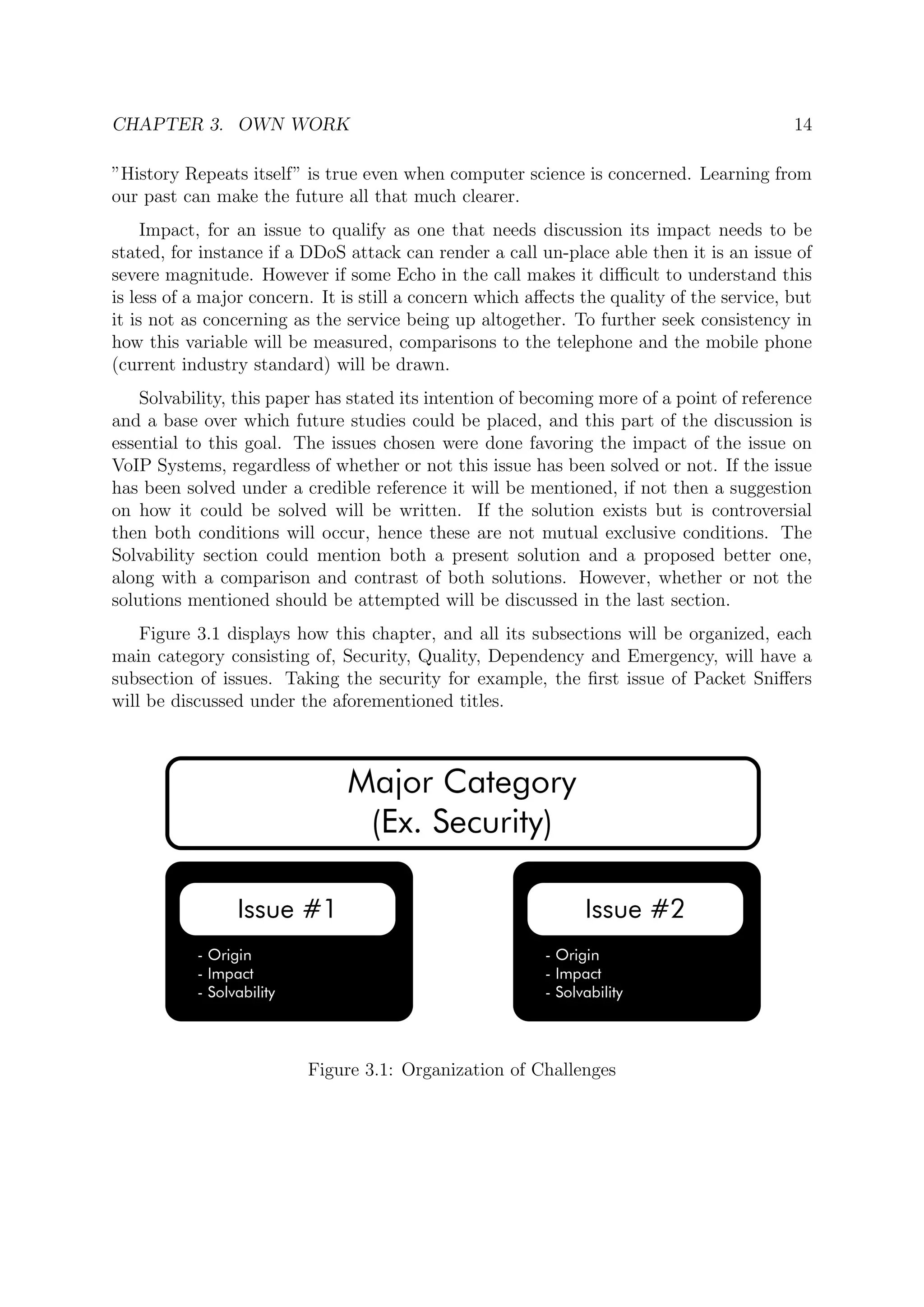
This document is a bachelor's thesis submitted by Mostafa Ahmed Mostafa El Beheiry to the German University in Cairo that examines challenges in VoIP (Voice over IP) systems. The thesis identifies four main categories of challenges - security, quality, dependency, and emergency services. It discusses specific issues within each category such as packet sniffing, bandwidth, power outages, and inability to call emergency services. It also includes a simulation of a SPIT (Spam over IP telephony) attack on a VoIP client/server setup. The thesis aims to comprehensively document challenges in VoIP systems and propose possible solutions to advance the field.



![Abstract
The remarkable advancement of VoIP Systems in the previous decades made possible what
was thought to be fiction. But with great prgress come great challenges, the development
of VoIP Systems is no different. This work is a collection, categorization and examination
of some of VoIP’s greatest challenges. This work has identified four main categories of
issues, Security, Quality, Dependency, Emergency and how they came to be during the
development of VoIP Systems. Their impact on Voice over IP (VoIP) Systems, whether
or not these issues are crippling to VoIP Systems. Included also are illustrations of the
various issues, for visualization purposes. A real time simulation of a singled out issue
is also included in this work. Finally, this work will also look into possible solutions if
present, or suggest solutions if the issues mentioned do not possess a certain, industry-
standard solution.
Certain topics amongst the four categories have been singled out as the most im-
portant, and will be the focus of this work. As for the Security category all of, Packet
Sniffers, Distributed Distributed Denial of Service (DDoS) Attacks, Eavesdropping, Spam
over IP Telephony (SPIT) Attacks, Difficulties with Firewalls and Operating System and
Network, have been the focus. Concerning Quality the issues of, Bandwidth, Codecs,
Queuing, and Low-Speed Links, will be discussed.
Collaboration has taken place with colleague Ahmed Khaled Saeed Metwally, in cre-
ating a simulation of a SPIT attack using his own implementation of a VoIP Client as a
base [11], and using OfficeSIP as a server.
IV](https://image.slidesharecdn.com/baafc7c9-b52b-44f8-bcd3-fea380945fdb-160701233408/75/Challenges-in-VoIP-Systems-Mostafa-Ahmed-Mostafa-El-Beheiry-First-Draft-Final-4-2048.jpg)





![Chapter 2
Background
The most notable work around the subject matter of Challenges in VoIP Systems as a
general whole subject, would be Hughes Systique Corporations VoIP [9] and its challenges.
Which focused further on the challenges facing VoIP Systems during its deployment phase.
Spoke of some security issues such as NAT and Firewall Traversal. Tackled Quality of
Service (QoS) briefly in a single, two paragraphed page containing 294 words[9, p. 7].
Which by all stretches of imagination is not deep enough for such an issue. It also went
on to focus its efforts on SPIT.
Although a much more in depth, concentrated and well-rounded effort has been made
by Fraunhofer Institute for Secure Information Technologys Rachid El Khayari. His own
work of SPAM over Internet Telephony and how to deal with it, has heavily influenced
this own works section concerning the subject matter[10].
DDoS, has been worked on in the title Evaluating DoS Attacks Against SIP-Based
VoIP Systems written by the collaborated efforts of M. Zubair Rafique, M. Ali Akbar
and Muddassar Farooq. The authors themselves have stated; ”The purpose of our study
is to help both VoIP vendors and academia better understand different vulnerabilities in
the existing SIP servers and how adequately they are protected against them.”[15, p. 1]
Their study however, did not include a solution to DDoS attacks, since the focus of their
paper has been merely the Evaluation of DDoS attacks.
Challenges in Securing Voice over IP and Top Ten Security Issues VoIP, covered the
remainder of the topics adequately and have been extensively read before attempting this
paper [17].
What follows is an explanation of any and all technologies used in this paper, detailing
all the relevant information used from these technologies.
