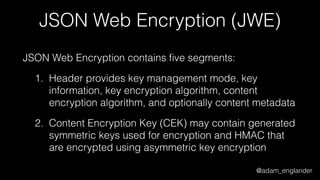
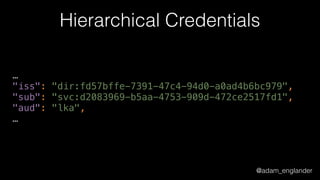
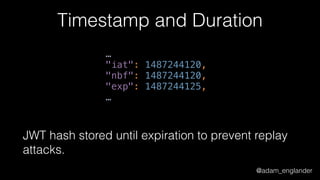
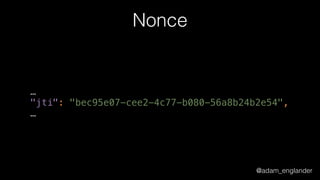
The document discusses the evolution of API security and the implementation of JavaScript Object Signing and Encryption (JOSE) to enhance authentication and data integrity. It highlights the improvements brought by JOSE, such as decoupling authentication and validation, reducing code complexity, and enabling better unit testing. Challenges with legacy implementations and the necessity for algorithm support in various programming languages are also addressed.






















![@adam_englander
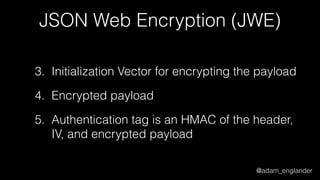
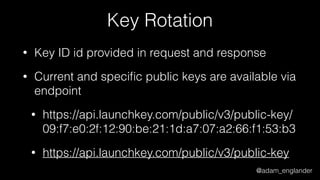
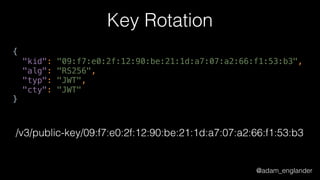
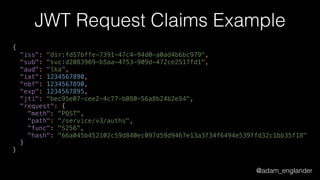
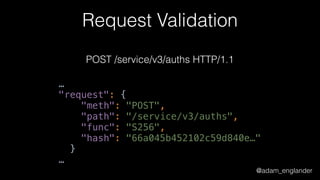
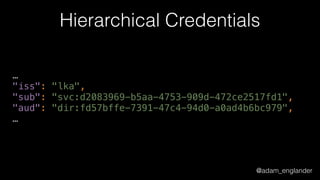
JWT Creation Example
$jwt = (new JWTCreator(new Signer(['RS512'])))->sign(
[
'iat' => time(),
'exp' => time() + 5,
'jti' => 'abc123',
],
['alg' => 'RS512'],
JWKFactory::createFromKeyFile(
'./private.key'
)
);](https://image.slidesharecdn.com/dontloosesleep-secureyourrest-170524214928/85/Don-t-Loose-Sleep-Secure-Your-Rest-php-tek-2017-45-320.jpg)
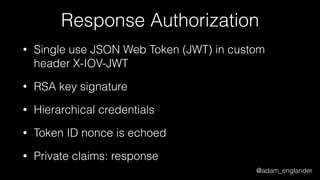
![@adam_englander
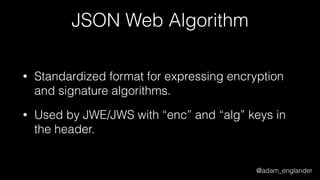
JWT Validation Example
$checkerManager = new CheckerManager();
$checkerManager->addClaimChecker(new IssuedAtChecker());
$jwtLoader = new JWTLoader(
$checkerManager,
new Verifier(['RS512'])
);
$keySet = new JWKSet();
$keySet->addKey(JWKFactory::createFromKeyFile(
'./public.key'
));
$jws = $jwtLoader->load($jwt, $keySet);
$jwtLoader->verify($jws, $keySet);](https://image.slidesharecdn.com/dontloosesleep-secureyourrest-170524214928/85/Don-t-Loose-Sleep-Secure-Your-Rest-php-tek-2017-46-320.jpg)

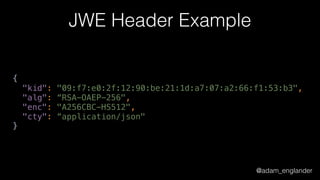
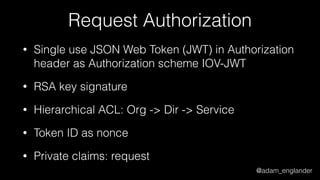
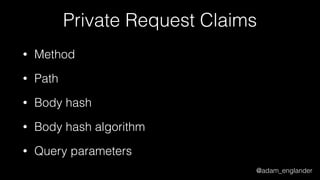
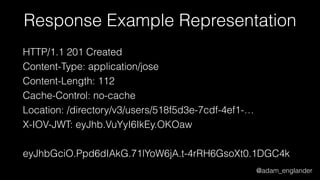
![@adam_englander
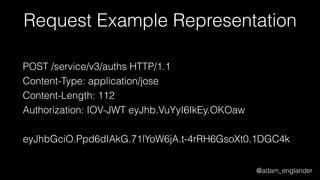
JWE Encryption Example
$encrypted = JWEFactory::createJWEToCompactJSON(
"Hello World!",
JWKFactory::createFromKeyFile(
'./public.key'
),
[
'enc' => 'A256CBC-HS512',
'alg' => 'RSA-OAEP-256',
'zip' => 'DEF',
]
);](https://image.slidesharecdn.com/dontloosesleep-secureyourrest-170524214928/85/Don-t-Loose-Sleep-Secure-Your-Rest-php-tek-2017-49-320.jpg)
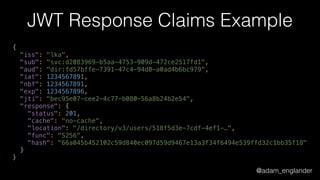
![@adam_englander
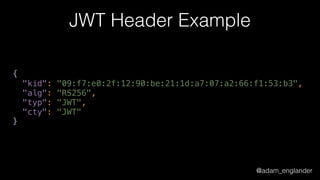
JWE Decryption Example
$decrypted = (new Loader)->loadAndDecryptUsingKey(
$encrypted,
JWKFactory::createFromKeyFile(
'./private.key'
),
['RSA-OAEP-256'], // Acceptable algs
['A256CBC-HS512'] // Acceptable encs
);](https://image.slidesharecdn.com/dontloosesleep-secureyourrest-170524214928/85/Don-t-Loose-Sleep-Secure-Your-Rest-php-tek-2017-50-320.jpg)