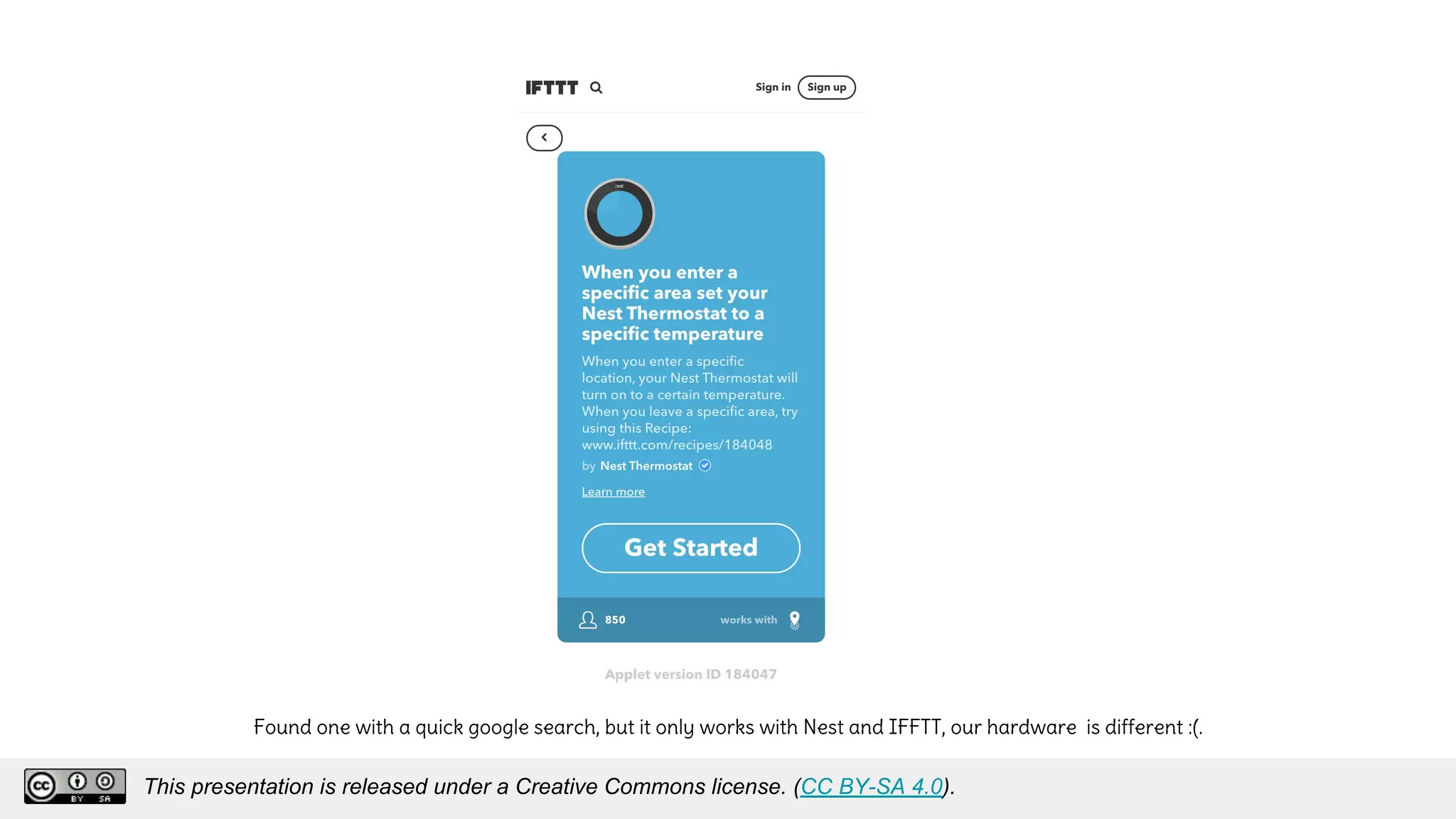
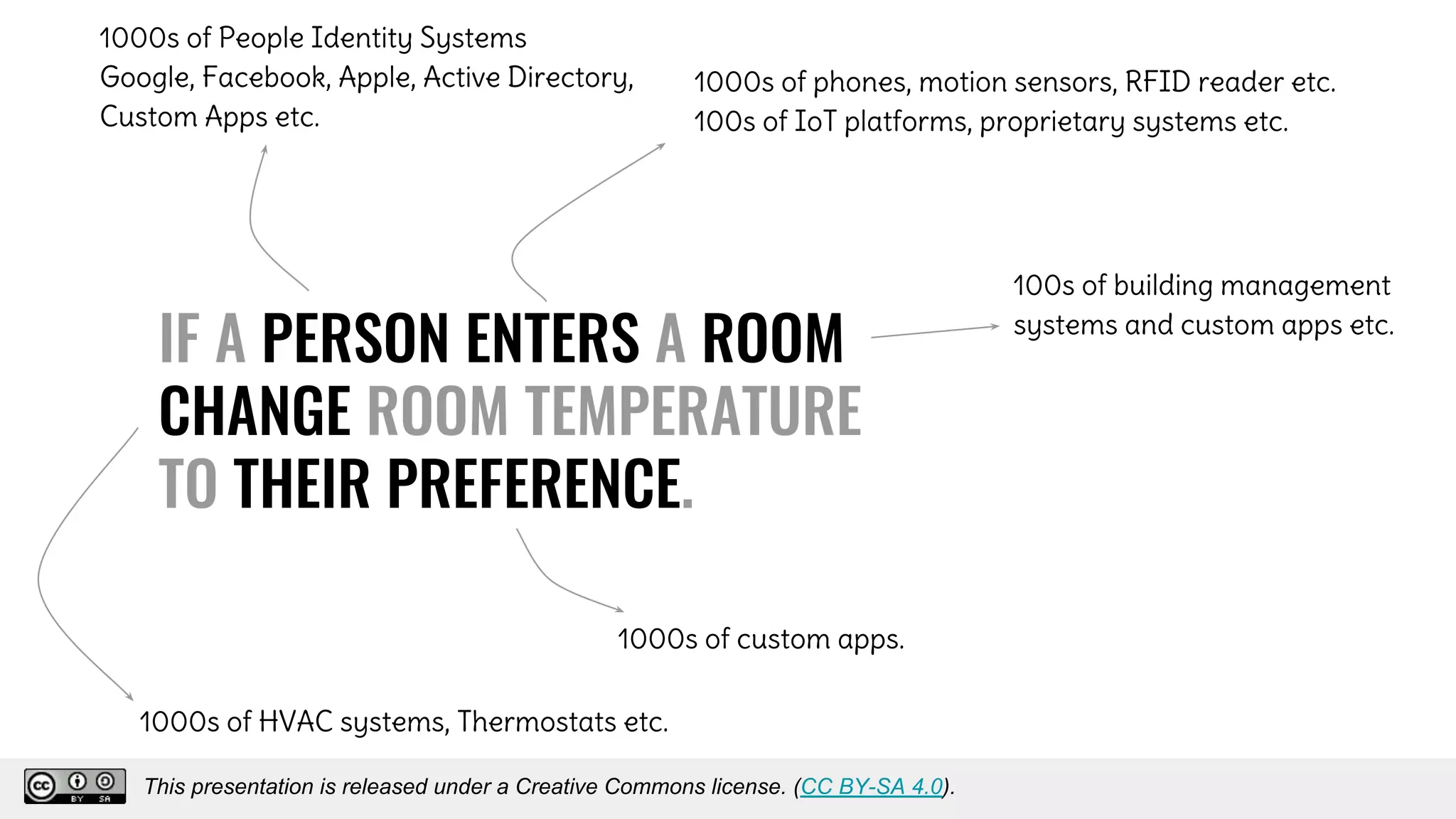
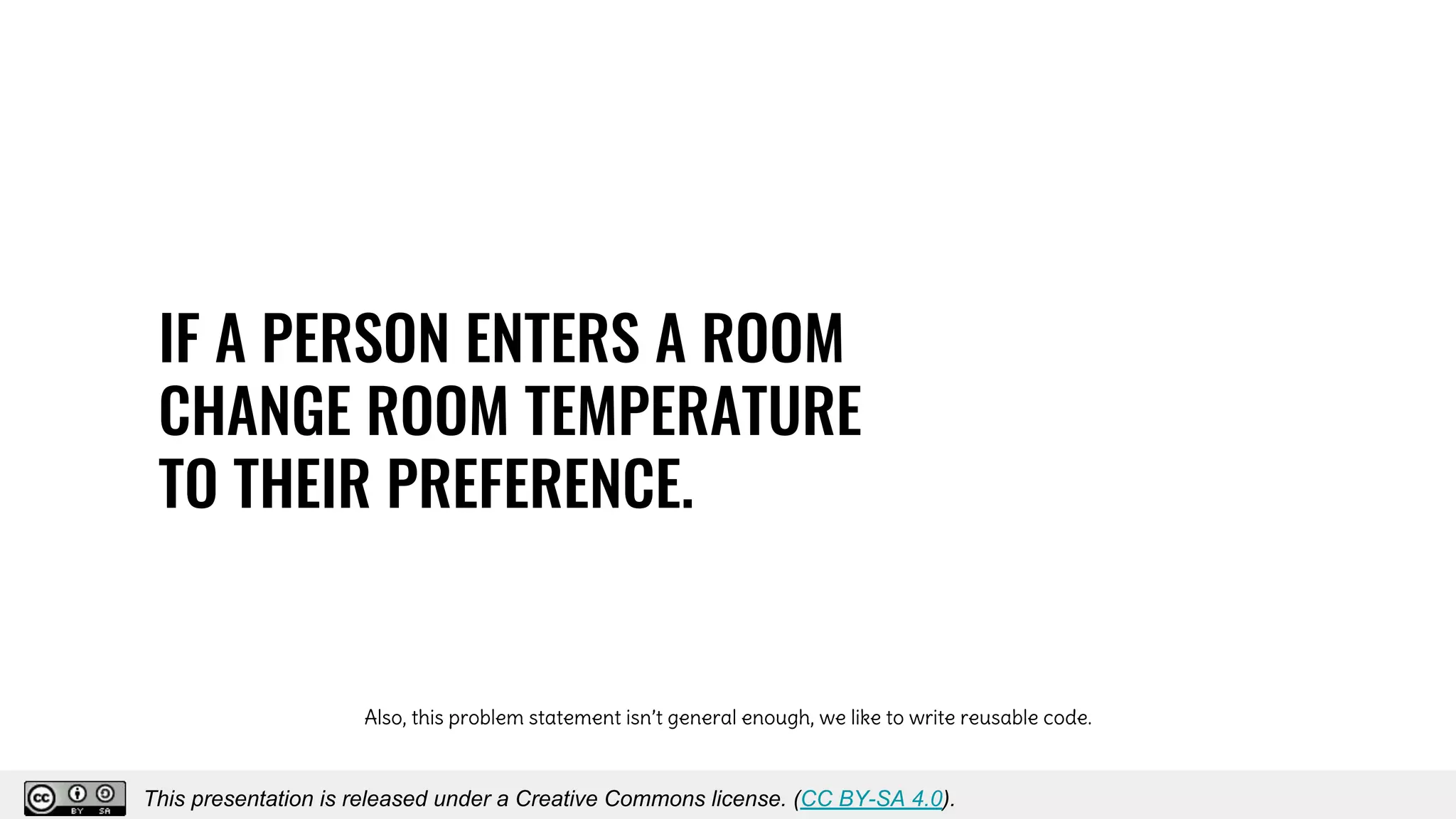
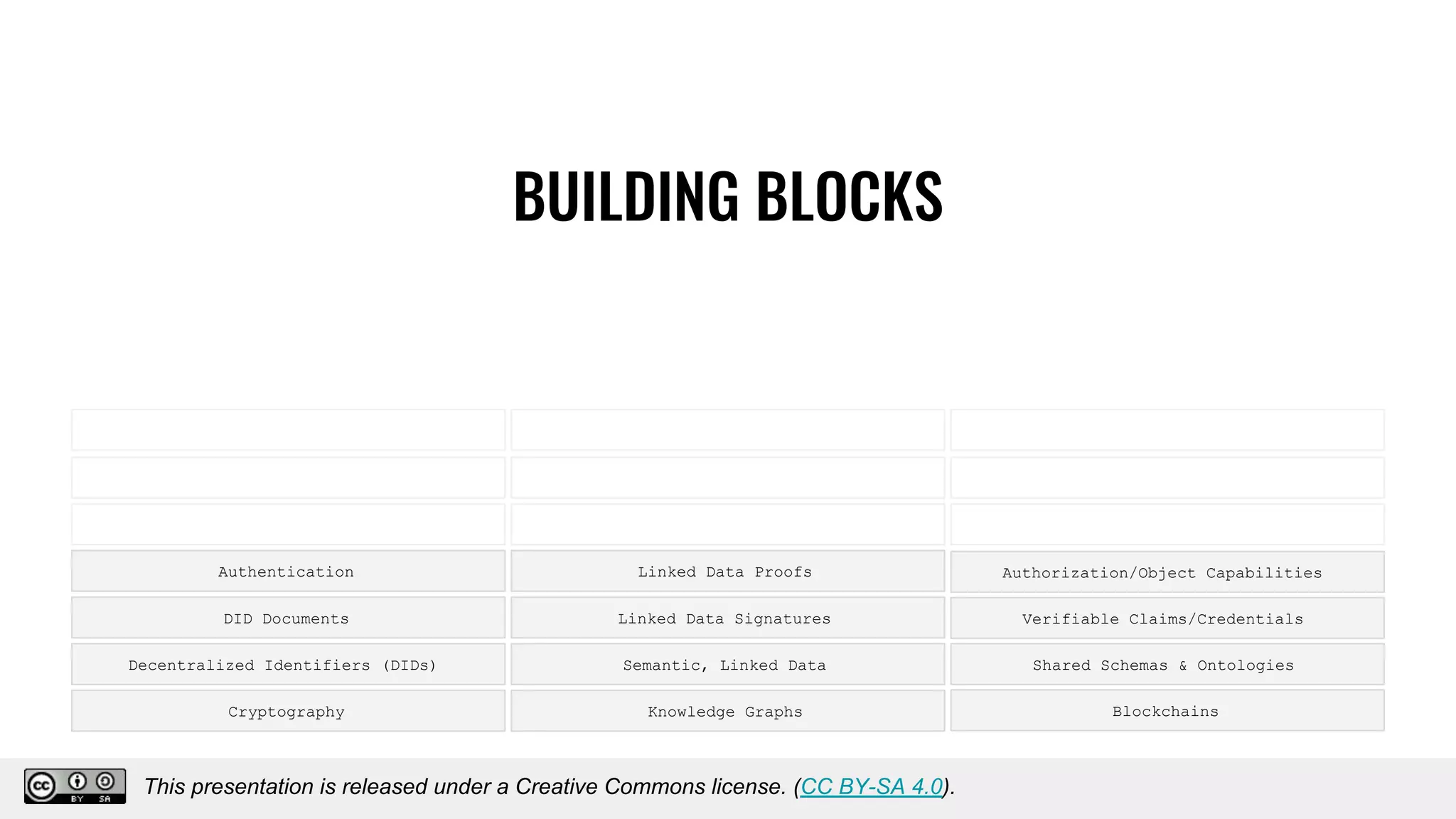
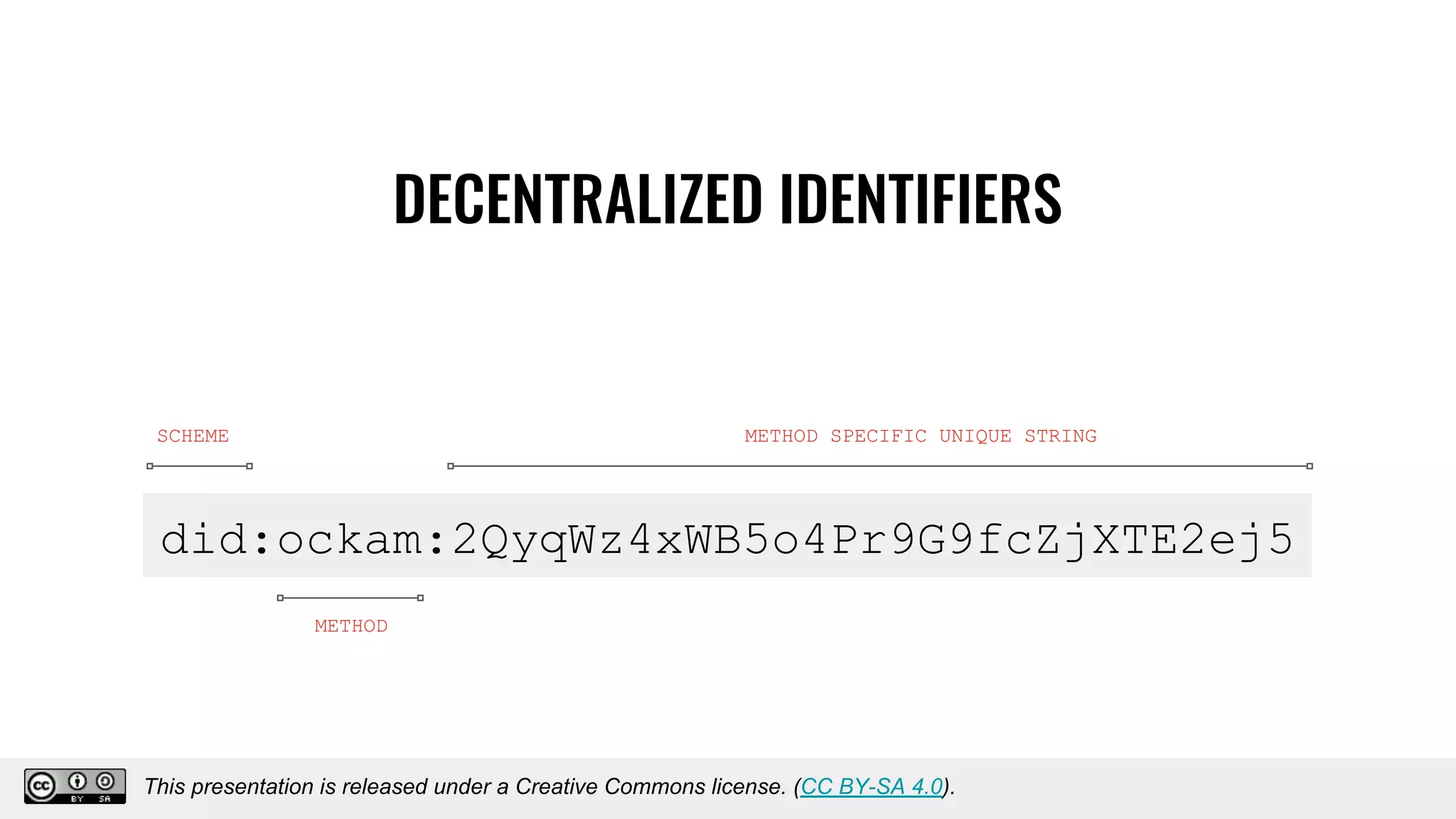