4](https://image.slidesharecdn.com/baafc7c9-b52b-44f8-bcd3-fea380945fdb-160701233408/75/Challenges-in-VoIP-Systems-Mostafa-Ahmed-Mostafa-El-Beheiry-First-Draft-Final-10-2048.jpg)
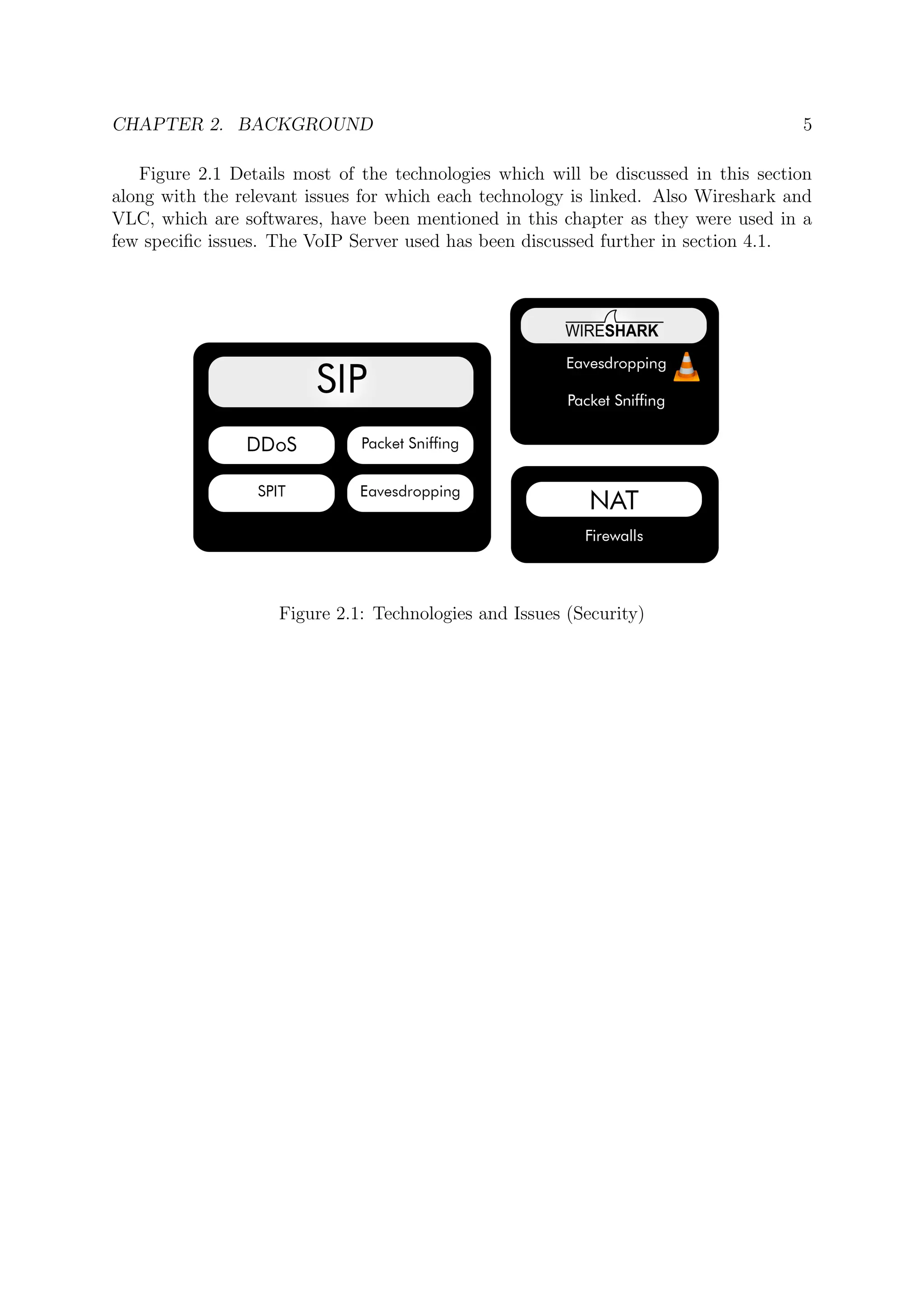
![CHAPTER 2. BACKGROUND 6
2.1 Session Initiation Protocol (SIP)
As mentioned above, only relevant to this work information about Session Initiation
Protocol (SIP) will be discussed.
Developed by Internet Engineering Task Force (IETF), it acts as the primary core for
VoIP Systems[16]. Of which many variants have been derived with the aim and goal of
further developing the protocol beyond its weaknesses.
It is a signaling protocol, its tasks are restricted to initiating, maintaining, and closing
the VoIP Call. It has become an industry standard which becomes its greatest strength
and weakness. Strength, in that any SIP based client can communicate with another SIP
based client disregarding most hindering factors. Weakness, in the fact that anyone can
manipulate or extract information from most SIP packets, valuable information at that.
Two of the greatest offenders of this weakness are the Invite Request, and the Message
Method. These will be extensively referenced in the coming chapters thus an explanation
of them is due.
2.1.1 SIP Invite Request
Figure 2.2: Sip Invite Request
The above code snippet in Figure 2.2 details the actual format of SIPs invite request
taken from IETFs own documentation of SIP.[16, 11] What is primarily a concern in this
work is the fact that this request contains the IP Addresses of the person receiving the
call and the person initiating it. It also shows the version of SIP used, the transportation
protocol used and the server handling the call.
The availability of these facts in the Invite Request is an important fact to take into
consideration for the coming chapters, as most of the weaknesses of SIP lay in the fact
that information such as this is readily available.](https://image.slidesharecdn.com/baafc7c9-b52b-44f8-bcd3-fea380945fdb-160701233408/75/Challenges-in-VoIP-Systems-Mostafa-Ahmed-Mostafa-El-Beheiry-First-Draft-Final-12-2048.jpg)
![CHAPTER 2. BACKGROUND 7
2.1.2 Message Method Extension
Added to SIP in 2002 [2], this is how SIP handles chat where possible, whether it be a
VoIP application such as Skype with a text chat feature, or an internal company system
with VoIP phones with SIP Messaging Service (SMS) enabled.
Since SIP is in nature a signaling protocol as mentioned is section 2.1, it can only
ever send request or response messages, the extension handles messaging in a way IETF
described as; ”using a metaphor similar to that of a two-way pager or SMS enabled
handset” [2, 2]
Hence, staying true to SIPs nature, the way Instant Messaging (IM) is done is by
sending a request using the Message Method which contains the deliverable message in
the body of the Request Message sent. Also, since it is a Request Message the receiver
must reply with a Response Message.
2.1.3 SIP Codes
The following are tables of the response codes used by SIP as taken from the IETF
Documentation. Some codes have been removed for sake of remaining concise to the
goal. Continued on page 8
1xx Provisional
100 Trying
180 Ringing
199
Early
Dialog Terminated
Table 2.1: Provisional SIP Codes
2xx Successful
200 OK
202 Accepted (Deprecated)
204 No Notification
Table 2.2: Successful SIP Codes](https://image.slidesharecdn.com/baafc7c9-b52b-44f8-bcd3-fea380945fdb-160701233408/75/Challenges-in-VoIP-Systems-Mostafa-Ahmed-Mostafa-El-Beheiry-First-Draft-Final-13-2048.jpg)

![CHAPTER 2. BACKGROUND 9
2.2 Real Time Protocol (RTP)
2.2.1 Packet Format
This section will be referred to later in the Bandwidth subsection of the Quality section.
A single Real Time Protocol (RTP) packet contains header fields which hold speech
sample time stamps along with sequence numbers and identify each voice packets con-
tents. The content fields however define the compression technique used.
Figure 2.3: RTP Packet
This packet is left unchanged on most protocols, aside from the edge header and
trailer which vary. The Digitized voice, RTP Header, User Diagram Protocol (UDP)
Header along with the IP Header remain unchanged.
The Ethernet Trailer is present to detect errors, while the Ethernet Header holds the
Local Area Network (LAN) Media Access Control (MAC) addresses of the devices it is
being transferred to and from. The IP Header holds the to and from IP Adresses along
with some control information. The UDP Header carries the portnumbers of the sending
and receiving devices. The digitized voice filed can carry anything from 10 to 320 bytes
of voice[18].](https://image.slidesharecdn.com/baafc7c9-b52b-44f8-bcd3-fea380945fdb-160701233408/75/Challenges-in-VoIP-Systems-Mostafa-Ahmed-Mostafa-El-Beheiry-First-Draft-Final-15-2048.jpg)
![CHAPTER 2. BACKGROUND 10
2.3 Wireshark
The Open Sourced nature of Internet development has made a tool such as Wireshark
available, primarily it functions as a traffic analysis tool, but its abilities go much further
than just that.
Its core function is capturing all traffic flowing in and out of a certain gateway/com-
puter/target device, for instance a simple capture of Wireshark on a certain computer
would reveal the packets being sent to and from that computer. With the luxury of most
of the industry standard protocols being open sourced, such as SIP, Wireshark has been
able to integrate a truly deep method of inspecting each and every packet rushing along
its target device.
It is a Multi-platform program, meaning it is available to the vast majority of users,
by which this means it is available to Windows, Linux, OS X, Solaris users amongst
others. Boasting filters for over a hundred protocols one could argue it is too powerful a
tool to be put, free of charge, to this vast majority of users.
Amongst the features it boasts to possess is a ”Rich VoIP analysis” meaning it is
especially capable in this field. Aided by the ability to capture a stream of data and not
only play but output the capture to a number of different formats after being compressed.
