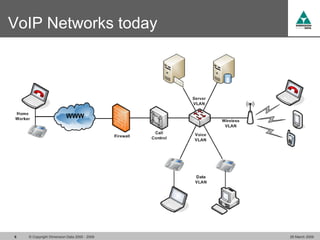
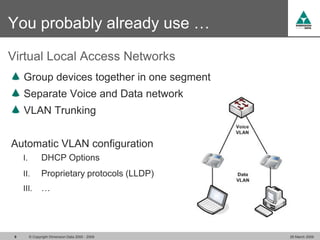
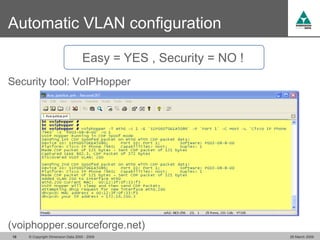
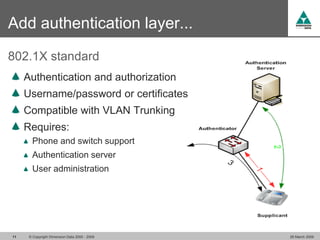
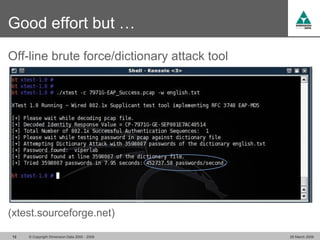
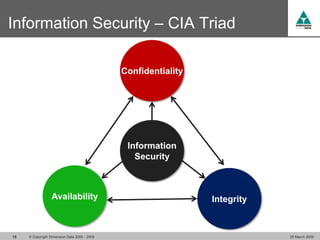
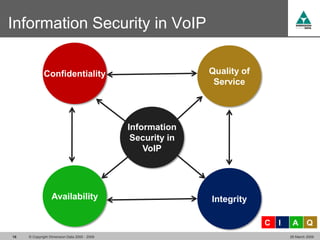
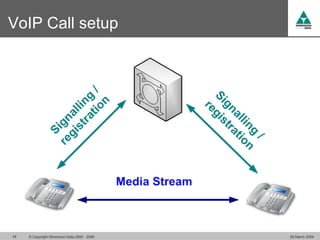
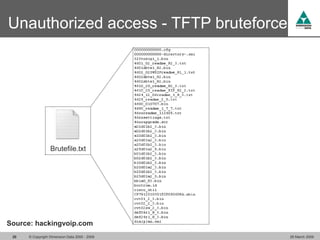
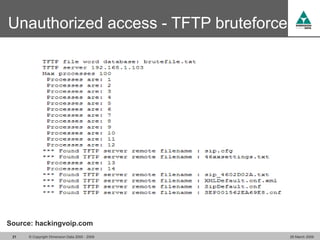
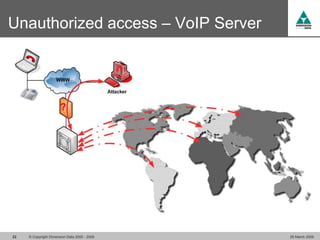
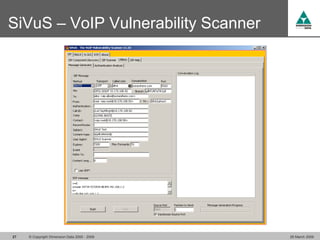
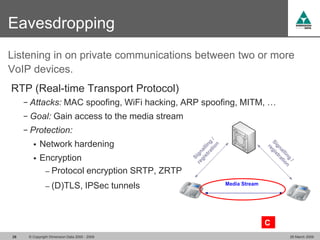
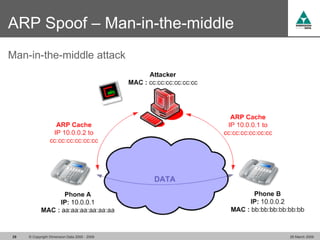
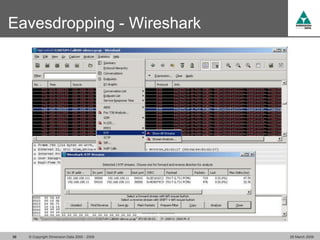
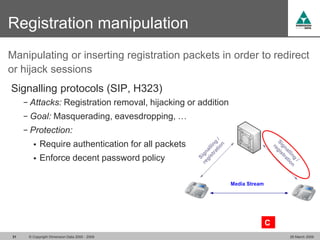
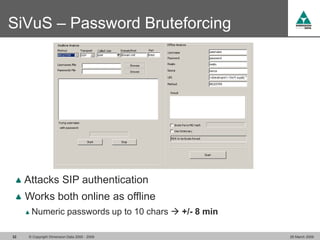
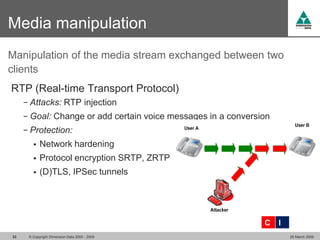
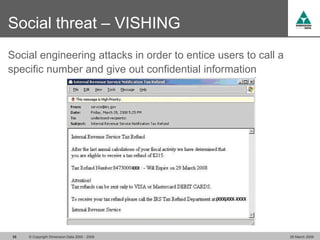
The document discusses security challenges in VoIP, emphasizing the need for segregation of voice and data networks to improve security and manage quality of service. It identifies various VoIP security threats such as unauthorized access, interruption of service, eavesdropping, and registration manipulation, and offers protective measures including encryption and authentication. The conclusion stresses the importance of designing secure networks and maintaining up-to-date security practices.