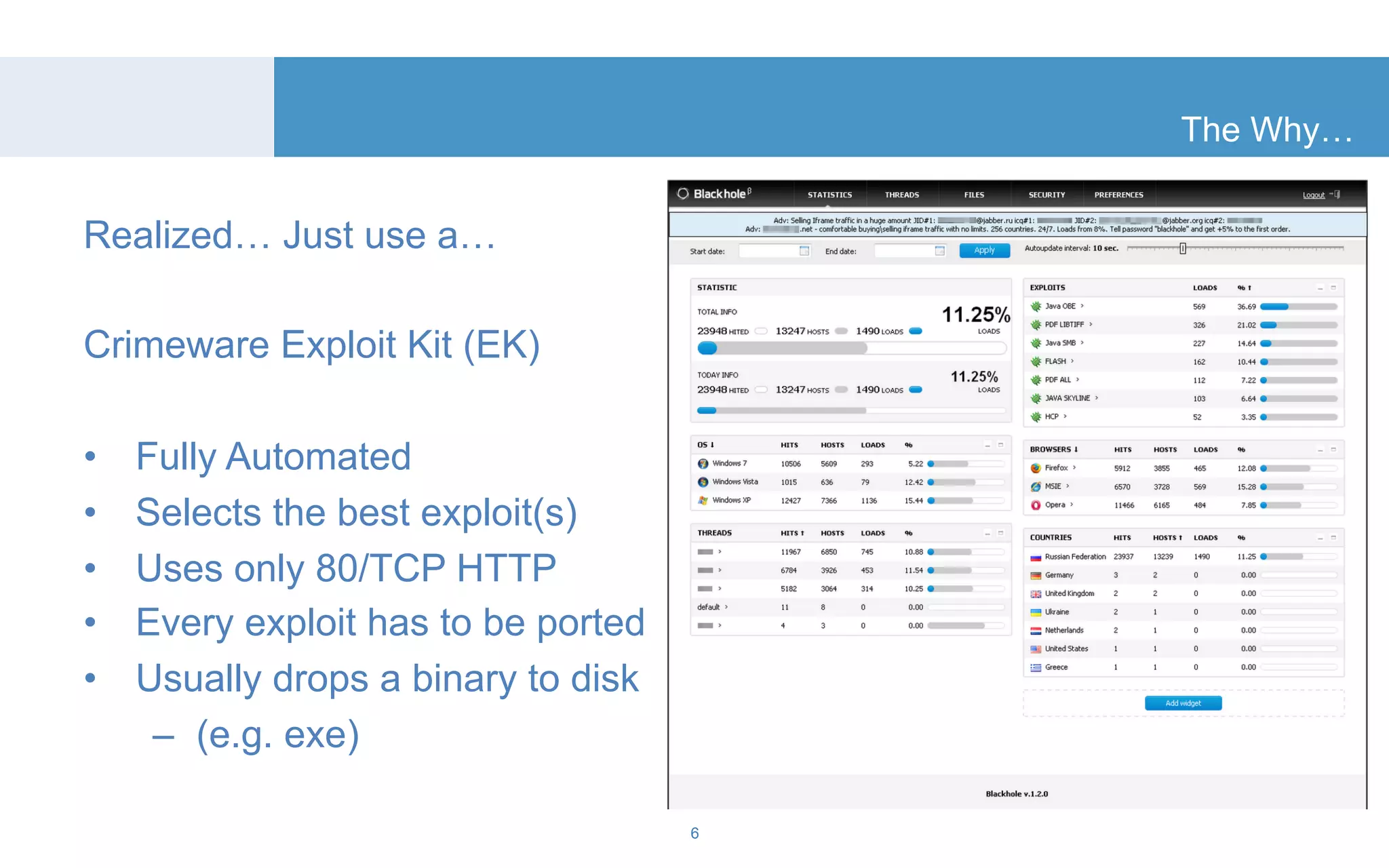
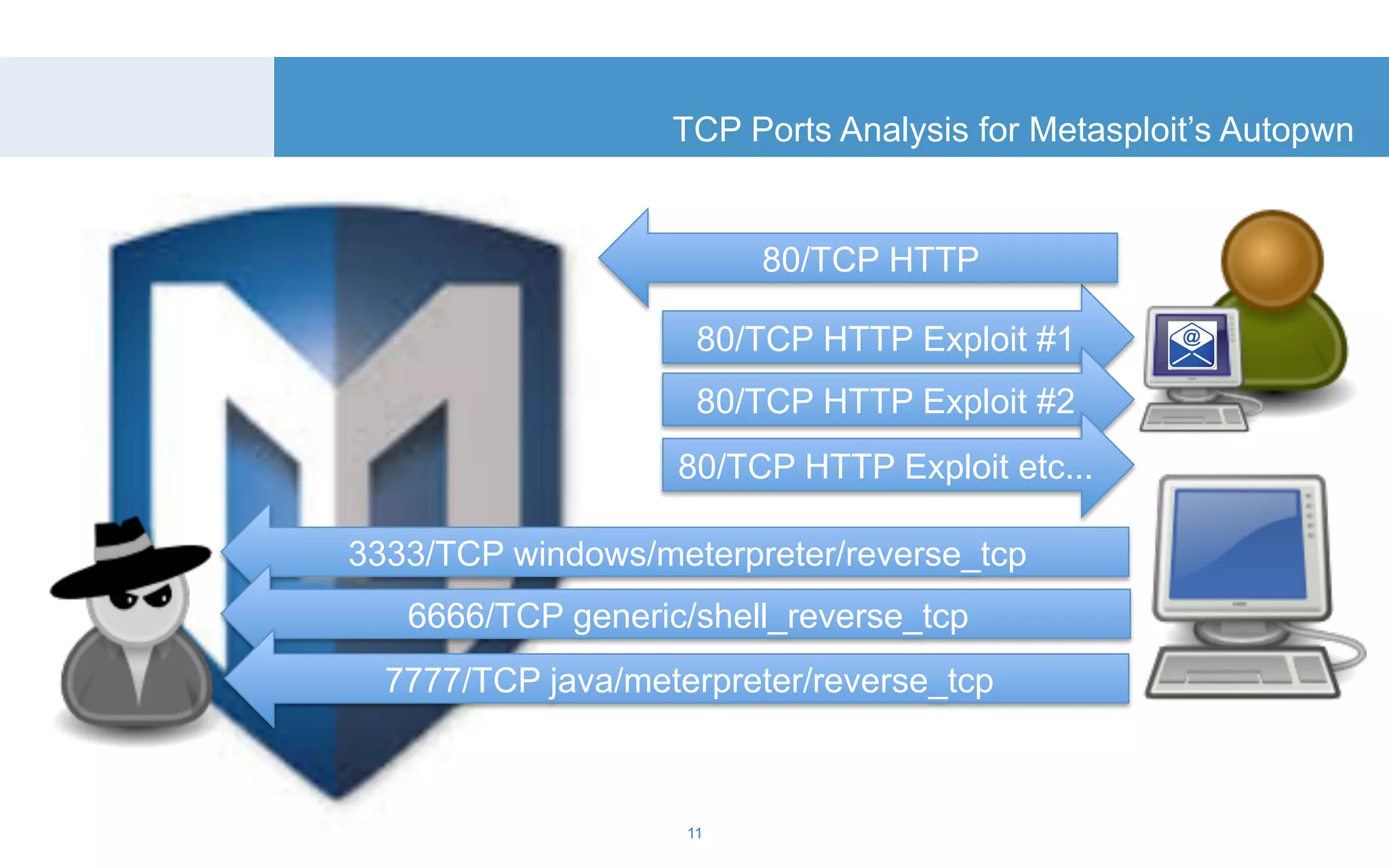
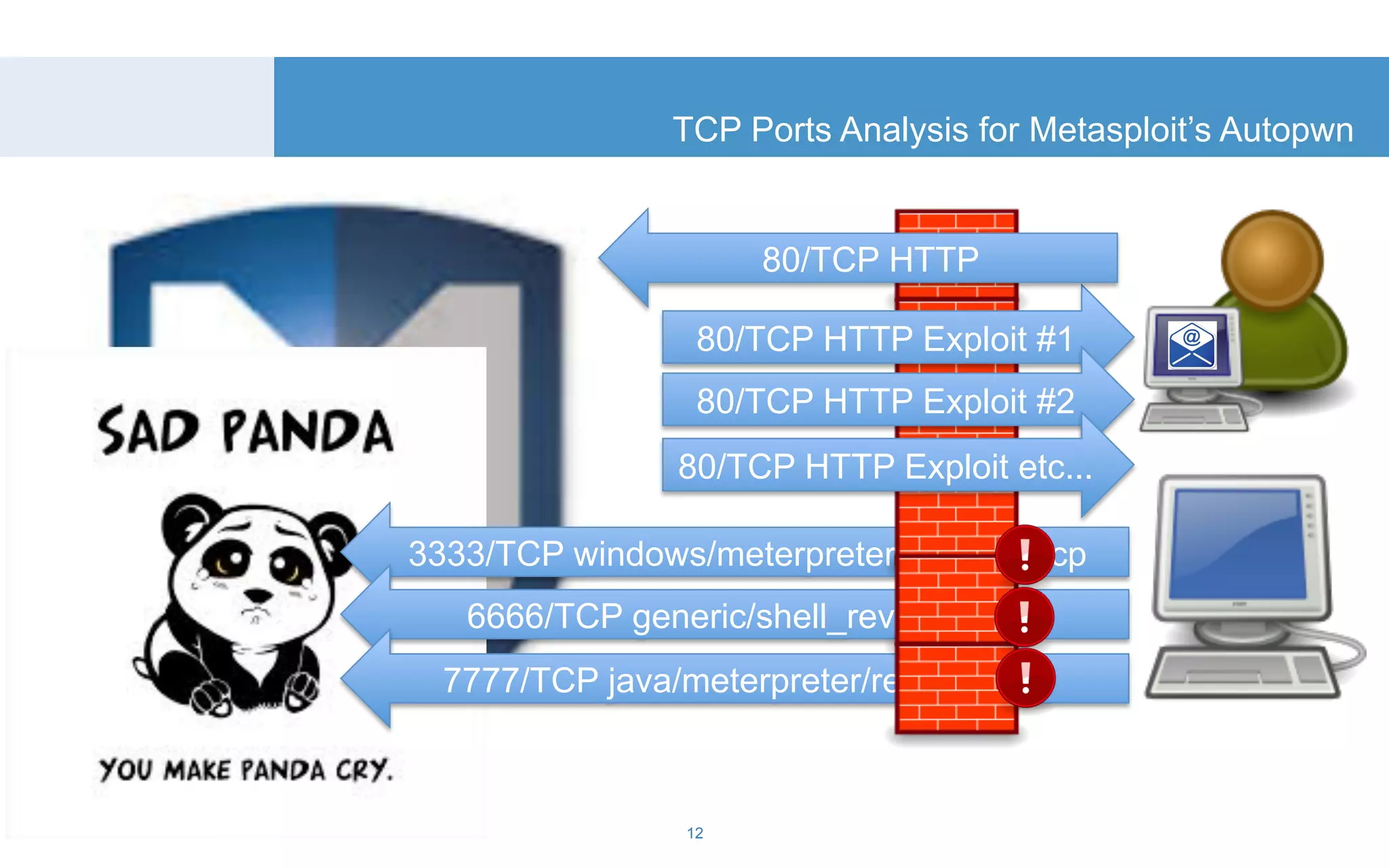
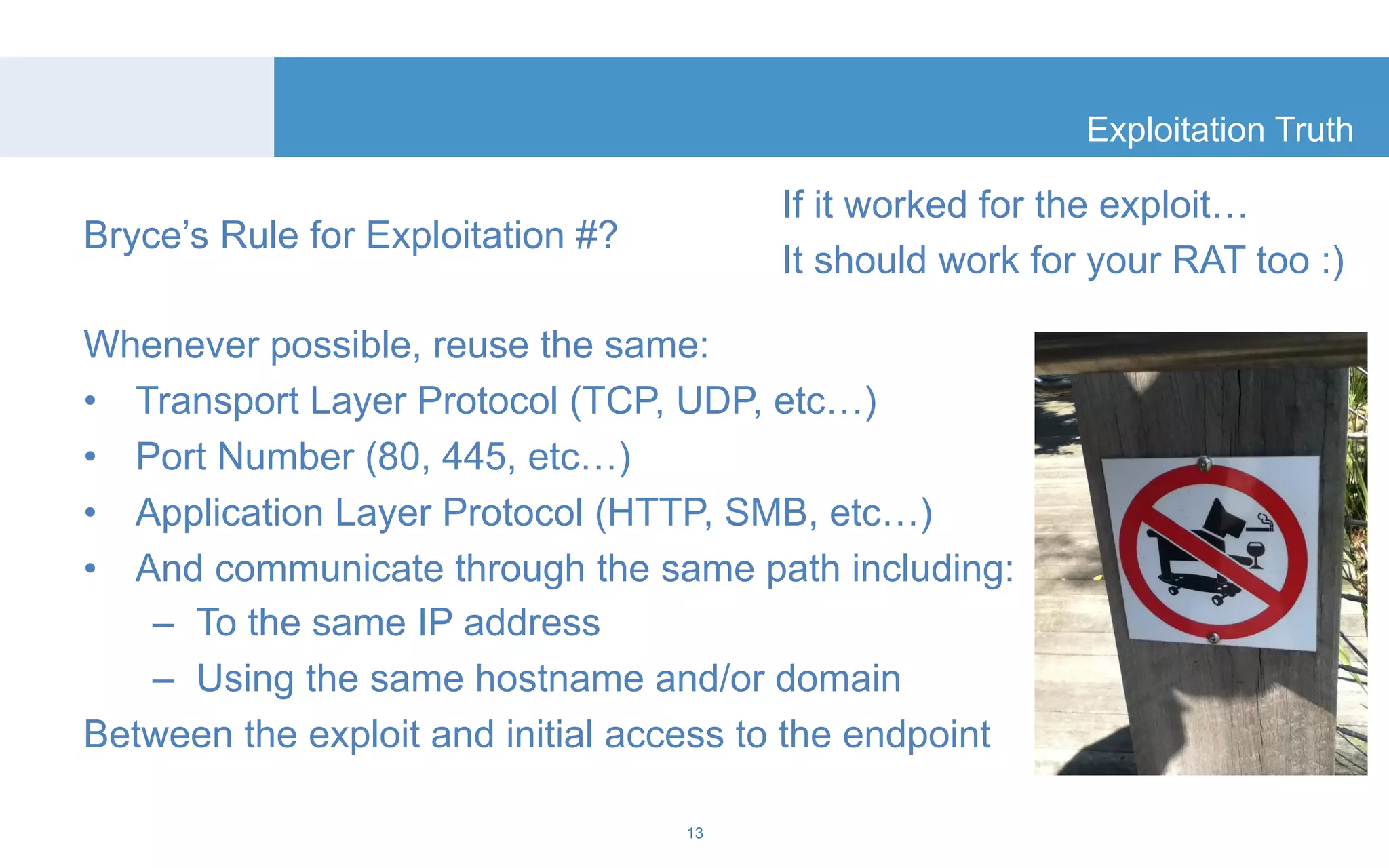
