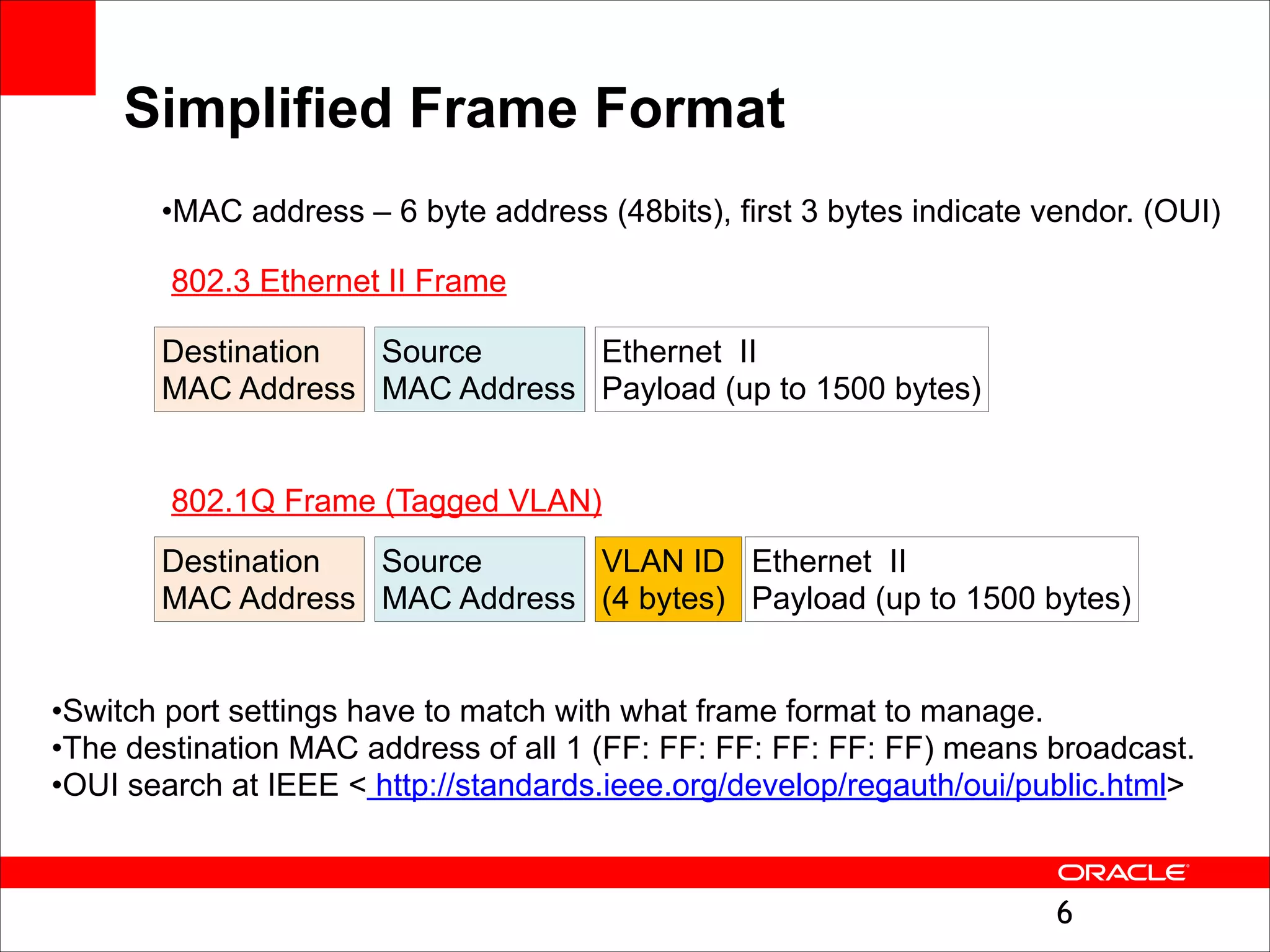
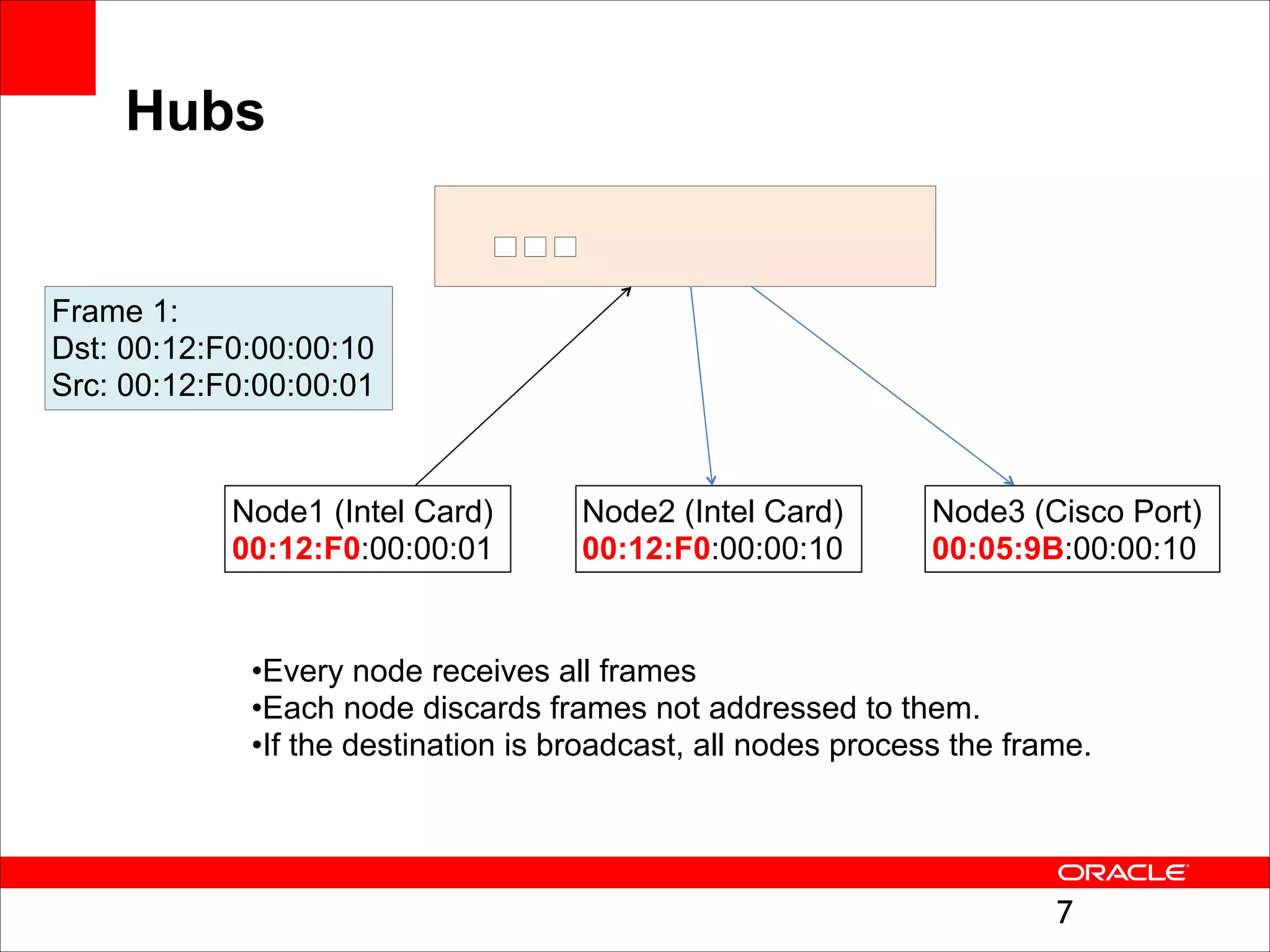
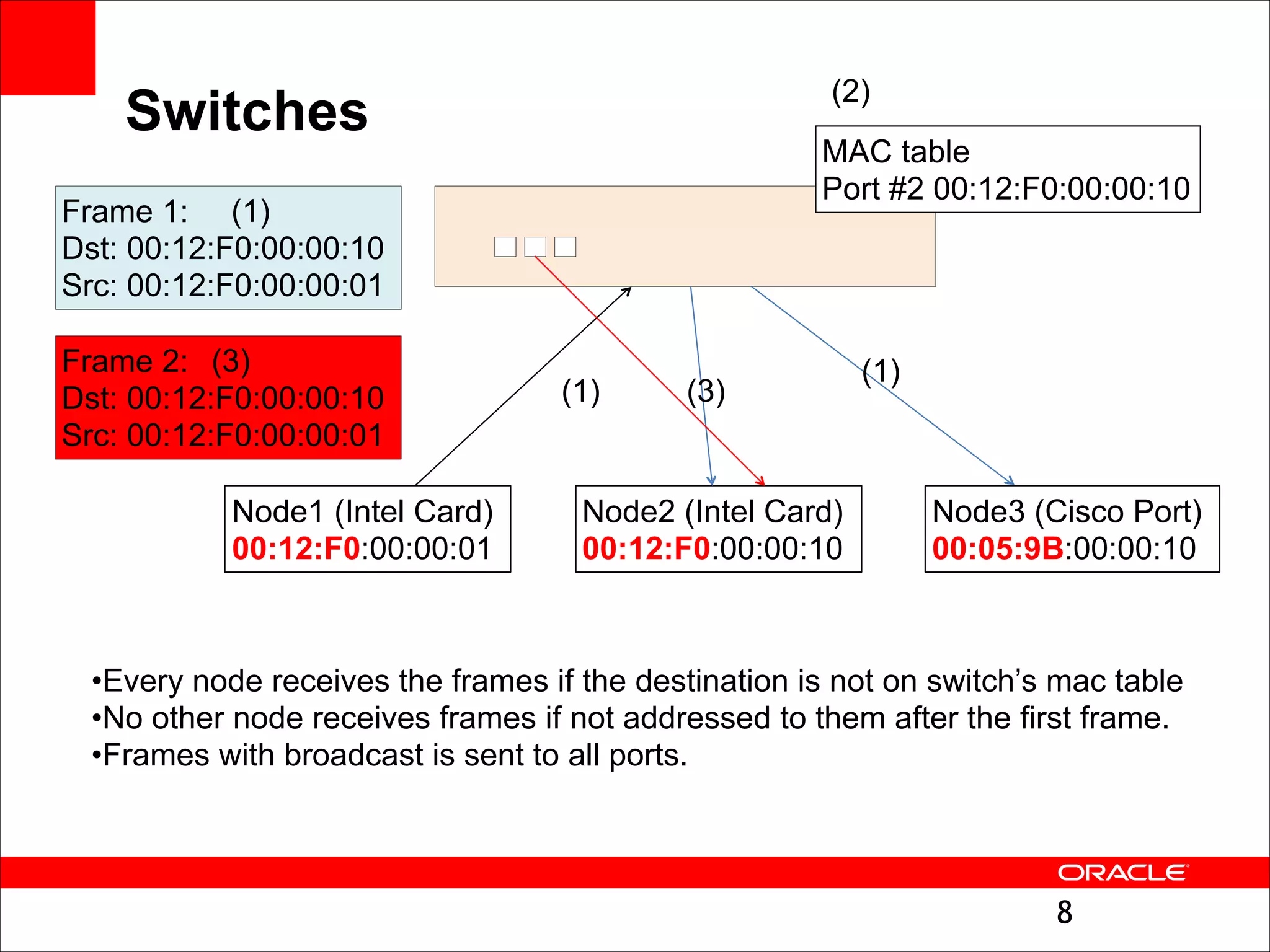
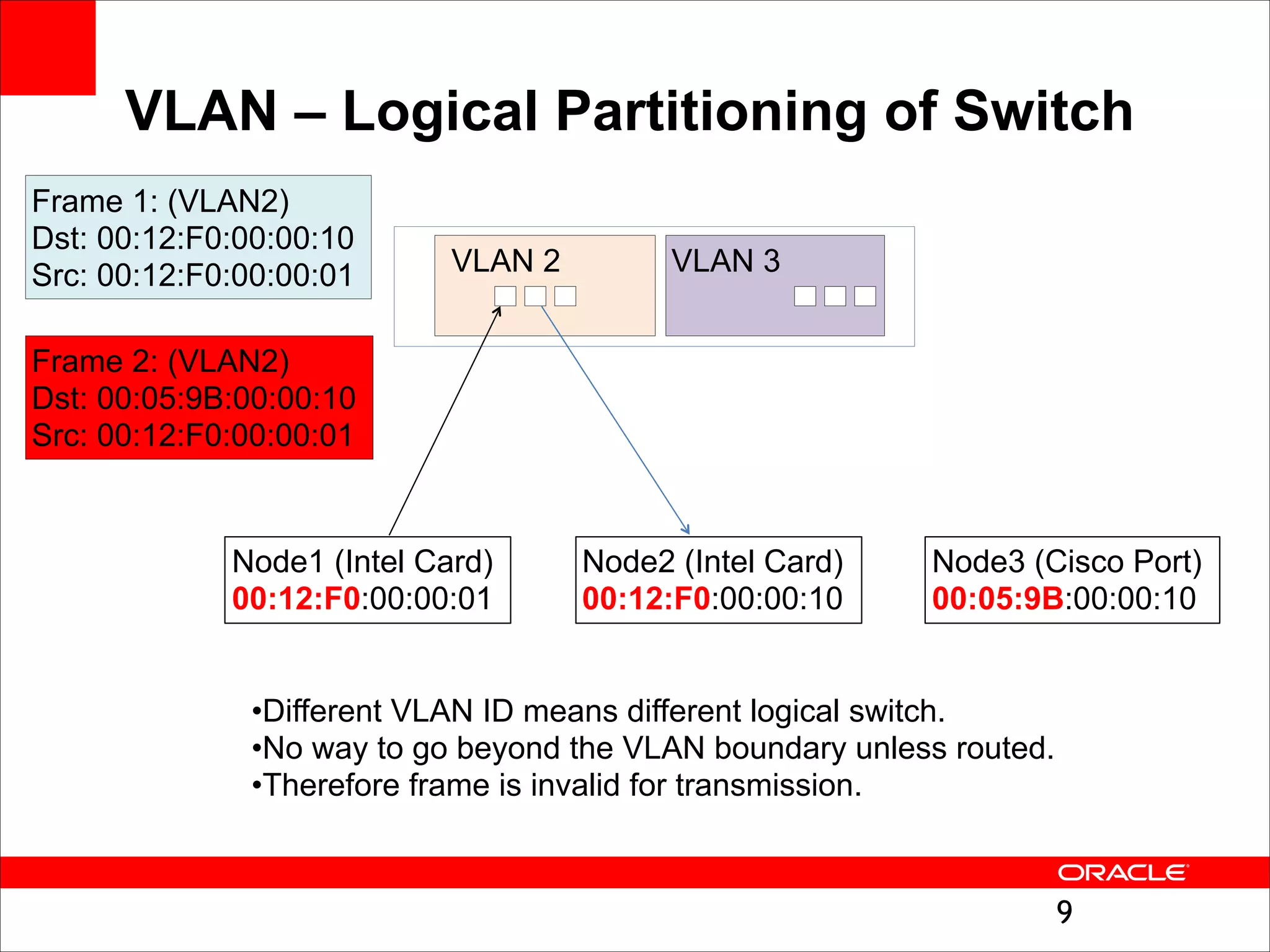
