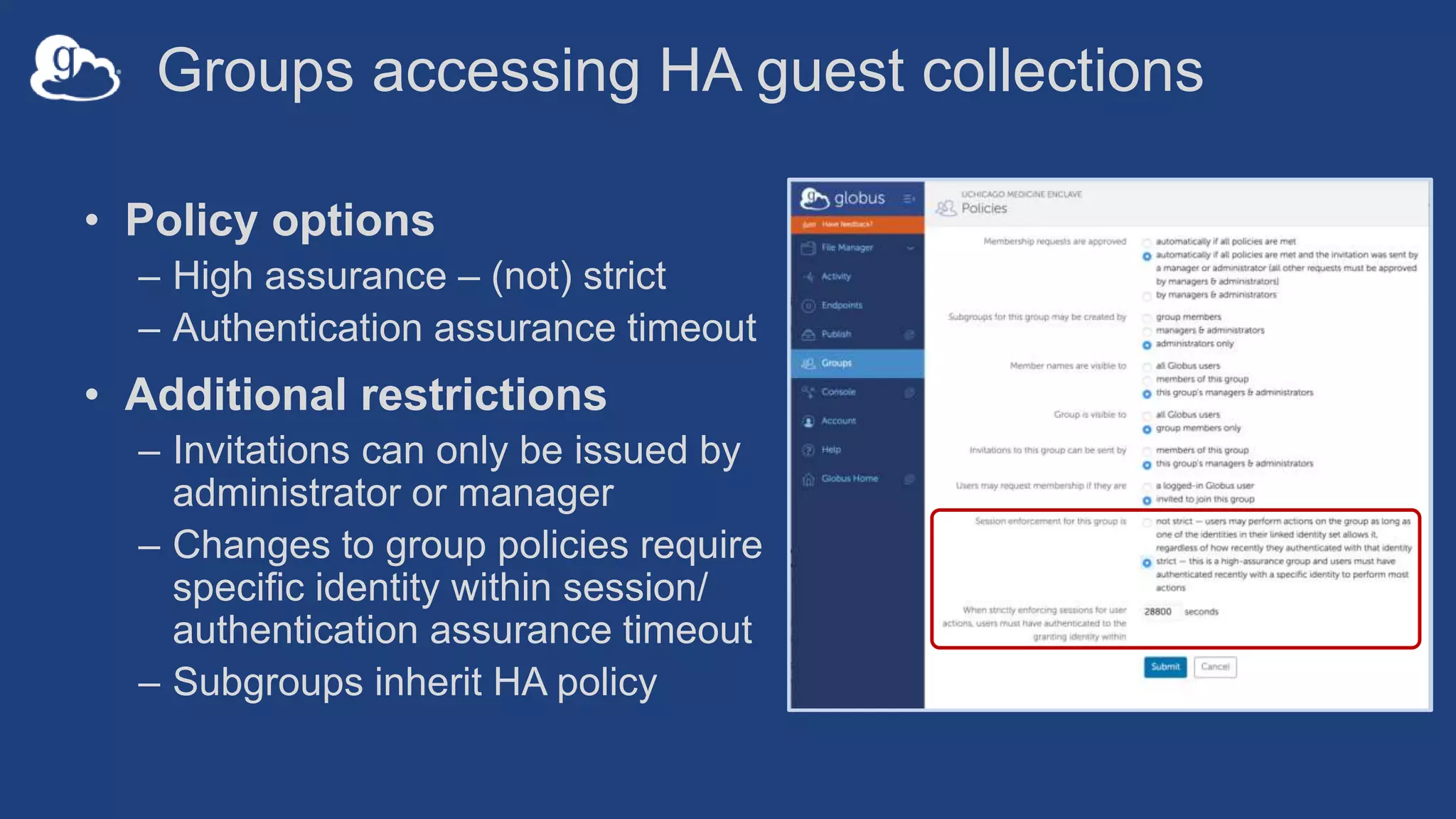
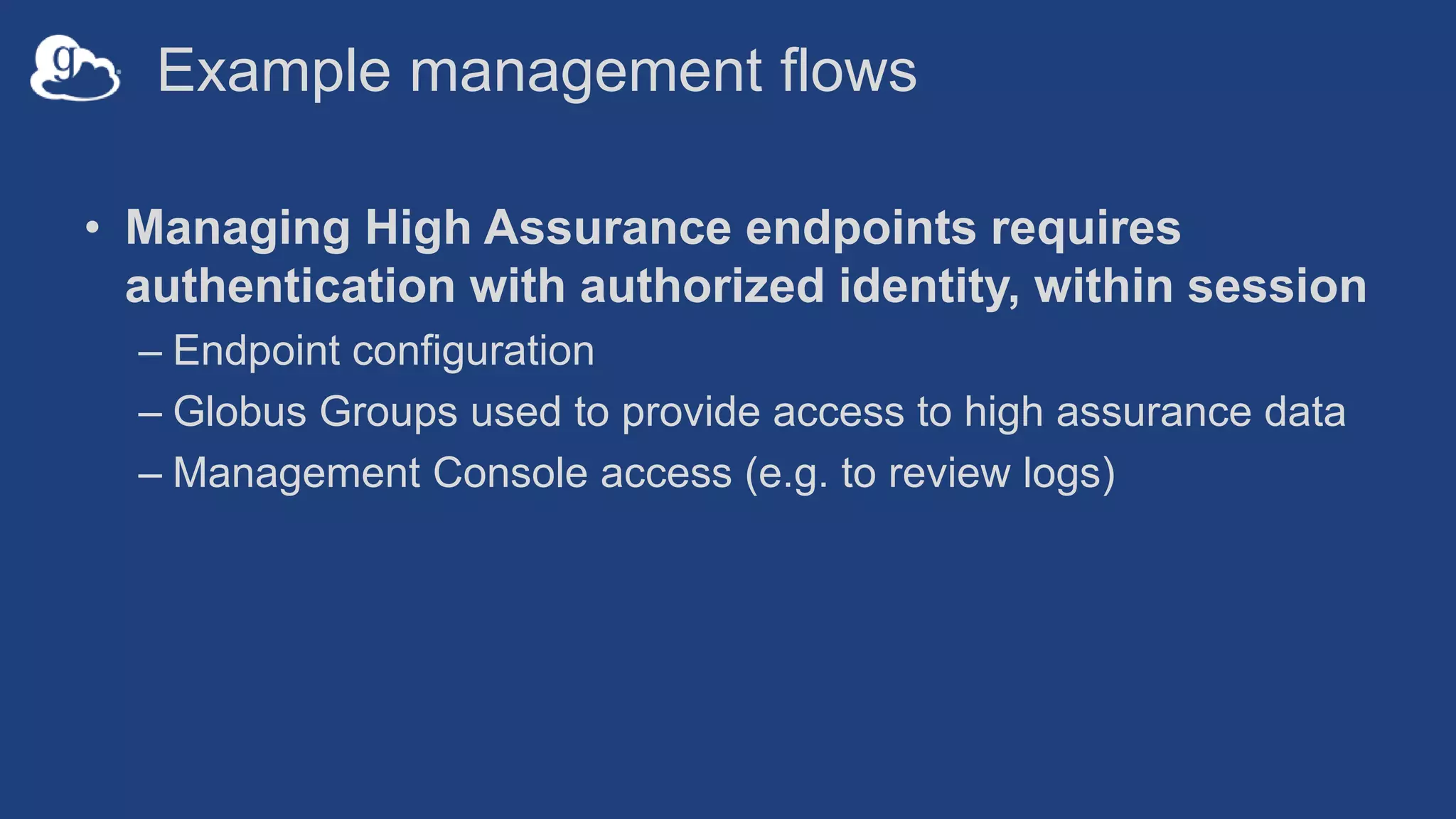
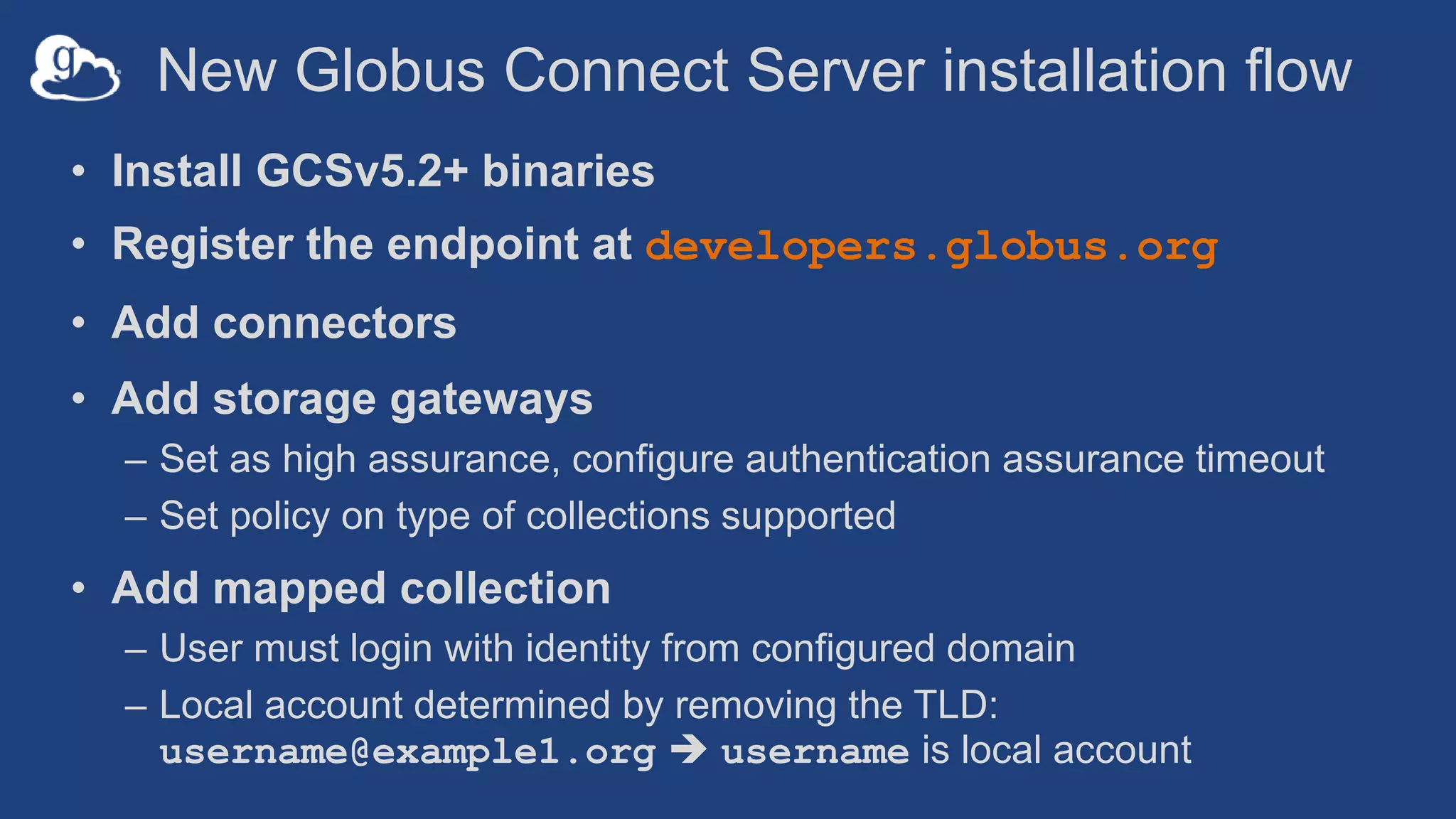
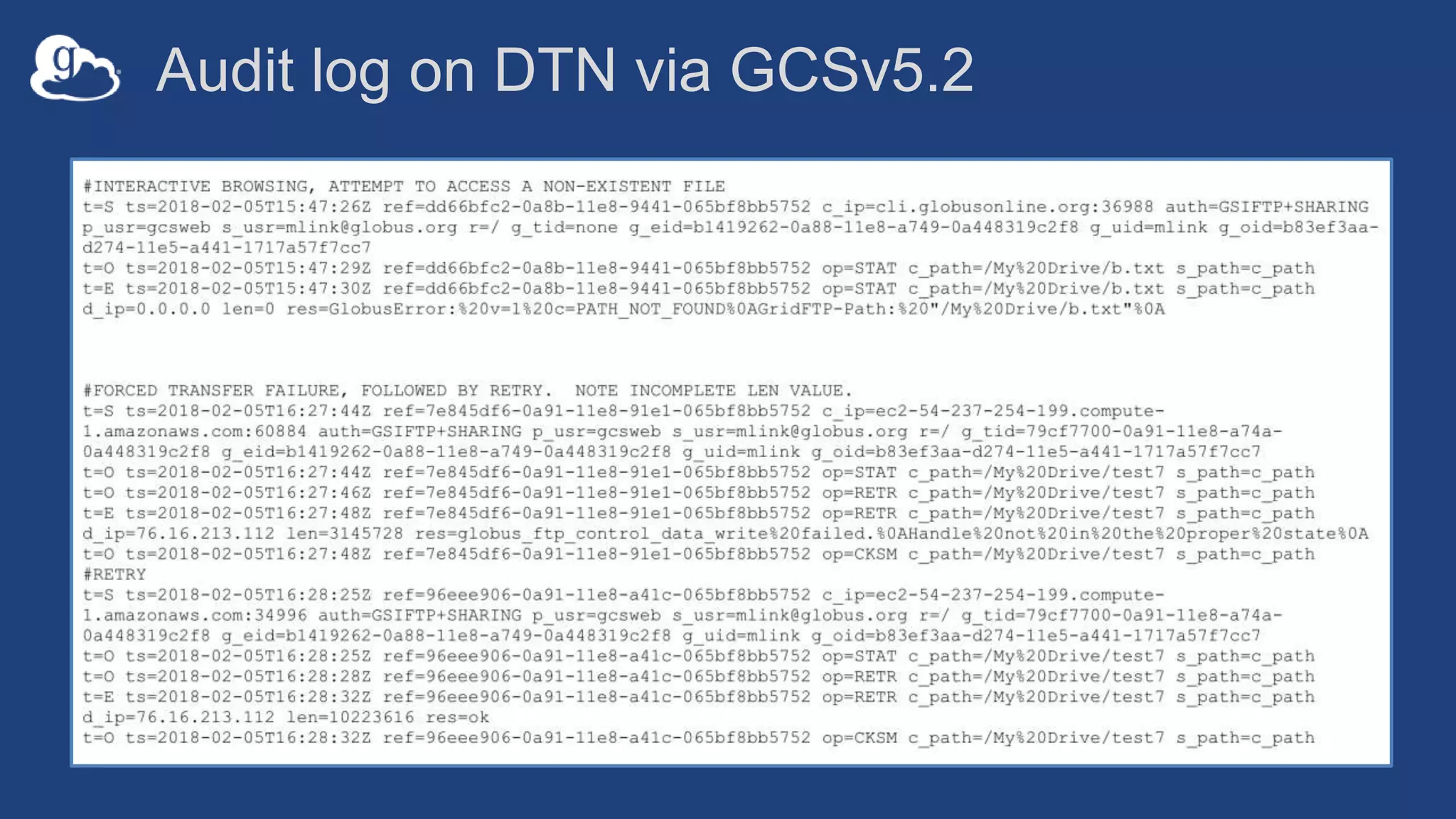
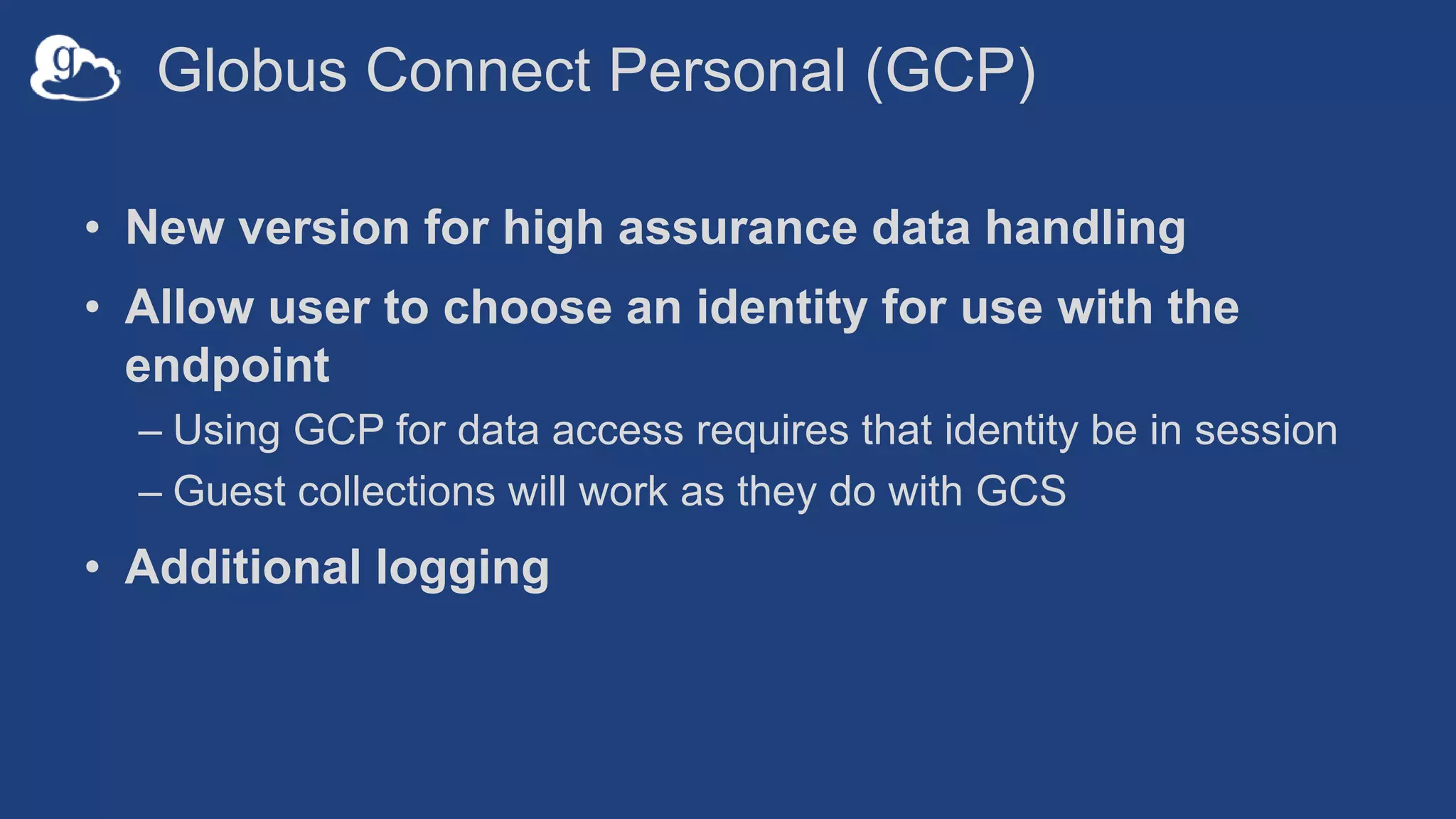
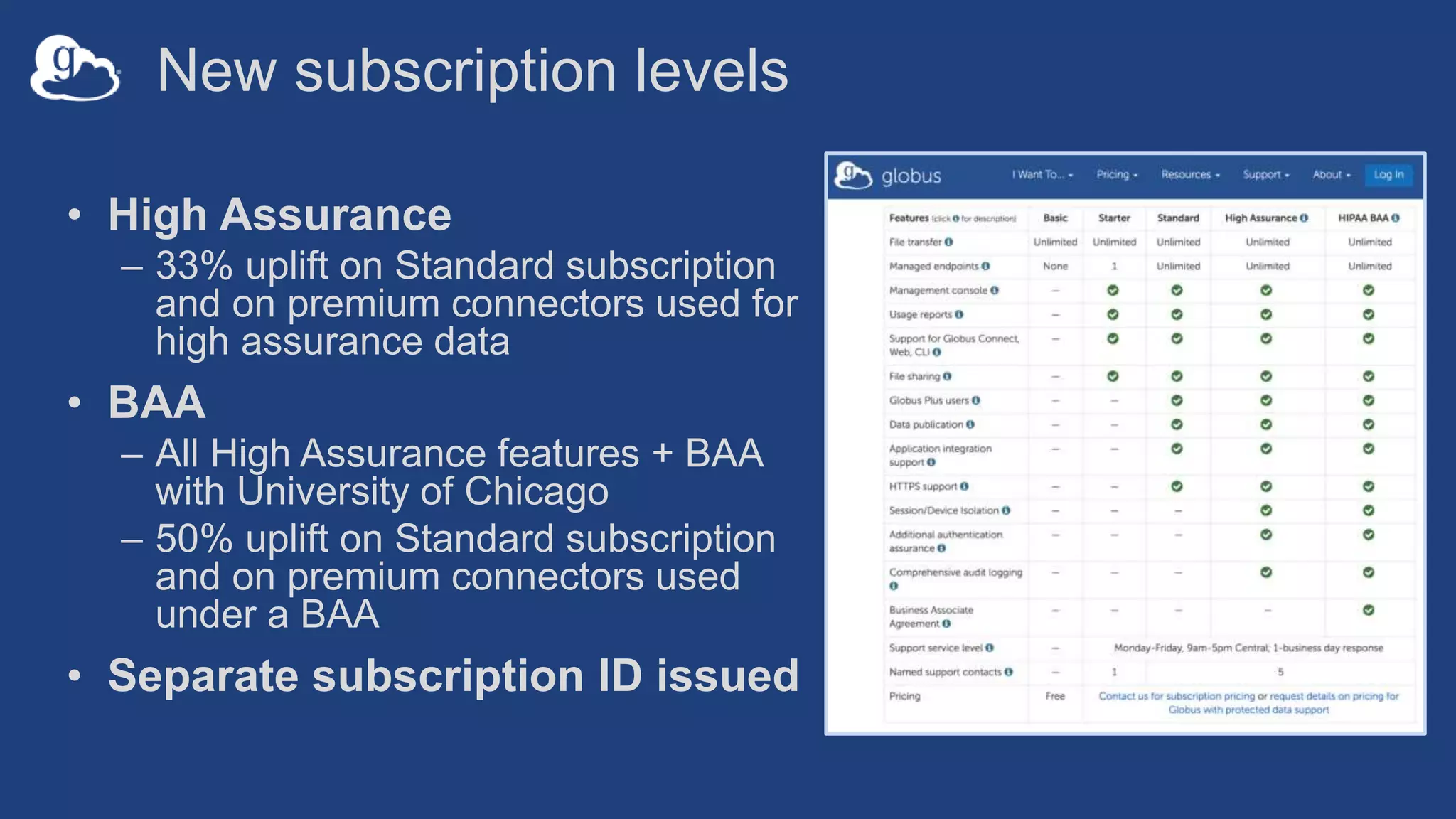
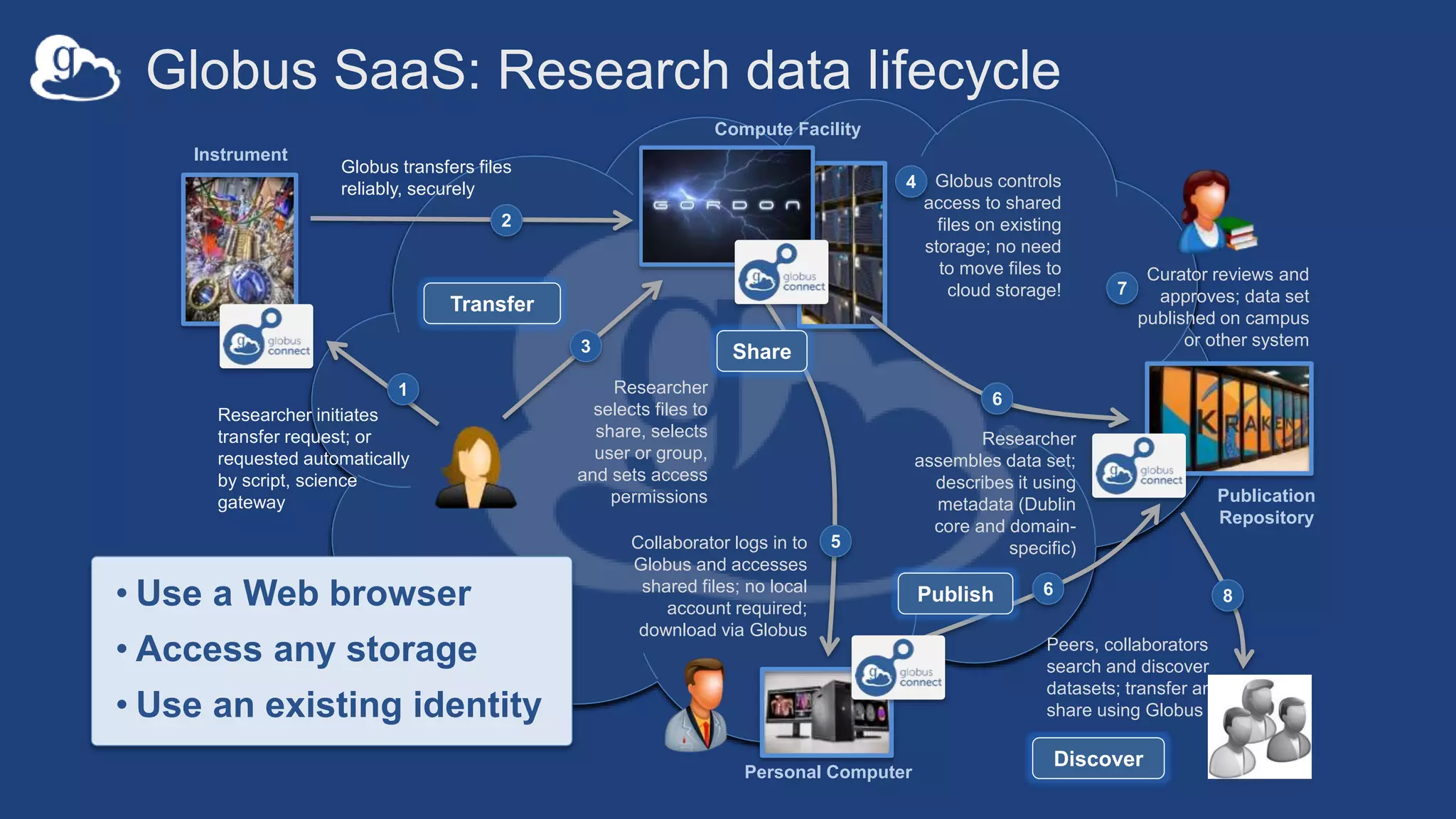
