Embed presentation
Download as PDF, PPTX


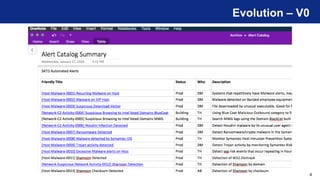
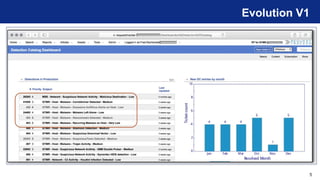
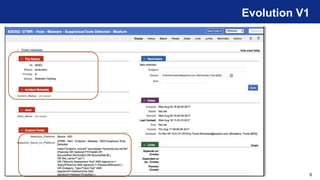



The document discusses the detection philosophy and evolution of threat detection catalog management within the context of the ATT&CK framework. It emphasizes the importance of maintaining a catalog for knowledge transfer and historical record, and outlines strategies for detecting suspicious network activity, specifically SMB worm behavior. Key lessons learned include the significance of nomenclature and proper documentation in enhancing operational effectiveness.








