Bw-Tree TaS Implementation Design
•
1 like•1,833 views
Ways to implement TaS for mapping table in Bw-Tree
Report
Share
Report
Share
Download to read offline
Recommended
Recommended
More Related Content
Similar to Bw-Tree TaS Implementation Design
Similar to Bw-Tree TaS Implementation Design (20)
JavaOne 2016 -Emerging Web App Architectures using Java and node.js

JavaOne 2016 -Emerging Web App Architectures using Java and node.js
Decipher Multi-Factor Authentication - A Developers Introduction

Decipher Multi-Factor Authentication - A Developers Introduction
Introduzione ai network penetration test secondo osstmm

Introduzione ai network penetration test secondo osstmm
Cyber-physical system with machine learning (Poster)

Cyber-physical system with machine learning (Poster)
Recently uploaded
Recently uploaded (20)
AI/ML Infra Meetup | ML explainability in Michelangelo

AI/ML Infra Meetup | ML explainability in Michelangelo
10 Essential Software Testing Tools You Need to Know About.pdf

10 Essential Software Testing Tools You Need to Know About.pdf
Facemoji Keyboard released its 2023 State of Emoji report, outlining the most...

Facemoji Keyboard released its 2023 State of Emoji report, outlining the most...
Microsoft 365 Copilot; An AI tool changing the world of work _PDF.pdf

Microsoft 365 Copilot; An AI tool changing the world of work _PDF.pdf
StrimziCon 2024 - Transition to Apache Kafka on Kubernetes with Strimzi.pdf

StrimziCon 2024 - Transition to Apache Kafka on Kubernetes with Strimzi.pdf
COMPUTER AND ITS COMPONENTS PPT.by naitik sharma Class 9th A mittal internati...

COMPUTER AND ITS COMPONENTS PPT.by naitik sharma Class 9th A mittal internati...
Entropy, Software Quality, and Innovation (presented at Princeton Plasma Phys...

Entropy, Software Quality, and Innovation (presented at Princeton Plasma Phys...
AI/ML Infra Meetup | Perspective on Deep Learning Framework

AI/ML Infra Meetup | Perspective on Deep Learning Framework
Tree in the Forest - Managing Details in BDD Scenarios (live2test 2024)

Tree in the Forest - Managing Details in BDD Scenarios (live2test 2024)
OpenChain @ LF Japan Executive Briefing - May 2024

OpenChain @ LF Japan Executive Briefing - May 2024
Agnieszka Andrzejewska - BIM School Course in Kraków

Agnieszka Andrzejewska - BIM School Course in Kraków
Workforce Efficiency with Employee Time Tracking Software.pdf

Workforce Efficiency with Employee Time Tracking Software.pdf
Mastering Windows 7 A Comprehensive Guide for Power Users .pdf

Mastering Windows 7 A Comprehensive Guide for Power Users .pdf
5 Reasons Driving Warehouse Management Systems Demand