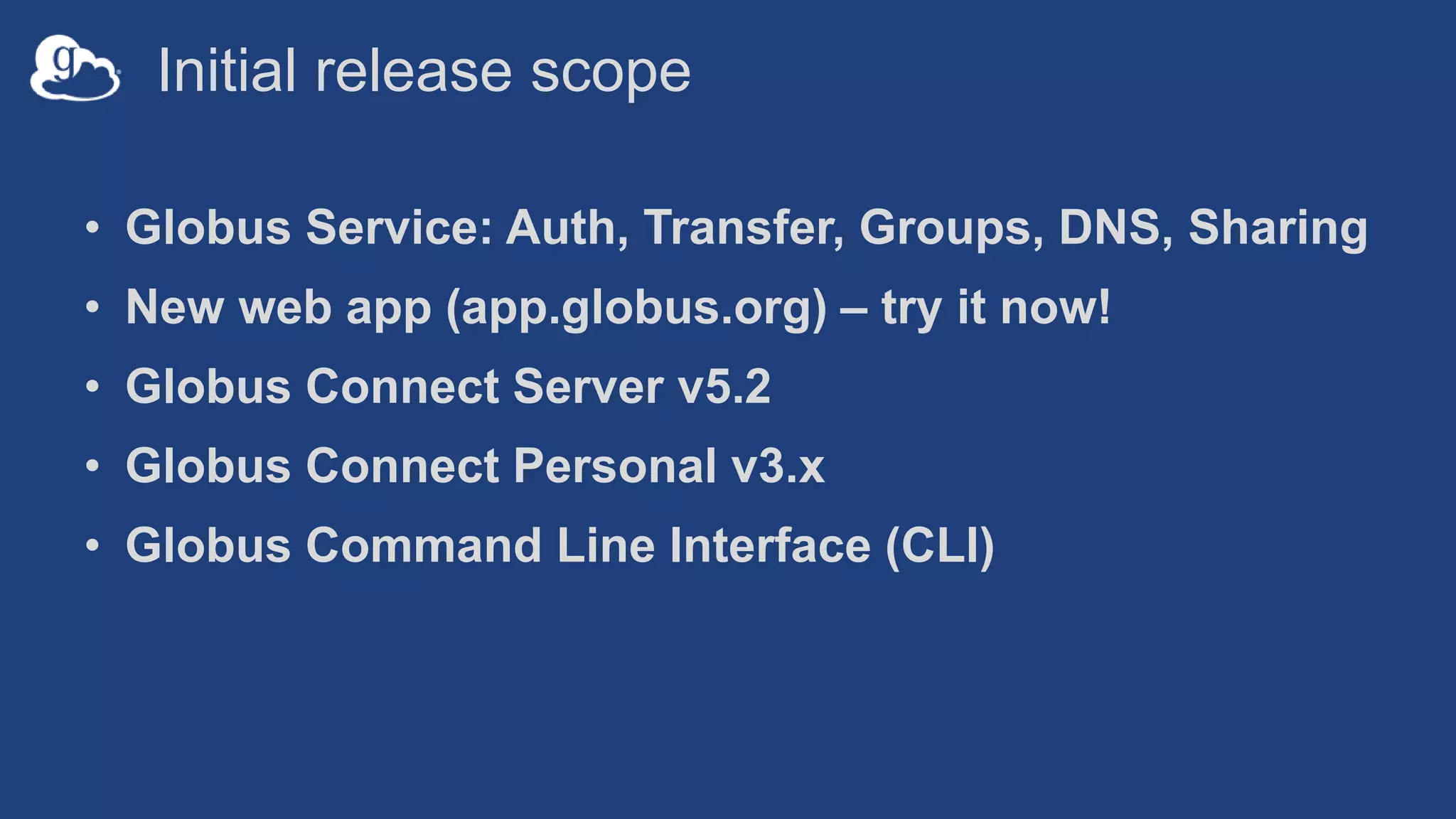
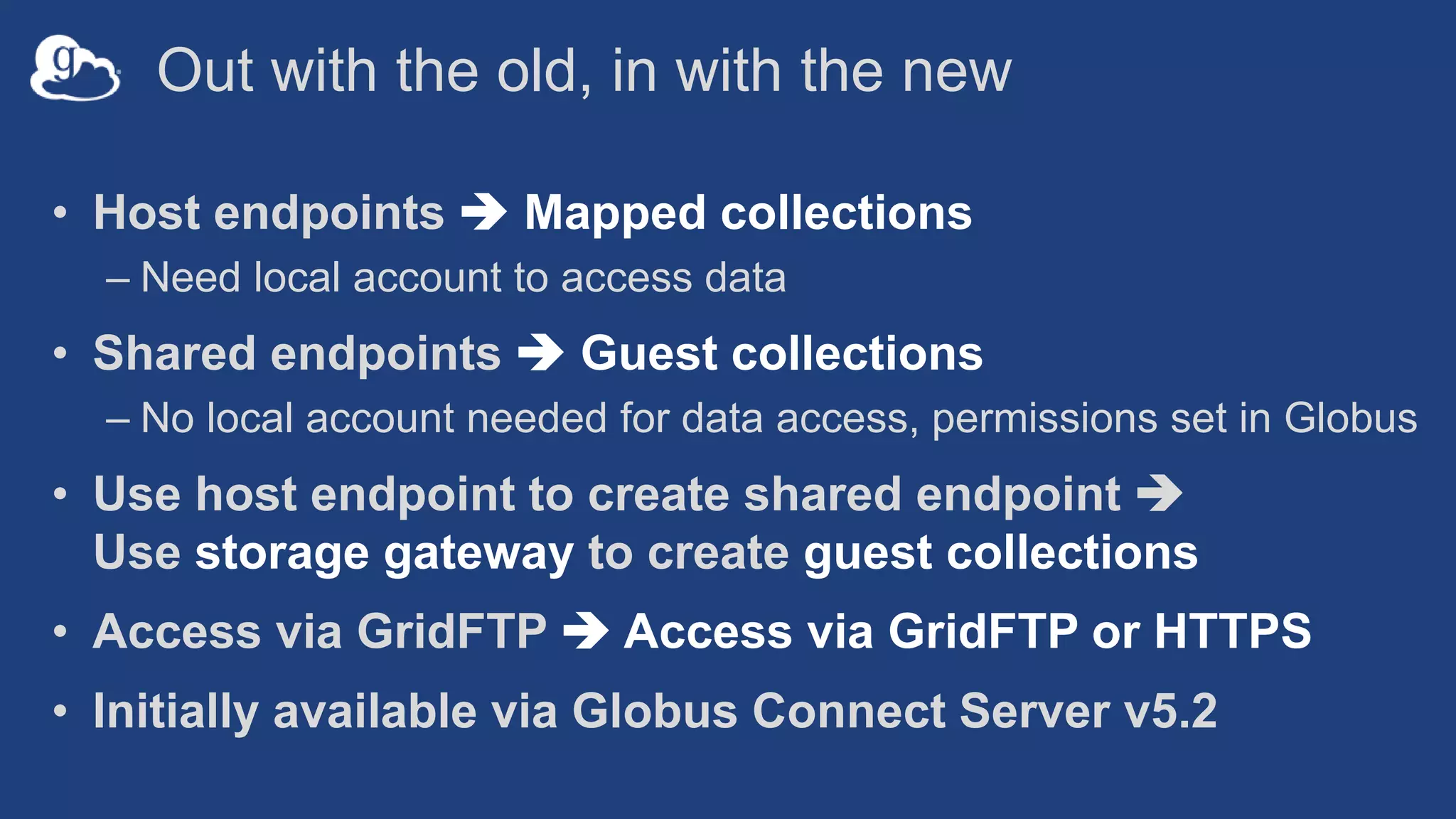
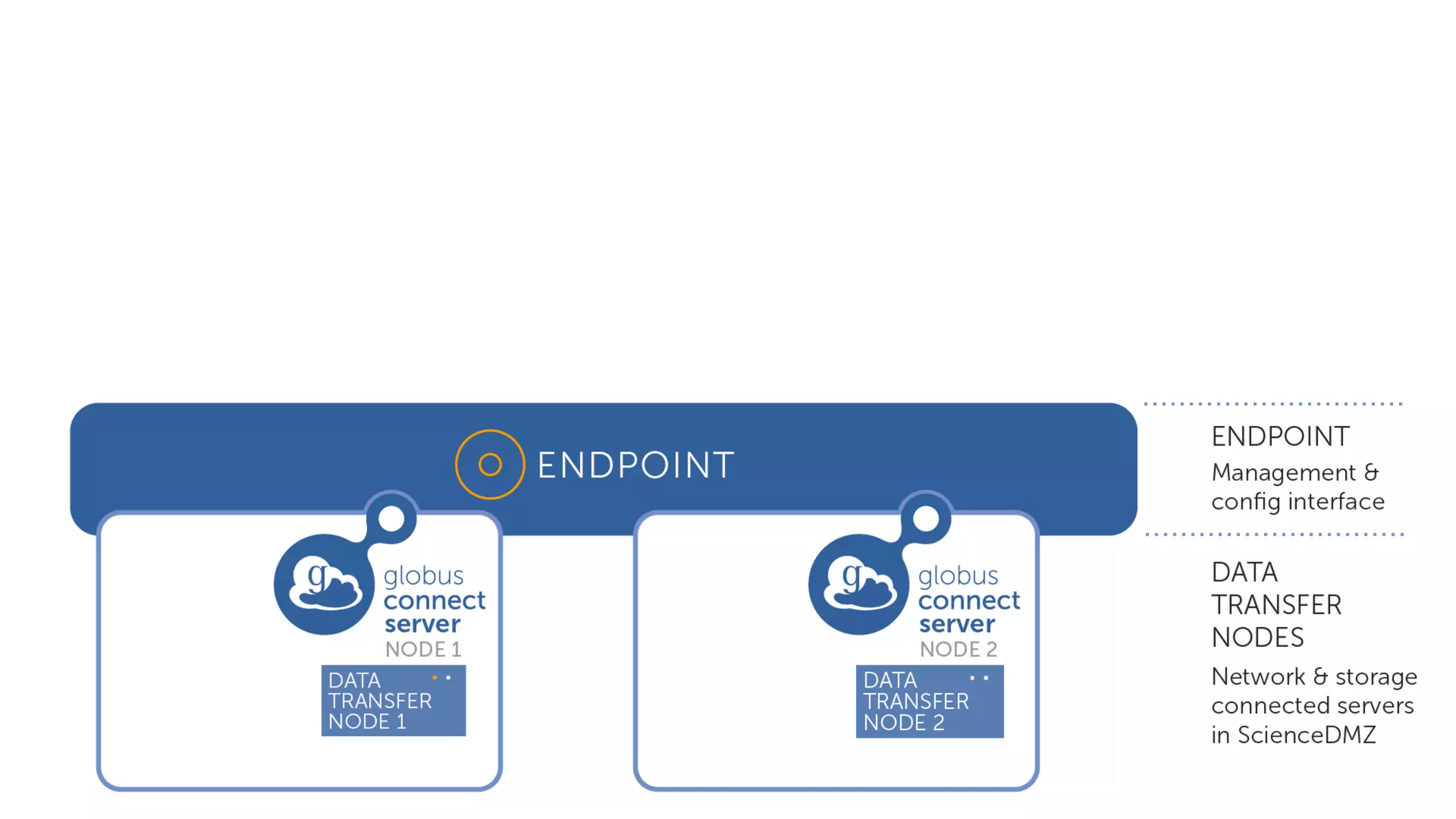
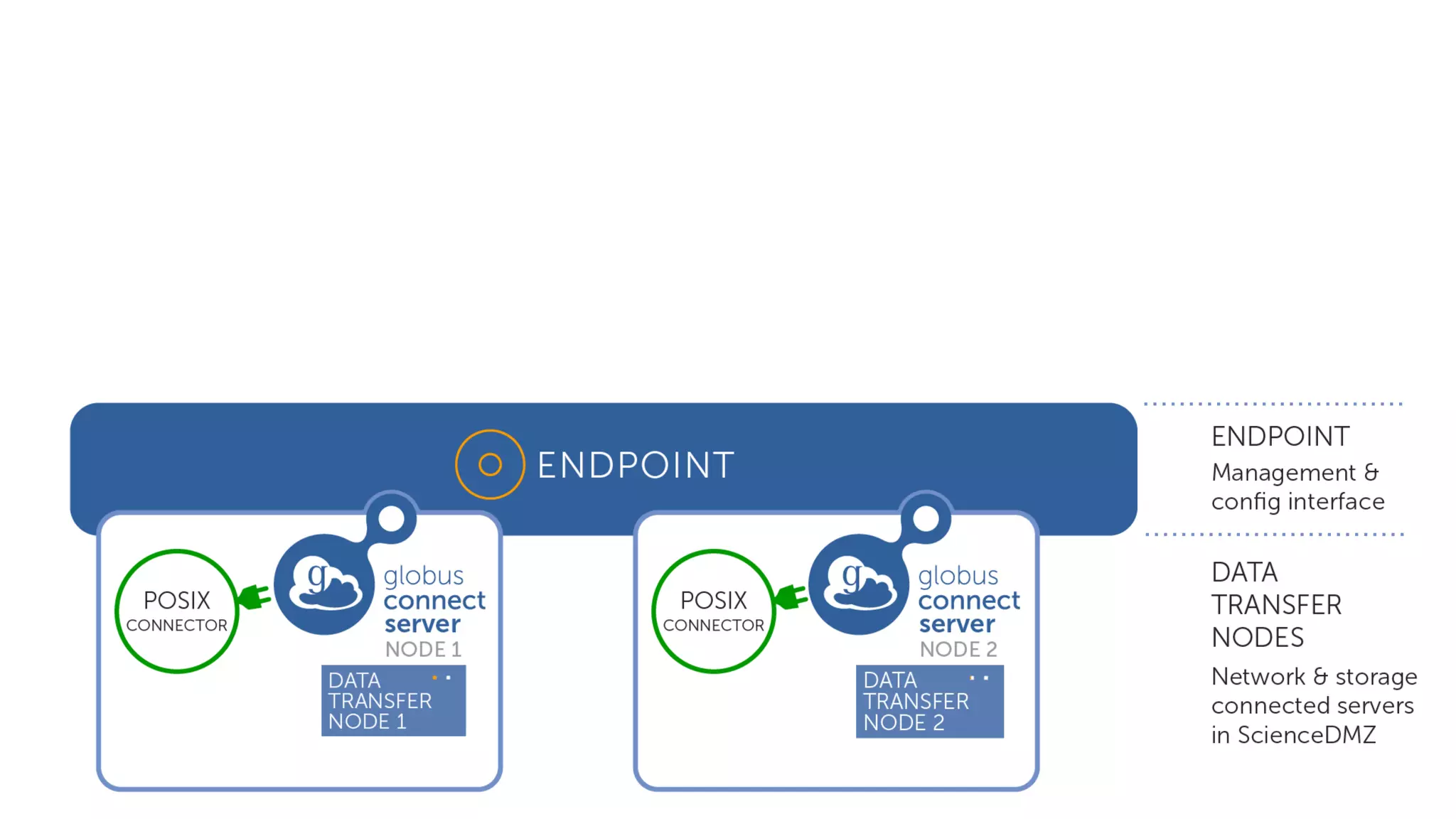
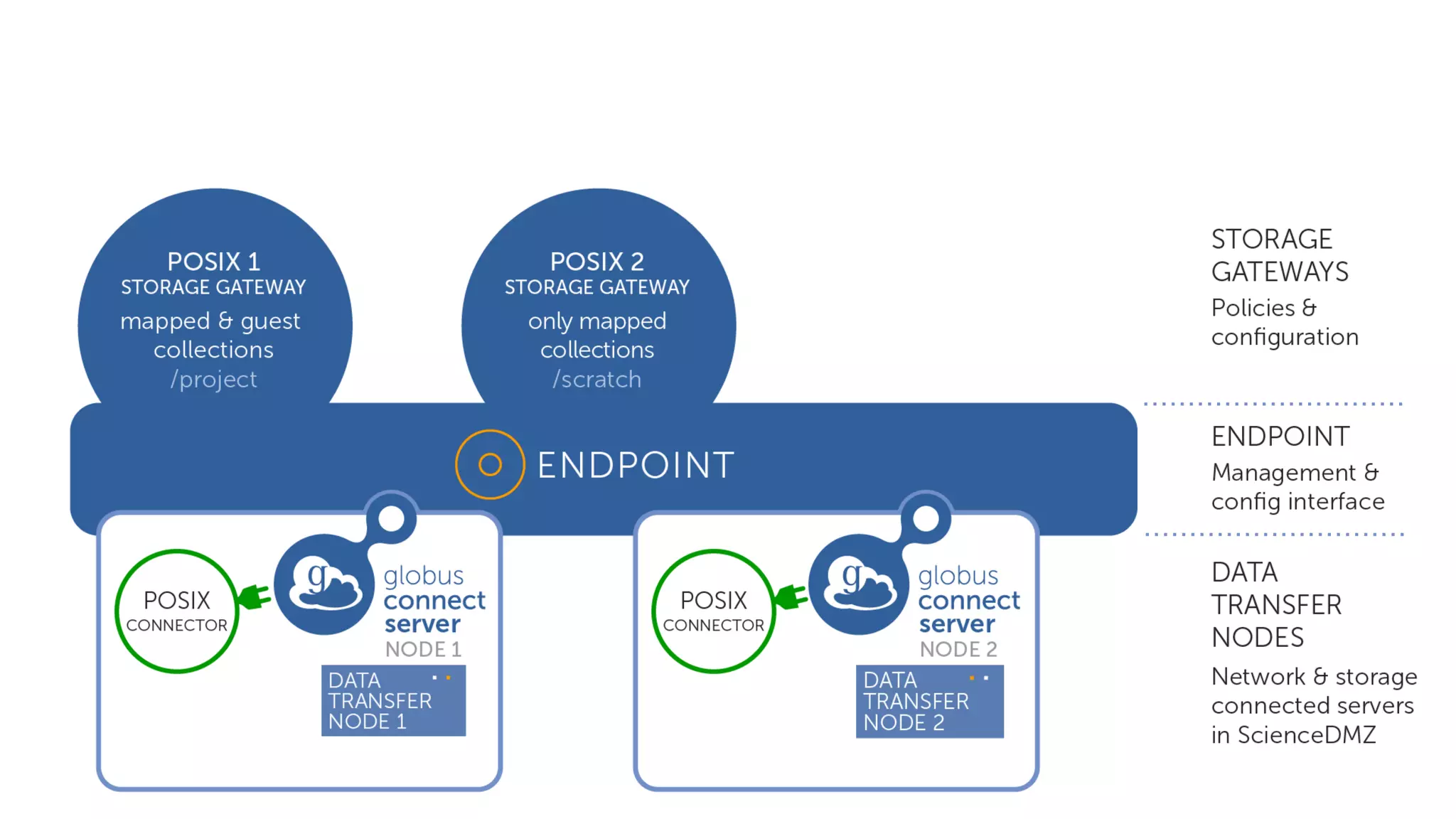
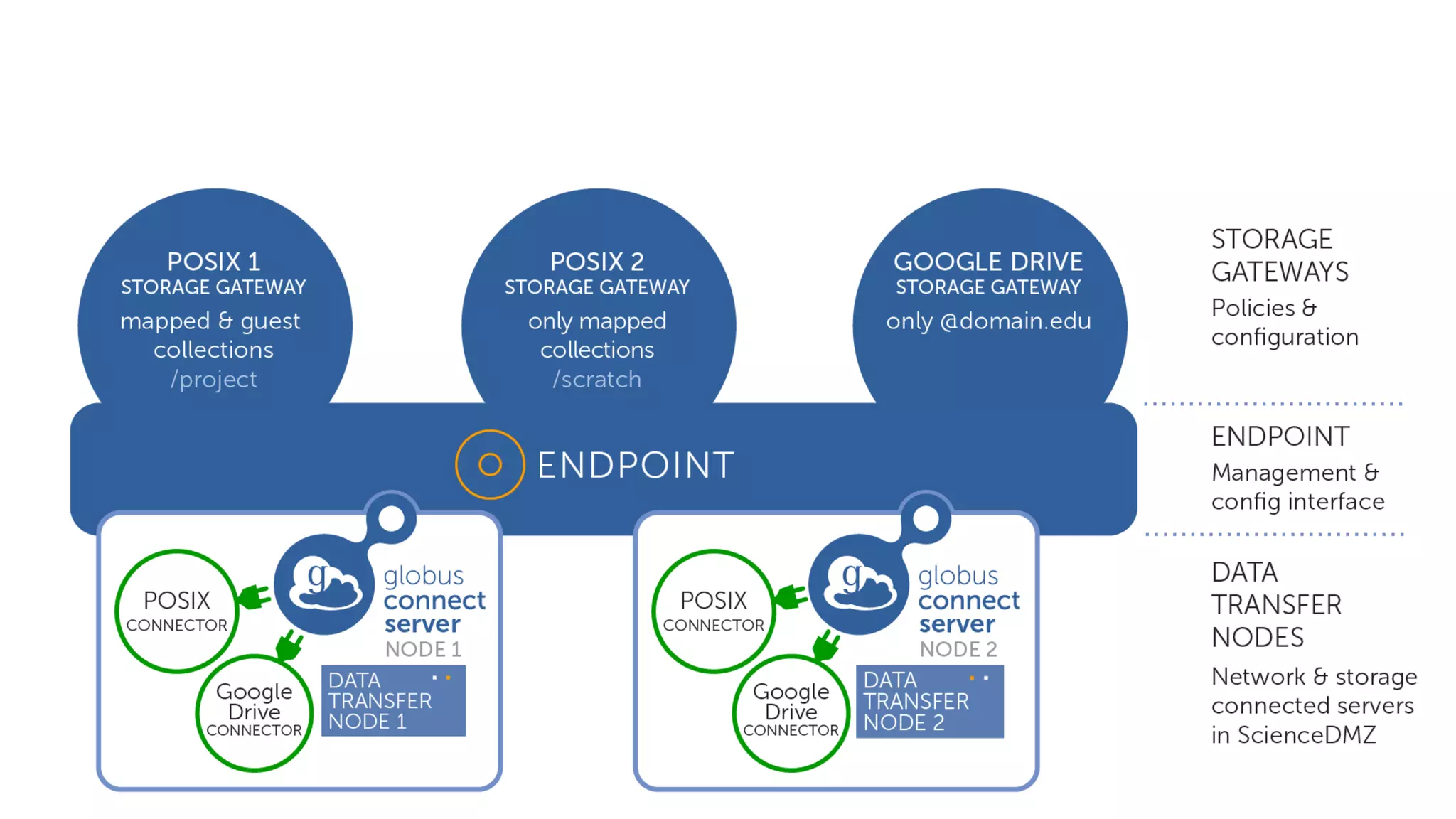
