The document provides a guide on deploying and optimizing open source web application firewalls (WAFs) like ModSecurity and the OWASP Core Rule Set (CRS). It outlines installation methods using package managers, Docker, and Ansible, as well as optimization strategies to improve performance and reduce processing costs. Key recommendations include logging efficiency, minimizing active rules, and managing request/response body access.





![Save Processing
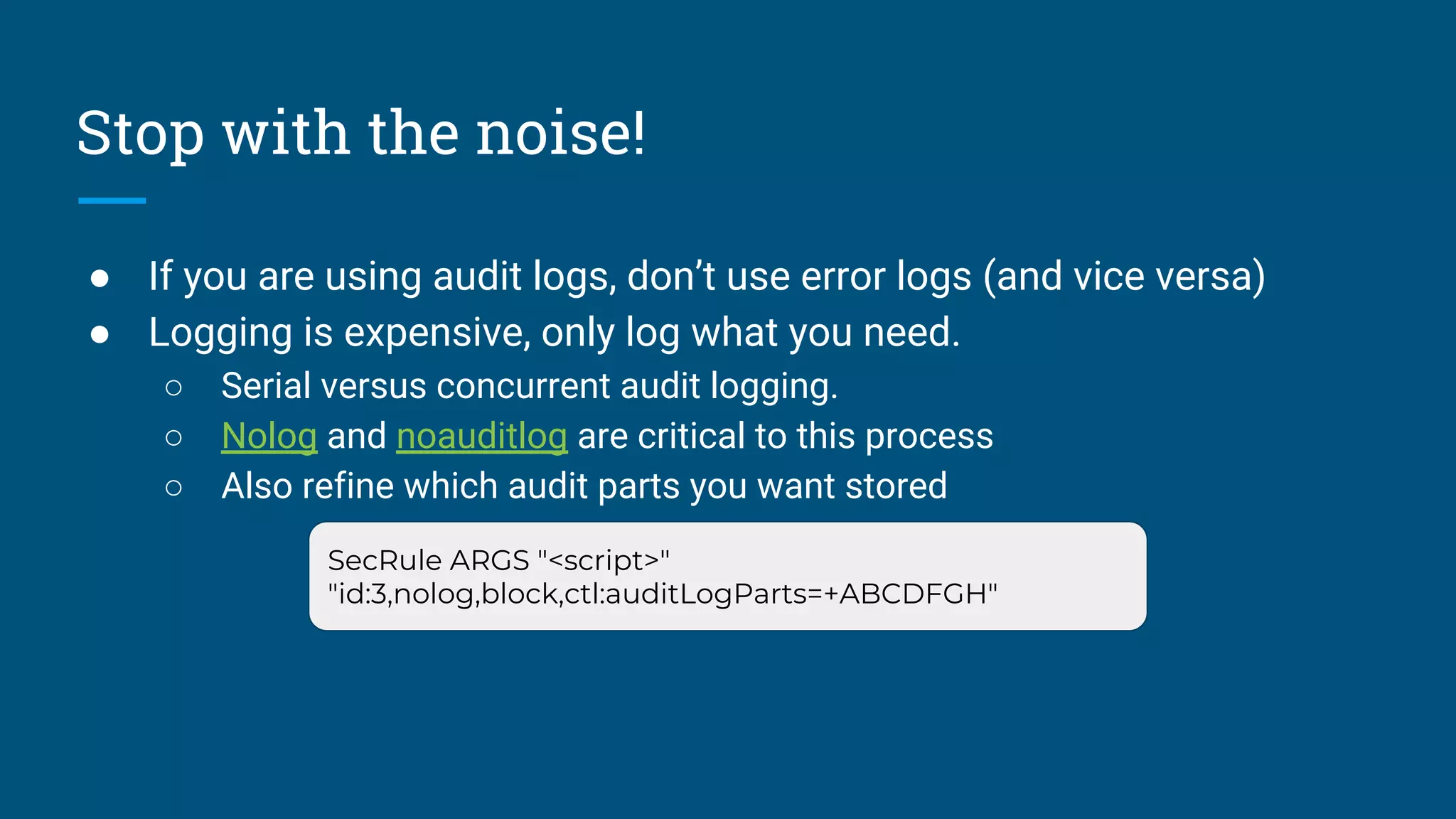
● Biggest gains come from reducing work
○ Restrict processing on content types you don’t care about.
■ SecResponseBodyMimeType
■ X
● Place the WAF where it doesn’t need to recreate the wheel
○ At or after the TLS termination proxy is a good place.
● Remove processors you don’t need or use (JSON/XML)
SecRule REQUEST_BASENAME ".*?(.[a-z0-9]{1,10})?$" "id:123, t:lowercase,
capture.setvar:tx.extension=/%{TX.1}/, chain,nolog, allow"
SecRule TX:EXTENSION "!@within %{tx.static_extensions}" "t:none"](https://image.slidesharecdn.com/chaimsanderseasilydeployingandoptimizingopensourcewebapplicationfirewalls-180419201324/75/BSides-Rochester-2018-Chaim-Sanders-Easily-Deploying-and-Optimizing-Open-Source-Web-Application-Firewalls-9-2048.jpg)