Consumer Concern for Online Privacy Remains High
•
2 likes•1,400 views
The document summarizes the results of surveys conducted in late 2014 and early 2015 regarding consumer privacy concerns, trust in companies, and actions taken to protect privacy online. It finds that consumer concern about privacy online remains high at 92%, while trust in businesses to protect personal information remains low at 55%. It also reports that 91% of internet users say they avoid companies that do not protect their privacy. The document outlines the top privacy concerns of consumers and actions they have taken online to protect their privacy. It also lists ways that companies and governments could increase consumer trust in how personal data is handled.
Report
Share
Report
Share
Download to read offline
Recommended
More Related Content
What's hot
What's hot (18)
Digiday Programmatic Media Summit. Glen Straub. Factual

Digiday Programmatic Media Summit. Glen Straub. Factual
Digiday Programmatic Media Summit. Eric Shih. Teads.

Digiday Programmatic Media Summit. Eric Shih. Teads.
Digiday Marketing Summit. Clementine Berlioz. Hello Fresh

Digiday Marketing Summit. Clementine Berlioz. Hello Fresh
Naughty or Nice? Holidays Stress Merchants' Cybersecurity

Naughty or Nice? Holidays Stress Merchants' Cybersecurity
The Third Wave of Enterprise Communications by Bryan Martin, 8x8

The Third Wave of Enterprise Communications by Bryan Martin, 8x8
mHealth Technologies that are Working and Obstacles to Innovation by Jim Bloe...

mHealth Technologies that are Working and Obstacles to Innovation by Jim Bloe...
October Webinar Slides - Social Media for Business

October Webinar Slides - Social Media for Business
State of the Digital Union by Overdrive Interactive

State of the Digital Union by Overdrive Interactive
Viewers also liked
Viewers also liked (10)
[Webinar Slides] Privacy Shield is Here – What You Need to Know![[Webinar Slides] Privacy Shield is Here – What You Need to Know](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Webinar Slides] Privacy Shield is Here – What You Need to Know](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[Webinar Slides] Privacy Shield is Here – What You Need to Know
EU US Privacy Shield vs. GDPR Infographic from TRUSTe

EU US Privacy Shield vs. GDPR Infographic from TRUSTe
Password manažeři detailněji – 1Password, LastPass, 2FA, sdílení

Password manažeři detailněji – 1Password, LastPass, 2FA, sdílení
How Good Privacy Practices can help prepare for a Data Breach from TRUSTe 

How Good Privacy Practices can help prepare for a Data Breach from TRUSTe
Webinar on New DAA Guidelines for Ads Compliance in 2016 from TRUSTe

Webinar on New DAA Guidelines for Ads Compliance in 2016 from TRUSTe
Similar to Consumer Concern for Online Privacy Remains High
Panel - Digital Marketing in the New Era of Privacy & Data Governance - Ashle...

Panel - Digital Marketing in the New Era of Privacy & Data Governance - Ashle...DigiMarCon - Digital Marketing, Media and Advertising Conferences & Exhibitions
Similar to Consumer Concern for Online Privacy Remains High (20)
TFOE - Social | A importância dos cookies e 1st party data para o e-commerce

TFOE - Social | A importância dos cookies e 1st party data para o e-commerce
The Intersection of Trust, Data Security and the Financial Industry

The Intersection of Trust, Data Security and the Financial Industry
The state of data privacy with dimensional research 

The state of data privacy with dimensional research
Thinking_Beyond_the_Third_Party_Cookie_Guide_Refresh_Offer.pdf

Thinking_Beyond_the_Third_Party_Cookie_Guide_Refresh_Offer.pdf
Consumer Mobile Policy & Security - Lightspeed & Kantar

Consumer Mobile Policy & Security - Lightspeed & Kantar
White Paper: The 2015 State of Consumer Privacy & Personalization

White Paper: The 2015 State of Consumer Privacy & Personalization
Panel - Digital Marketing in the New Era of Privacy & Data Governance - Ashle...

Panel - Digital Marketing in the New Era of Privacy & Data Governance - Ashle...
SVB Cybersecurity Impact on Innovation Report - Overview

SVB Cybersecurity Impact on Innovation Report - Overview
Google Think Mobile - Accelerating the Mobile Wave

Google Think Mobile - Accelerating the Mobile Wave
BDVe Webinar Series - Helping SMEs and Startups comply with GDPR

BDVe Webinar Series - Helping SMEs and Startups comply with GDPR
More from TrustArc
More from TrustArc (20)
TrustArc Webinar - How to Build Consumer Trust Through Data Privacy

TrustArc Webinar - How to Build Consumer Trust Through Data Privacy
TrustArc Webinar - How to Live in a Post Third-Party Cookie World

TrustArc Webinar - How to Live in a Post Third-Party Cookie World
TrustArc Webinar - TrustArc's Latest AI Innovations

TrustArc Webinar - TrustArc's Latest AI Innovations
TrustArc Webinar - Managing Online Tracking Technology Vendors_ A Checklist f...

