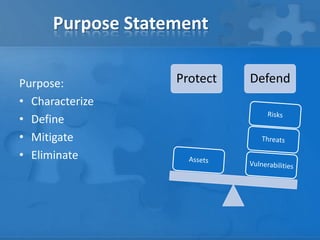
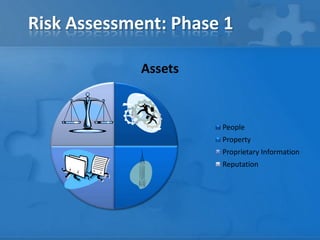
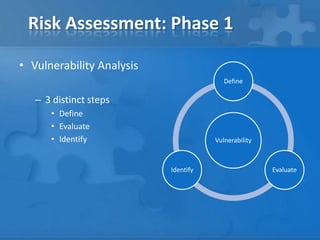
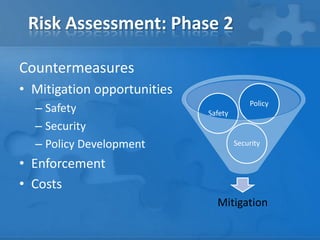
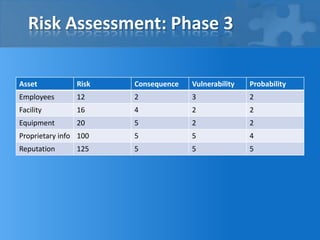
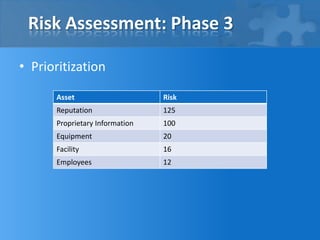
This document outlines the phases and steps of completing a risk analysis. It discusses (1) analyzing risks by identifying assets, threats, vulnerabilities and risks; (2) developing countermeasures through mitigation opportunities and policy planning; and (3) applying the process in practice using a small business example. The goal is to characterize, define, mitigate and eliminate risks to protect assets.