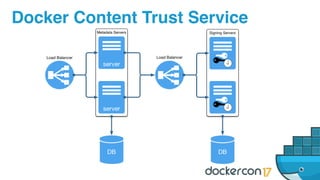
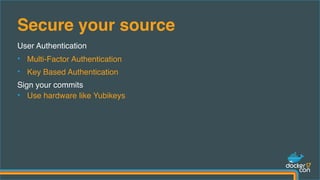
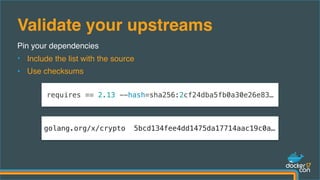
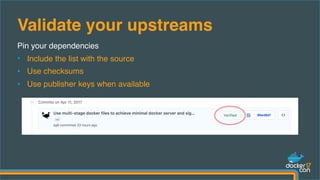
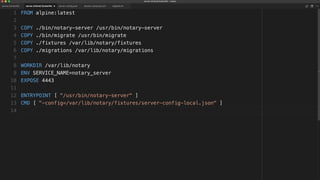
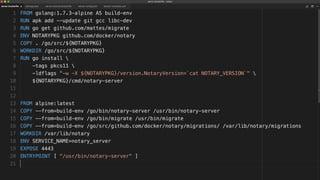
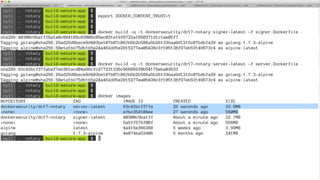
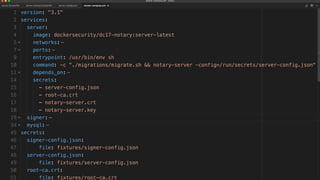
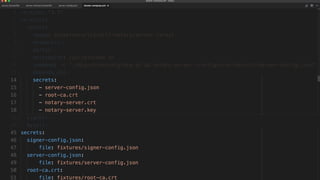
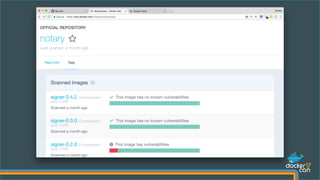
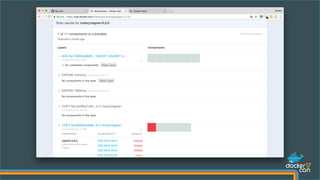
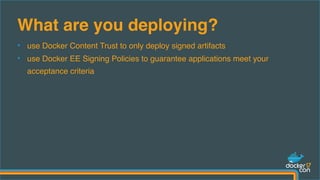
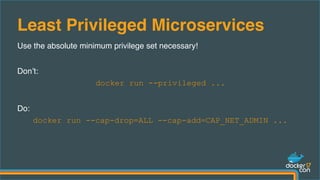
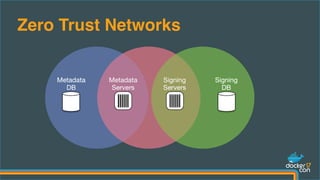
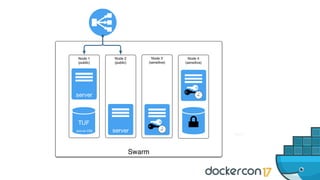
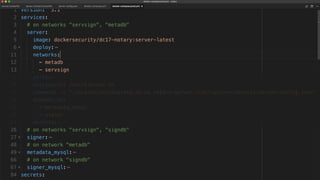
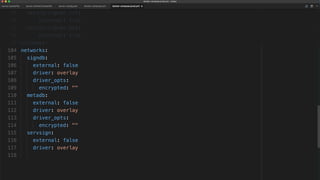
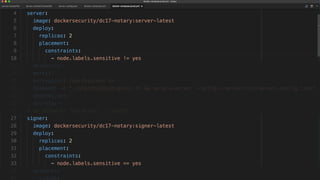
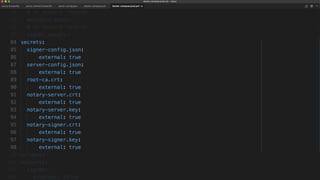
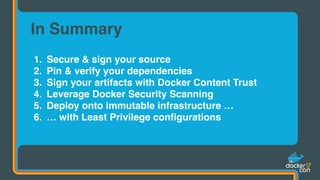
The document outlines best practices for building secure Docker applications, emphasizing the importance of user authentication, dependency management, and image signing through Docker Content Trust (DCT). It advocates for proactive security measures, such as vulnerability scanning and the use of least privilege configurations to enhance security in production environments. Key recommendations include validating upstream sources, signing artifacts, and deploying immutably to safeguard sensitive workloads.