Also it boasts to be able to capture traffic and output the capture to another network
analysis tool, making it more flexible than any other choice in the industry[4].
Figure 2.4 shows an actual capture taken by Wireshark of a UDP Packet.
Figure 2.4: SCCP UDP Packet Capture](https://image.slidesharecdn.com/baafc7c9-b52b-44f8-bcd3-fea380945fdb-160701233408/75/Challenges-in-VoIP-Systems-Mostafa-Ahmed-Mostafa-El-Beheiry-First-Draft-Final-16-2048.jpg)
![CHAPTER 2. BACKGROUND 11
2.4 Network Address Translators (NAT)
Network Address Translators (NAT) was created as a countermeasure to delay the im-
pending depletion of IPv4 addresses, it functions by allowing for IP Address reuse through
a router function. This occurs by dividing the networks into a stub for which the router
can assign the same addresses assigned in other stubs.
Figure Figure 2.5 depicts an operational network in which NAT is used, as is taken
from the IETF Documentation. [6]
Figure 2.5: NAT Operaction](https://image.slidesharecdn.com/baafc7c9-b52b-44f8-bcd3-fea380945fdb-160701233408/75/Challenges-in-VoIP-Systems-Mostafa-Ahmed-Mostafa-El-Beheiry-First-Draft-Final-17-2048.jpg)
![CHAPTER 2. BACKGROUND 12
2.5 VideoLAN Client (VLC)
VLC originally began as a client for streaming videos over a network. A product of Ecole
Centrale Paris students and began as a purely academic endeavor is now a media player
managed by the VideoLAN Non-profit organization. Amassing over 1.3 billion downloads
for Windows and OSX alone[19].
It is arguably the strongest media player in the industry, in which it does not simply
retrieve a file from the Hard Disk Drive (HDD). The various methods of input are its
greatest strength and above all the various ways in which it can receive content is what
truly makes it stand out.
The windows version for instance can play a video using the following protocols: UD-
P/RTP Unicast, UDP/RTP Multicast, Hypertext Transfer Protocol (HTTP)/File Trans-
fer Protocol (FTP), Multimedia Messaging Service (MMS), Transmission Control Proto-
col (TCP)/RTP Unicast, File on HDD, Digital Video Disc (DVD), Video CD (VCD),
Super VCD (SVCD), Audio CD, Digital Video Broadcasting (DVB) (Satellite), Digitale
TV, Cable TV, Motion Pictures Experts Group (MPEG) Encoder, Video Acquisition
(Direct Show).
For a show of its strength in playable formats, all of the following can be played on
all of the Windows, OS X and Linux versions: MPEG, Audio Video Interleave (AVI),
Advanced Systems Format (ASF)/Windows Media Video (WMV)/Windows Media Audio
(WMA), MPEG 4 (MP4)/QuickTime File Format (MOV)/Third Generation Partnership
Project (3GP), Ogging (OGG)/OGG Movie (OGM)/Annodex, Matroska Video (MKV),
Real, Waveform Audio File Format (WAV), Raw Audio, Raw DV, Free Lossless Audio
Codec (FLAC), Flash Video (FLV), Material eXchange Format (MXF), Nut, Musical
Instrument Digital Interface (MIDI)/Standard MIDI File (SMF), CreativeTM Voice.
Figure Figure 2.6 details on what versions are these features available
Figure 2.6: Input Media and Formats of VLC](https://image.slidesharecdn.com/baafc7c9-b52b-44f8-bcd3-fea380945fdb-160701233408/75/Challenges-in-VoIP-Systems-Mostafa-Ahmed-Mostafa-El-Beheiry-First-Draft-Final-18-2048.jpg)


![CHAPTER 3. OWN WORK 16
Impact
Figure 3.2: SIP Invite Request, as captured by Wireshark
Figure 3.2 [8] shows an actual SIP Invite Request packet captured using Wireshark, and
immediately the magnitude of the issue is made obvious. The IP Address of 107 along
with the IP Address of 101 are known using the two consecutive lines of From and To.
Also the Via line shows the last hop the packet took in order to reach its destination,
allowing for further abuse of the network, and how it is set up.
In Section 2.1.3 the various SIP Response Codes were noted, and since SIP is a
signaling protocol the Invite Request needs a Response. However, the response will also
be sniffed, and the sniffer would now know not only who attempted to call who, but the
state of the callee depending on the response code which is sniffed.
Moreover, the Message Method, which is SIPs own way of handling IM as was men-
tioned in Section 2.1.2, can be sniffed and immediately the chat would become apparent
to the intruder. An argument could be made that this is not worrisome in VoIP Systems
since they are primarily focused with Voice, but many newer systems come with SMS
Enabled devices, and in the case of Skype, it is built around the notion of chatting in the
first place.
The reason why Packet Sniffing is placed amongst the highest on the impact charts is
simple. If a call is denied, as in the case of DDoS, there is no information leaked. If a call
is breached however, this is another matter entirely. The only real argument that could
be made is for Eavesdropping as a contender for the most impactful security breech, but
Eavesdropping is merely an afterthought of Packet Sniffing, Eavesdropping in on its own
does not reveal IP Addresses nor reveal chat messages, and hence Packet Sniffing was
ranked higher.](https://image.slidesharecdn.com/baafc7c9-b52b-44f8-bcd3-fea380945fdb-160701233408/75/Challenges-in-VoIP-Systems-Mostafa-Ahmed-Mostafa-El-Beheiry-First-Draft-Final-22-2048.jpg)

![CHAPTER 3. OWN WORK 18
3.1.2 Eavesdropping
Origin
Eavesdropping could be considered Packet Sniffings younger, stronger, but less intelligent
brother. To provide context and follow up on this analogy, Packet Sniffing is more
intelligent in which it requires knowledge in order to know where to look and for what,
and in the end it returns information which in turn requires a good mind to know how
to use. Eavesdropping however merely plays out or outputs a conversation, making it
hypothetically no different from phone tapping.
To note, this section deals with Eavesdropping as a standalone issue, there are tools
available for eavesdropping on a certain connection, attempting to pick up any UDP
Packets and play them, regardless of IP Address. While the more classical way of viewing
eavesdropping is that it is a level above Packet Sniffing, this work has the notion of the
opposite. From packet sniffing one can eavesdrop and not the other way around.
Eavesdropping is much more of a difficult subject to discuss, it bears so much similarity
to Packet Sniffing, yet it remains a different topic. Hence for interest of eliminating
repetitiveness this chapter will remain shorter.
Impact
”It is said that if you know your enemies and know yourself, you will not be imperiled in
a hundred battles...” - Sun Tzu The Art of War
Another adage dating back to first written history which rings true to this day, knowl-
edge is power as Sun Tzu told of in The Art of War, an intruder peering into your own
calls freely needs not much proof to warrant its position on the impact list.
Even more so, today there are techniques to spot a certain word uttered during the
conversation, so for instance if used in espionage or in tyrannous countries could have
severe implications.
Solvability
One would assume the easiest way to solve this issue is as the above issue was solved,
until recently most of the community working in this industry thought so as well. In
order to encrypt a VoIP Call without losing time to encryption it is also compressed
with Variable Bit Rate (VBR) to shorten the sending time. However, recent studies have
shown that the language of the audio being compressed could be accurately achieved from
the encrypted stream. This, along with searching for a single phrase it has been proven
with over fifty percent accuracy to be successfully able to identify whether an encrypted
stream contained a certain phrase or not. Which calls in question the true strength of
these methods of encryption [20].
Another research suggests to randomly pad the outputs of the VBR encoder to dif-
ferent lengths in order to overcome this issue[14].](https://image.slidesharecdn.com/baafc7c9-b52b-44f8-bcd3-fea380945fdb-160701233408/75/Challenges-in-VoIP-Systems-Mostafa-Ahmed-Mostafa-El-Beheiry-First-Draft-Final-24-2048.jpg)
![CHAPTER 3. OWN WORK 19
3.1.3 Distributed Denial of Service (DDoS)
Origin
To compare to an older long distance communication method and to provide an analogy
of sorts. If a post man on average under normal circumstances has to deliver 1000 letters
per day, and on a certain day he receives 100,000 letters to deliver. There is virtually
little this man can do to distribute 100x his normal workload. It also comes as no surprise
to the postman when he opens these letters and finds than 99,000 of them are empty and
from the same person. This type of attack did not occur due to the cost and effort needed
to launch such a massive attack, numbers aside.
However, in a hypothetical word, where there was only one very fast postman, but
paper was free, and stamps were unlimited, such an attack could still be feasible, and
this is precisely what happens in VoIP DDoS attacks.
