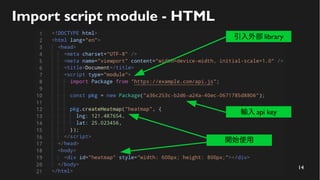
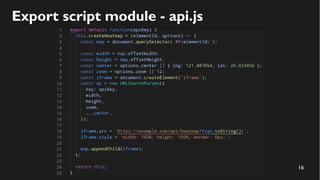
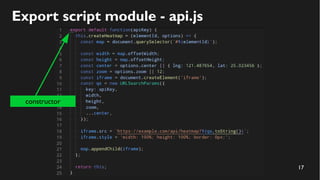
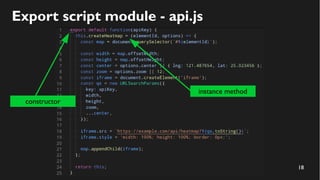
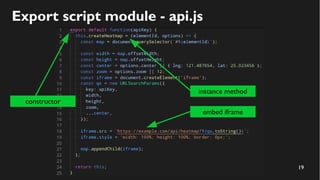
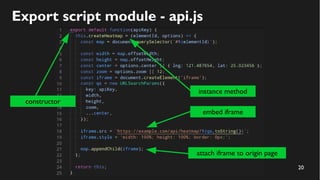
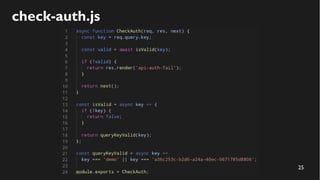
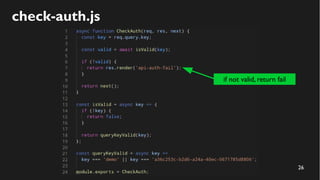
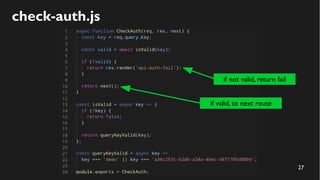
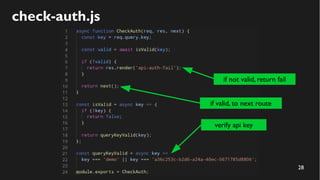
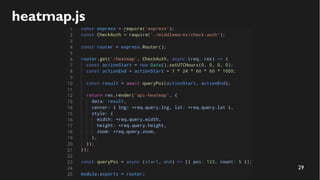
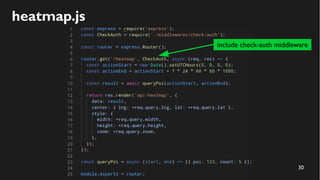
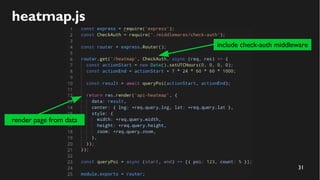
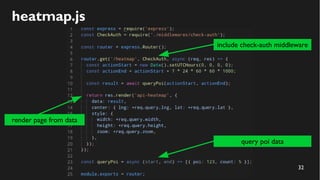
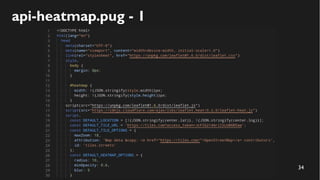
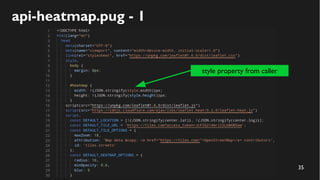
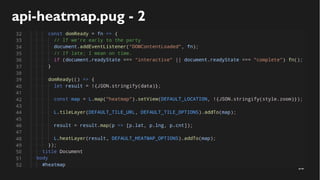
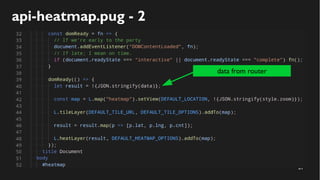
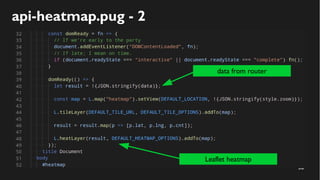
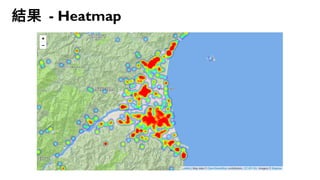
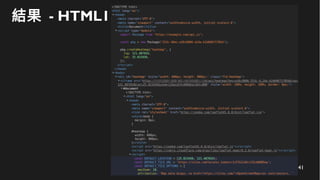
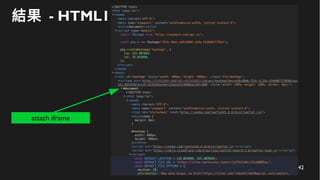
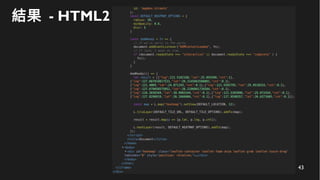
