04 18-2018--netcat port-80_blue
•Download as PPTX, PDF•
0 likes•49 views
by alexander bitar
Report
Share
Report
Share
Recommended
More Related Content
What's hot
What's hot (20)
Network Penetration Testing Toolkit - Nmap, Netcat, and Metasploit Basics

Network Penetration Testing Toolkit - Nmap, Netcat, and Metasploit Basics
Similar to 04 18-2018--netcat port-80_blue
Similar to 04 18-2018--netcat port-80_blue (20)
Information Theft: Wireless Router Shareport for Phun and profit - Hero Suhar...

Information Theft: Wireless Router Shareport for Phun and profit - Hero Suhar...
SR-IOV, KVM and Emulex OneConnect 10Gbps cards on Debian/Stable

SR-IOV, KVM and Emulex OneConnect 10Gbps cards on Debian/Stable
Figure 3 TCP Session Hijacking Attack victims to execute the mali.pdf

Figure 3 TCP Session Hijacking Attack victims to execute the mali.pdf
More from Alexander Bitar
More from Alexander Bitar (20)
Recently uploaded
Recently uploaded (20)
Automating Business Process via MuleSoft Composer | Bangalore MuleSoft Meetup...

Automating Business Process via MuleSoft Composer | Bangalore MuleSoft Meetup...
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
Integration and Automation in Practice: CI/CD in Mule Integration and Automat...

Integration and Automation in Practice: CI/CD in Mule Integration and Automat...
Breaking the Kubernetes Kill Chain: Host Path Mount

Breaking the Kubernetes Kill Chain: Host Path Mount
Neo4j - How KGs are shaping the future of Generative AI at AWS Summit London ...

Neo4j - How KGs are shaping the future of Generative AI at AWS Summit London ...
Factors to Consider When Choosing Accounts Payable Services Providers.pptx

Factors to Consider When Choosing Accounts Payable Services Providers.pptx
#StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024

#StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024
08448380779 Call Girls In Friends Colony Women Seeking Men

08448380779 Call Girls In Friends Colony Women Seeking Men
Transcript: #StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024

Transcript: #StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024
Presentation on how to chat with PDF using ChatGPT code interpreter

Presentation on how to chat with PDF using ChatGPT code interpreter
[2024]Digital Global Overview Report 2024 Meltwater.pdf![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[2024]Digital Global Overview Report 2024 Meltwater.pdf
Enhancing Worker Digital Experience: A Hands-on Workshop for Partners

Enhancing Worker Digital Experience: A Hands-on Workshop for Partners
Handwritten Text Recognition for manuscripts and early printed texts

Handwritten Text Recognition for manuscripts and early printed texts
04 18-2018--netcat port-80_blue
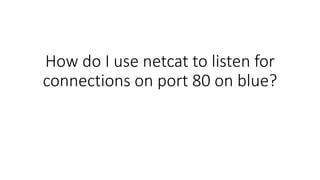
- 1. How do I use netcat to listen for connections on port 80 on blue?
- 2. 1. Turn on red and blue VM’s. Log onto root for blue. • Execute the following command : ‘nc –lvp 80’ • ‘nc’ is the netcat command • -l is the listening flag where it will listen to a specified port ( -p ) • -v is the verbose flag where output is generated onto the terminal. • -p is the port command, where we specify a port to do a task on ( in this case we are listening to port 80 ) • ‘80’ is the specified port
- 3. 2. Execute ‘nc –lvp 80’
- 4. You are now listening on port 80 on blue! • Go onto red and execute the following as root : ‘nc –nv 10.0.2.12 80’ • -n is a flag. This is used to stop a DNS lookup. • -v is verbose, where output is printed. • We are connecting to ‘10.0.2.12’ and port ‘80’ on that machine. • Once executed, type some text to test the connection. You should see the text written on red appear on blue!
- 5. Output on both machines :
- 6. Once we cancel netcat on the connecting machine ( red).. Blue stops to listen :