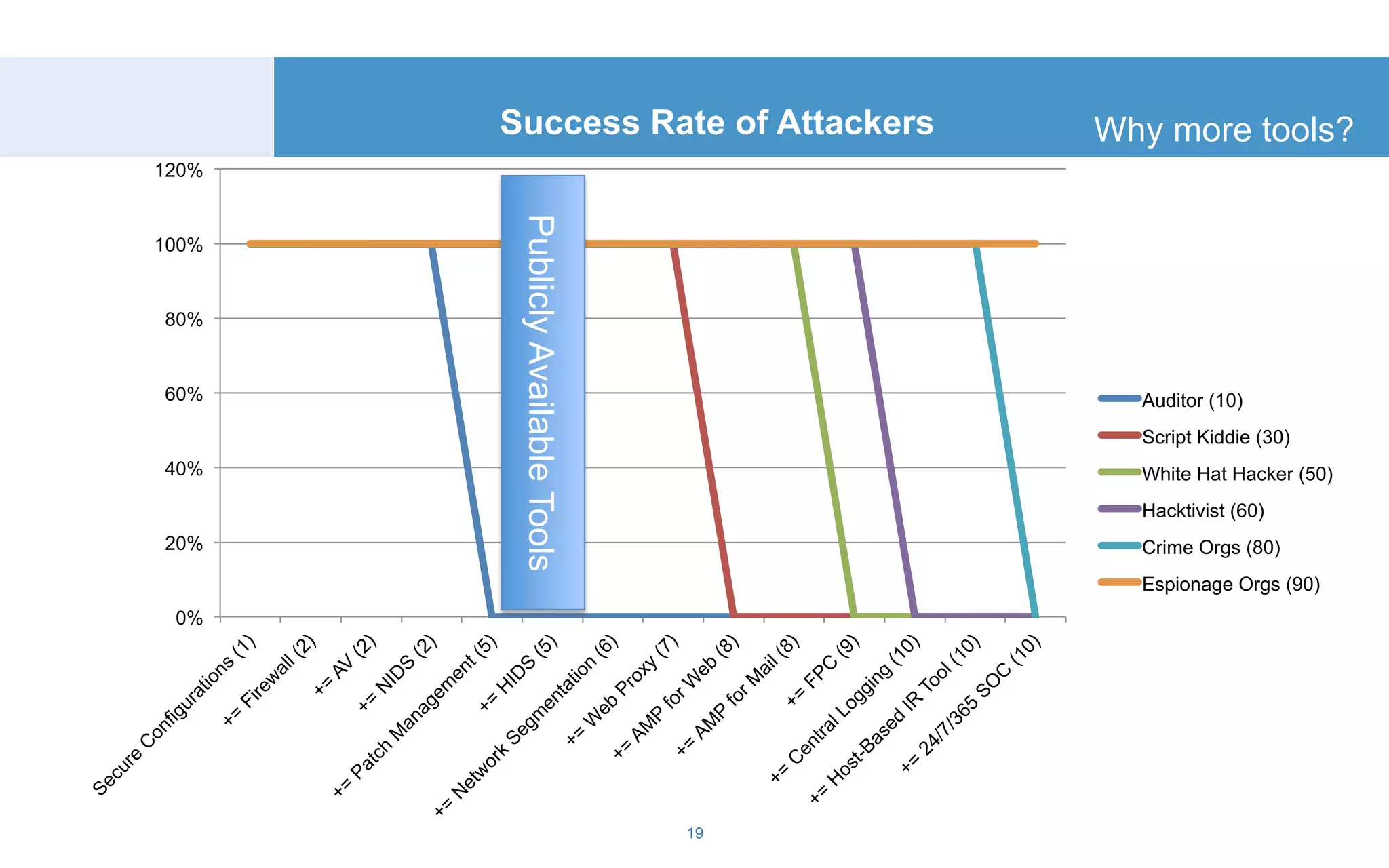
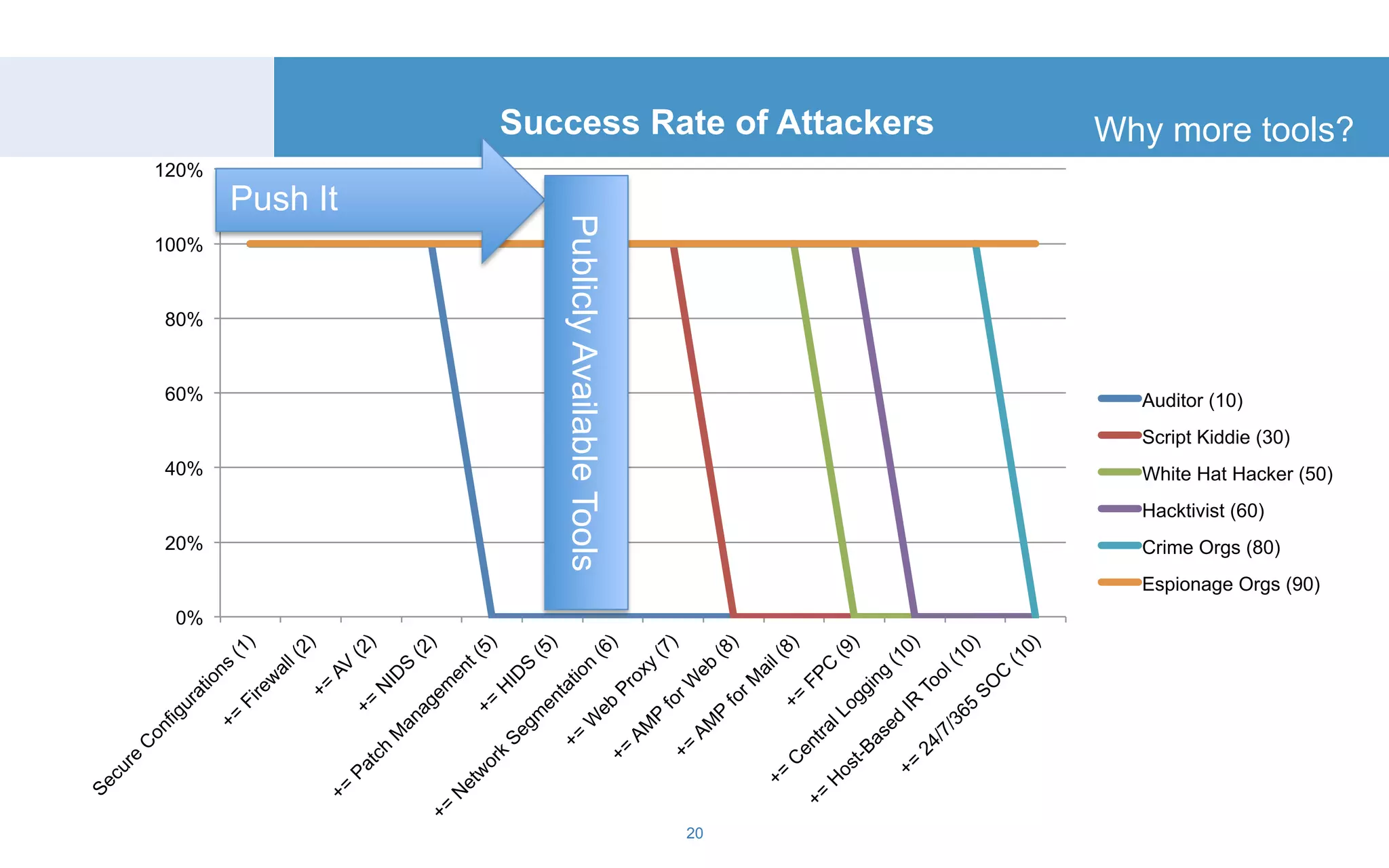
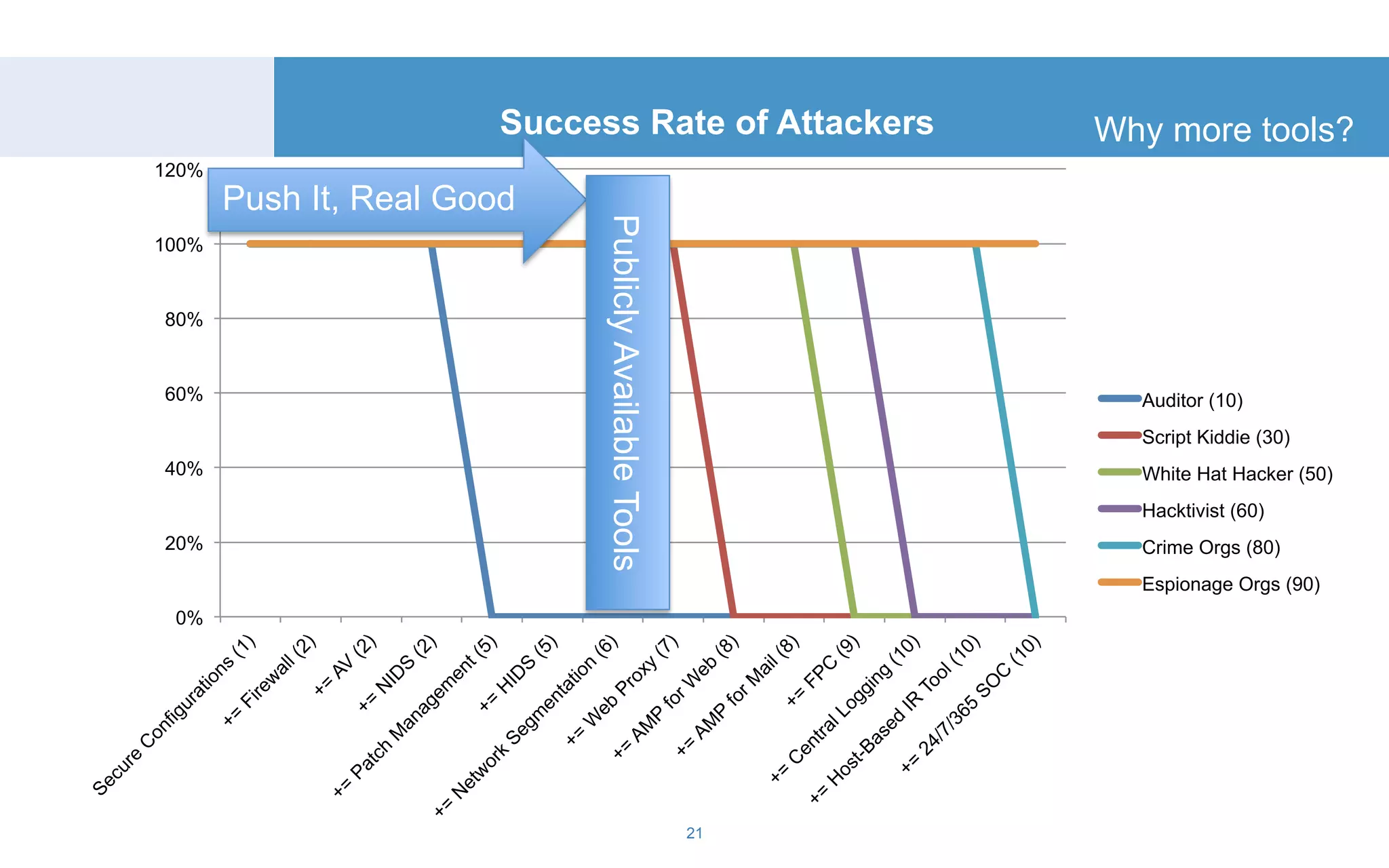