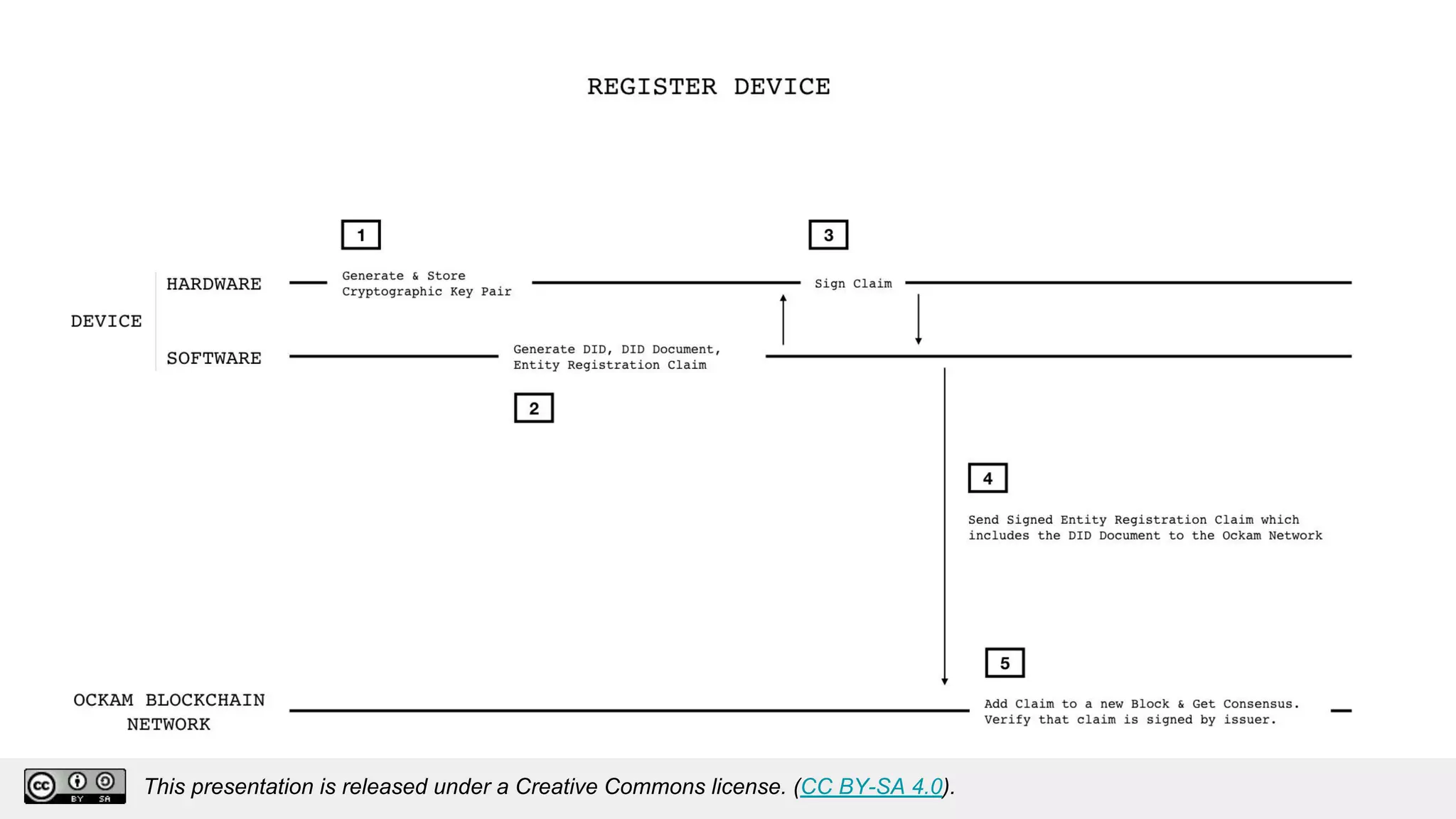
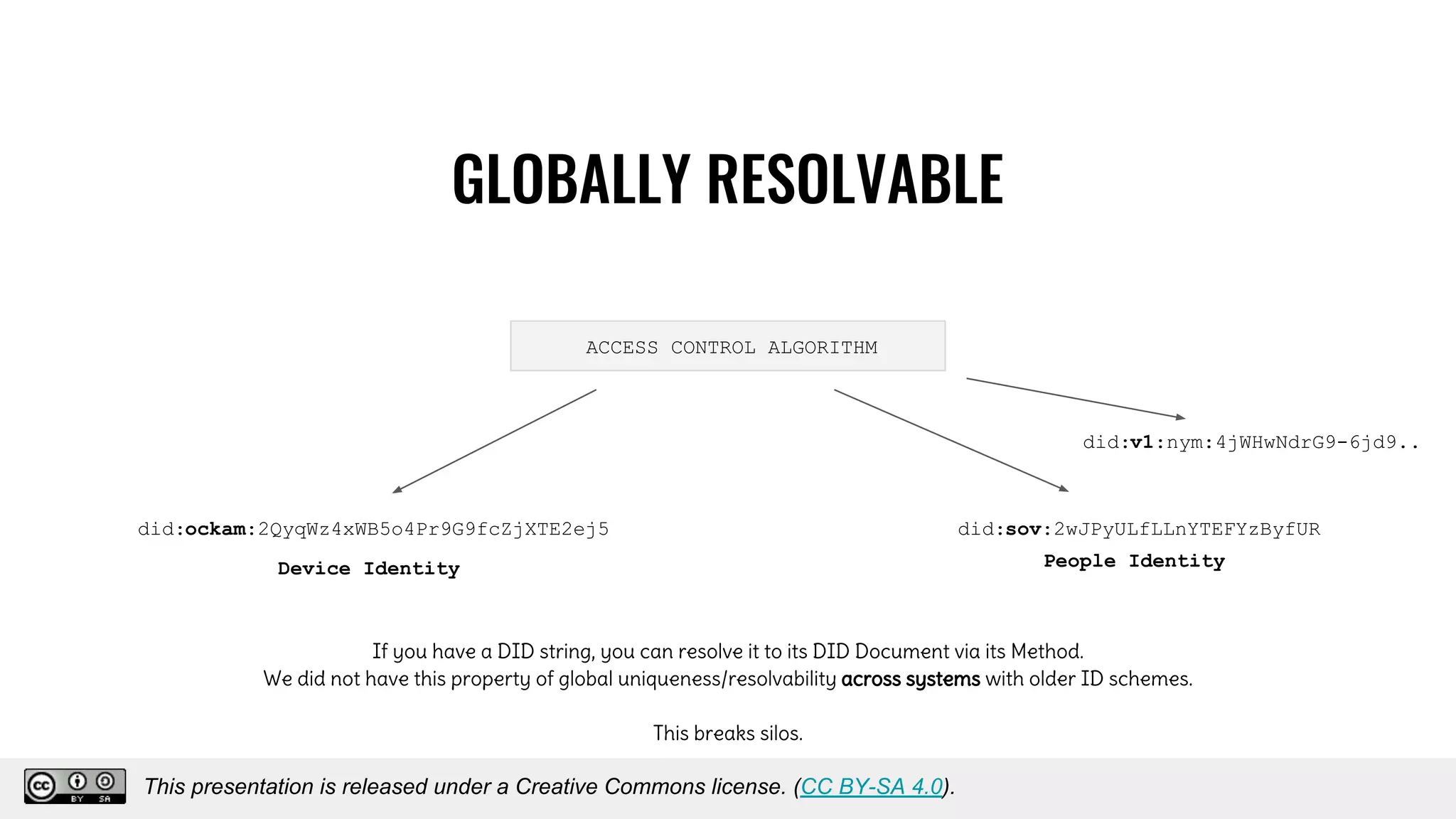
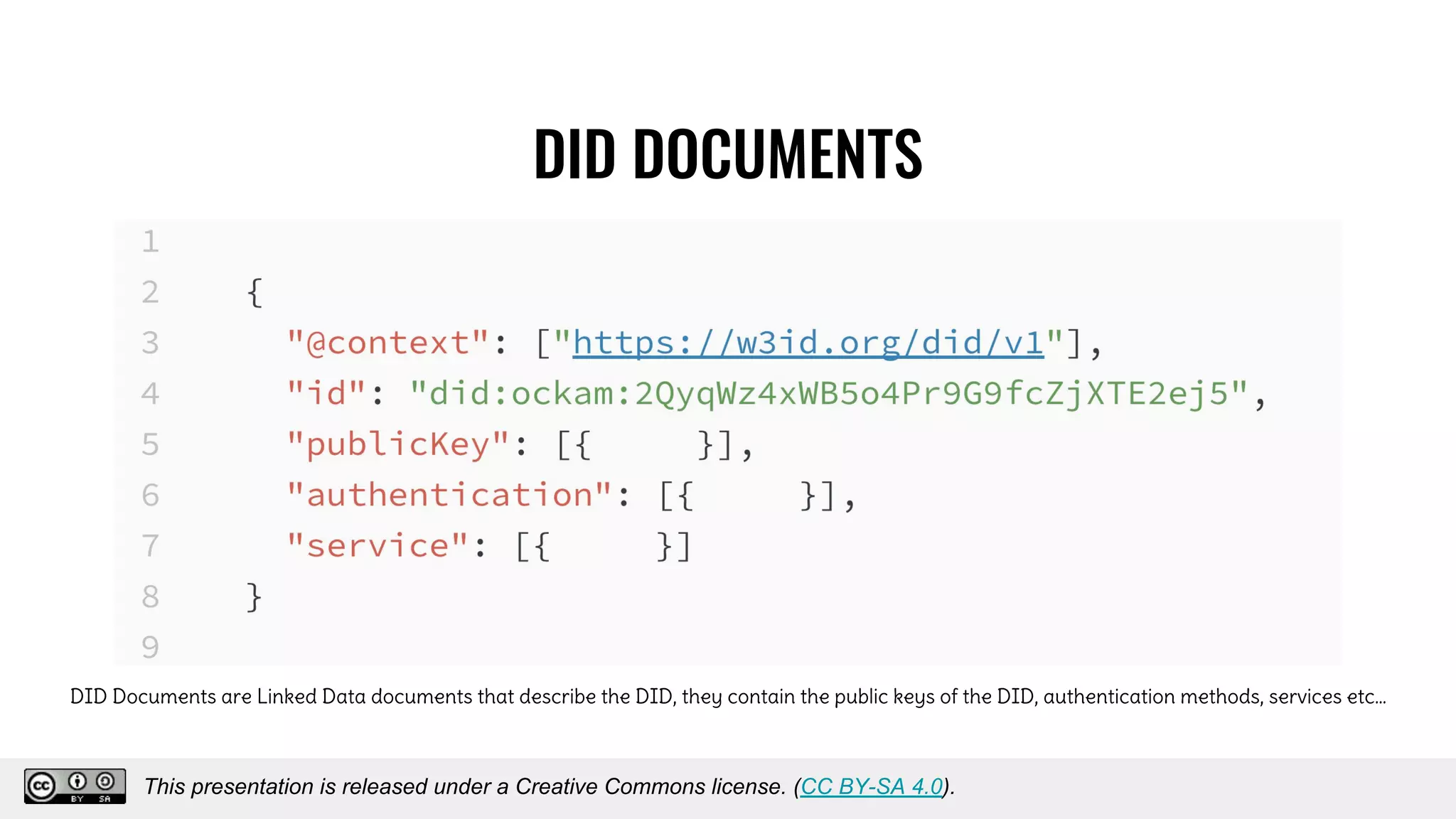
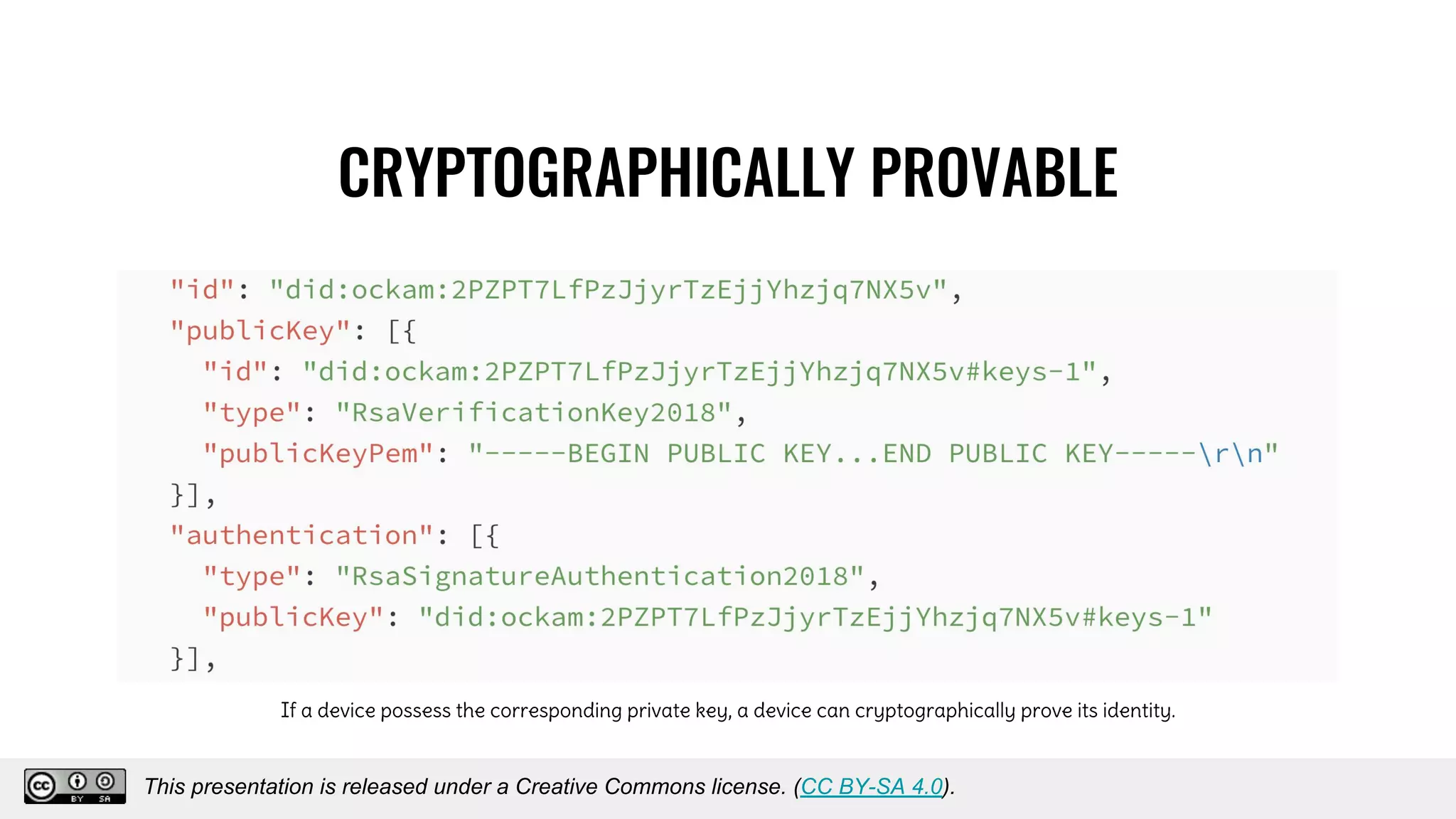
