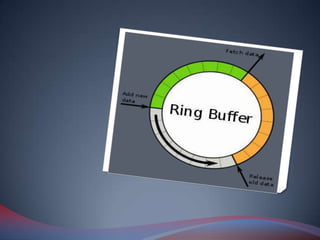
Java rings are wearable finger rings with microprocessors that function similarly to smart cards. They originated from Dallas Semiconductor's "touch memory" devices called i-buttons in 1989. Java rings contain an i-button microchip with memory, real-time clock, and a Java Virtual Machine that can run customized applets. They allow secure storage and transmission of user data and preferences for remote transactions, access control, and other applications while being durable, wearable devices. Potential disadvantages include high costs and limited memory capacity.