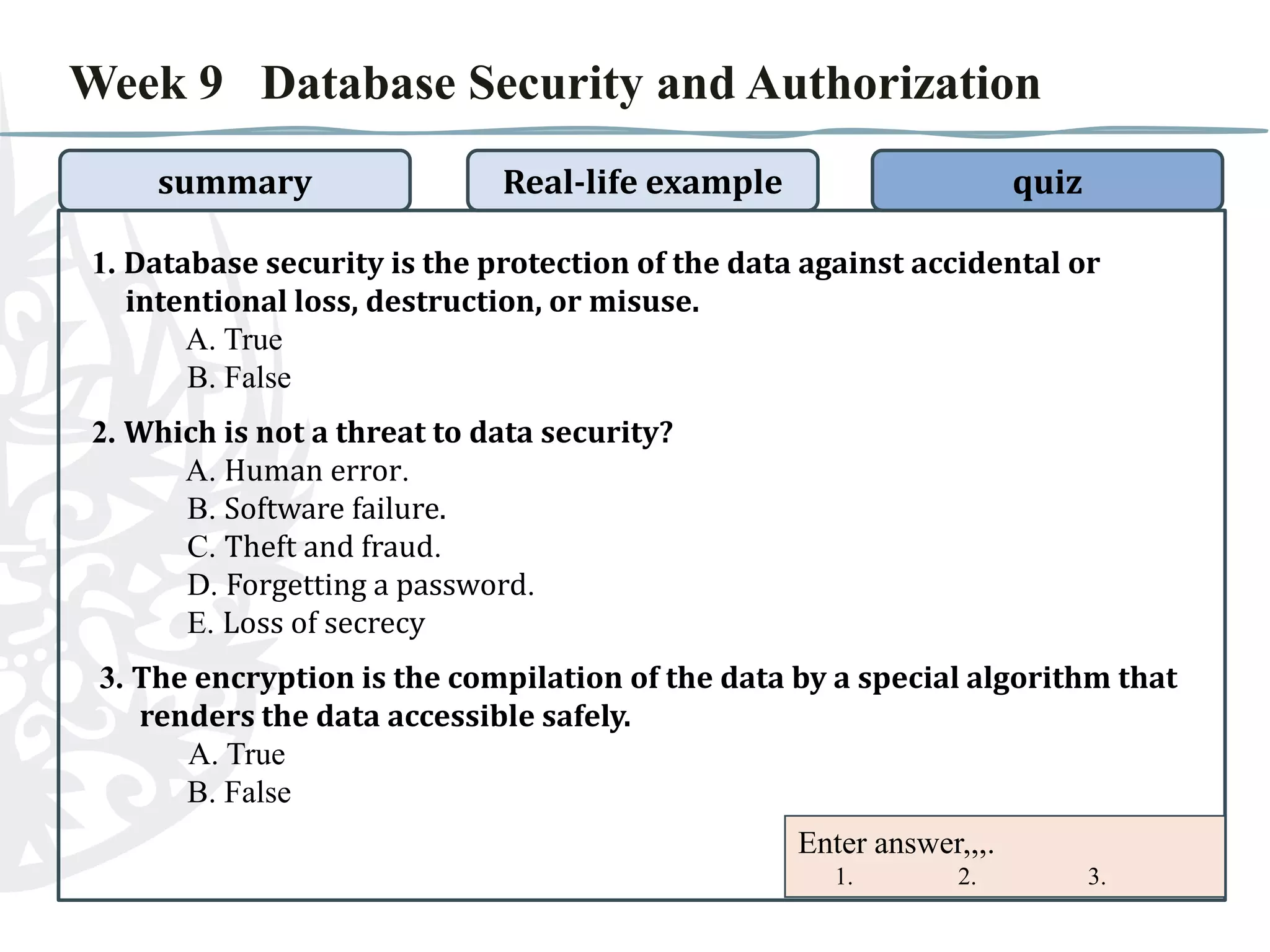
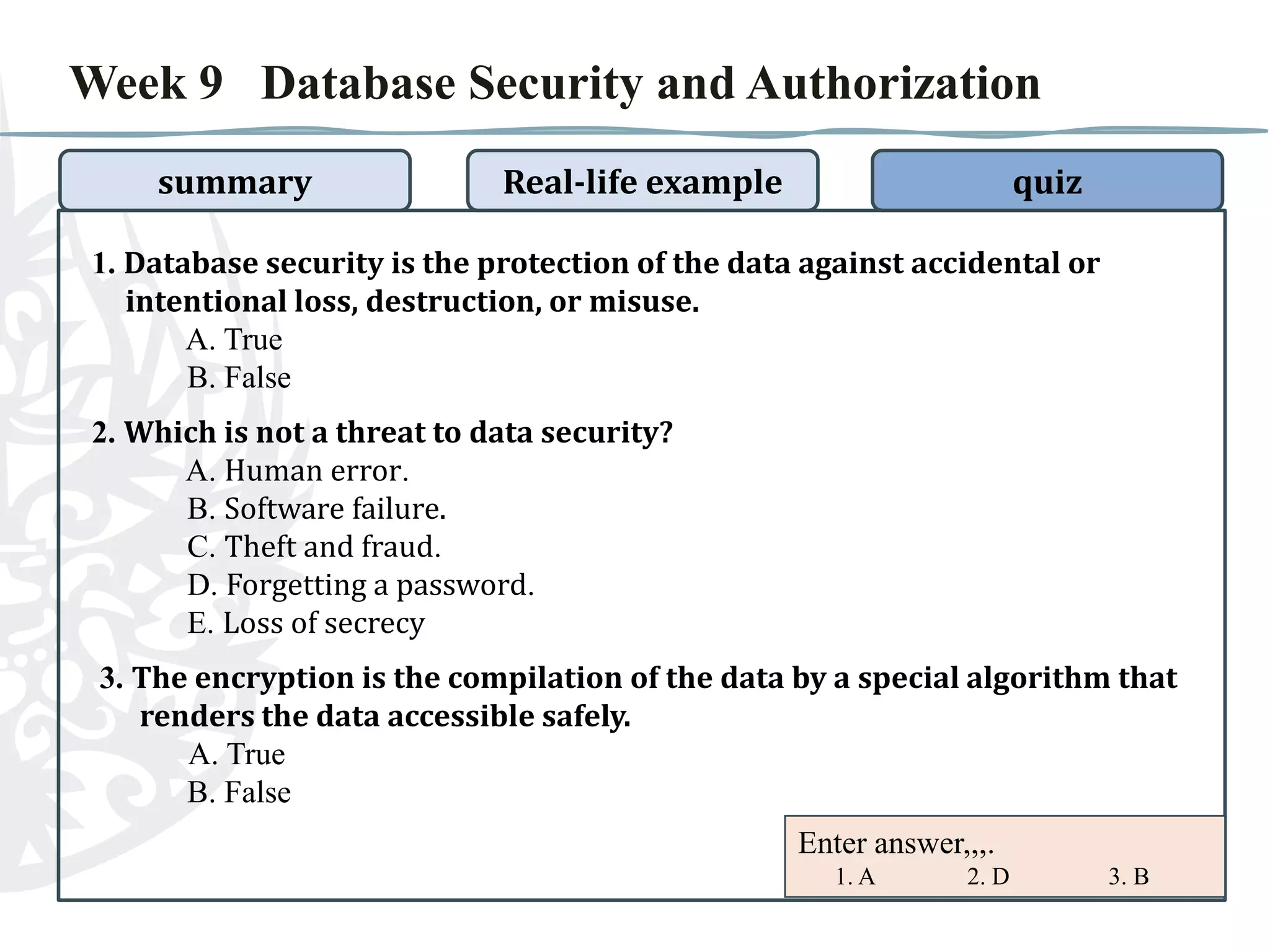
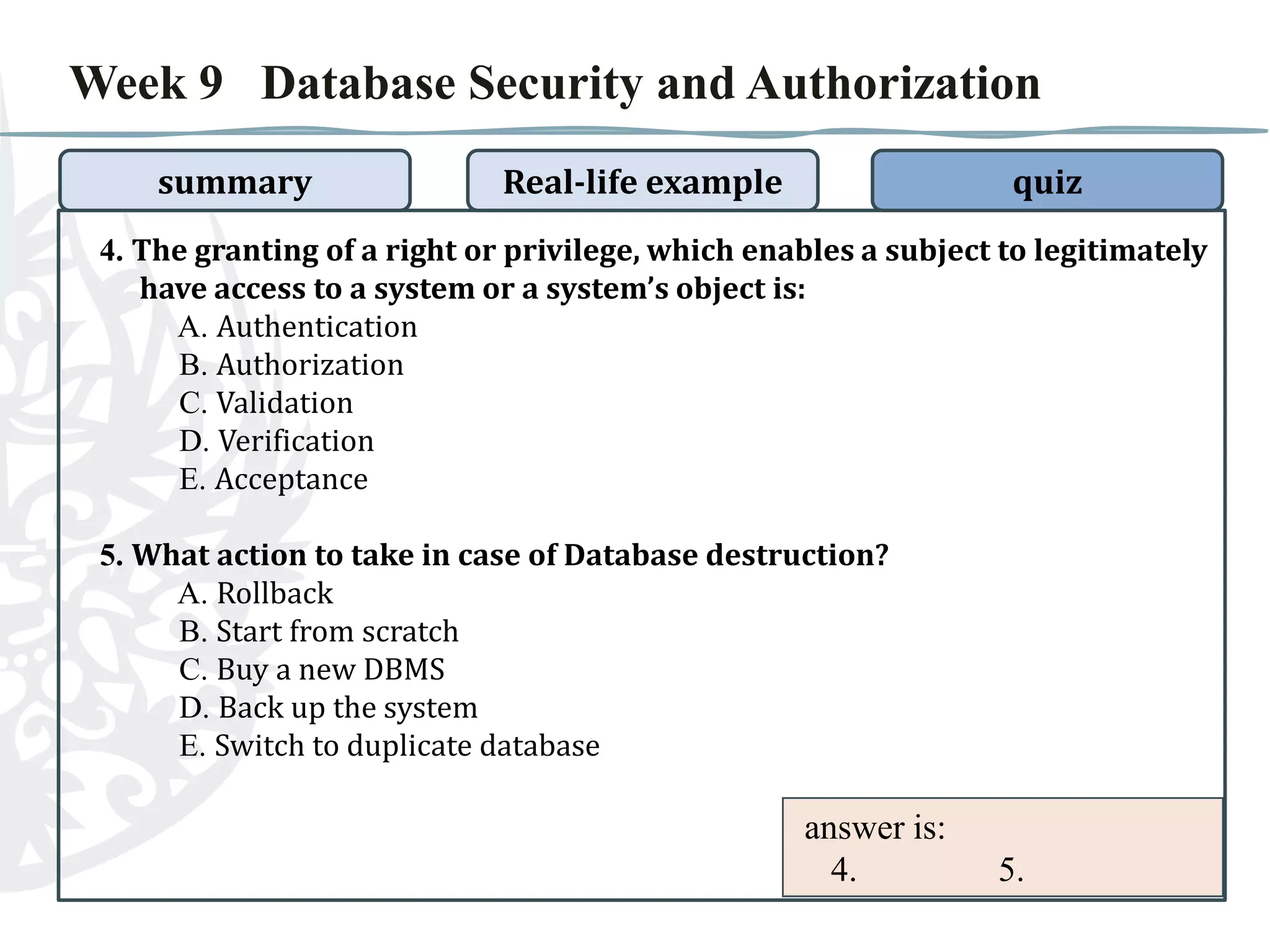
