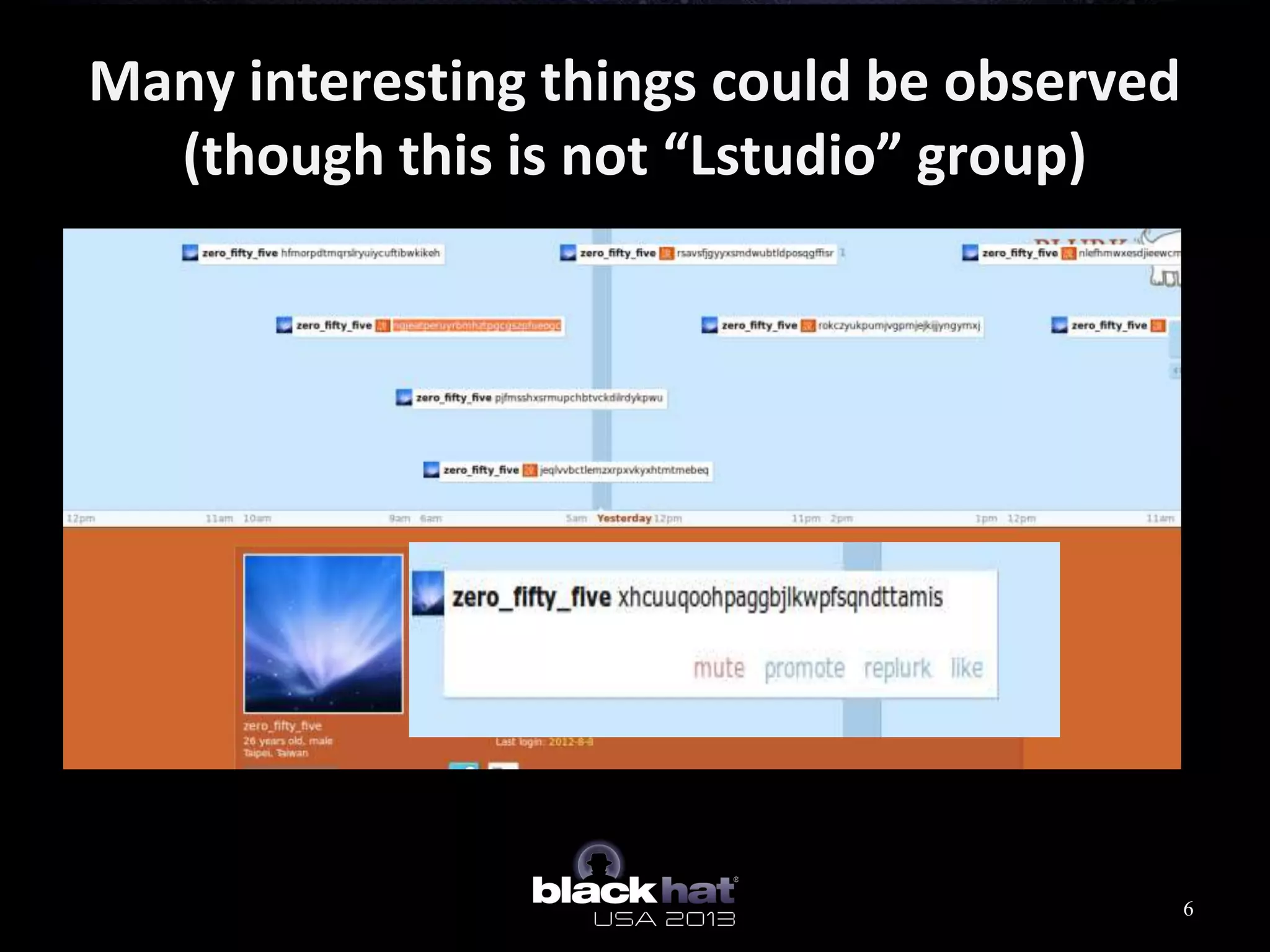
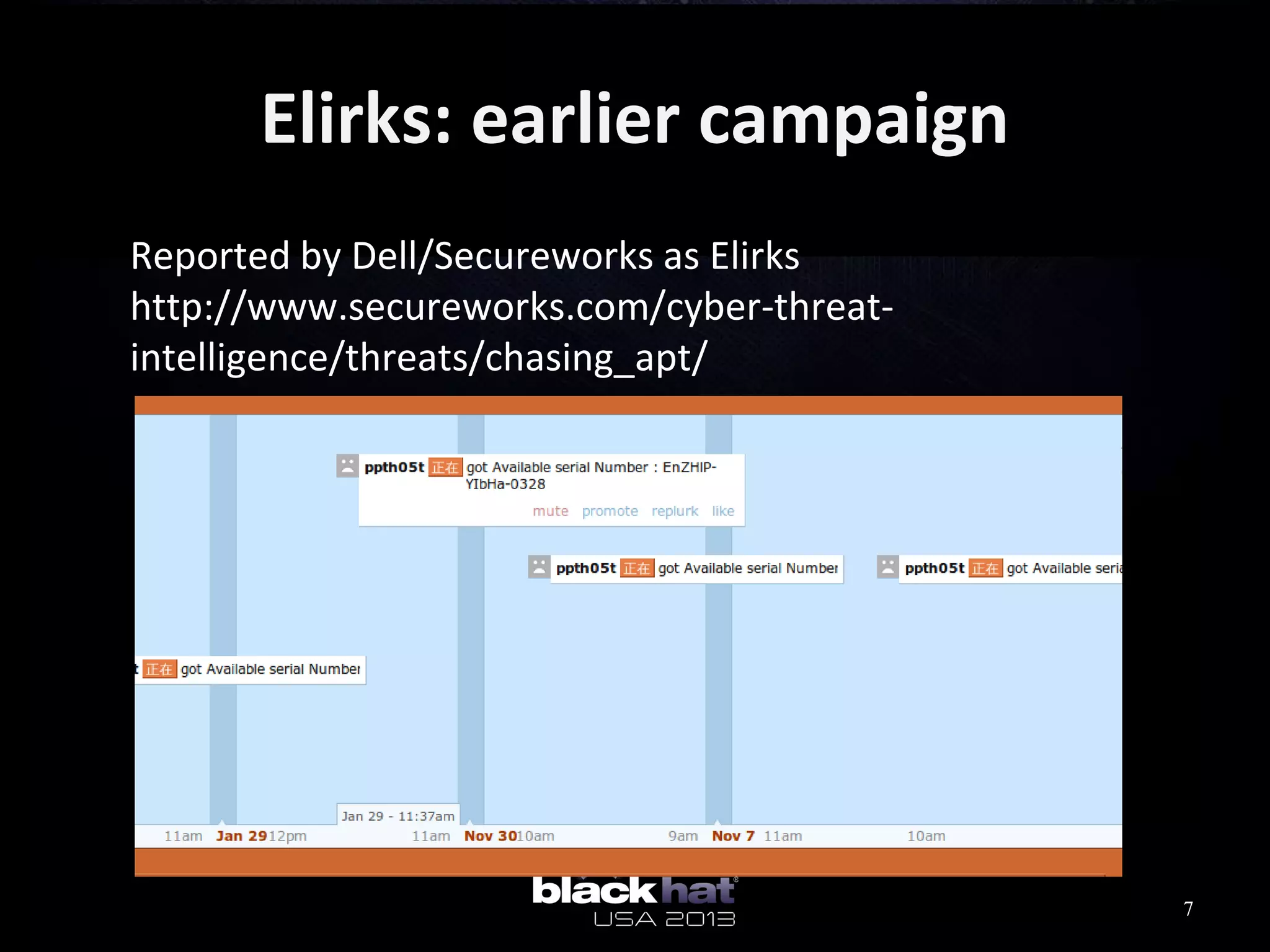
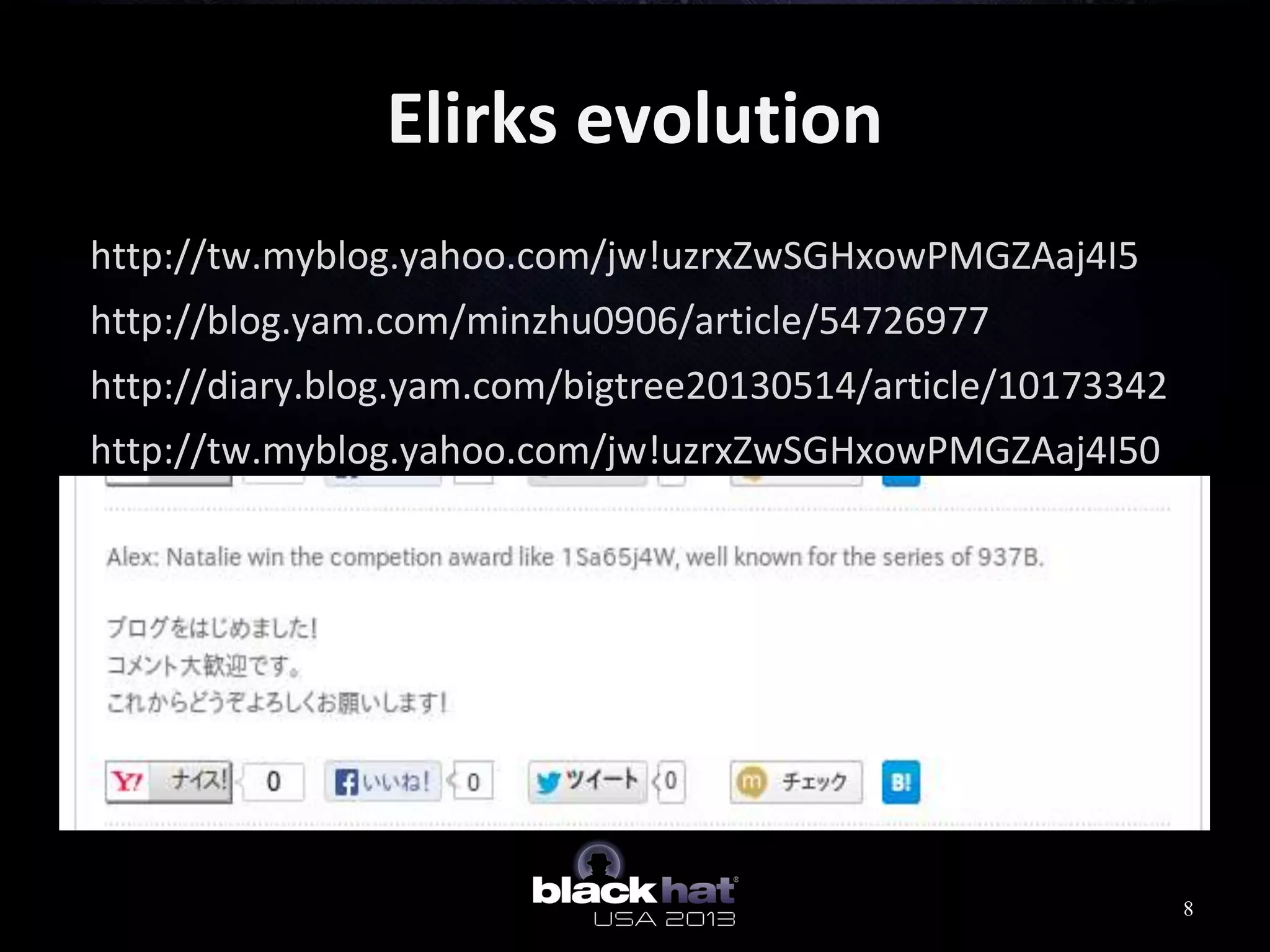
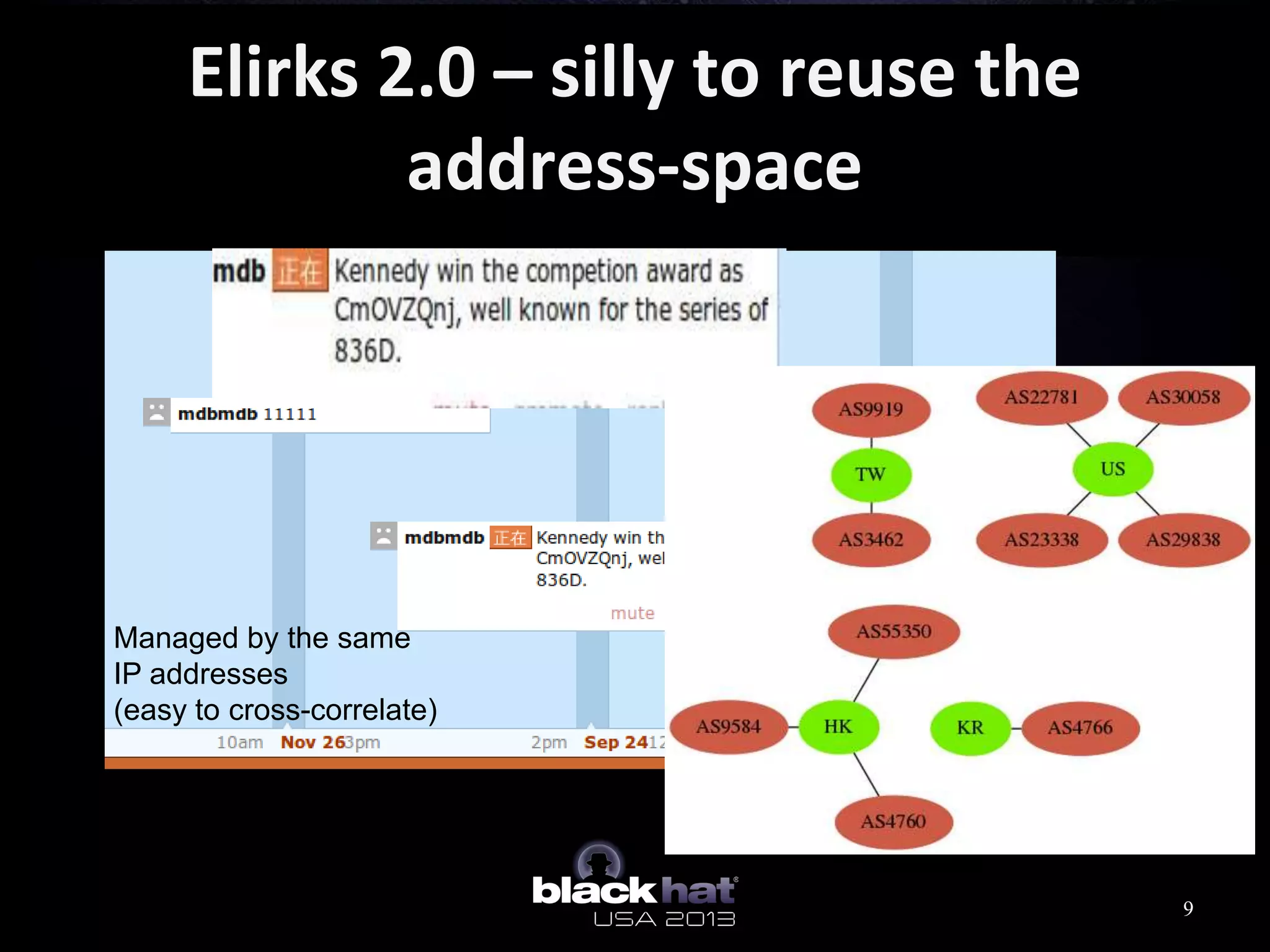
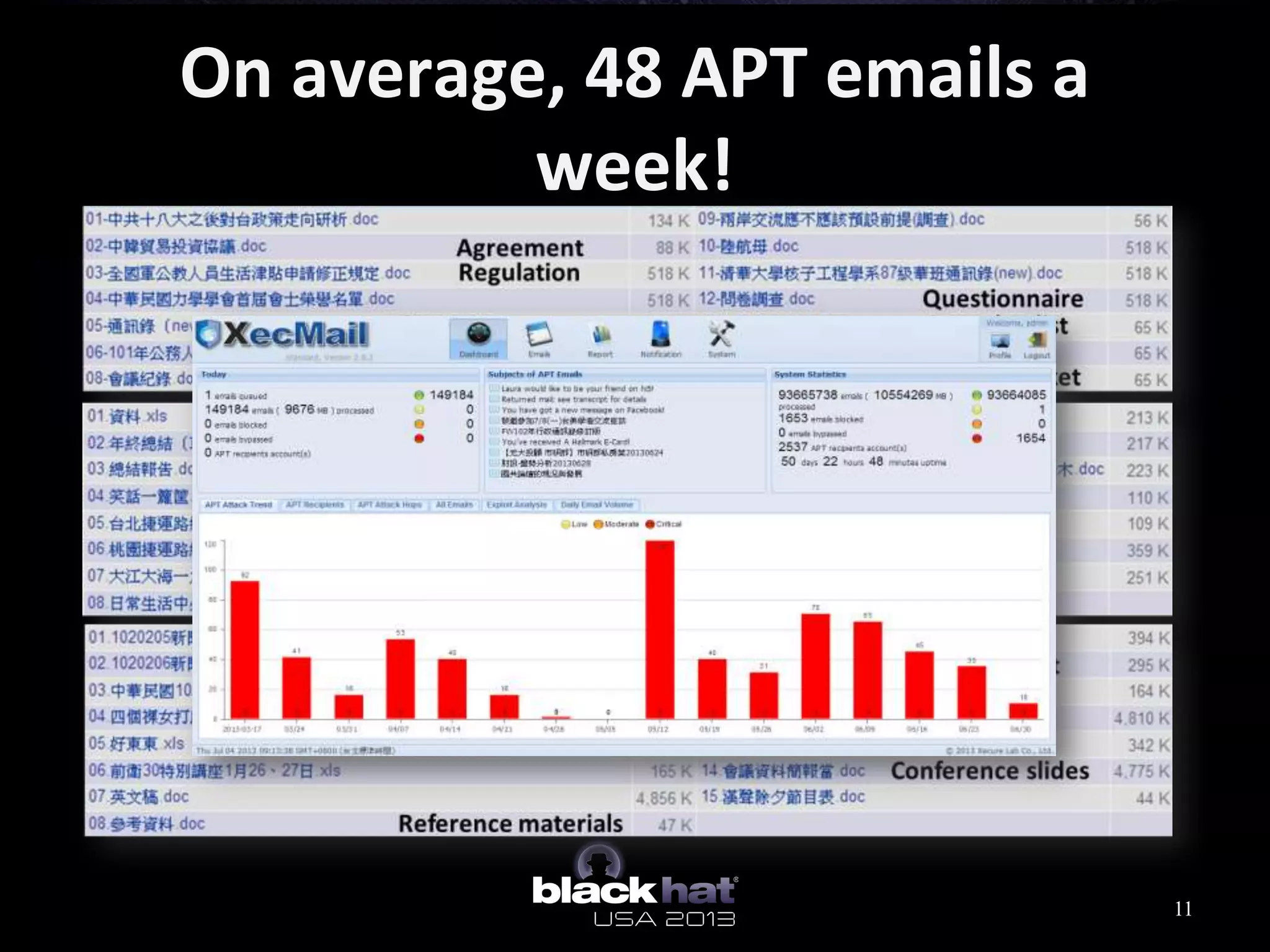
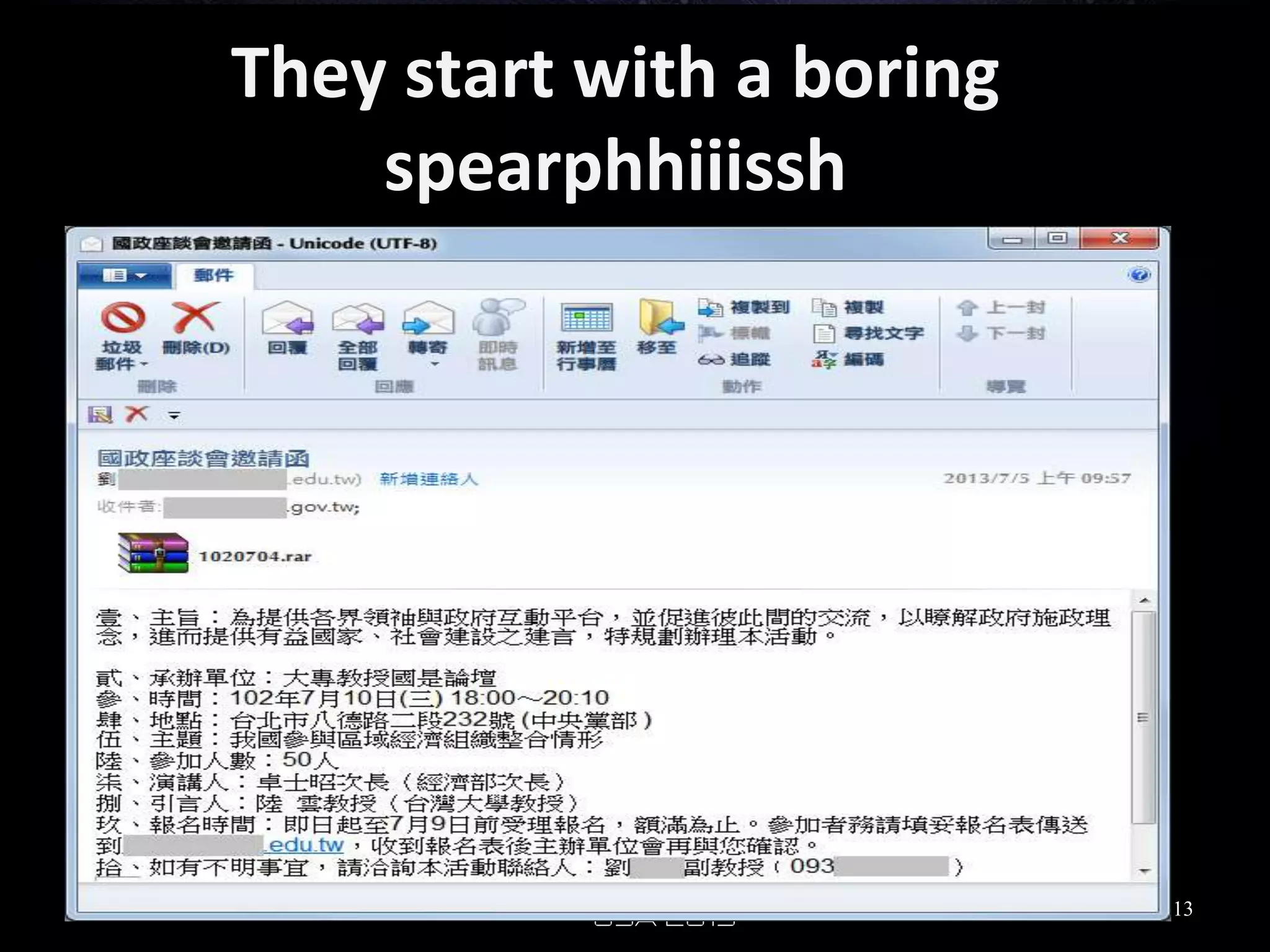
