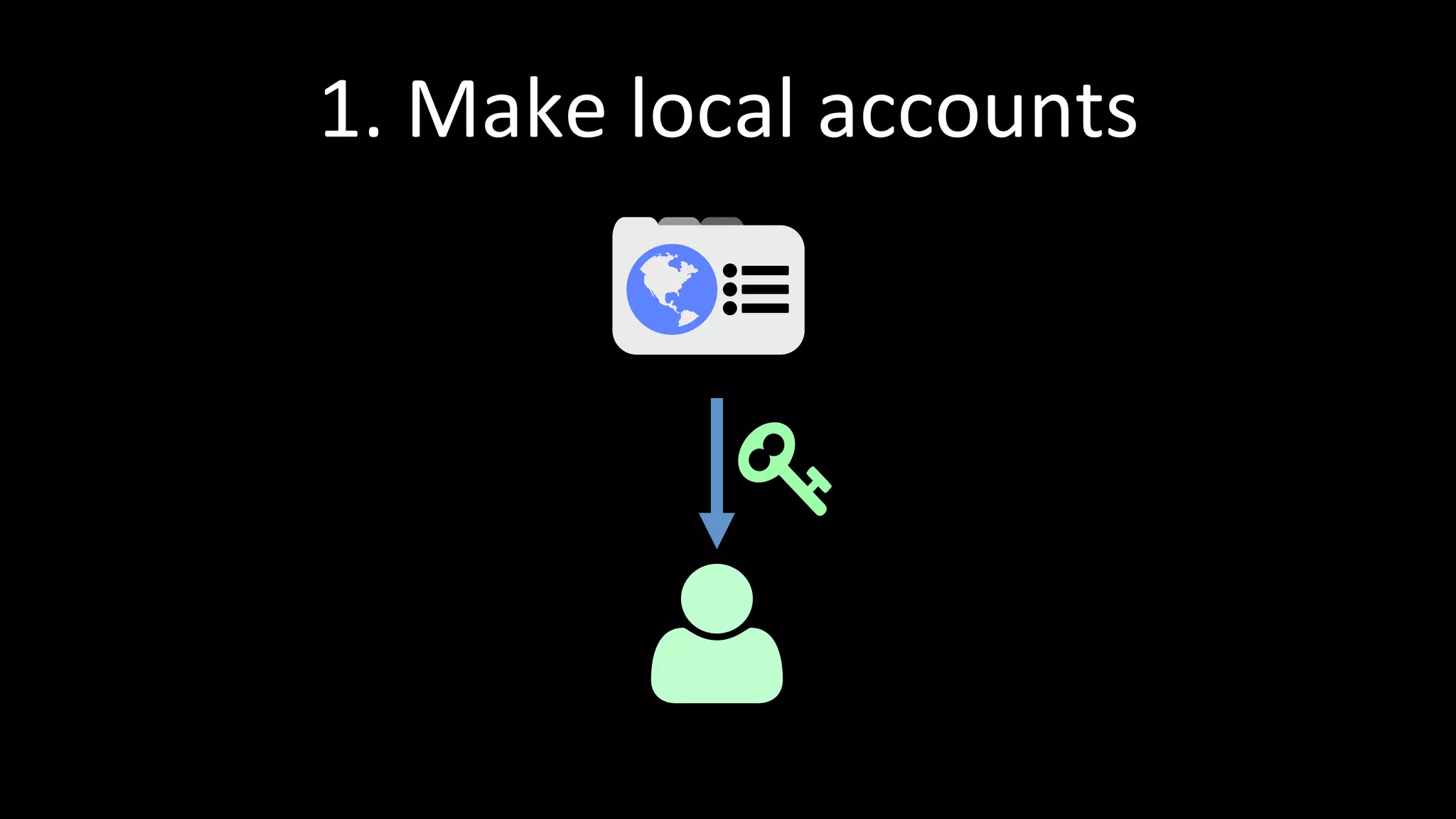
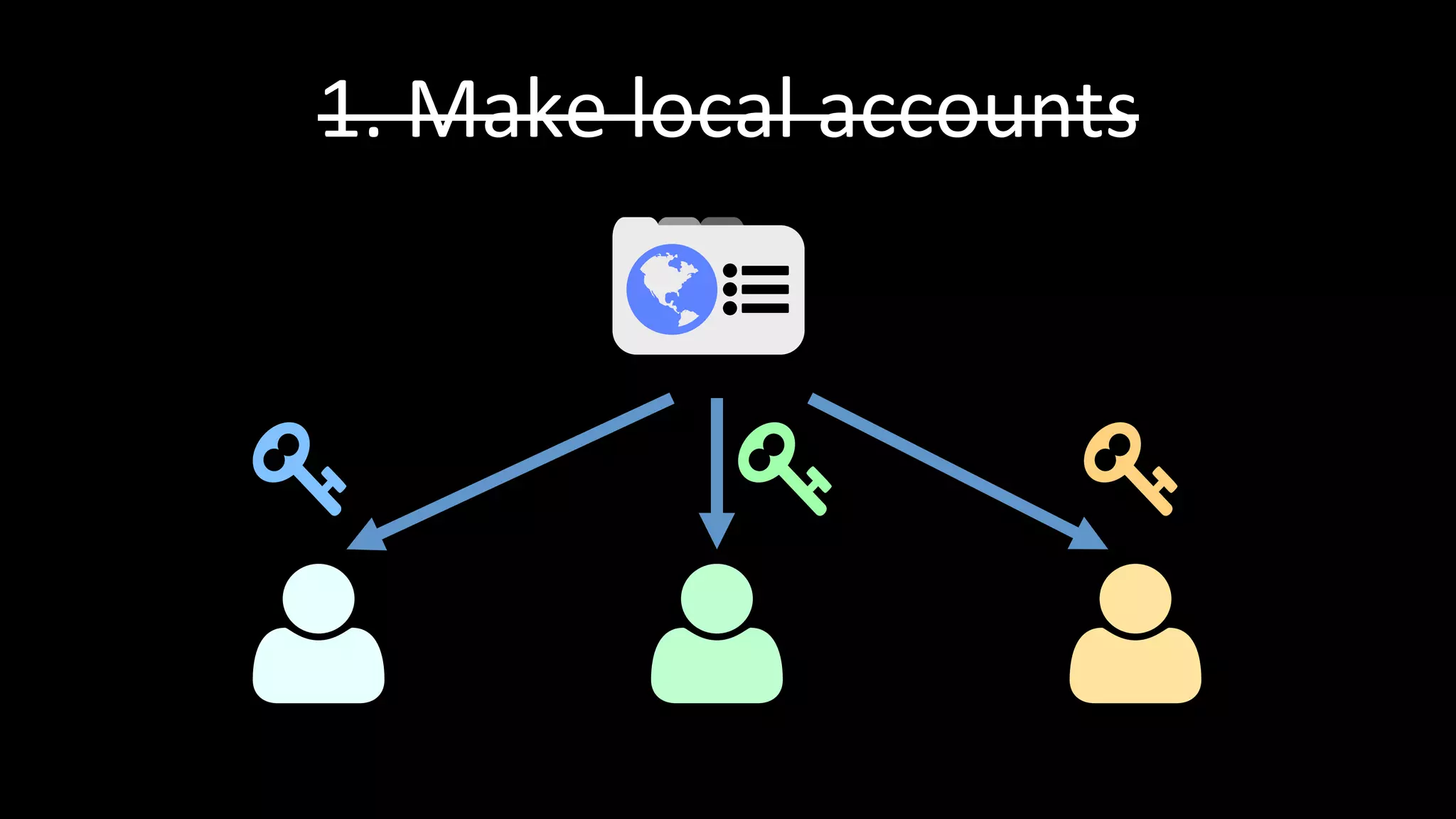
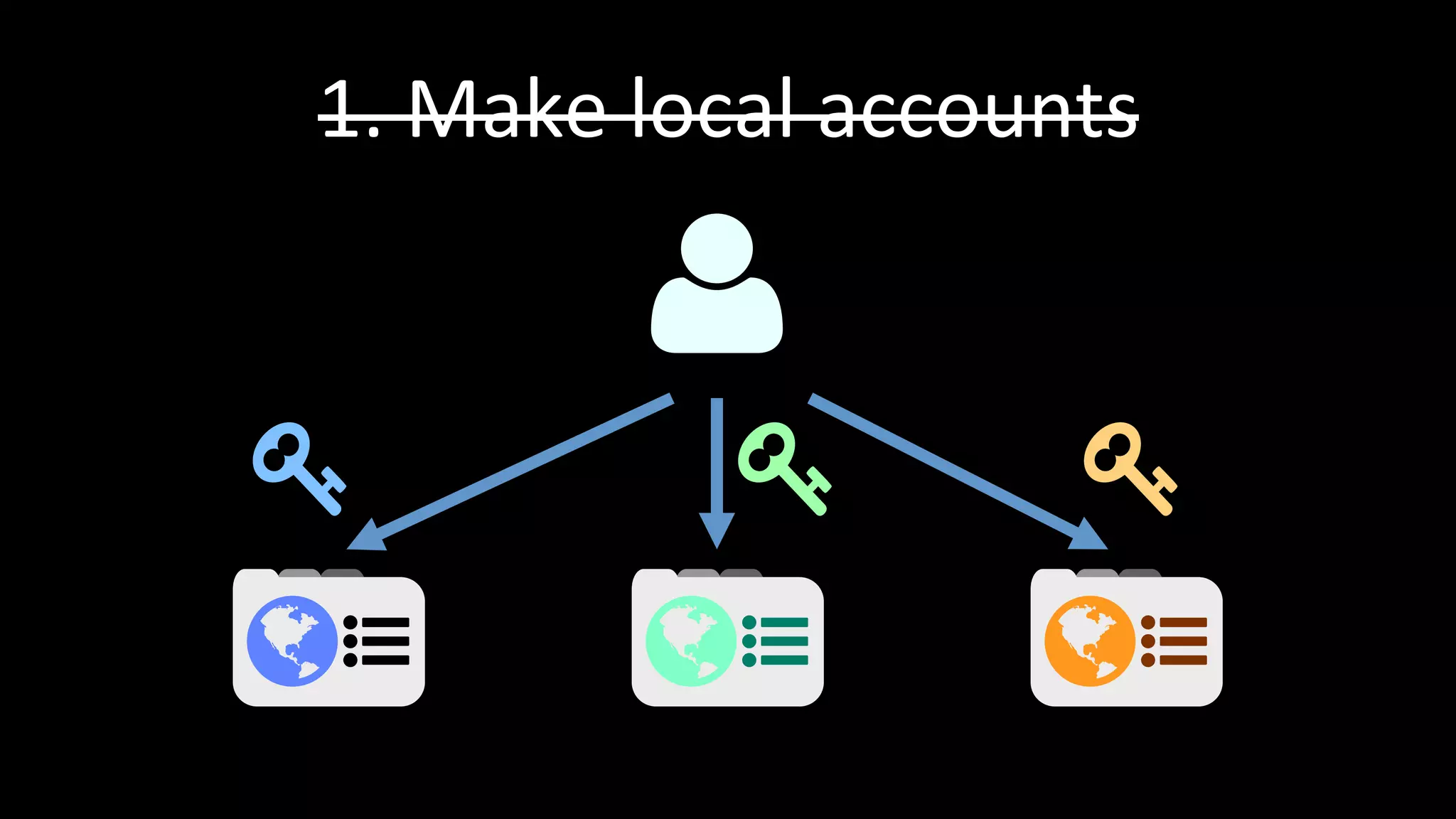
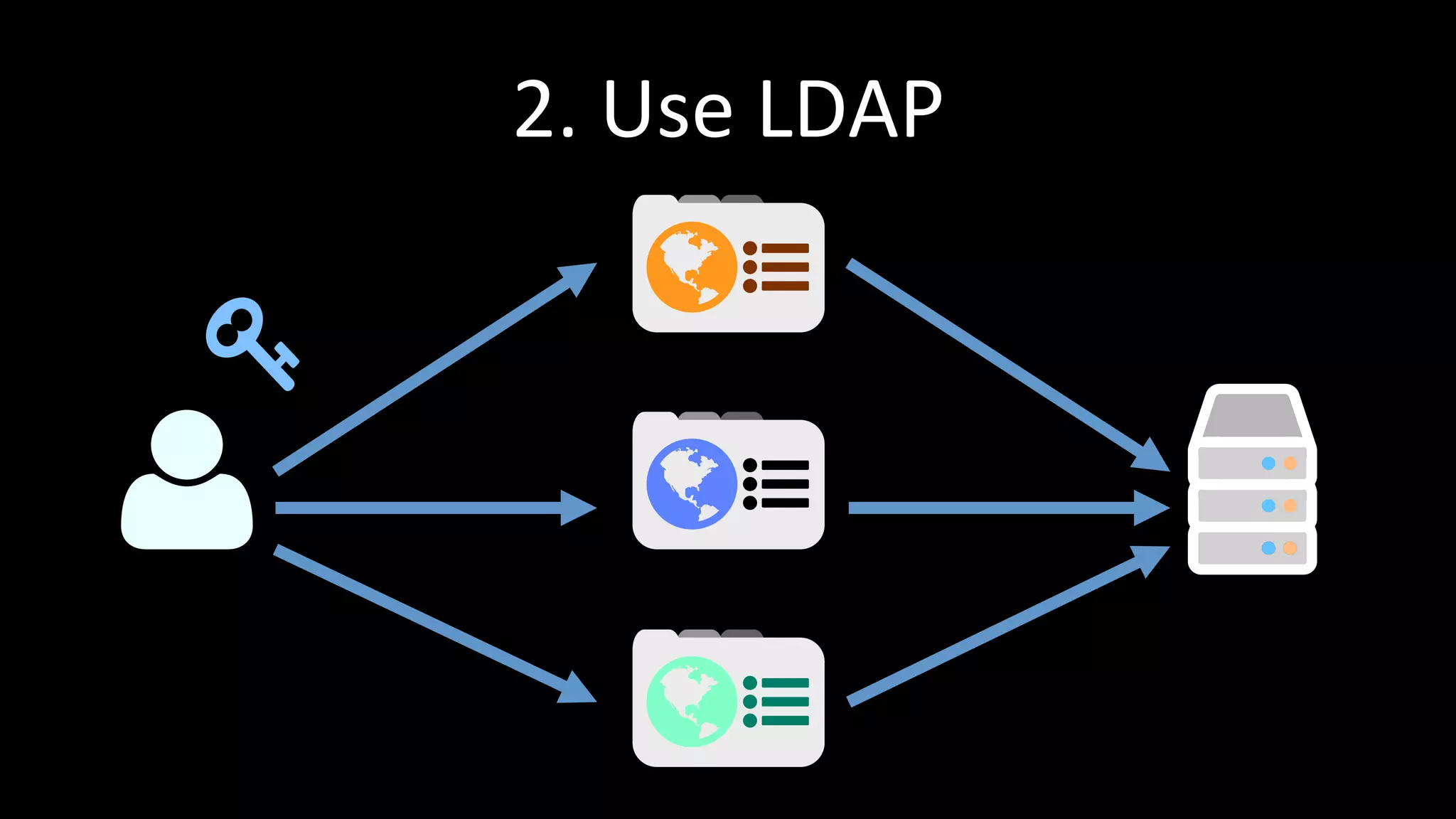