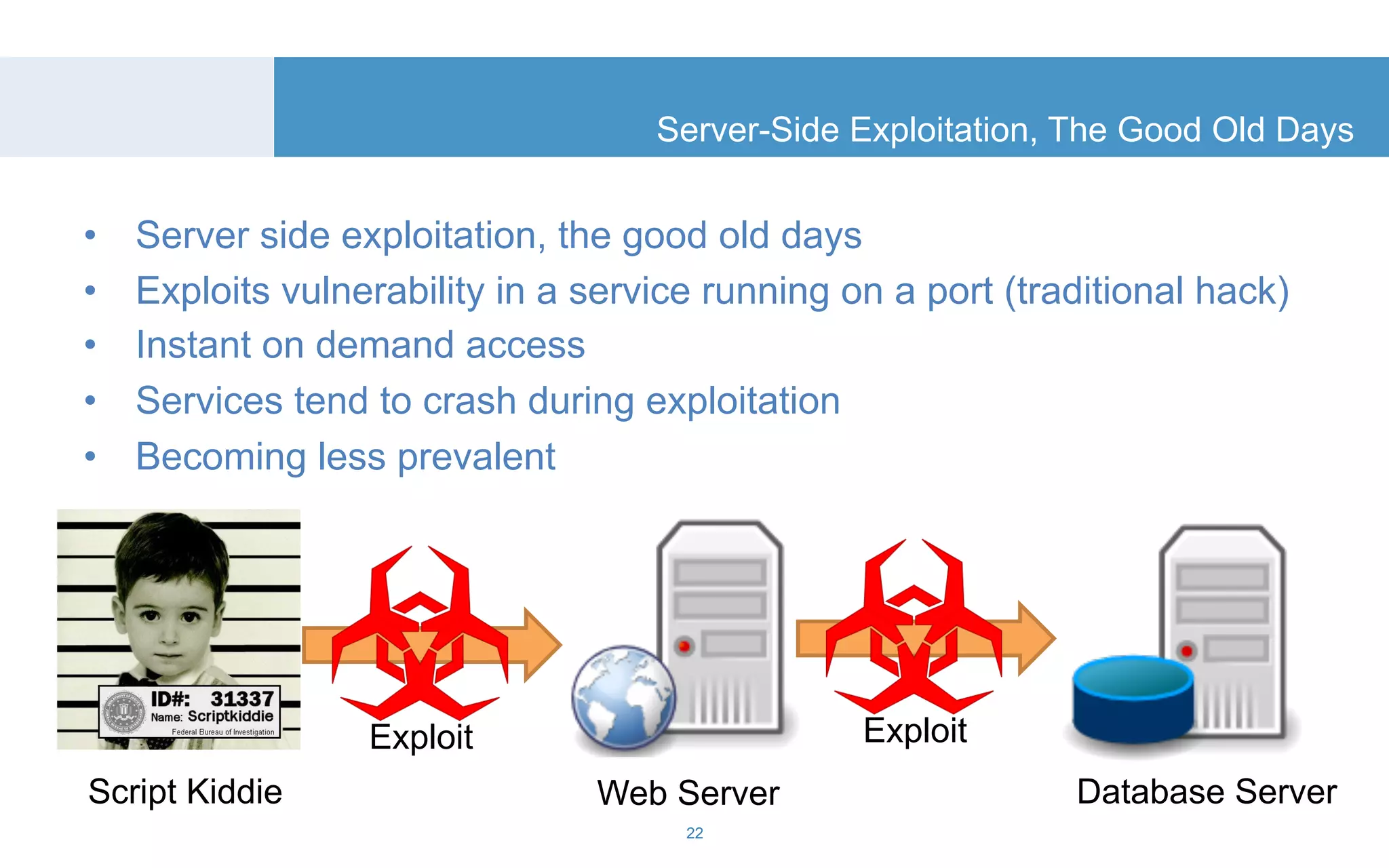
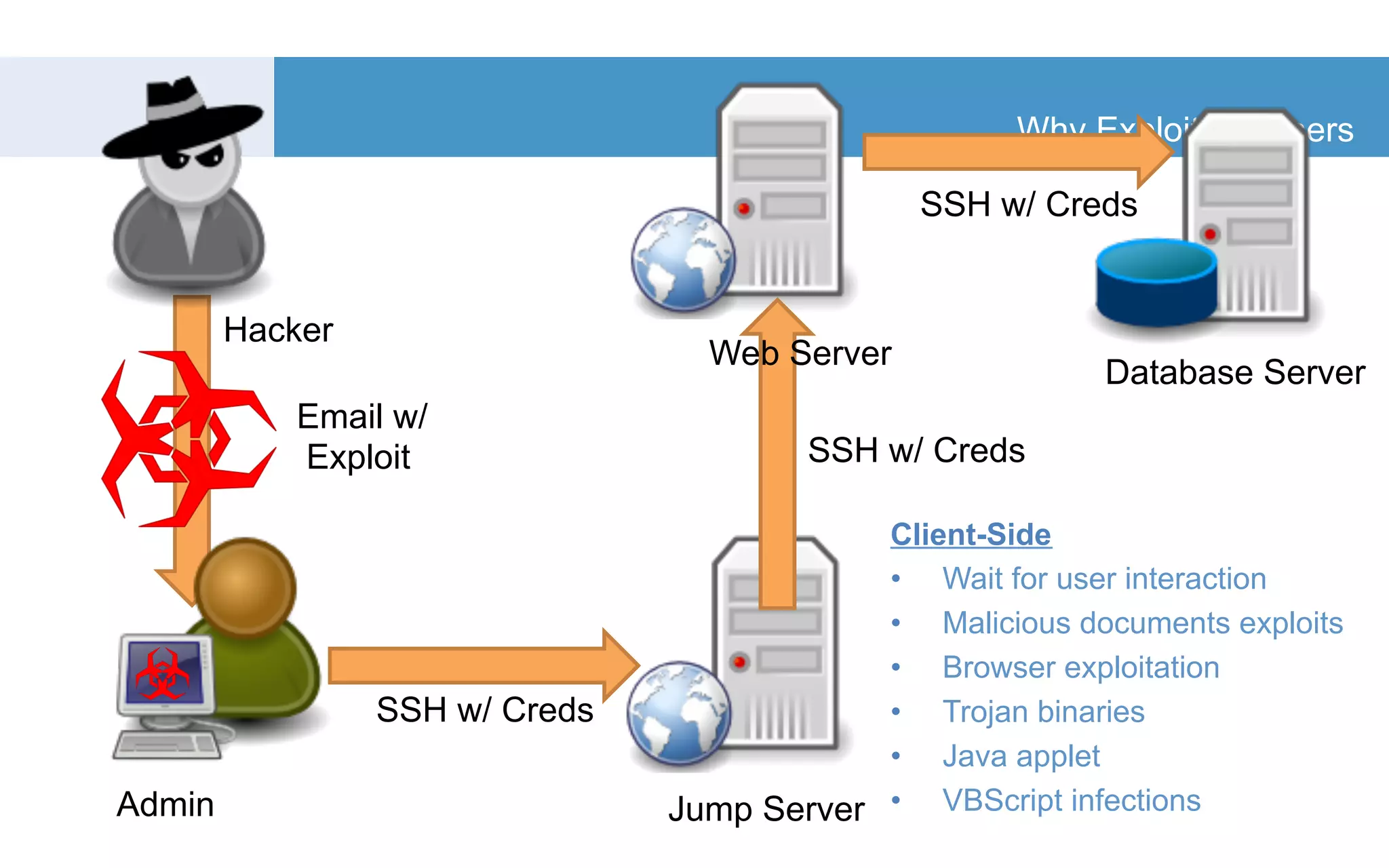
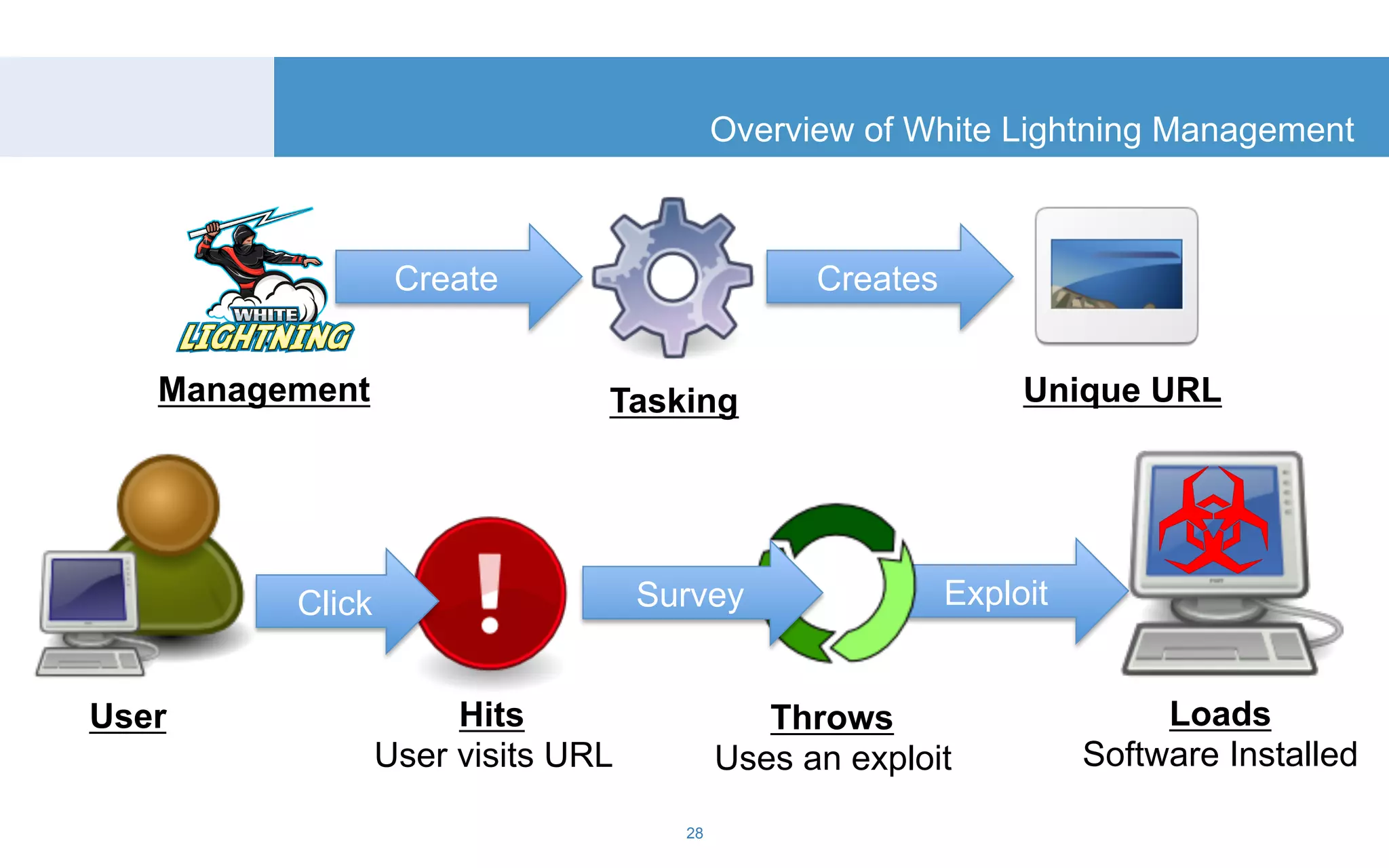
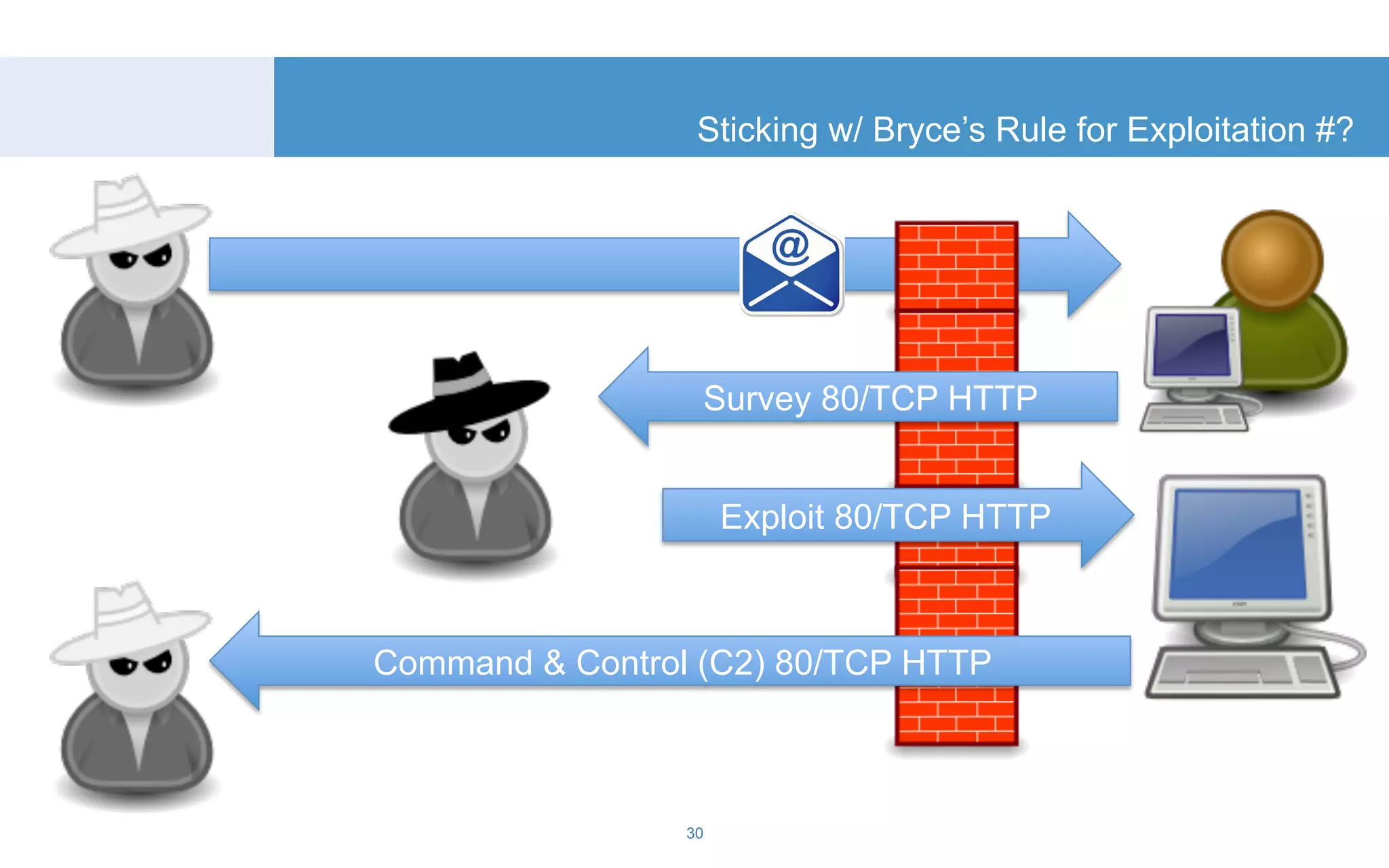