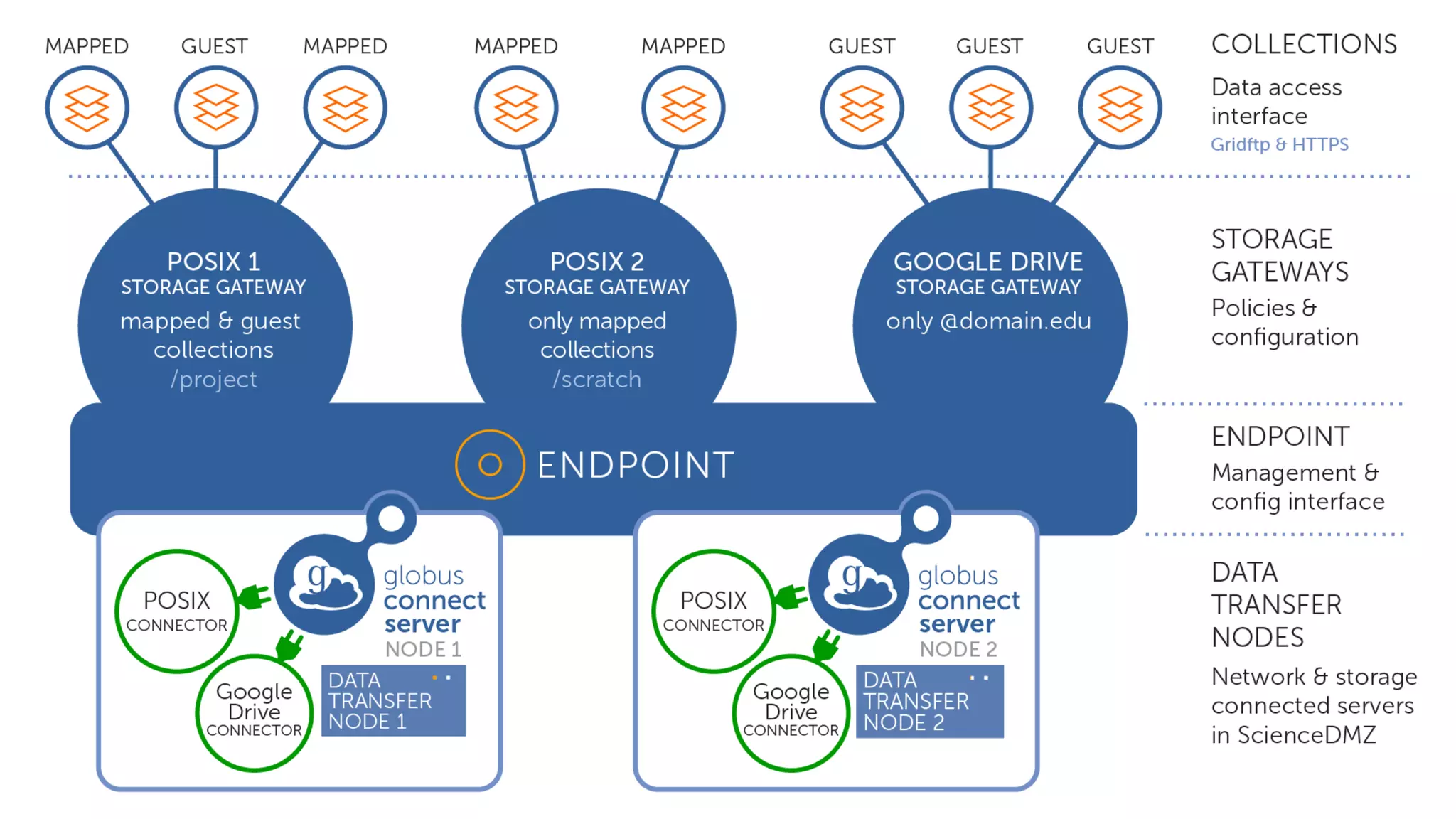
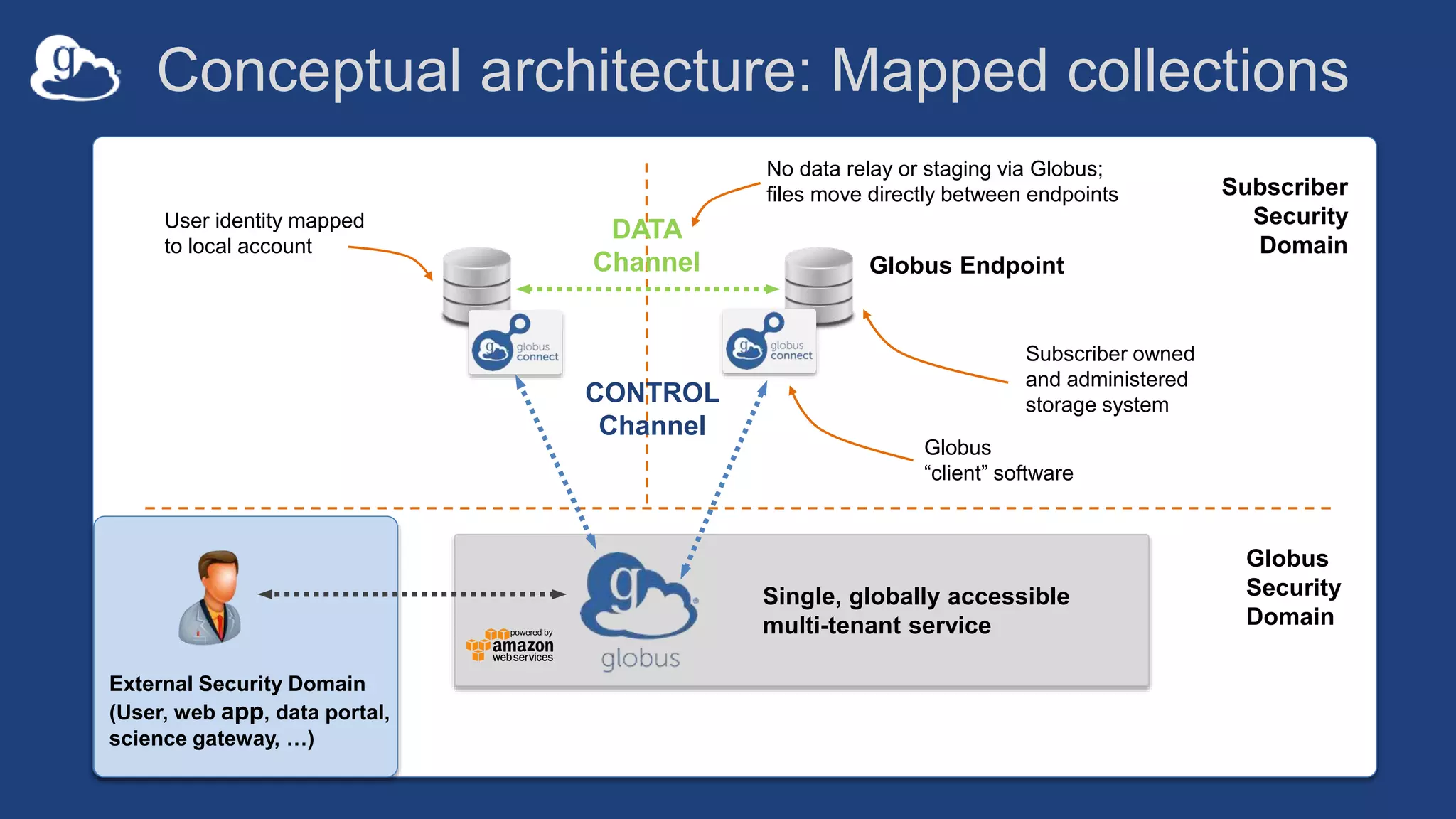
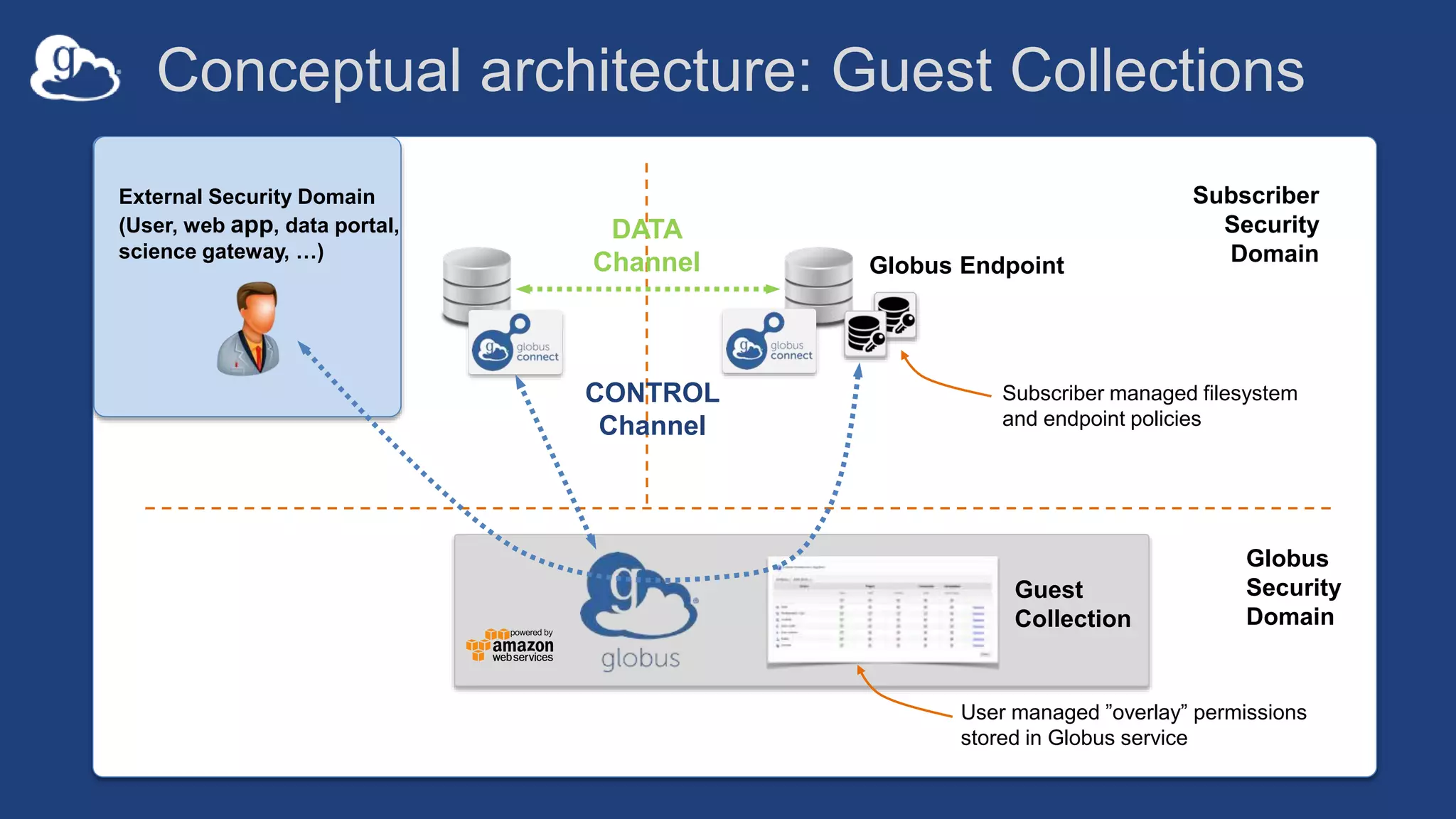
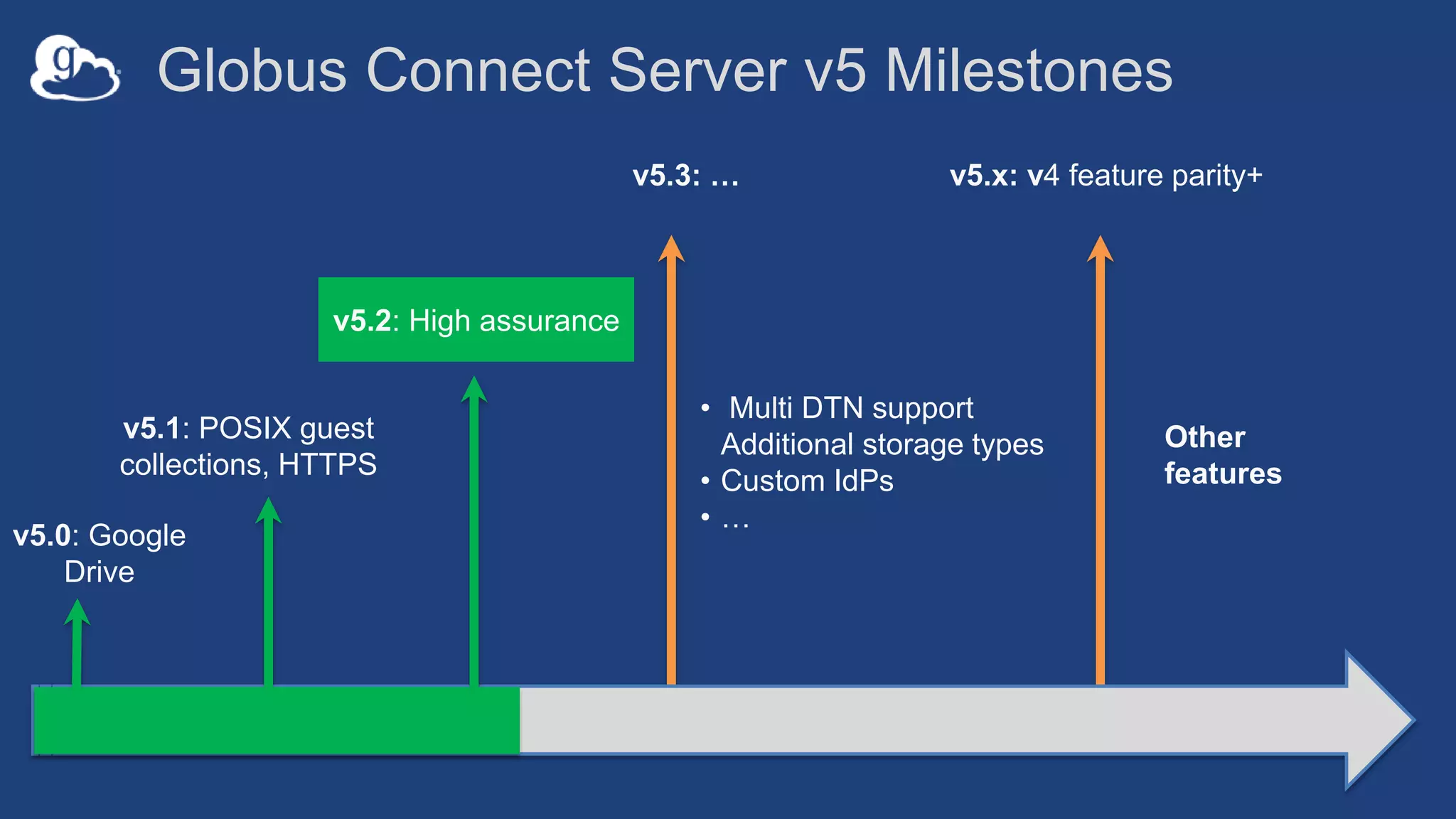
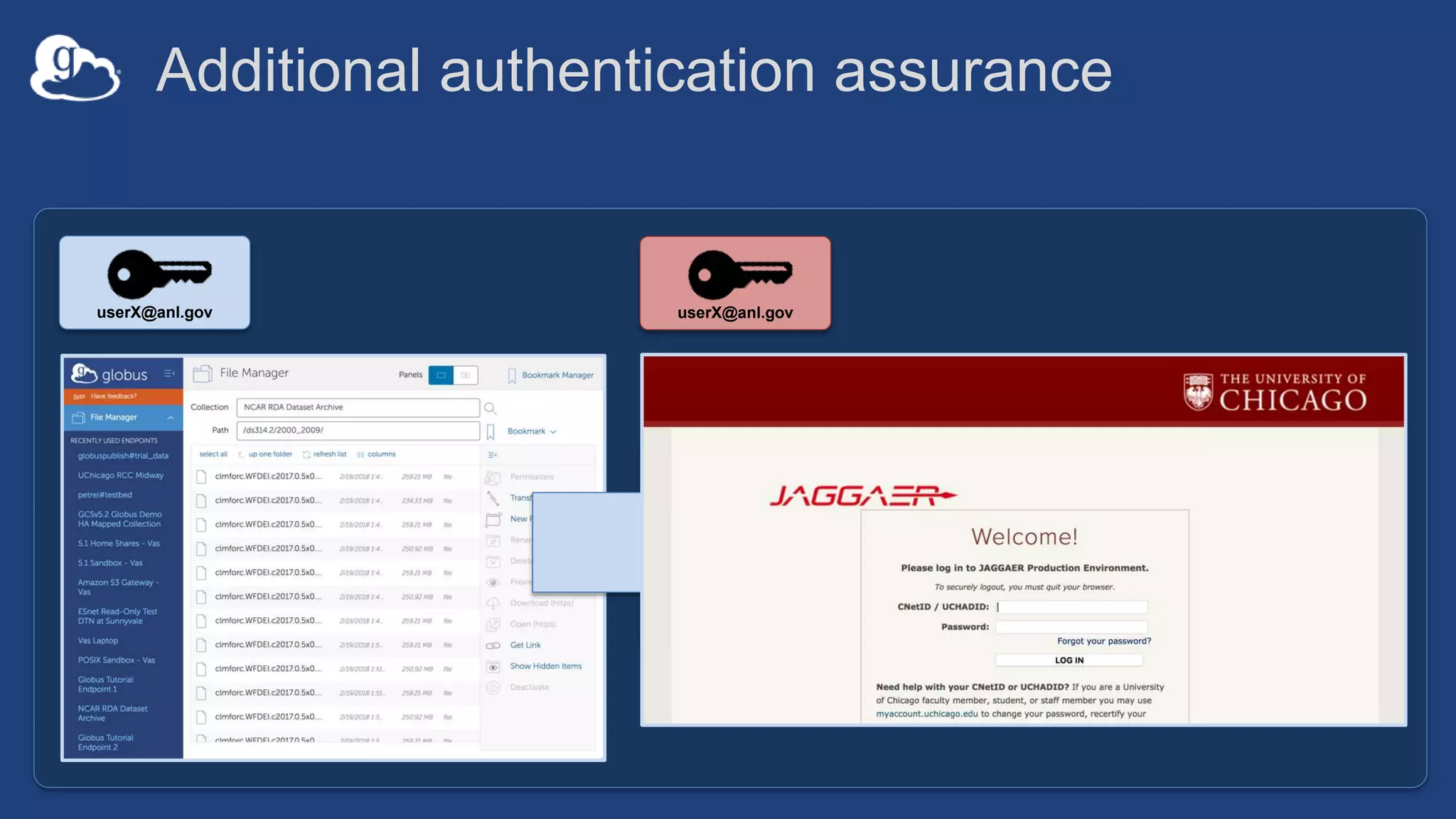
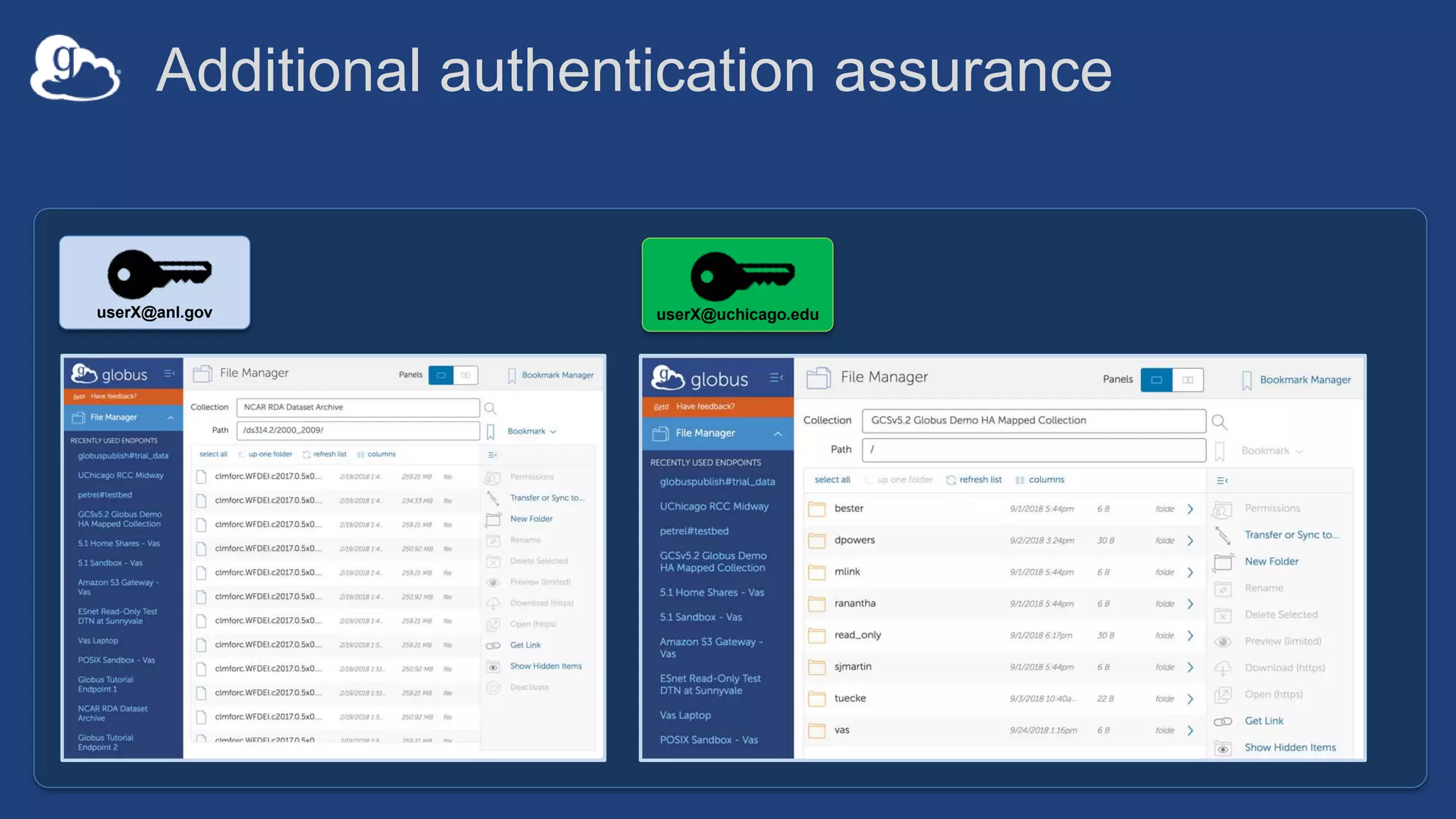
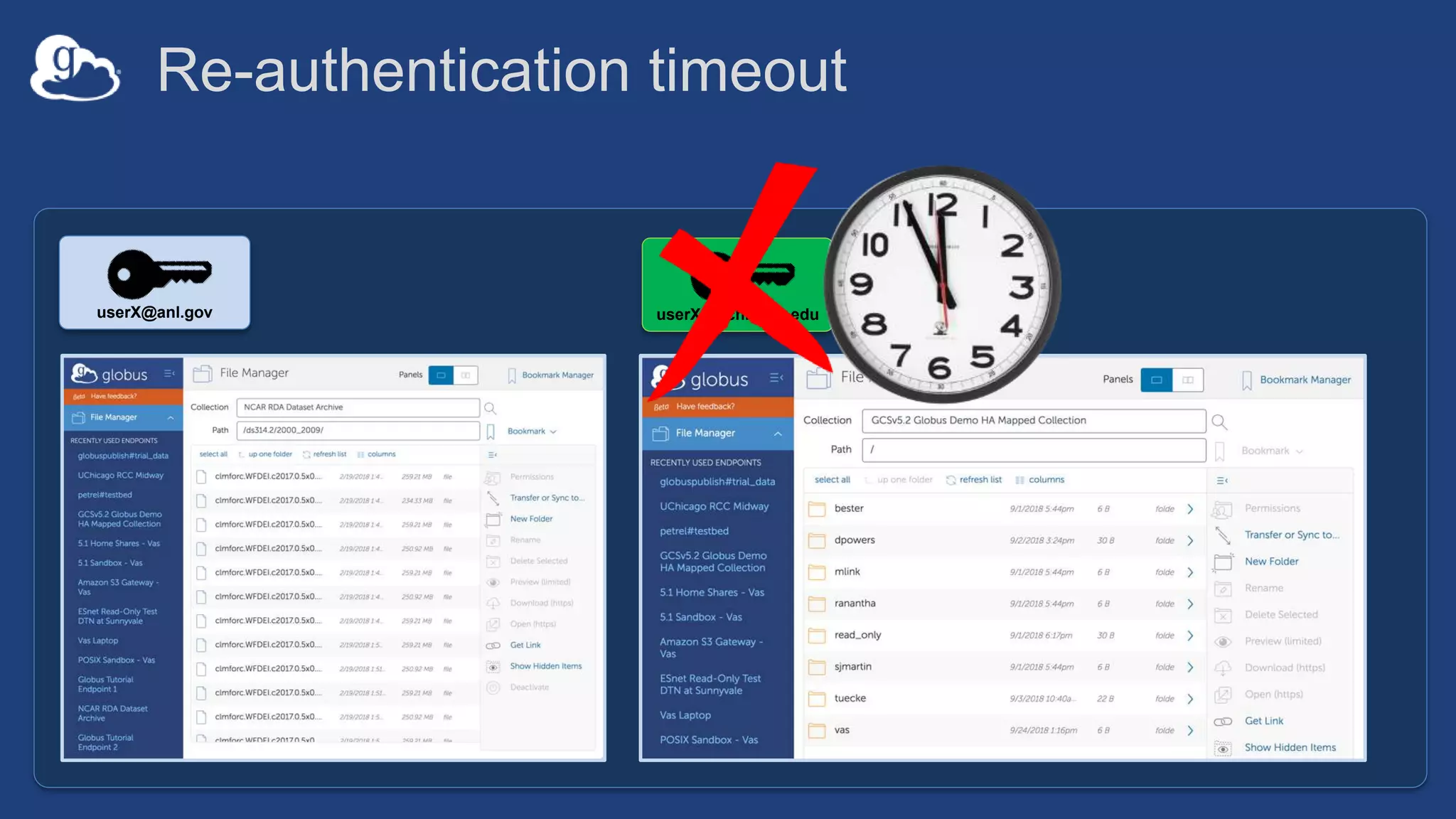
