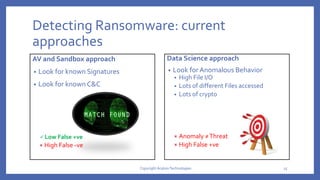
The document discusses the evolution and significance of deception technologies in cybersecurity, detailing its historical applications from natural survival to modern cyber warfare. It explains various types of deception tactics, such as low and high interaction deceptions, and emphasizes the need for dynamic deception methods to counteract attackers. Additionally, it highlights the challenges of deploying these technologies and their effectiveness in detecting cybersecurity threats like ransomware.