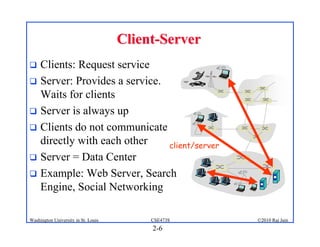
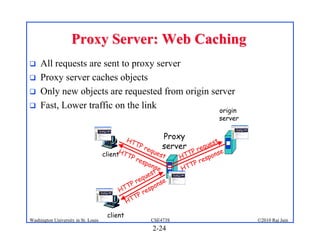
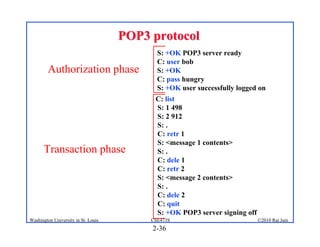
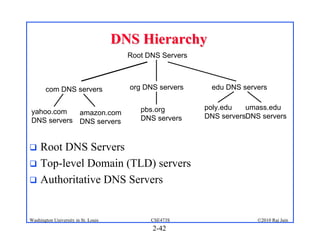
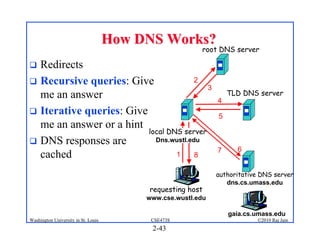
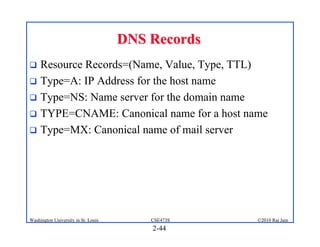
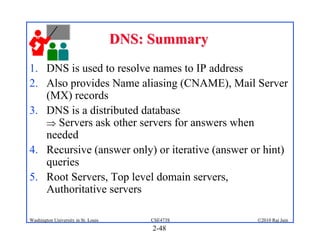
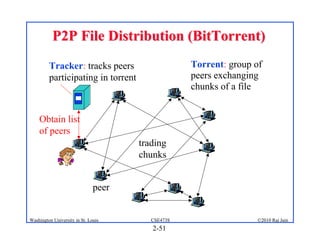
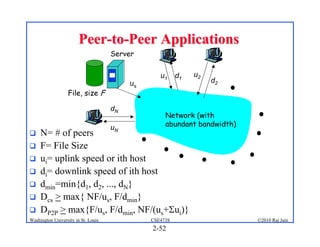
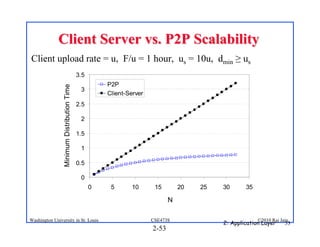
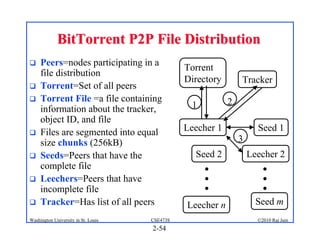
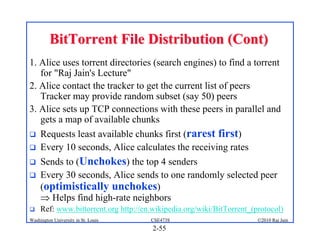
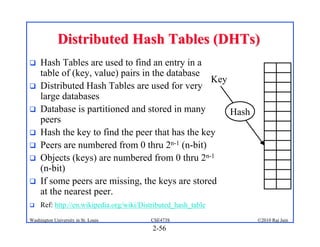
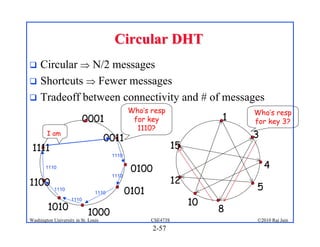
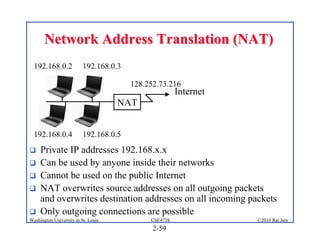
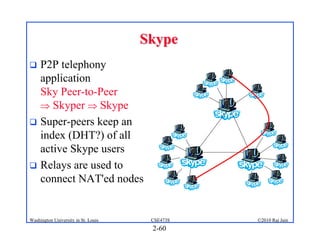
1. The document discusses network application architectures including client-server and peer-to-peer models.
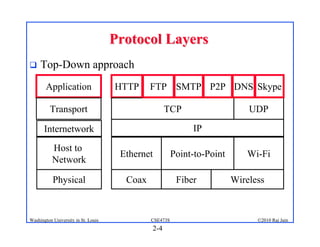