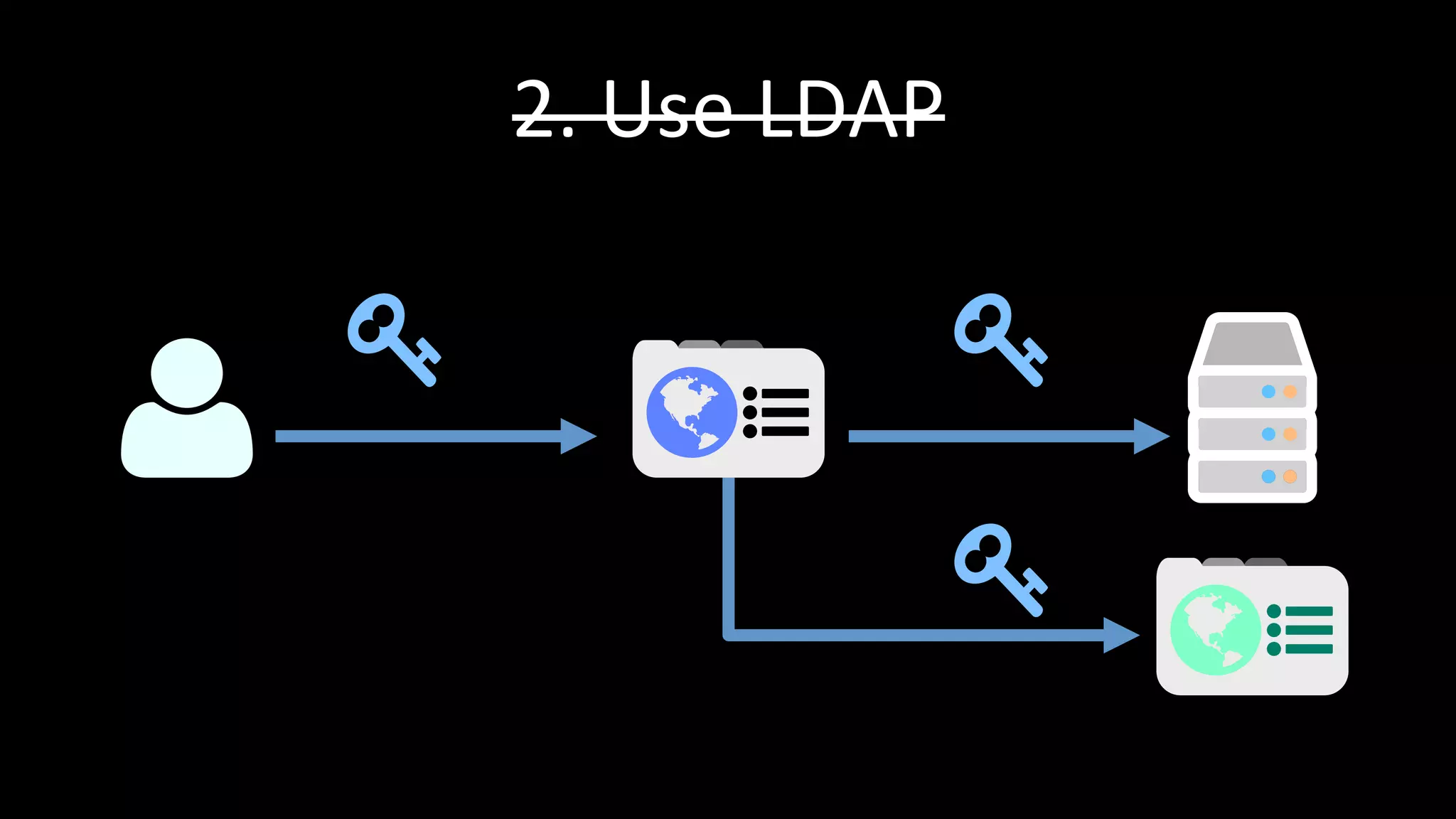
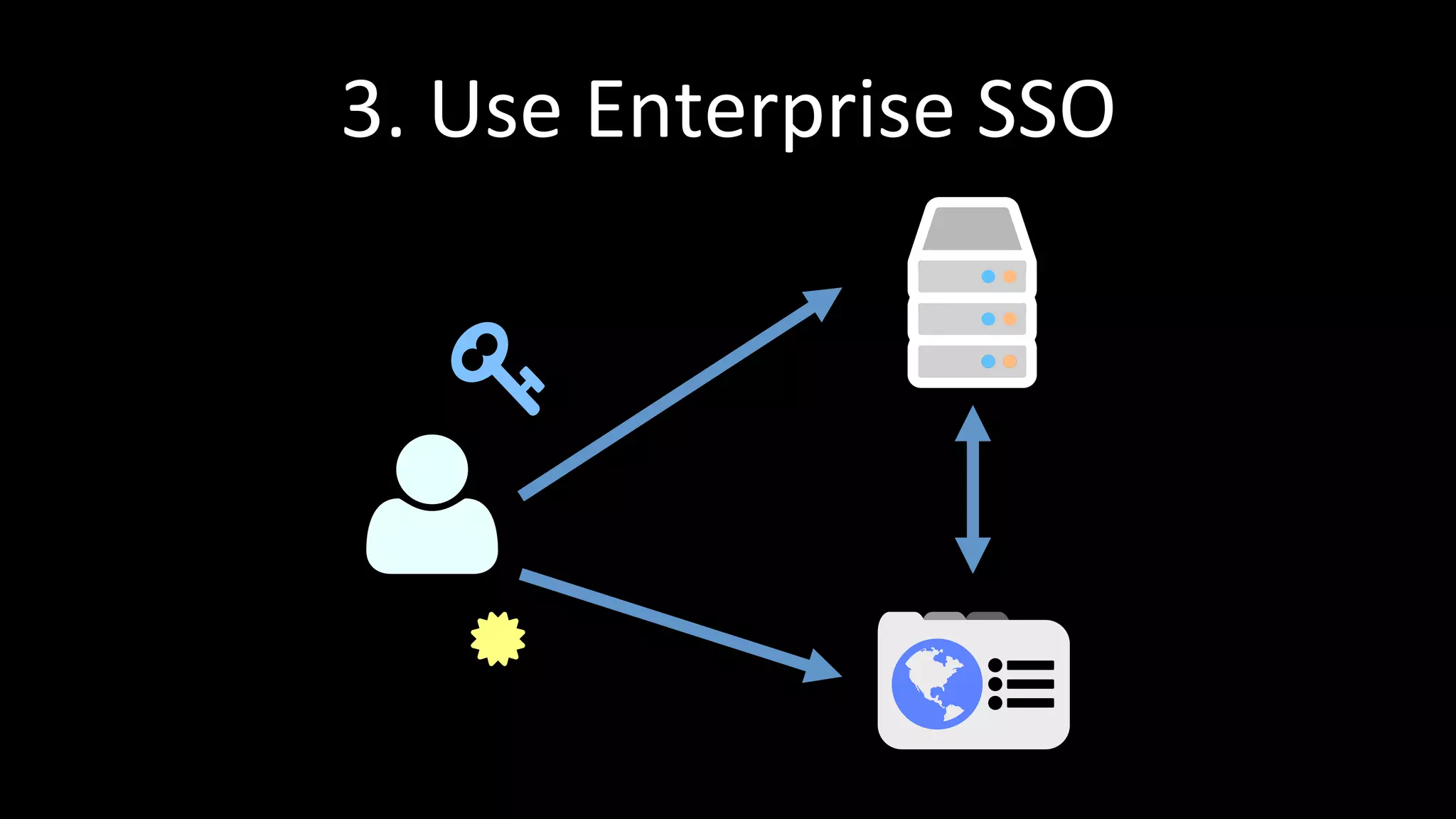
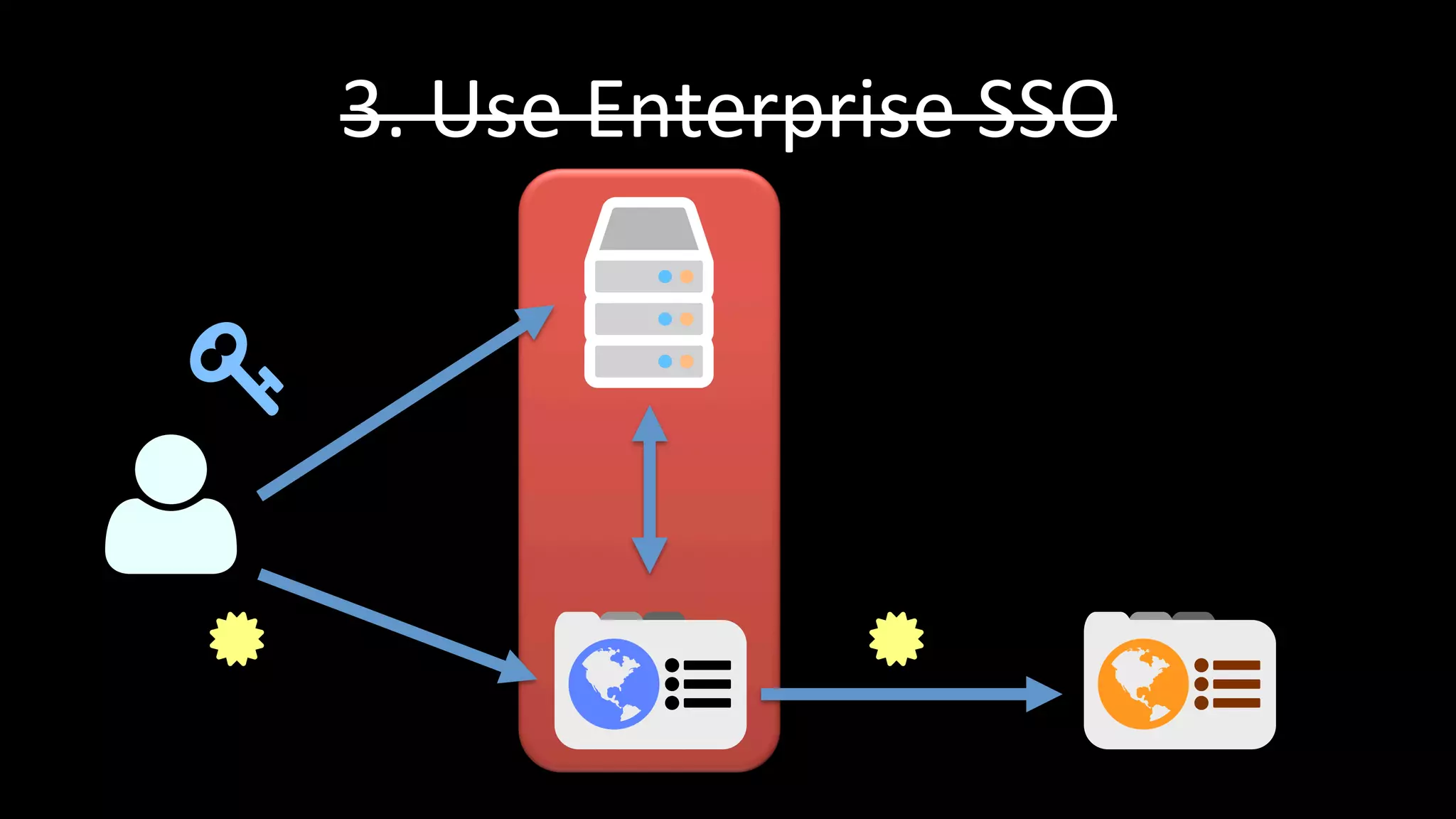
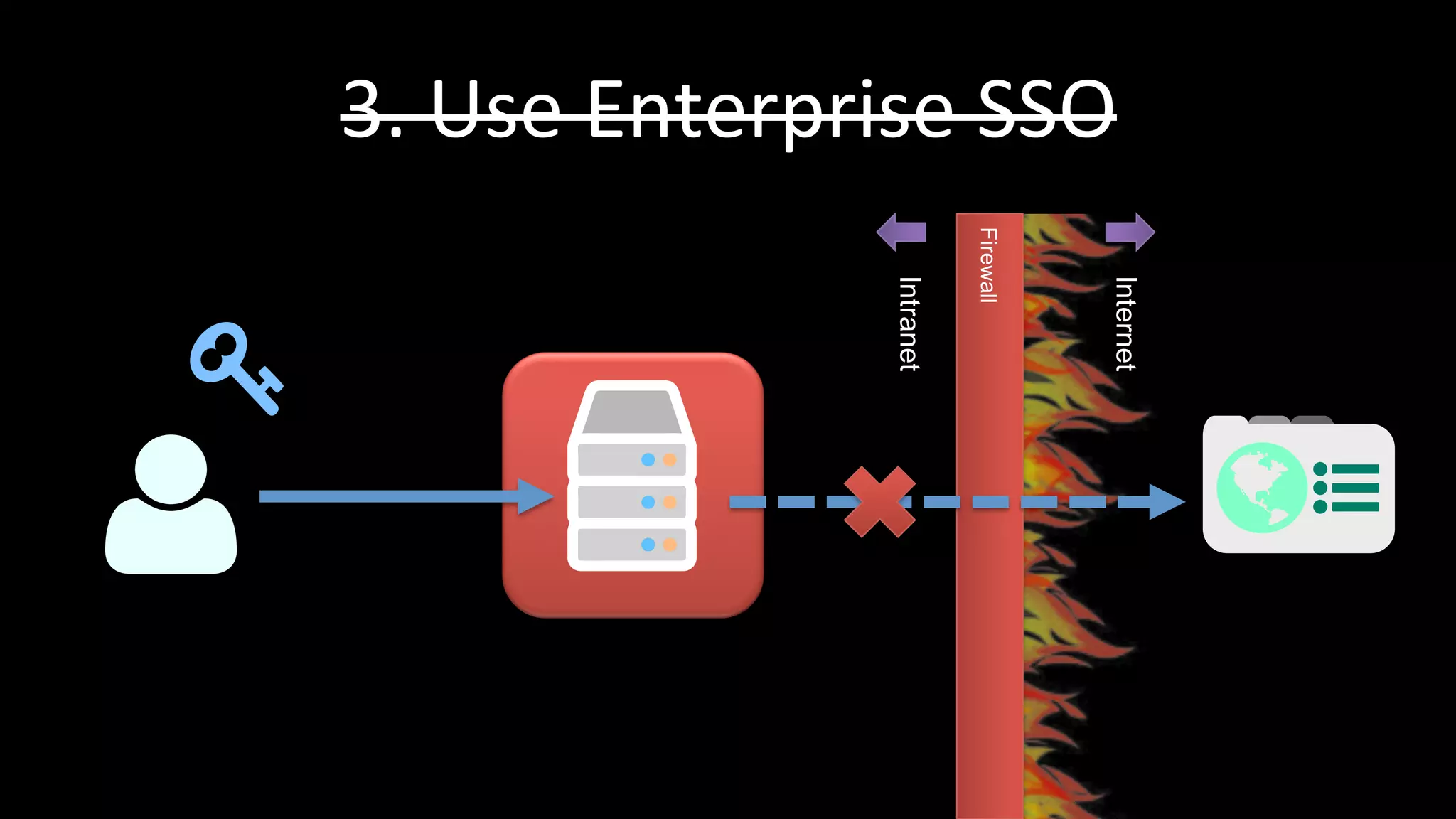
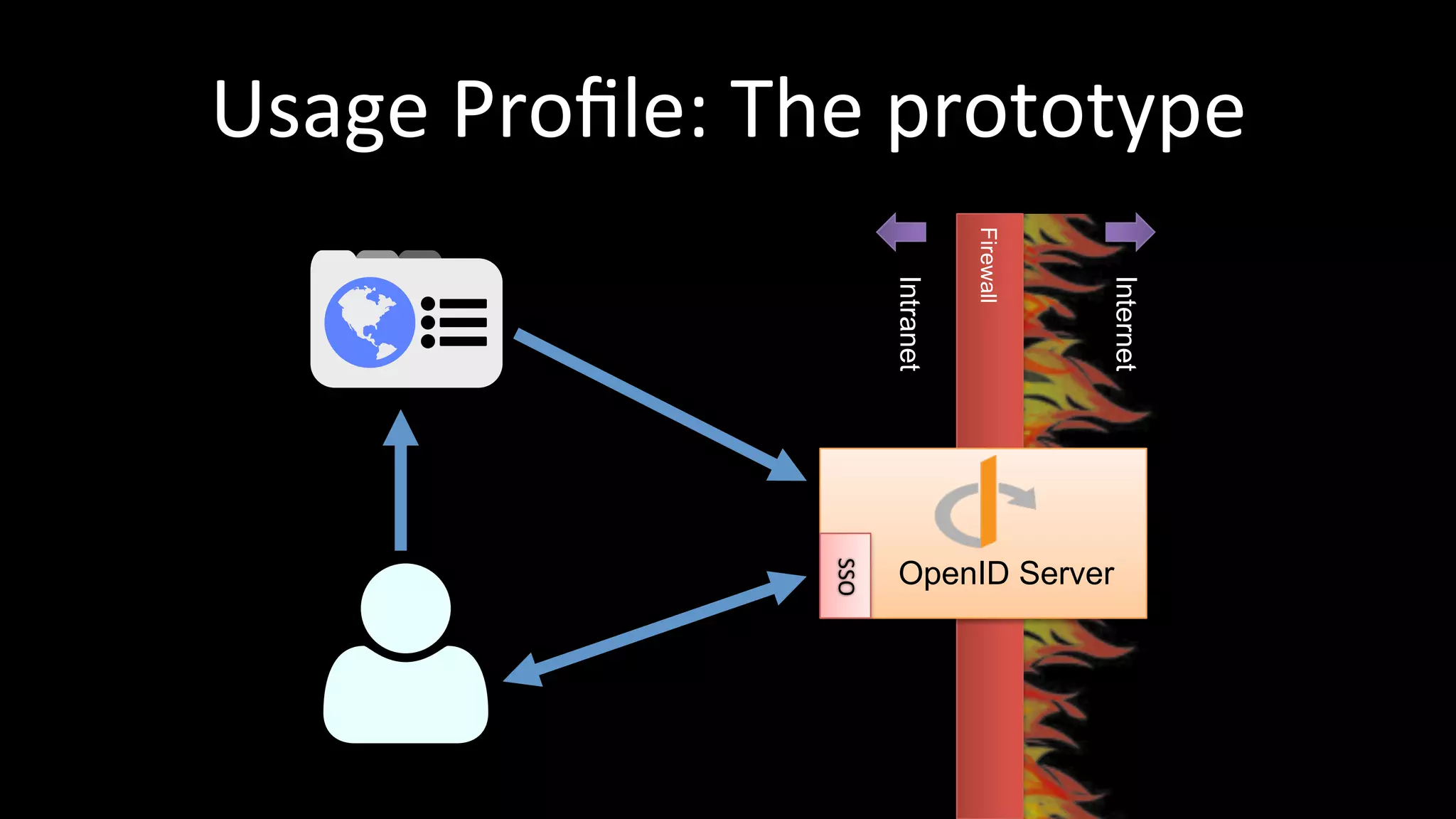
