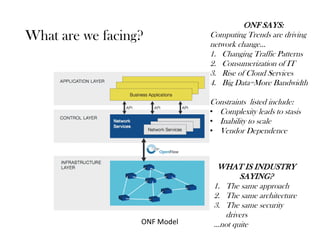
The document discusses security considerations and concerns for standardization of software defined networking. It notes computing trends driving network changes and constraints faced. Industry is said to be taking the same approach and architecture but security drivers may not be quite the same. The document discusses using a defense in depth model with baseline security models, integrity checks, and physical security. It also discusses accomplishing security without failing standards from various organizations and using a flexible security model while remembering physical security. It summarizes that a flexible approach is needed given advancing technology and existing best practices should be leveraged, but a more complex risk mitigation matrix may be required long term which will be difficult for industries to address.