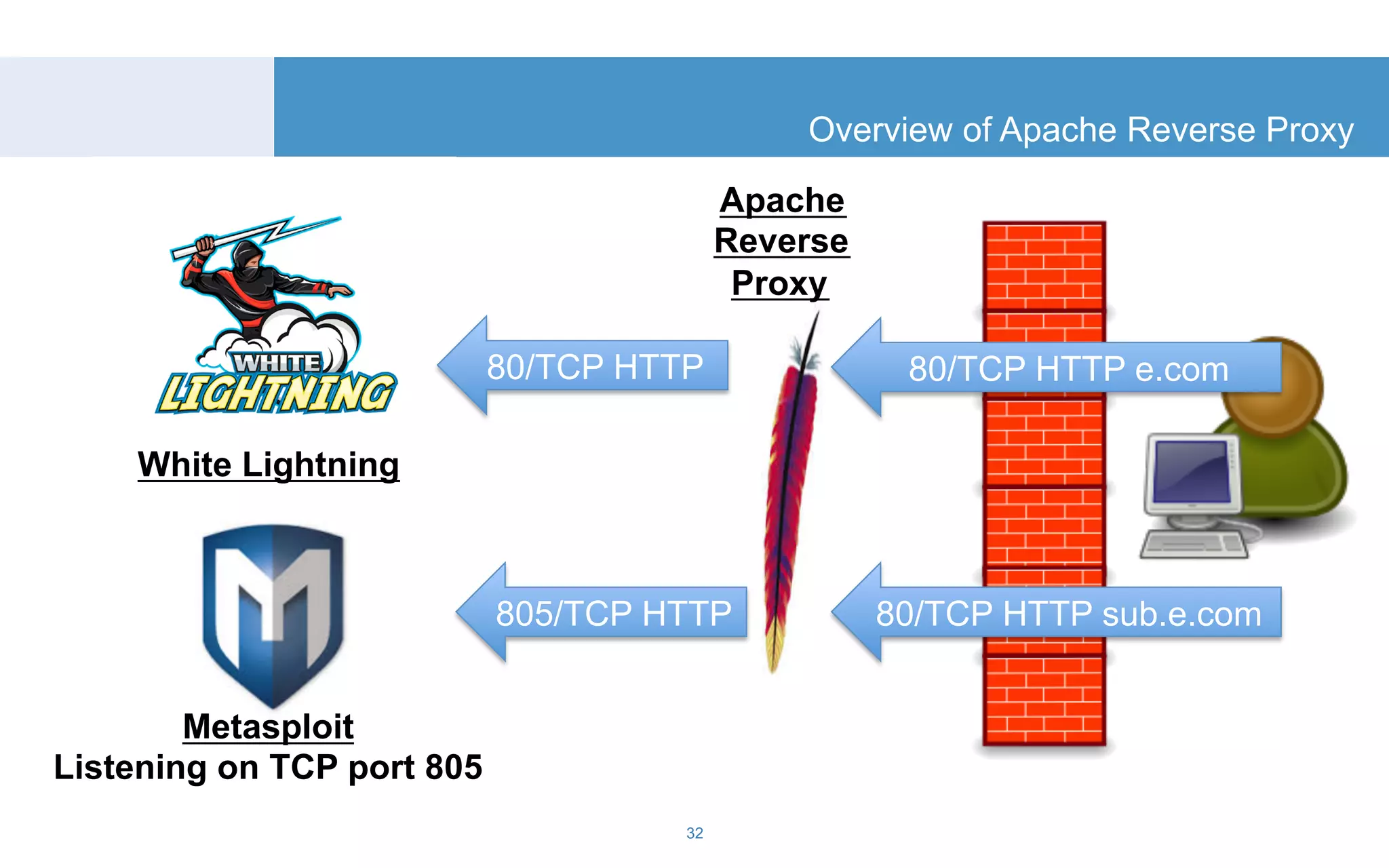
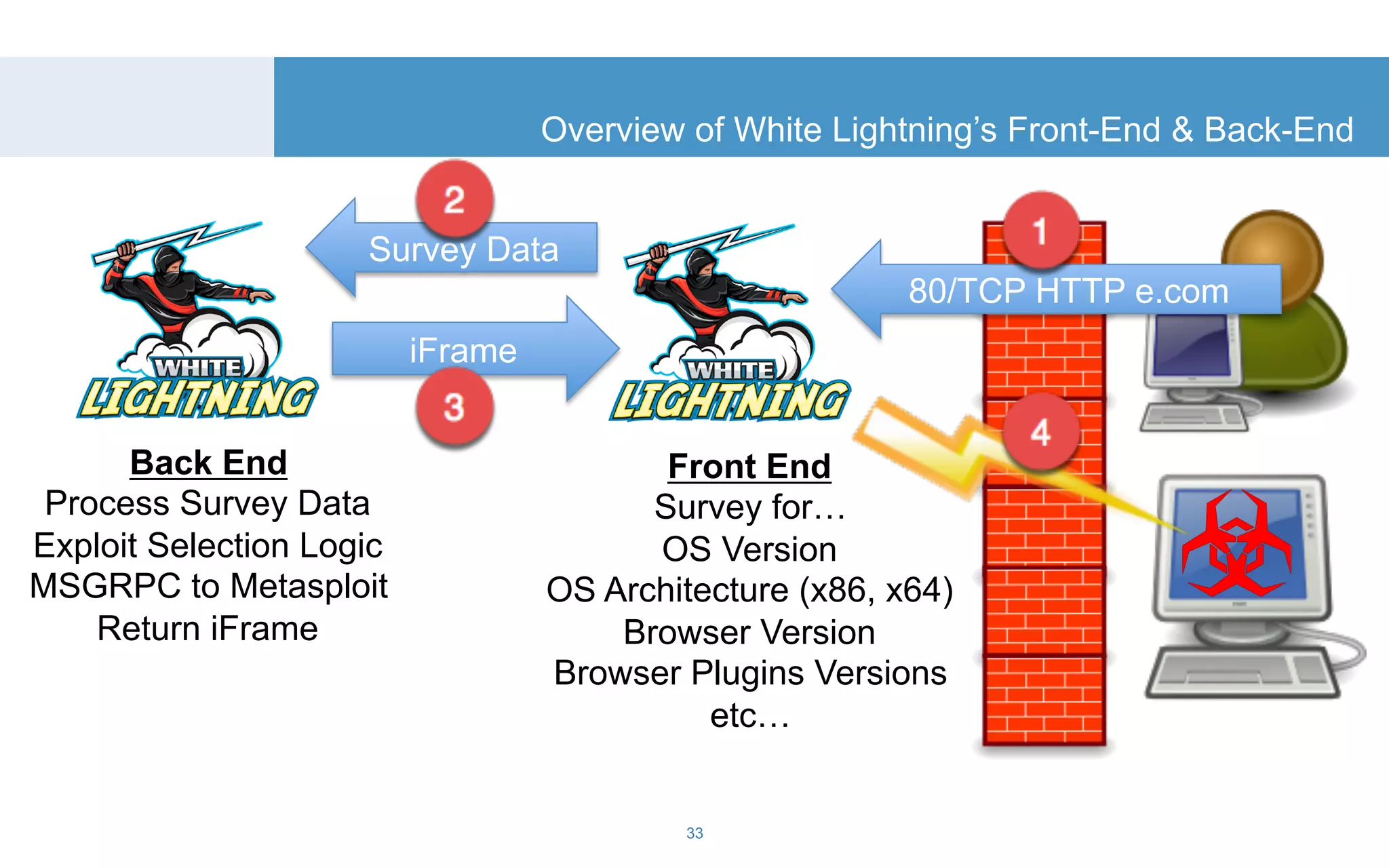
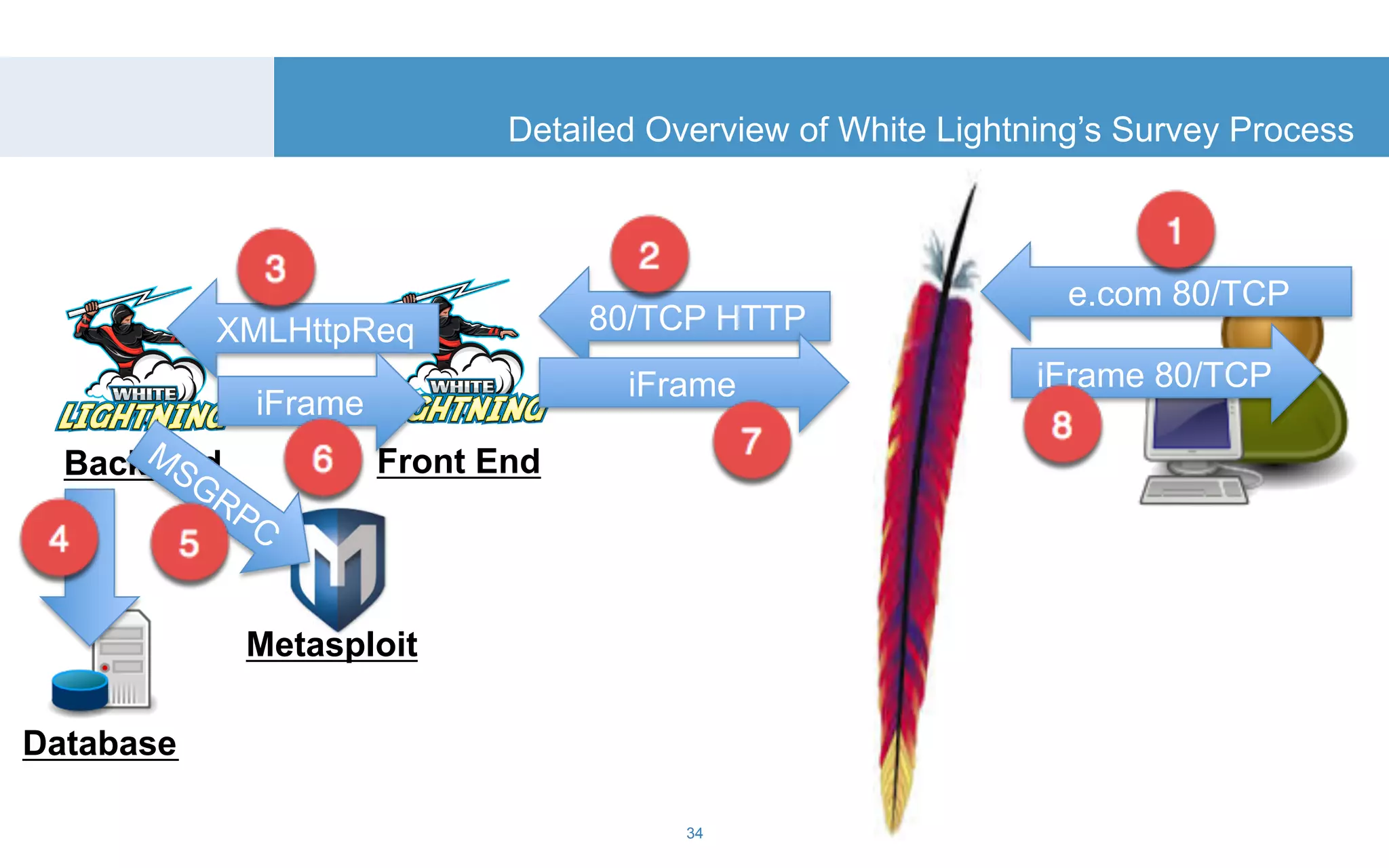