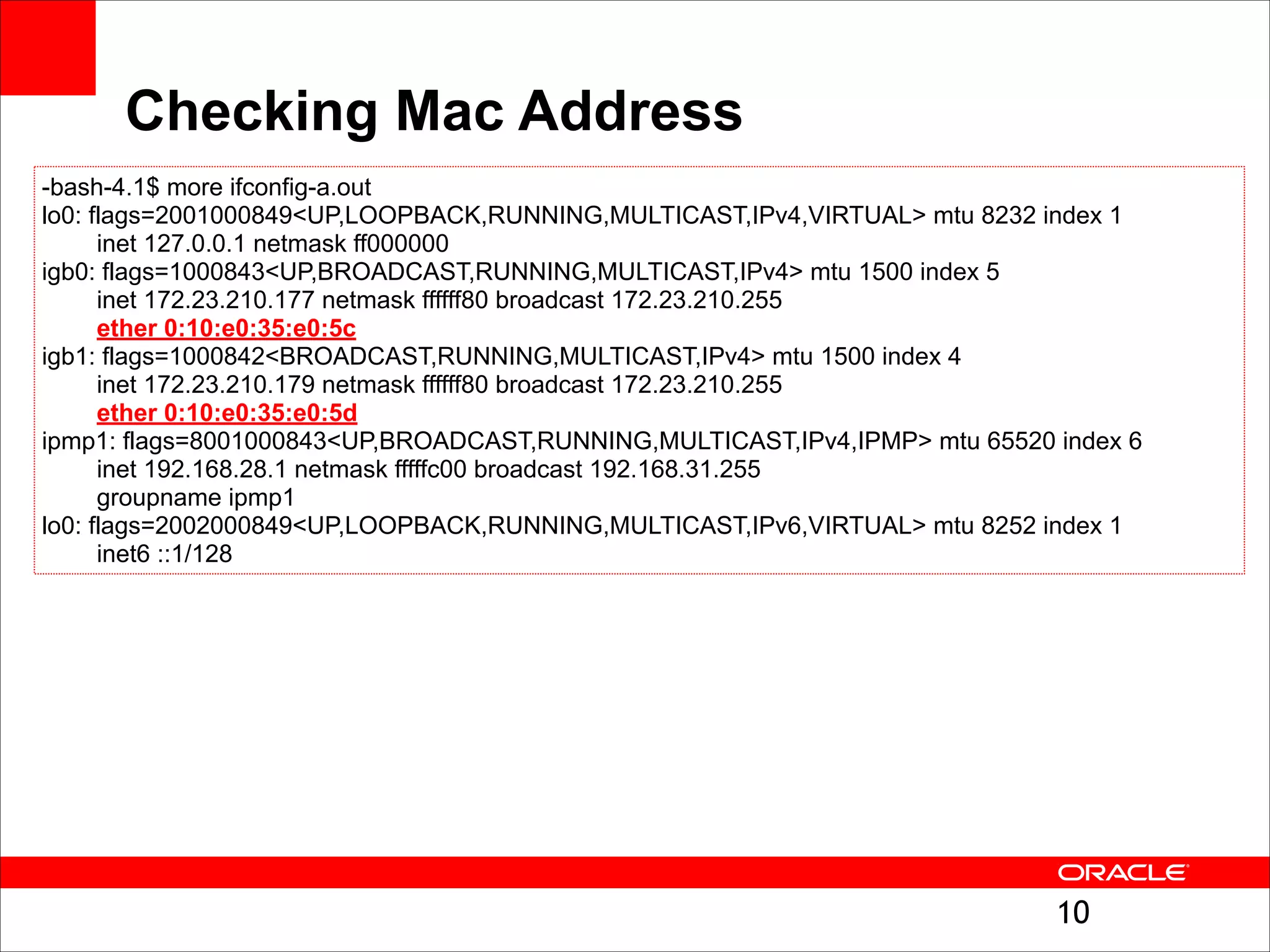
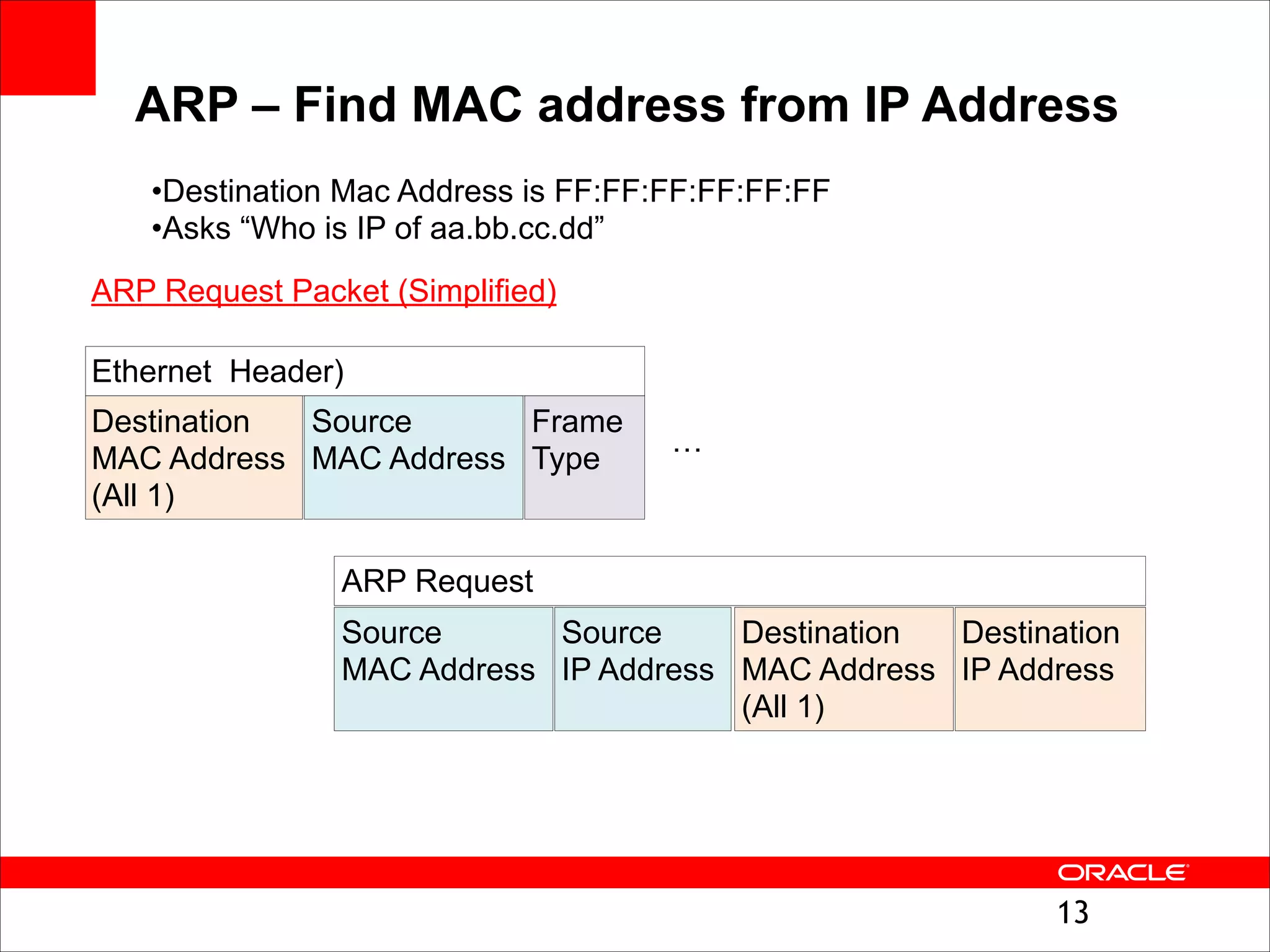
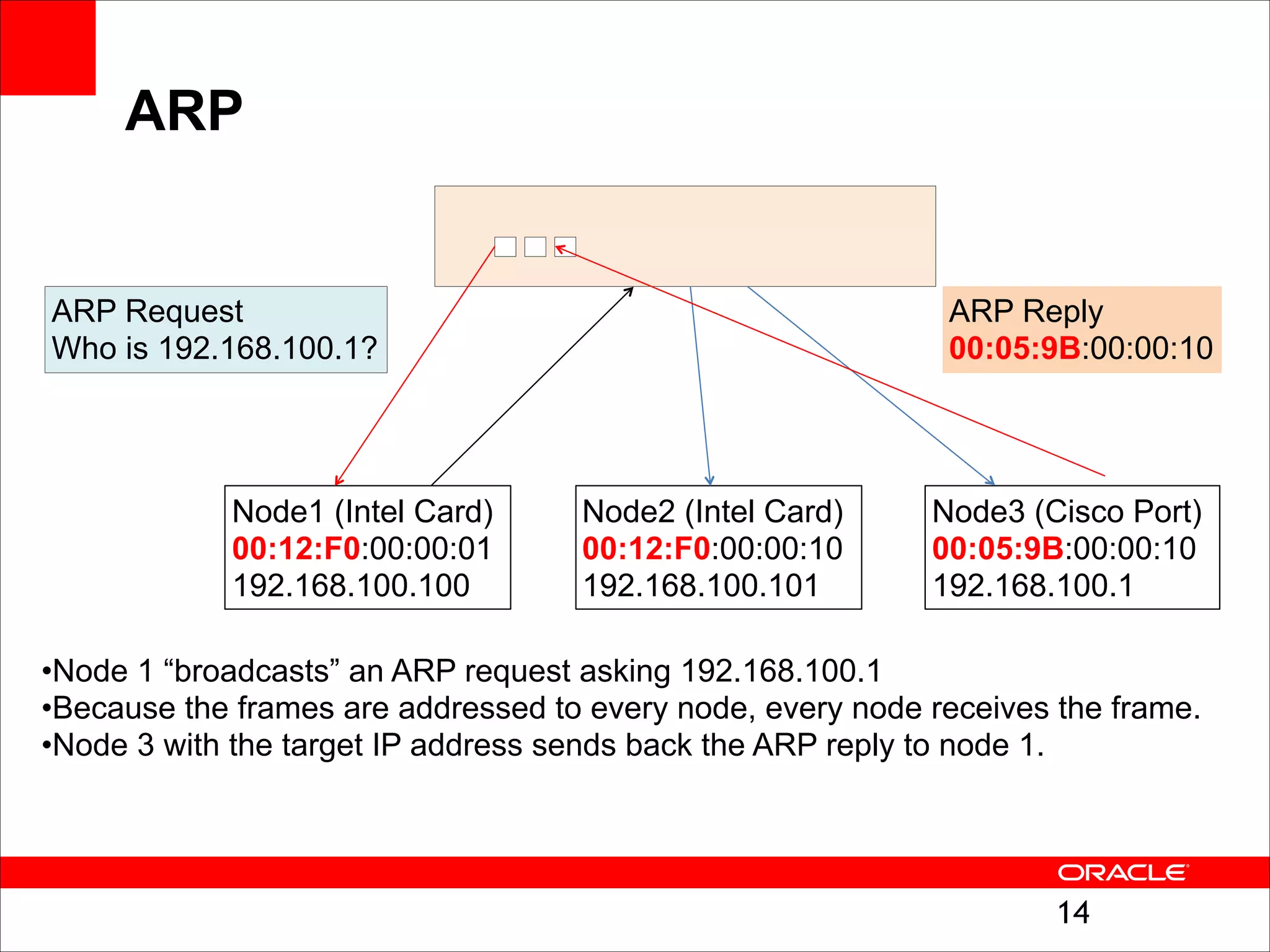