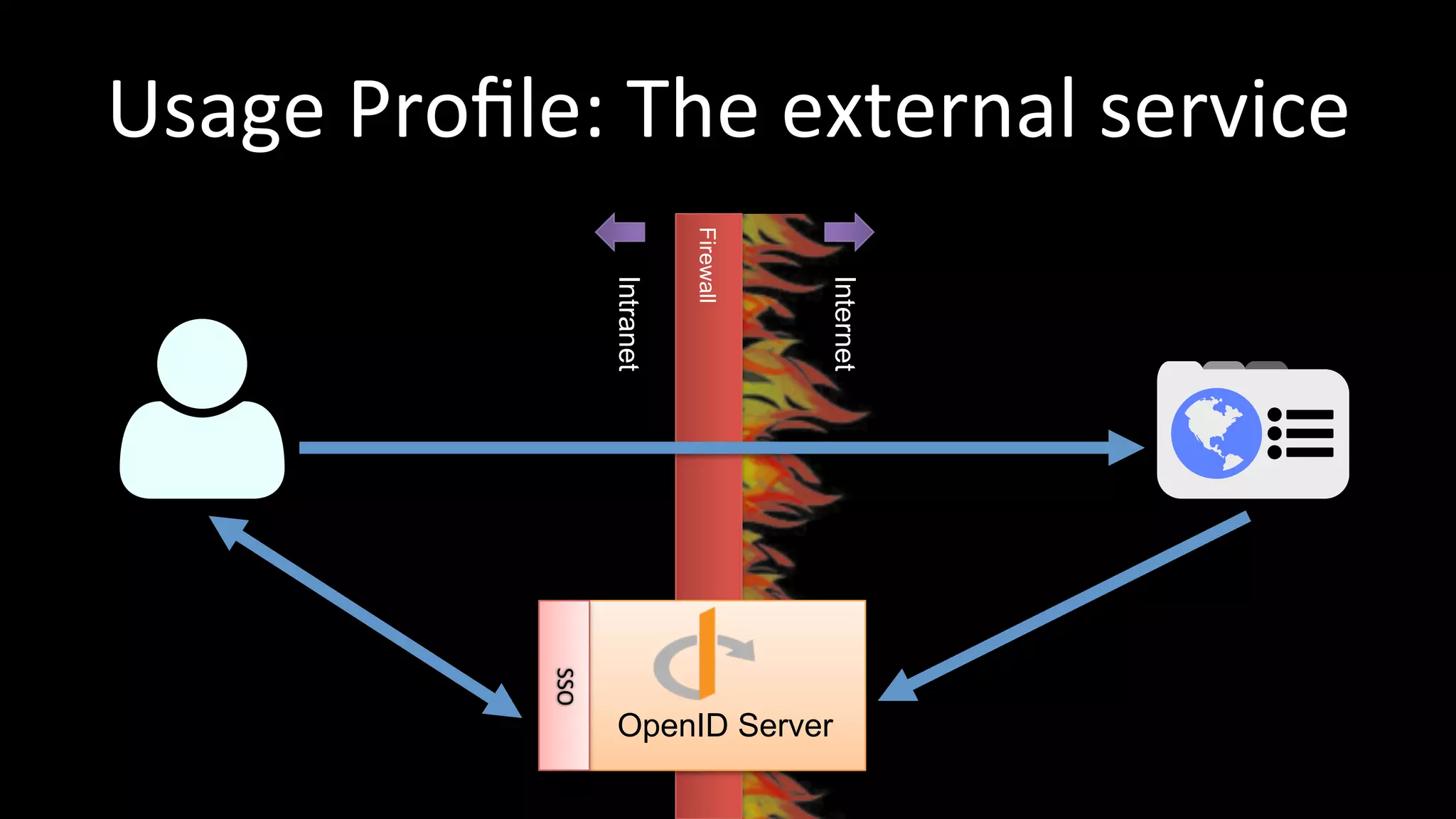
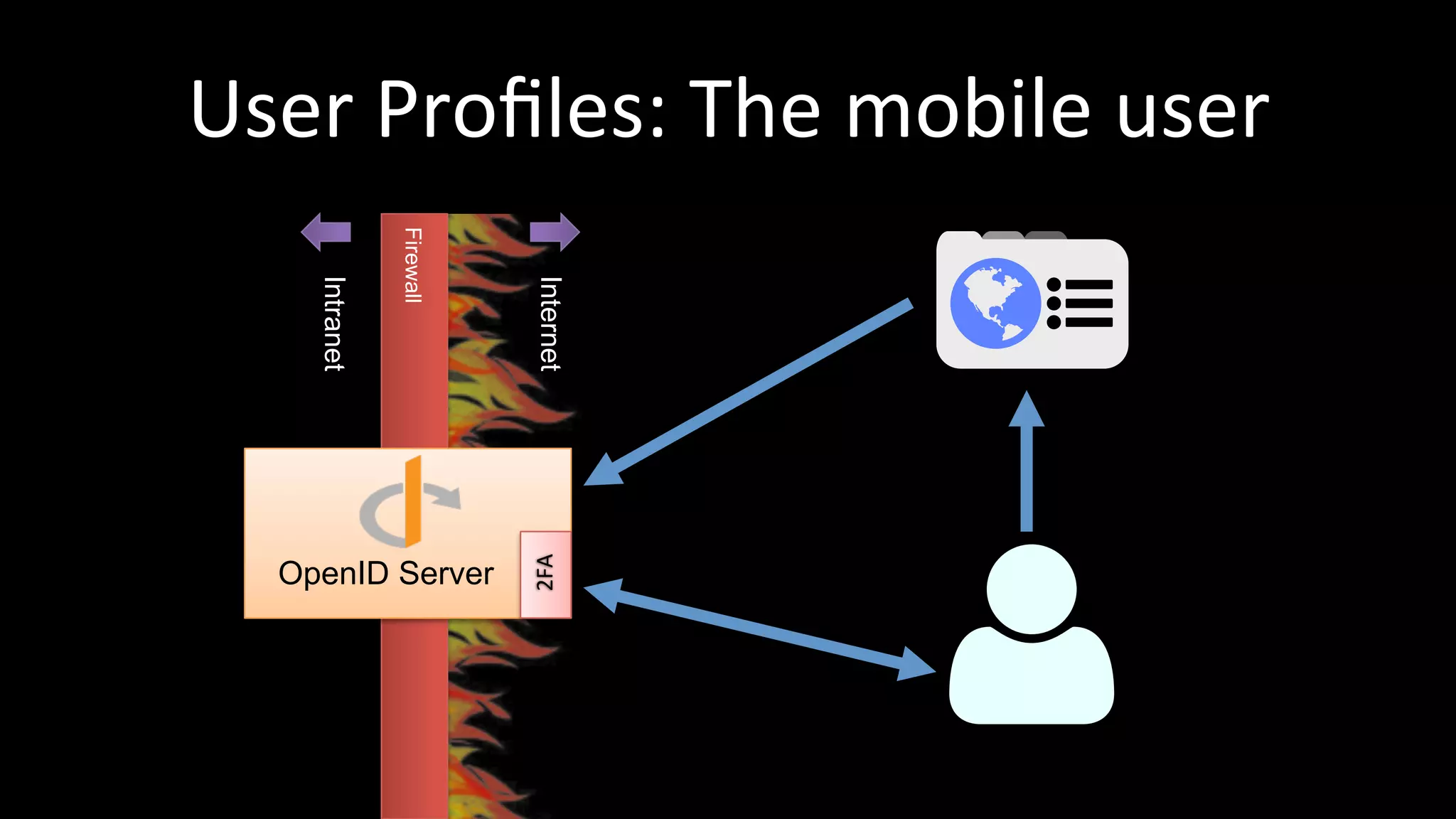
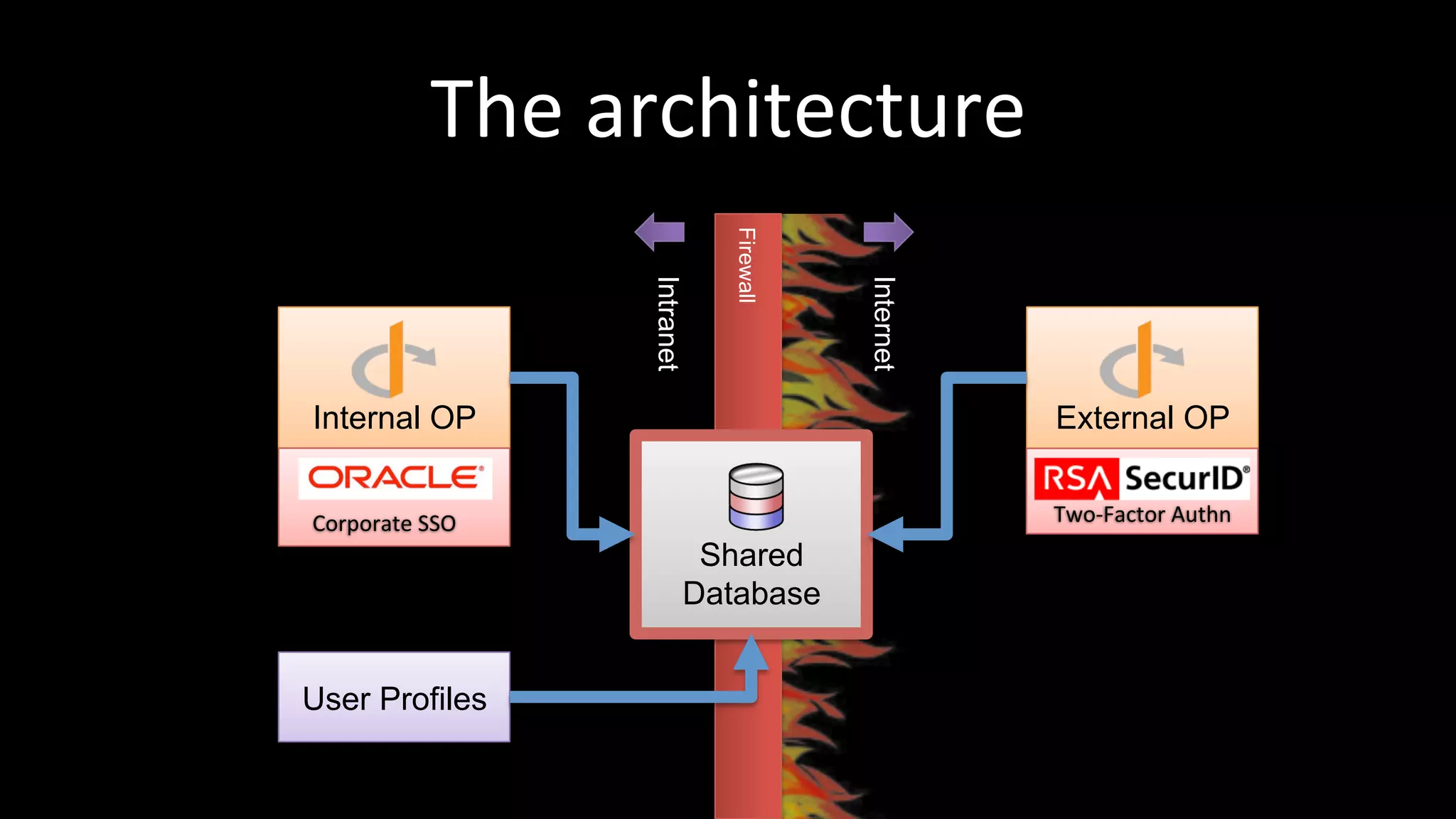
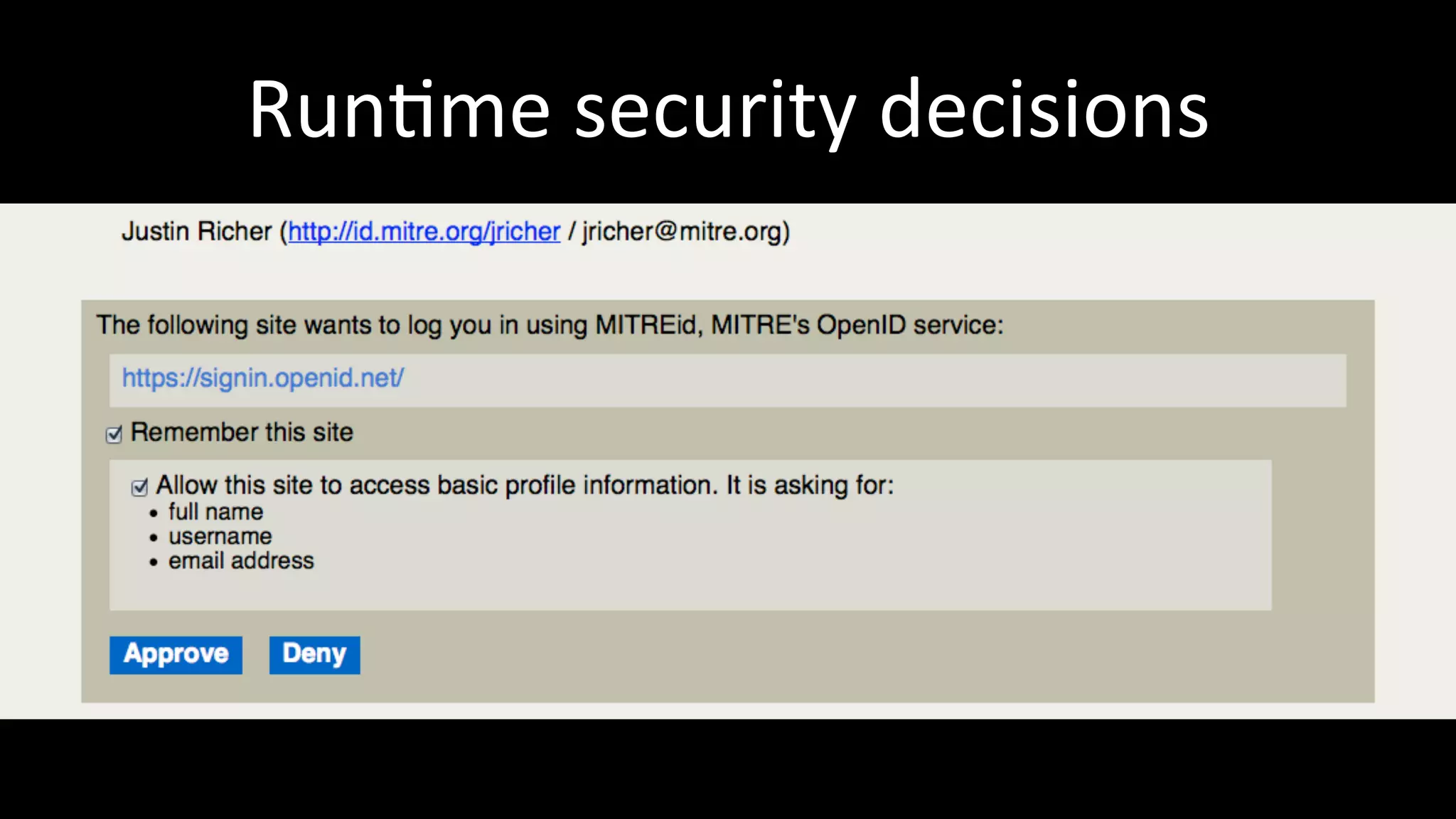