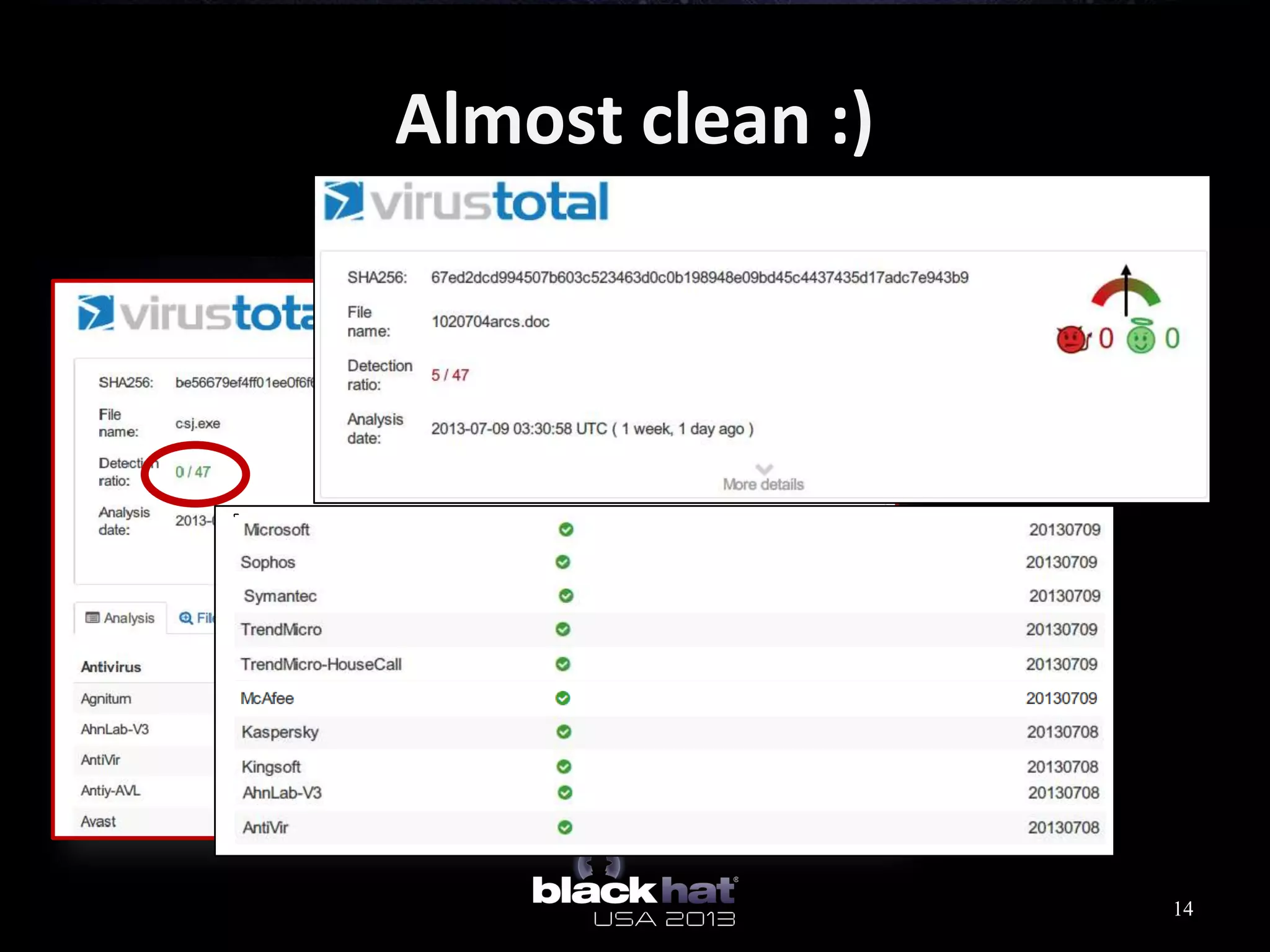
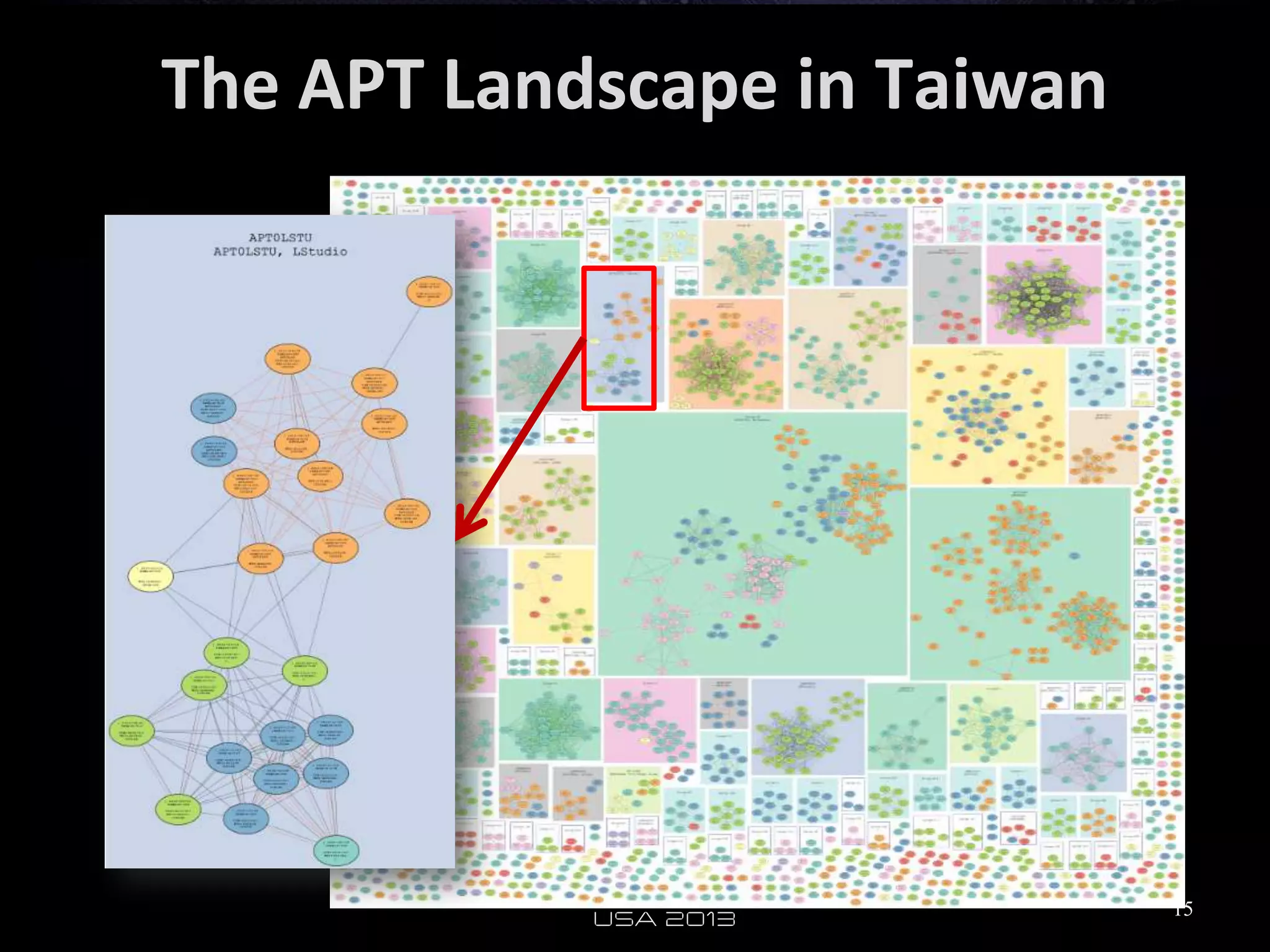
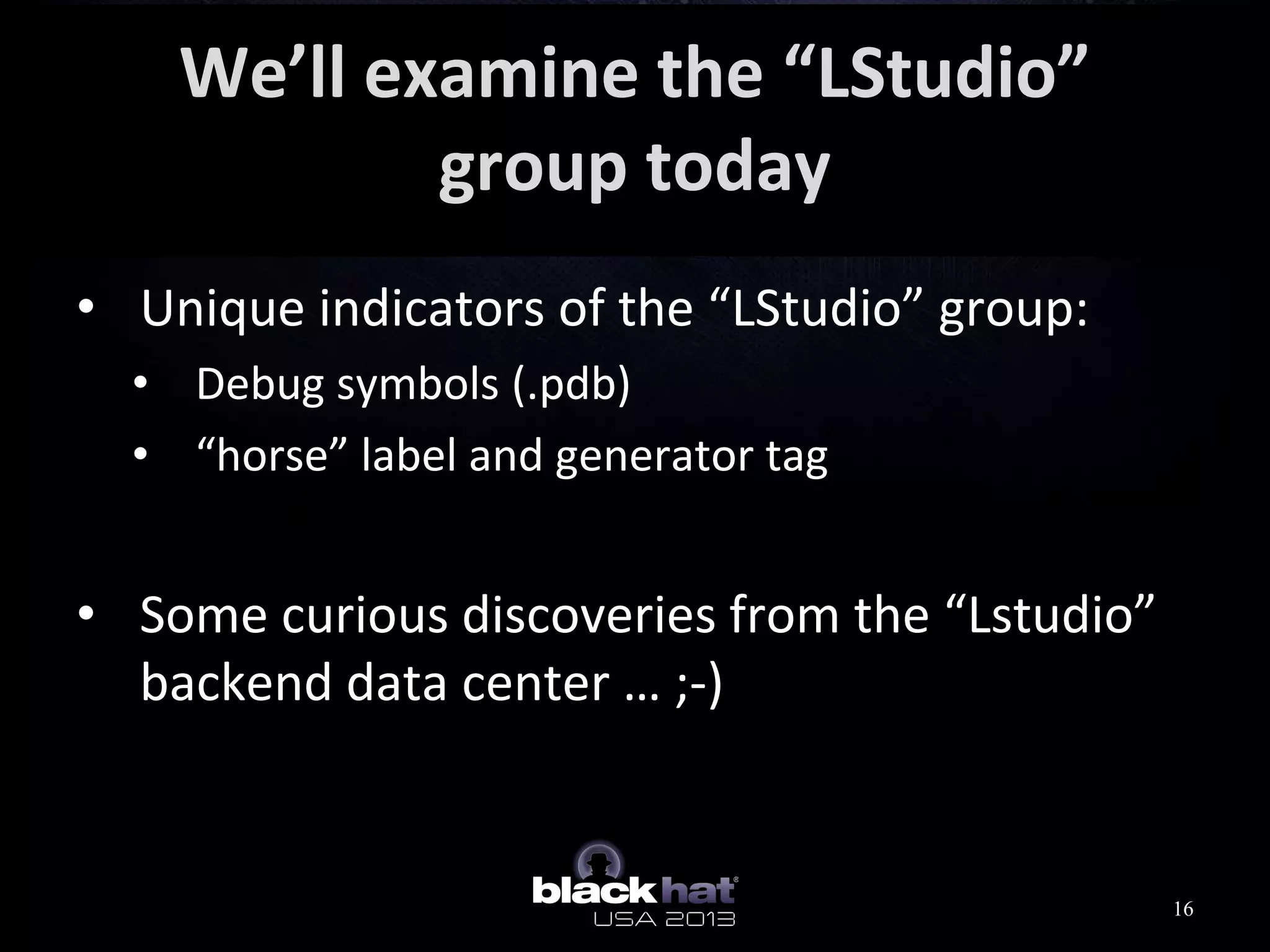
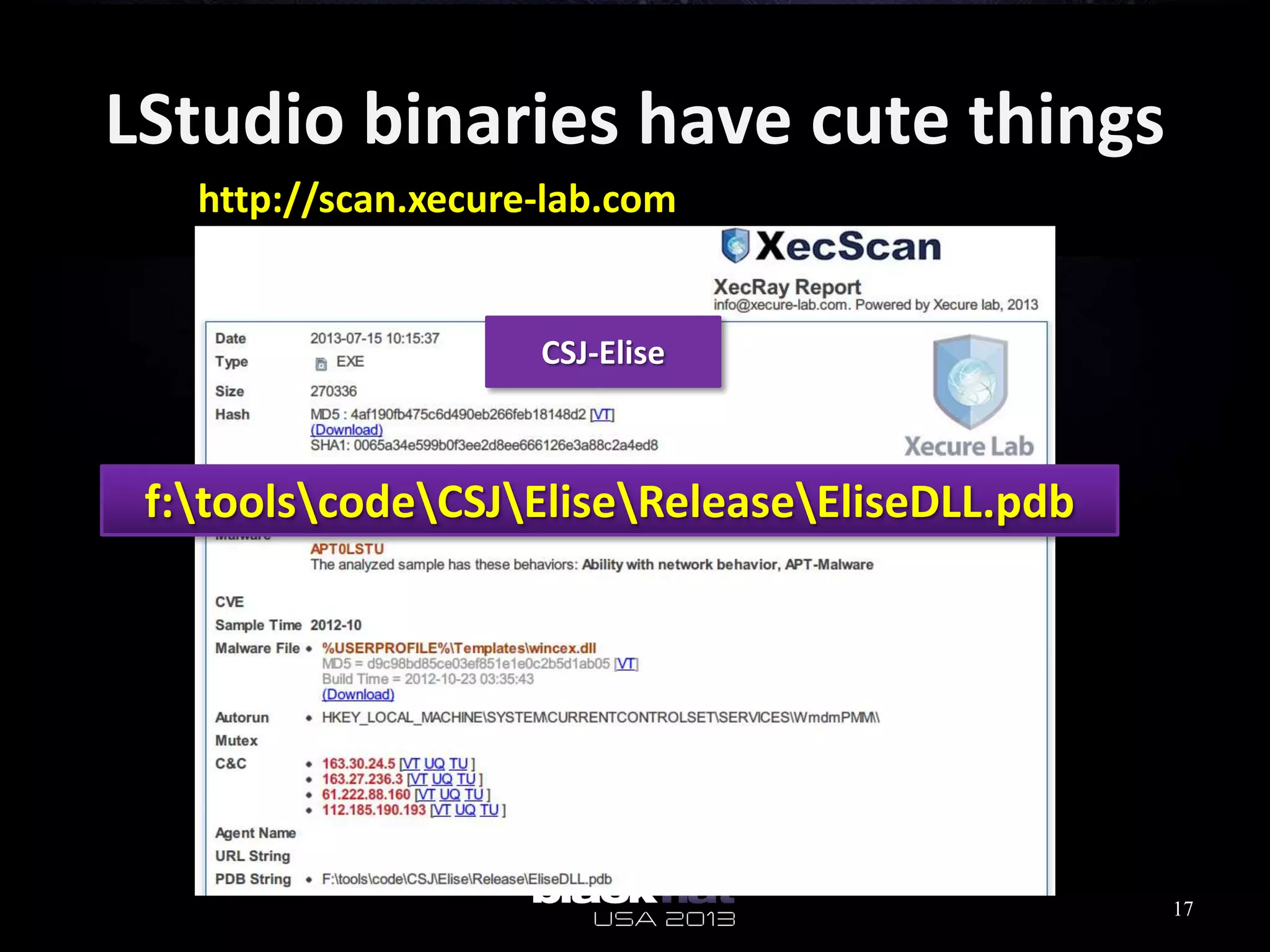
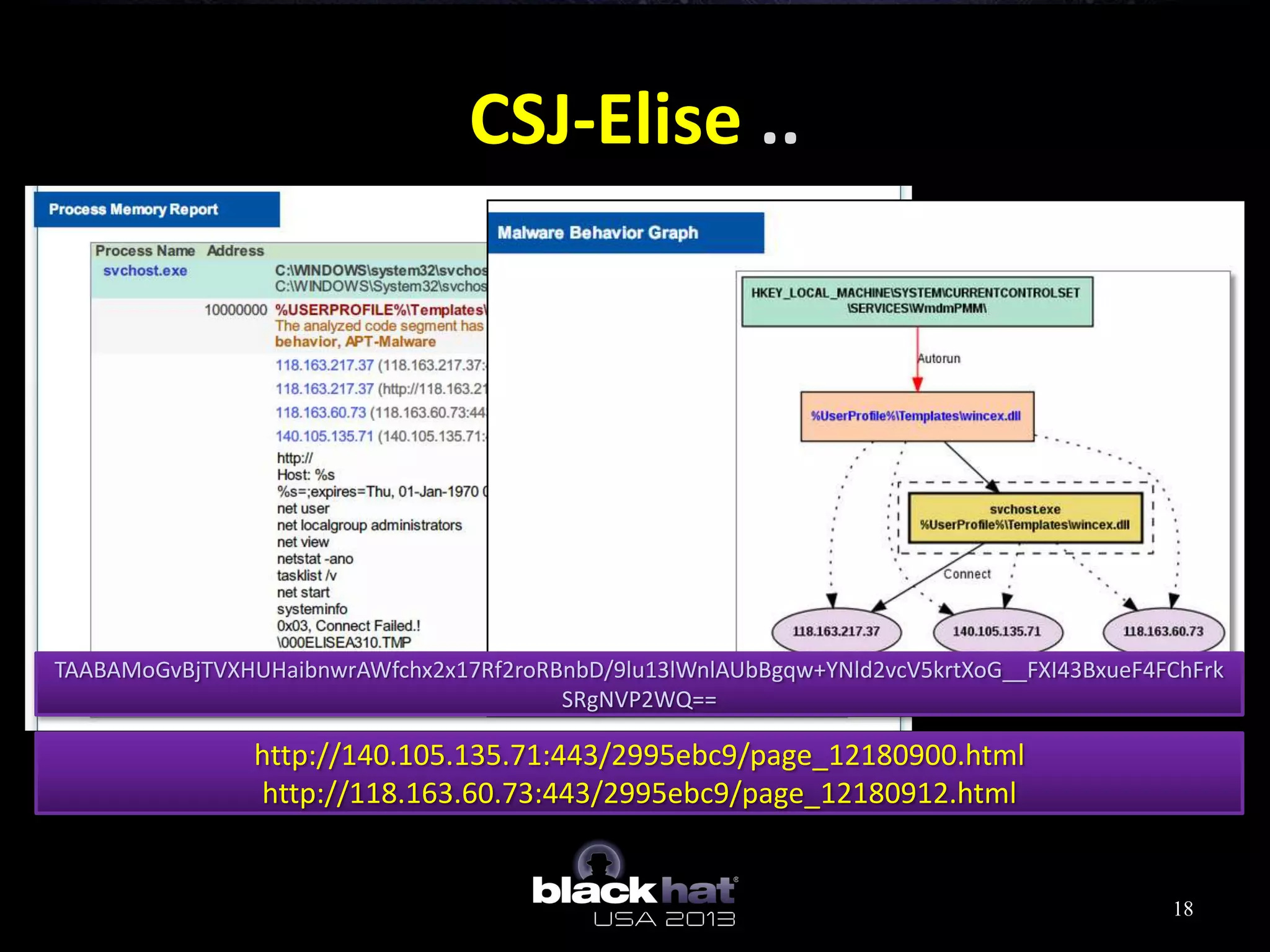
