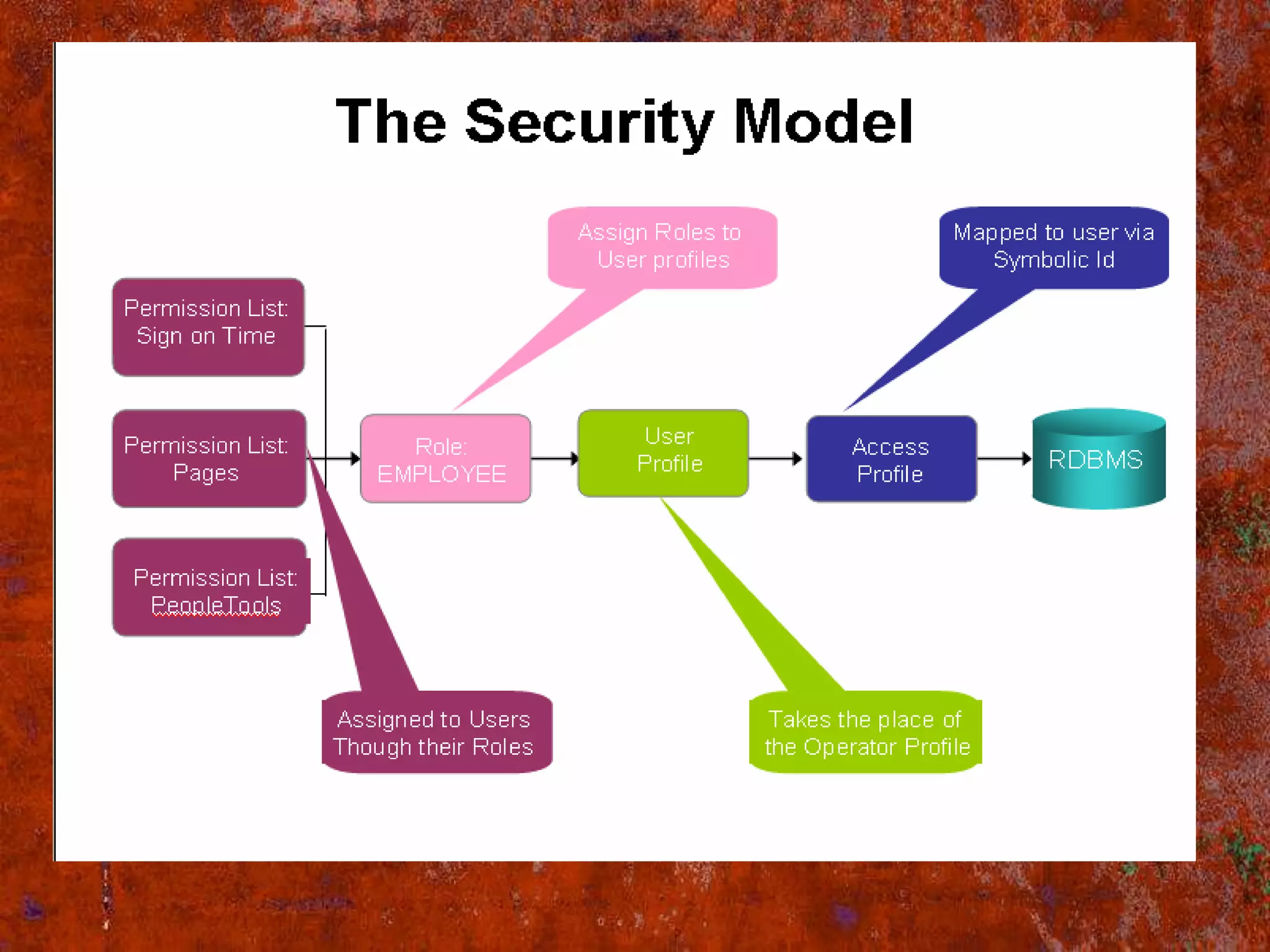