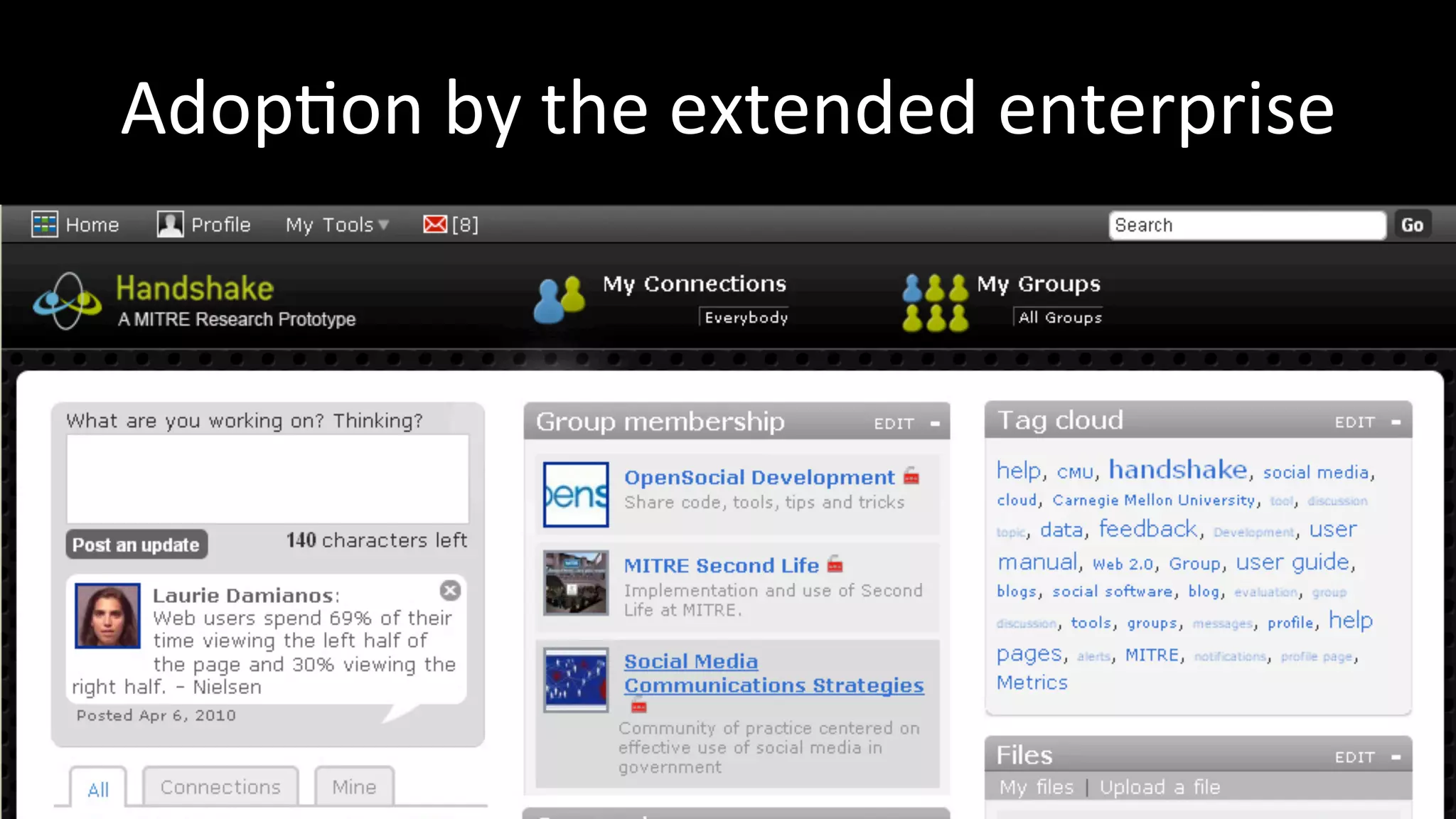
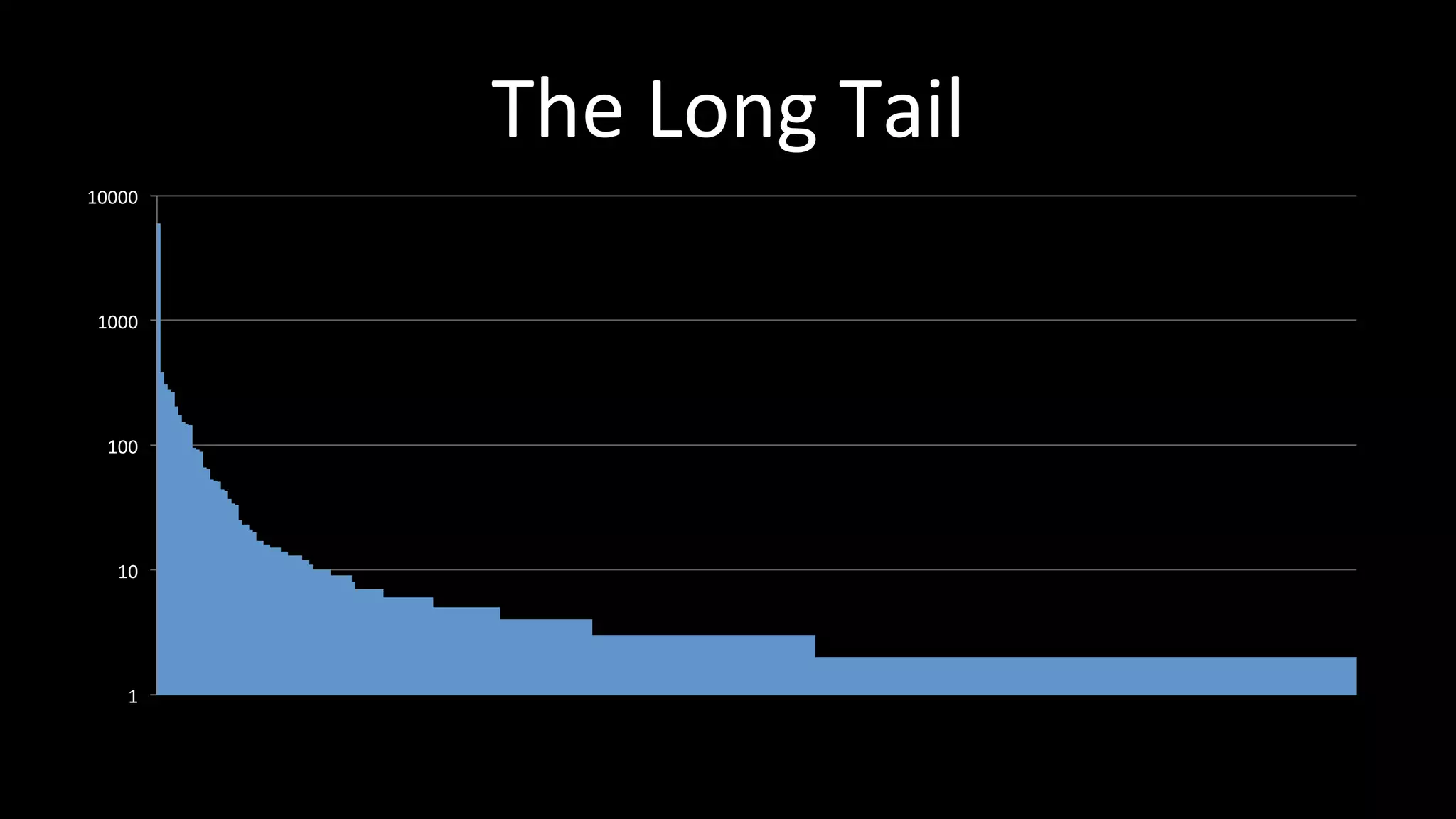
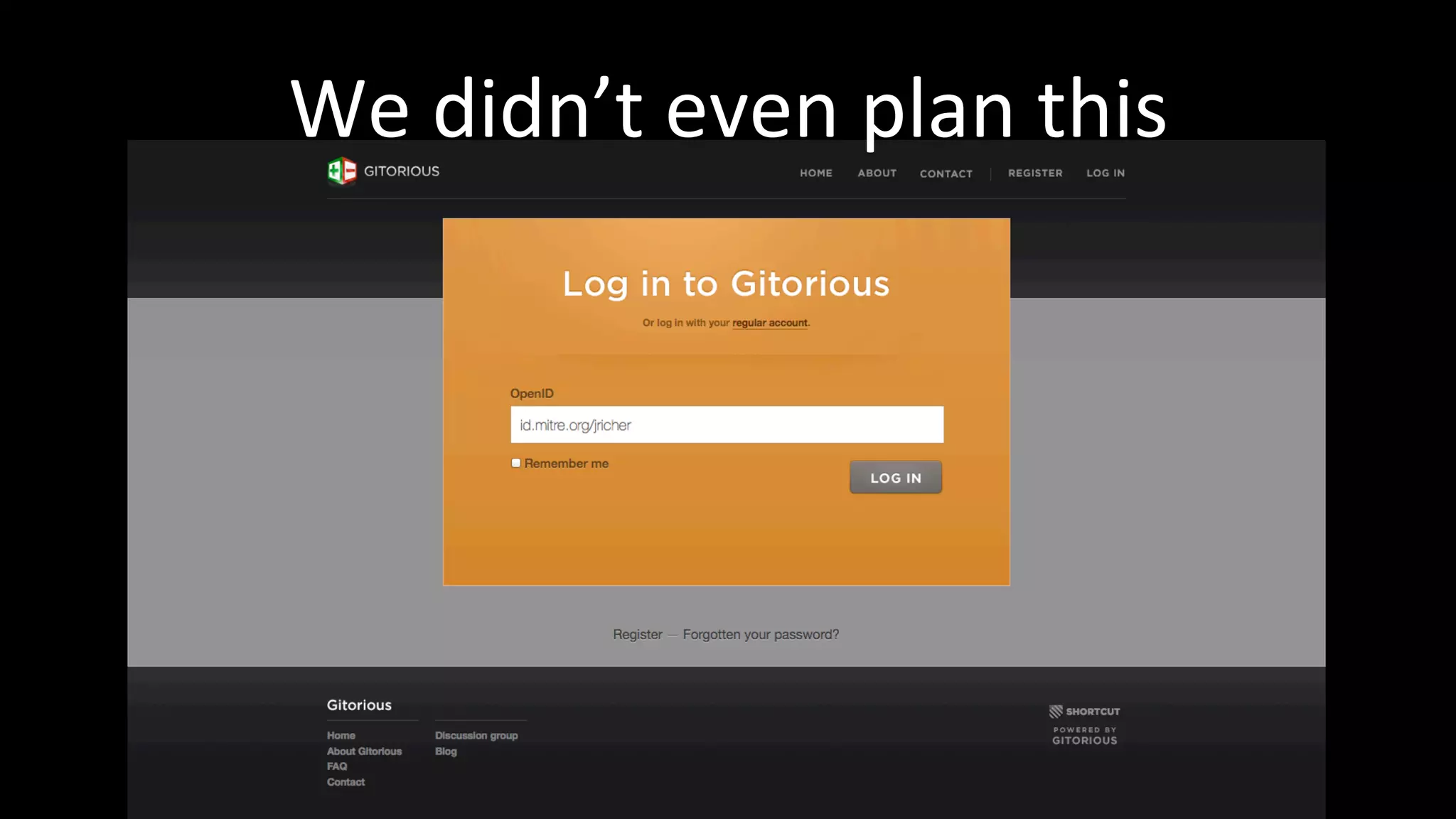
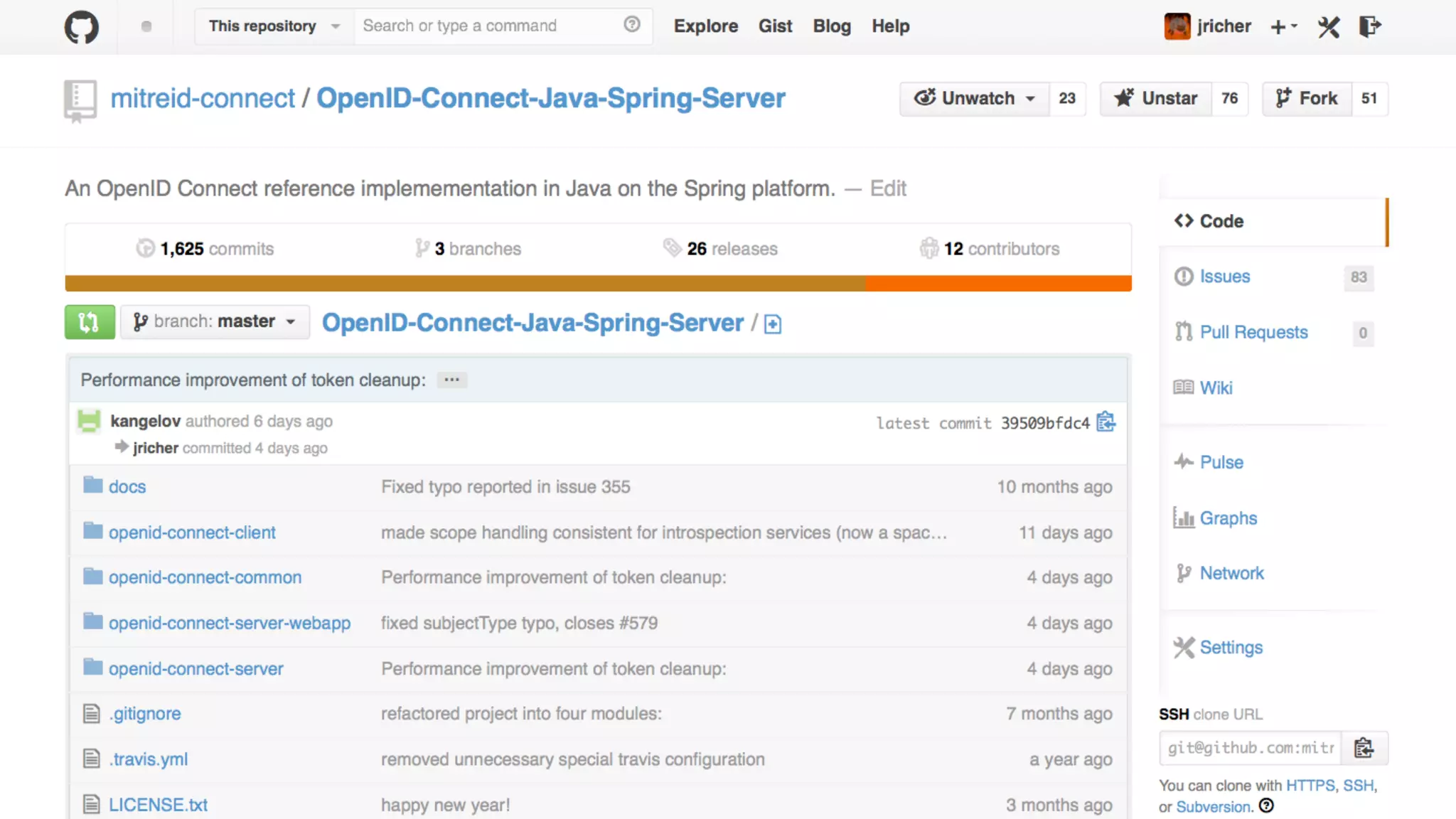
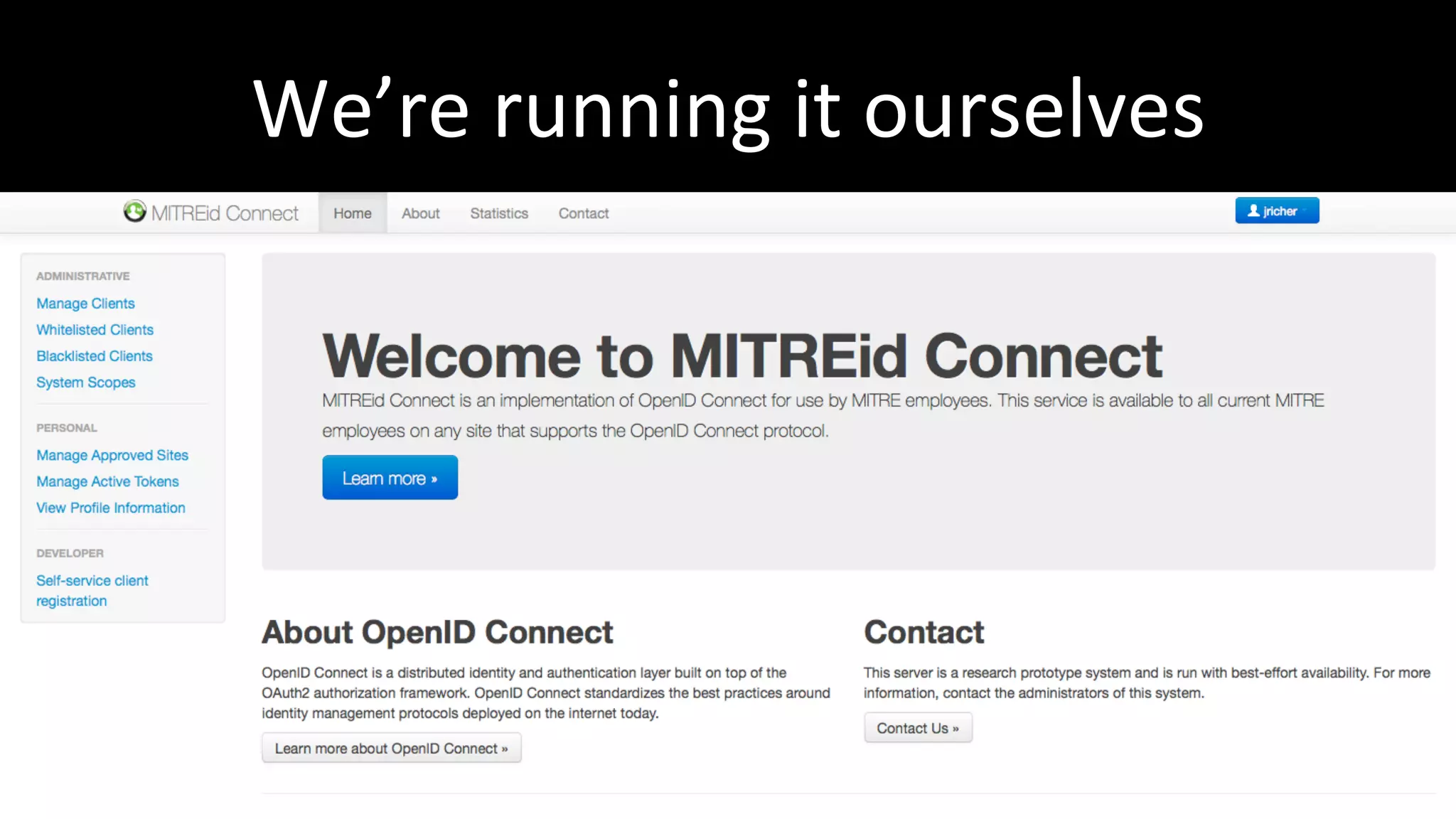
