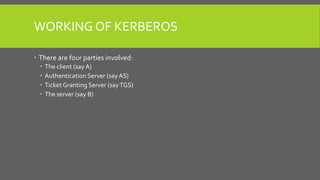
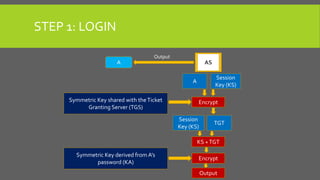
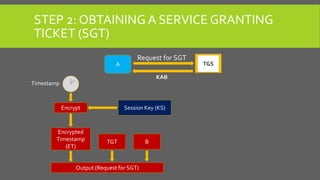
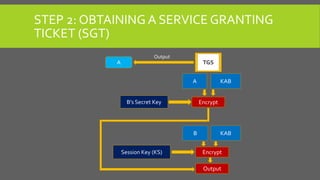
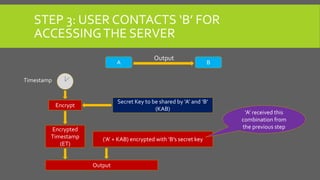
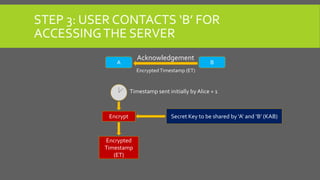
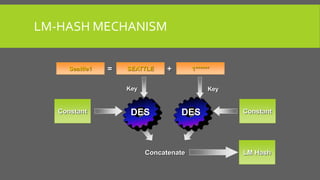
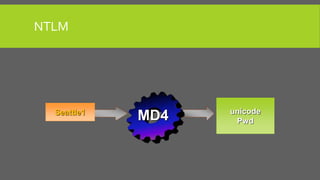
The document provides an overview of Kerberos, LM-HASH, and NTLM, focusing on their functionalities and vulnerabilities. Kerberos, developed at MIT, uses symmetric key cryptography and requires a trusted third party while LM-HASH is a legacy password hashing mechanism with significant weaknesses. NTLM serves as an authentication and session security protocol in Microsoft systems, but it is also vulnerable to various attacks like 'pass the hash' and 'cross-site scripting.'