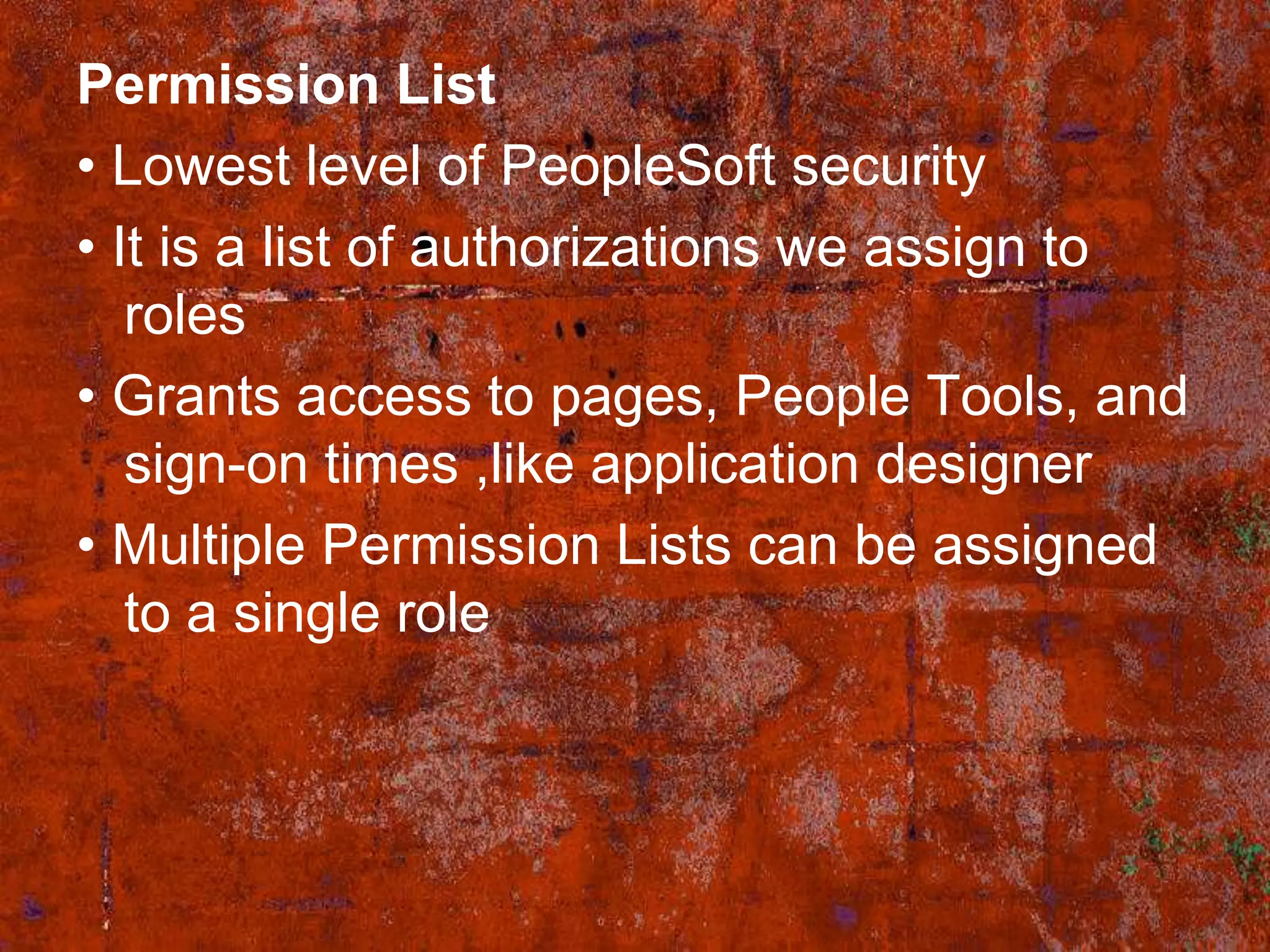
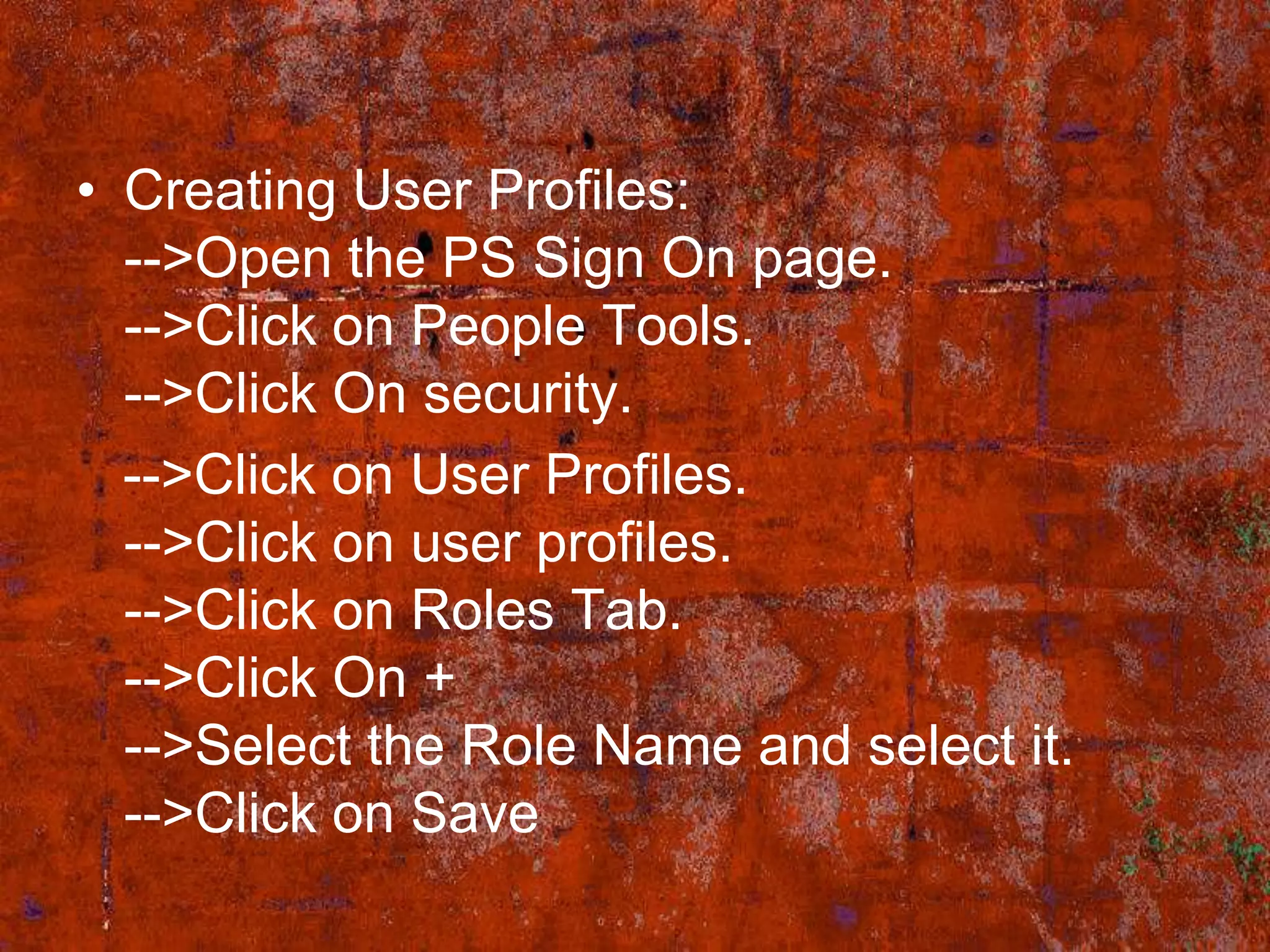