5 Reasons Driving Warehouse Management Systems Demand
Bw-Tree TaS Implementation Design
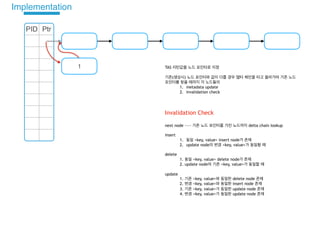
- 1. PID Ptr 1 TAS ( ) 1. metadata update 2. invalidation check Invalidation Check next node ~~~ delta chain lookup insert 1. <key, value> insert node 2. update node <key, value> delete 1. <key, value> delete node 2. update node <key, value> update 1. <key, value> delete node 2. <key, value> insert node 3. <key, value> update node 4. <key, value> update node Implementation
- 2. PID Ptr 0 1 2 node ( )1 2 node 1 -> 2 TAS Implementation
- 3. PID Ptr 0 1 2 node ( )1 2 node 1 -> 2 TAS 1: TAS == . Delta chain lookup Implementation
- 4. PID Ptr 0 1 1 2 node 1 -> 2 TAS 1: TAS == . Delta chain lookup 2: TAS 1 . 0 delta chain lookup 2 node ( ) Implementation
- 5. PID Ptr 0 1 2 3 4 5 Delta Chain Lookup 1: - 2: 1 3: 1~2 4: 1~3 5: 1~4 1~5 delta node Delta Node Insertion Workflow Previous: do { check abort create delta node } while (CAS) TAS: check abort create delta node TAS Invalidation check & metadata update Invalidation check & metadata update: node ( delta node ) . length < # of threads Invalidation Check
- 6. PID Ptr 0 1 2 3 4 5 1~5 delta node : 1. Invalidation check node ? valid / invalid 2. Abort delta node handling issue invalid node ? 1) prev node next pointer next pointer => TAS ? 2) node validation bit Invalidation Check
- 7. PID Ptr i <5, 5> i <4, 4> i <3, 3> i <2, 2> i <1, 1> 1: i <6, 6> 2: i <7, 7> 3: i <6, 6> 4: d <5, 5> 5: d <5, 5> Traverse 1~5 delta node Invalidation Check not yet finished. (Consider as Valid) Invalid delta node. Valid delta node. Node Traverse(lookup) requested by other thread. Invalidation Check in progress
- 8. PID Ptr i <5, 5> i <4, 4> i <3, 3> i <2, 2> i <1, 1> 1: i <6, 6> 2: i <7, 7> 3: i <6, 6> 4: d <5, 5> 5: d <5, 5> Traverse present_set i <6, 6> i <7, 7> i <6, 6> i <5, 5> i <4, 4> i <3, 3> i <2, 2> i <1, 1> deleted_set d <5, 5> d <5, 5> = <1, 1> <2, 2> <3, 3> <4, 4> <5, 5> <6, 6> <7, 7>
- 9. PID Ptr 0: i <5, 5> i <4, 4> i <3, 3> i <2, 2> i <1, 1> 1: i <6, 6> 2: i <7, 7> 3: i <6, 6> 4: d <5, 5> 5: d <5, 5> Traverse Check delta Node 2 & 1 (since node 0 is initial starting point) 2: i <7, 7> => OK 1: i <6, 6> => invariant doesn't hold. set invalid bit
- 10. PID Ptr 0: i <5, 5> i <4, 4> i <3, 3> i <2, 2> i <1, 1> 1: i <6, 6> 2: i <7, 7> 3: i <6, 6> 4: d <5, 5> 5: d <5, 5> Traverse present_set i <6, 6> i <7, 7> i <6, 6> i <5, 5> i <4, 4> i <3, 3> i <2, 2> i <1, 1> deleted_set d <5, 5> d <5, 5> = <1, 1> <2, 2> <3, 3> <4, 4> <5, 5> <6, 6> <7, 7>
- 11. PID Ptr 0: i <5, 5> i <4, 4> i <3, 3> i <2, 2> i <1, 1> 1: i <6, 6> 2: i <7, 7> 3: i <6, 6> 4: d <5, 5> 5: d <5, 5> Traverse Check delta Node until reaching node 0 (since node 0 is initial starting point) Both delta node is valid.
- 12. PID Ptr 0: i <5, 5> i <4, 4> i <3, 3> i <2, 2> i <1, 1> 1: i <6, 6> 2: i <7, 7> 3: i <6, 6> 4: d <5, 5> 5: d <5, 5> Traverse Check delta Node until reaching node 0 (since node 0 is initial starting point) No matter which node starts invalidation check first, node 4 will be checked as valid and node 5 will set invalid bit.
- 13. PID Ptr 0: i <5, 5> i <4, 4> i <3, 3> i <2, 2> i <1, 1> 1: i <6, 6> 2: i <7, 7> 3: i <6, 6> 4: d <5, 5> 5: d <5, 5> Traverse present_set i <6, 6> i <7, 7> i <6, 6> i <5, 5> i <4, 4> i <3, 3> i <2, 2> i <1, 1> deleted_set d <5, 5> d <5, 5> = <1, 1> <2, 2> <3, 3> <4, 4> <5, 5> <6, 6> <7, 7>
- 14. PID Ptr 0: i <5, 5> i <4, 4> i <3, 3> i <2, 2> i <1, 1> 1: i <6, 6> 2: i <7, 7> 3: i <6, 6> 4: d <5, 5> 5: d <5, 5> Traverse <1, 1> <2, 2> <3, 3> <4, 4> <5, 5> <6, 6> <7, 7> node traverse . delta node . e.g.) i <8, 8> & d <8, 8> <8, 8> : abort i <8, 8> <8, 8> : abort d <8, 8>