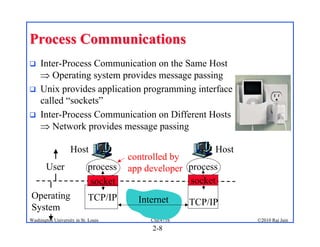
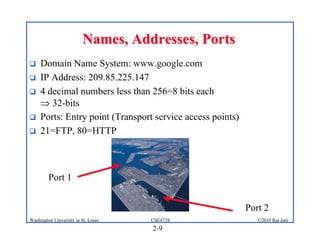
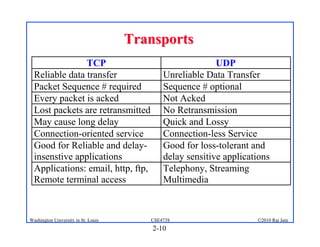
2. Applications use sockets to communicate between processes on the same or different hosts using names, addresses, ports, and transports like TCP and UDP.
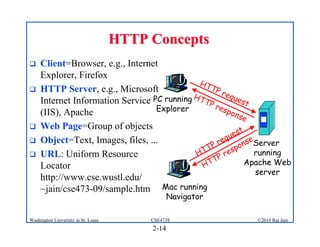
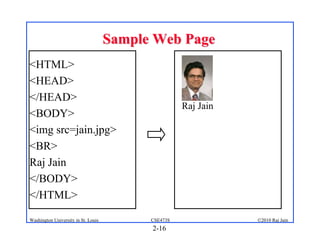
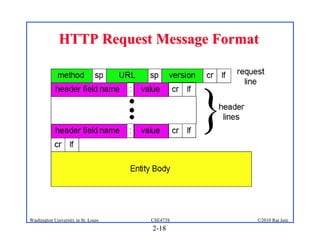
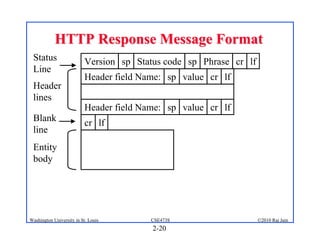
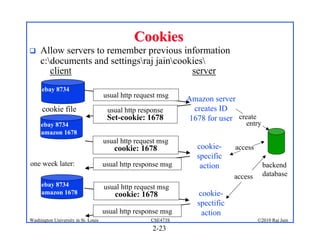
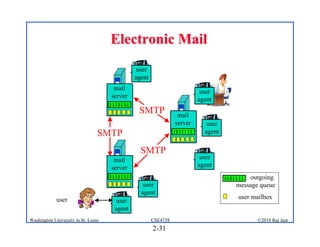
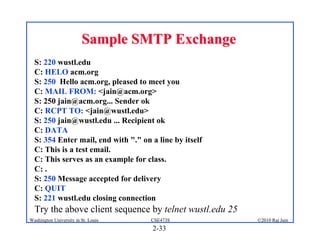
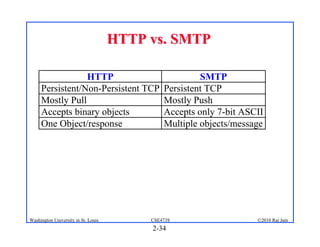
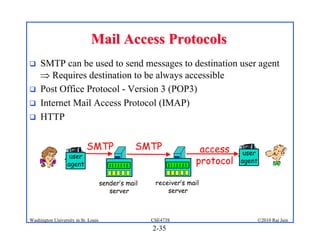
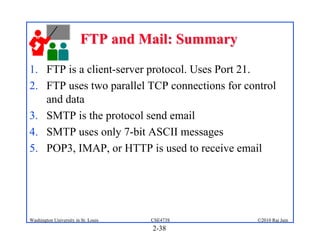
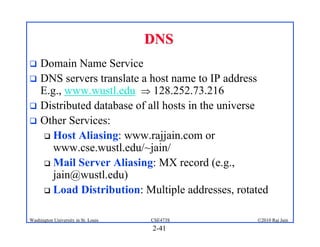
3. Specific application layer protocols are mentioned, including HTTP, FTP, SMTP, DNS, and peer-to-peer applications.