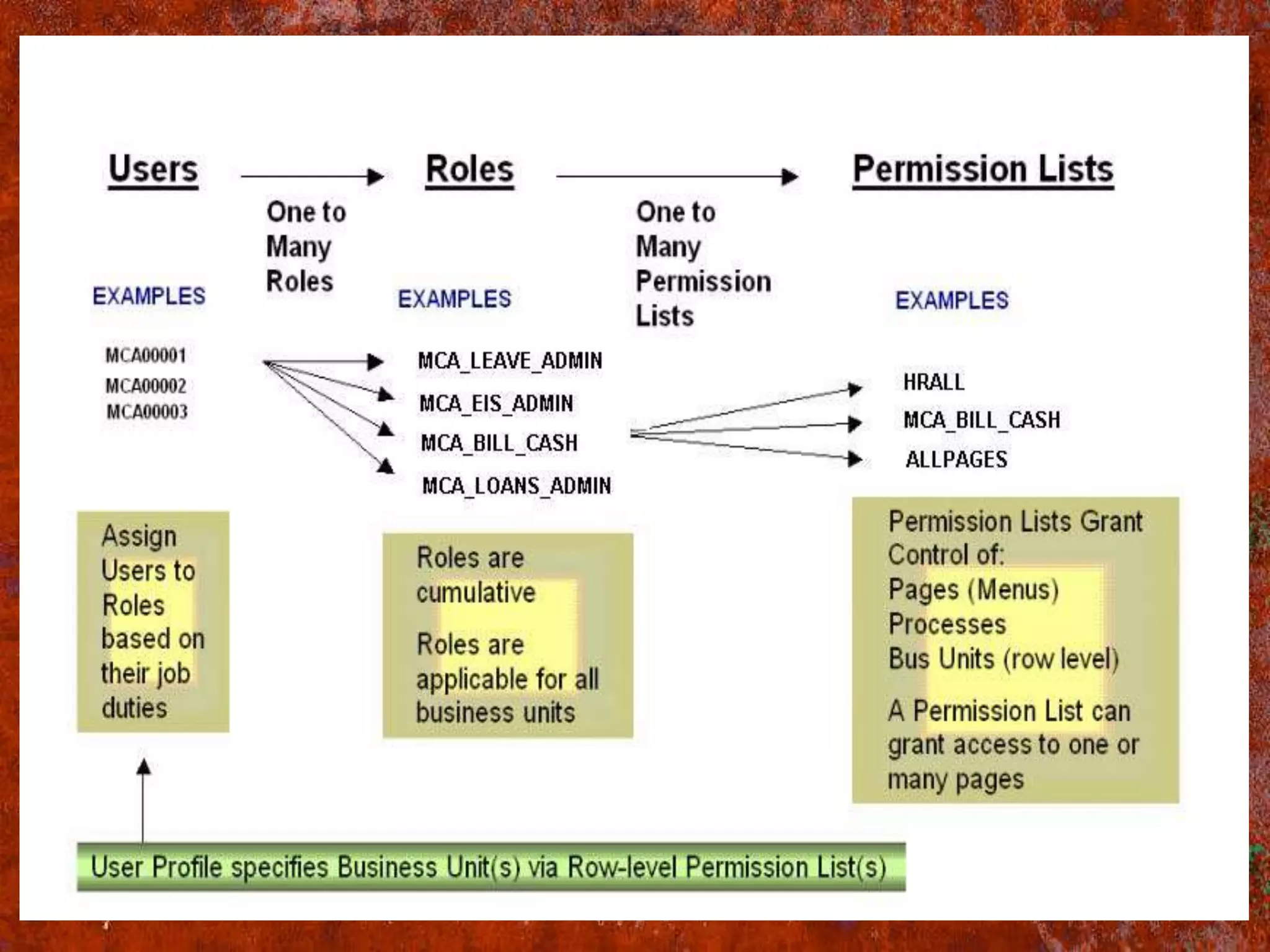