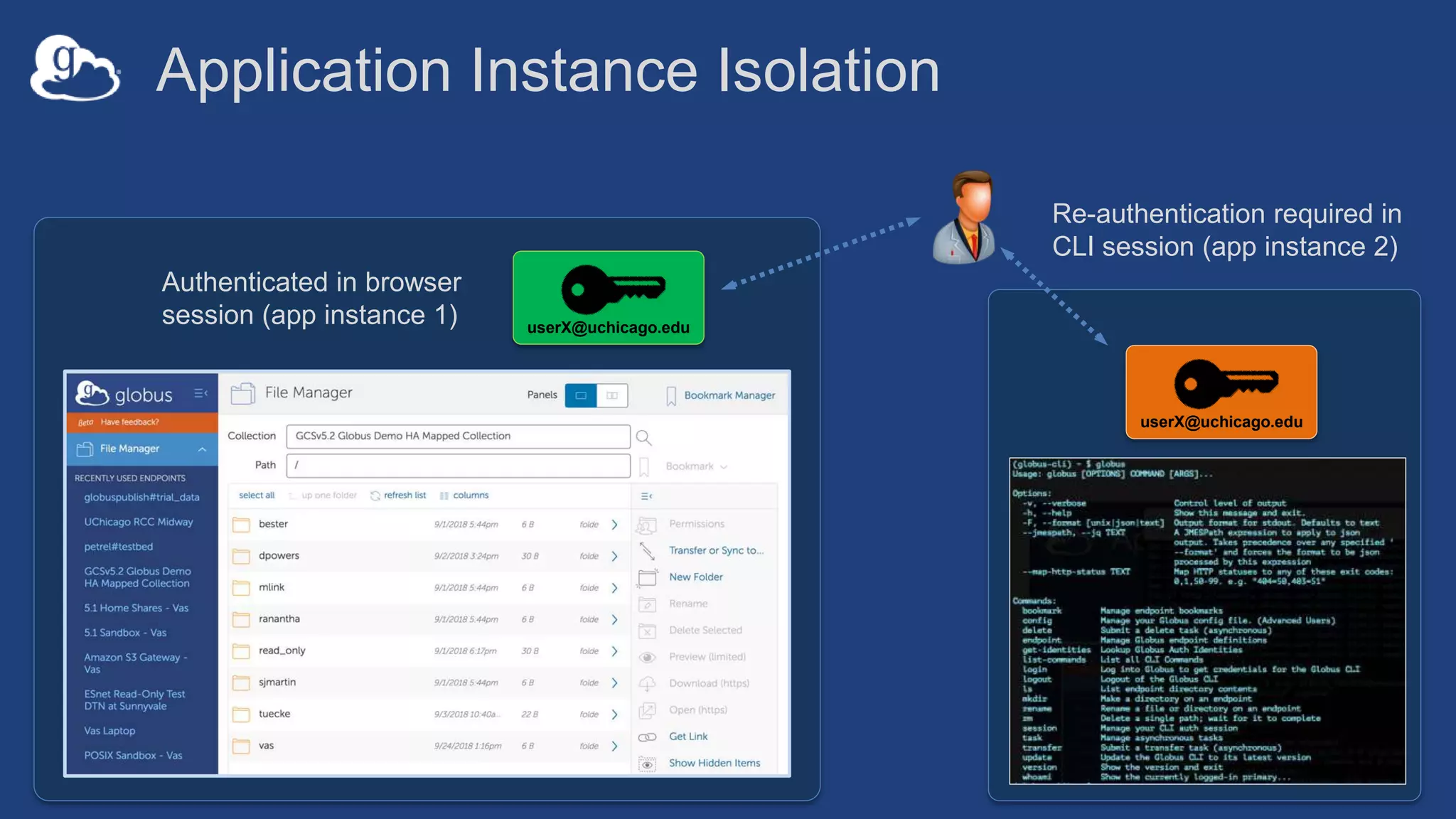
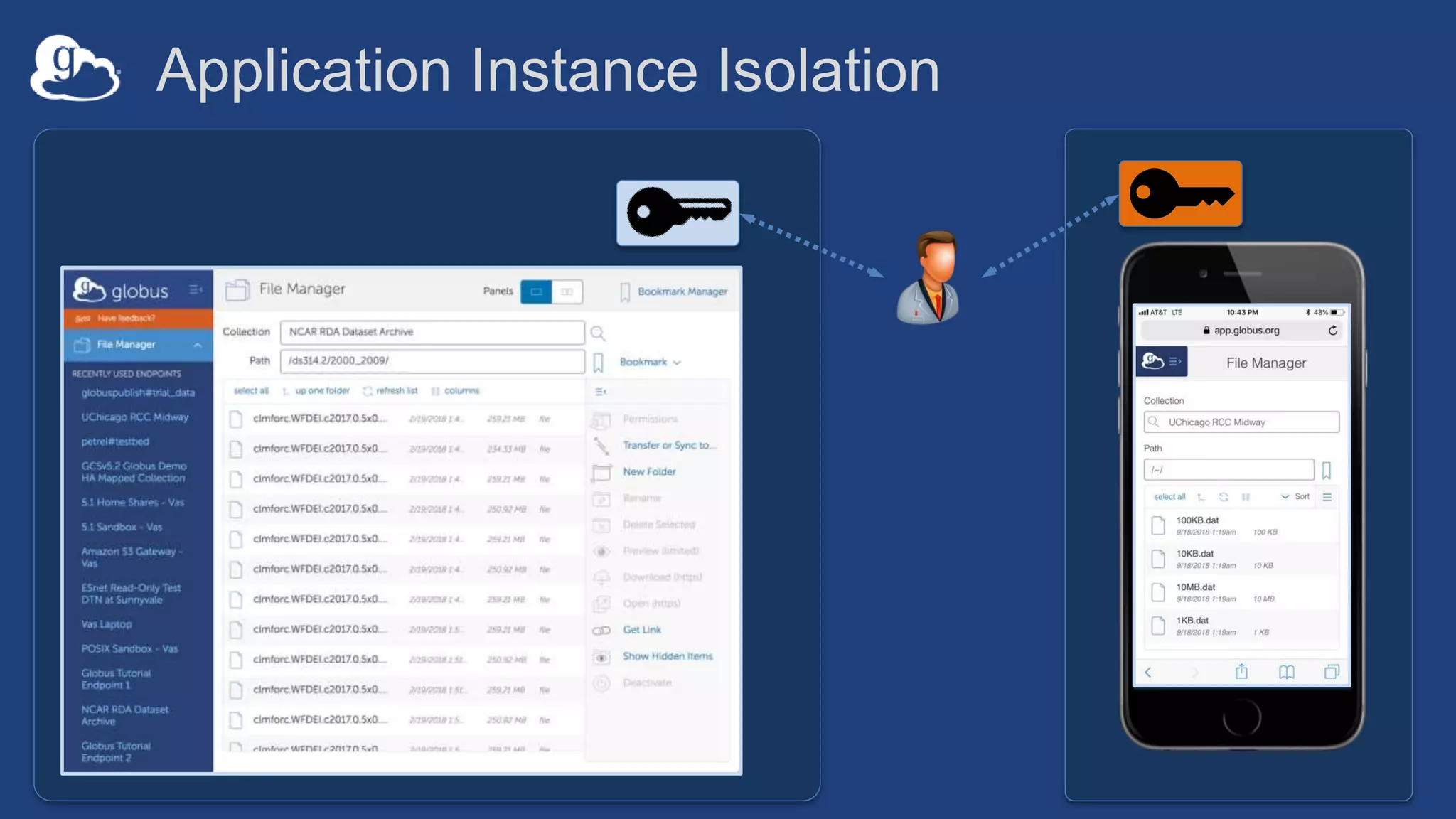
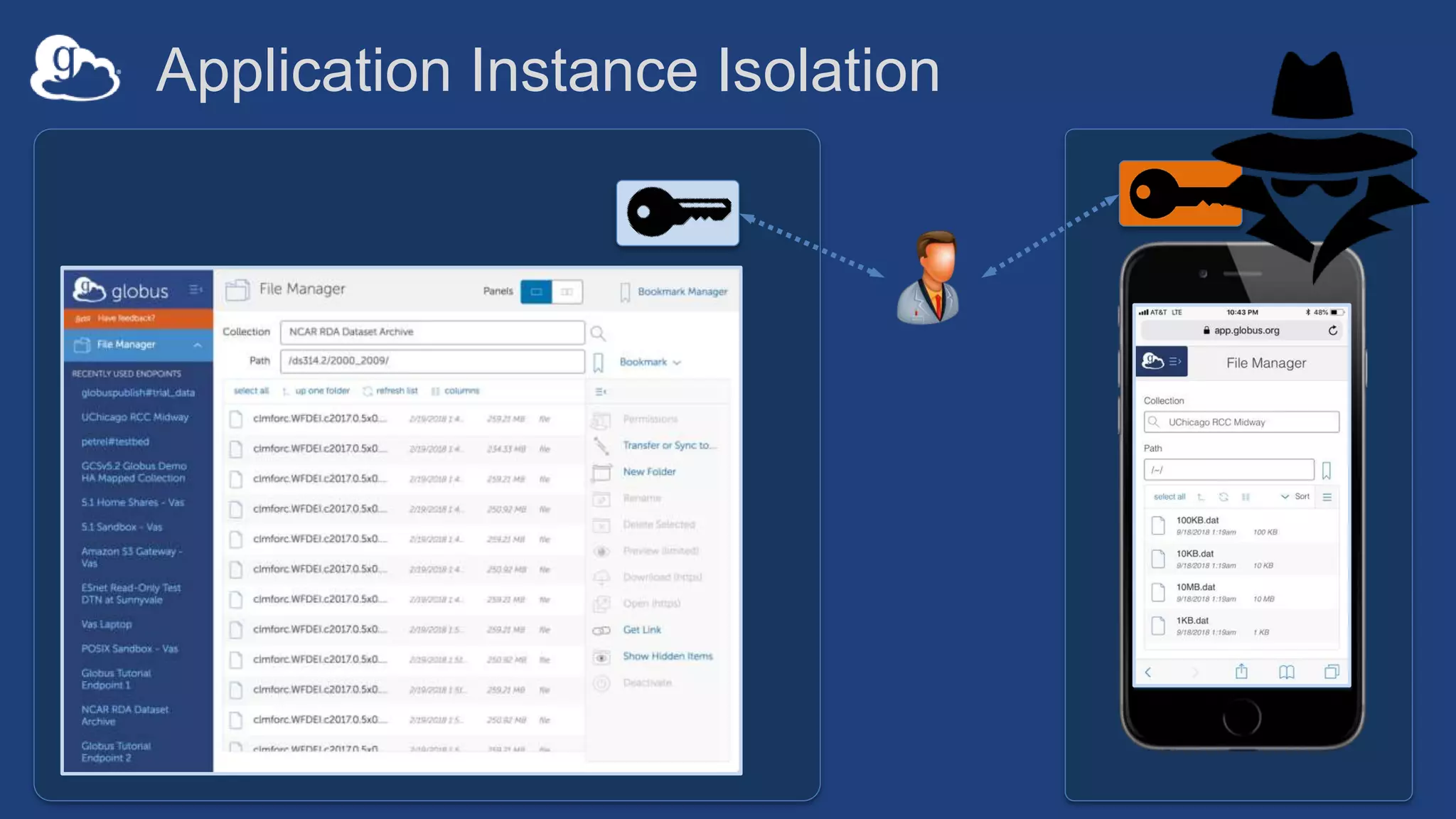
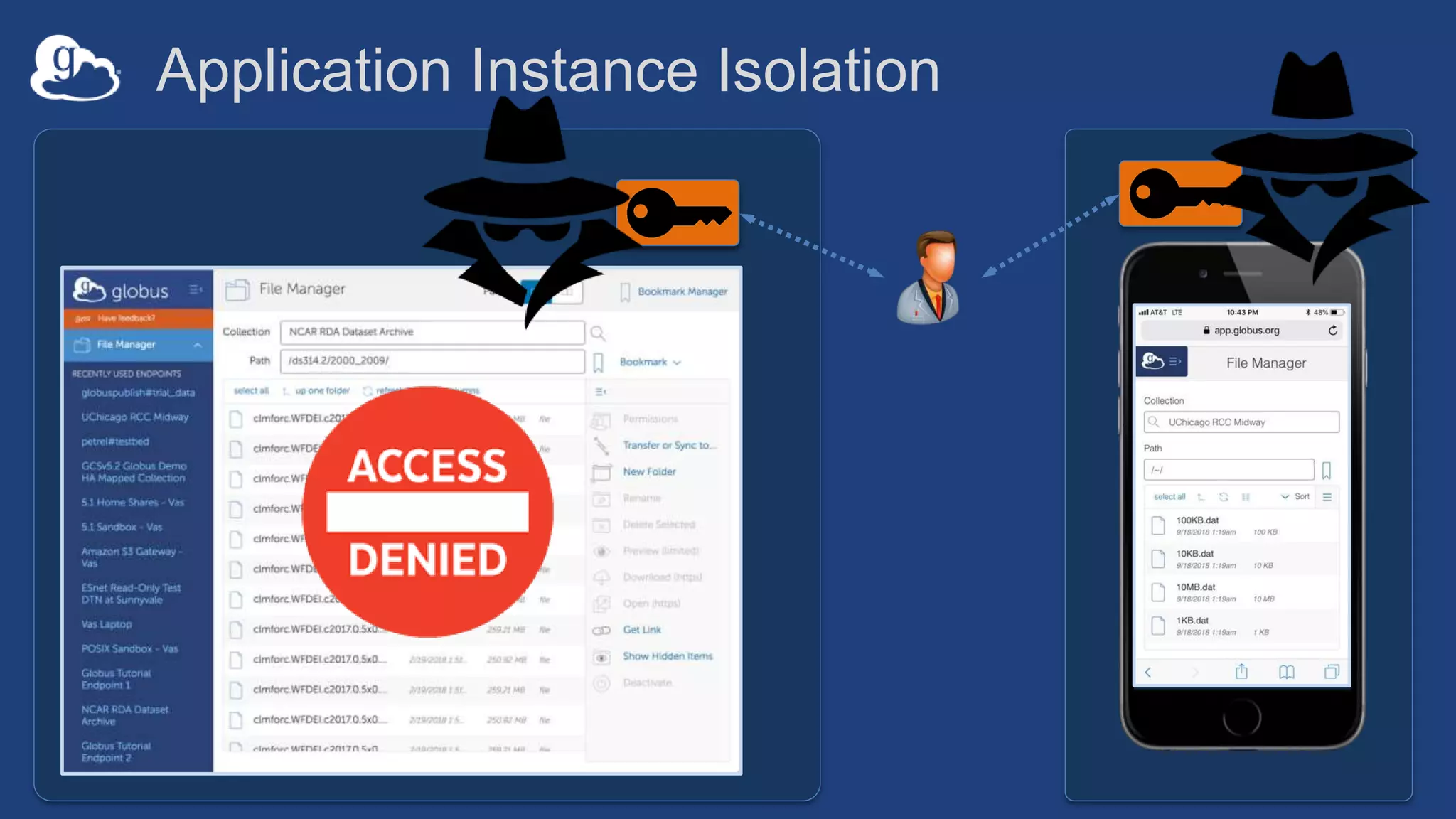
This document discusses how Globus can be used to manage protected and controlled data with high assurance. It describes features for restricting data handling according to standards like NIST 800-53 and 800-171. Compliance focuses on access control, configuration management, maintenance, and accountability. Restricted data passed to Globus does not include file contents. The initial release includes a new web app, Globus Connect Server v5.2, and Connect Personal. High assurance capabilities include additional authentication, application instance isolation, encryption, and detailed auditing. Subscription levels like High Assurance and BAA provide these features.