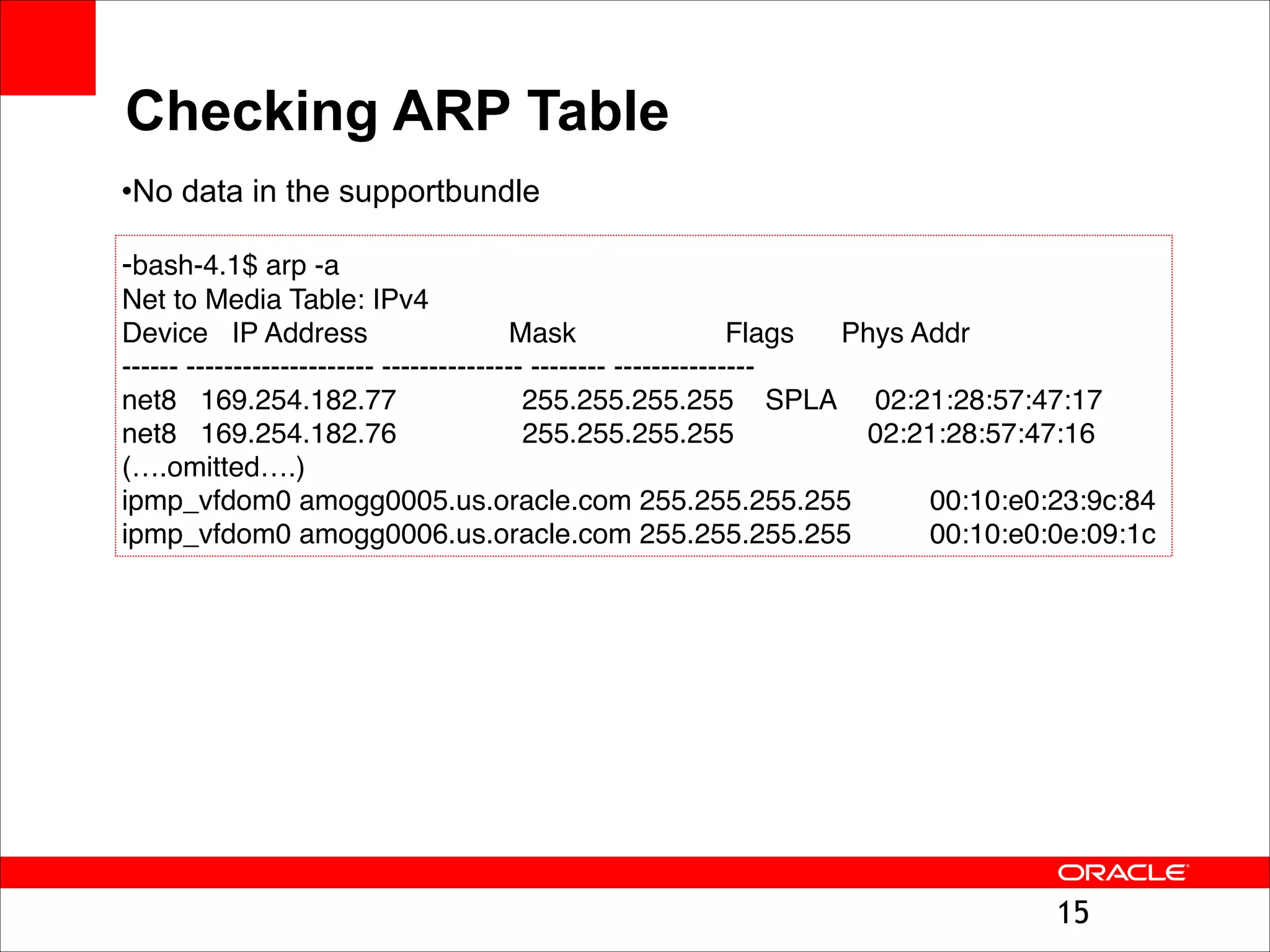
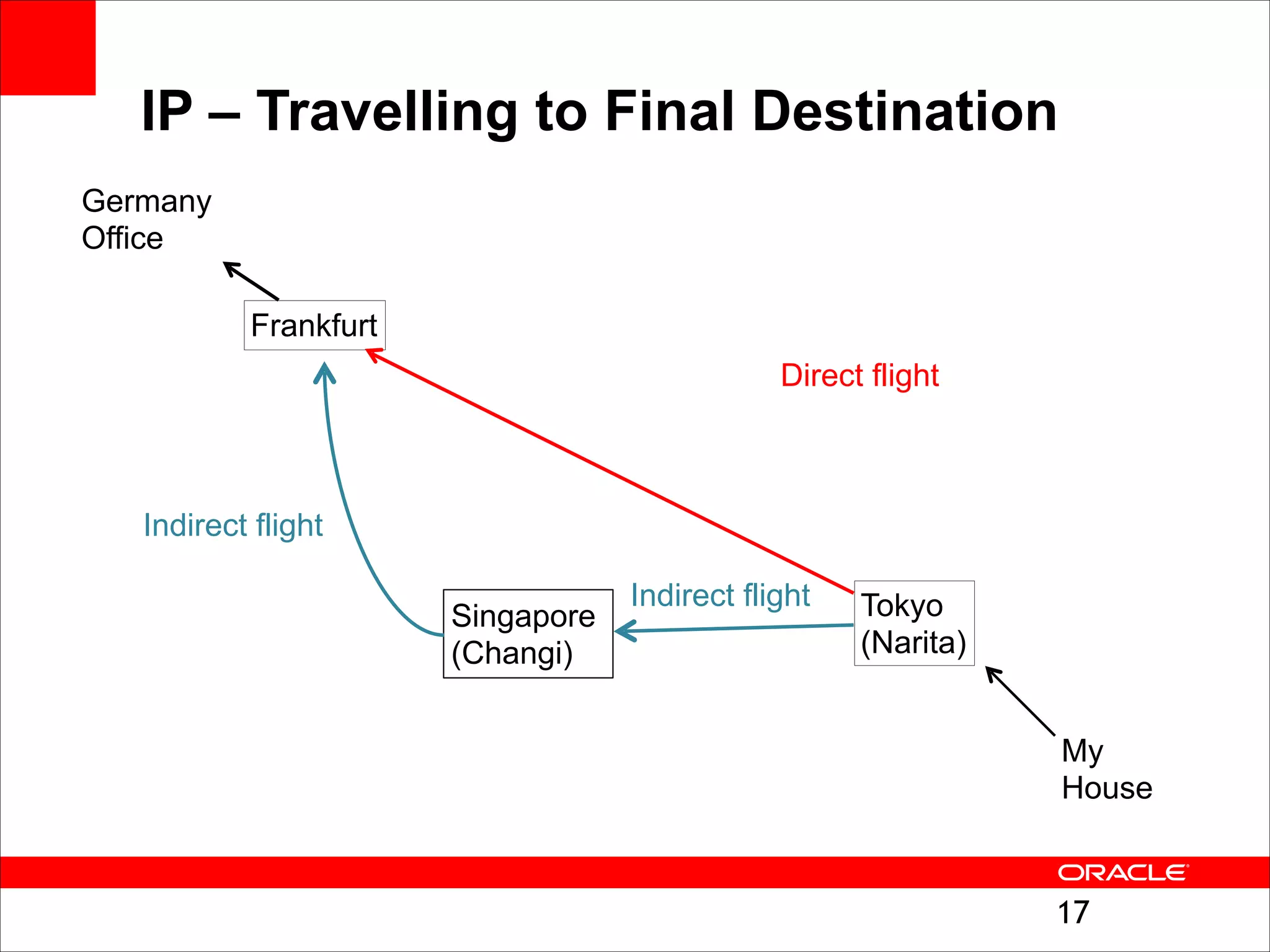
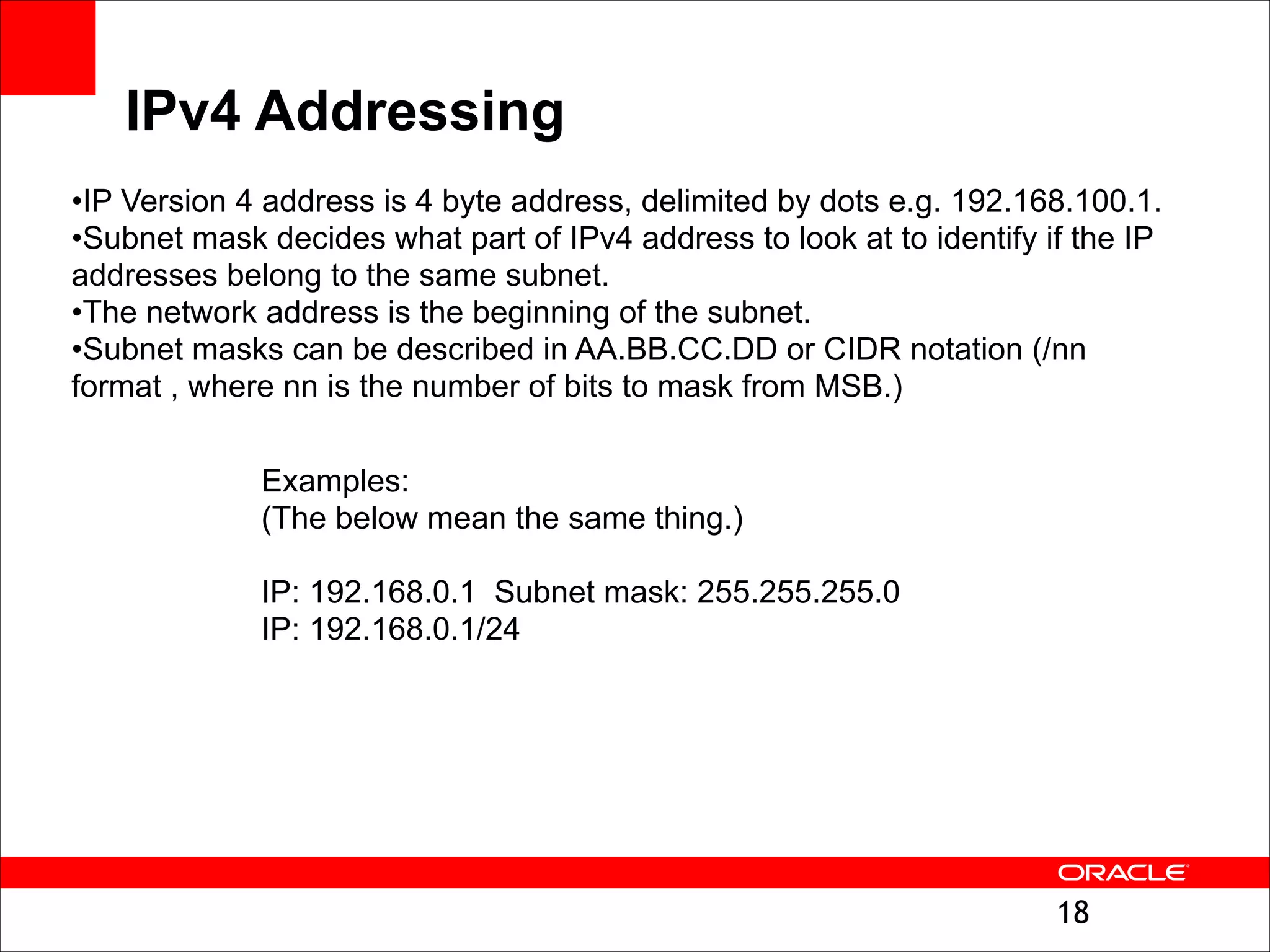
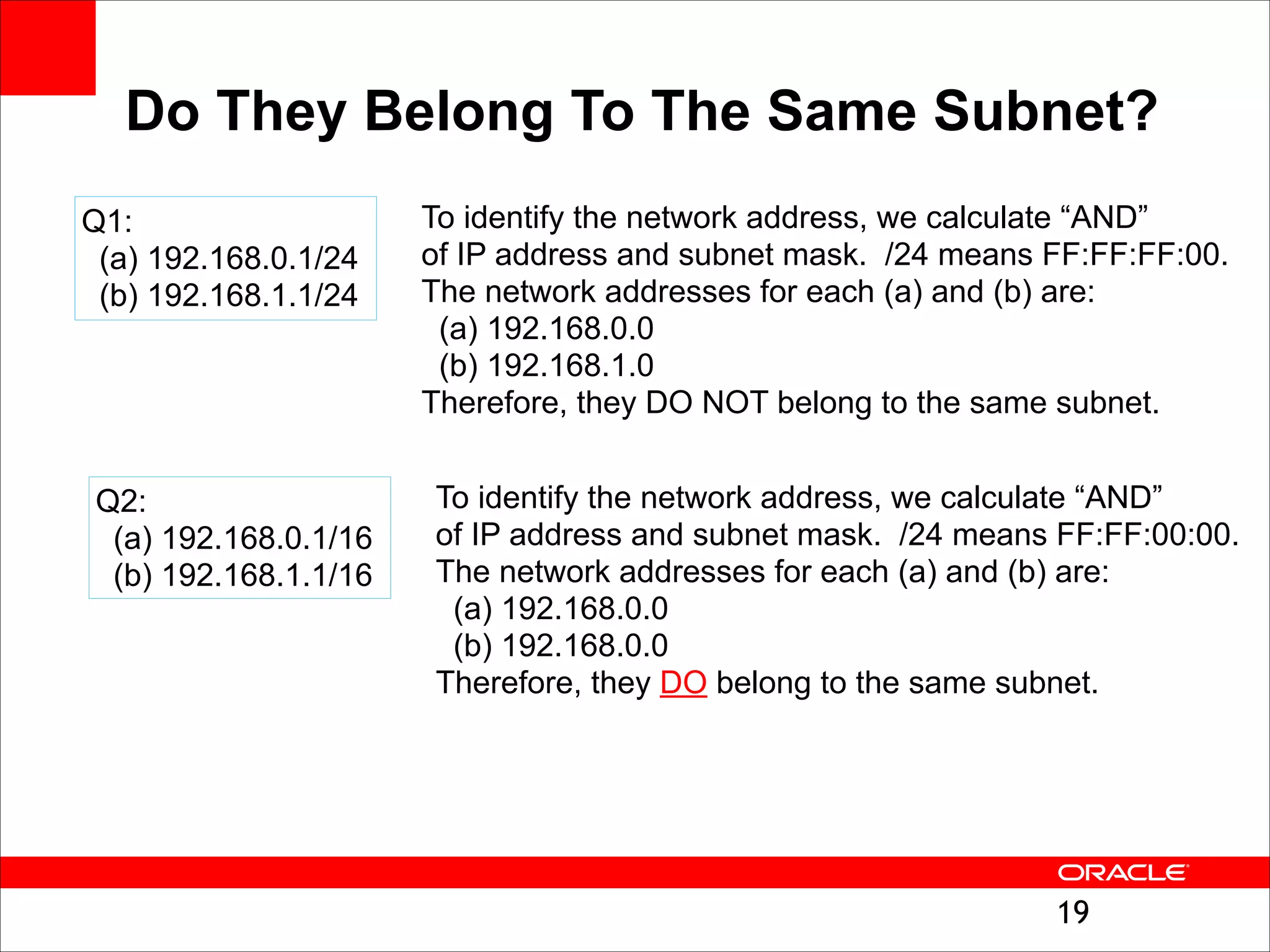