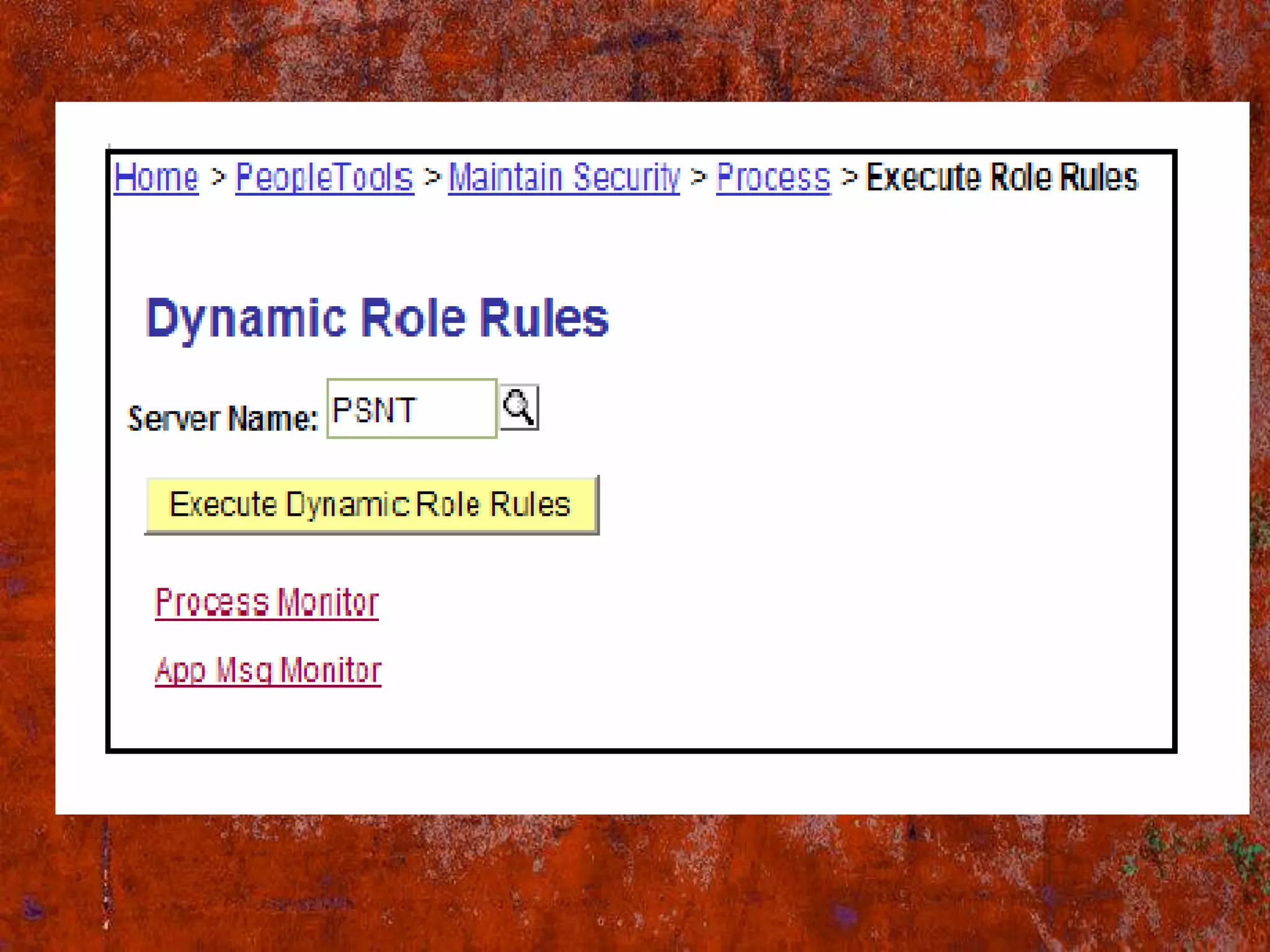
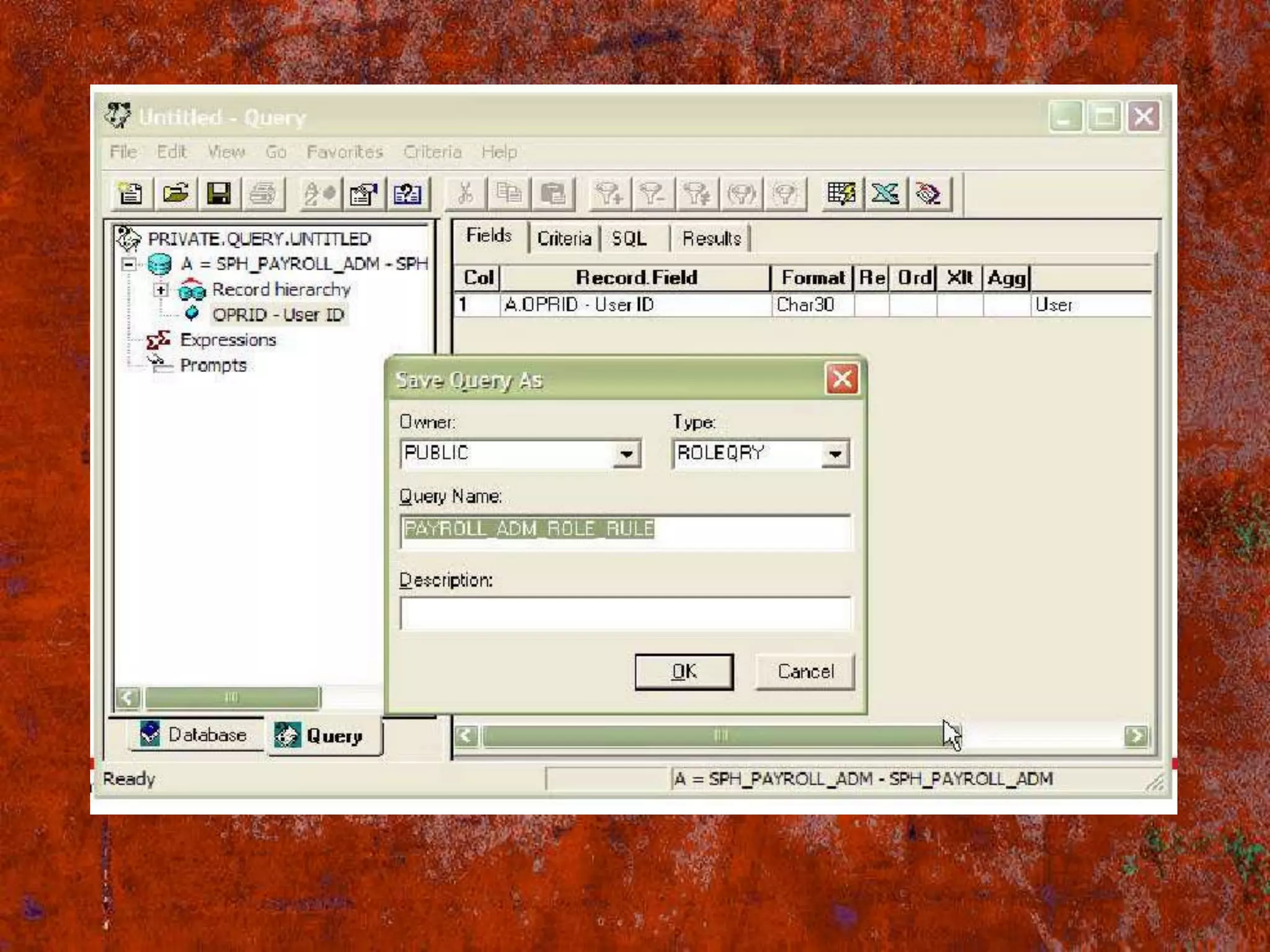