DDoS attacks first originated from 1989, as people discovered they could render ma-
chines inoperable using the -f (flood) command in ping.c source code. And soon developed
into almost bankrupting a high profile New York based ISP! (ISP!) in 1996 [5].
A flash forward to 2013, and the largest recorded high profile DDoS attacks of 300
Gbps in the first half of the year.
Impact
The sole reason this is not placed higher than it is on the impact list, is that there is
simply more to be gained from allowing a call to go through and knowing what was said
than denying it altogether. Denying the call however remains the next best thing.
The severity of the DDoS attack is limited only by its scope.
Figure 3.4: Simple DDoS Attack by Sisle](https://image.slidesharecdn.com/baafc7c9-b52b-44f8-bcd3-fea380945fdb-160701233408/75/Challenges-in-VoIP-Systems-Mostafa-Ahmed-Mostafa-El-Beheiry-First-Draft-Final-25-2048.jpg)
![CHAPTER 3. OWN WORK 20
Solvability
DDoS attacks are growing daily in size and frequency, and are now used as prime tools in
Cyber Warfare. Everything from Governments to Gaming Companies have been at one
point in time been the target of DDoS Attacks, of various magnitudes.
Recent researches [15] have shown that, while SIP Servers vary from robustness and
at which point they reach a contrived Breaking Point, all of the servers available for use
today can indeed be knocked down by a simple flooding of Invite requests.
The solution mentioned was the implementation of a SIP Intrusion Detection System
(IDS), to expand on this, simply allowing users a limited number of attempts to send
invite requests before shutting them out of the server for a time would solve the issue,
since in order to place an invite request one needs to be registered on the server in the
first place.
This is a very solid potential for future work, if not the solutions mentioned but the
subject matter itself, as said above DDoS attacks are only getting stronger, so it is only
natural for the next focus of research to concern surefire ways of defending against DDoS
attacks.
To shed further light on the severity of the issue, companies dedicated to ”Cloud
Based DDoS Mitigation” have recently opened up and have attained immediate success
[5].](https://image.slidesharecdn.com/baafc7c9-b52b-44f8-bcd3-fea380945fdb-160701233408/75/Challenges-in-VoIP-Systems-Mostafa-Ahmed-Mostafa-El-Beheiry-First-Draft-Final-26-2048.jpg)
![CHAPTER 3. OWN WORK 21
3.1.4 Spam over IP Telephony (SPIT)
Origin
If for example Bob knows that Carl is expecting an important call from Alice on the 13th
of April, and Bob wants to stop Carl from answering this call, a valid way of doing this
is repetitively calling Carl and hence making it seem for Alice that Bob is busy. This is
what is known as SPAM. SPIT however is much easier and less costly to execute.
Also it is much like E-Mail SPAM, except with E-Mail a person can go through them
all and in a sense Randomly Access the mails they deem important. Unlike E-Mail SPAM,
SPIT is more direct, the phone is ringing and will not stop ringing until it is answered or
declined. At the same time any legitimate calls are not being allowed into the system.
Also, E-Mails are scanned at an E-Mail server before being distributed to the user,
and hence most SPAM can be detected before it even reaches the user, unlike SPIT which
directly arrives to the user. E-Mails are also much easier to analyze, they give room for
analysis with the information they carry, yet a SPIT call cannot be determine pre-hand
for it arrives as a regular call would.
SPIT faced a difficulty in its definition, but recently it is being agreed on the definition
of: ”bulk unsolicited set of session initiation attempts (e.g., INVITE requests) [10], at-
tempting to establish a voice, video, instant messaging, or other type of communications
session. Meaning that SPIT could very easily be identified as Telemarketing of VoIP.
Impact
A step below DDoS attacks, but a sizable one at that. While DDoS attacks render an
entire server unusable, SPIT attacks only target bulks of people. To perform a SPIT
attack, the VoIP network is scanned and information regarding the IPs of the users on
the network is gathered. Afterwards attempts to establish calls with as much of these
users as possible being, and in the instance one picks up a message is relayed.
Solvability
As with all SPAM based attacks, simple black lists could suffice to prevent SPIT calls,
but this is a reactive solution and not a proactive one. And simply placing addresses
accused with SPIT in a blacklist is impractical at best.
A method of dealing with SPAM, or rather unwanted automation over the Internet
in general is Completely Automated Public Turing test to tell Completely Automated
Public Turing test to tell Computers and HumansApart (CAPTCHA) but even this can
be worked around by performing a CAPTCHA Relay Attack, by relaying it to human
solvers.](https://image.slidesharecdn.com/baafc7c9-b52b-44f8-bcd3-fea380945fdb-160701233408/75/Challenges-in-VoIP-Systems-Mostafa-Ahmed-Mostafa-El-Beheiry-First-Draft-Final-27-2048.jpg)


![CHAPTER 3. OWN WORK 24
3.1.5 NAT Traversal
Origin
VoIP, or rather, SIPs issues with Firewalls originate from three major points. Older
Firewalls predate SIP entirely, or did not anticipate the need to let SIP Messages pass
unhindered, making for blocked SIP Messages entirely.
Yet, even with new firewalls VoIP systems seemed to struggle to preform, as the newer
firewalls put more emphasis on security over all else, and when a firewall finds a mass
of RTP packets wanting to pass through, it will feel compelled to check each and every
one. Causing an unsettling delay in the call, and in lower end computers possibly jitter
as well.
The last origin of issues with reach-ability stems from the impending depletion of IPv4
addresses, and the short term solution of NAT, as was described in Section 2.3, along
with how SIP Messages are constructed[9].
Since the internal IP Address is different from the Public IP Address the SIP message
leaving the network will hold the wrong internal IP Address and not the Public IP and
Port.
Impact
A SIP Packet going to its destination with a wrong return address has only one impli-
cation. The response will be sent to the wrong return address, and probably lost along
the way. This is however an issue with the setup of the system and has a multitude of
solutions.
Solvability
Simply using a NAT Box to change the IP Payload of the SIP packets would be enough
to solve this issue. This would allow for a simple change of the IP to the correct Public
and Port variant.
Application Level NATing could be also considered by adding an Application aware
gateway to handle the VoIP Traffic. Known as, Application Layer Gateways (ALG).
However this solution is flawed at its core, for it the ALG would have to change the
packet and hence decrypt the packet, meaning that this solutions defeats the purpose of
encryption.
The solution proposed by IETF is one which involves yet another protocol, and re-
quires the presence of a Relay Server. Skype however use a protocol of their own and it
would be advisable to follow in these footsteps when building a VoIP System.](https://image.slidesharecdn.com/baafc7c9-b52b-44f8-bcd3-fea380945fdb-160701233408/75/Challenges-in-VoIP-Systems-Mostafa-Ahmed-Mostafa-El-Beheiry-First-Draft-Final-30-2048.jpg)


![CHAPTER 3. OWN WORK 28
3.2.1 Bandwidth
Origin
This particular issue stems from the amount of other activities using up the bandwidth
available, along with the large bandwidth required to properly set up a VoIP call.
For instance, a soft-phone using any of SIP, H.323 or MGCP along with RTP sends
a single voice packet every 10 to 40 ms. This can be either compressed, uncompressed or
encrypted. RTP will send the same number of packets regardless. It can take anywhere
from ten to a hundred packets to carry a single word using this standard system in the
best of cases, so the need for bigger bandwidth becomes more apparent.
Fundamentally the delay from end to end needs to remain as low and little as possible
for the quality to remain at an adequate level. As the size of the packet decreases the time
it takes to create and send it go down proportionally to it. Yet the need for bandwidth
relates with inverse proportionality to the size of the packet. The smaller the packet, the
more packets are sent, and the bigger the packet overhead becomes.
The issue with long packets however is that they are being sent over UDP, meaning
that if a packet is lost it will not be easily fixed.
On average, a packet will be sent each 20-30ms, depending on the implementation in
question, meaning that in a single second a total of about 50 packets are sent, and as
mentioned in section 2.2.1, the digitized voice field can carry up to 320 bytes of voice.
Meaning that for 50 packets per second a total of 16 KB are being sent in the digitized
voice field alone.
Impact
” In reality, there is no Voice over IP. It is really voice over RTP, over UDP, over IP
and usually over Ethernet. The headers and trailers are required fields for the networks
to carry the packets. The header and trailer overhead can be called the shipping and
handling cost.