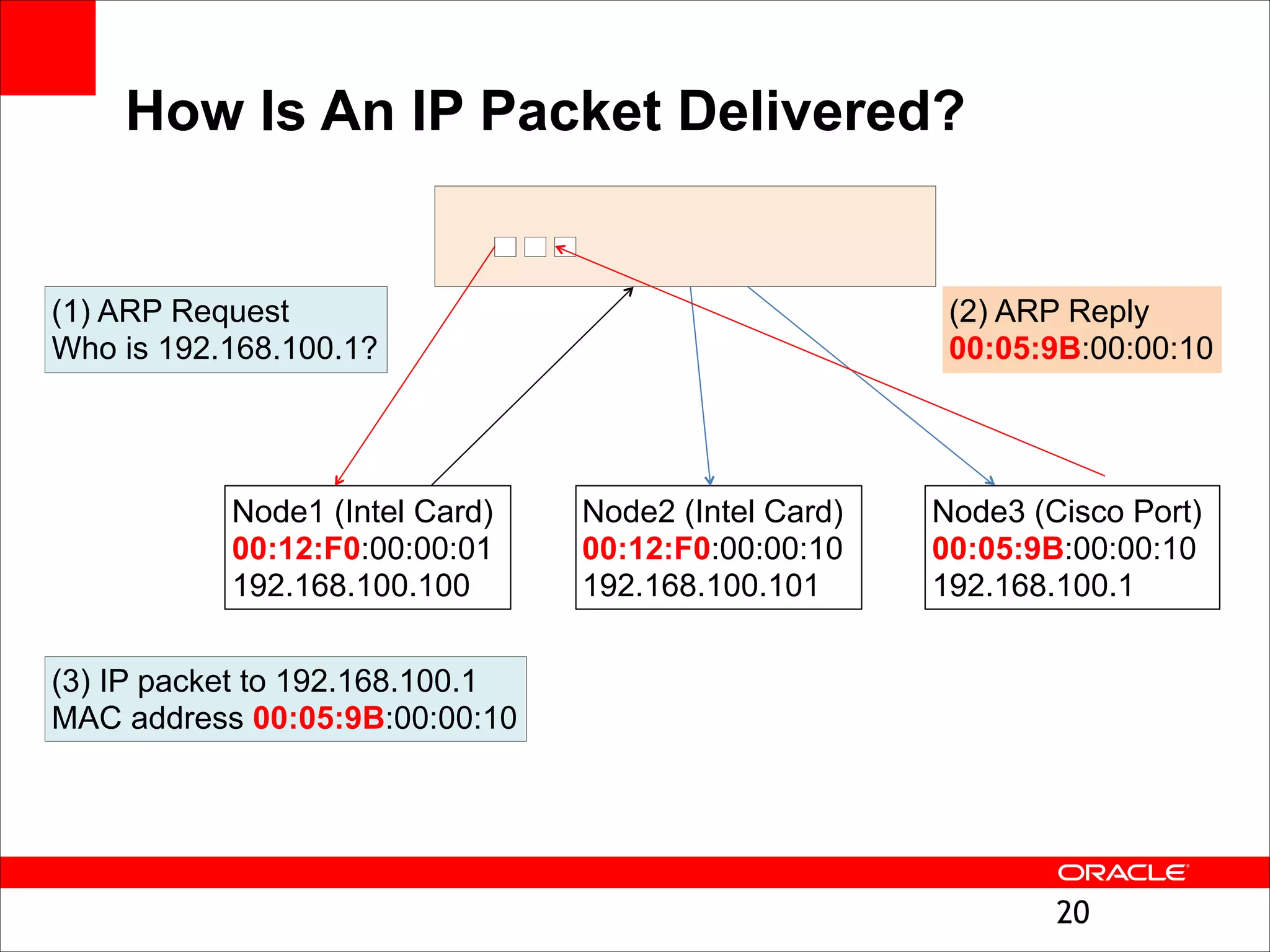
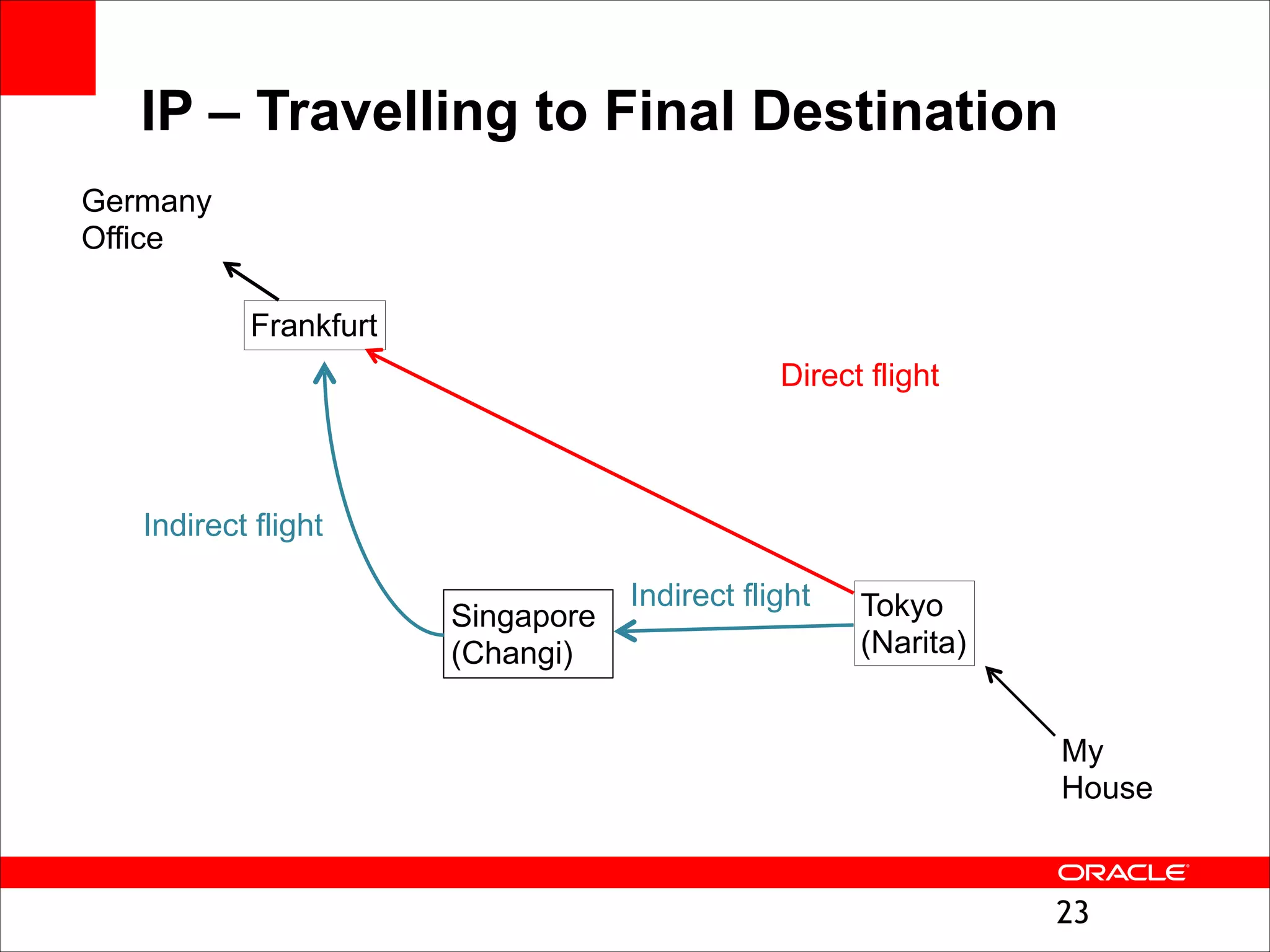
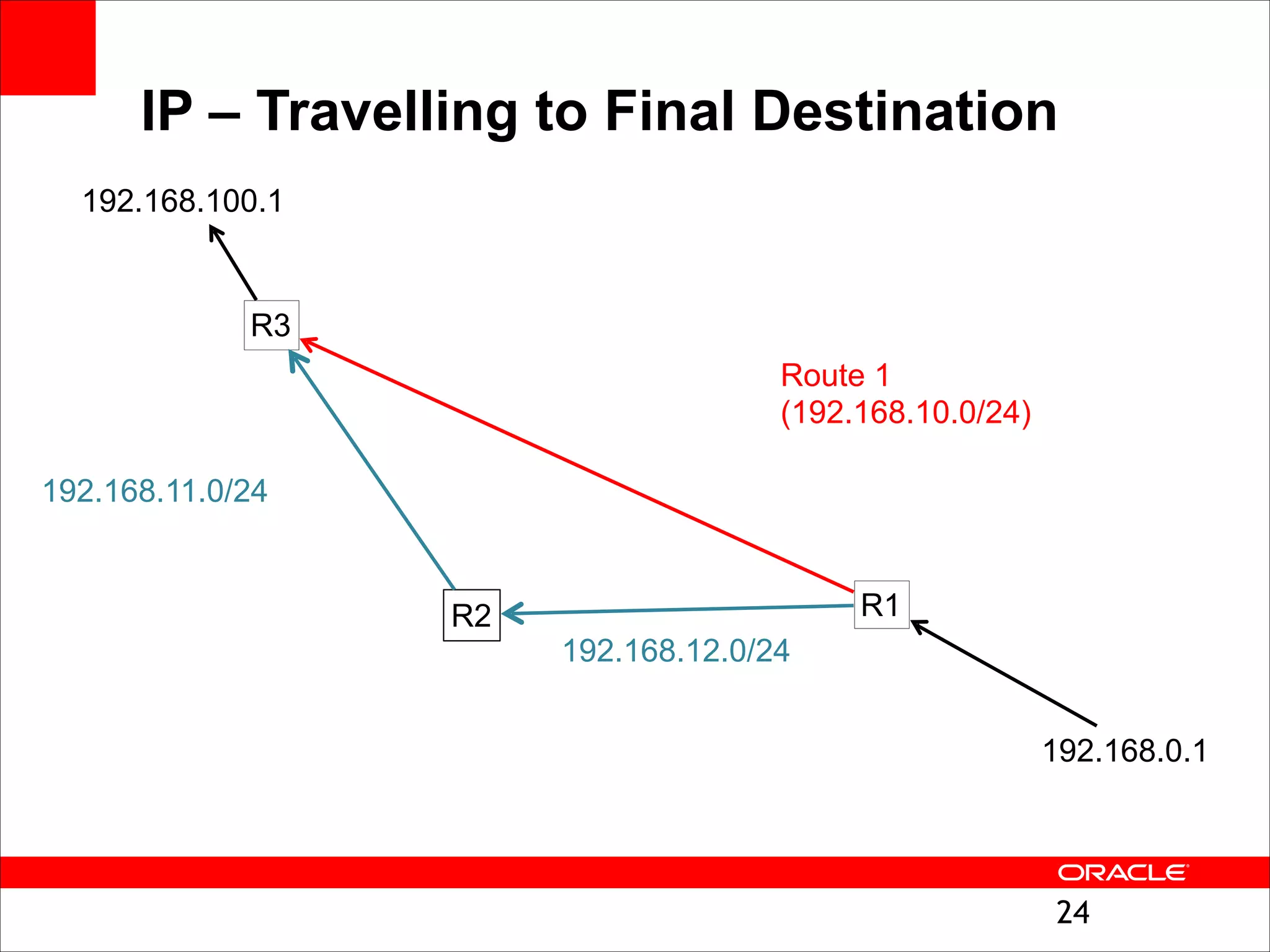