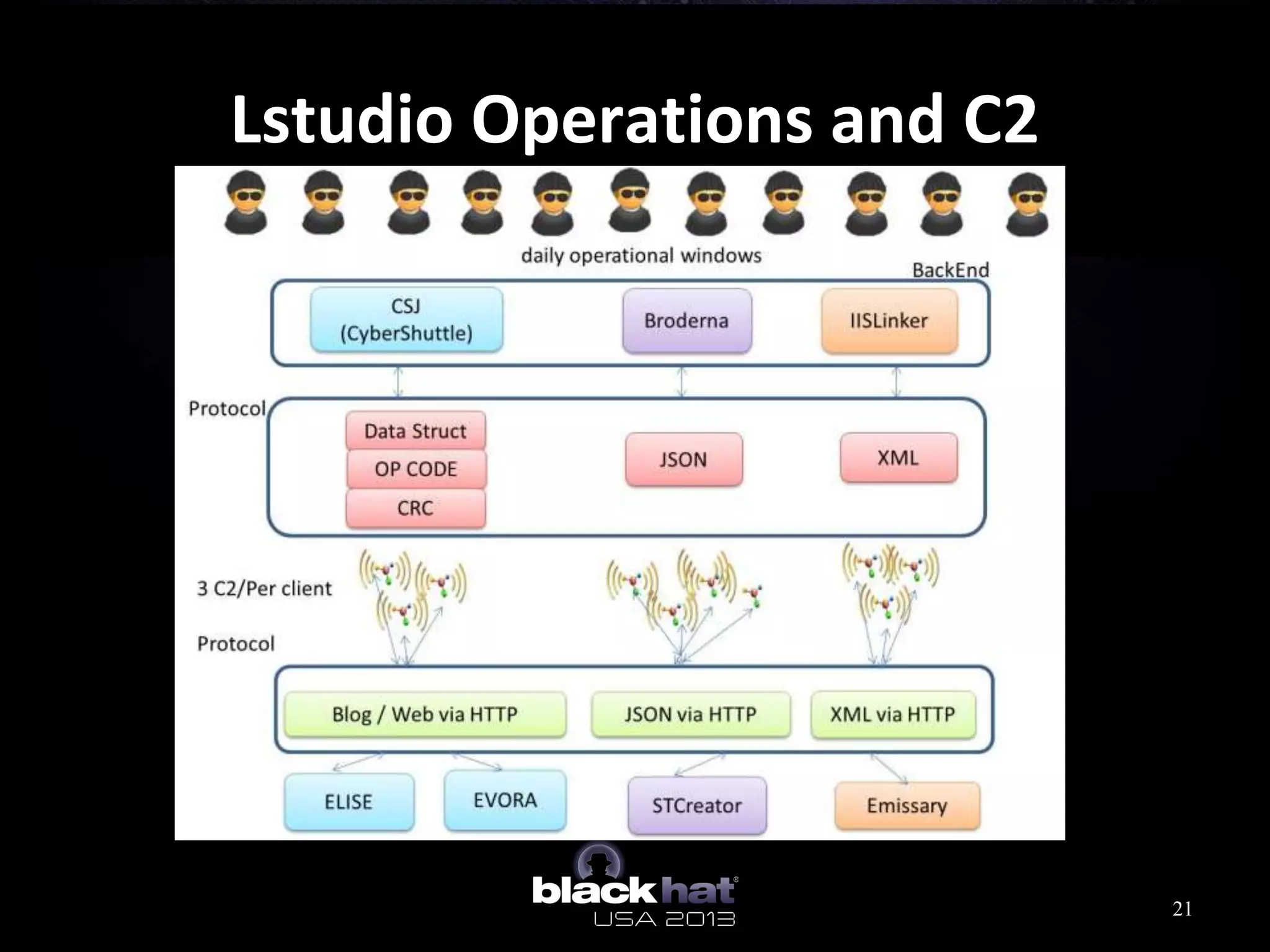
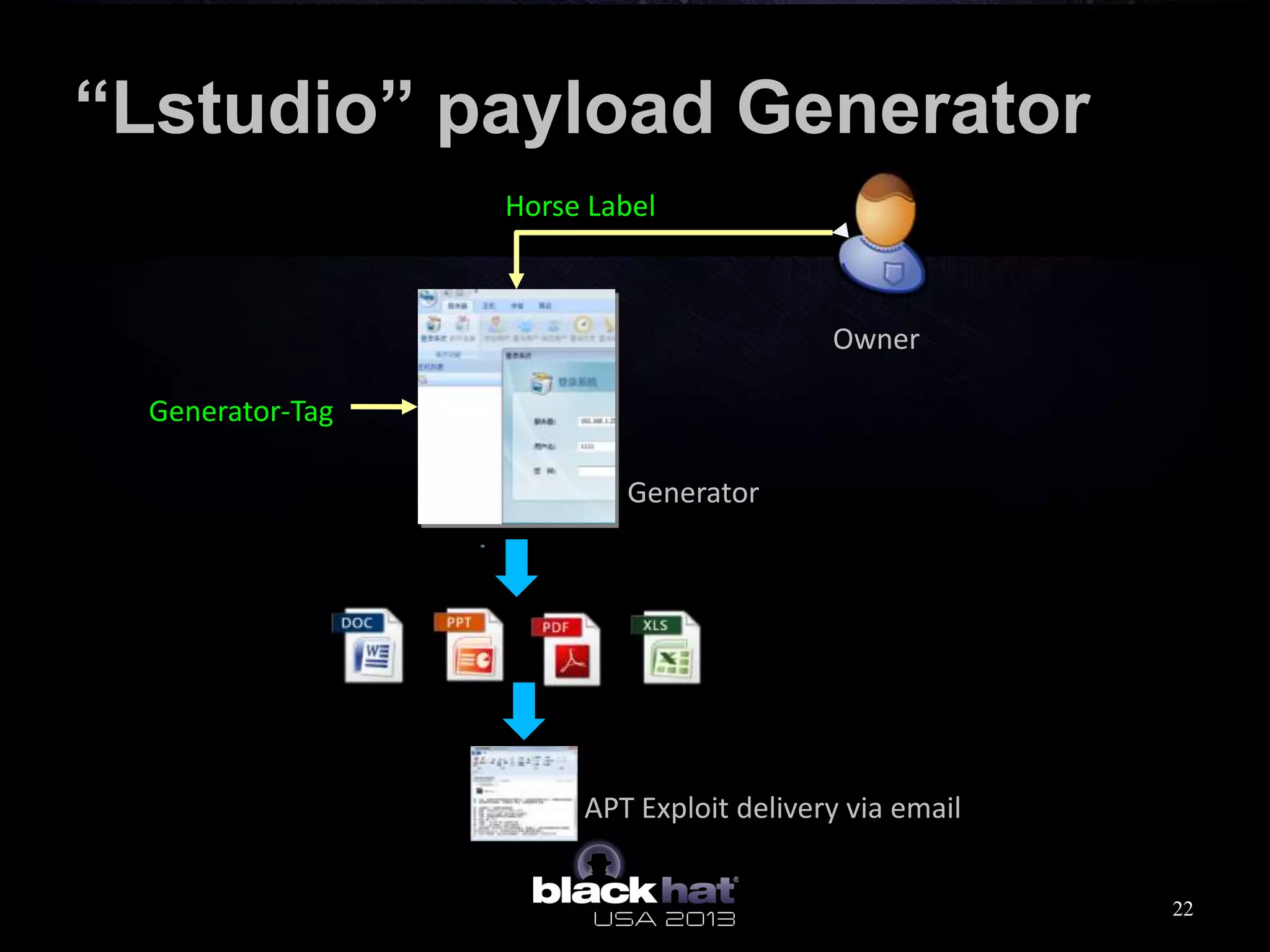
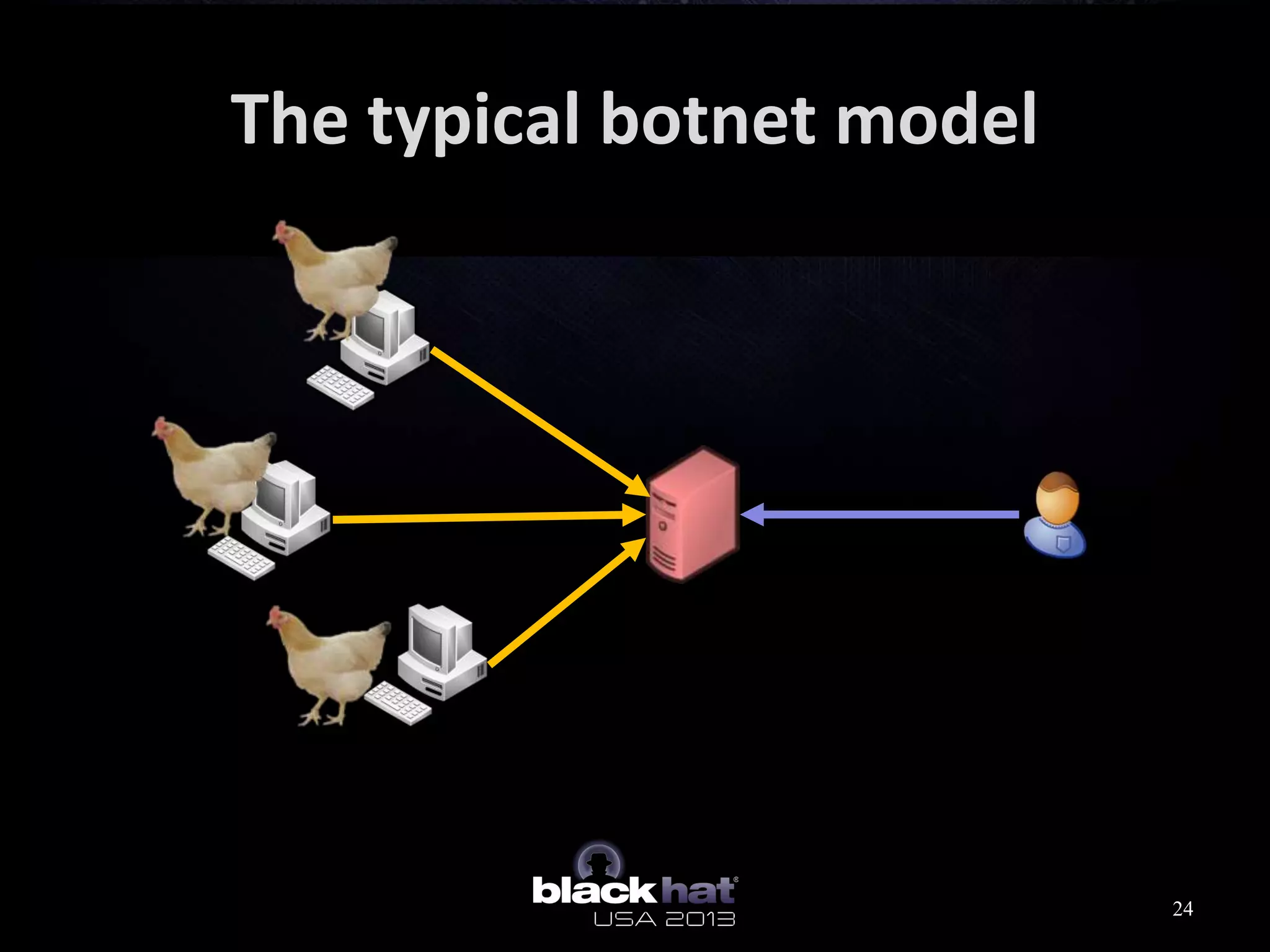
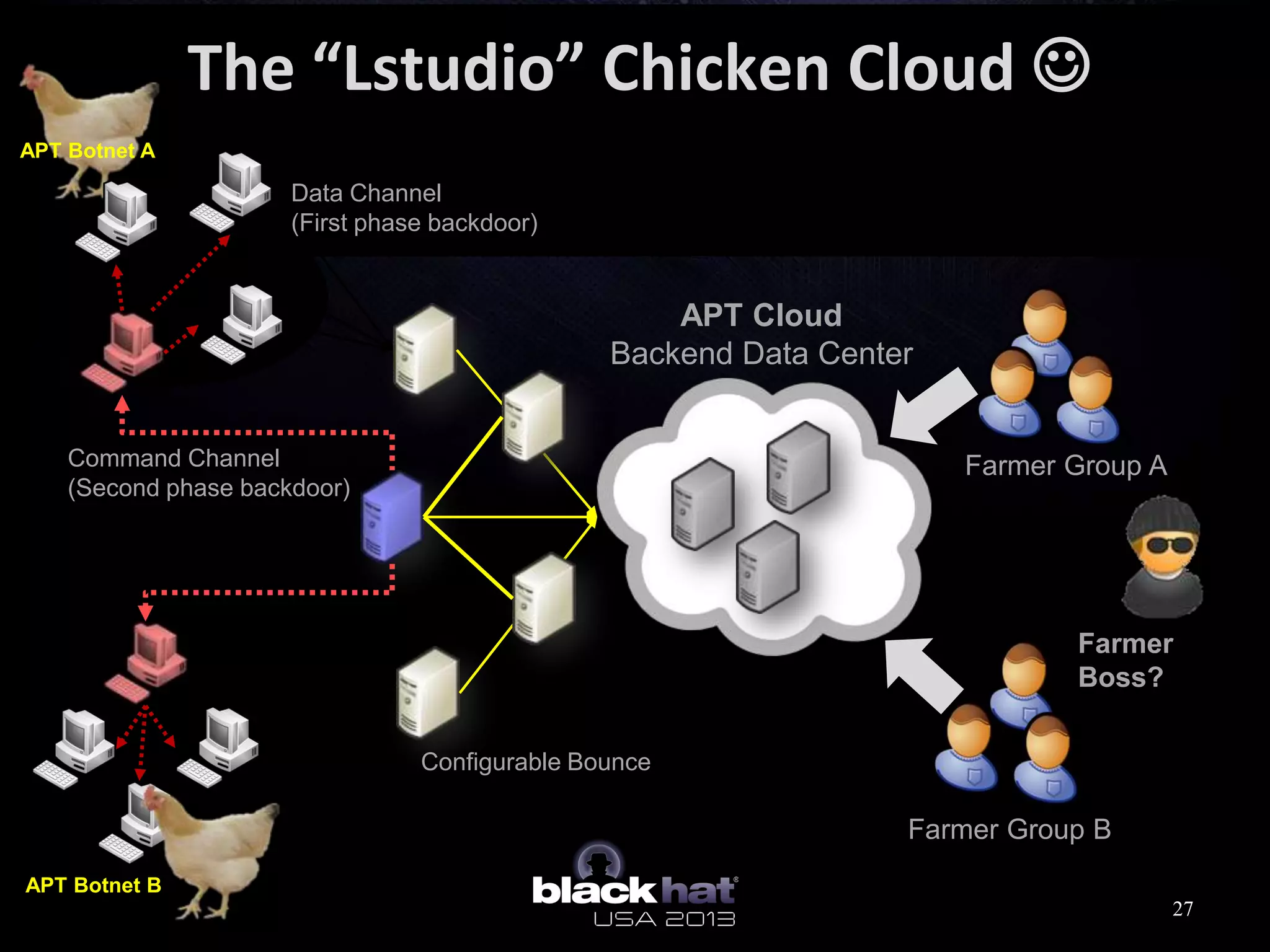
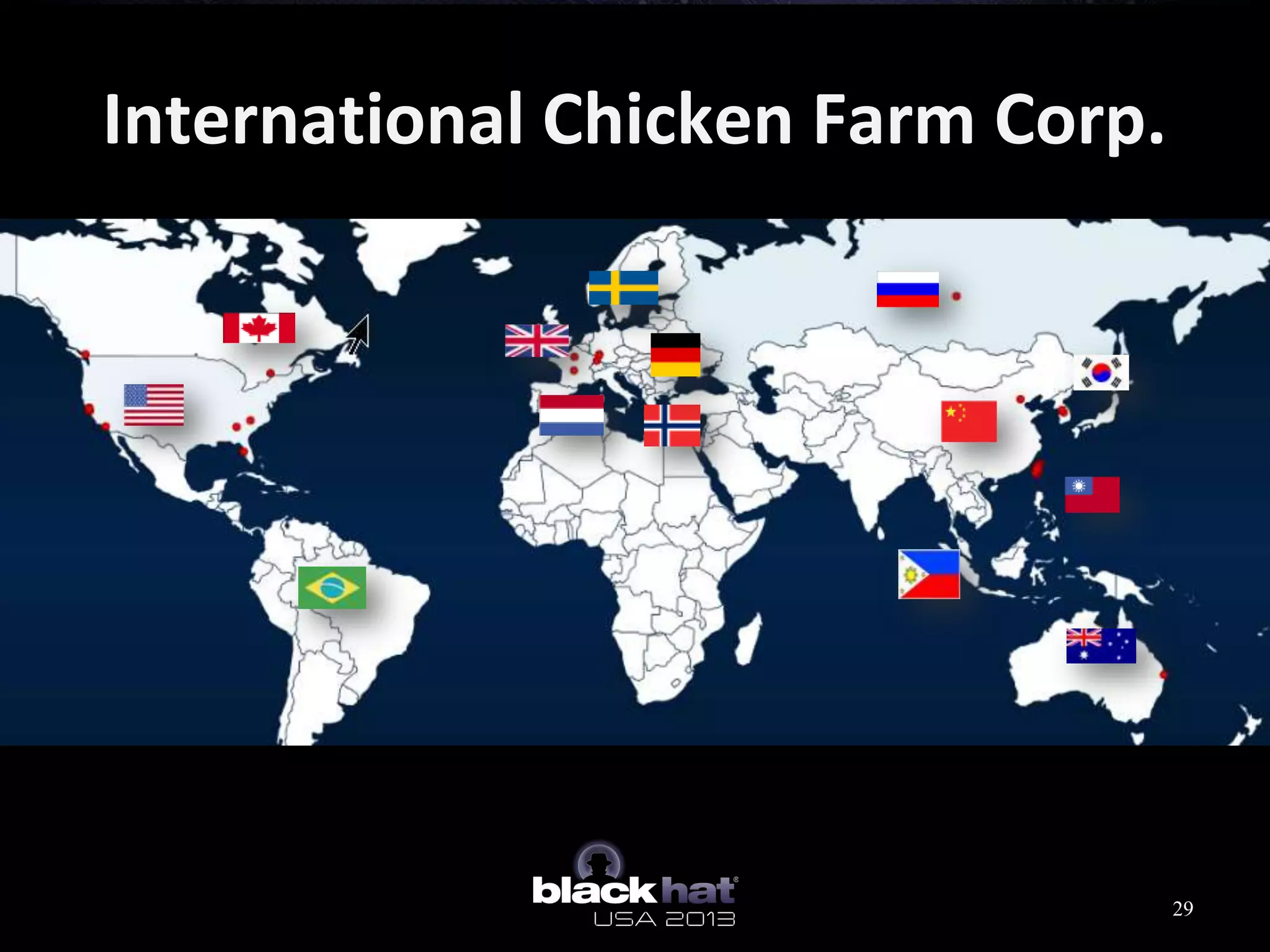
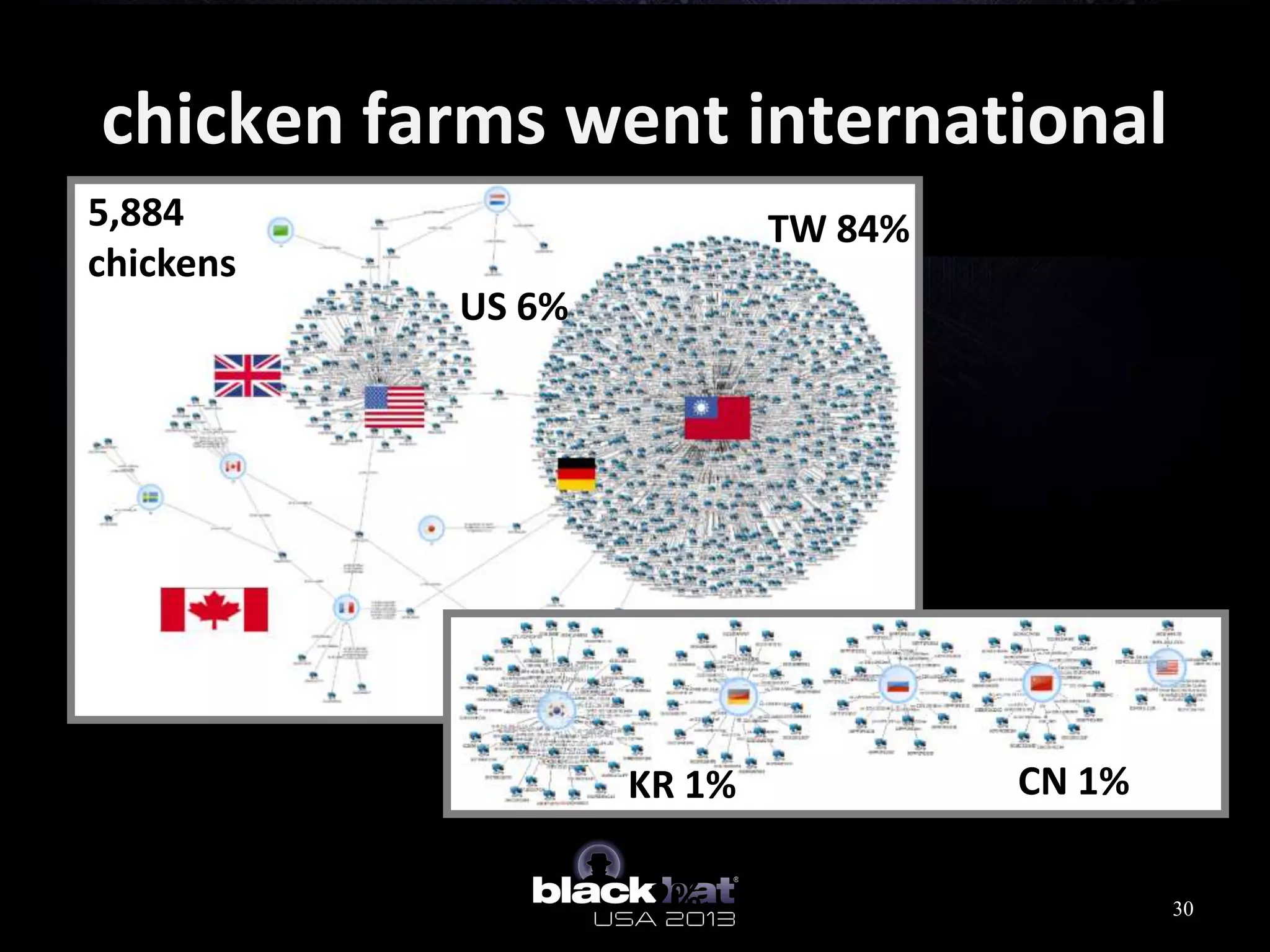
