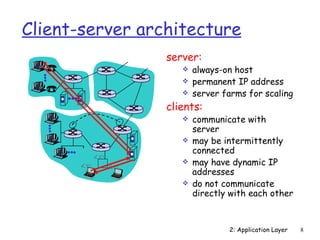
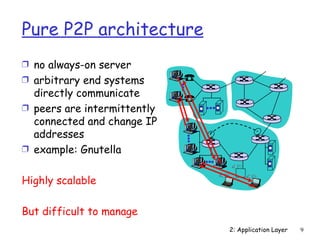
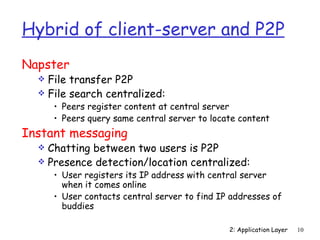
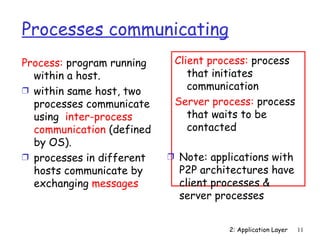
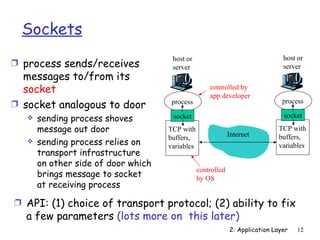
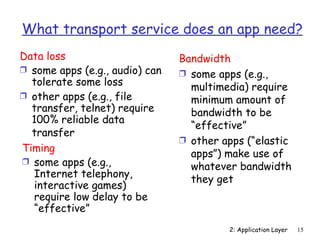
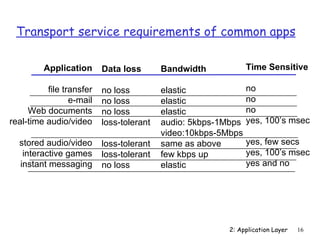
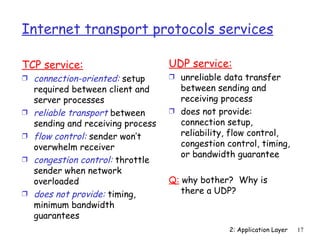
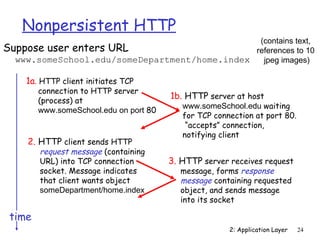
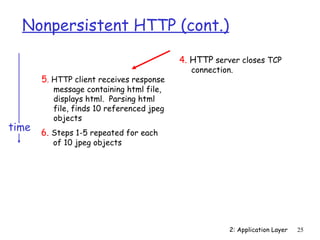
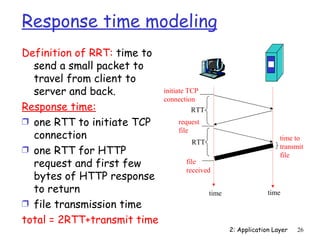
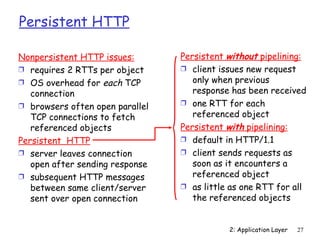
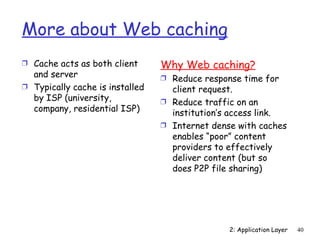
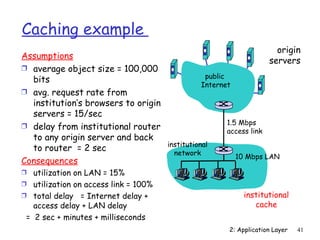
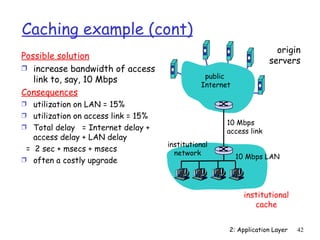
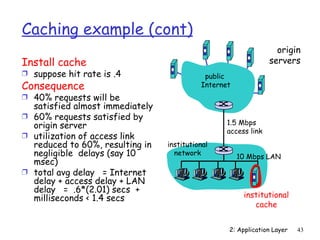
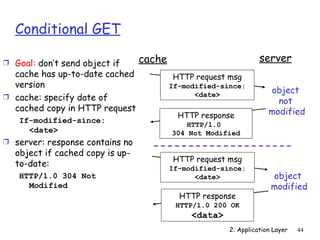
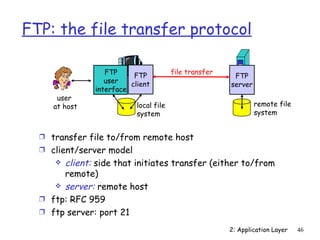
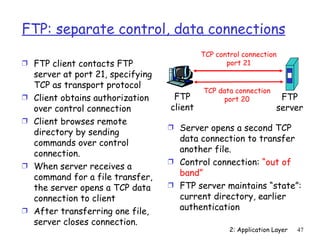
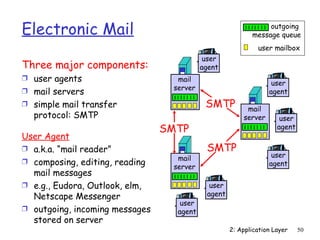
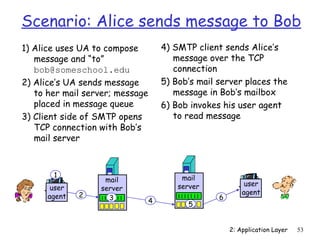
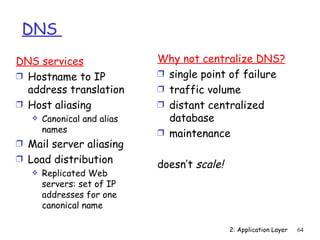
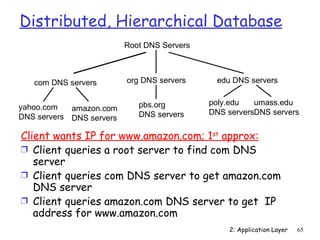
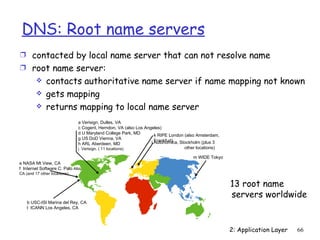
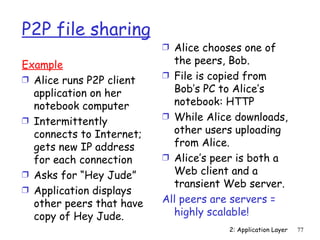
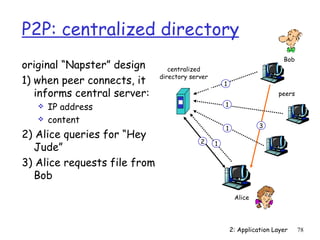
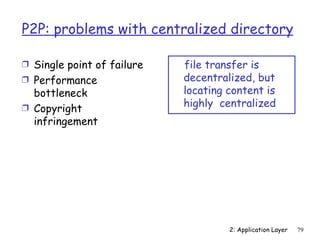
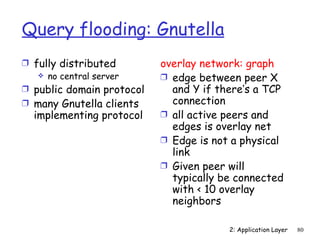
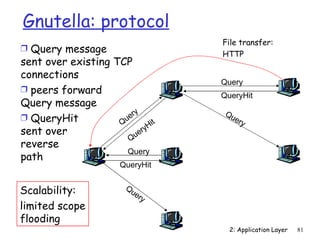
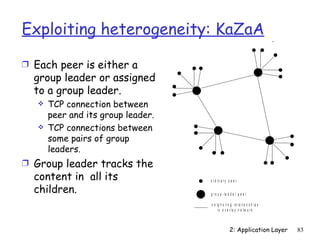
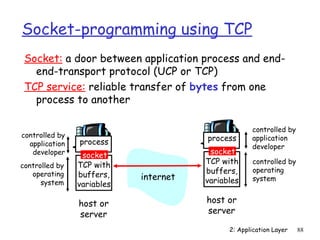
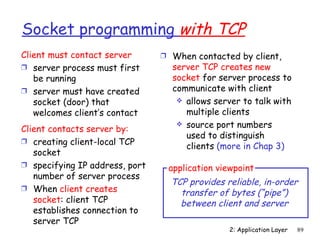
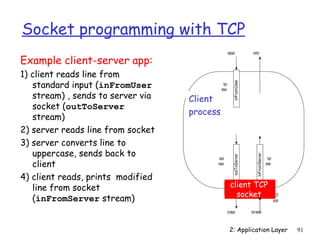
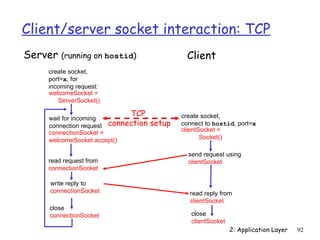
