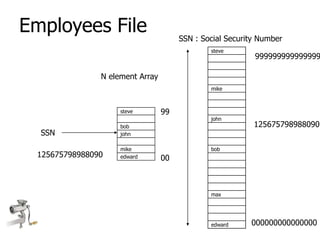
This document describes hash maps and hash tables. It provides examples of using a hash function to map keys to indexes in an array, which can store key-value pairs. It discusses concepts like collisions, load factor, and different strategies for handling collisions like open addressing and closed addressing.



























































![Bucket Table Implementation
KEY VAL
char keys Array [M] int values Array [M]](https://image.slidesharecdn.com/hashmap-150723131344-lva1-app6891/85/Hash-map-62-320.jpg)
![Put(key, value) simplified algo
M = # bucket entries
index = hash (key)
While Key [index) != empty
index = (index + 1) % M
End while
Key [index] = key
Values [index] = value](https://image.slidesharecdn.com/hashmap-150723131344-lva1-app6891/85/Hash-map-63-320.jpg)





![Get(key)
M = # buckets
index = hash (key)
valueToReturn = -1 // value to return if the key is not in the map
While Key [index] != key and Key [index] != empty
index = (index + 1) % M
End while
If (Key [index] = key) valueToReturn = Values [index]
Return valueToReturn](https://image.slidesharecdn.com/hashmap-150723131344-lva1-app6891/85/Hash-map-69-320.jpg)
































![Remove (key) simplified algo
M = # buckets
index = hash (key)
While Key [index) != key and Key [index) != empty
index = (index + 1) % M
End while
Key [index] = 0, Value [index] = 0
// rehash
index = (index + 1) % M
While Key [index) != empty
savedKey = Key [index], savedValue = Value [index]
Key [index] = 0 Value [index] = 0
Put ( savedKey , savedValue )
index = (index + 1) % M
End while](https://image.slidesharecdn.com/hashmap-150723131344-lva1-app6891/85/Hash-map-102-320.jpg)