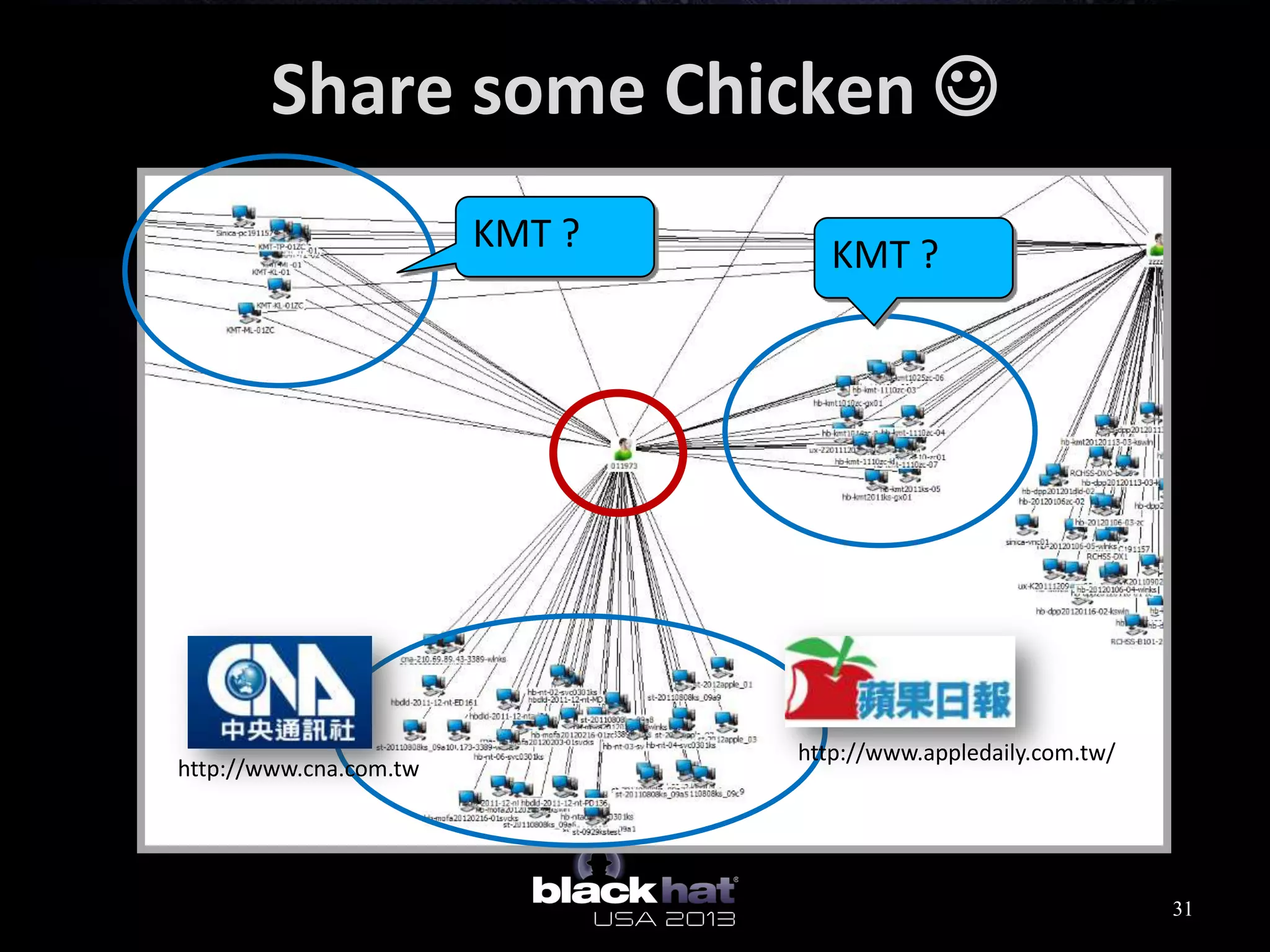
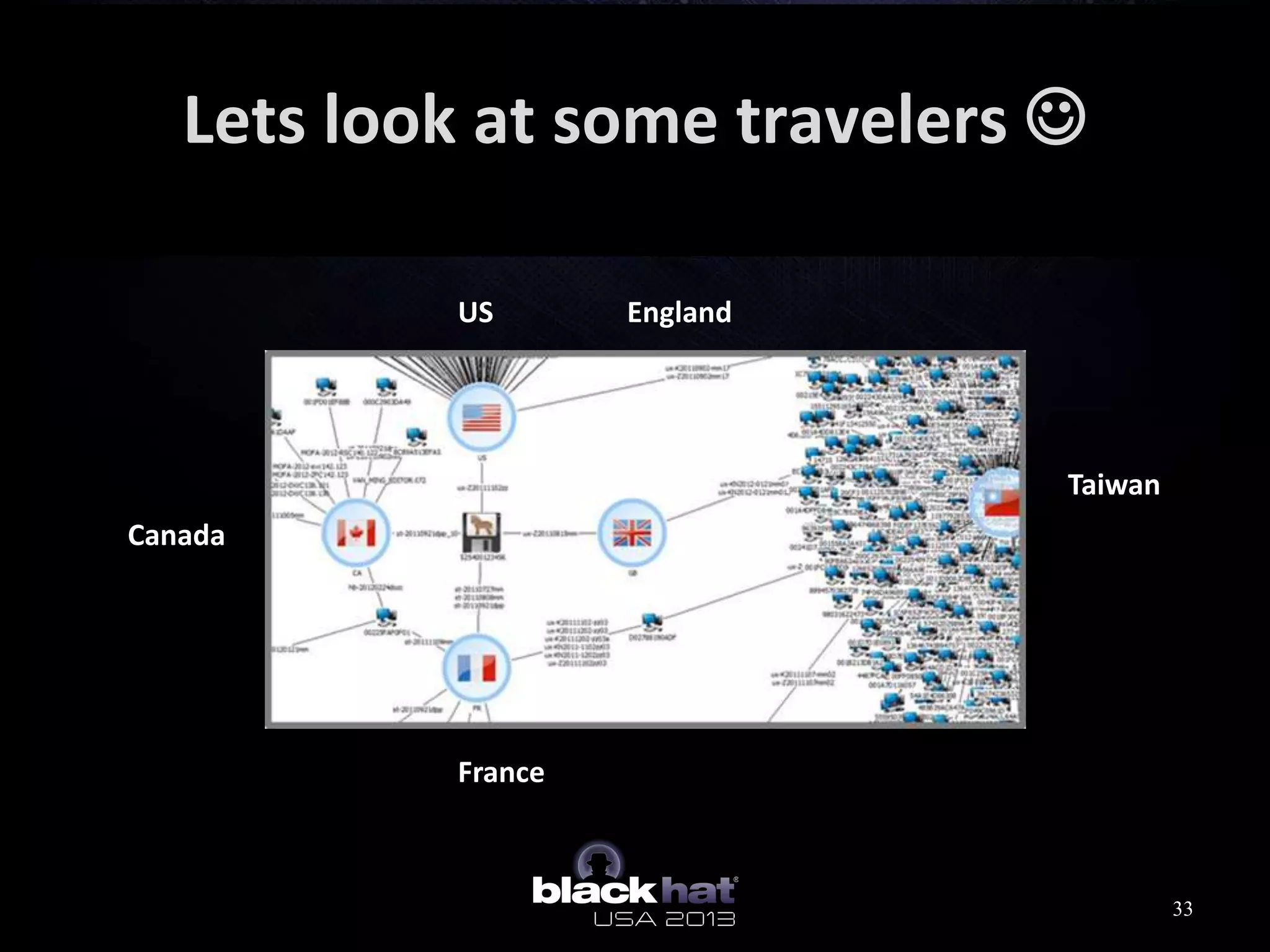
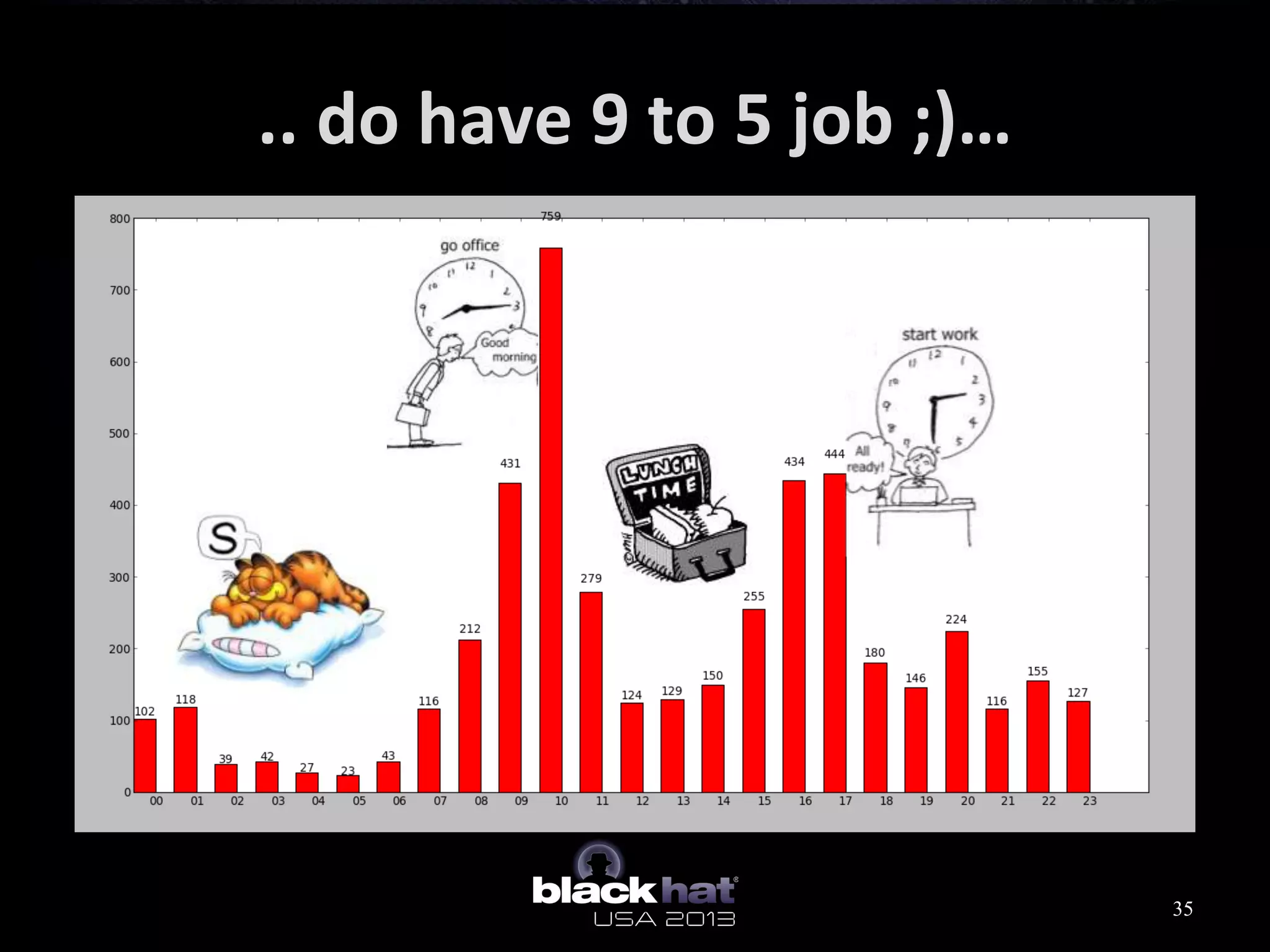
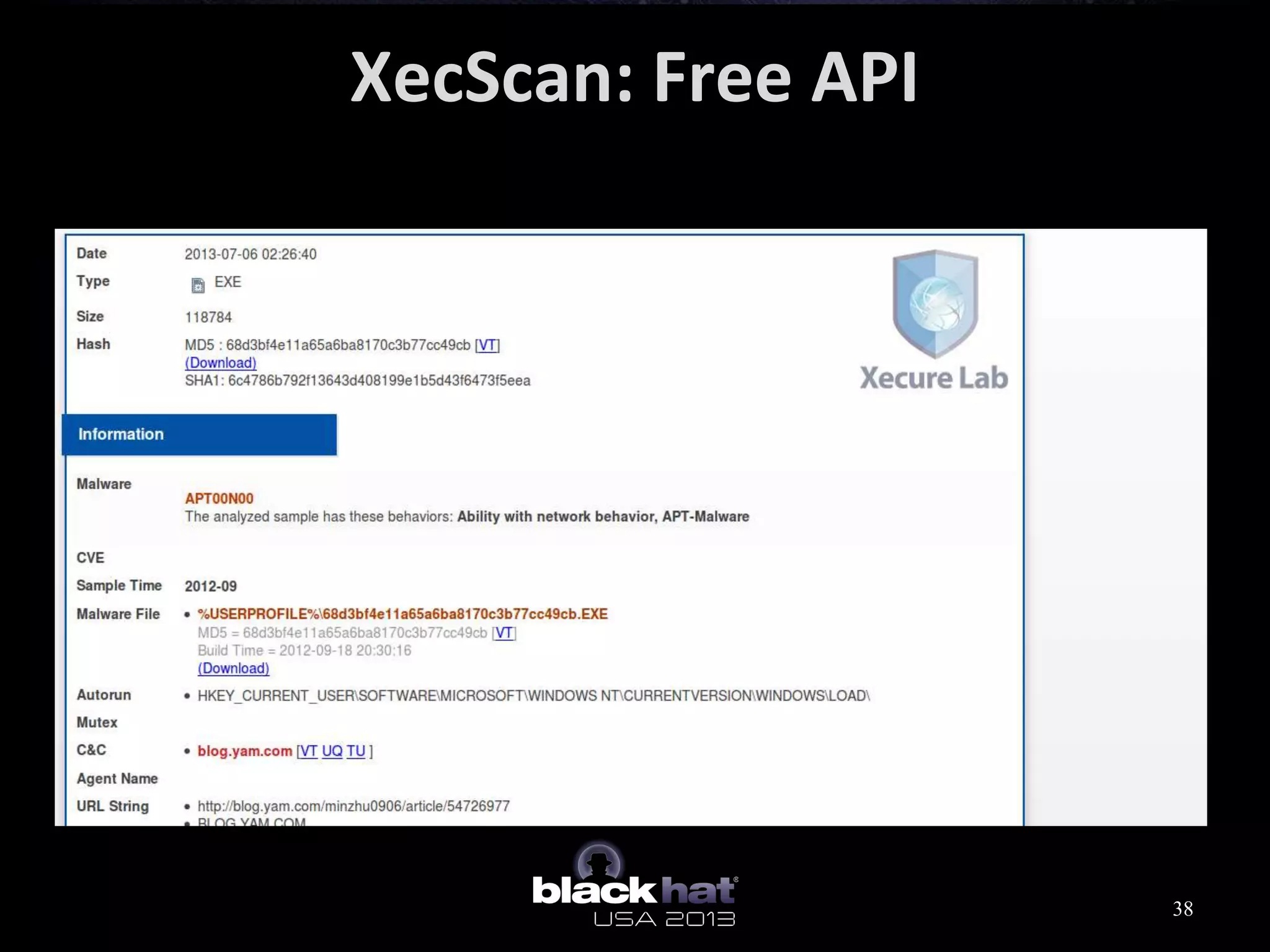
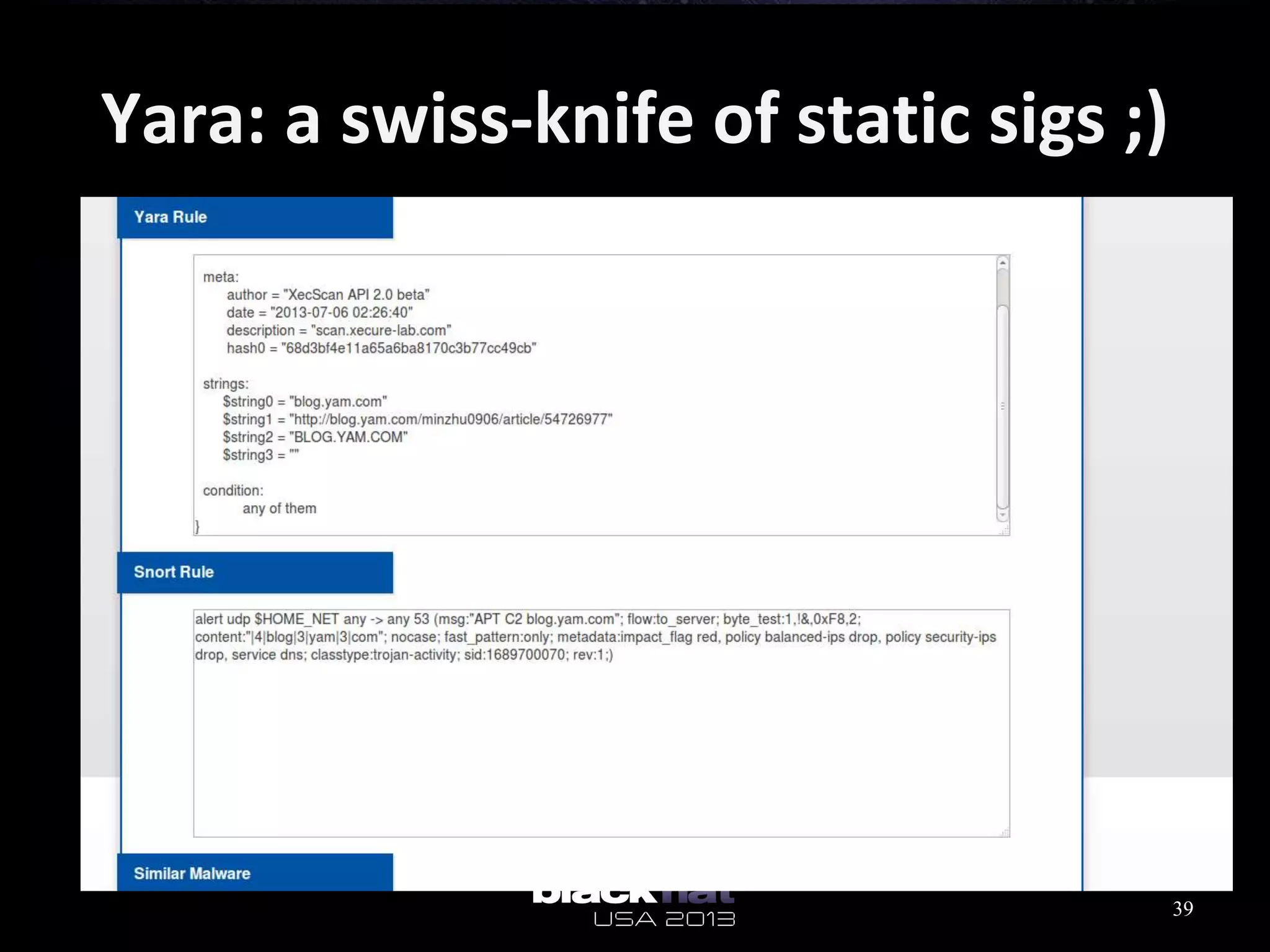
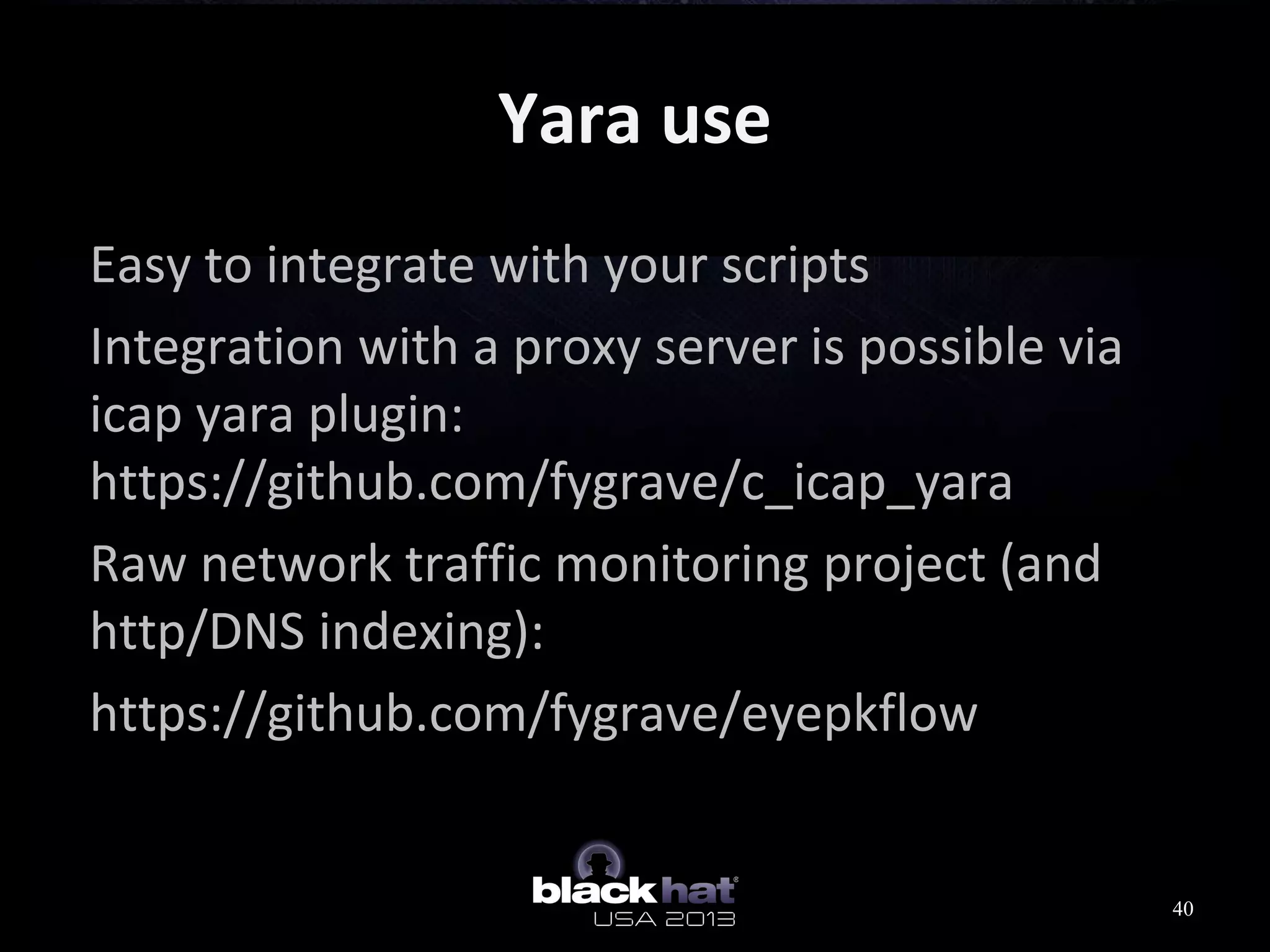