Keeping this in mind, a few calculations and numbers should be considered. The RTP,
UDP, IP headers add 40 bytes to the digitized voice mentioned, the Ethernet trailer and
header contribute with 18 bytes overhead. A total of 58 bytes of overhead are generated
outside of any voice bytes in the packet, this can account for 80 to 20 percent of the
bandwidth used in a VoIP call. This is in a single packet, and this shows how inefficient
shorter packets are in contrast to longer ones. And this is all before any encryption is
added. [1]
From the above discussion we can conclude that the bandwidth consumption of a VoIP
call relies on, Compression Techniques used, Packet Overheads, and Network Protocol
used.](https://image.slidesharecdn.com/baafc7c9-b52b-44f8-bcd3-fea380945fdb-160701233408/75/Challenges-in-VoIP-Systems-Mostafa-Ahmed-Mostafa-El-Beheiry-First-Draft-Final-34-2048.jpg)
![CHAPTER 3. OWN WORK 29
Solvability
An issue such as this has indeed attained a significant amount of attention and for the
most part can be considered solvable, with various applicable solutions.
The first of which would be compressing voice in the RTP packets, which in the end
makes up the majority of the bandwidth usage. Which is how Codecs came by, and will
be discussed in depth in the coming section.
However compressing voice comes at a price and creates an interesting trade off which
needs to be taken into consideration. The lower the size of the file the easier it is to
send and the smaller the delay, however compression in essence usually involves a loss of
data. Hence in order to better the quality of a call for a low bandwidth link, it could
be that the quality is being brought down in terms of the actual call itself. Also, while
compression decreases the delay in sending the packet it does create a sort of processing
delay to compress the packet in the first place.
Strategies on choosing a certain codec will be discussed in the coming section, this
section could be considered as an introductory section to the coming one, or the coming
a supplementary section to this[1].
Figure 3.7: Bandwidth Calculation
Another way to manage this issue, is to allocate bandwidth where possible to VoIP
calls alone. This can be attained by calculating the bandwidth needed by the system and
reserving this amount exclusively for the VoIP calls.](https://image.slidesharecdn.com/baafc7c9-b52b-44f8-bcd3-fea380945fdb-160701233408/75/Challenges-in-VoIP-Systems-Mostafa-Ahmed-Mostafa-El-Beheiry-First-Draft-Final-35-2048.jpg)

![CHAPTER 3. OWN WORK 31
Figure 3.8: Codec Influence
Solvability
As is mentioned in the Bandwidth section, given the bandwidth available along with the
available codecs, a good VoIP System can dynamically change the codec to use for each
call.
For instance, if the network is congested at peak time, a lower quality codec should
be used to compensate for the lack of available bandwidth, and on the other hand, during
low periods a higher quality codec could be used.
The following are the four most popular codecs [1] along with an analysis of each,
the last table will showcase the codecs Cisco use along with a table provided from their
website and official docs.
G.711, the industry standard which digitizes voice, with no encryption at 64 Kbps.
G.722, as with G.711 it operates at the same 64 Kbps, but offers much higher quality
speech by delivering analog sound range of 7kHz as opposed to the 3.4kHz by its
G.711 counterpart.
G.723.1, reduces bandwidth consumption greatly but the speech is noticeably poorer than
its counterparts. It runs at 6.3 5.3 Kbps.
G.729, compresses at 8 Kbps, with a quality that falls just short of G.711.
Quick suggestions would refer G.722 for the best links, G.729 for the moderate ones,
and G.723.1 for the worst of links.](https://image.slidesharecdn.com/baafc7c9-b52b-44f8-bcd3-fea380945fdb-160701233408/75/Challenges-in-VoIP-Systems-Mostafa-Ahmed-Mostafa-El-Beheiry-First-Draft-Final-37-2048.jpg)
![CHAPTER 3. OWN WORK 32
A more detailed look can be had at the other available codecs from figure 3.9 taken
from Cisco [3].
Figure 3.9: Codecs](https://image.slidesharecdn.com/baafc7c9-b52b-44f8-bcd3-fea380945fdb-160701233408/75/Challenges-in-VoIP-Systems-Mostafa-Ahmed-Mostafa-El-Beheiry-First-Draft-Final-38-2048.jpg)
![CHAPTER 3. OWN WORK 33
3.2.3 Queueing
Traffic lights exist in the digital world as much as they do in the real world, a big part of
QoS is prioritizing which traffic moves on and which is delayed based on its classification
or characteristics.
Origin
When dealing with traffic in the real world, very little distinguishment is made, leading
to important cargo being put behind lesser important ones when being processed due to
the nature of how things work.
However in the digital world, there is a way to classify packets based on their priority,
based on how fast they need to be dealt with. The issue at hand is congestion, with the
various forms of traffic on any given system at any given time, any VoIP System will be
faced with the issue of Congestion.
Impact
Simply put, if handled in an improper fashion, congestion will lead to huge amounts of
lag inside calls, without proper prioritizing for the packets carrying the voice a proper
call would never take place.
Solvability
To solve the issue of congestion and to ensure that the higher priority packets be dealt with
immediately, a series of Queueing Systems were established. This section will highlight
four queuing systems, and their role in VoIP Systems [12].
First In First Out (FIFO), is the first, easiest, and most inefficient method. In reality
it is not a real queueing system, it simply transmits by order of arrival.
Priority Queuing (PQ), this method assigns four different priorities for each packet
based on its classification, ranging from High, Medium, Normal, and to Low. Simply
put, when packets are received those in the High Queue are transmitted before those in
medium, and then those in normal and finally those in low. The fundamental flaw in this
system is that the Low Priority Queue might never be handled if there is an influx of the
higher priorities.
Custom Queueing (CQ), sixteen queues are offered with this method and as with PQ
the packets are assigned to these queues based on classification. It operates in a round
robin and its goal was to stop protocol starvation, this method does however introduce a
large amount of overhead and can prove to be detrimental.
Weighted Fair Queueing (WFQ), dynamically assigns bandwidth to the traffic reliant
on the weight or IP Precedence Value within the IP headers. This method however may](https://image.slidesharecdn.com/baafc7c9-b52b-44f8-bcd3-fea380945fdb-160701233408/75/Challenges-in-VoIP-Systems-Mostafa-Ahmed-Mostafa-El-Beheiry-First-Draft-Final-39-2048.jpg)

![CHAPTER 3. OWN WORK 35
3.2.4 Low Speed Links
Catering for lower speed links can be difficult, but what exactly is defined as a low speed
link? The speeds considered by modern day researches to be slow links range from 56
kbps, to 2 Mbps. And hence special care should be given to those links.
Origin
Bandwidth in developing countries, or indeed any bandwidth that passes through un-
derwater cables, is very expensive to attain. Taking into consideration the weak infras-
tructure, poverty rates, and general quality of life in these countries would lead to the
conclusion that a well set up person would most likely actively work under a low speed
link.
Impact
What this means however, is that there is little and less bandwidth to provide for whatever
work is being done alongside a VoIP Call, which takes high priority in its share for
bandwidth.
This means that not all the VoIP Quality Assurance Parameters are satisfied, delays
could increase the 150ms barrier, jitter extends the 25ms margin, and packet loss exceeds
the maximum allowed.
Solvability
Researches have shown that the methods mentioned in this paper can be enough to deal
with these types of links. [13]
More advanced Queuing Algorithms such as Weighted Random Early Detect (WRED)
and Low Latency Queing (LLQ), have been proposed as possible solutions.
Mixed with various selection of codecs, and through testing of these various Queuing
methods these results were attained.
For the speeds between 2Mbps and 128kbs, WFQ showed prominence, along with
G.711, while the G.728 has shown good performance for all speeds but will be excluded
on account of its much lower quality. For the lower links however no form of satisfiable
QoS was obtained after applying the various queuing algorithms and the lowest OS codecs.
Researches however still favor the G.723.1 codec as a highly recommended to use codec
for future use. The research also showed that the main culprit of QoS Degradation in
low speed links was jitter.](https://image.slidesharecdn.com/baafc7c9-b52b-44f8-bcd3-fea380945fdb-160701233408/75/Challenges-in-VoIP-Systems-Mostafa-Ahmed-Mostafa-El-Beheiry-First-Draft-Final-41-2048.jpg)



![CHAPTER 3. OWN WORK 39
3.4 Emergency
The last of the glaring challenges this work focused on, but by all means not the last
challenge facing VoIP in general.
”The ability to access emergency services by dialing 911 is a vital component of public
safety and emergency preparedness. It is imperative that consumers of telephone service
be able to reach emergency services regardless of the technology used to place a 911 call.”
[7]
This is a statement issued on the Federal Communications Commission (FCC)s own
website, which is responsible for moderating the standards of communications in the
United States of America.
