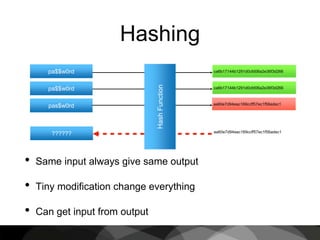
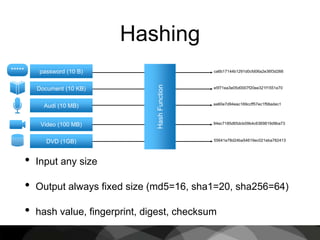
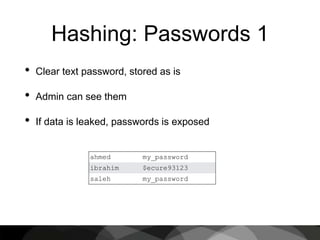
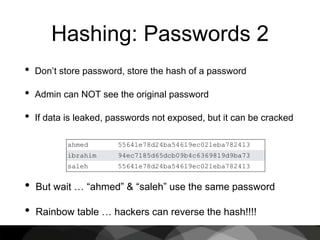
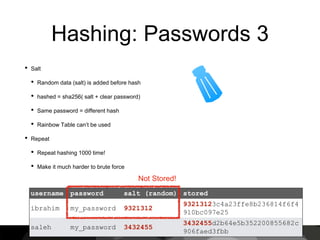
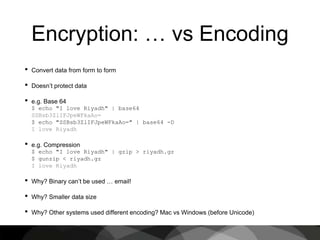
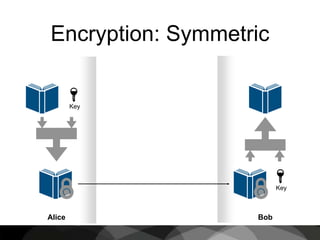
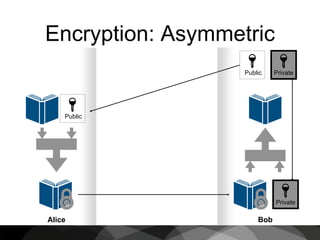
This document provides an introduction to cryptography, focusing on hashing, encryption, and PGP (Pretty Good Privacy). It explains the differences between hashing and encryption, and discusses password security, symmetric and asymmetric encryption, and the use of keys in secure communication. The document also delves into practical aspects of PGP for secure email communication, signing messages, and the importance of public key infrastructure.