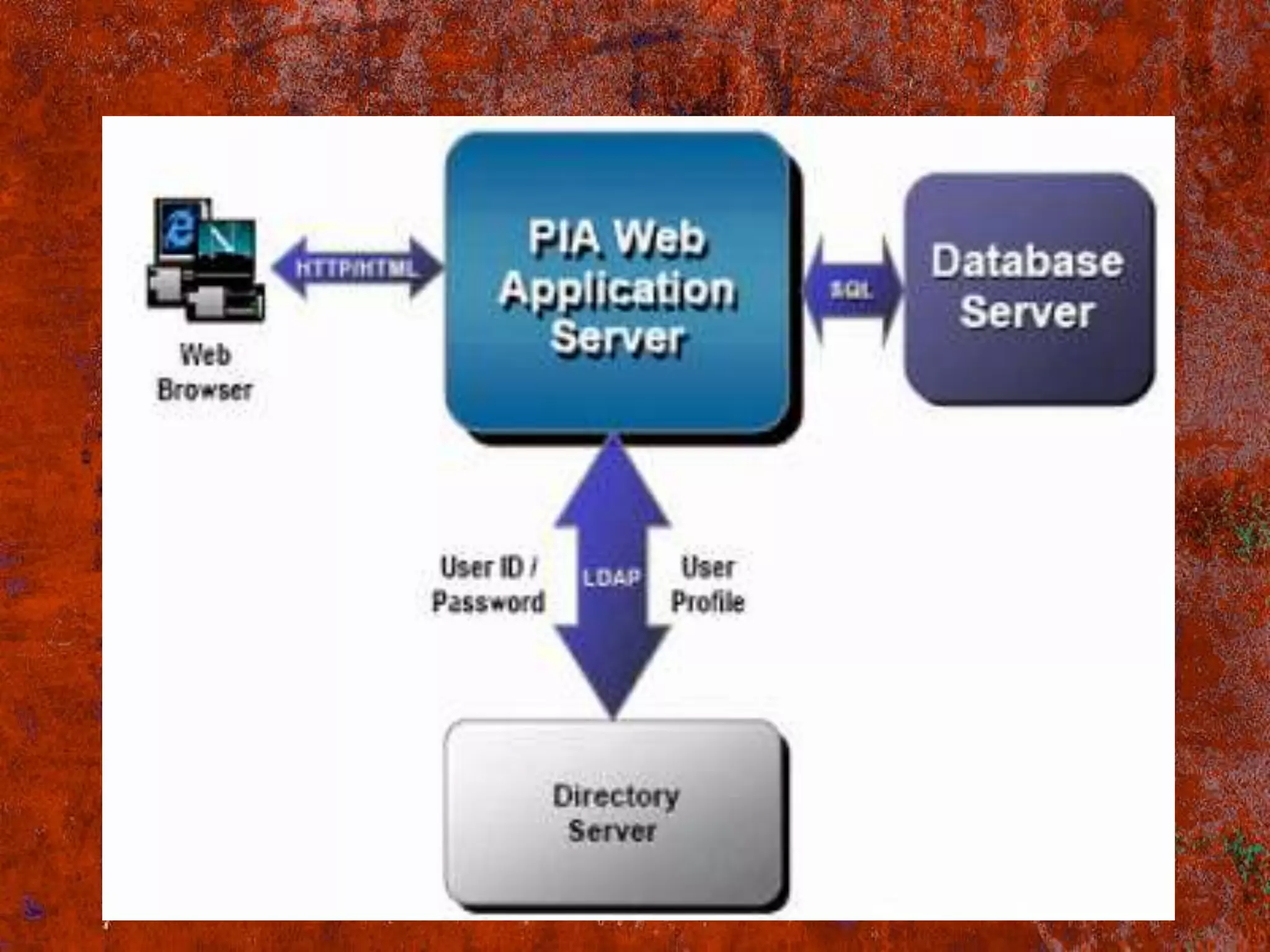