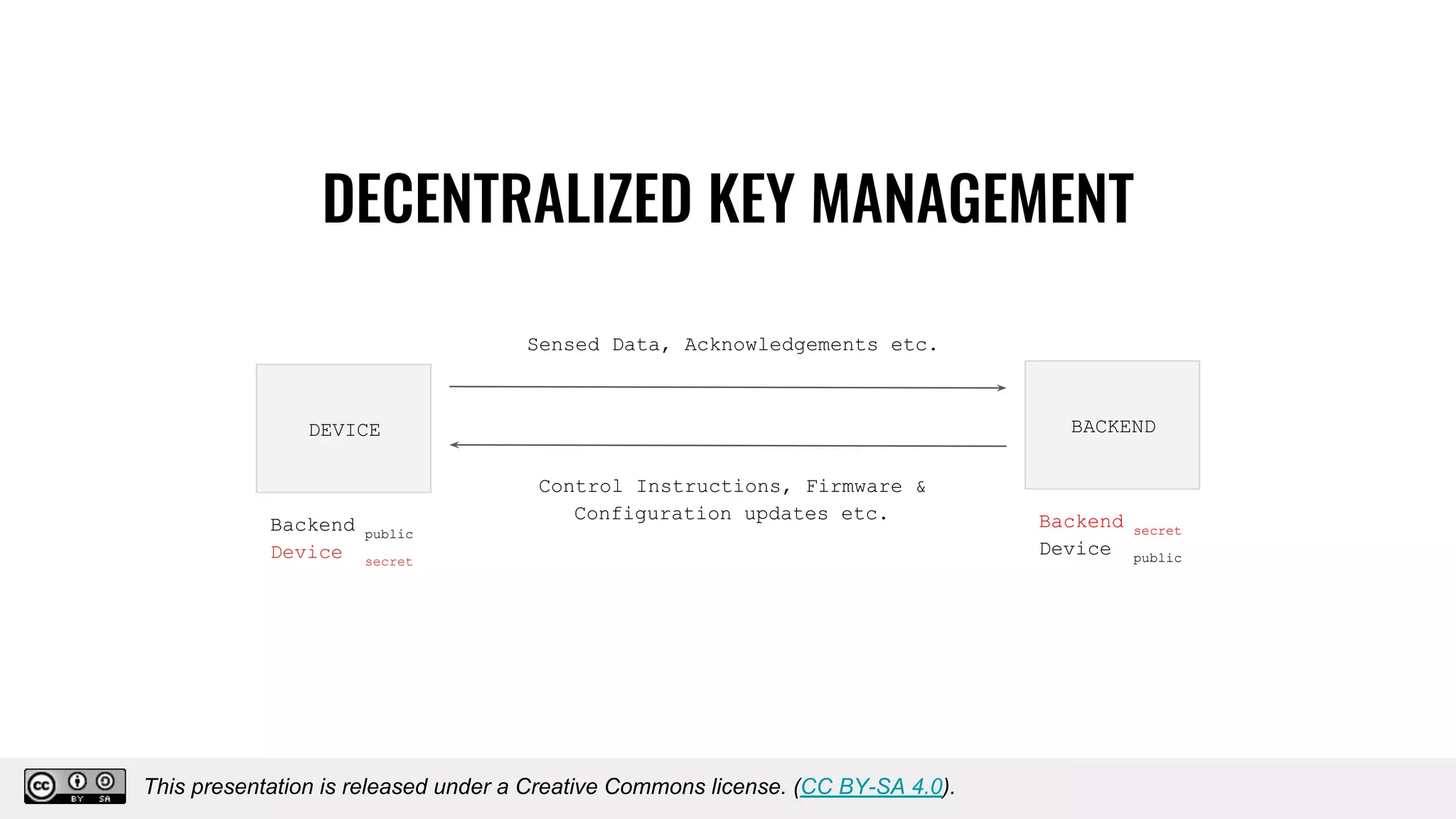
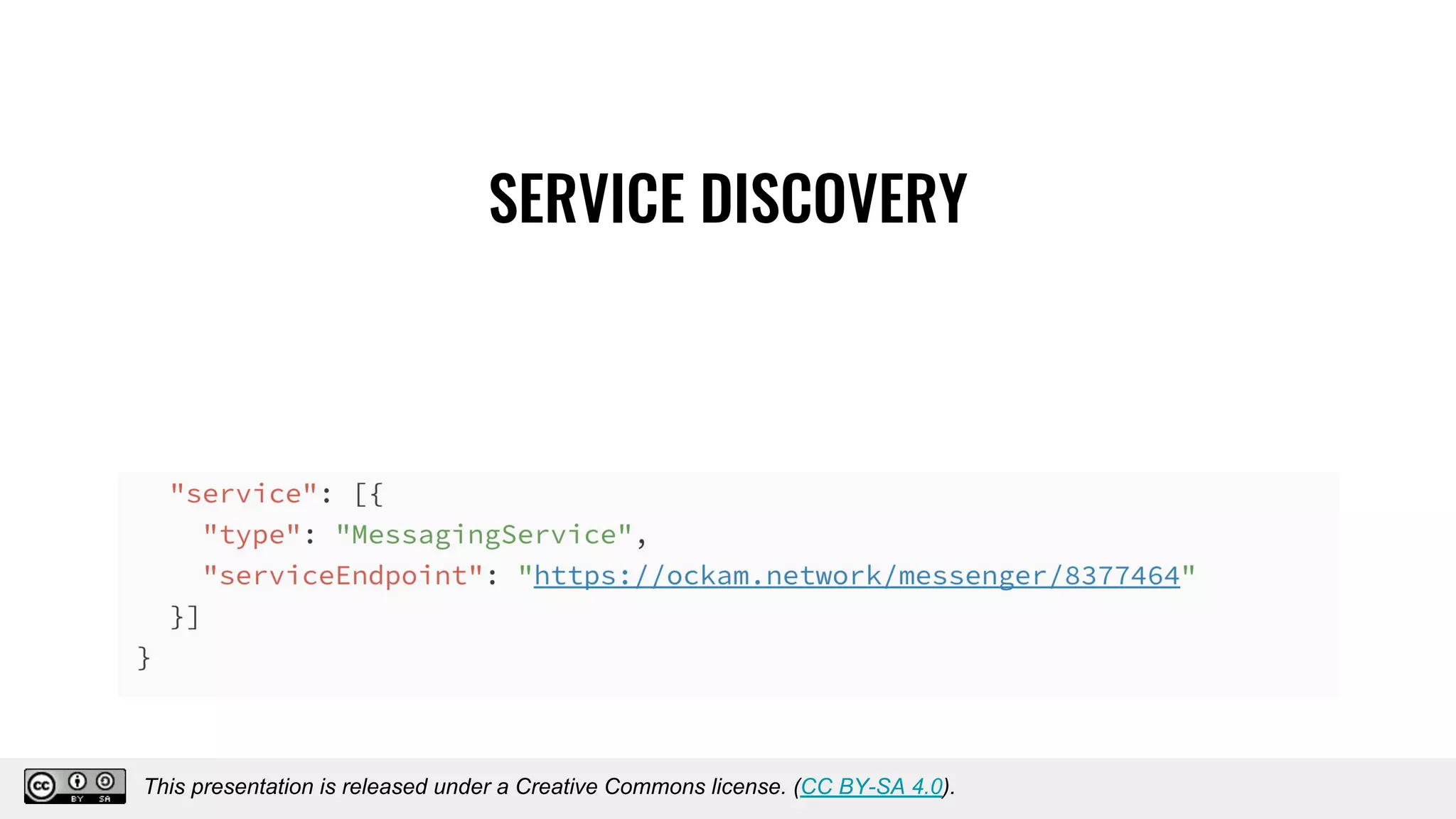
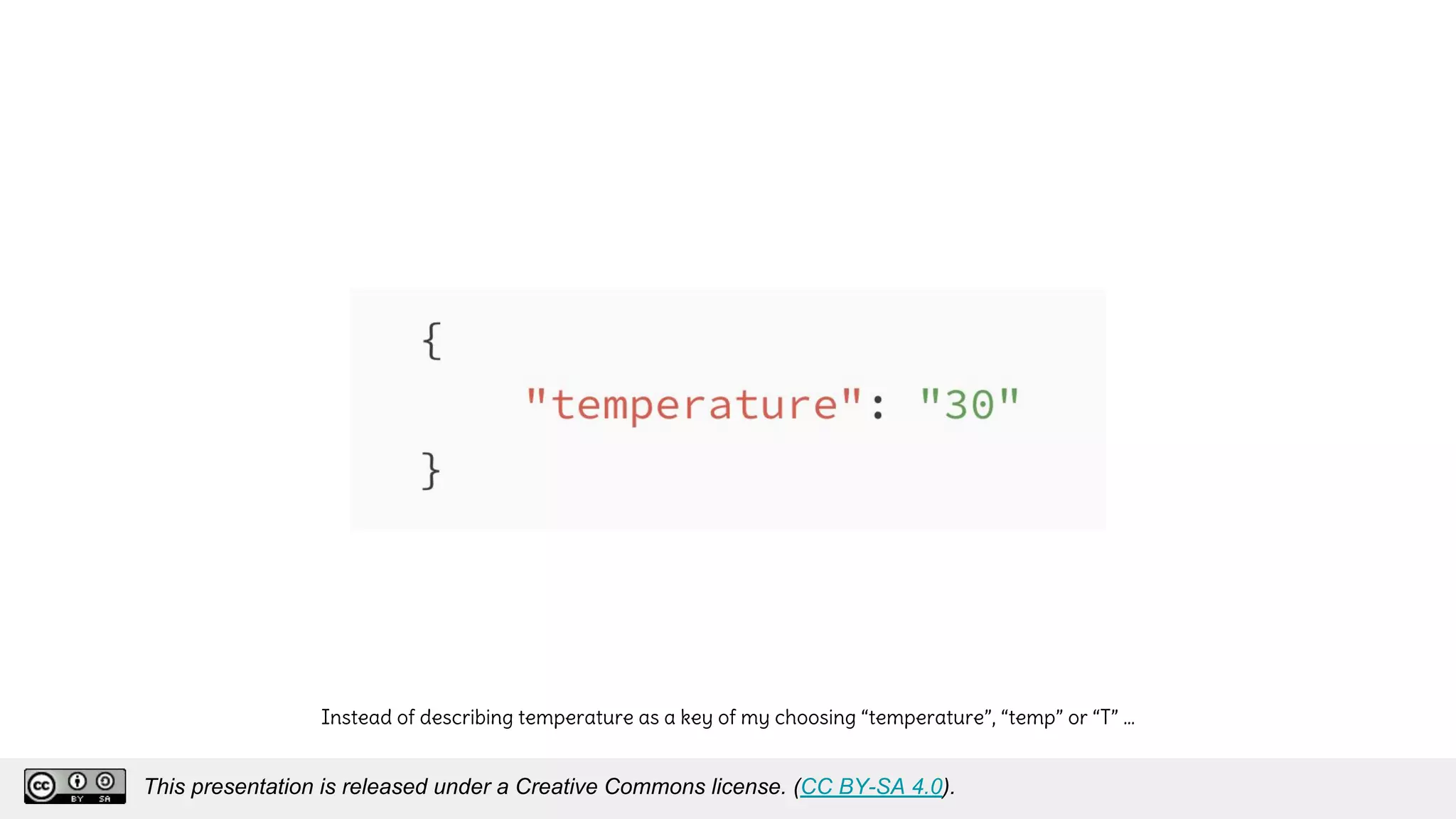
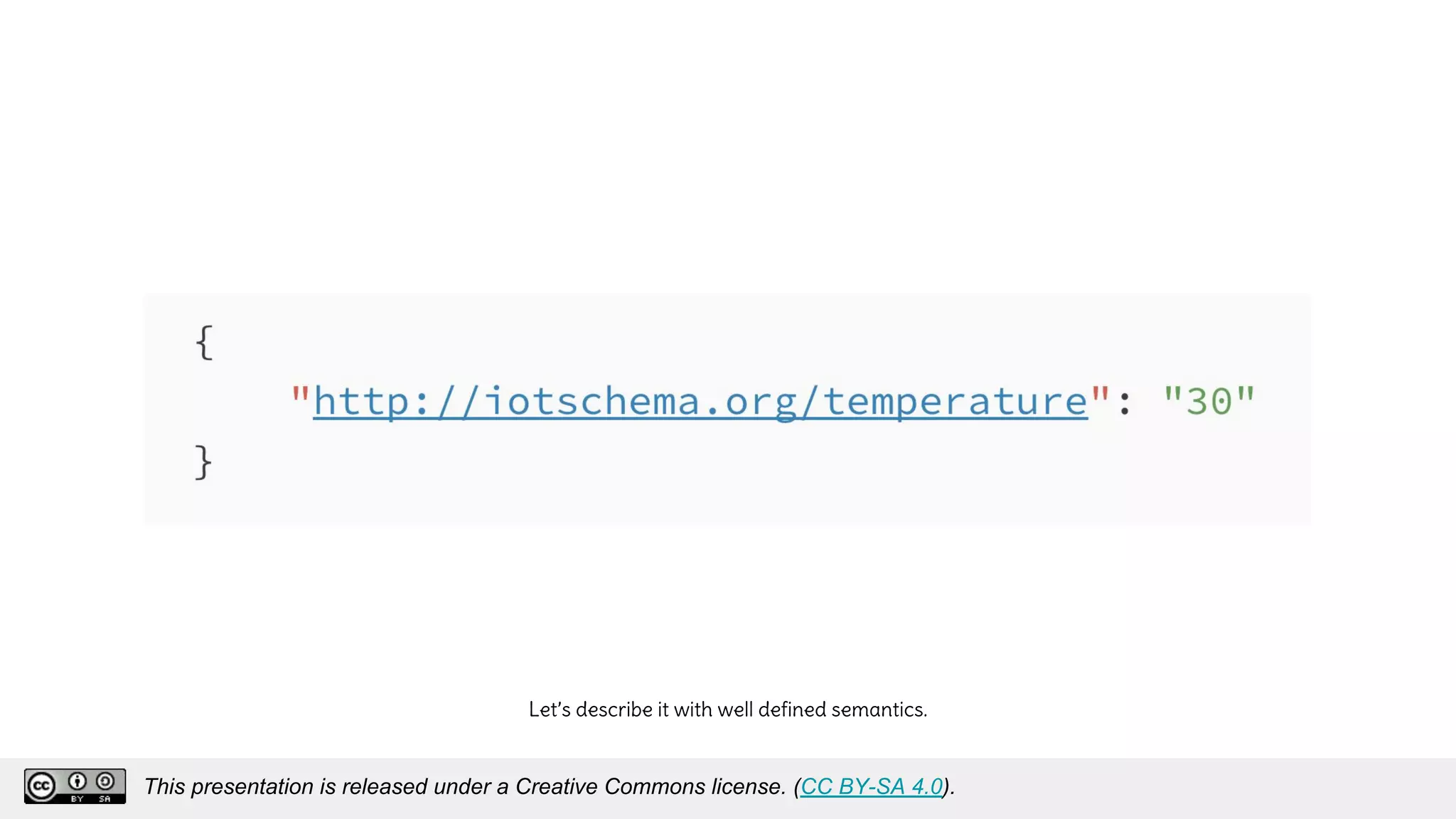
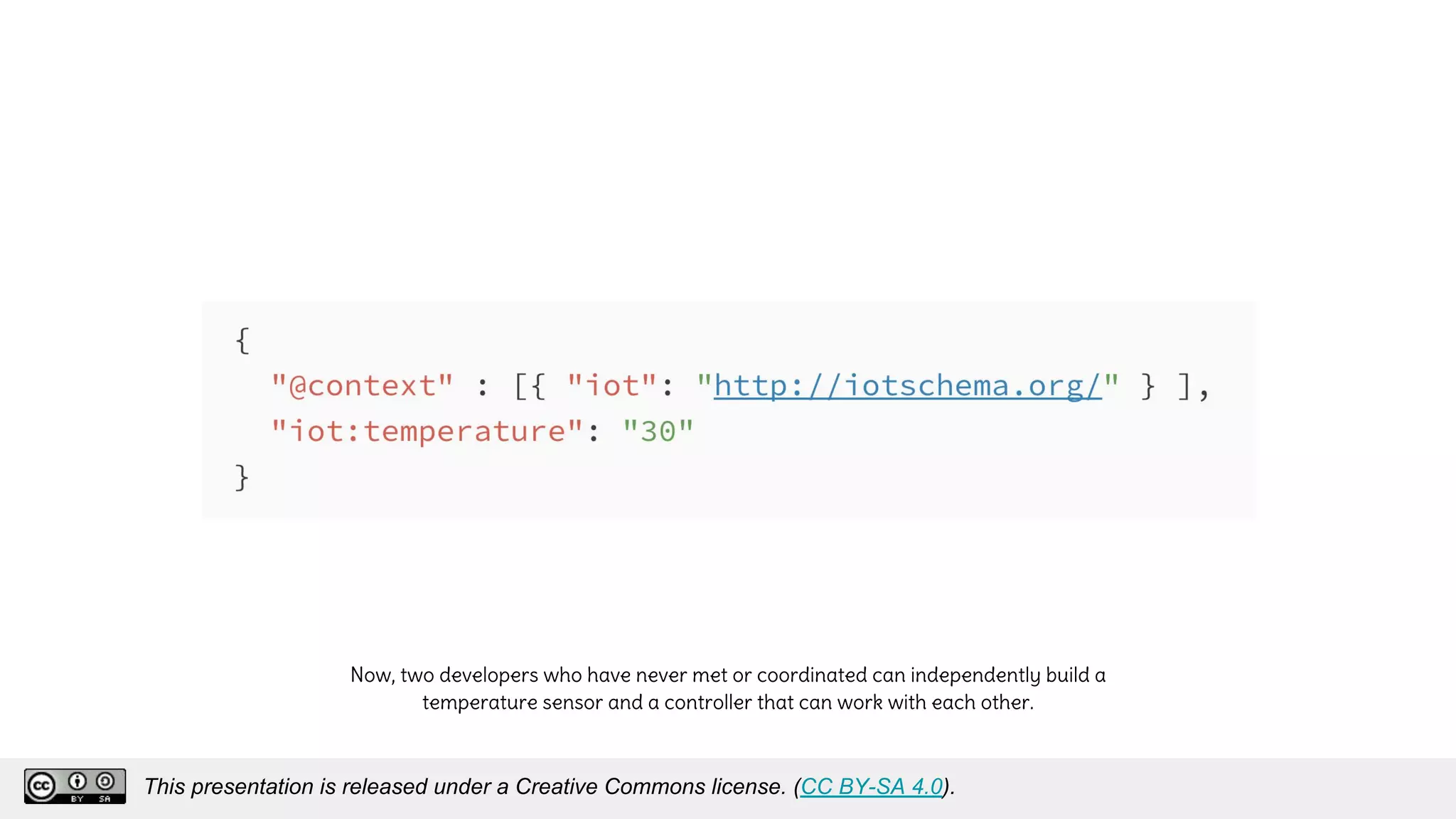
