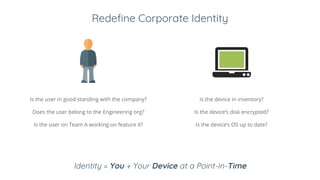
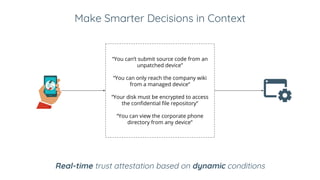
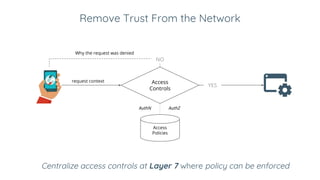
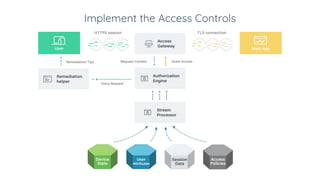
Ivan Dwyer presented on Google's BeyondCorp approach to closing the adherence gap between written security policies and actual practices. BeyondCorp moves away from network-based access controls and instead bases access on authenticating the user, authorizing their identity and device, and encrypting the connection. It aims to allow employees to work from any network without a VPN. BeyondCorp takes a zero-trust approach, dynamically assessing identity as the user plus their device at a given time. Access decisions are made in real-time based on the request context and policies that consider user attributes, device security and more. BeyondCorp implementations generally start with inventories, write use cases, determine policy frameworks, and then implement dynamic access controls.