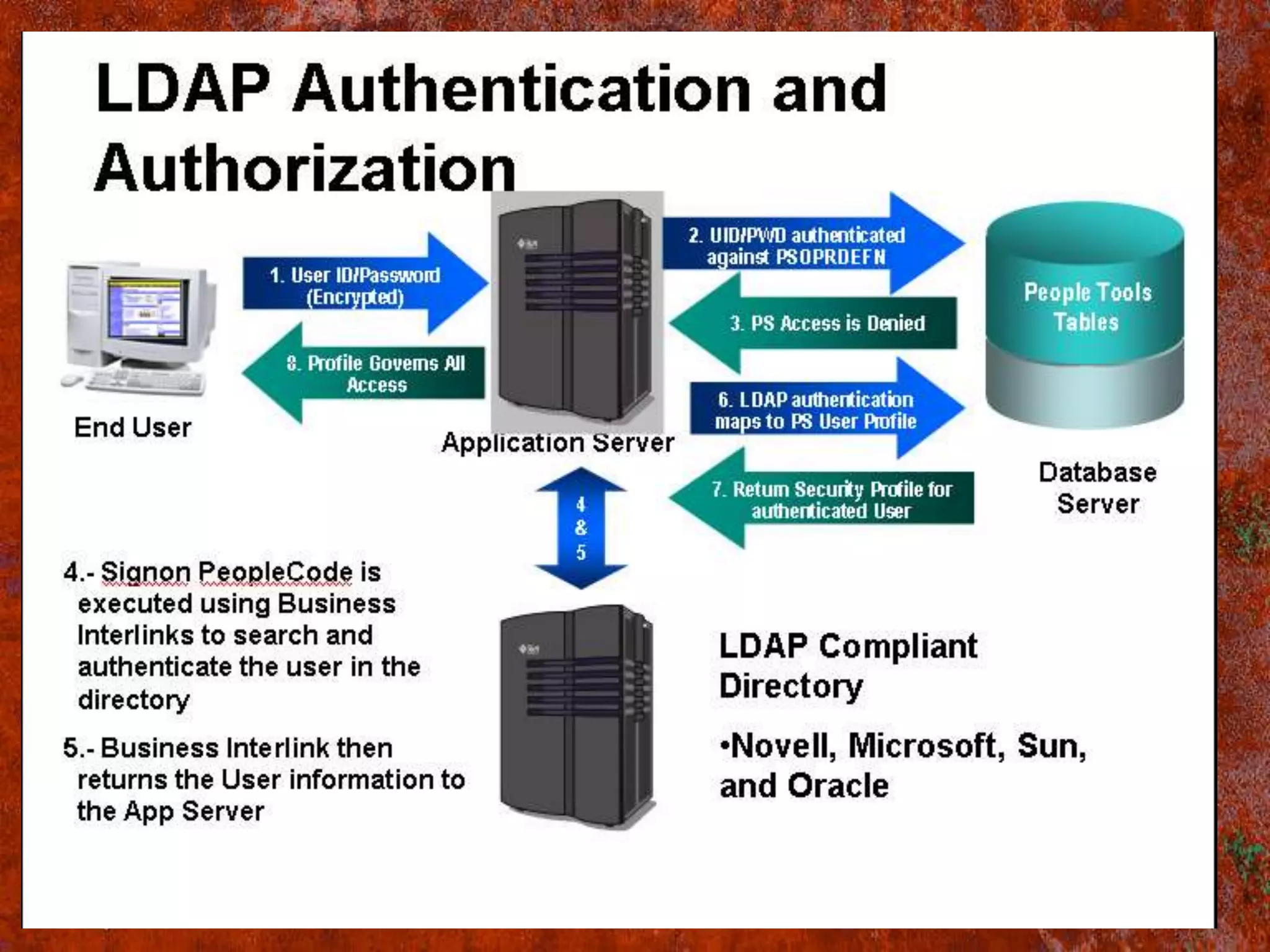
