Embed presentation
Download as PDF, PPTX



















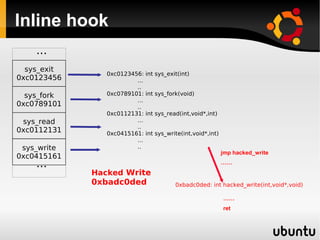


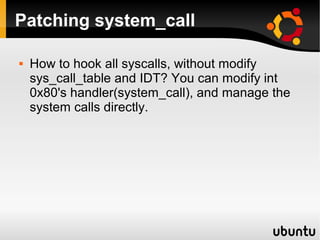



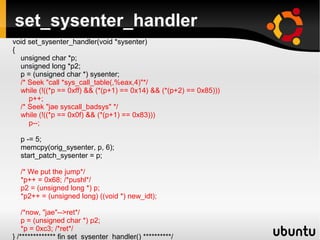
















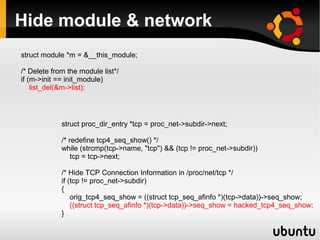





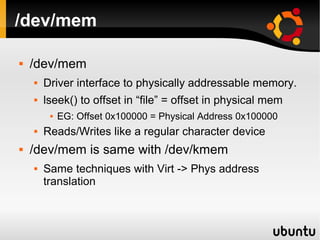
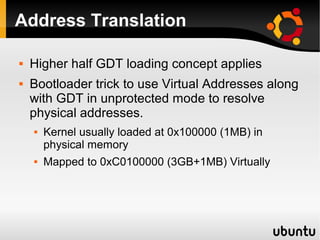








This document describes techniques for creating rootkits on Linux x86 systems. It discusses obtaining the system call table, hooking system calls through various methods like direct modification of the table, inline hooking of system call code, and patching the system call handler. It also presents the idea of abusing debug registers to generate exceptions and intercept system calls. The goal is to conceal running processes, files, and other system data from detection.




























