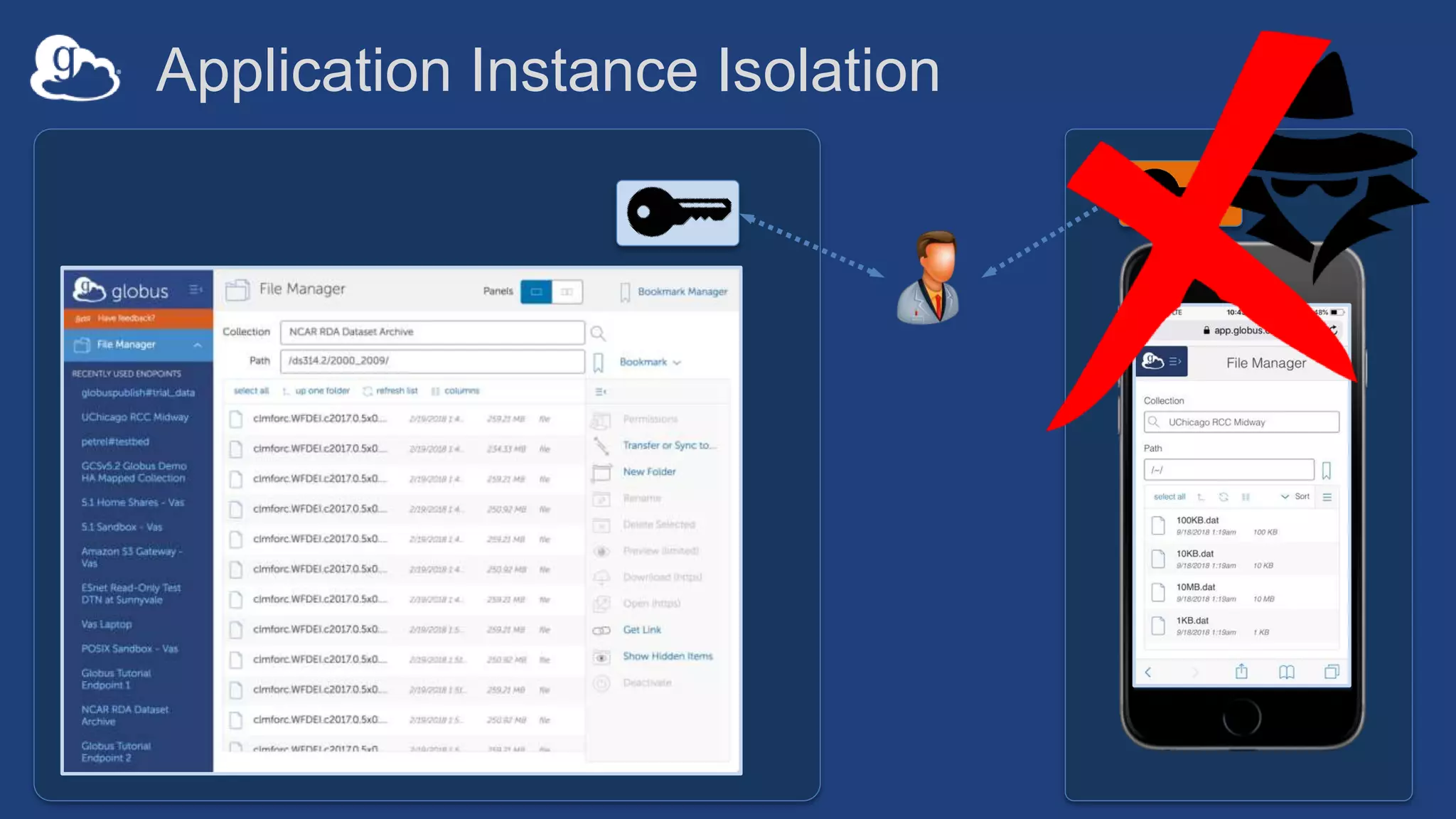
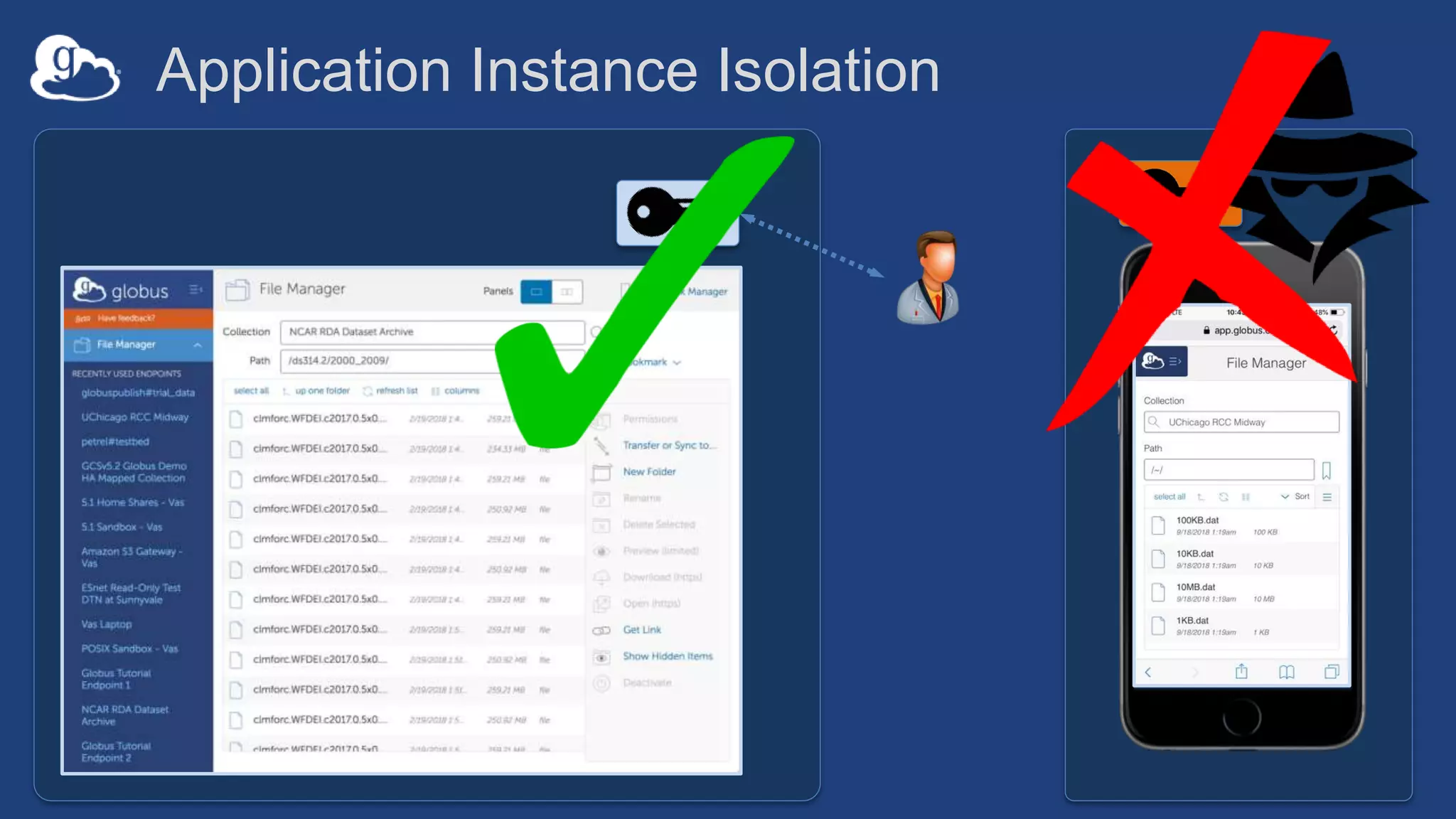



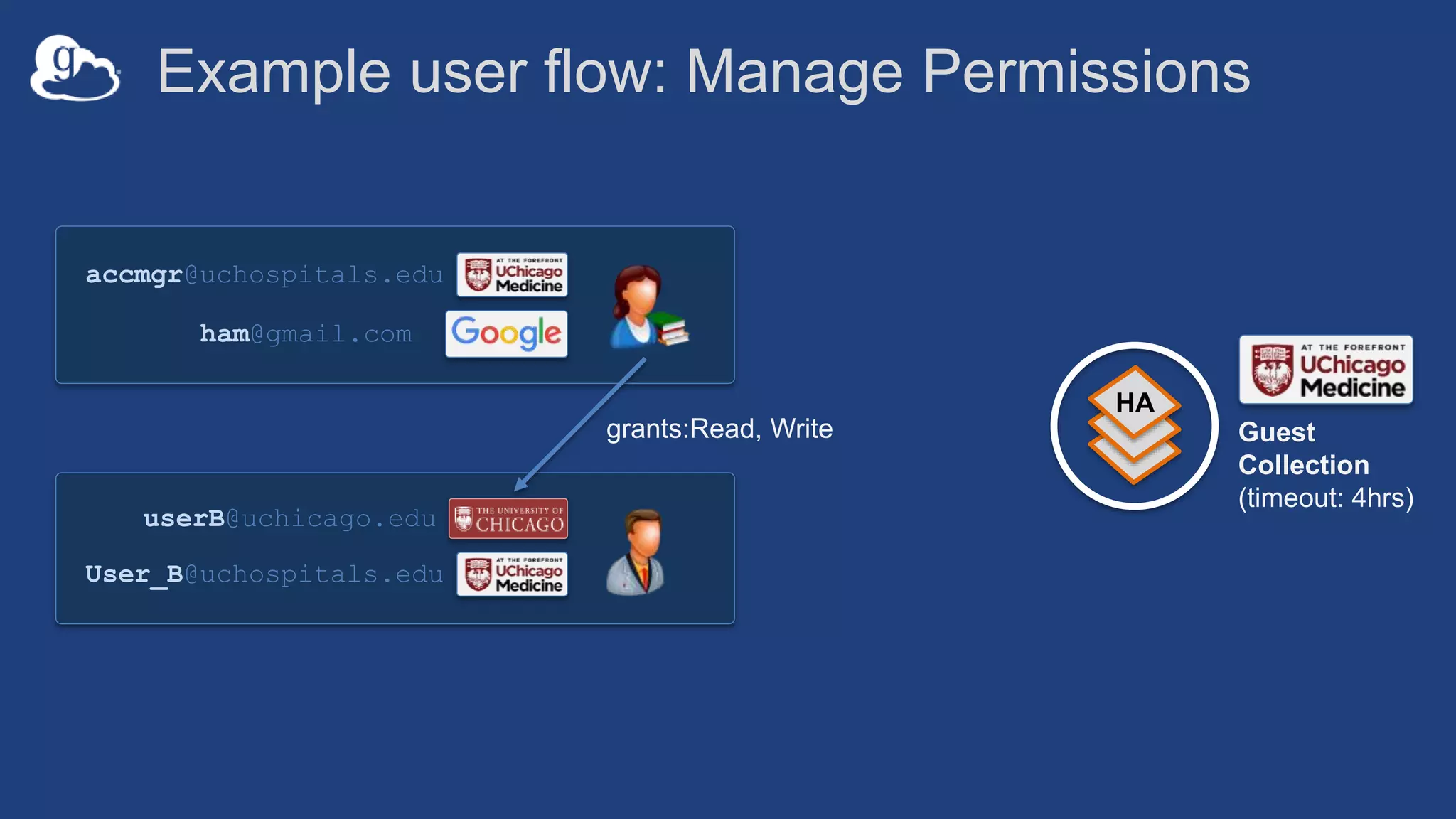
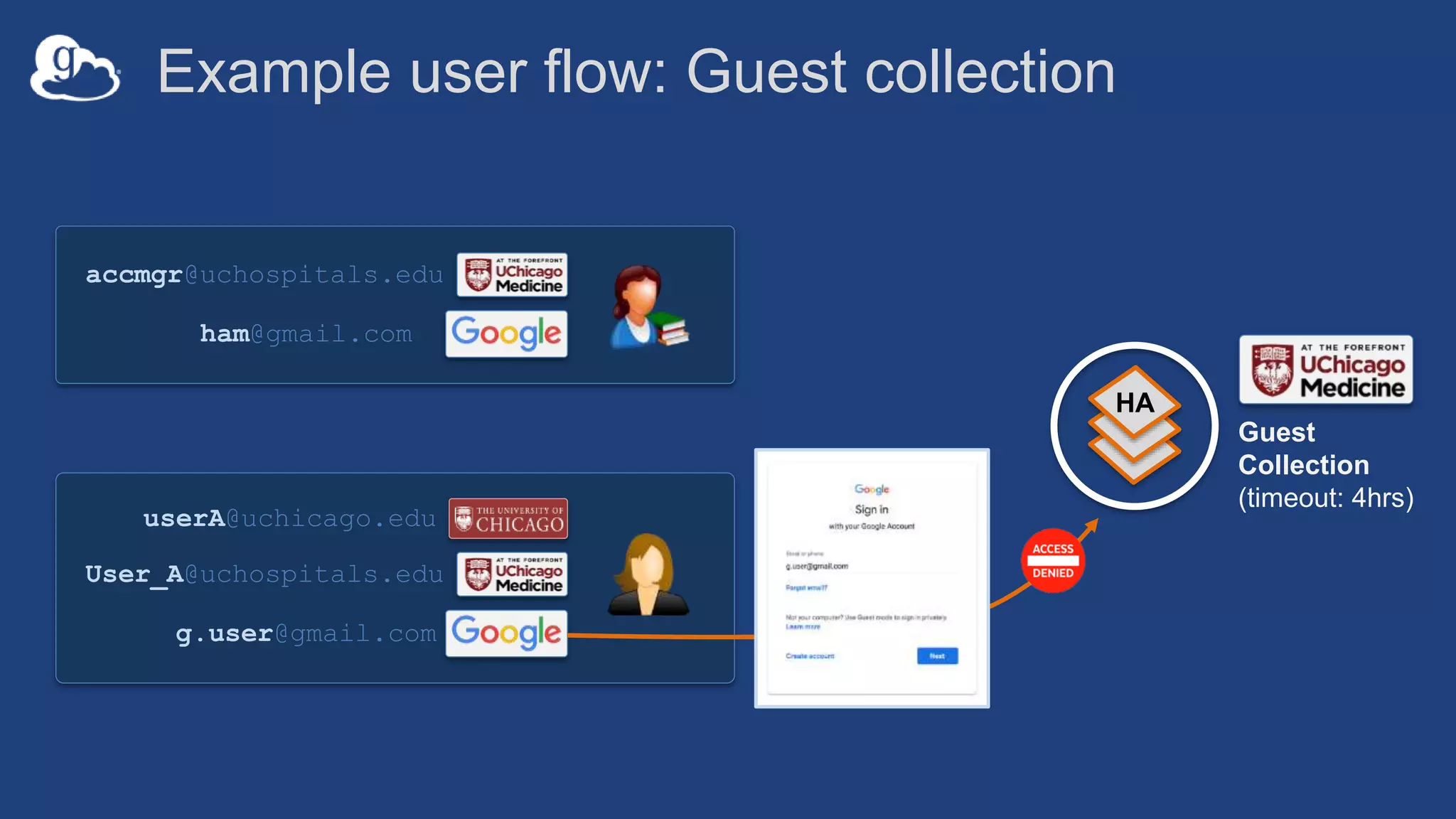
![Example user flow: Guest collection
HA
userA@uchicago.edu
User_A@uchospitals.edu
g.user@gmail.com
accmgr@uchospitals.edu
ham@gmail.com
Guest
Collection
(timeout: 4hrs)
[Role:Access Manager]
grants:Read](https://image.slidesharecdn.com/181015techex2018globusprotecteddataupdate-181019125406/75/Managing-Protected-and-Controlled-Data-with-Globus-32-2048.jpg)