The document discusses the application layer and summarizes key points about several popular application layer protocols including HTTP, FTP, SMTP, POP3, IMAP, and DNS. It also covers principles of network applications, application architectures including client-server and peer-to-peer, how processes communicate across a network using sockets, and what transport service requirements common applications have in terms of data loss, bandwidth, and timing.


![Internet apps: application, transport protocols
Application Underlying
Application layer protocol transport protocol
e-mail SMTP [RFC 2821] TCP
remote terminal access Telnet [RFC 854] TCP
Web HTTP [RFC 2616] TCP
file transfer FTP [RFC 959] TCP
streaming multimedia proprietary TCP or UDP
(e.g. RealNetworks)
Internet telephony proprietary
(e.g., Vonage,Dialpad) typically UDP
2: Application Layer 18](https://image.slidesharecdn.com/3rdeditionchapter2-120425221753-phpapp01/85/3rd-edition-chapter2-18-320.jpg)
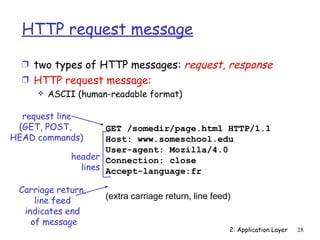
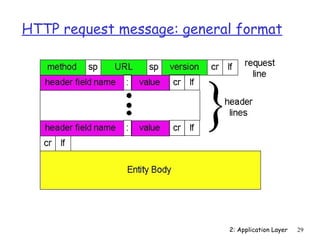
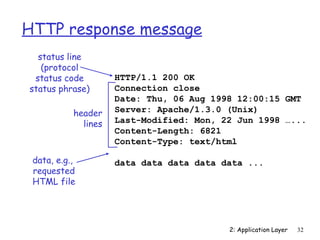
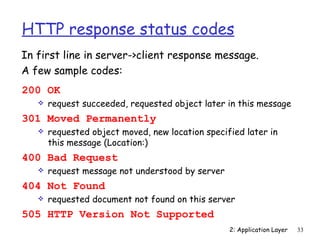



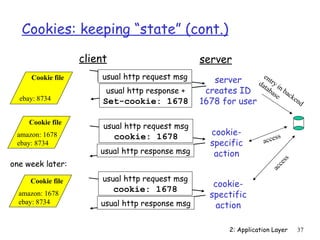

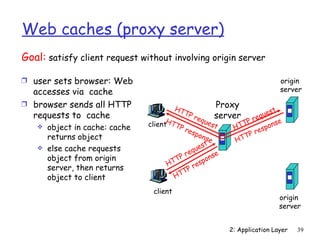
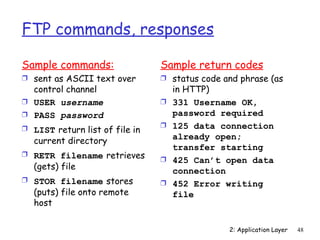
![Electronic Mail: SMTP [RFC 2821]
Ì uses TCP to reliably transfer email message from client
to server, port 25