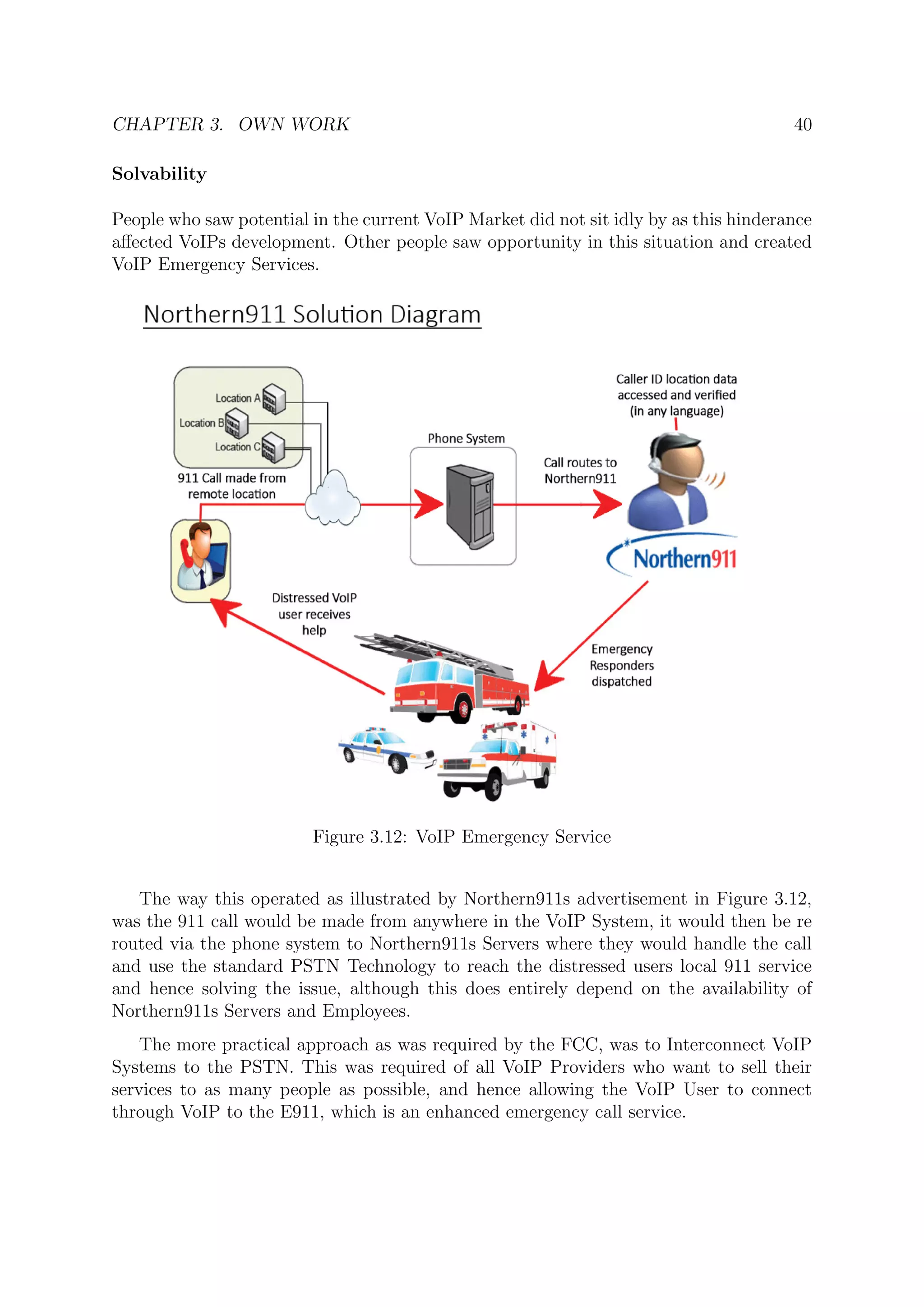
Origin
As with the power dependency issue, VoIP Systems were initially created as a way to
have vocal exchanges over the Internet or over LAN. It was not initially developed with
the mindset of defeating PSTN Telephones.
People simply aspire to use the most cost efficient methods possible to them, and
hence VoIP Systems were brought into contention with PSTN Telephones.
The way 911 calls operate is solely through the PSTN, and so it would seem that
all LAN VoIP Systems would not have the remote ability to contact 911, or even VoIP
Systems in general.
Other than this, traditional phones have a specific phone number linked to a specific
fixed address, and so upon reaching 911 Emergency Call, the location is quickly identified
and aid can be quickly offered.
However in VoIP Systems a single user can connect from virtually anywhere if the
service allows it, whether it be from home or in office. This portability raises many
challenges for VoIP Systems in regard to emergency calls.
Impact
Needless to discuss, the impact of not being able to contact 911 is great by will vary. For
instance in the office where there probably is a normal telephone in the vicinity it will
not be as big an issue as in a corporate building which focuses its communications soley
on VoIP.
Aside from the impact in reality, this issue is a defying block between VoIP Systems
chance at eclipsing PSTN phones. And so in order for VoIP Systems to progress and
develop in the mainstream consumer market a solution will need to be put into action.](https://image.slidesharecdn.com/baafc7c9-b52b-44f8-bcd3-fea380945fdb-160701233408/75/Challenges-in-VoIP-Systems-Mostafa-Ahmed-Mostafa-El-Beheiry-First-Draft-Final-45-2048.jpg)
![Chapter 4
SPIT Simulation
In order to not restrain this work to theoretics, and to further elaborate on the issues
raised by this work. Collaboration with Ahmed Khaled Saad Metwally took place, in
which this work and his merged for mutual benefit.[11]
A Running VoIP System was needed in order to present the chosen topic, which
in order to present at peak capacity needed to be restrained to a single topic, as was
suggested.
For the topic, SPIT Attacks were chosen, since it is a good basis for future work, and
can be underestimated by the majority of people. A demonstration in the true power of
SPIT even on a local scale should reveal the fact that it is a real threat that will rear its
face with the spread of VoIP Systems.
To find a suitable VoIP System, which had an open source code that was under-
standable and easy to manipulate would prove to be difficult, after much research the
conclusion to collaborate and use Ahmed Khaled’s VoIP System using Java would be the
safest and best option available. After having already build the client, the collaboration
took place when connecting it to a server, particularly the setup of a server.
While this may be slightly irrelevant to the SPIT Attack, the process should still be
mentioned and documented.
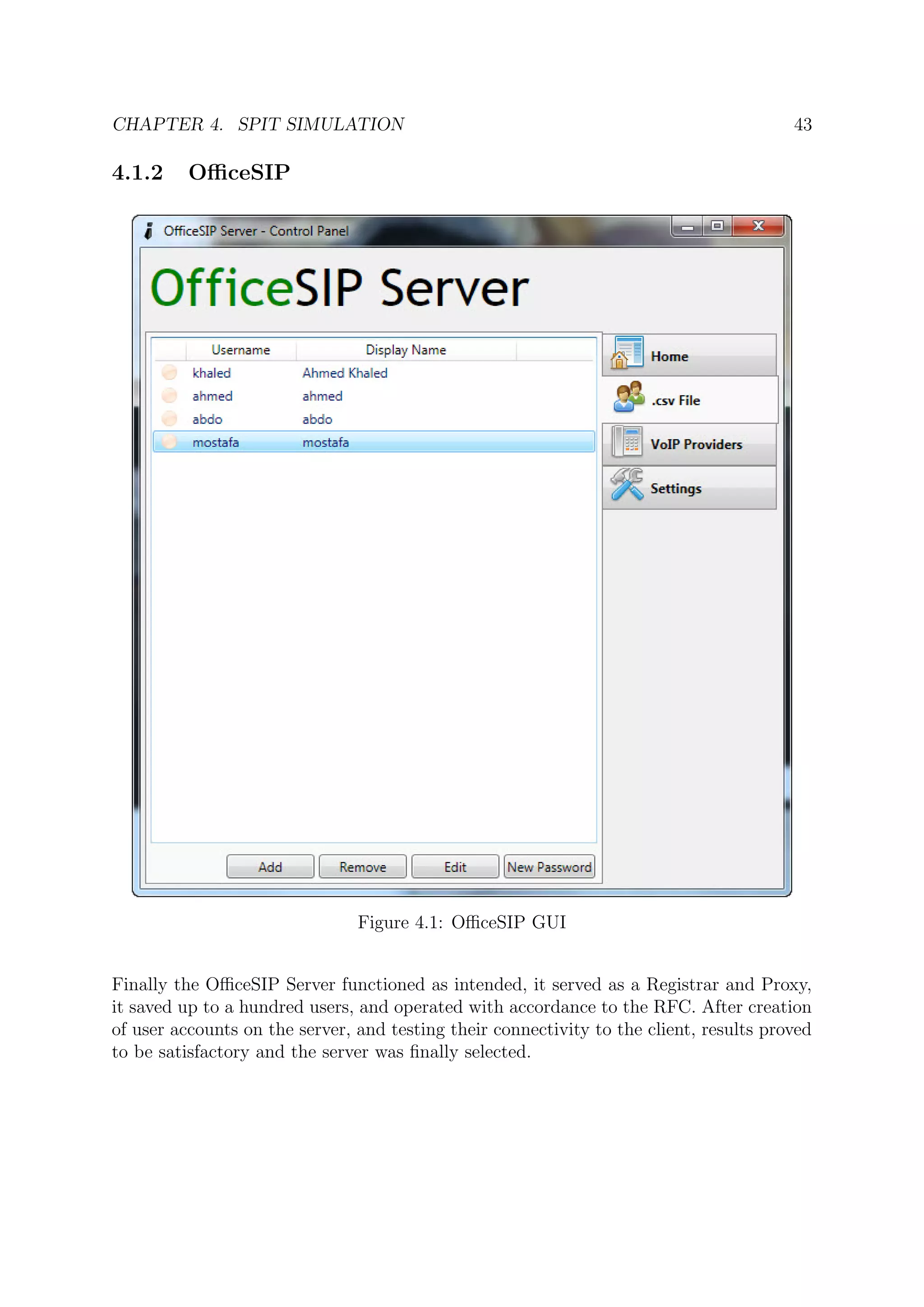
4.1 Server
Finding a suitable VoIP Proxy Server which did not act as a Private Branch Exchange
(PBX) took time to locate and install. Bearing in mind that the only Linux distributions
available at the time was Ubuntu, which was run over Oracle’s Virtual Machine. Hence
the only choice with which there was sufficient experience was Windows.
