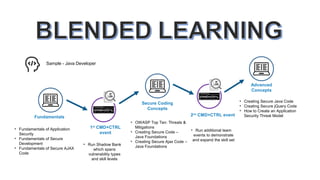
The document discusses a simulation platform designed for cybersecurity teams to enhance their skills and manage workforce planning. It offers an engaging training environment that covers various security concepts, including secure coding practices and threat modeling. The platform allows for assessment of individual and team performance and helps in mapping learning paths to foster a security culture.