Ì direct transfer: sending server to receiving server
Ì three phases of transfer
handshaking (greeting)
transfer of messages
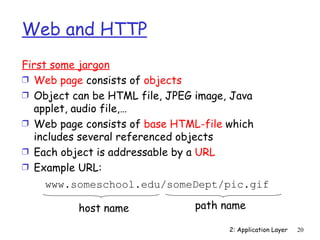
closure
Ì command/response interaction
commands: ASCII text
response: status code and phrase
Ì messages must be in 7-bit ASCII
2: Application Layer 52](https://image.slidesharecdn.com/3rdeditionchapter2-120425221753-phpapp01/85/3rd-edition-chapter2-52-320.jpg)


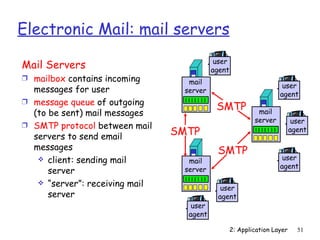
![Mail access protocols
SMTP SMTP access user
user
agent protocol agent
sender’s mail receiver’s mail
server server
Ì SMTP: delivery/storage to receiver’s server
Ì Mail access protocol: retrieval from server
POP: Post Office Protocol [RFC 1939]
• authorization (agent <-->server) and download
IMAP: Internet Mail Access Protocol [RFC 1730]
• more features (more complex)
• manipulation of stored msgs on server
HTTP: Hotmail , Yahoo! Mail, etc.
2: Application Layer 59](https://image.slidesharecdn.com/3rdeditionchapter2-120425221753-phpapp01/85/3rd-edition-chapter2-59-320.jpg)





![Example: Java client (TCP)
import java.io.*;
import java.net.*;
class TCPClient {
public static void main(String argv[]) throws Exception
{
String sentence;
String modifiedSentence;
Create
input stream BufferedReader inFromUser =
new BufferedReader(new InputStreamReader(System.in));
Create
