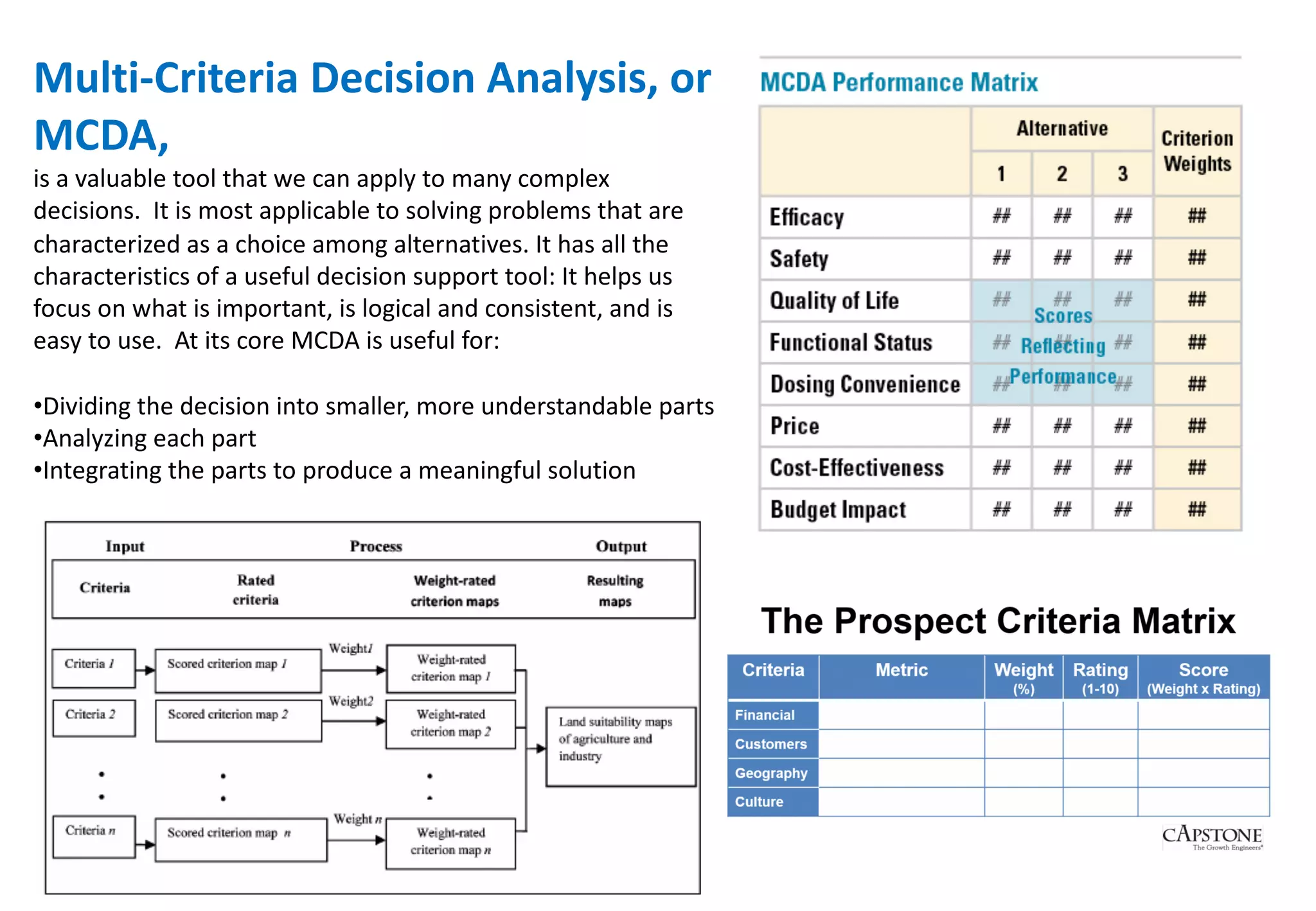
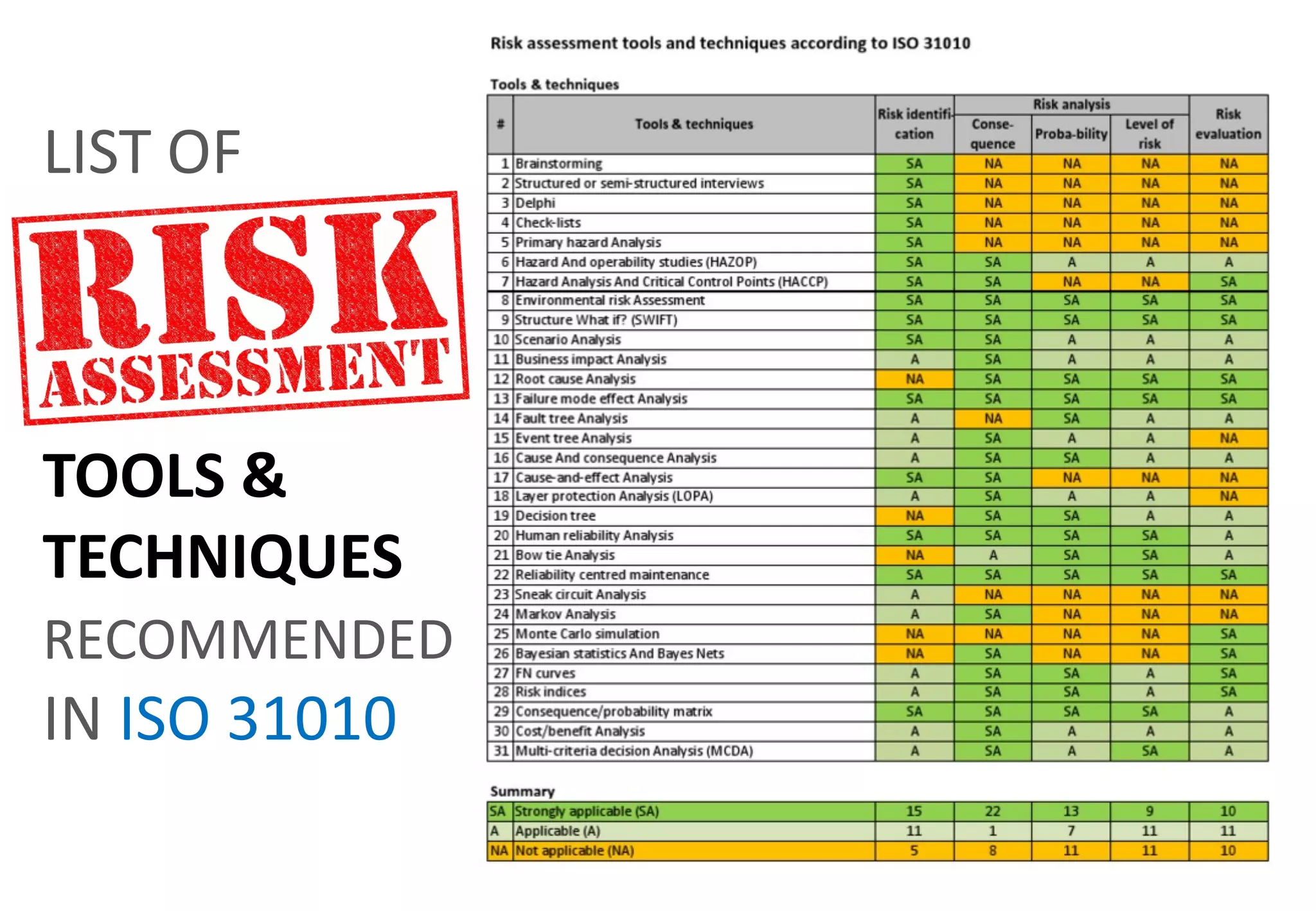
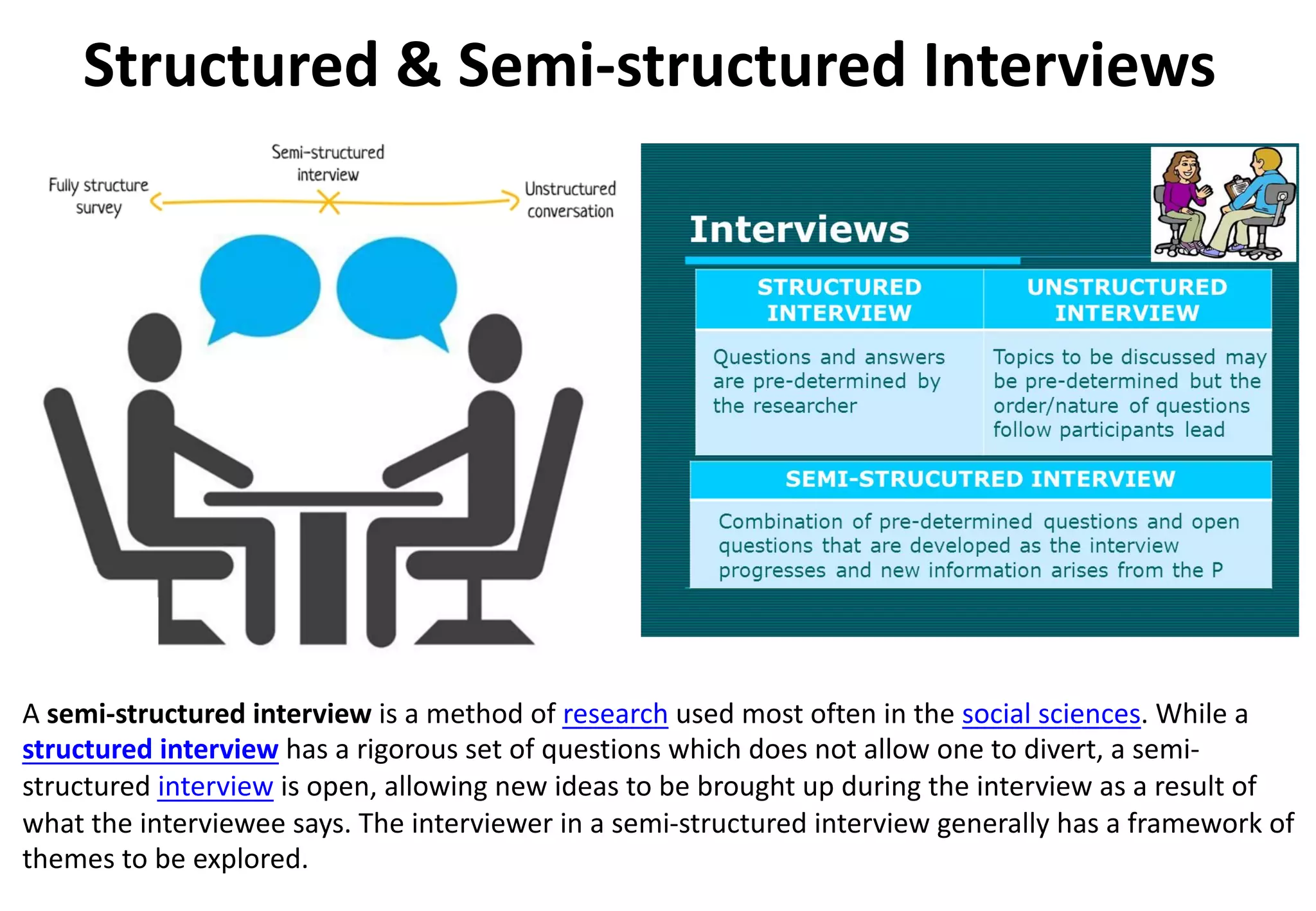
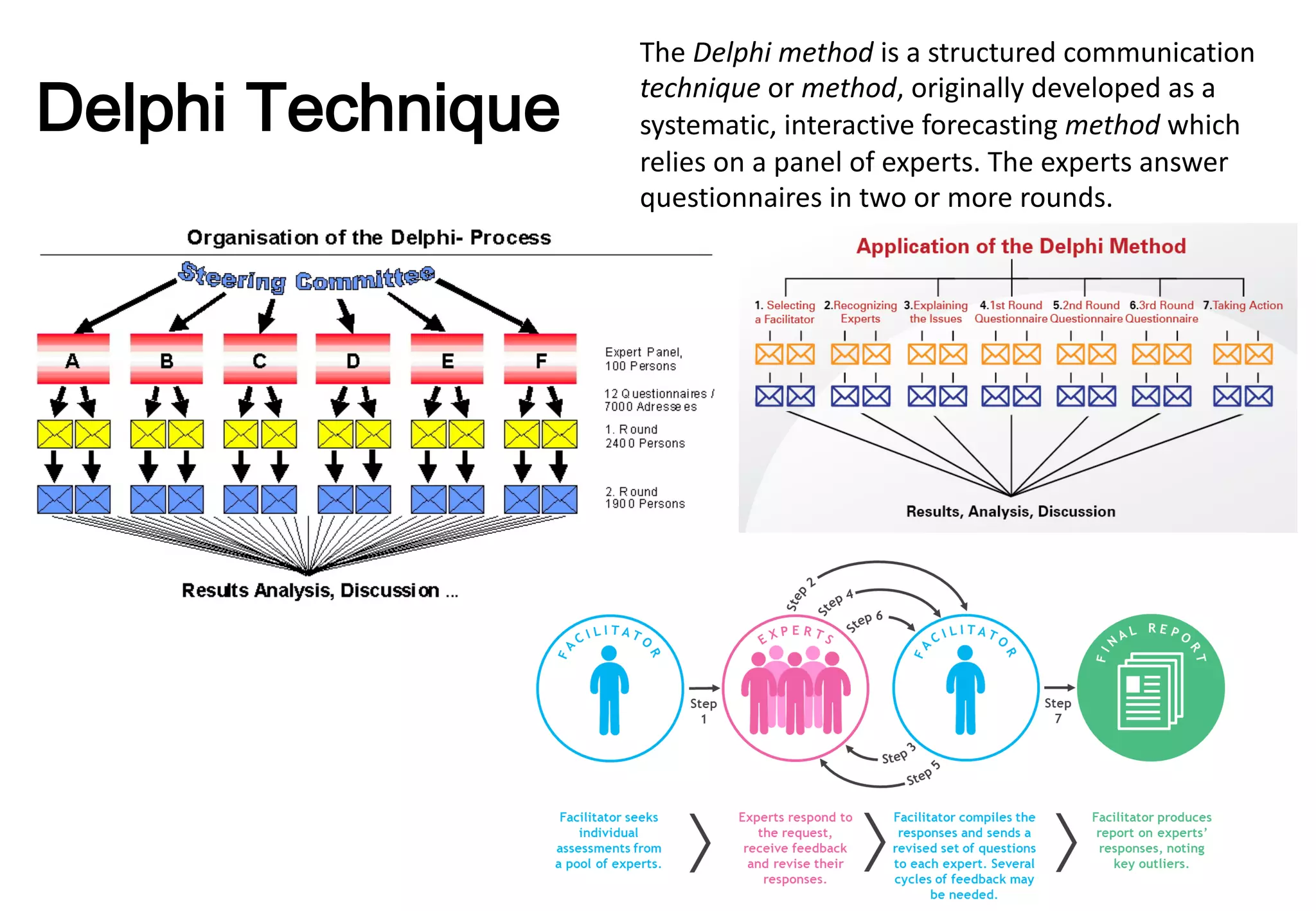
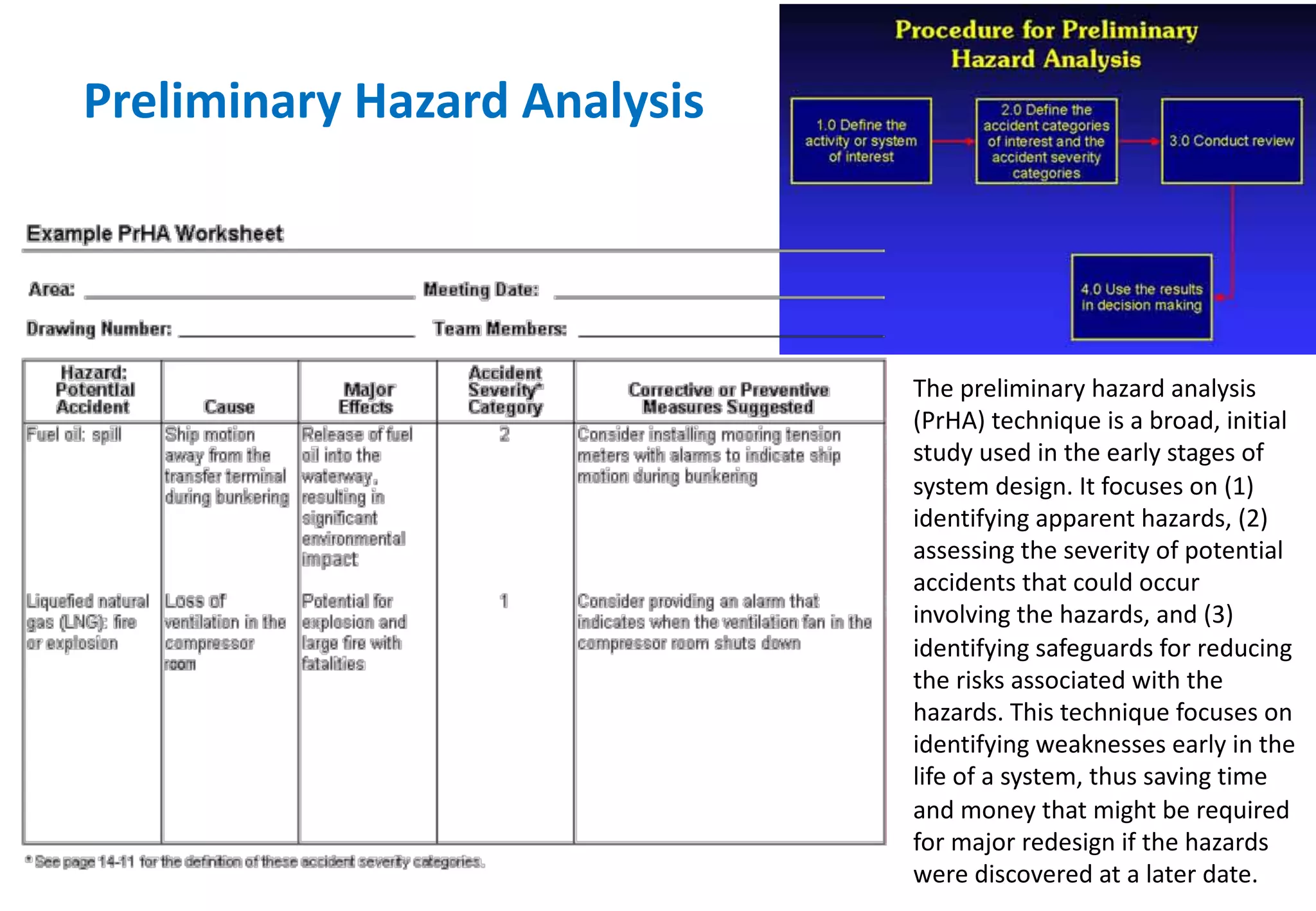
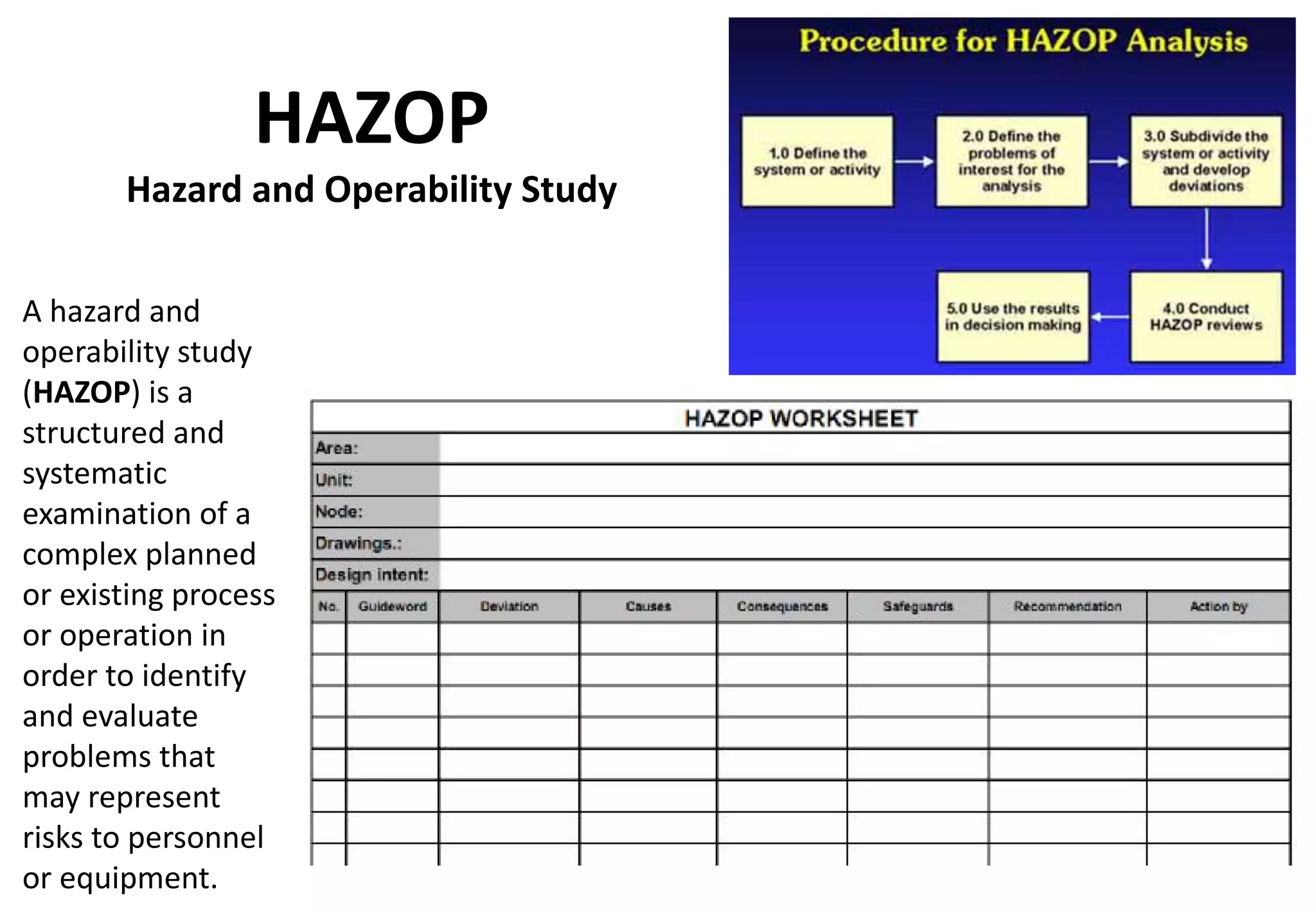
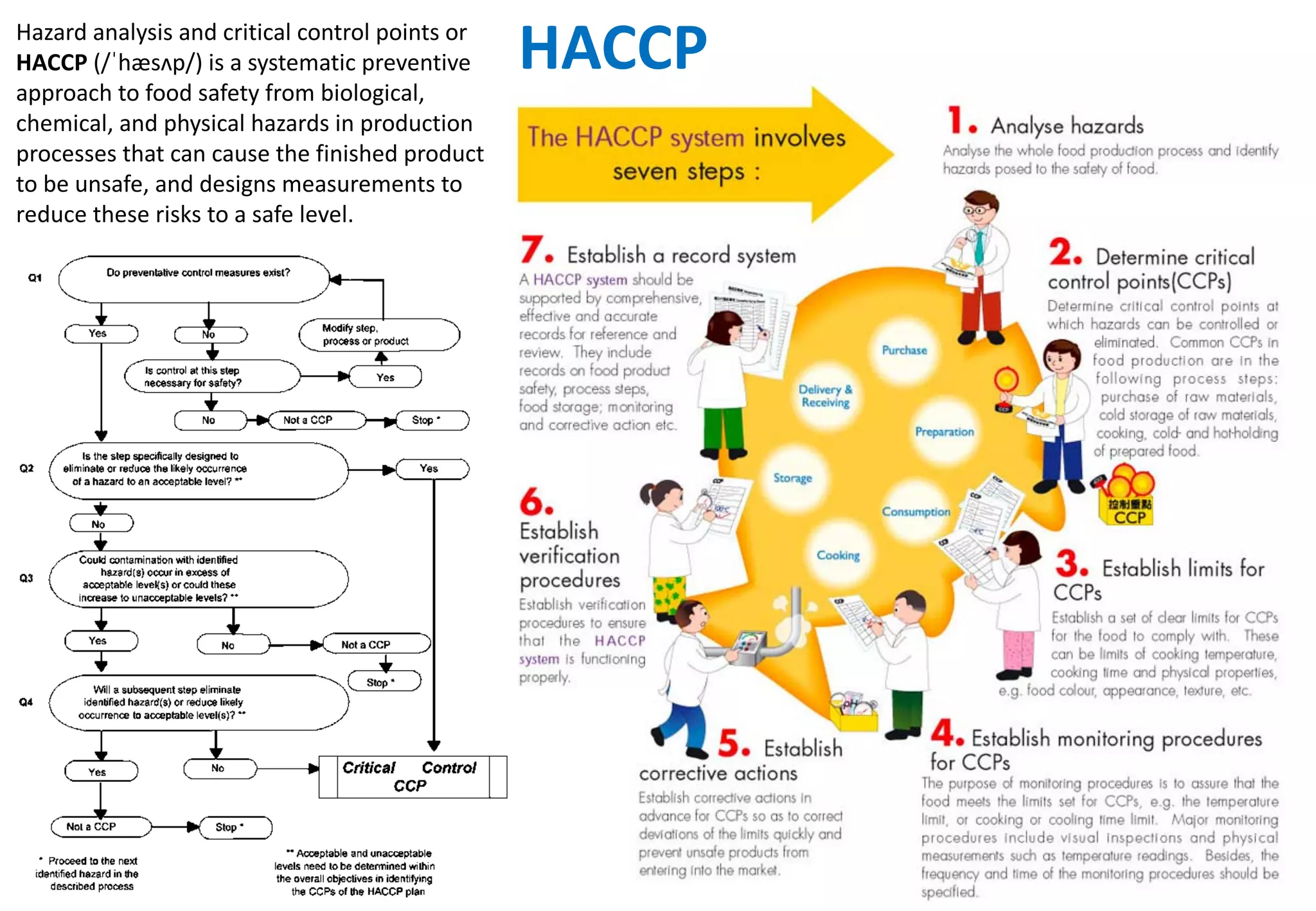
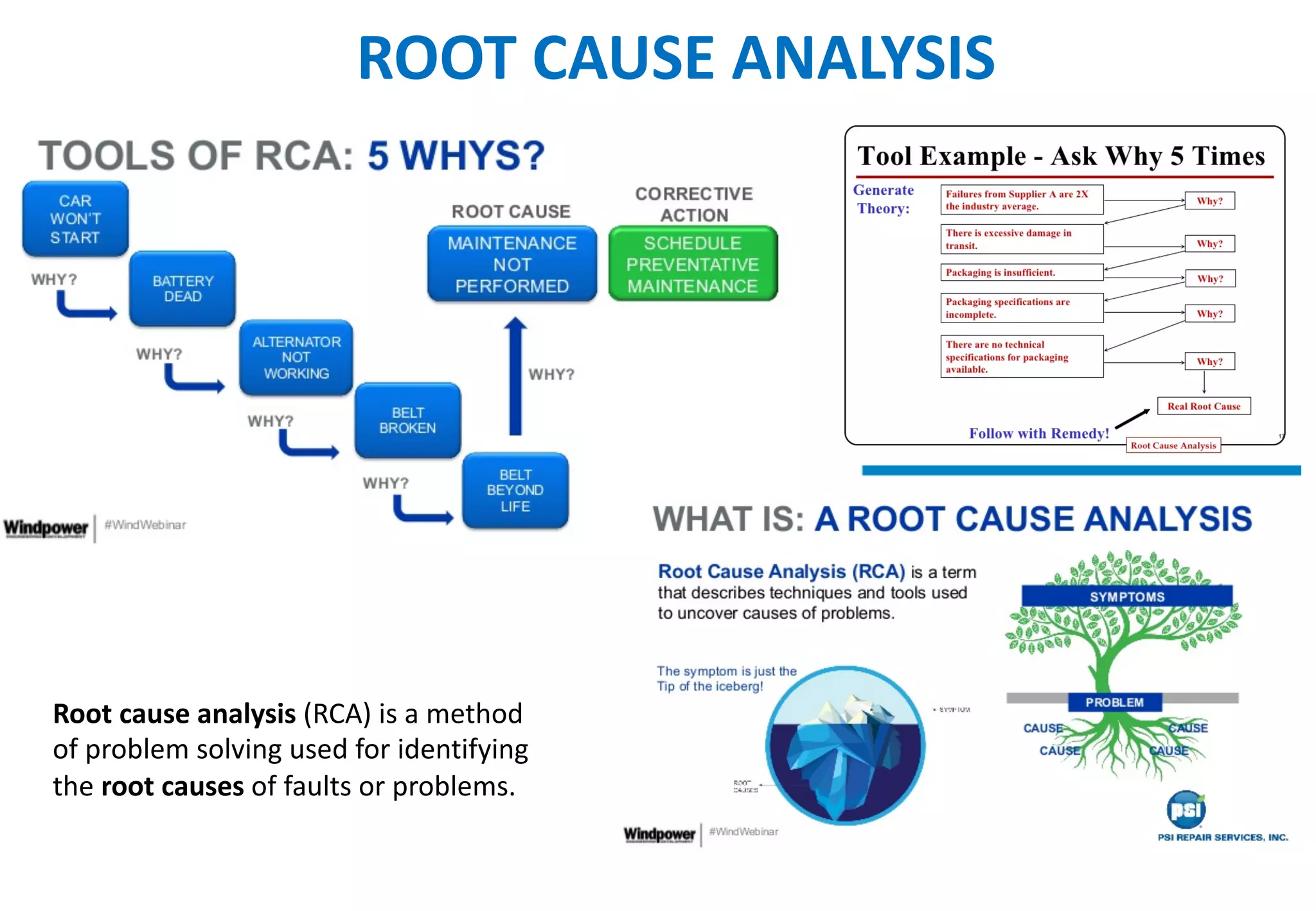
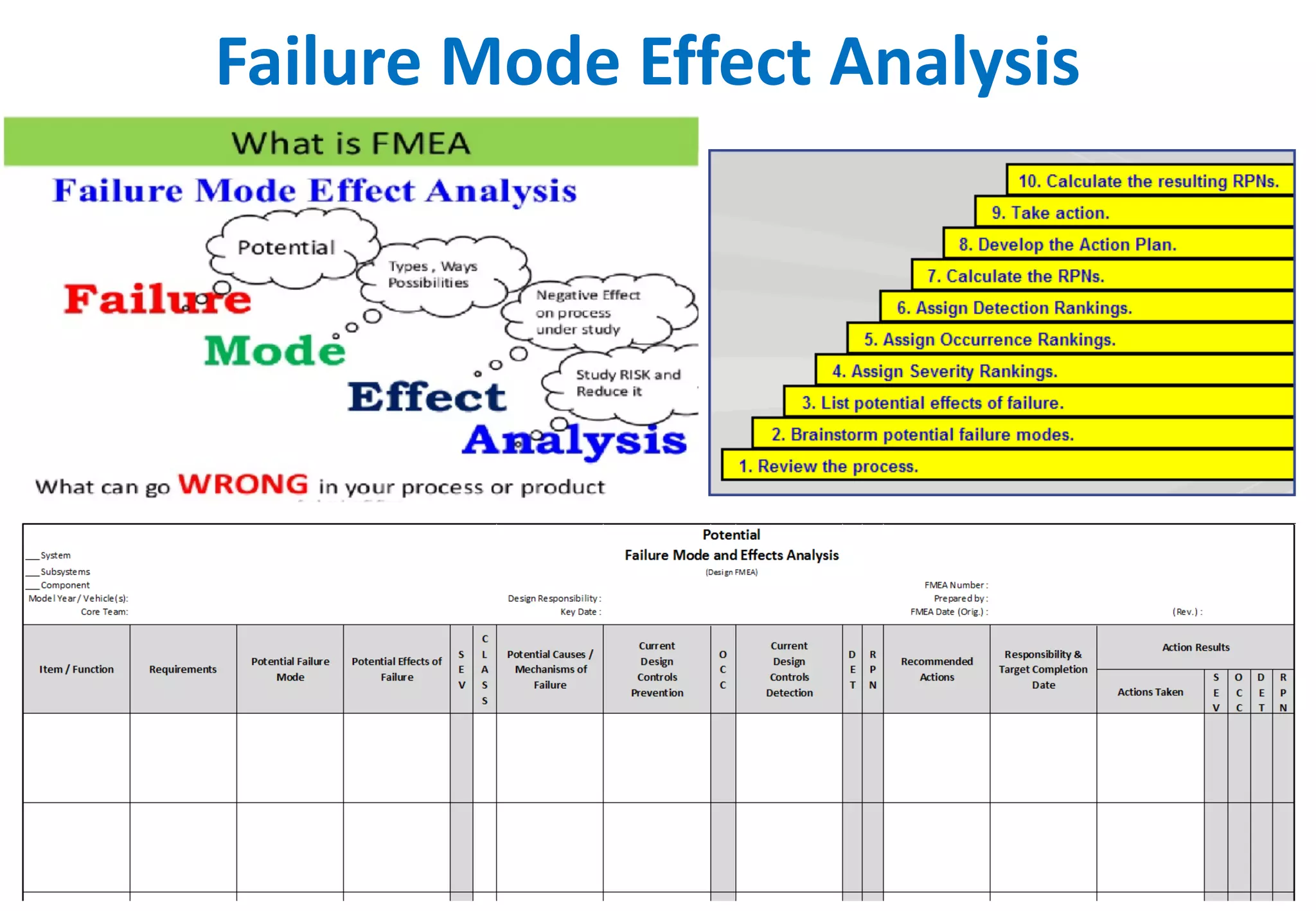