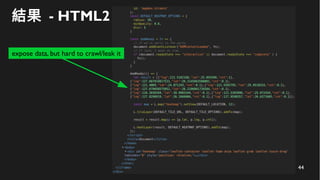
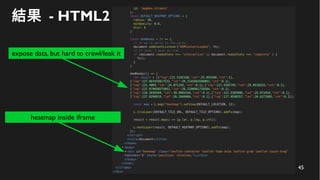
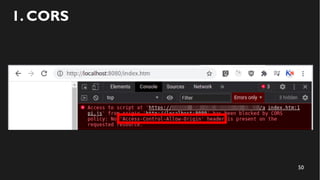
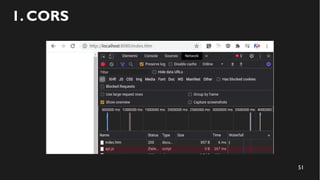
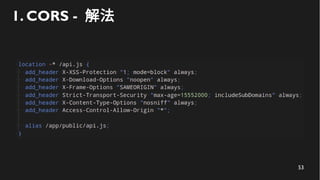
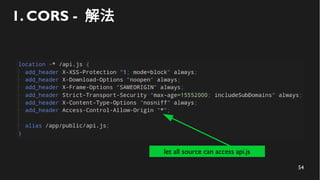
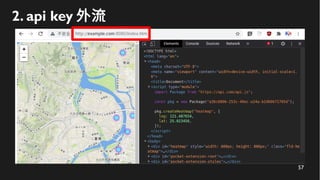
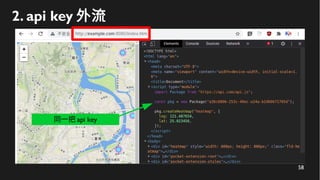
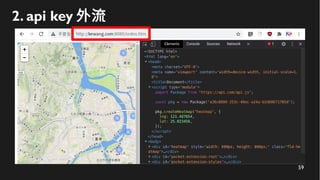
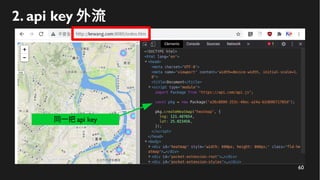
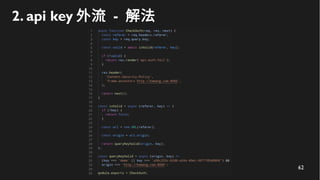
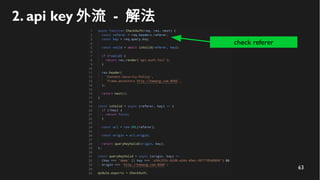
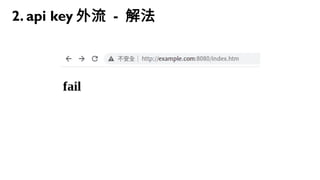
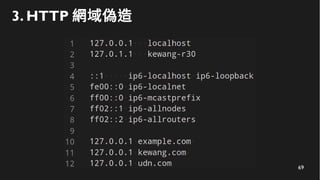
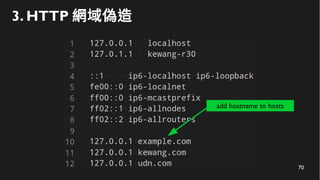
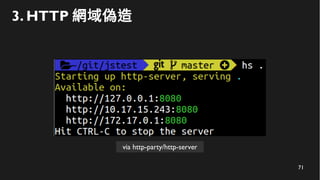
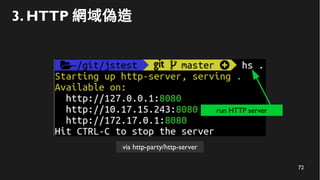
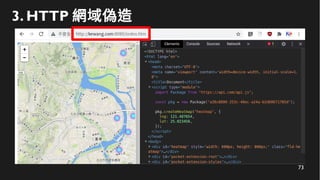
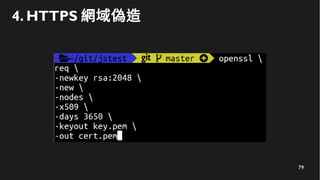
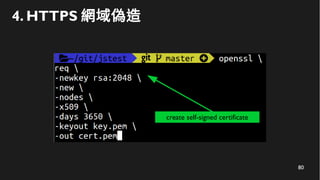
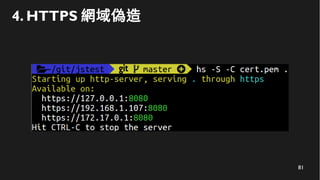
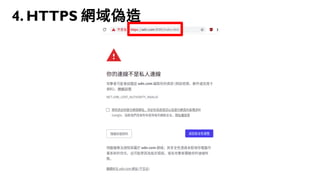