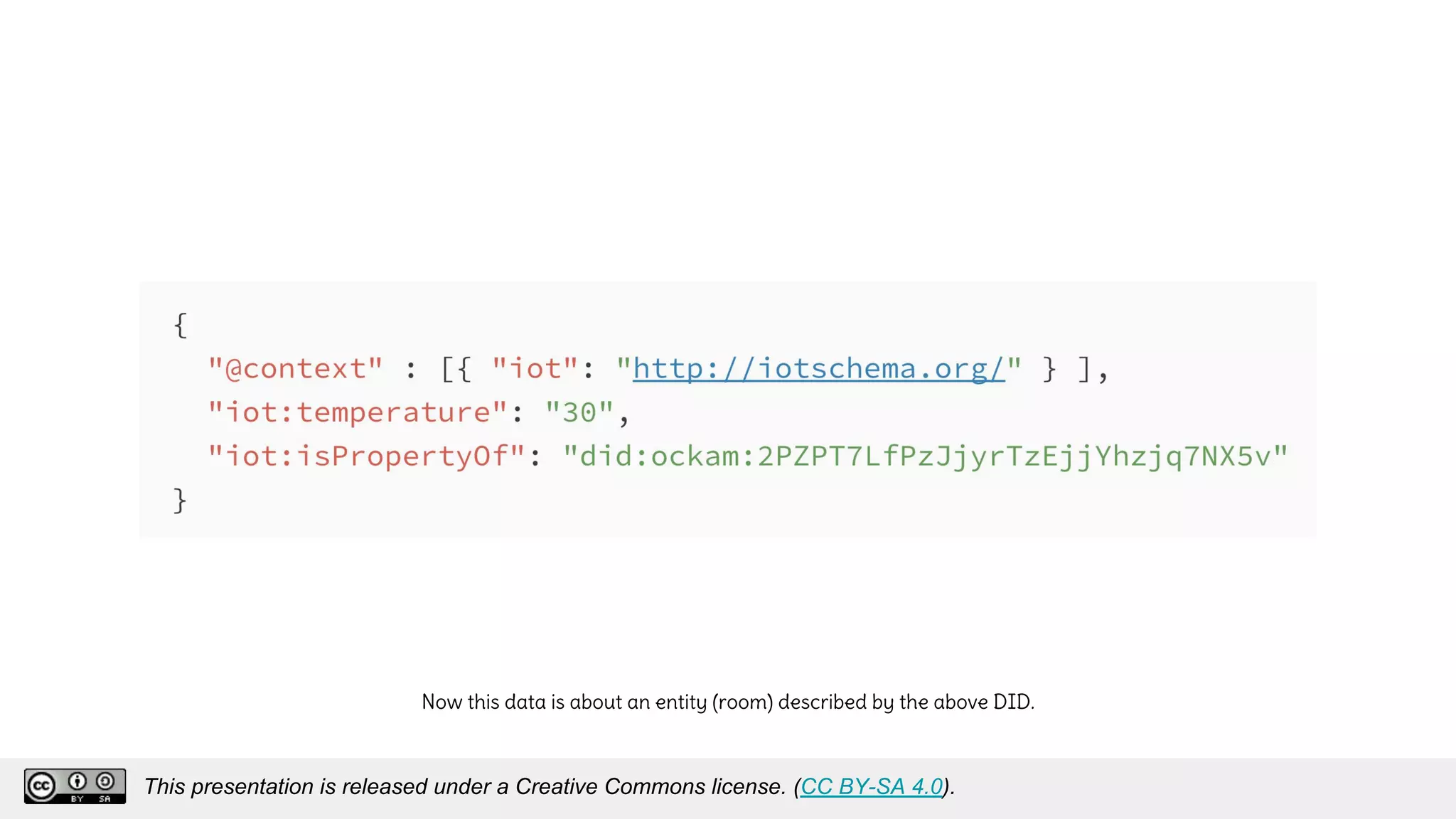
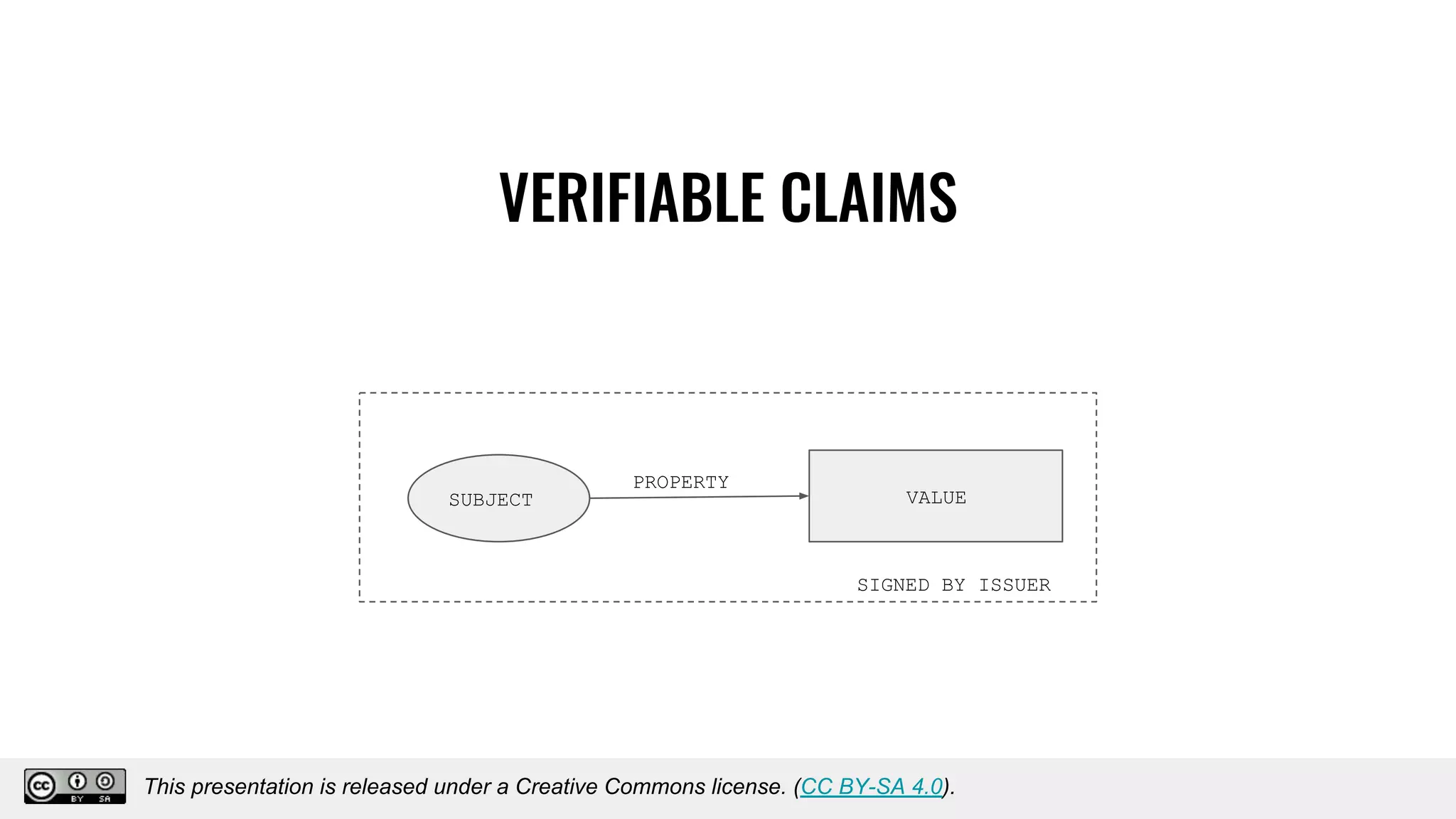
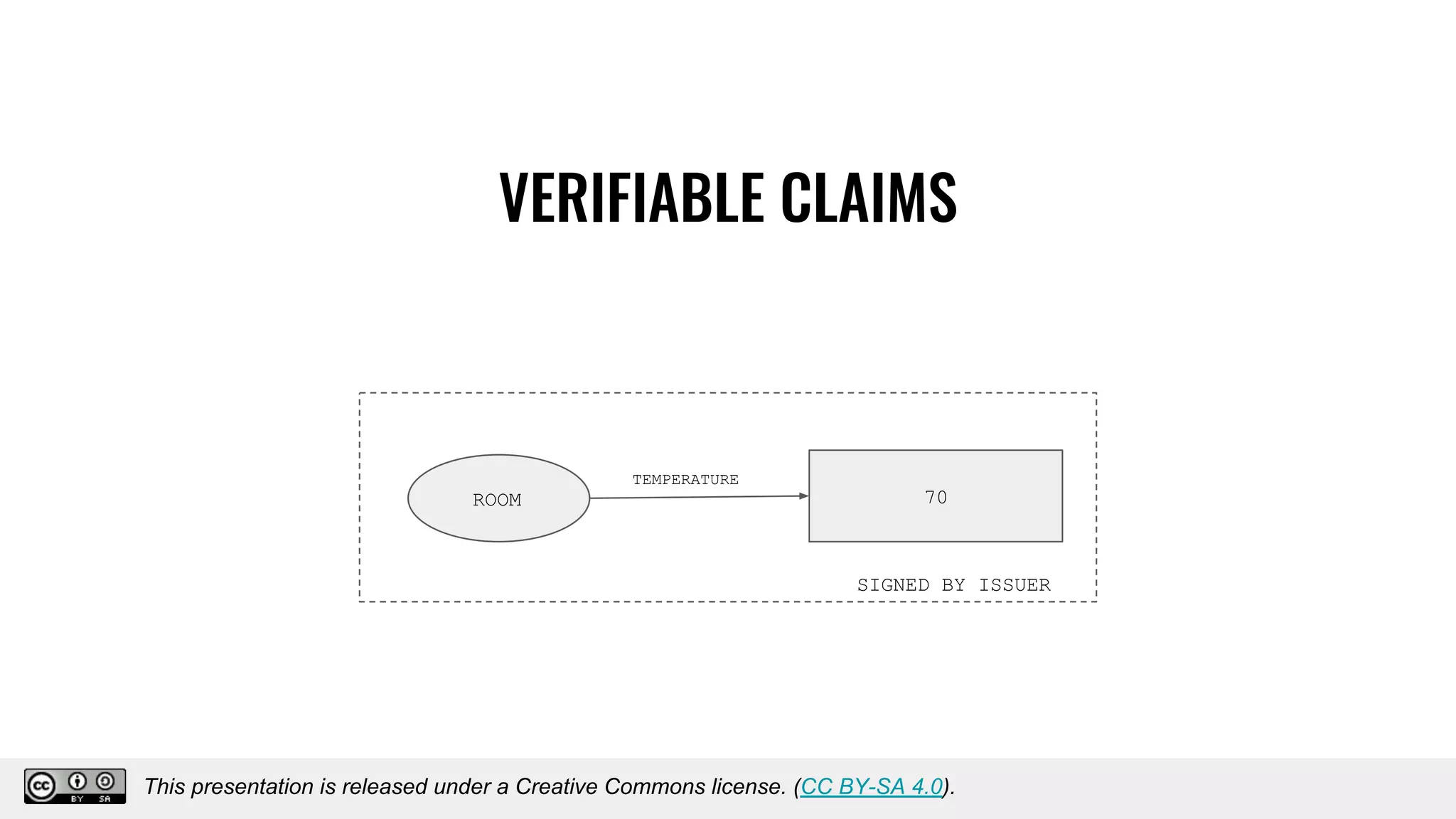
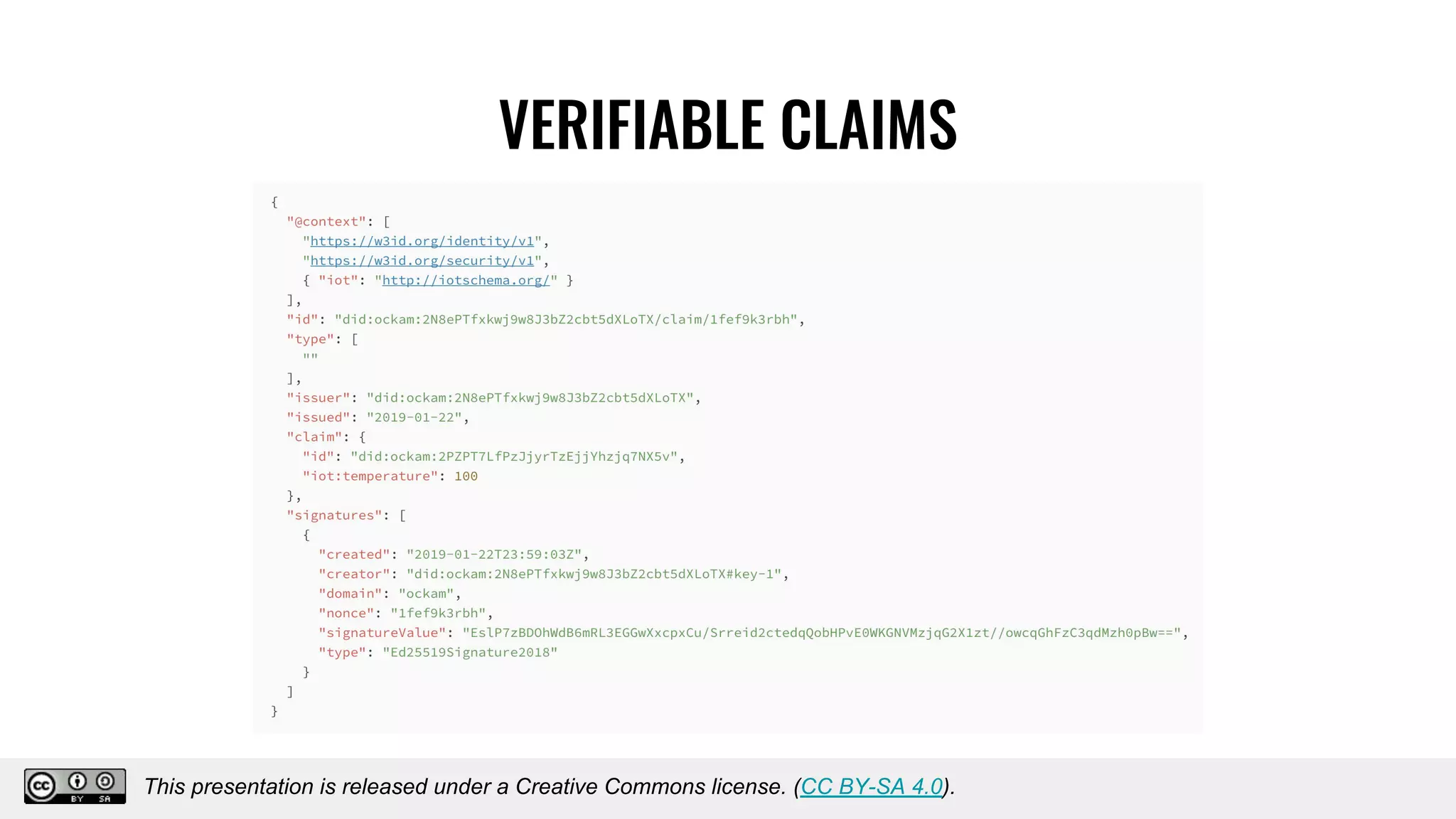
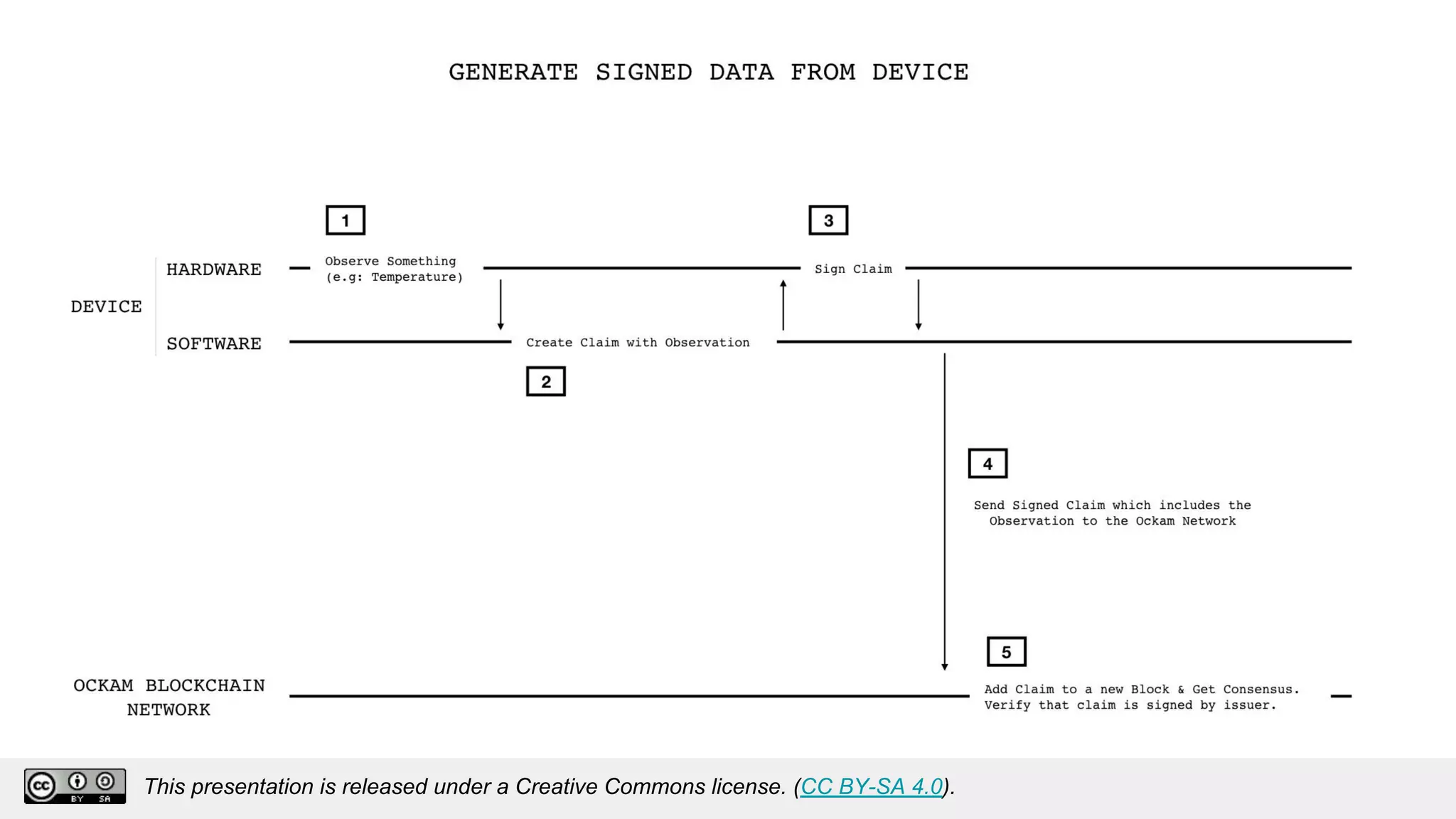