41](https://image.slidesharecdn.com/baafc7c9-b52b-44f8-bcd3-fea380945fdb-160701233408/75/Challenges-in-VoIP-Systems-Mostafa-Ahmed-Mostafa-El-Beheiry-First-Draft-Final-47-2048.jpg)






![CHAPTER 4. SPIT SIMULATION 49
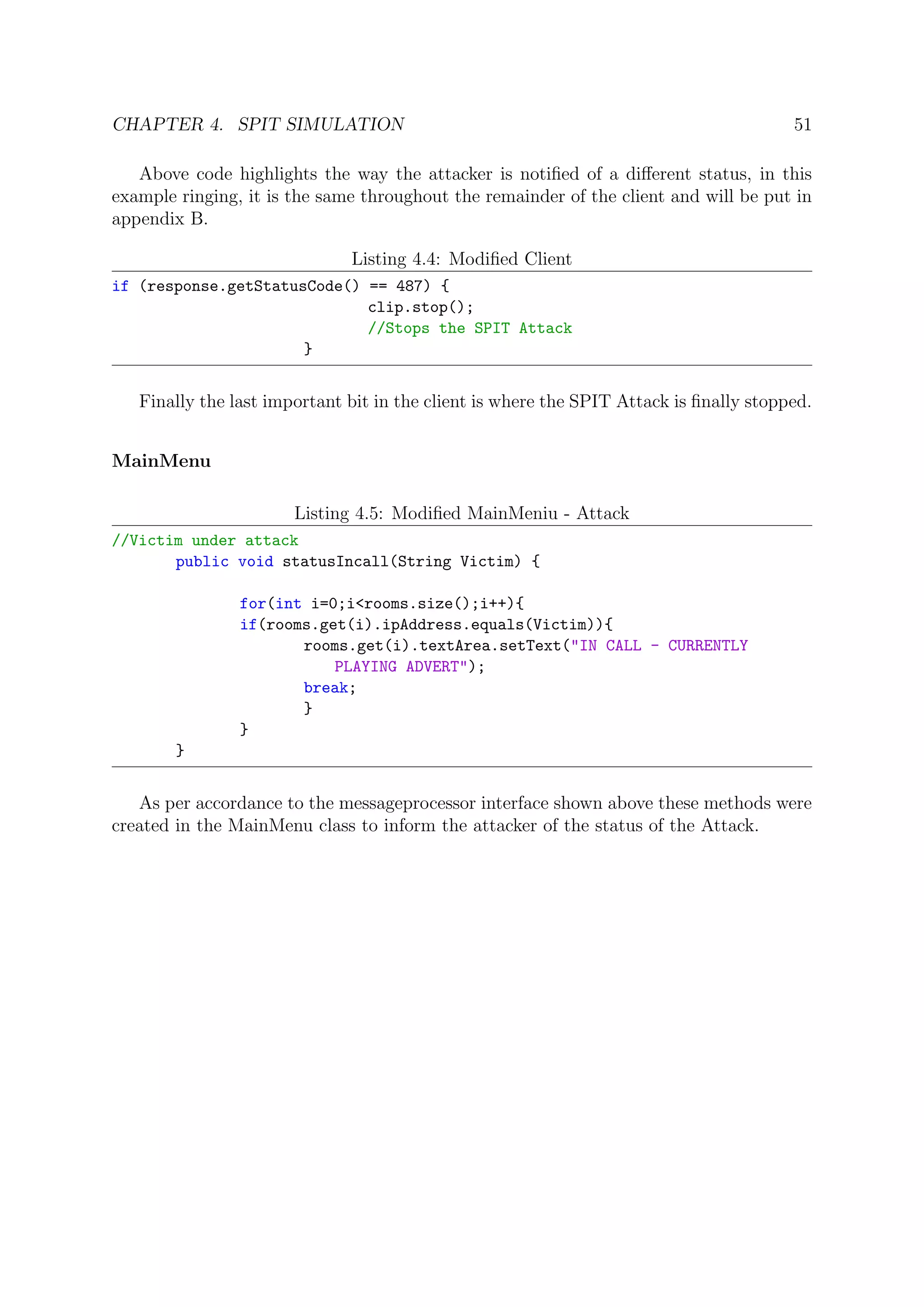
4.3.2 Code
This section details what was changed in Ahmed Khaled’s Client in technical terms. To
be noted as a reminder that the client was made entirely in Java and hence the code
displayed in this chapter is Java code.
For a detailed description on how Ahmed Khaled handled his own client, the report
VOIP in Java is available and is cited here [11].
The coming section will dissect the changes and tackle them per class.
messageprocessor
Listing 4.1: Modified RTP Sender
public void statusIncall(String Victim);
// Tells the attacker that the call has been established
public void statusCalling(String Victim);
// Tells the attacker that the user is being called
public void statusUserEndedcall(String Victim);
// Tells the attacker that the user ended the call
public void statusUserOffline(String Victim);
// Tells the attacker that the user is offline
public void statususerbusy(String Victim);
// Tells the attacker that the user is busy
These methods were added to the messageprocessor interface, to facilitate communi-
cation between the back and front ends.