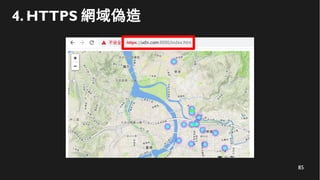
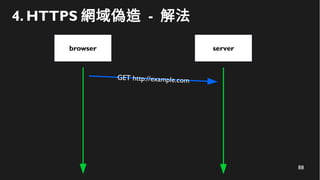
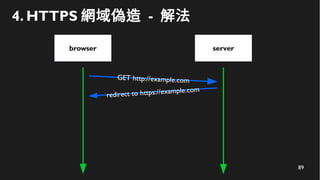
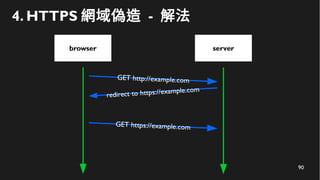
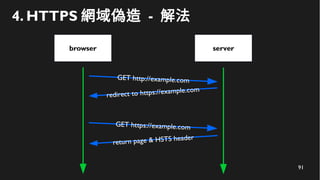
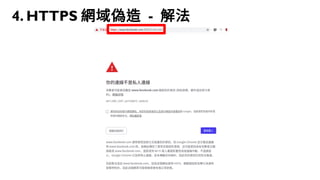
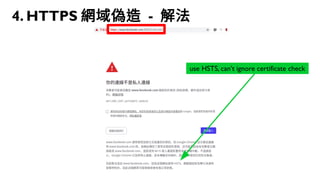
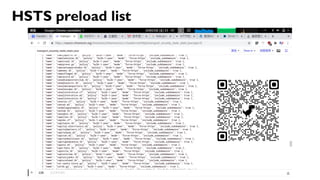
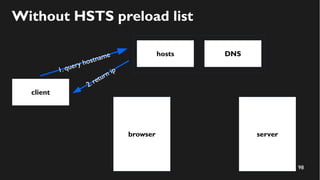
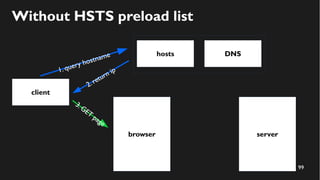
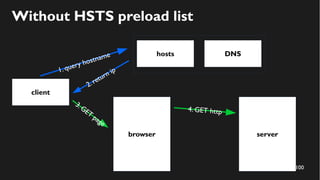
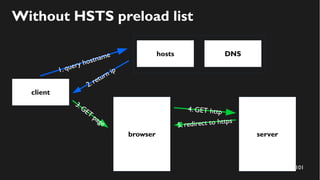
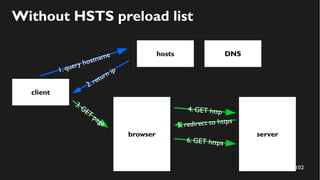
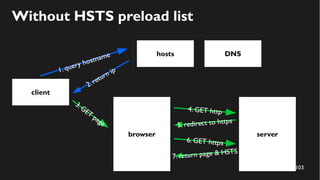
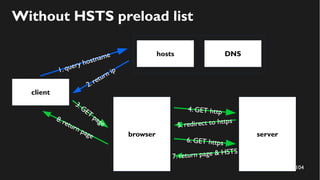
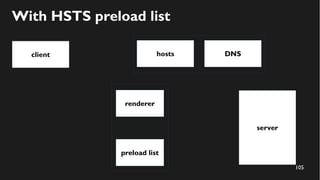
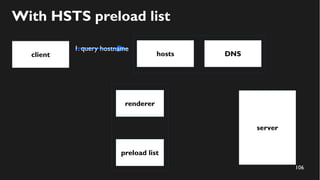
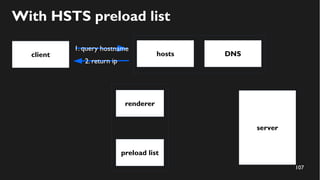
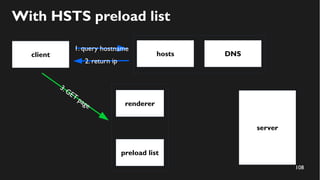
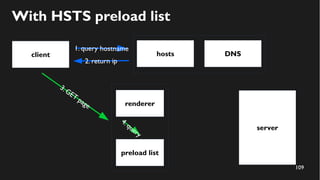
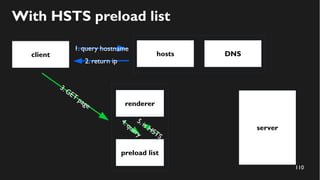
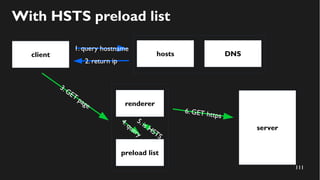
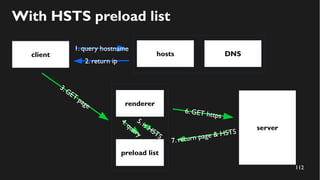