TrustArc Webinar - Managing Online Tracking Technology Vendors_ A Checklist f...
TrustArc Webinar - Privacy in Healthcare_ Ensuring Data Security

TrustArc Webinar - Privacy in Healthcare_ Ensuring Data Security
Unlocking AI Potential: Leveraging PIA Processes for Comprehensive Impact Ass...

Unlocking AI Potential: Leveraging PIA Processes for Comprehensive Impact Ass...
Mitigating Third-Party Risks: Best Practices for CISOs in Ensuring Robust Sec...

Mitigating Third-Party Risks: Best Practices for CISOs in Ensuring Robust Sec...
Nymity Framework: Privacy & Data Protection Update in 7 States

Nymity Framework: Privacy & Data Protection Update in 7 States
CBPR - Navigating Cross-Border Data Privacy Compliance

CBPR - Navigating Cross-Border Data Privacy Compliance
Everything You Need to Know about DPF But Are Afraid to Ask.pdf

Everything You Need to Know about DPF But Are Afraid to Ask.pdf
Your Guide to Understanding the Global Privacy Control (GPC): Preparing for C...

Your Guide to Understanding the Global Privacy Control (GPC): Preparing for C...
Privacy Enhancing Technologies: Exploring the Benefits and Recommendations

Privacy Enhancing Technologies: Exploring the Benefits and Recommendations
Building Trust and Competitive Advantage: The Value of Privacy Certifications

Building Trust and Competitive Advantage: The Value of Privacy Certifications
The California Age Appropriate Design Code Act Navigating the New Requirement...

The California Age Appropriate Design Code Act Navigating the New Requirement...
2023 Global Privacy Benchmarks Survey - Webinar May 30 2023.pdf

2023 Global Privacy Benchmarks Survey - Webinar May 30 2023.pdf
Artificial Intelligence Bill of Rights: Impacts on AI Governance

Artificial Intelligence Bill of Rights: Impacts on AI Governance
The Ultimate Balancing Act: Using Consumer Data and Maintaining Trust

The Ultimate Balancing Act: Using Consumer Data and Maintaining Trust
The Cost of Privacy Teams: What Your Business Needs To Know

The Cost of Privacy Teams: What Your Business Needs To Know
TrustArc Webinar_ How Data Privacy Demands Impact Your Marketing Team.pdf

TrustArc Webinar_ How Data Privacy Demands Impact Your Marketing Team.pdf
Recently uploaded
Hot Sexy call girls in Panjabi Bagh 🔝 9953056974 🔝 Delhi escort Service

Hot Sexy call girls in Panjabi Bagh 🔝 9953056974 🔝 Delhi escort Service9953056974 Low Rate Call Girls In Saket, Delhi NCR
Recently uploaded (20)
Dev Dives: Streamline document processing with UiPath Studio Web

Dev Dives: Streamline document processing with UiPath Studio Web
"Federated learning: out of reach no matter how close",Oleksandr Lapshyn

"Federated learning: out of reach no matter how close",Oleksandr Lapshyn
Scanning the Internet for External Cloud Exposures via SSL Certs

Scanning the Internet for External Cloud Exposures via SSL Certs
Hot Sexy call girls in Panjabi Bagh 🔝 9953056974 🔝 Delhi escort Service

Hot Sexy call girls in Panjabi Bagh 🔝 9953056974 🔝 Delhi escort Service
Tampa BSides - Chef's Tour of Microsoft Security Adoption Framework (SAF)

Tampa BSides - Chef's Tour of Microsoft Security Adoption Framework (SAF)
"Debugging python applications inside k8s environment", Andrii Soldatenko

"Debugging python applications inside k8s environment", Andrii Soldatenko
"LLMs for Python Engineers: Advanced Data Analysis and Semantic Kernel",Oleks...

"LLMs for Python Engineers: Advanced Data Analysis and Semantic Kernel",Oleks...
My INSURER PTE LTD - Insurtech Innovation Award 2024

My INSURER PTE LTD - Insurtech Innovation Award 2024
Unblocking The Main Thread Solving ANRs and Frozen Frames

Unblocking The Main Thread Solving ANRs and Frozen Frames
Gen AI in Business - Global Trends Report 2024.pdf

Gen AI in Business - Global Trends Report 2024.pdf
Transcript: New from BookNet Canada for 2024: BNC BiblioShare - Tech Forum 2024

Transcript: New from BookNet Canada for 2024: BNC BiblioShare - Tech Forum 2024
Unleash Your Potential - Namagunga Girls Coding Club

