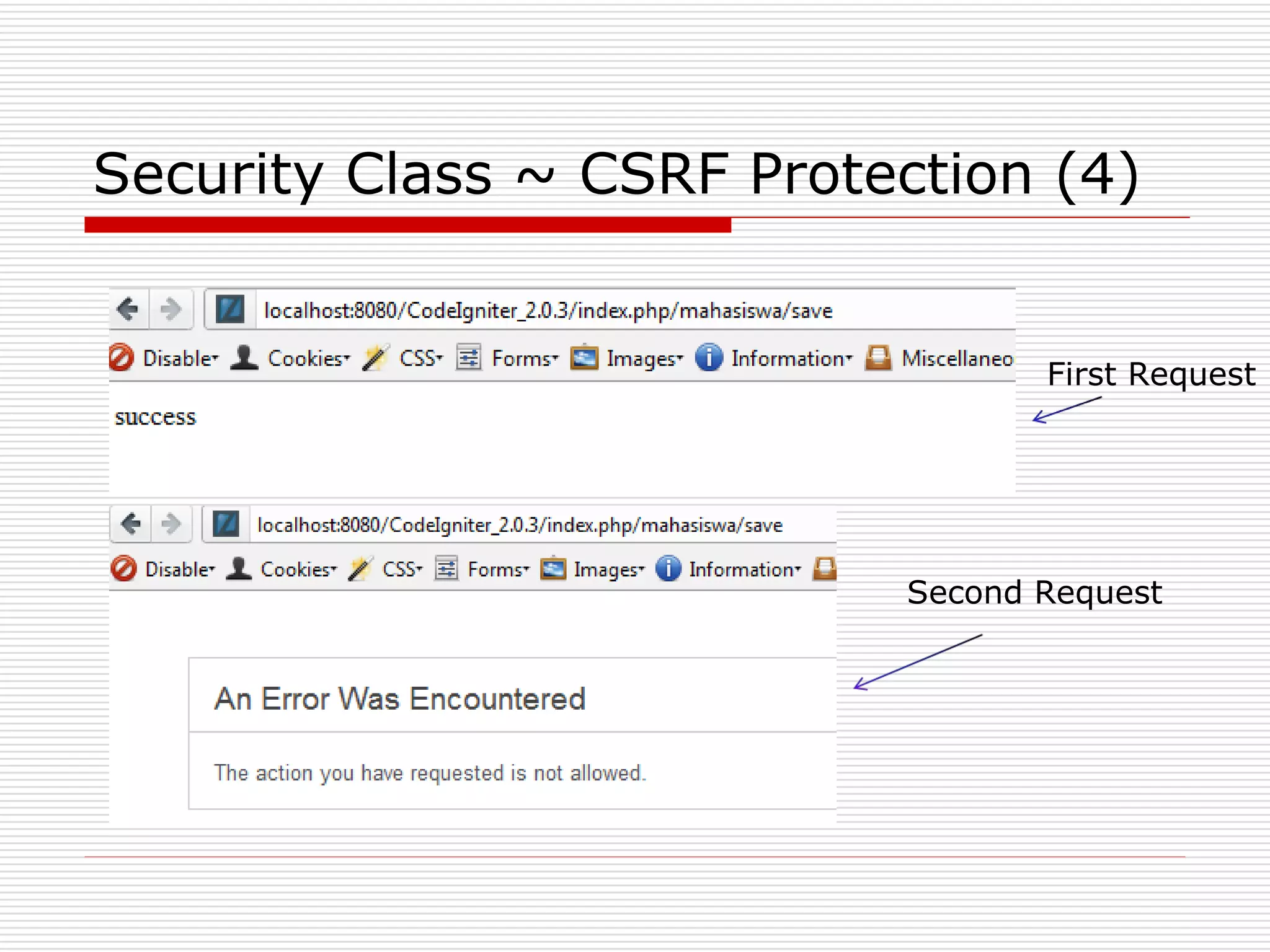
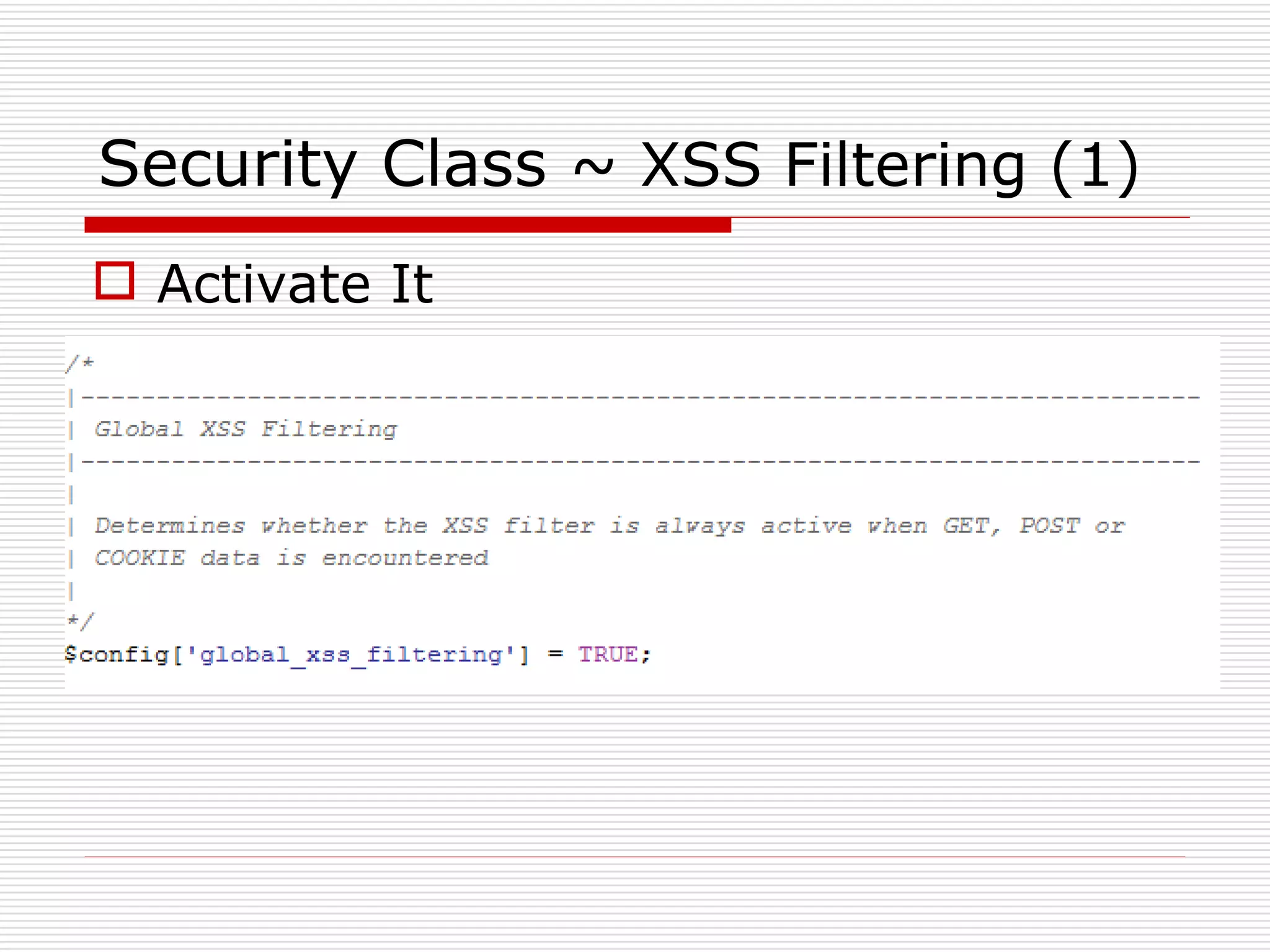