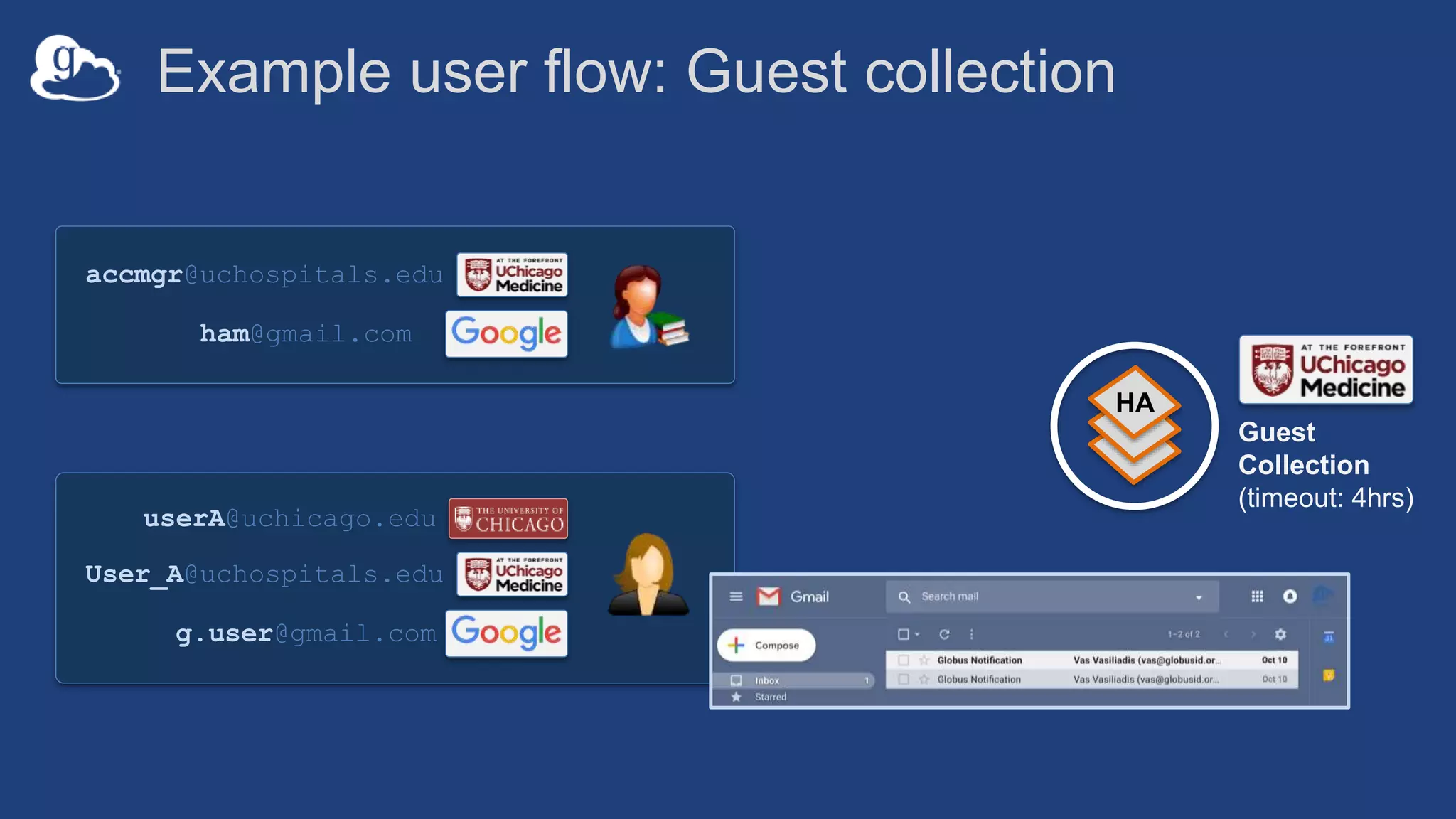
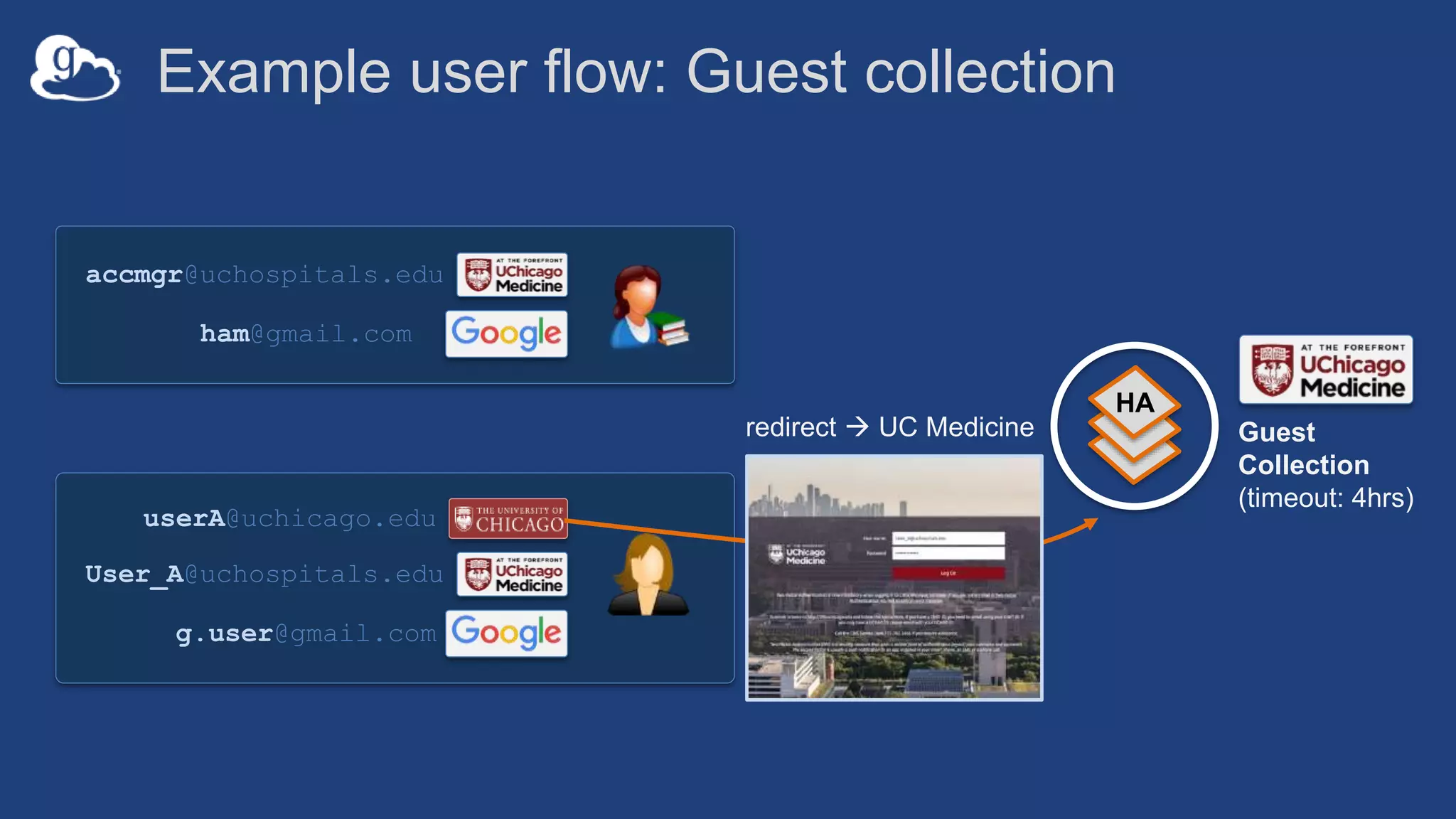
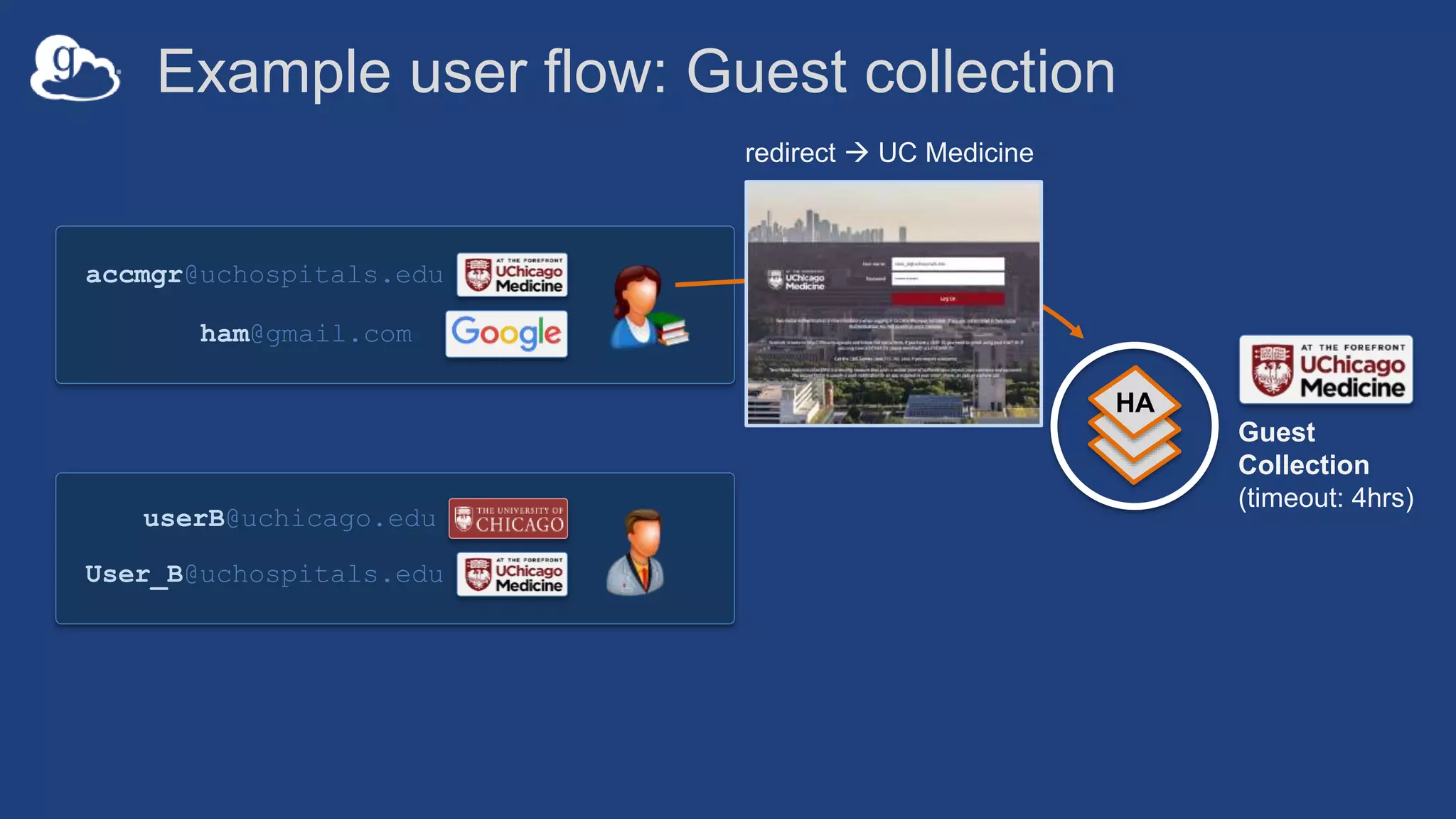
![Example user flow: Guest collection
HA
userA@uchicago.edu
User_A@uchospitals.edu
g.user@gmail.com
accmgr@uchospitals.edu
ham@gmail.com
[Permission:Read]
Guest
Collection
(timeout: 4hrs)](https://image.slidesharecdn.com/181015techex2018globusprotecteddataupdate-181019125406/75/Managing-Protected-and-Controlled-Data-with-Globus-36-2048.jpg)