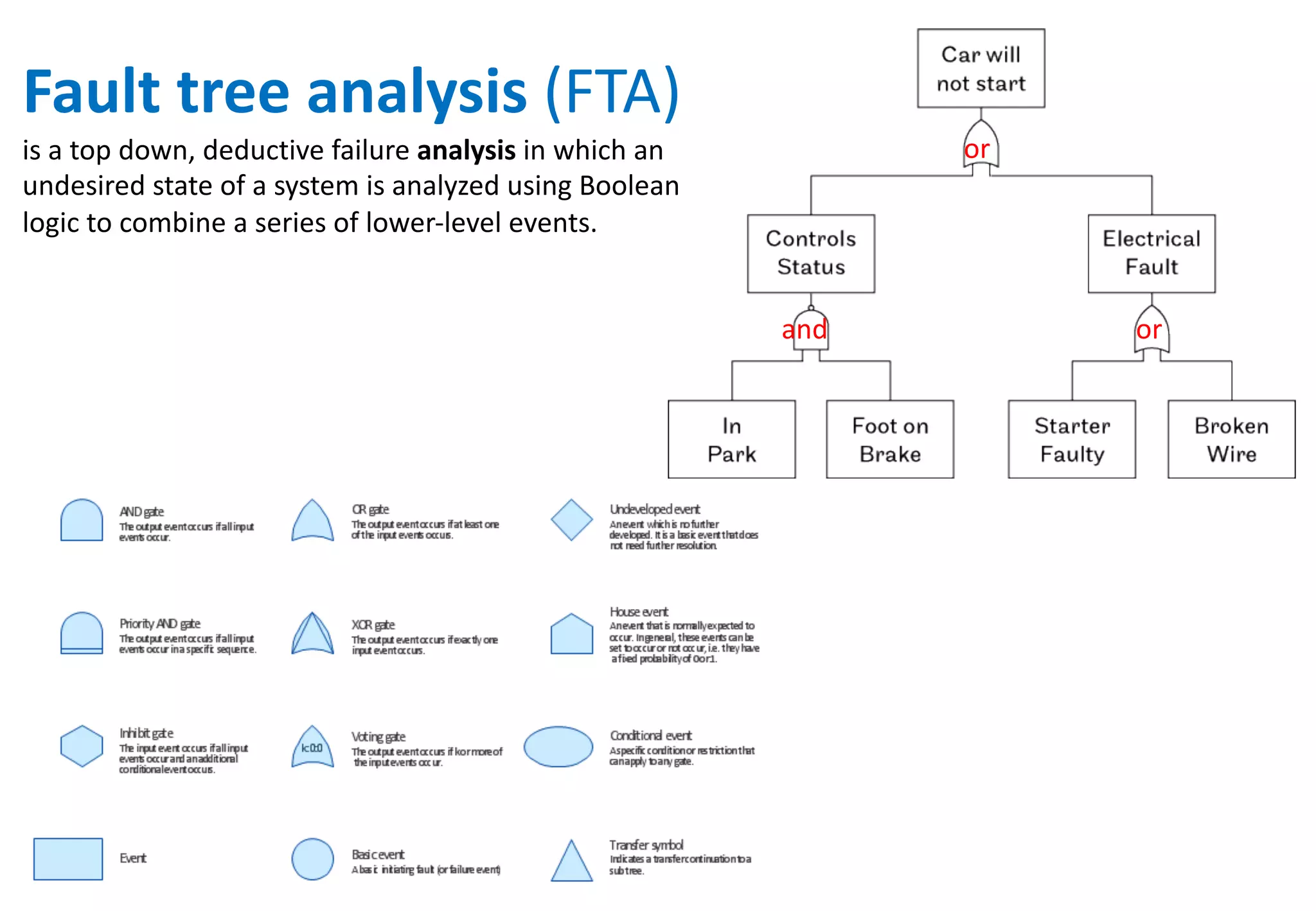
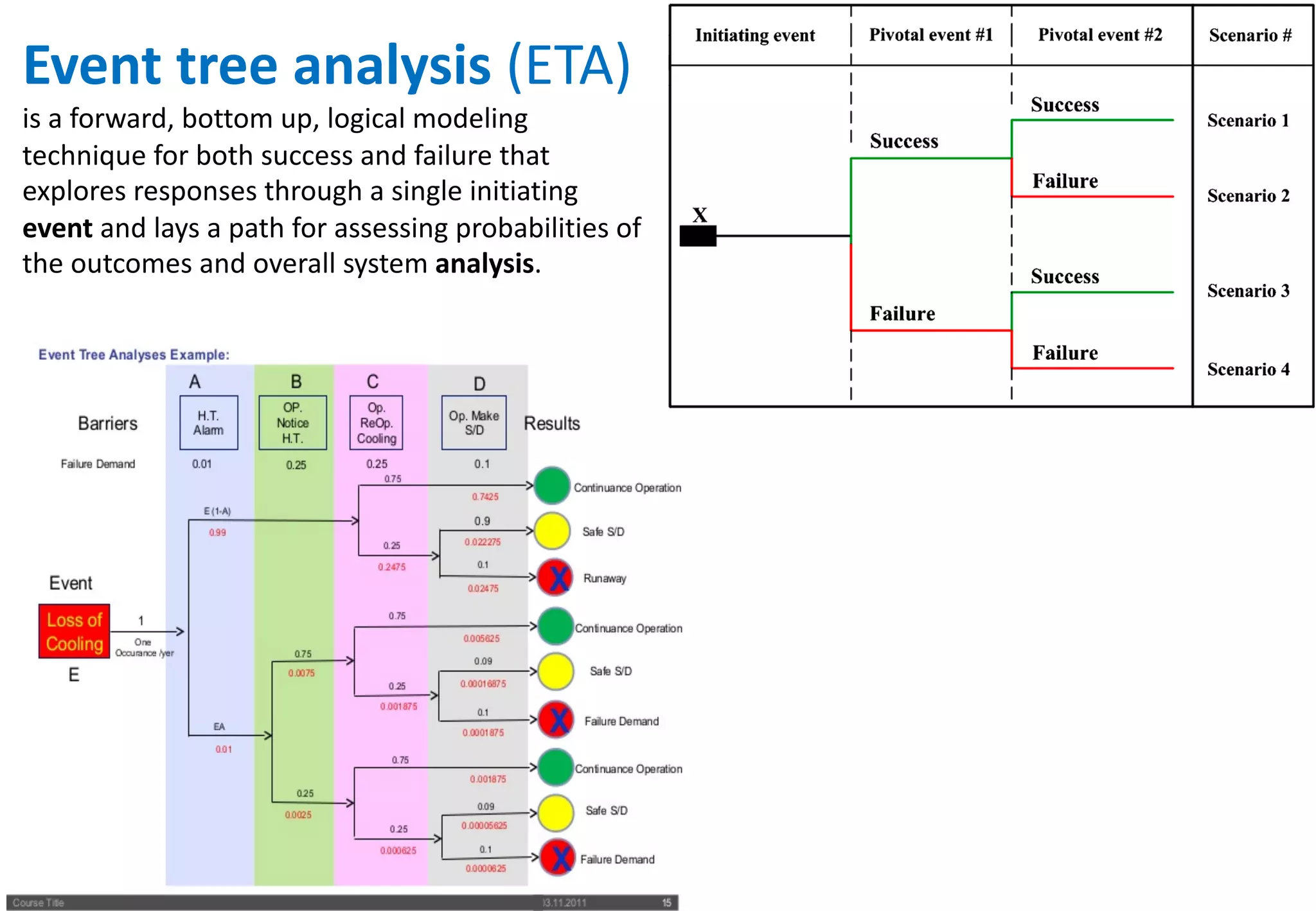
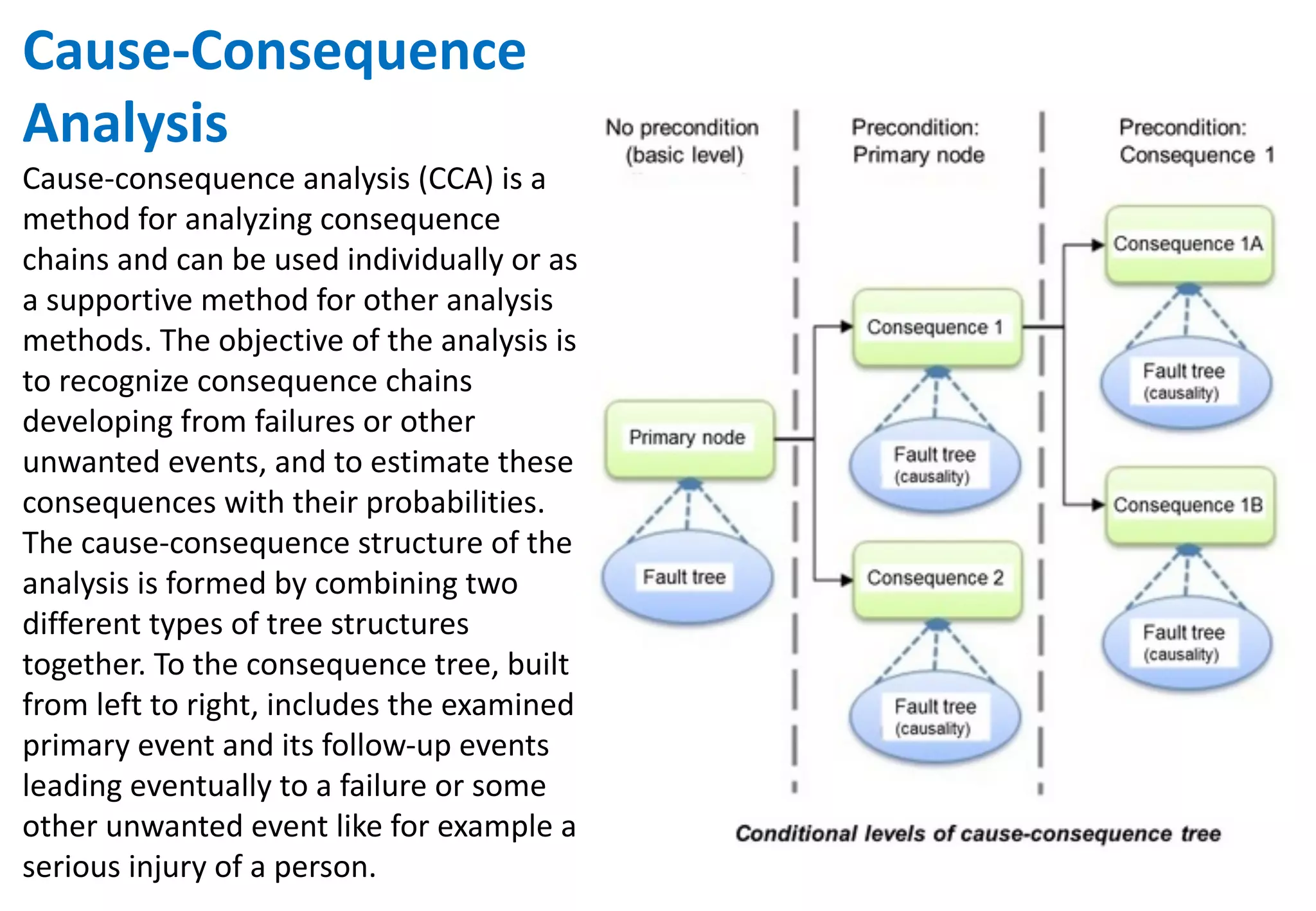
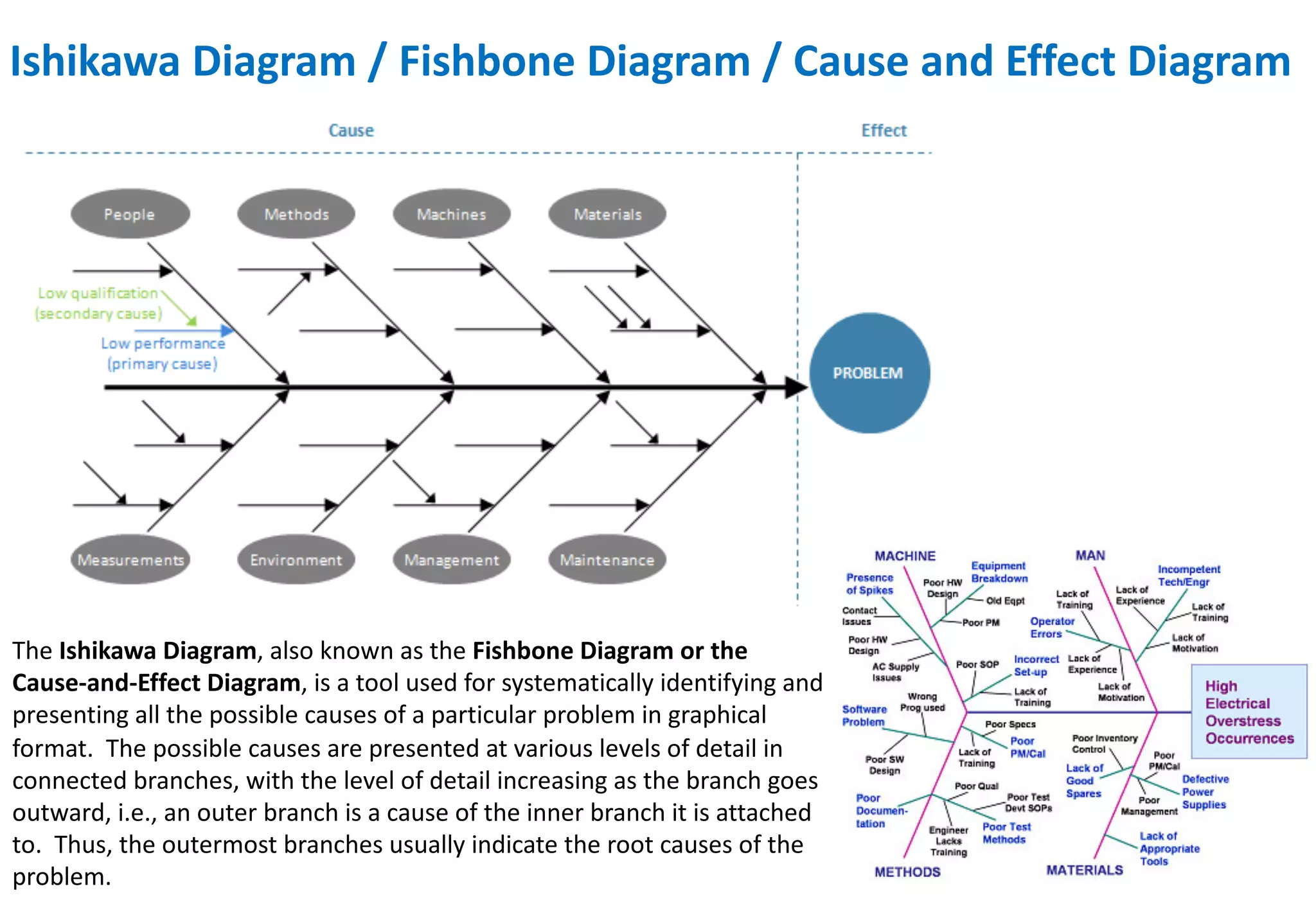
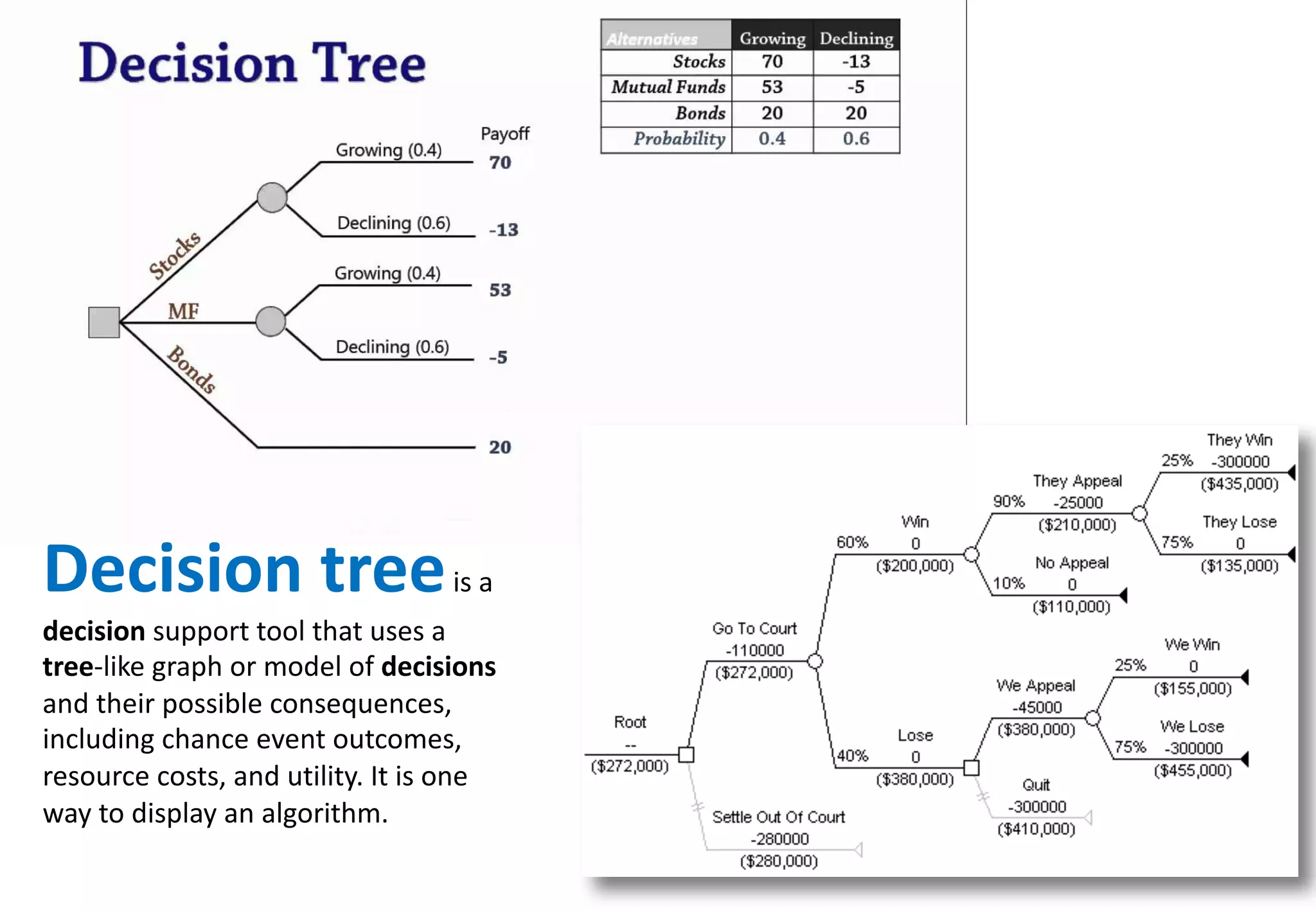
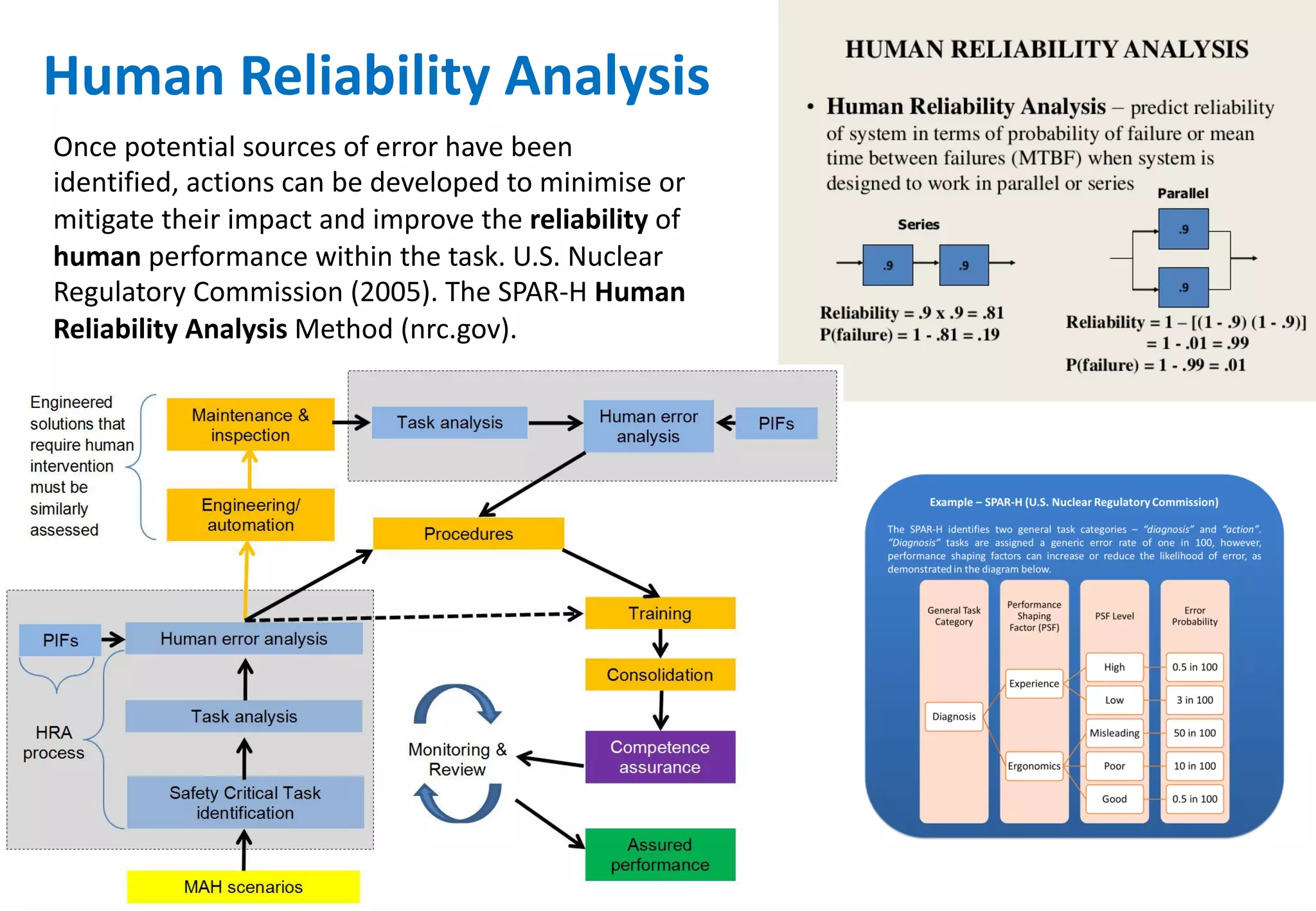
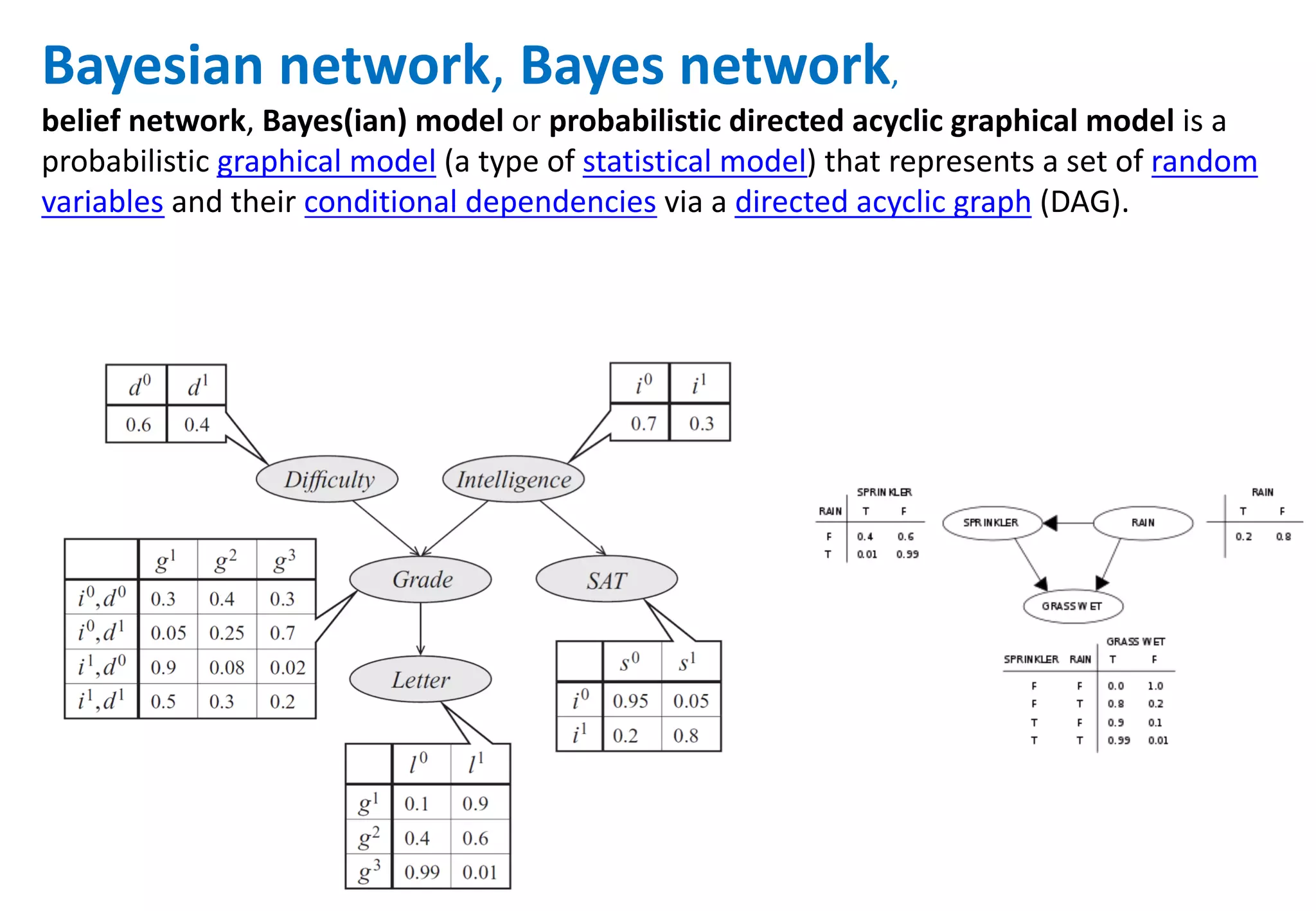
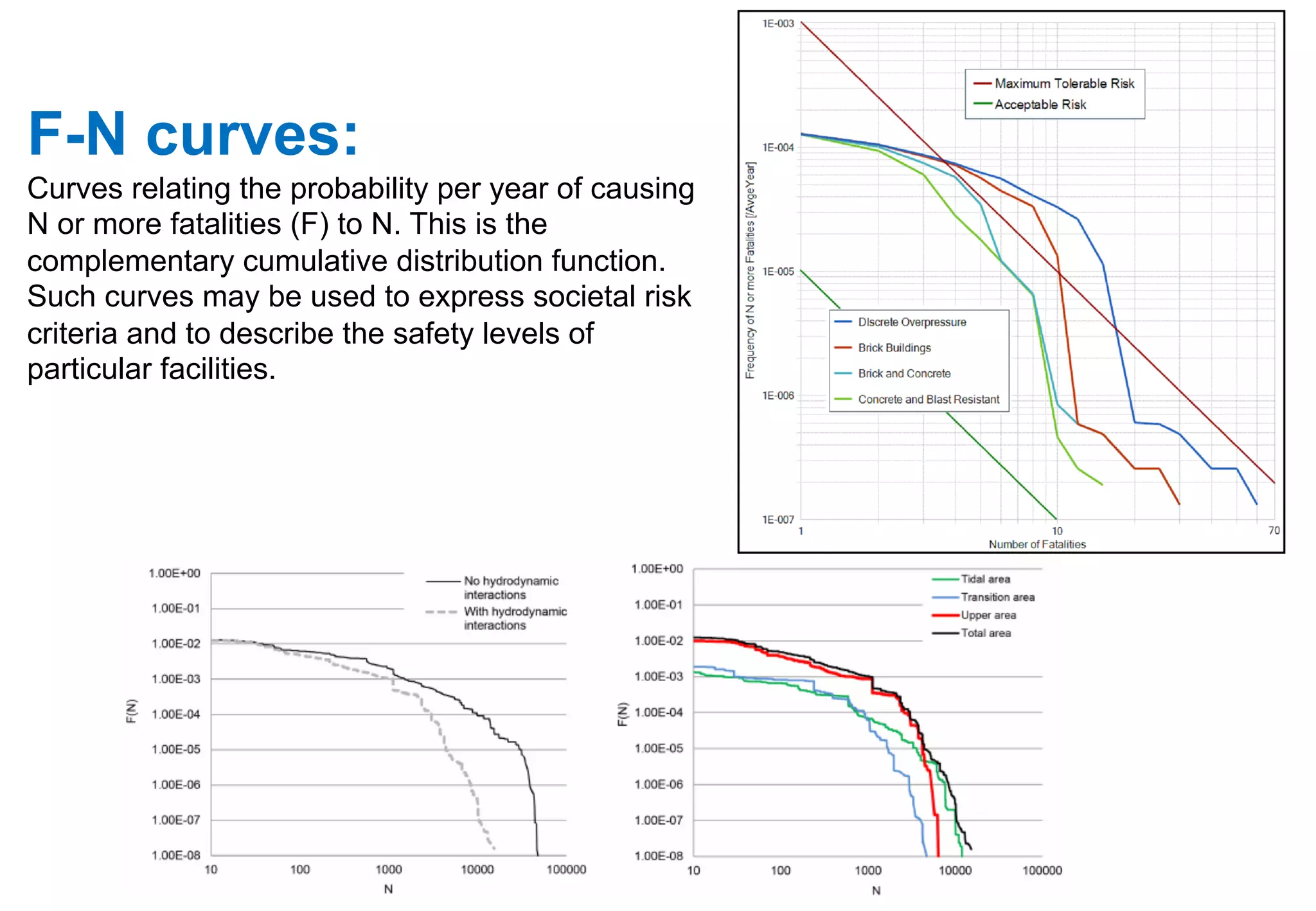