They handle the status box shown in figure 4.8 on page 48. The statuses available are
the ones the attacker needs to concern himself with, such as whether the victim’s phone
is ringing, or whether the call is established and a certain advert is beind played, or if
the user ended the call and the SPIT attack attempts to redial, or if the user is simply
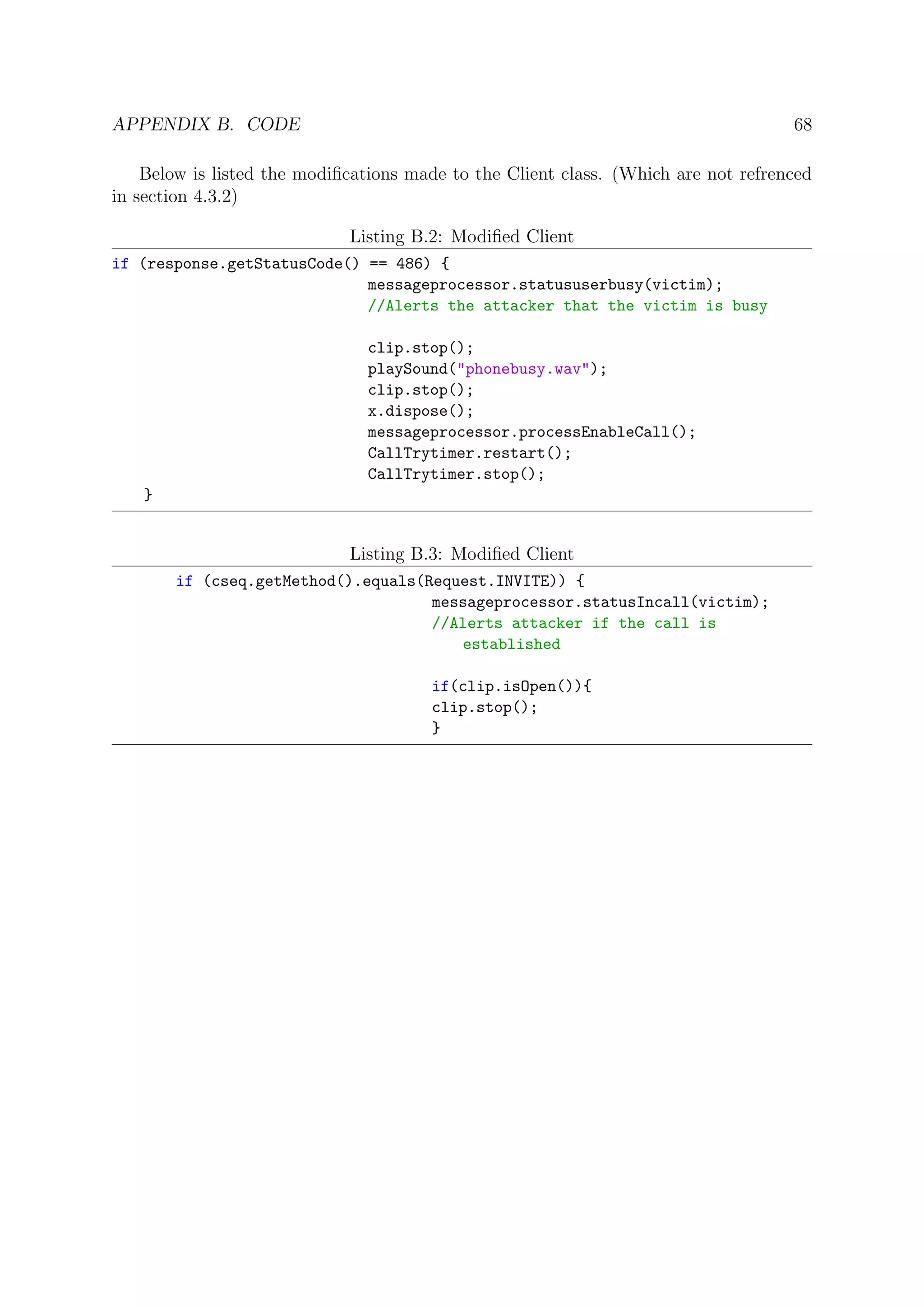
offline or is in a call.](https://image.slidesharecdn.com/baafc7c9-b52b-44f8-bcd3-fea380945fdb-160701233408/75/Challenges-in-VoIP-Systems-Mostafa-Ahmed-Mostafa-El-Beheiry-First-Draft-Final-55-2048.jpg)


![CHAPTER 5. CONCLUSION AND FUTURE WORK 53
5.1 Security
5.1.1 Packet Sniffers
The suggested solution to this issue, was to find a good trade-off between security and
compatibility depending on the system in question, a casual chat application will need
to be more compatible on more devices than a Secret Service Agency would need, and
in turn the Agency would prefer to capitalize on the strongest security possible hence
decreasing the amount of devices with the capability of compatibility drastically.
For future work in this matter, the suggestion would be to research for the possible
optimal level of security to compatibility, for instance creation of a rating system to rate
the security and the compatibility of the VoIP System in terms of encryption and a study
to ensue to establish a Security to Compatibility ratio.
5.1.2 Eavesdropping
Assuming an encrypted system, to further protect against eavesdropping researches sug-
gest to use a random length padding to the VBR encoded output to confuse and throw
off the newer methods of realizing a phrase when uttered throughout a call.
This subject, while very specific, is considered fertile ground for future work. The
two strongly backed researches mentioned should be read and considered, and to build
on their work the suggested solution implemented. The reports in question are [20] and
[14].
5.1.3 DDoS
Further research in this area is a must, the need is rising quickly and the only real defence
available it to mitigate the DDoS attack, high profile targets should look at Cloud Based
Mitigation companies, while more middle ranged targets should look to implement an
IDS.
The toughest task to tackle due to the ease of its execution but the one in most need
of handling.
5.1.4 SPIT
An area of great controversy as there is a vast multitude of solutions available, but all
possess exploitable weaknesses, anyone with the ability to: Device Spoof, SIP Identity
Spoof, SIP Header Spoof, Reputation Push or Pull, CAPTCHA Relay Attack, SIP Iden-
tity Hijack, Call Rate Adapt and Account Switch, will breech all currently available](https://image.slidesharecdn.com/baafc7c9-b52b-44f8-bcd3-fea380945fdb-160701233408/75/Challenges-in-VoIP-Systems-Mostafa-Ahmed-Mostafa-El-Beheiry-First-Draft-Final-59-2048.jpg)


![CHAPTER 5. CONCLUSION AND FUTURE WORK 56
5.2.4 Low Speed Links
The current solutions for Low Speed Links are not satisfactory, yet research in the matter
is not considered to be a priority since the world is advancing in terms of speed and
quality of links available, yet research in this field is still crucial. Developing countries,
or countries with weak infrastructure for the Internet such as Egypt for example could
benefit from a detailed study and research in this particular field.
A look in [13] would prove useful for future research.](https://image.slidesharecdn.com/baafc7c9-b52b-44f8-bcd3-fea380945fdb-160701233408/75/Challenges-in-VoIP-Systems-Mostafa-Ahmed-Mostafa-El-Beheiry-First-Draft-Final-62-2048.jpg)













![Bibliography
[1] Gary Audin. Voip bandwidth fundamentals. 2008.
[2] Ed B. Campbell, J. Rosenberg, H. Schulzrinne, C. Huitema, and D. Gurle. Sip
message extension. Standards Track, 2002.
[3] Cisco. Voice over ip - per call bandwidth consumption. 2006.
[4] Gerald Combs. About wireshark. 2014.
[5] defense.net. Ddos attack timeline: The history and changing nature of ddos attacks.
2014.
[6] K Egevang and P Francis. The ip network address translator (nat). Request for
Comments, 1994.
[7] FederalCommunicationsCommission. Voip and 911 service. 2005.
[8] Nick Galea. The main sip invite header fields explained. 3CX Blog, 2010.
[9] HughesCoporation. Voip and it’s challenges. 2006.
[10] Rachid Khayari. Spam over internet telephony and how to deal with it. 2011.
[11] Ahmed Khaled Saeed Metwally. Voip using java. Bachelor Thesis, page 0, 2014.
[12] Richard Parsons. Voip congestion management - basic queuing methods. TIP, 2004.
[13] Julije Ivana Pezelj. Voip qos on low speed links. 2012.
[14] Vasily Prokopov and Oleksii Chyrkov. Eavesdropping on encrypted voip conversa-
tions: phrase spotting attack and defense approaches. 2011.
[15] M Rafique, M Akbar, and Muddassar Farooq. Evaluating dos attacks against sip-
based voip systems. 2008.
[16] J. Rosenberg, H. Schulzrinne, G. Camarillo, A. Johnston, J. Peterson, R. Sparks,
M. Handley, and E. Schooler. Sip: Session initiation protocol. Request for Comments,
2002.
77](https://image.slidesharecdn.com/baafc7c9-b52b-44f8-bcd3-fea380945fdb-160701233408/75/Challenges-in-VoIP-Systems-Mostafa-Ahmed-Mostafa-El-Beheiry-First-Draft-Final-83-2048.jpg)
![BIBLIOGRAPHY 78
[17] Matthew Ruck. Top ten security issues with voice over ip (voip). designData, 1:0,
2010.
[18] H. Schulzrinne, S. Casner, R. Frederick, and V. Jacobson . Rtp: A transport protocol
for real-time applications. Request for Comments, 2003.
[19] VLC Staff. Vlc download statistics. https://videolan.org/vlc/stats/downloads.html,
2014.
[20] Charles Wright, Lucas Ballard, Scott Coull, Fabian Monrose, and Gerald Masson.
Uncovering spoken phrases in encrypted voice over ip conversations. 2010.](https://image.slidesharecdn.com/baafc7c9-b52b-44f8-bcd3-fea380945fdb-160701233408/75/Challenges-in-VoIP-Systems-Mostafa-Ahmed-Mostafa-El-Beheiry-First-Draft-Final-84-2048.jpg)