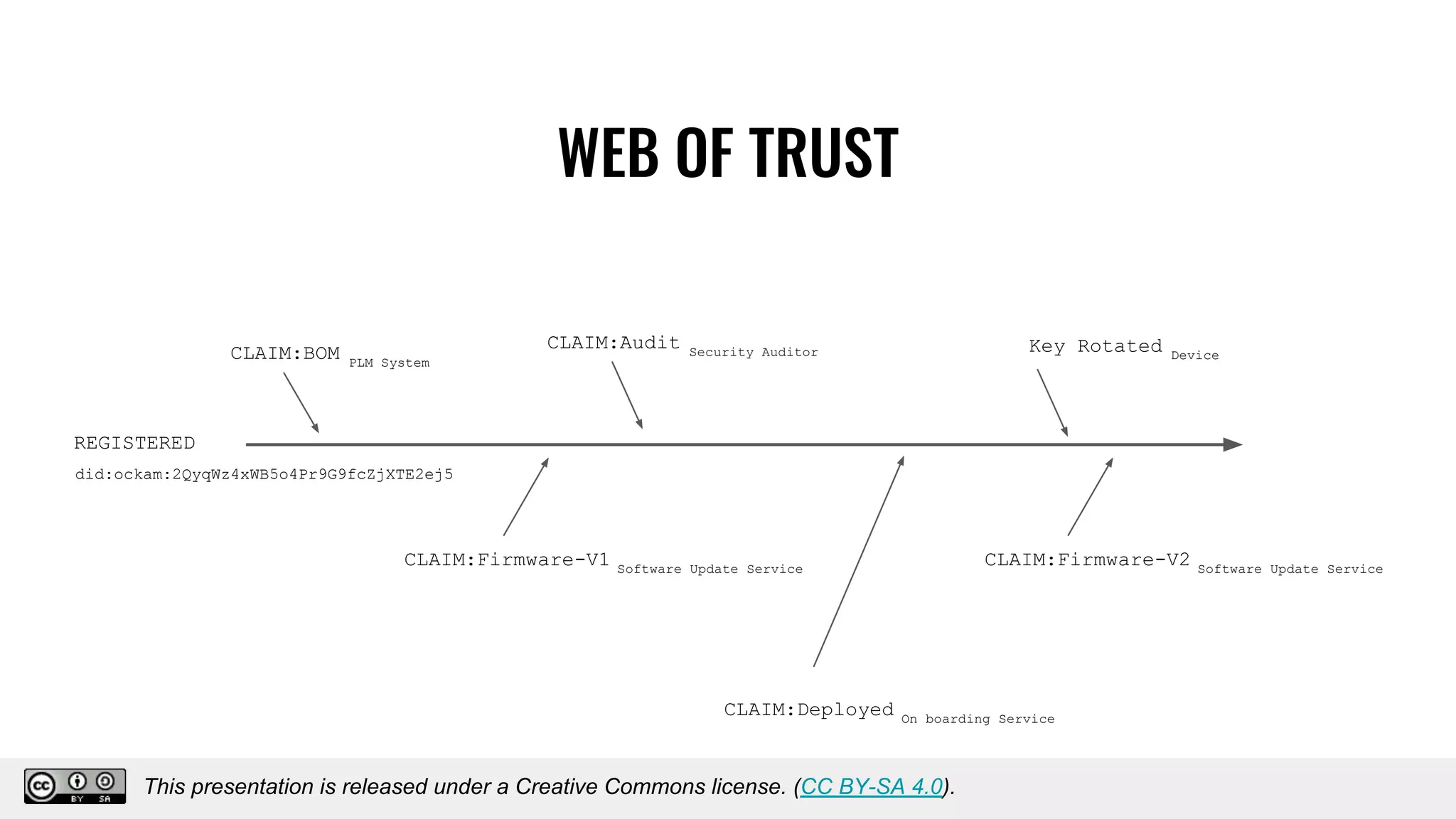
The document discusses using decentralized identifiers (DIDs) and verifiable credentials to enable trust and interoperability in the Internet of Things (IoT). It describes how traditional IoT systems face challenges with identity, authentication, authorization, and interoperability due to fragmented identification schemes. The presentation introduces DIDs as a new type of identifier that allows entities to prove control over digital identities. It also discusses how verifiable credentials and decentralized key management can improve trustworthiness for IoT devices and systems. The goal is to establish a common foundation for identity to simplify development of autonomous systems using connected devices and machines.