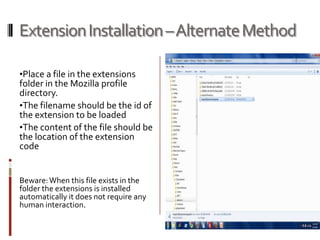
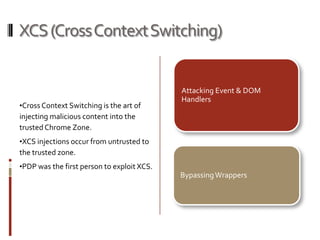
This presentation demonstrates how the Mozilla Firefox platform could potentially be misused through malicious extensions or cross-context switching attacks. It discusses the modular and pluggable nature of Firefox extensions, and shows how extensions can be installed without review and gain full system privileges. The presentation then demonstrates attacks like keylogging, executing native code, and extracting passwords by building a malicious extension. It also explores techniques like cross-context switching and event handler attacks to subvert extension security. Developers are advised to follow security best practices to avoid these kinds of issues in their own extensions.