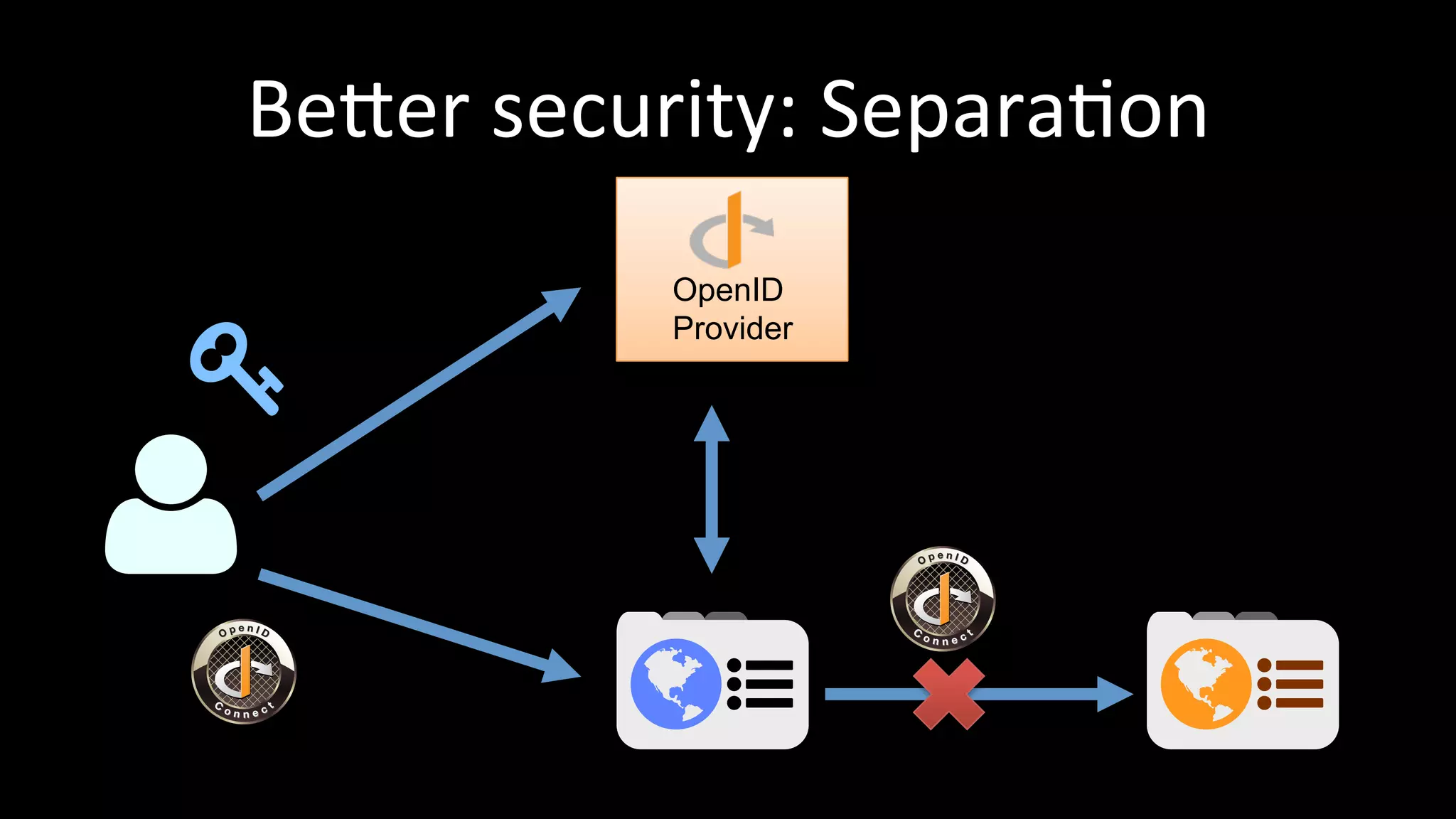
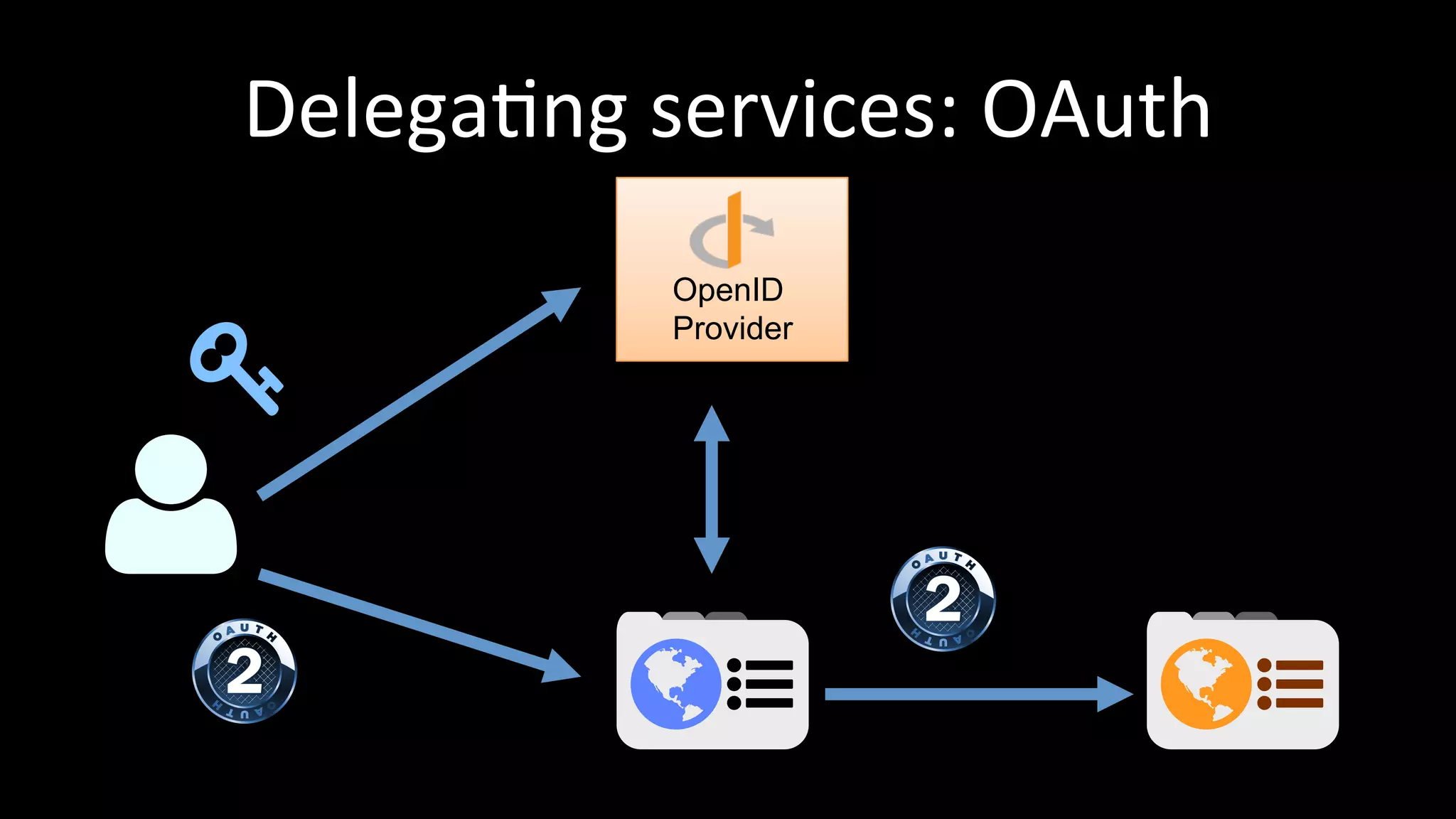
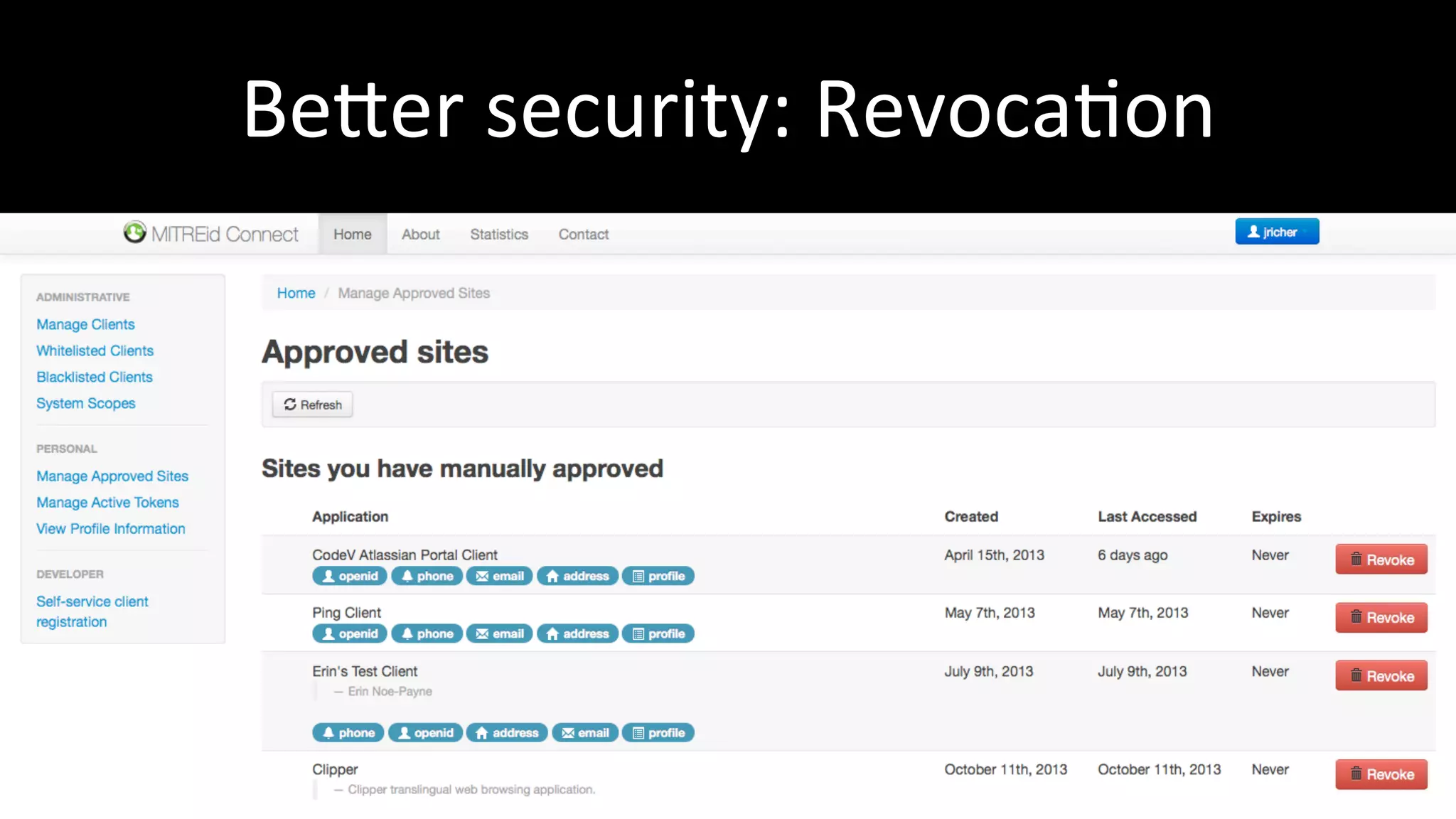
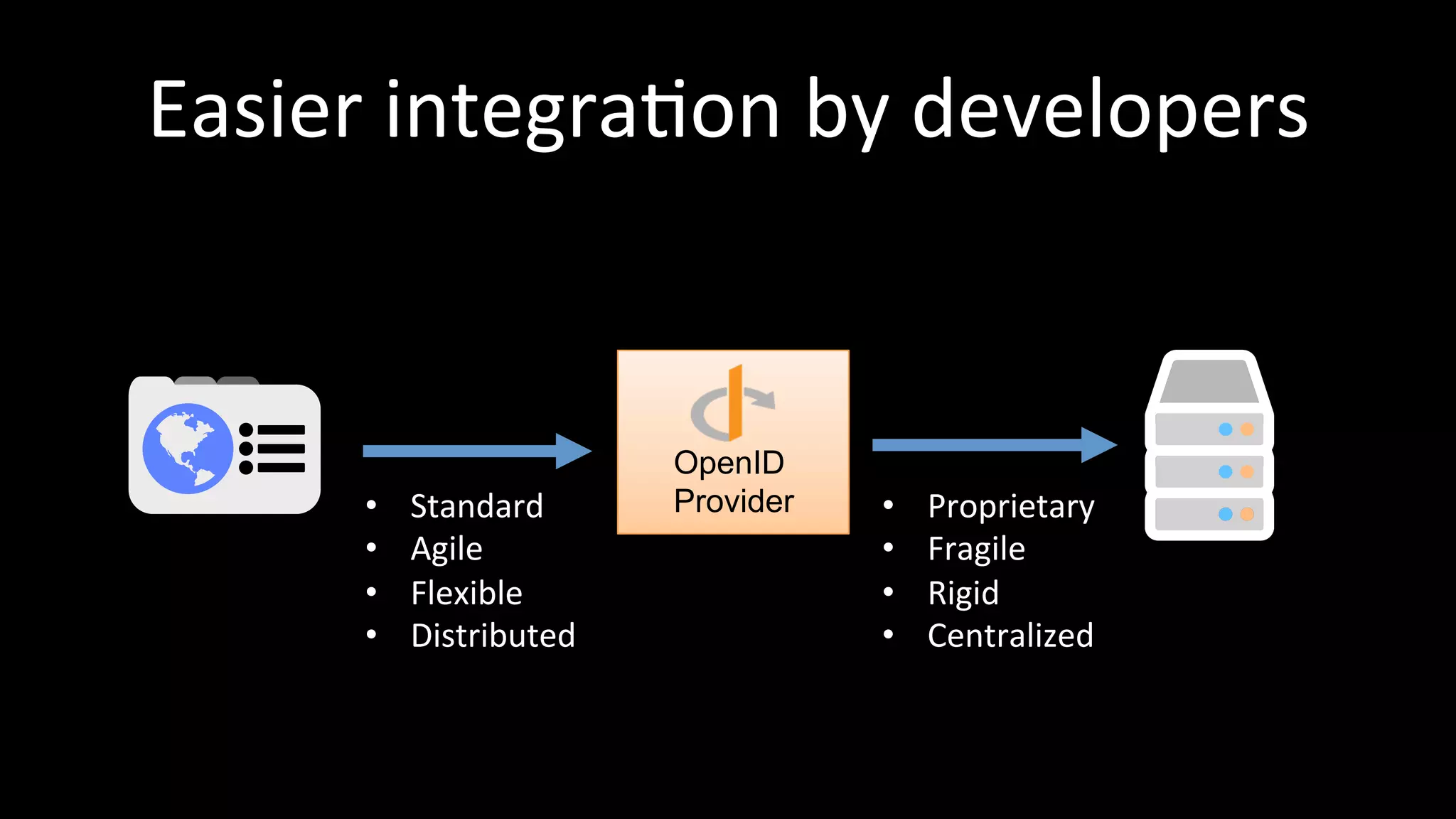