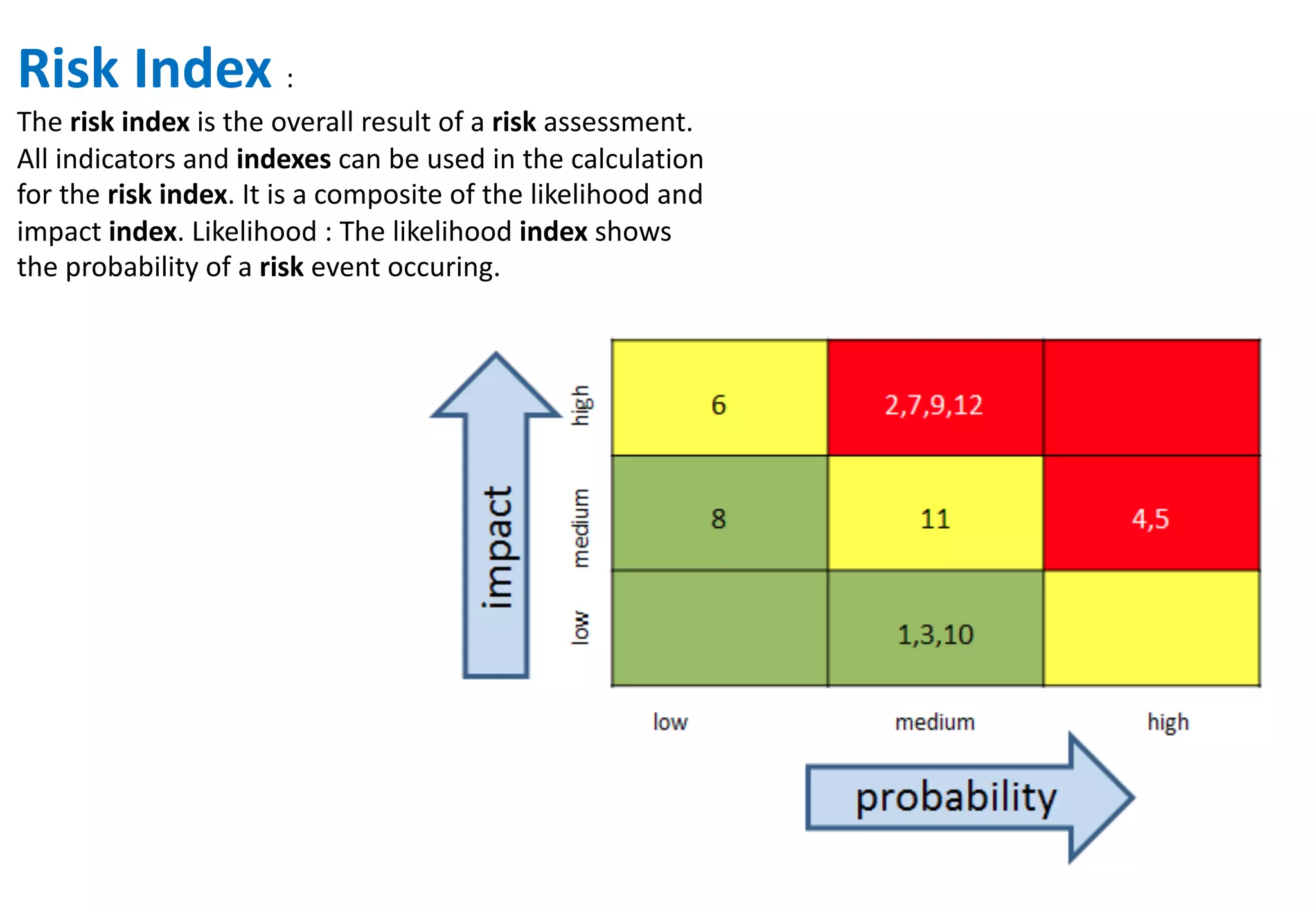
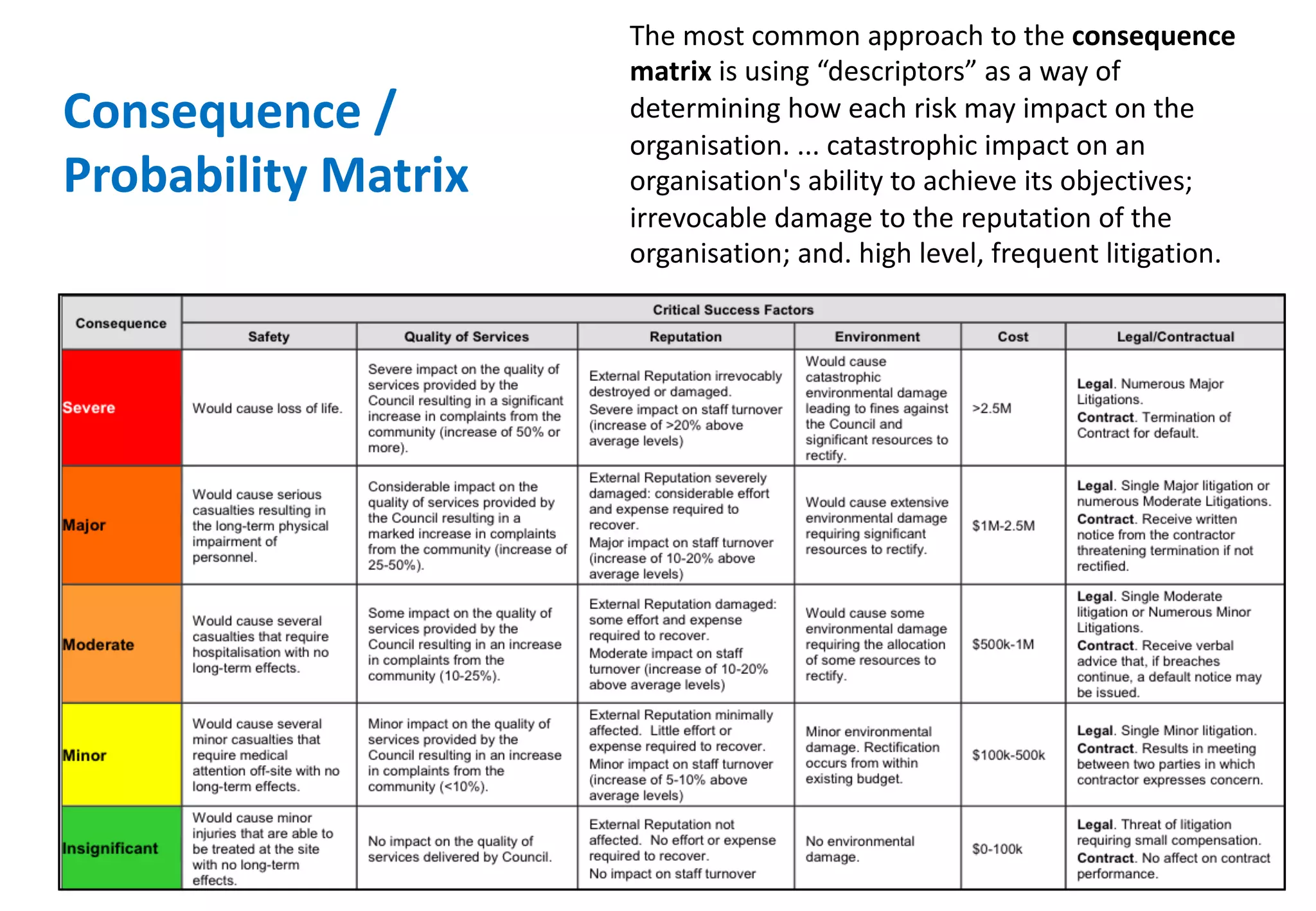
The document outlines various tools and techniques recommended in ISO 31010 for risk assessment and management, including brainstorming, interviews, and the Delphi method. It discusses techniques such as Hazard and Operability Studies (HAZOP), Hazard Analysis and Critical Control Points (HACCP), and various analysis methods like Root Cause Analysis and Multi-Criteria Decision Analysis. Additionally, it covers concepts like risk indexes, Monte Carlo simulations, and cost-benefit analysis, emphasizing their importance in decision-making processes.

![Layer of Protection
Analysis (LOPA)
technique is described in detail in The
American
Institute of Chemical Engineers Center for
Chemical Process Safety (CCPS) publication
on
the subject [2]. An overview of the technique
is presented here. For more information the
reader is referred to the CCPS publication,
which contains a number of worked
examples and
extensive references.](https://image.slidesharecdn.com/riskassessmenttechnique-170923010930/75/Risk-assessment-tools-and-techniques-19-2048.jpg)

![Cost
benefit
analysis
(CBA),
sometimes
called
benefit
cost
analysis (BCA),
is
a
systematic
approach
to
estimating
the
strengths
and
weaknesses
of
alternatives
(for
example
in
transactions,
activities,
functional
business
requirements
or
projects
investments);
it
is
used
to
determine
options
that
provide
the
best
approach
to
achieve
benefits
while
preserving
savings.[1] The
CBA
is
also
defined
as
a
systematic
process
for
calculating
and
comparing
benefits
and
costs of
a
decision,
policy
(with
particular
regard
to
government
policy)
or
(in
general)
project.
Broadly,
CBA
has
two
main
purposes:
1.To
determine
if
an
investment/decision
is
sound
(justification/feasibility)
– verifying
whether
its
benefits
outweigh
the
costs,
and
by
how
much;
2.To
provide
a
basis
for
comparing
projects
–
which
involves
comparing
the
total
expected
cost
of
each
option
against
its
total
expected
benefits.[2]](https://image.slidesharecdn.com/riskassessmenttechnique-170923010930/75/Risk-assessment-tools-and-techniques-31-2048.jpg)