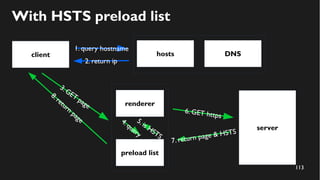
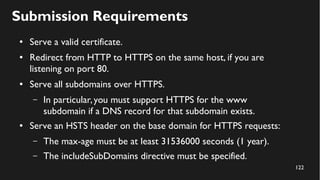
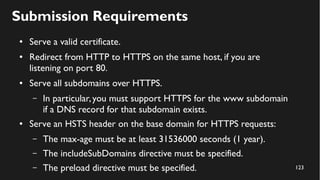
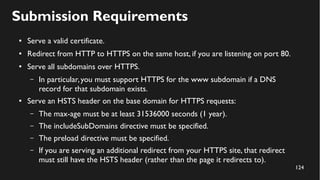
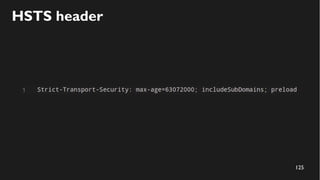
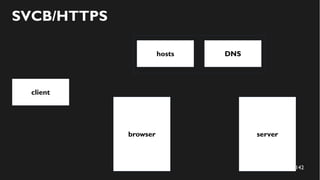
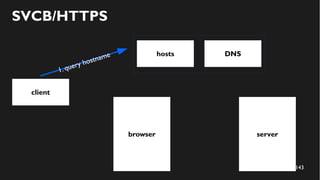
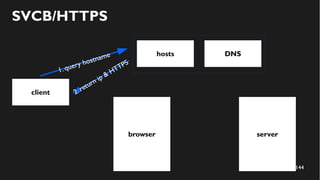
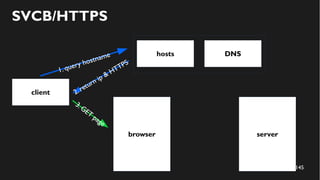
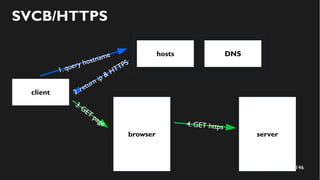
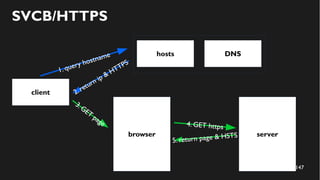
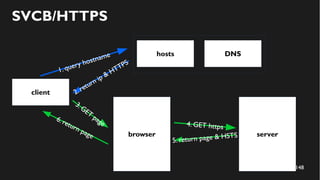
This document discusses how to create a front-end library using iframes while addressing security concerns such as CORS, API key exposure, and domain spoofing. It outlines methods for ensuring safe usage and management of API keys, including allowing whitelisted domains and employing HSTS. The document ultimately provides a conclusion on maintaining safety and ease of updates in front-end application development.