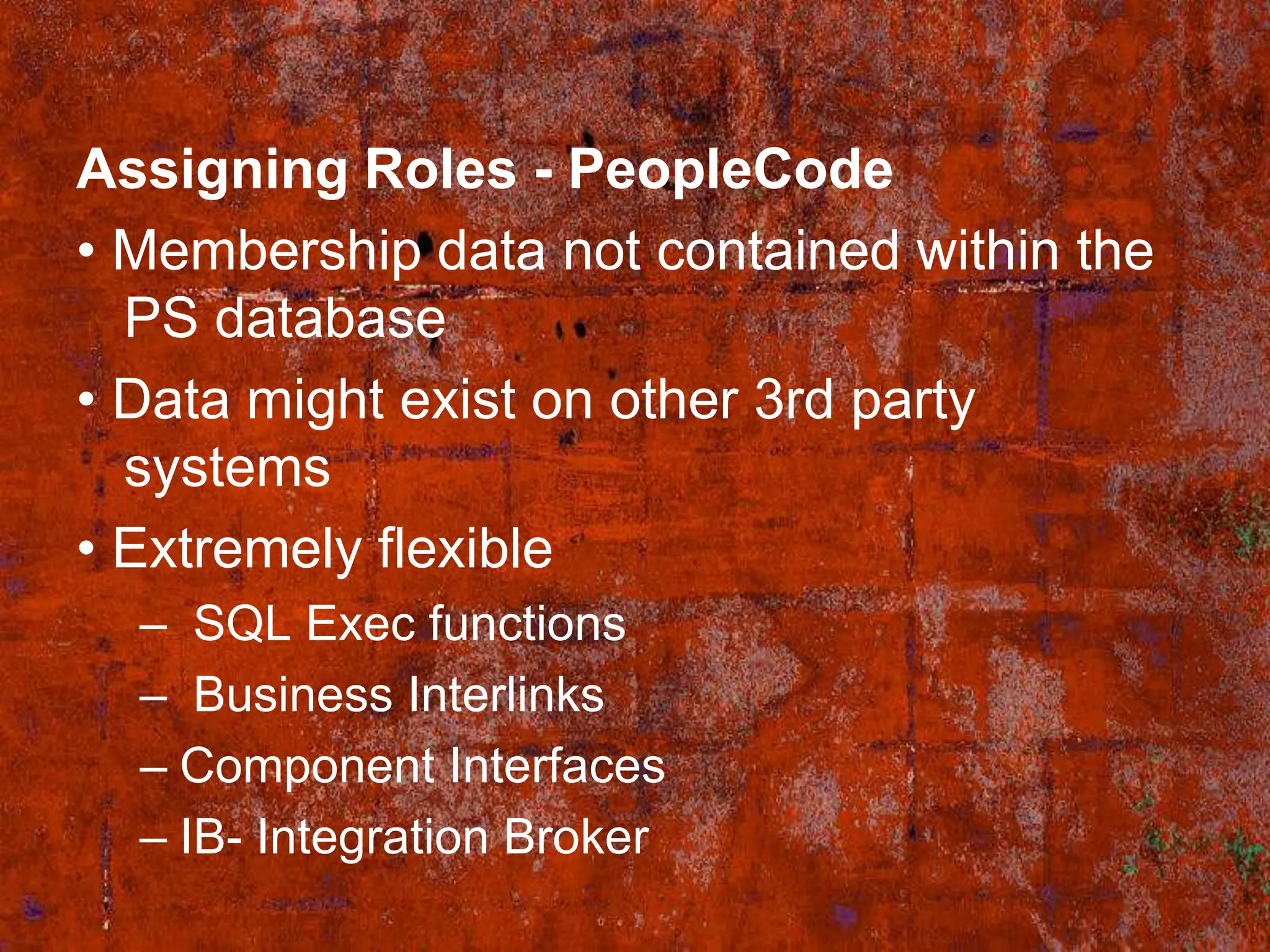
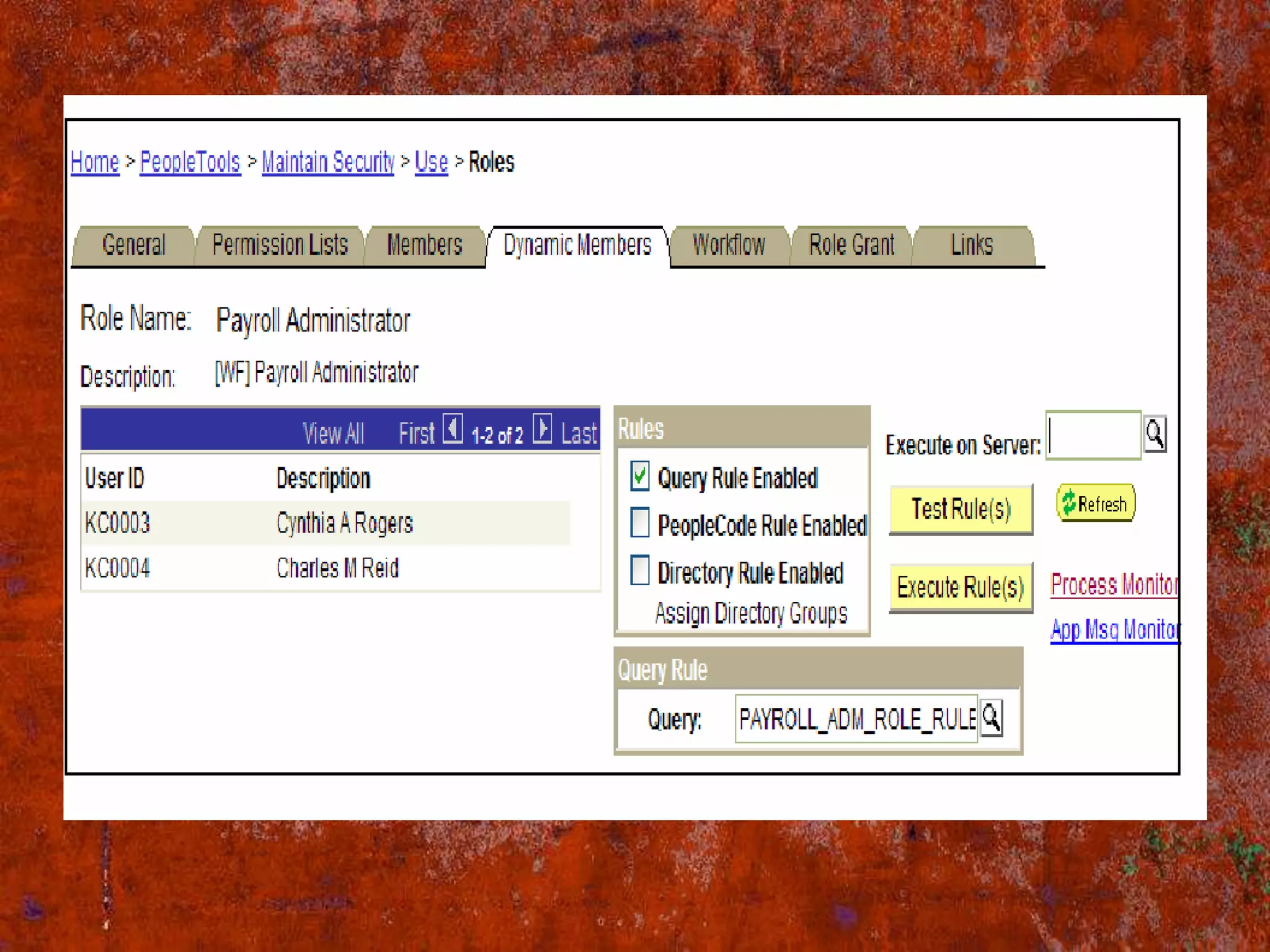
