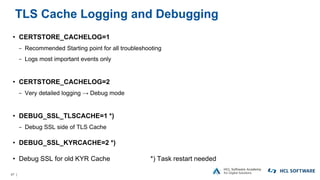
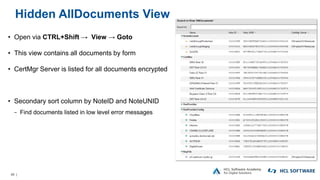
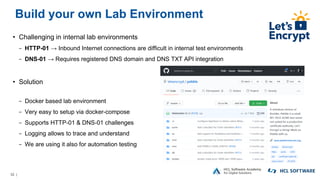
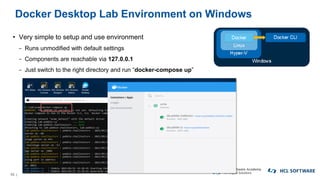
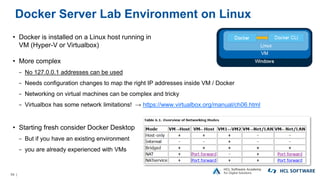
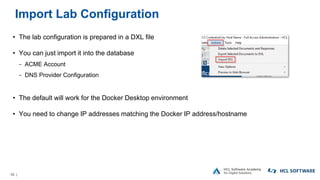
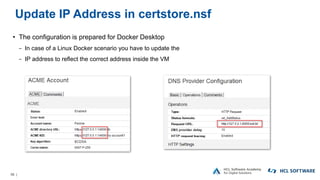
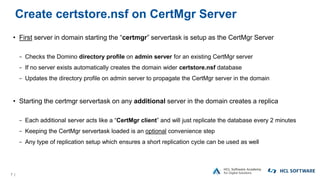
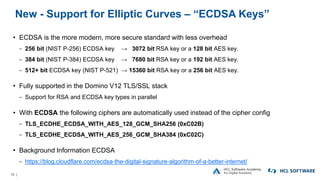
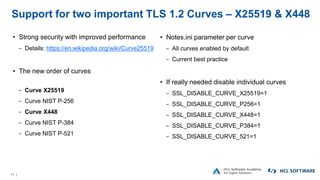
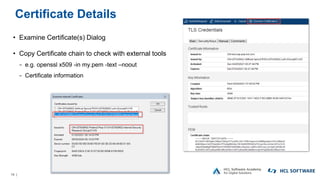
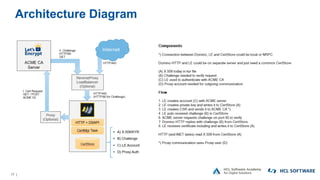
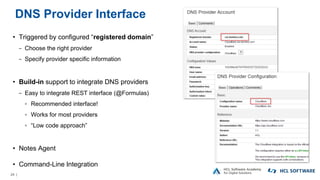
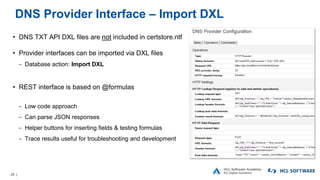
The OpenNTF webinar focused on the Domino v12 Certification Manager, presenting its features like automated certificate management and an integrated certstore.nsf for secure TLS credential handling. The new system simplifies certificate management for users, replacing complex formats with standard ones, and includes enhanced support for modern cryptographic standards, including elliptic curve cryptography. Participants were encouraged to engage with the community through various projects and provided channels for questions and future webinars.



































![46 |
Debugging and Troubleshooting Command Line
• -v = Verbose logging (log.nsf)
• -d = Debug mode
− IBM_TECHNICAL_SUPPORT/certmgr_debug_[..].log
• -l = Log all Curl I/O to file
− IBM_TECHNICAL_SUPPORT/certmgr_curl__[..].log
• -z = Connectivity test: Just get the ACME directory URLs and terminate
− Useful for testing internet connectivity
• Example: load certmgr -d -l](https://image.slidesharecdn.com/openntf-2021-june-210617172706/85/June-OpenNTF-Webinar-Domino-V12-Certification-Manager-52-320.jpg)