Unleash Your Potential - Namagunga Girls Coding Club
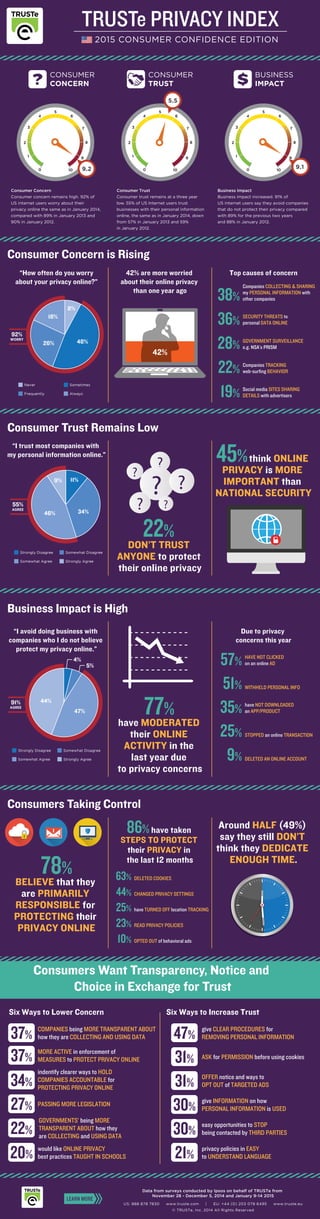
Consumer Concern for Online Privacy Remains High
- 1. 0 1 2 3 4 5 6 7 8 9 100 1 2 3 4 5 6 7 8 9 100 1 2 3 4 5 6 7 8 9 10 9.2 Companies COLLECTING & SHARING my PERSONAL INFORMATION with other companies38% HAVE NOT CLICKED on an online AD57% WITHHELD PERSONAL INFO51% have NOT DOWNLOADED an APP/PRODUCT35% STOPPED an online TRANSACTION25% DELETED AN ONLINE ACCOUNT9% 86% have taken STEPS TO PROTECT their PRIVACY in the last 12 months DELETED COOKIES63% CHANGED PRIVACY SETTINGS44% READ PRIVACY POLICIES23% OPTED OUT of behavioral ads10% have TURNED OFF location TRACKING25% SECURITY THREATS to personal DATA ONLINE36% GOVERNMENT SURVEILLANCE e.g. NSA’s PRISM28% Companies TRACKING web-surfing BEHAVIOR22% Social media SITES SHARING DETAILS with advertisers19% 42% are more worried about their online privacy than one year ago 22% DON’T TRUST ANYONE to protect their online privacy 77% have MODERATED their ONLINE ACTIVITY in the last year due to privacy concerns 78% BELIEVE that they are PRIMARILY RESPONSIBLE for PROTECTING their PRIVACY ONLINE Six Ways to Lower Concern Six Ways to Increase Trust Around HALF (49%) say they still DON’T think they DEDICATE ENOUGH TIME. 45%think ONLINE PRIVACY is MORE IMPORTANT than NATIONAL SECURITY Due to privacy concerns this year Top causes of concern 42% “How often do you worry about your privacy online?” Never Sometimes Frequently Always Strongly Disagree Somewhat Disagree Somewhat Agree Strongly Agree 92% WORRY 8% 48%26% 18% “I trust most companies with my personal information online.” “I avoid doing business with companies who I do not believe protect my privacy online.” 55% AGREE 11% 34%46% 9% Strongly Disagree Somewhat Disagree Somewhat Agree Strongly Agree 91% AGREE 47% 44% 9.1 5.5 BUSINESS IMPACT CONSUMER CONCERN CONSUMER TRUST TRUSTe PRIVACY INDEX 2015 CONSUMER CONFIDENCE EDITION Consumer Concern Consumer concern remains high. 92% of US internet users worry about their privacy online the same as in January 2014, compared with 89% in January 2013 and 90% in January 2012. Consumer Trust Consumer trust remains at a three year low. 55% of US Internet users trust businesses with their personal information online, the same as in January 2014, down from 57% in January 2013 and 59% in January 2012. Business Impact Business impact increased. 91% of US internet users say they avoid companies that do not protect their privacy compared with 89% for the previous two years and 88% in January 2012. Consumer Concern is Rising Consumer Trust Remains Low Business Impact is High Consumers Taking Control Consumers Want Transparency, Notice and Choice in Exchange for Trust 4% 5% US: 888 878 7830 www.truste.com | EU: +44 (0) 203 078 6495 www.truste.eu © TRUSTe, Inc. 2014 All Rights Reserved LEARN MORE Data from surveys conducted by Ipsos on behalf of TRUSTe from November 28 - December 5, 2014 and January 9-14 2015 COMPANIES being MORE TRANSPARENT ABOUT how they are COLLECTING AND USING DATA37% give CLEAR PROCEDURES for REMOVING PERSONAL INFORMATION47% ASK for PERMISSION before using cookies 31% OFFER notice and ways to OPT OUT of TARGETED ADS31% give INFORMATION on how PERSONAL INFORMATION is USED30% easy opportunities to STOP being contacted by THIRD PARTIES30% privacy policies in EASY to UNDERSTAND LANGUAGE21% MORE ACTIVE in enforcement of MEASURES to PROTECT PRIVACY ONLINE37% indentify clearer ways to HOLD COMPANIES ACCOUNTABLE for PROTECTING PRIVACY ONLINE 34% PASSING MORE LEGISLATION 27% would like ONLINE PRIVACY best practices TAUGHT IN SCHOOLS20% GOVERNMENTS’ being MORE TRANSPARENT ABOUT how they are COLLECTING and USING DATA 22%