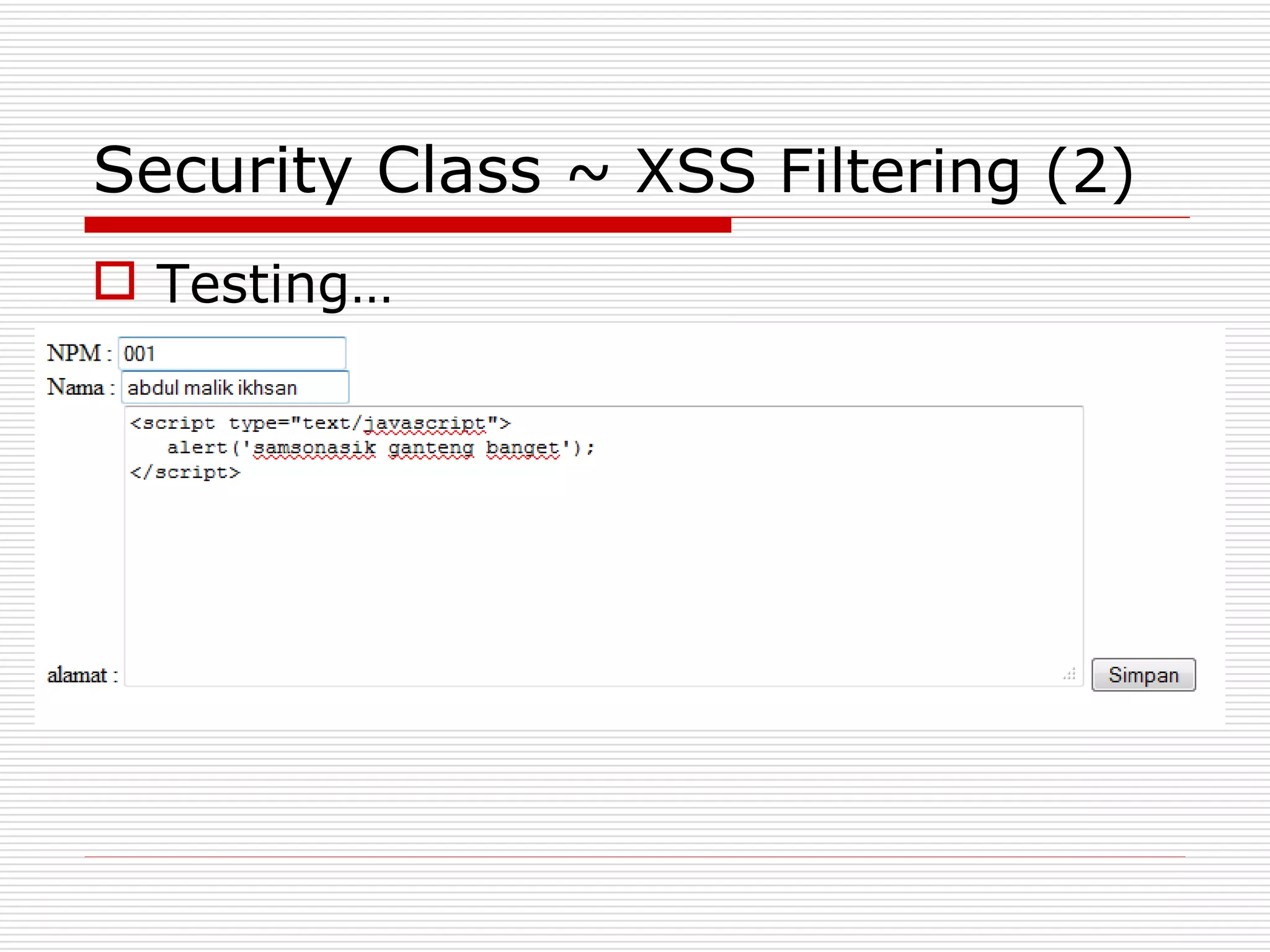
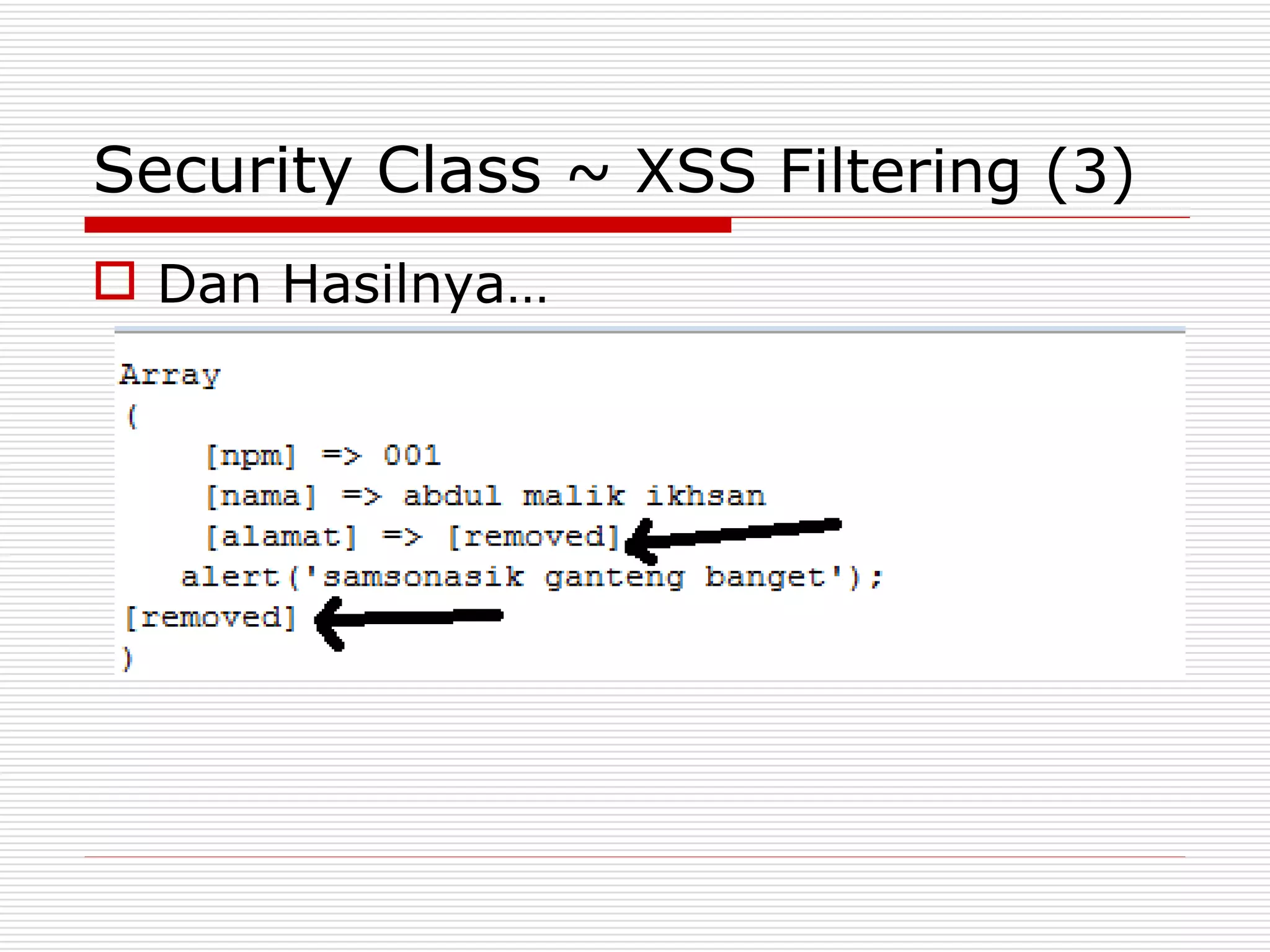
