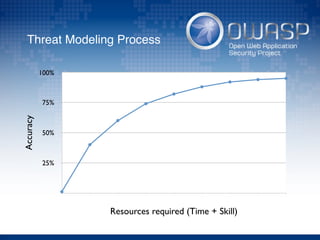
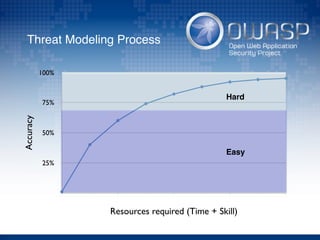
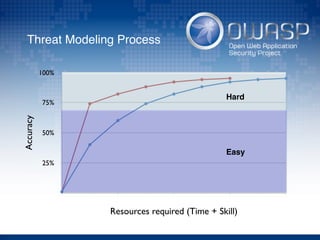
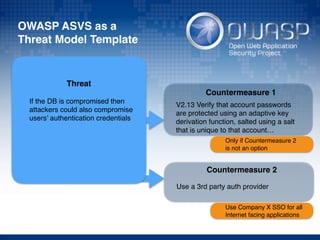
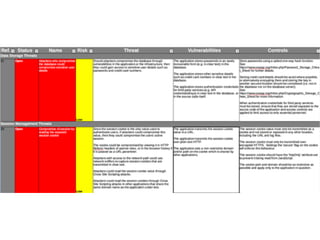
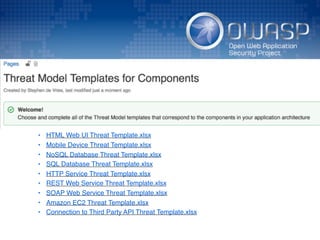
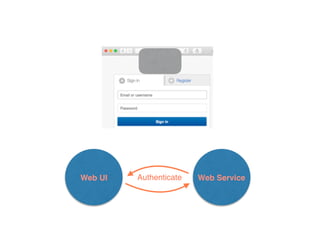
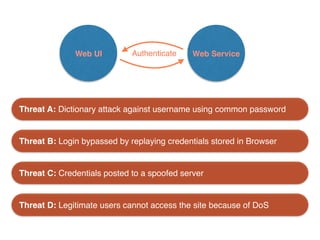
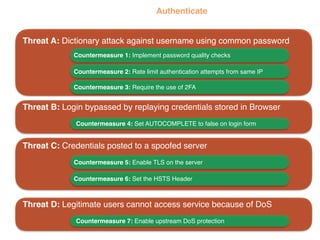
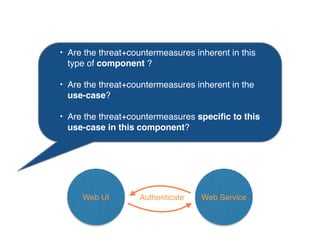
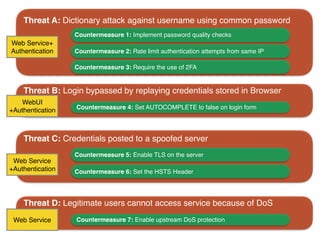
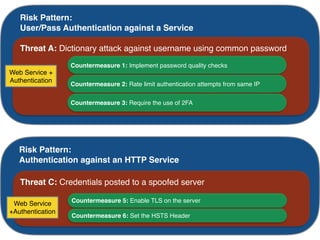
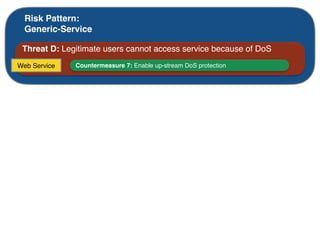
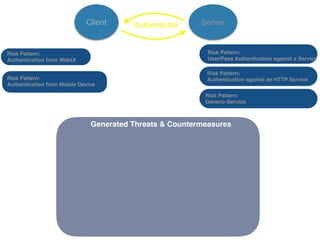
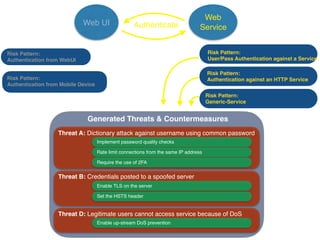
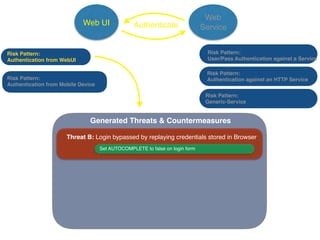
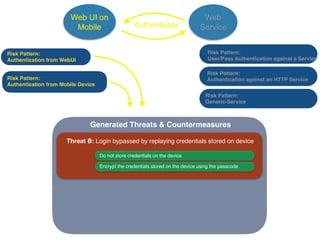
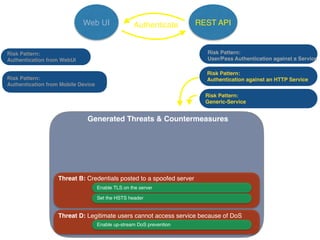
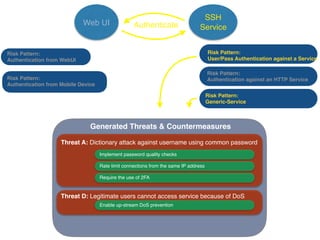
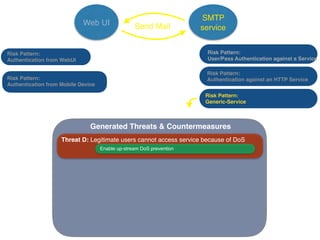
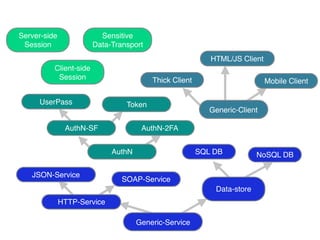
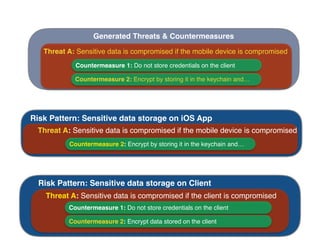
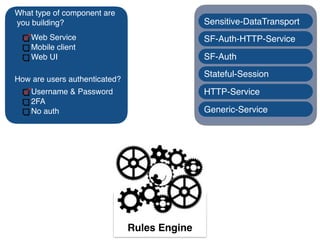
The document discusses using architectural risk patterns to help speed up and scale the threat modeling process. It proposes decomposing common threat modeling templates into reusable risk patterns that can be combined based on system components and authentication methods. Rules engines can then automatically generate threats and countermeasures by inheriting from relevant risk patterns. The approach aims to make threat modeling faster, more consistent and create a shared knowledge base of threats and countermeasures. However, it is noted the results rely on the quality of the input and checklists could short-circuit deeper analysis of issues.