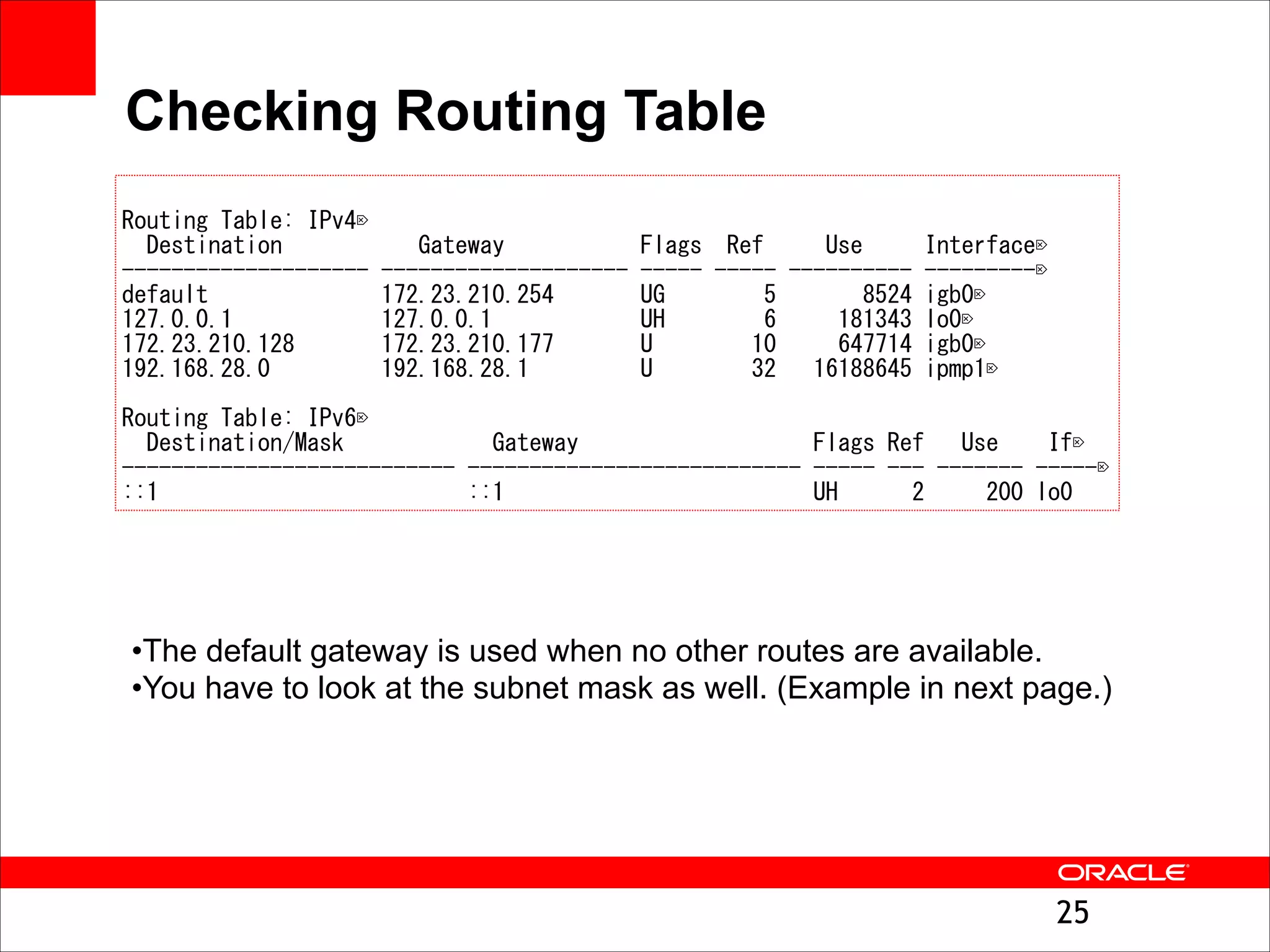
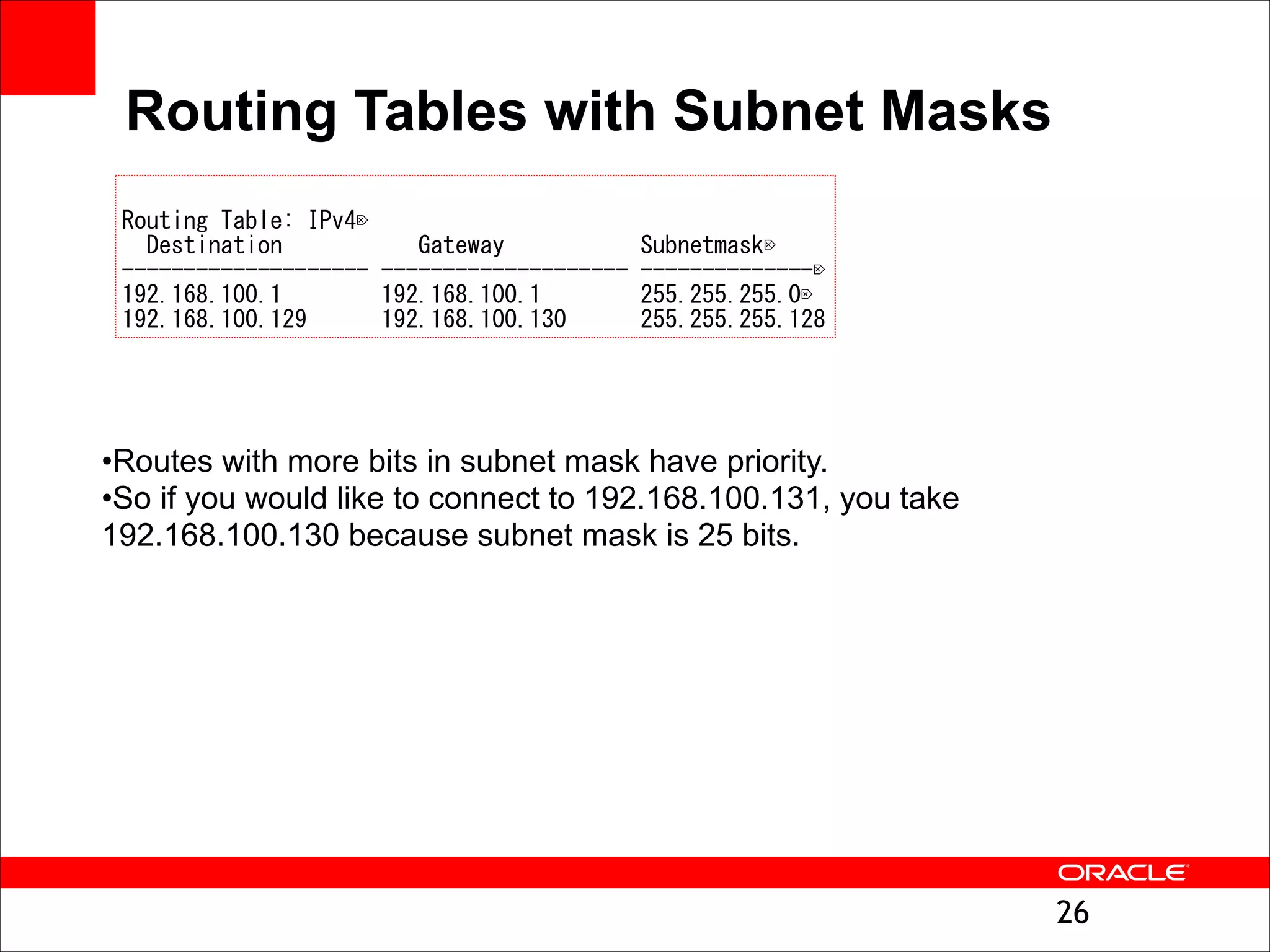
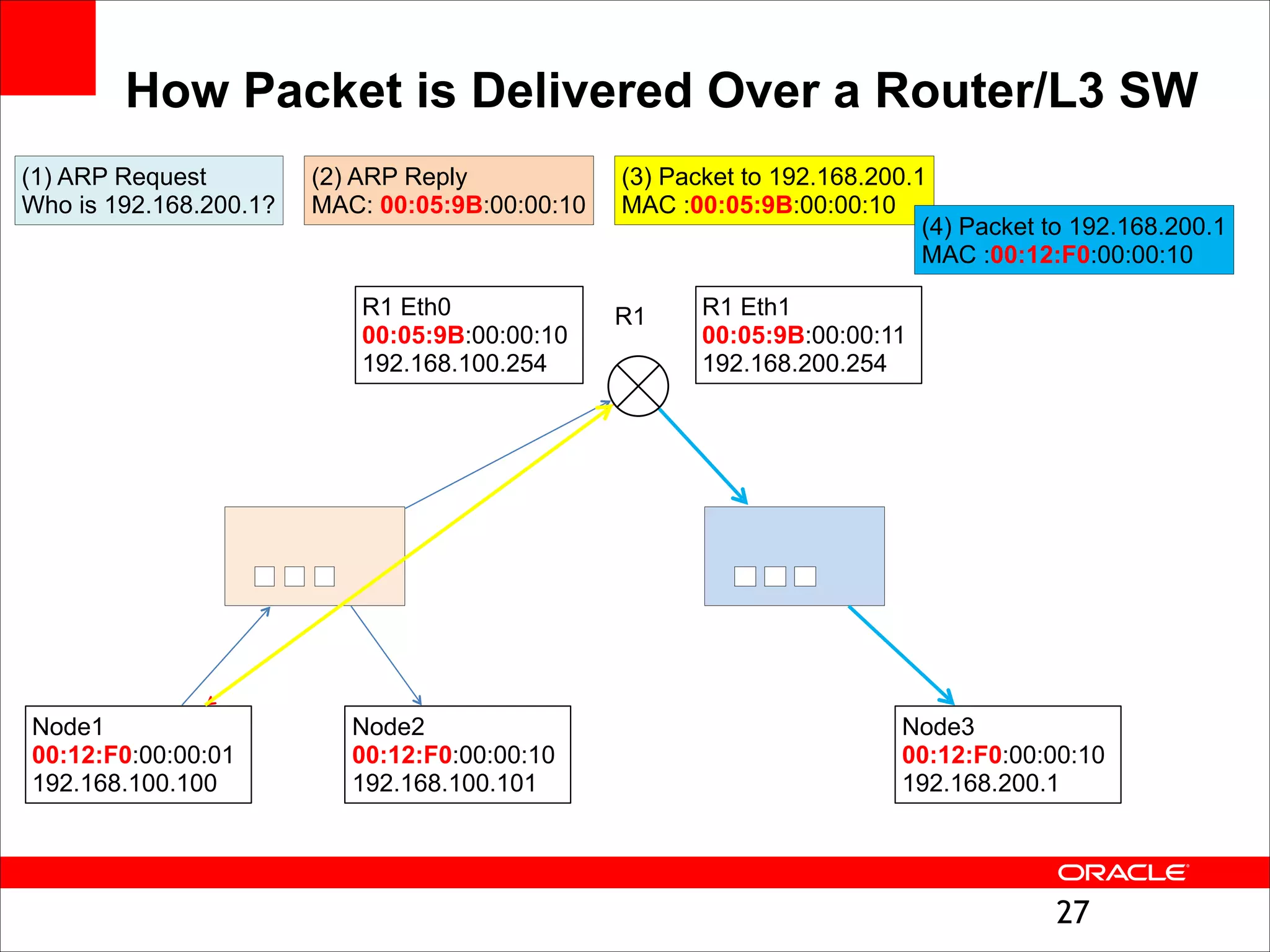
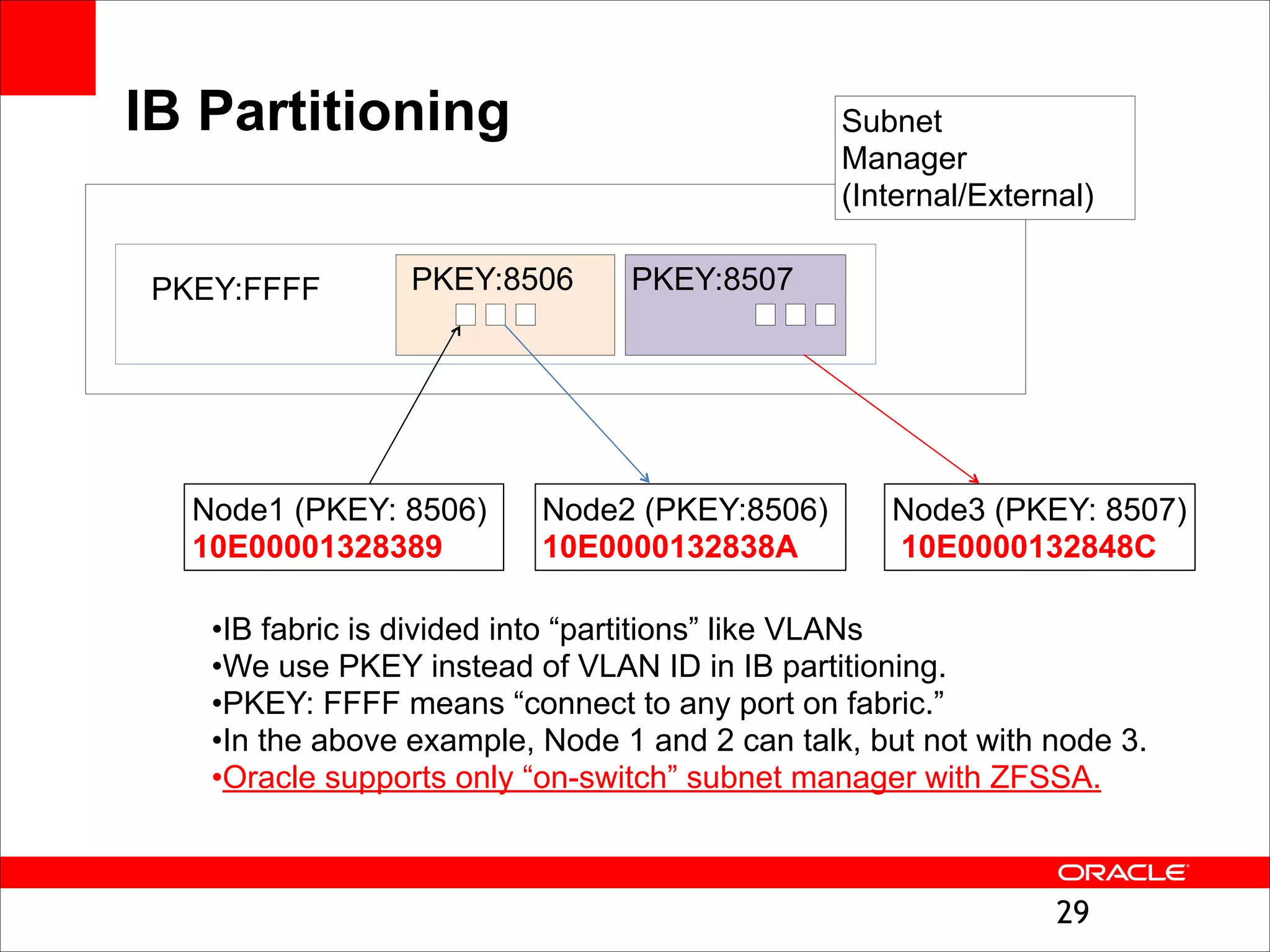