client socket, Socket clientSocket = new Socket("hostname", 6789);
connect to server
Create DataOutputStream outToServer =
output stream new DataOutputStream(clientSocket.getOutputStream());
attached to socket
2: Application Layer 93](https://image.slidesharecdn.com/3rdeditionchapter2-120425221753-phpapp01/85/3rd-edition-chapter2-93-320.jpg)
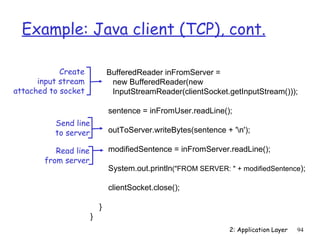
![Example: Java server (TCP)
import java.io.*;
import java.net.*;
class TCPServer {
public static void main(String argv[]) throws Exception
{
String clientSentence;
Create String capitalizedSentence;
welcoming socket
ServerSocket welcomeSocket = new ServerSocket(6789);
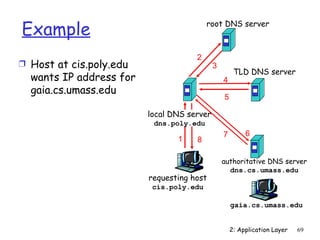
at port 6789
while(true) {
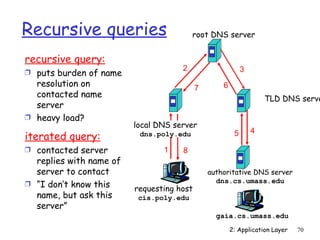
Wait, on welcoming
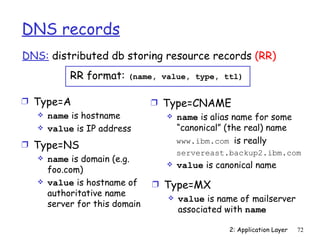
socket for contact Socket connectionSocket = welcomeSocket.accept();
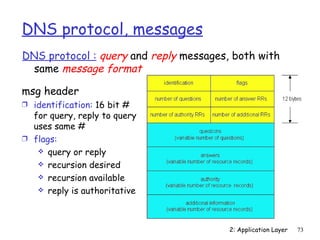
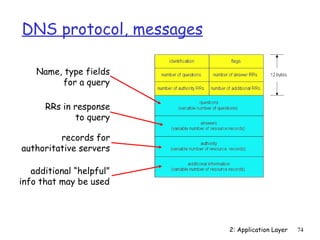
by client
BufferedReader inFromClient =
Create input new BufferedReader(new
stream, attached InputStreamReader(connectionSocket.getInputStream()));
to socket
2: Application Layer 95](https://image.slidesharecdn.com/3rdeditionchapter2-120425221753-phpapp01/85/3rd-edition-chapter2-95-320.jpg)
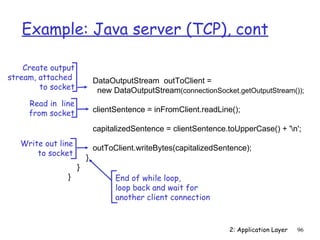
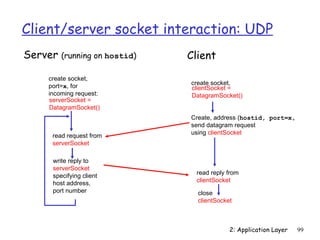
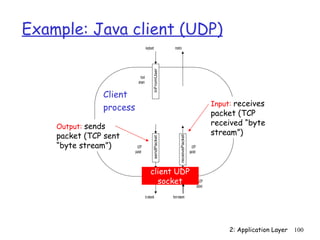
![Example: Java client (UDP)