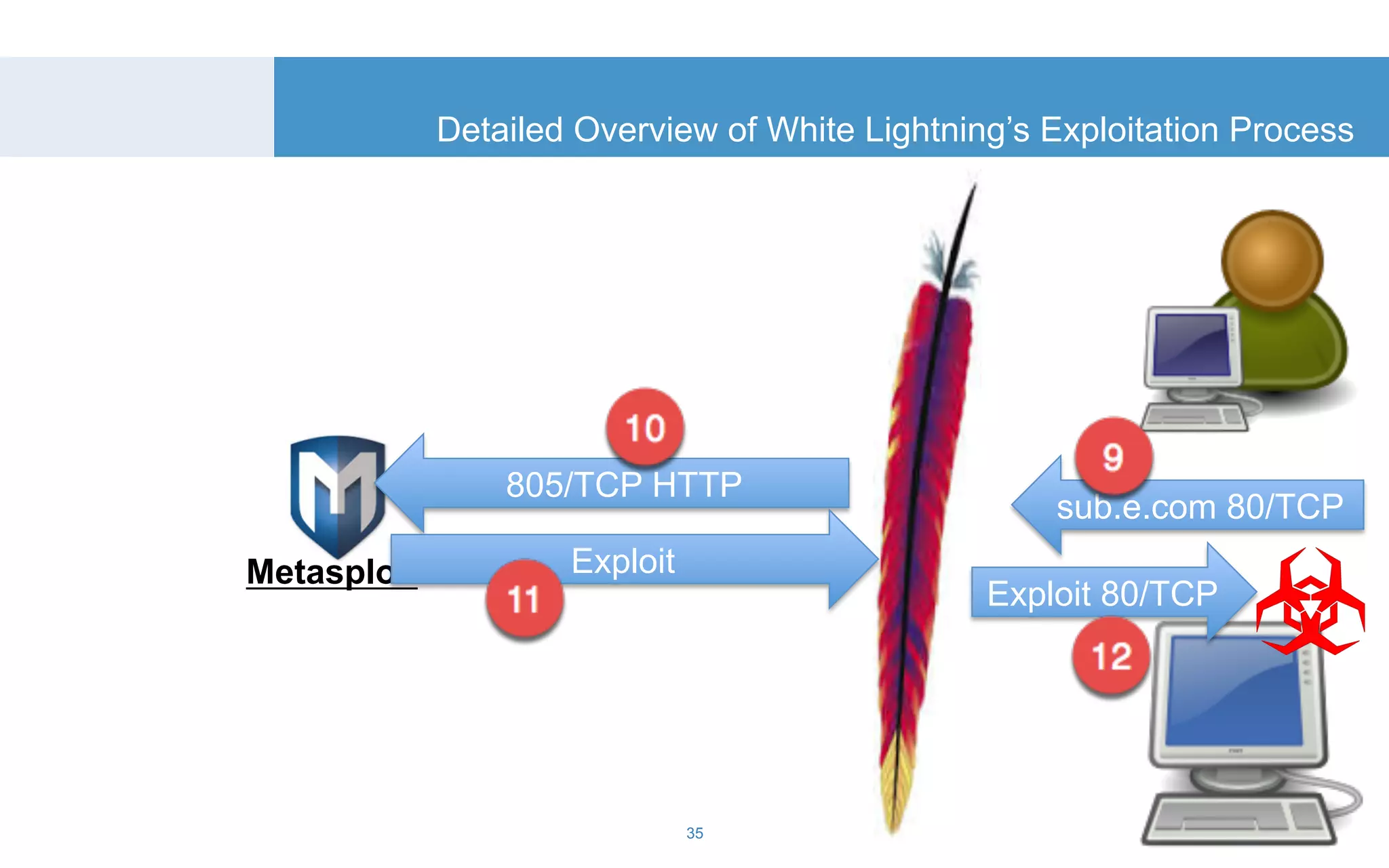
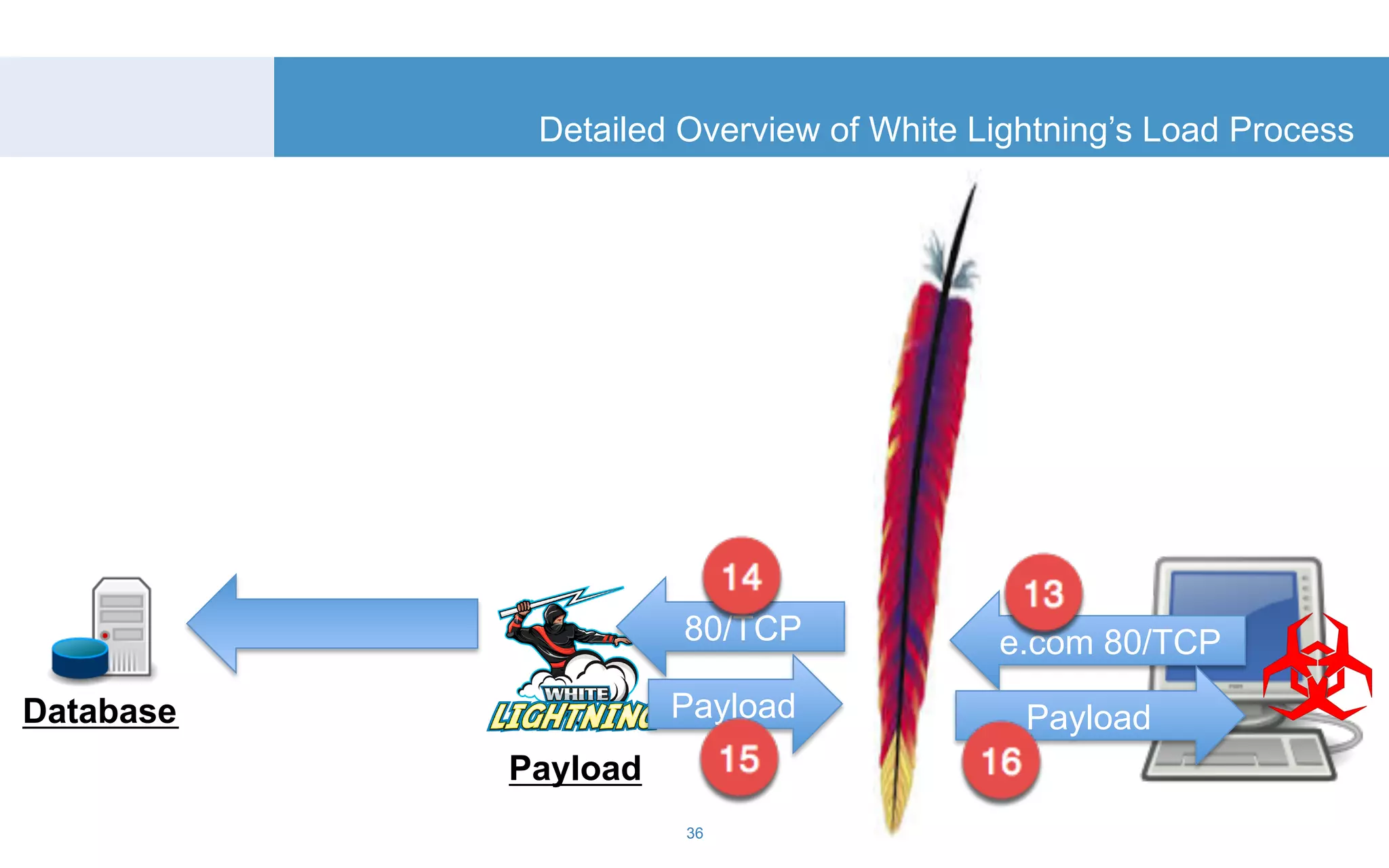
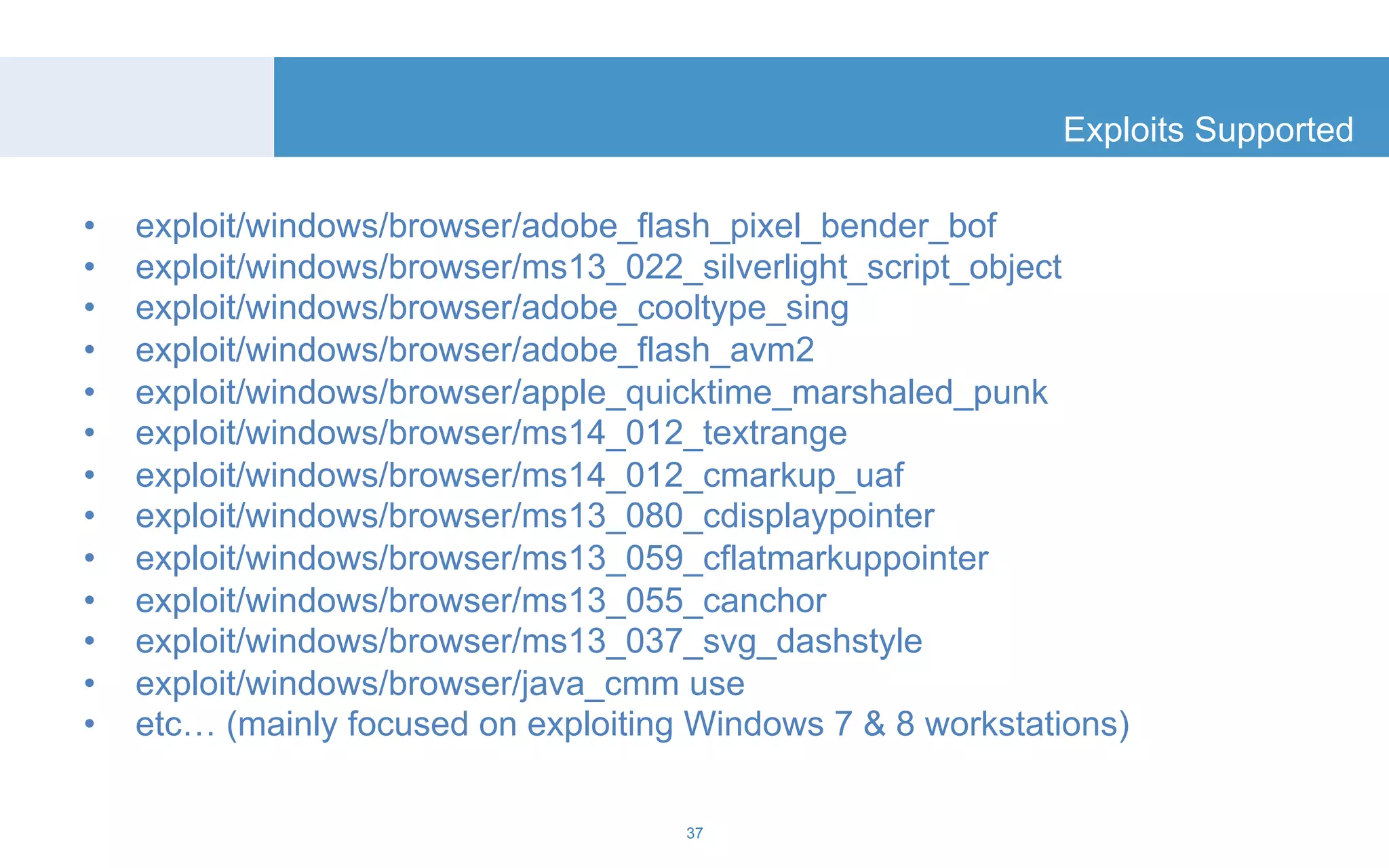
The document discusses a tool called White Lightning, which is a platform for browser exploitation. It uses surveys and exploits delivered over HTTP to compromise endpoints without requiring any downloads. The tool integrates with Metasploit to select and run exploits, reusing ports and protocols to maintain communication. Details are provided on its architecture, exploitation process, and supported exploits. A demo is shown and future development plans outlined.