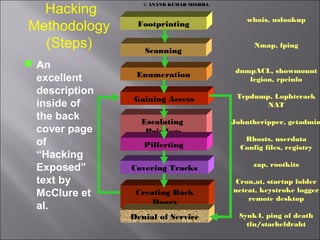
Hacking step (Methodology)
- 1. Hacking Methodology (Steps) An excellent description inside of the back cover page of “Hacking Exposed” text by McClure et al. Scanning Footprinting Enumeration Gaining Access Escalating Privilege Pilferting Covering Tracks Creating Back Doors Denial of Service whois, nslookup Nmap, fping dumpACL, showmount legion, rpcinfo Tcpdump, Lophtcrack NAT Johntheripper, getadmin Rhosts, userdata Config files, registry zap, rootkits Cron,at, startup folder netcat, keystroke logger remote desktop Synk4, ping of death tfn/stacheldraht © ANAND KUMAR MISHRA
- 2. Footprinting Information gathering. Sam Spade is window-based network query tool. Find out target IP address/phone number range Why check phone numbers? Namespace acquisition. Network Topology (visualRoute). It is essential to a “surgical” attack. The key here is not to miss any details. Note that for penetration tester, this step is to avoiding testing others instead of your client and to include all systems to be tested (sometime the organization will not tell you what their systems consist of). Defense: deploy NIDS (snort), RotoRouter Technique s Open Source search Find domain name, admin, IP addresses name servers DNS zone transfer Tools Google, search engine, Edgar Whois (Network solution; arin) Nslookup (ls –d) dig
- 3. Scanning Bulk Target assessment Which machine is up and what ports (services) are open Focus on most promising avenues of entry. To avoid being detect, these tools can reduce frequency of packet sending and randomize the ports or IP addresses to be scanned in the sequence. Note that some machine does not respond to ping but responds to requests to ports that actually open. Ardor is an example. Technique s Ping sweep TCP/UDP port scan OS detection Tools Fping, icmpenum WS_Ping ProPack nmap Nmap Superscan fscan Nmap queso siphon
- 4. Enumeration Identify valid user accounts or poorly protected resource shares. Most intrusive probing than scanning step. Techniques list user accounts list file shares identify applications Tools Null sessions DumpACL Sid2usre onSiteAdmin Showmount NAT legion Banner grabing with telnet or netcat, rpcinfo
- 5. Gaining Access Based on the information gathered so far, make an informed attempted to access the target. Techniq ues Password eavesdroppin g File share brute forcing Password File grab Buffer overflow Tools Tcpdump/ssld ump L0phtcrack readsmb NAT legion Tftp Pwddump2(NT ) Ttdb, bind IIS .HTR/ISM. DLL
- 6. Escalating Privilege If only user-level access was obtained in the last step, seek to gain complete control of the system. Techniques Password cracking Known Exploits Tools John the ripper L0phtcrack Lc_messages, Getadmin, sechole
- 7. Pilfering Webster's Revised Unabridged Dictionary (1913) Pilfer Pil"fer, v. i. [imp. & p. p. Pilfered; p. pr. & vb. n. Pilfering.] [OF. pelfrer. See Pelf.] To steal in small quantities, or articles of small value; to practice petty theft. Gather info on identify mechanisms to allow access of trusted systems. Techniques Evaluate Trusts Search for cleartext passwords Tools rhosts LSA secrets User data, Configuration files Registry
- 8. Covering Tracks Once total ownership of the target is secured, hiding this fact from system administrators become paramount, less they quickly end the romp. Techniques Clear Logs Hide tools Tools Zap, Event Log GUI Rootkits file streaming
- 9. Creating Back Doors Trap doors will be laid in various parts of the system to ensure that privilege access is easily regained whenever the intruder decides. Technique s Create rogue user accounts Schedule batch jobs Infect startup files Tools Members of wheel, admin Cron, AT rc, startup folder, registry keys Technique s Plant remote control services Install monitoring mechanisms Replace appls with Trojans Tools Netcat, remote.exe VNC, B02K remote desktop Keystroke loggers, add acct. to secadmin mail aliases Login, fpnwcint.dll
- 10. Denial of Services If atacker is unsuccessful in gaining access, they may use readily available exploit code to disable a target as a last resort. Technique s Syn flood ICMP techniques Identical src/dst SYN requests Tools synk4 Ping to death smurf Land Latierra Technique s Overlapping fragment/offse t bugs Out of bounds TCP options (OOB) DDoS Tools Netcat, remote.exe VNC, B02K remote desktop Keystroke loggers, add acct. to secadmin mail aliases Trinoo TFN stacheldraht