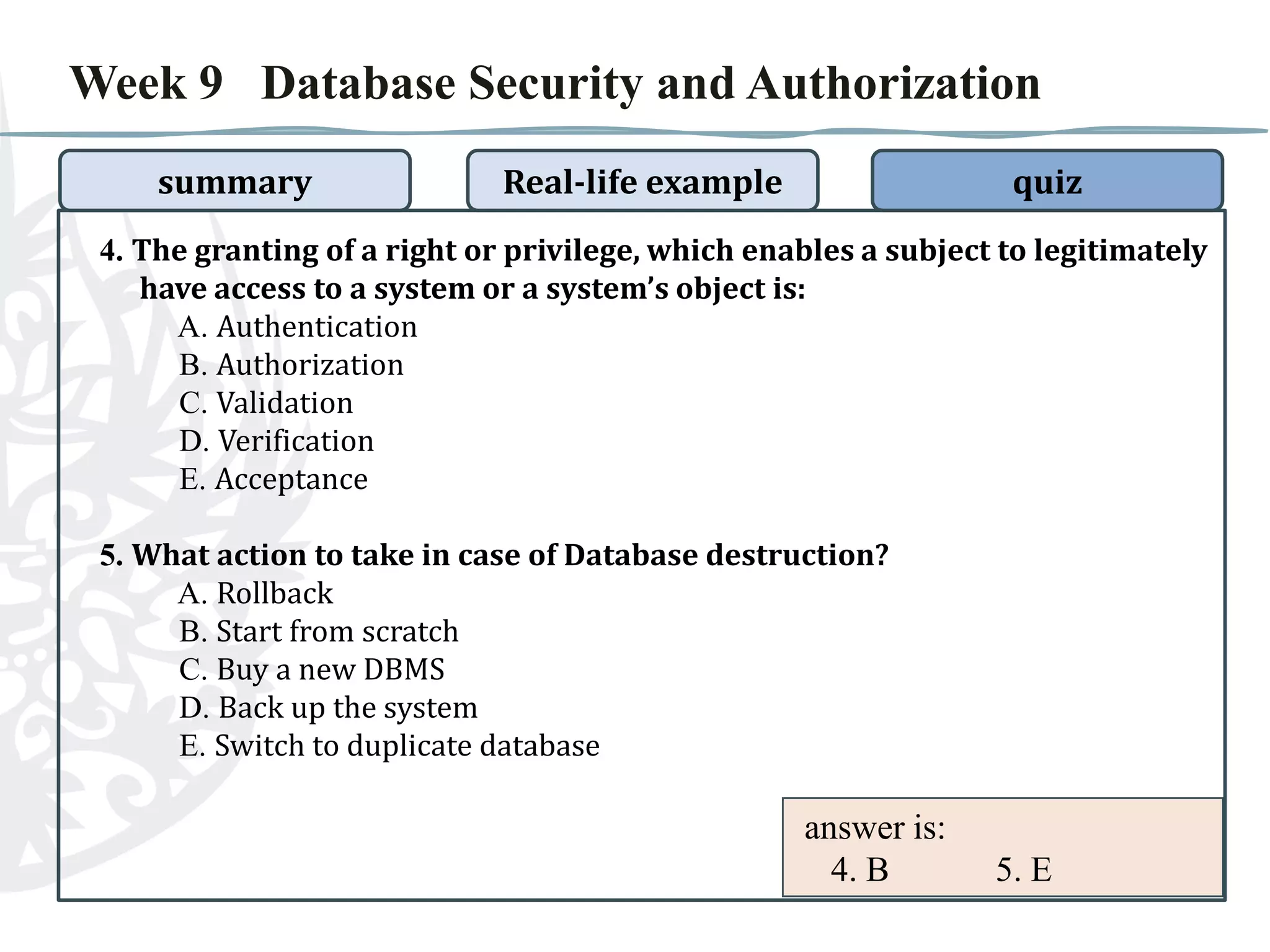
The document discusses database security and authorization. It covers threats to data security like human error and theft. Authentication verifies users' identities while authorization grants access privileges. Encryption encodes data for safe access. The document provides examples of improper authorization in schools and banks. It also includes a quiz on database security and authorization topics.