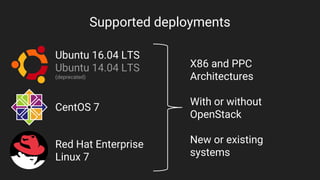
The document discusses the complexities of securing OpenStack clouds and introduces the openstack-ansible-security role, which automates industry-standard security hardening while minimizing disruptions. It details the integration of security guidelines from the Defense Information Systems Agency (DISA) into Ansible for effective security management across various Linux distributions. The role's features include configurability, zero disruptions, and compatibility with both new and existing systems.