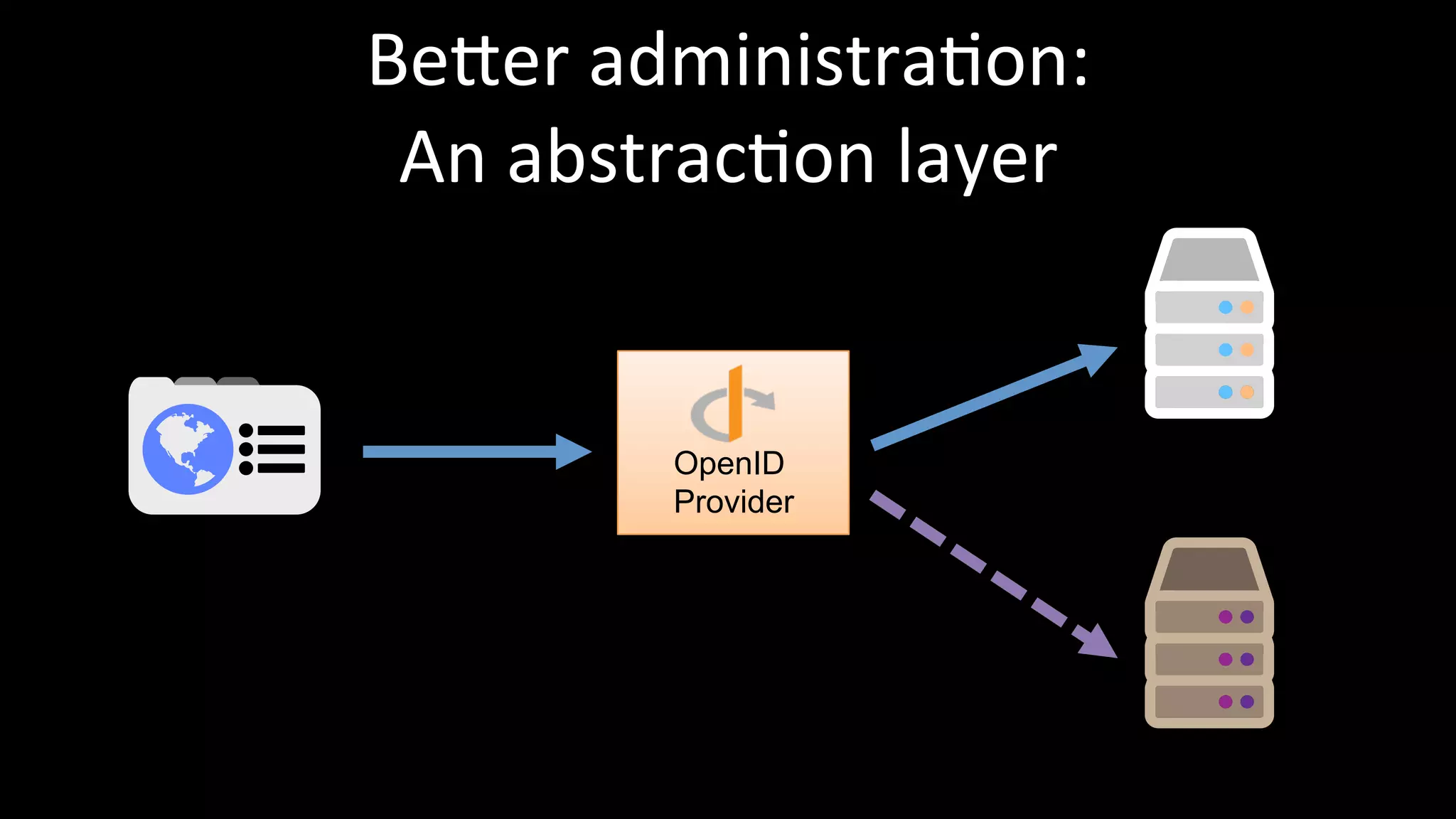
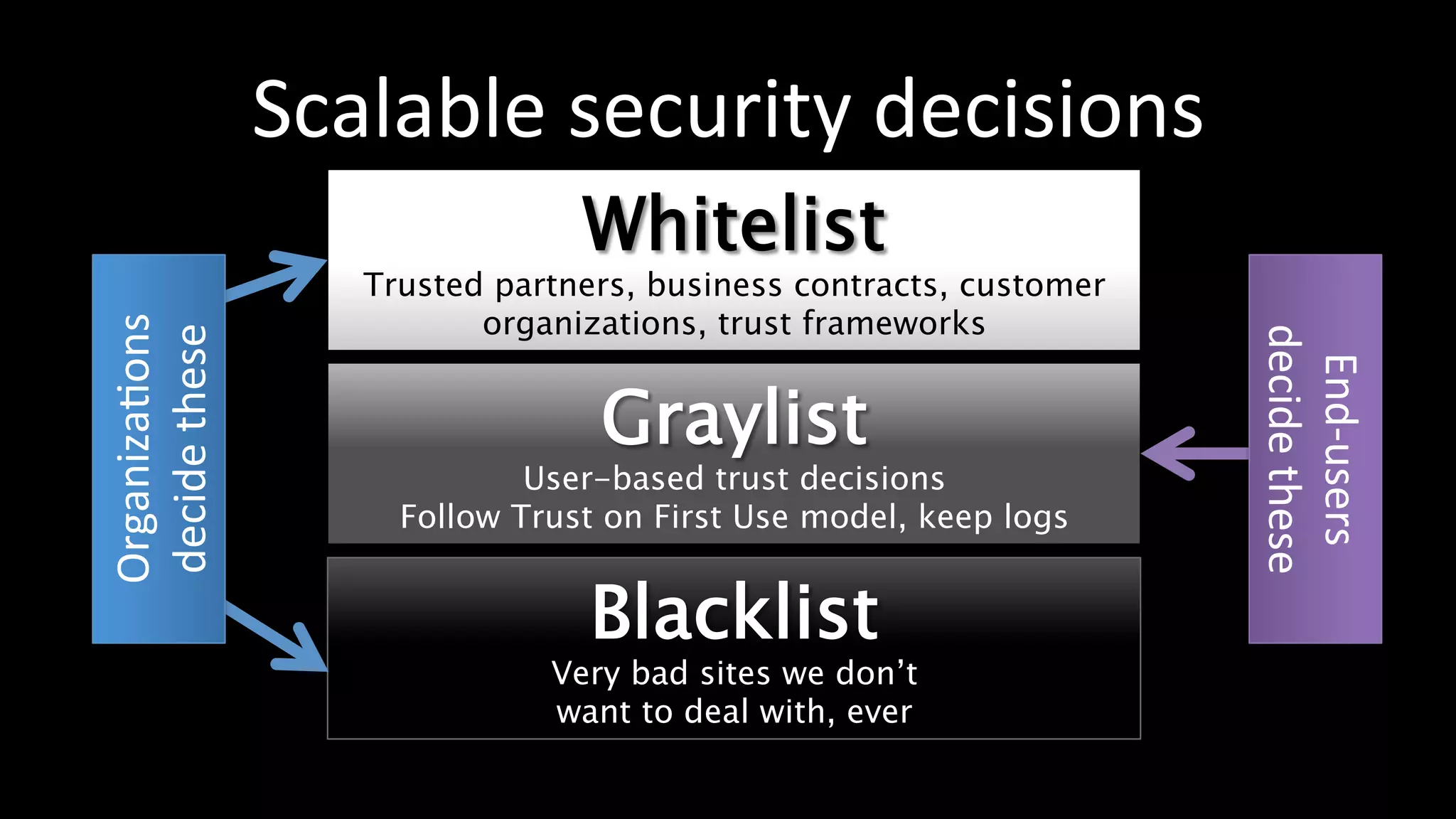
The document discusses the challenges faced by software developers in managing digital identities and provides solutions such as implementing OpenID 2.0 and OAuth 2.0 for federated identity management. It emphasizes building secure, scalable systems to facilitate user authentication and provides various programming libraries for developers. The conclusion advocates the use of open standards and user-driven trust models for better security and integration in digital identity management.