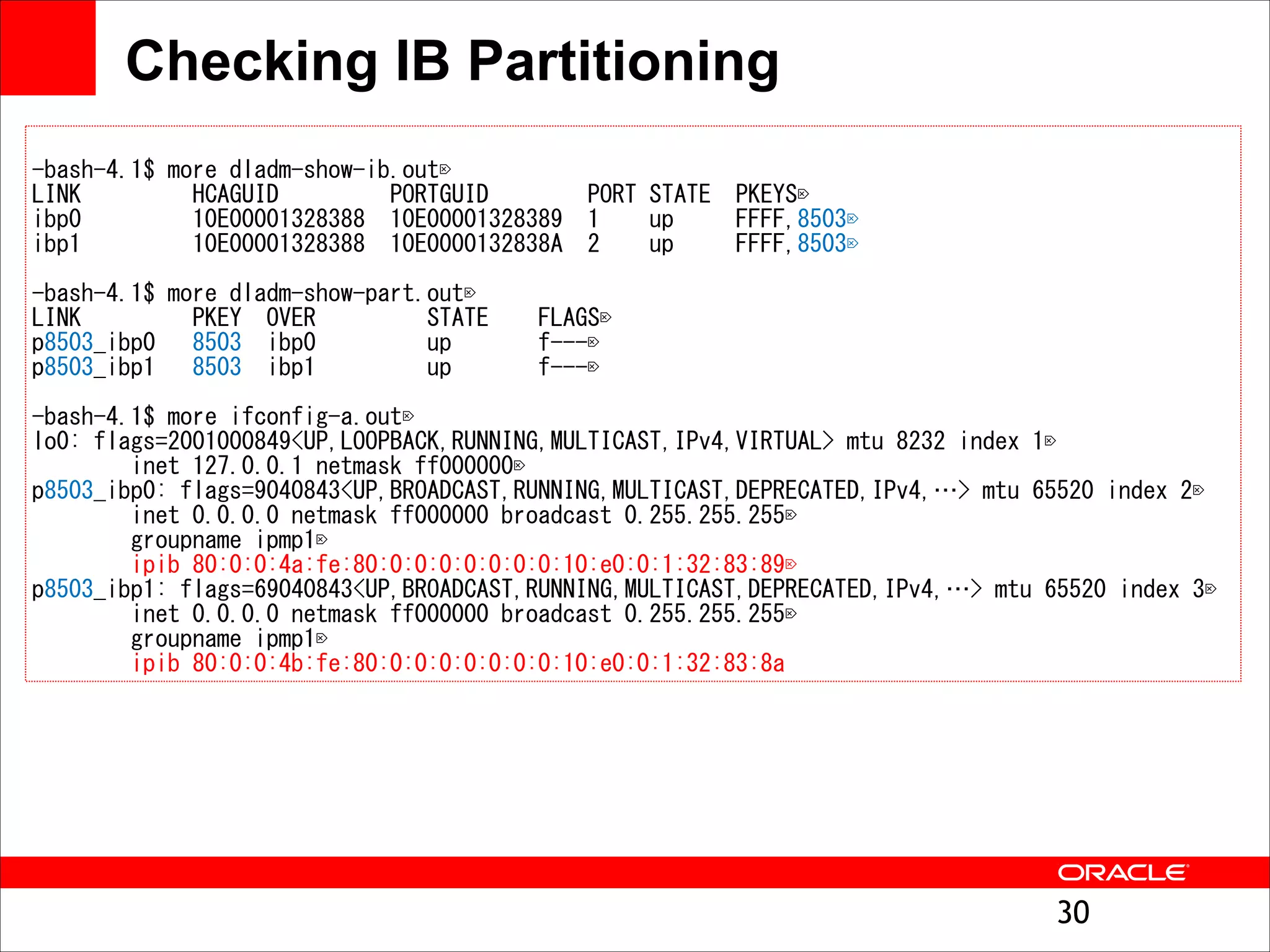
The document outlines the basics of networking concepts, focusing on Ethernet frames, ARP, IP addressing, routing, and InfiniBand partitioning. It explains how data is transmitted across networks via MAC addresses, the importance of VLANs, and the role of ARP in mapping IP addresses to MAC addresses. Additionally, it covers tools and commands for checking network configurations and routing tables.