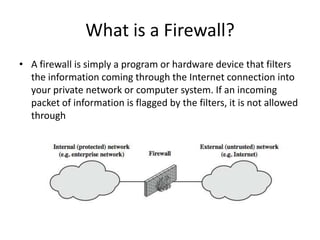
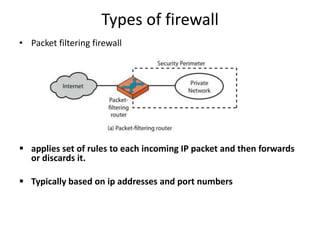
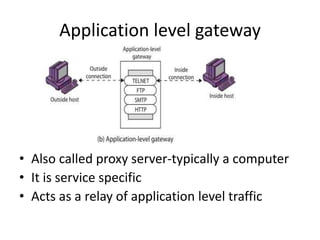
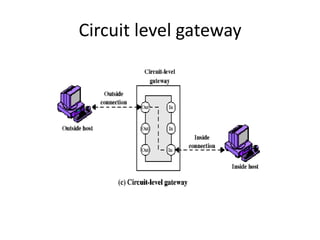
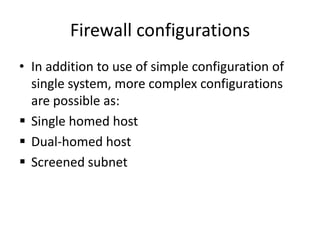
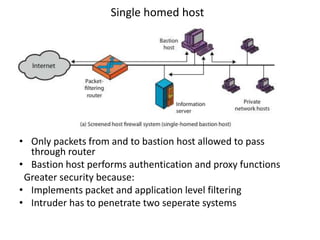
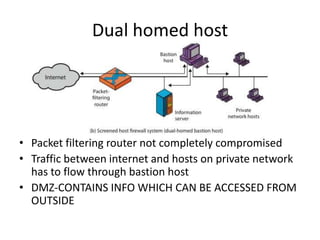
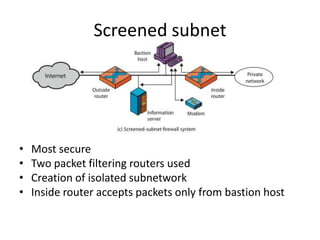
This document discusses firewalls, including what they are, their purposes, types, configurations, and limitations. A firewall is a program or device that filters network traffic and blocks unauthorized access. Firewalls protect systems and networks from threats, provide controlled access to and from the internet, and ensure only approved traffic passes through. There are different types of firewalls that use packet filtering, application proxies, or circuit gateways to screen for threats. Firewalls can be configured as single hosts, dual-hosted, or in screened subnets for increased security. However, firewalls cannot protect from all attacks and internal/virus threats.