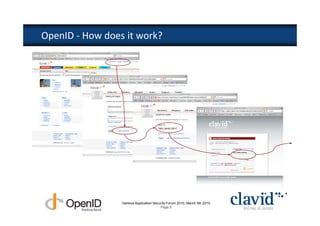
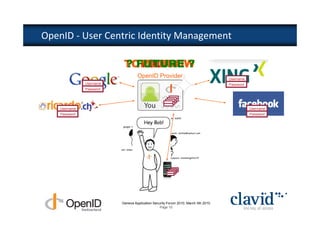
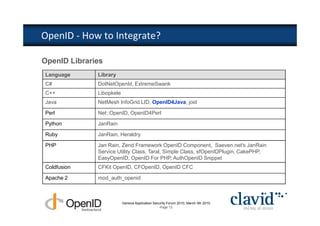
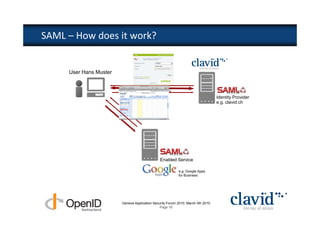
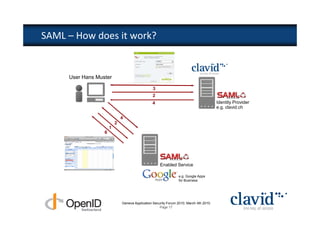
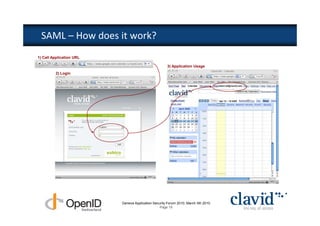
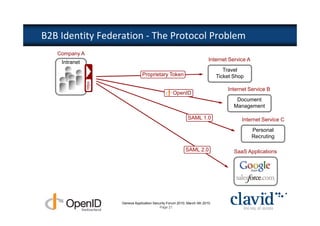
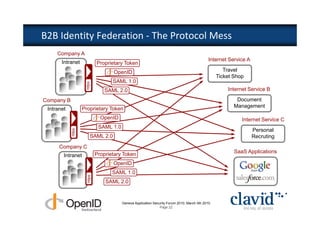
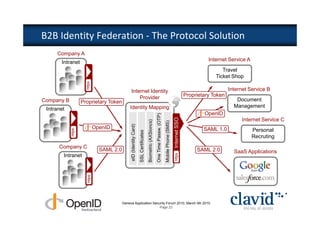
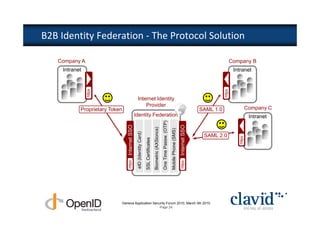
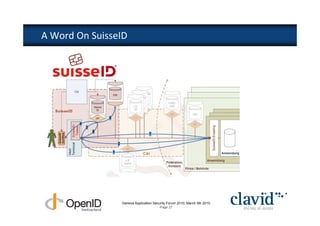
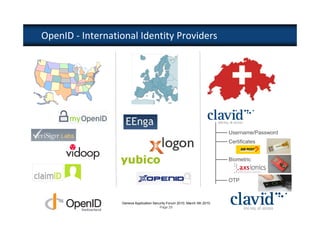
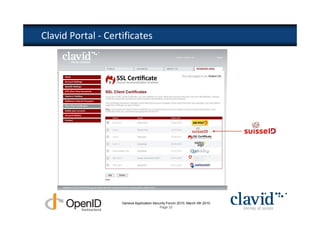
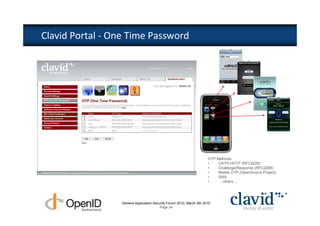
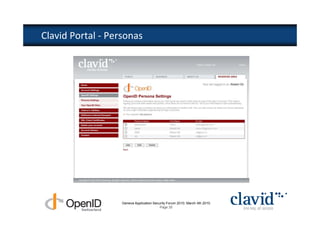
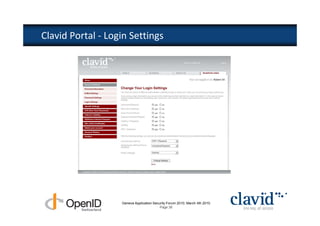
The document discusses OpenID and SAML technologies for internet single sign-on, detailing their structures, operations, and integration methods. It covers identity federation, the emerging SuisseID for strong authentication, and emphasizes the importance of user-centric identity management. The conclusion encourages the adoption of OpenID and SAML to enhance internet services and user authentication experiences.