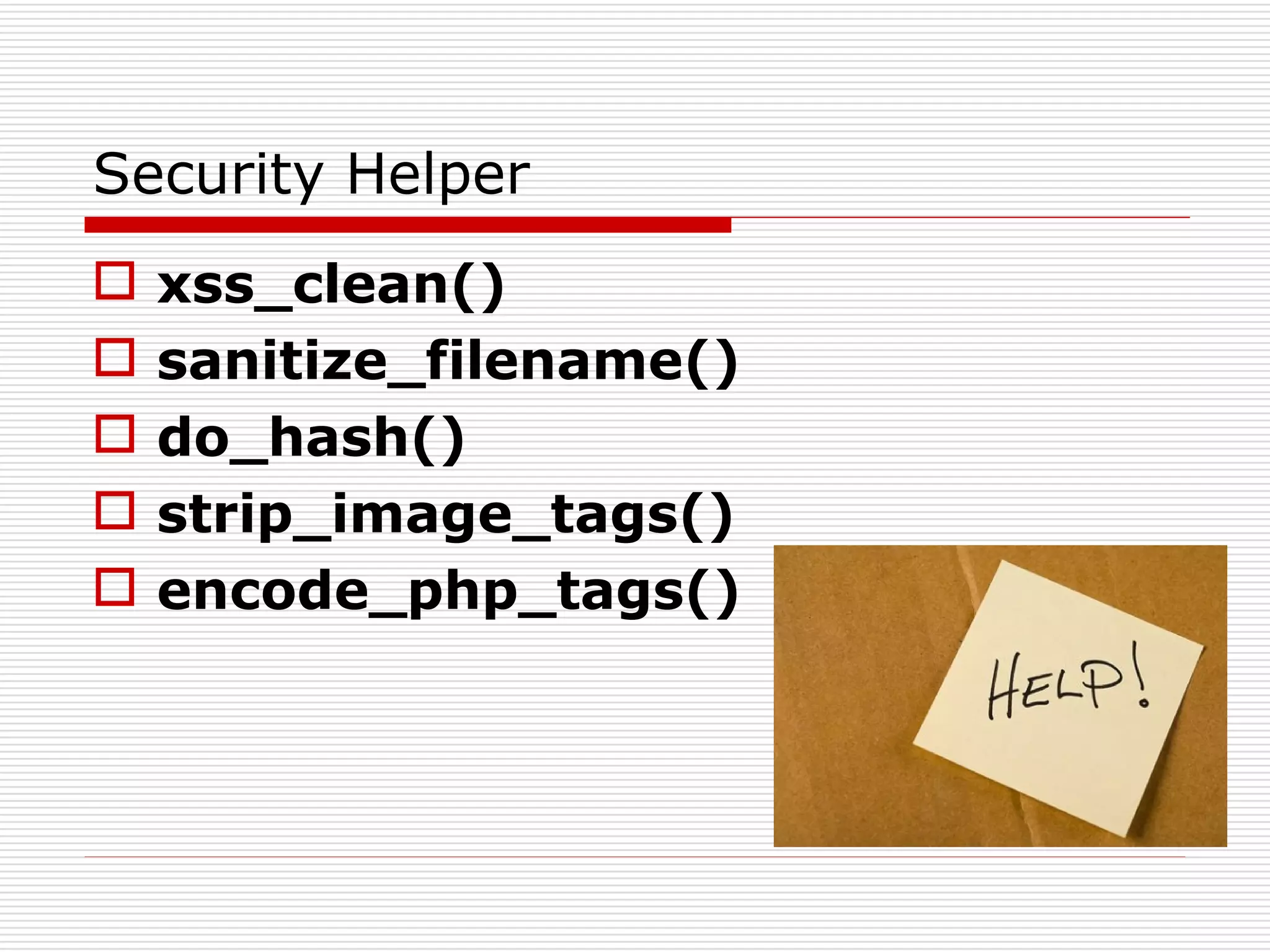
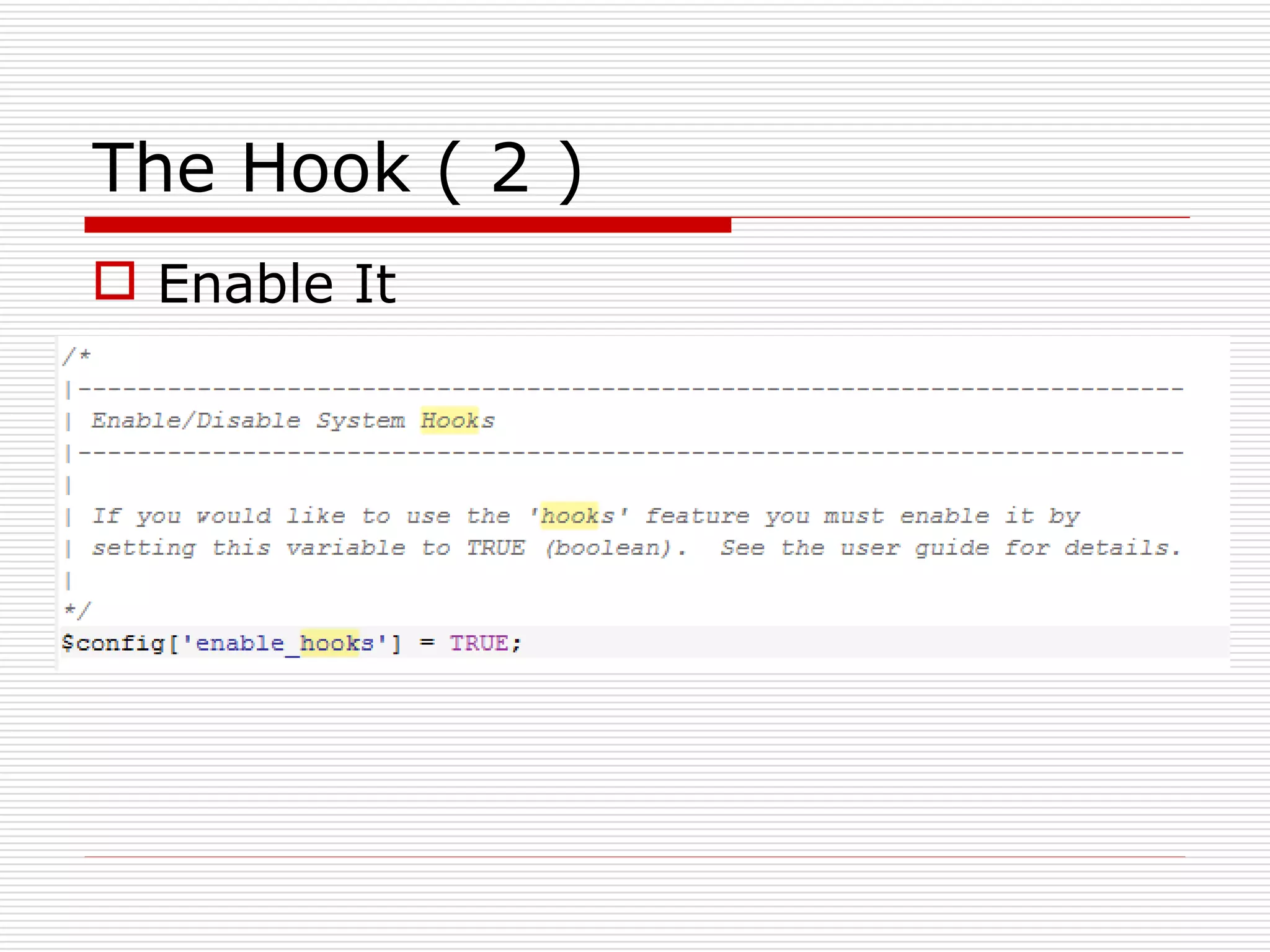
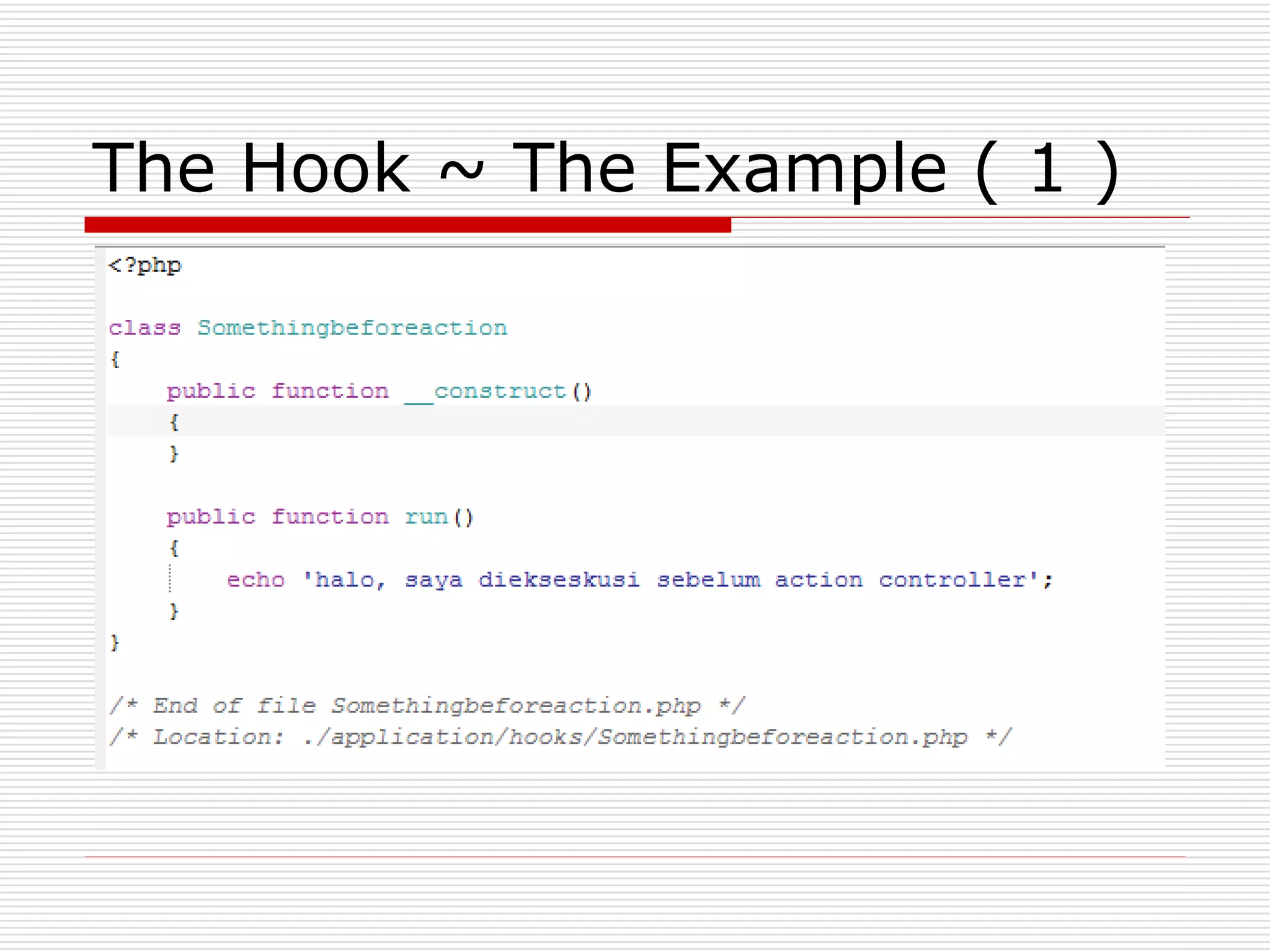