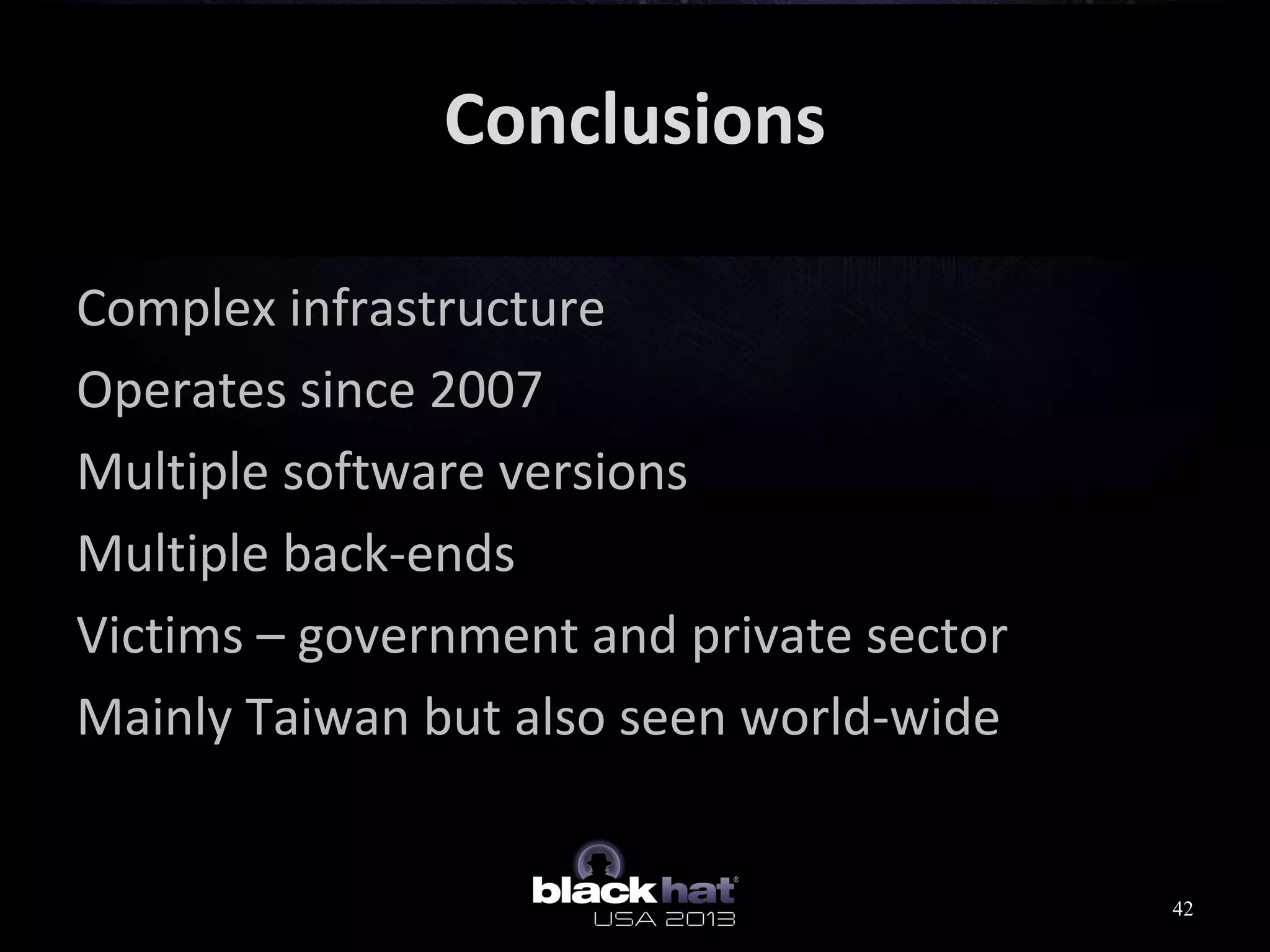
This document analyzes advanced persistent threat (APT) attacks targeting Taiwan, focusing on the "Lstudio" group. It describes the group's infrastructure including command and control servers, use of botnets to control thousands of compromised machines internationally, and development of custom tools. The summary highlights key points about the group's operations since 2007, use of multiple software versions and back-ends, and targeting of both government and private sector victims primarily in Taiwan but also worldwide.

![whoweare
Based in Taiwan
Interests in Computer Forensics
Access to some raw network traffic data (fun!)
Get to fish interesting things (PROFFFIIITT!)
@bensonwu [secret] @fygrave
[censored]
3](https://image.slidesharecdn.com/bh2013-final-release-130821085435-phpapp02/75/Hunting-The-Shadows-In-Depth-Analysis-of-Escalated-APT-Attacks-3-2048.jpg)