import java.io.*;
import java.net.*;
class UDPClient {
public static void main(String args[]) throws Exception
{
Create
input stream BufferedReader inFromUser =
new BufferedReader(new InputStreamReader(System.in));
Create
client socket DatagramSocket clientSocket = new DatagramSocket();
Translate
InetAddress IPAddress = InetAddress.getByName("hostname");
hostname to IP
address using DNS byte[] sendData = new byte[1024];
byte[] receiveData = new byte[1024];
String sentence = inFromUser.readLine();
sendData = sentence.getBytes();
2: Application Layer 101](https://image.slidesharecdn.com/3rdeditionchapter2-120425221753-phpapp01/85/3rd-edition-chapter2-101-320.jpg)
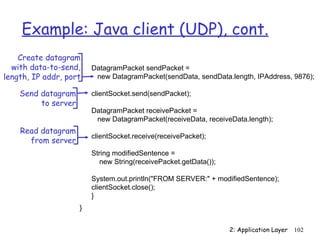
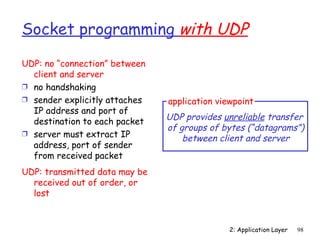
![Example: Java server (UDP)
import java.io.*;
import java.net.*;
class UDPServer {
public static void main(String args[]) throws Exception
Create {
datagram socket
DatagramSocket serverSocket = new DatagramSocket(9876);
at port 9876
byte[] receiveData = new byte[1024];
byte[] sendData = new byte[1024];
while(true)
{
Create space for
DatagramPacket receivePacket =
received datagram
new DatagramPacket(receiveData, receiveData.length);
Receive serverSocket.receive(receivePacket);
datagram
2: Application Layer 103](https://image.slidesharecdn.com/3rdeditionchapter2-120425221753-phpapp01/85/3rd-edition-chapter2-103-320.jpg)