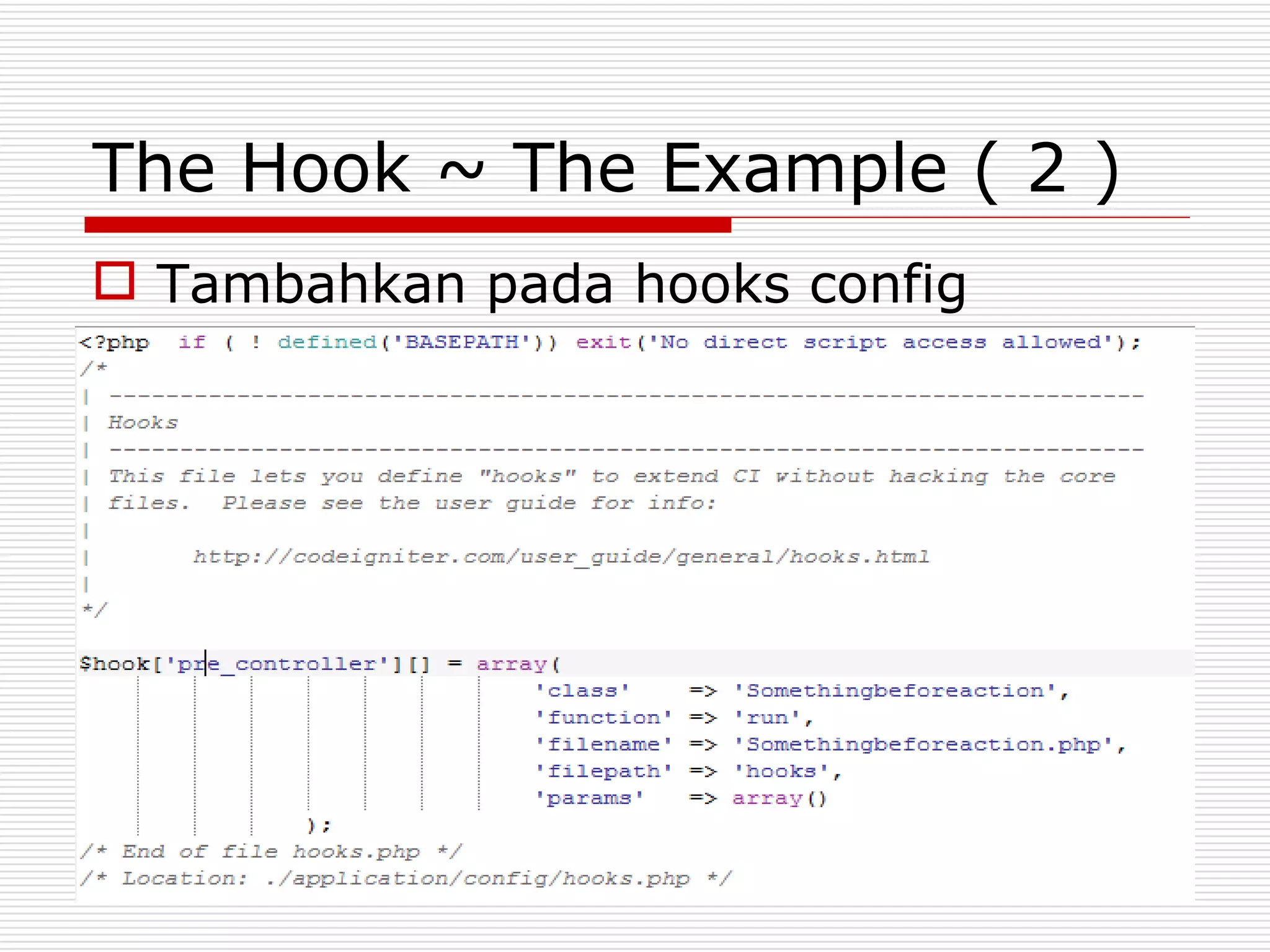
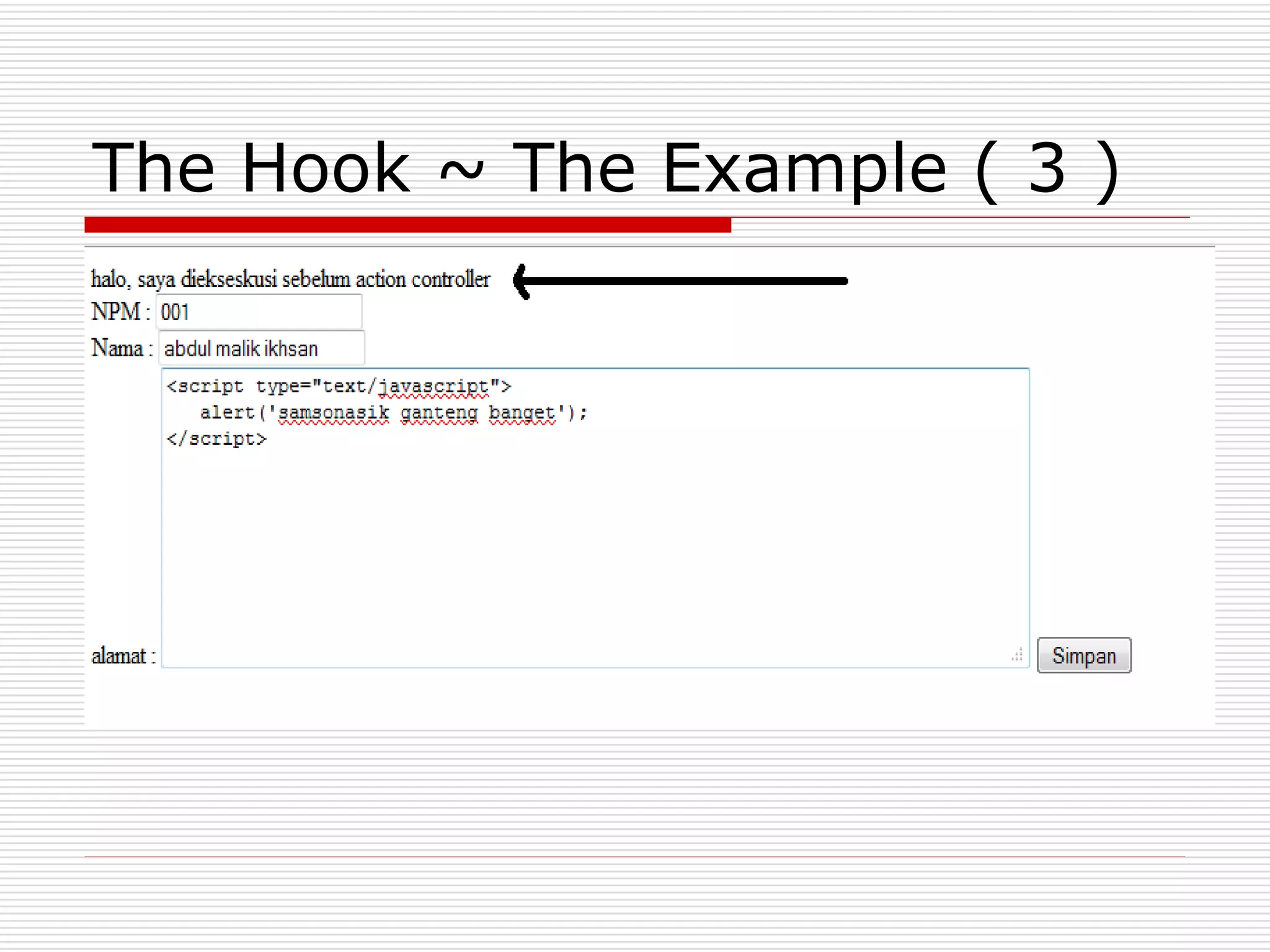
This document discusses security features and hooks in CodeIgniter. It covers CSRF protection, XSS filtering, security helpers like xss_clean(), and how hooks allow calling scripts before or after system processes to enable extensions of functionality. Examples are provided of adding a hook to the configuration to call a function after the controller is run.