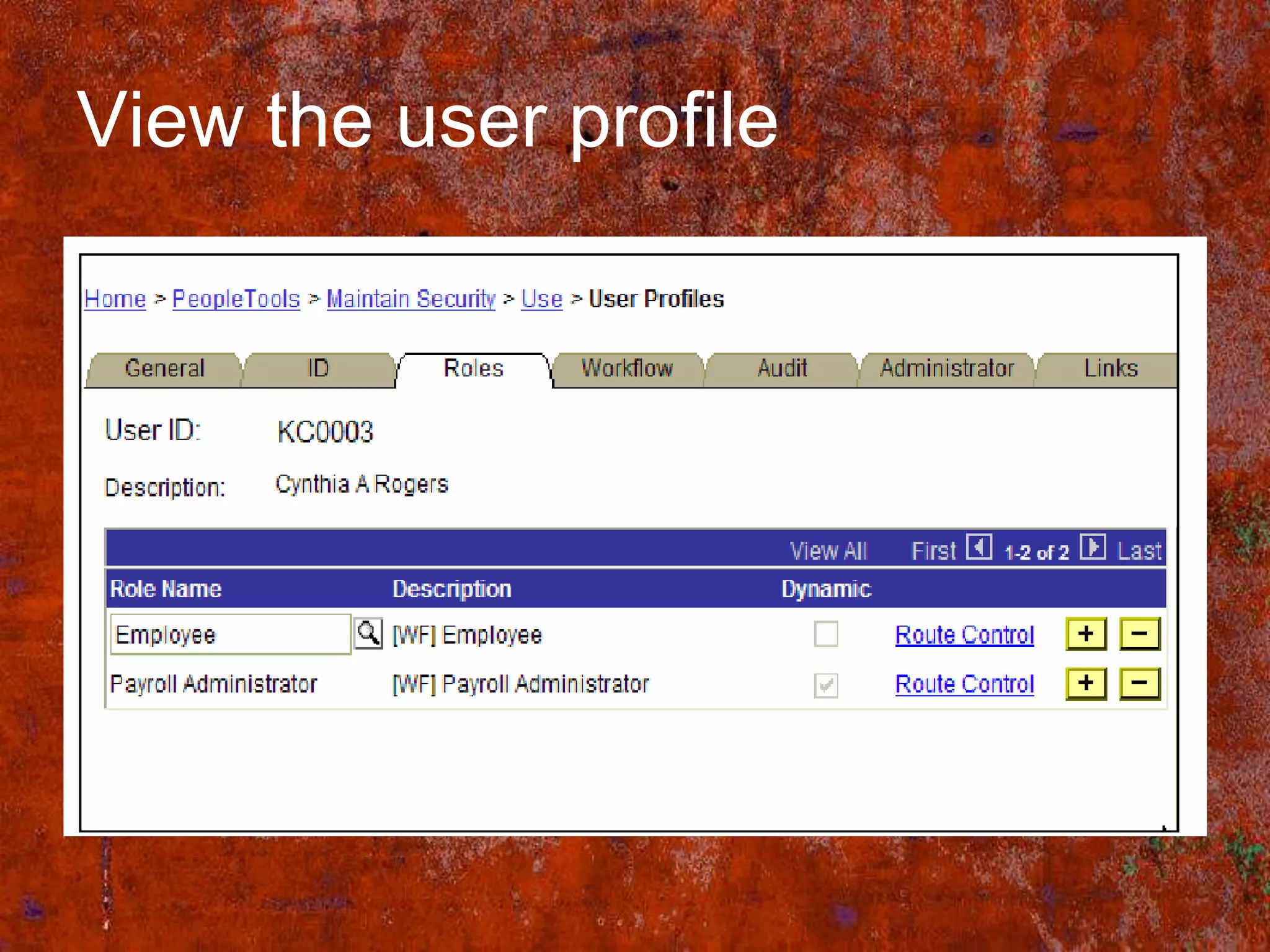
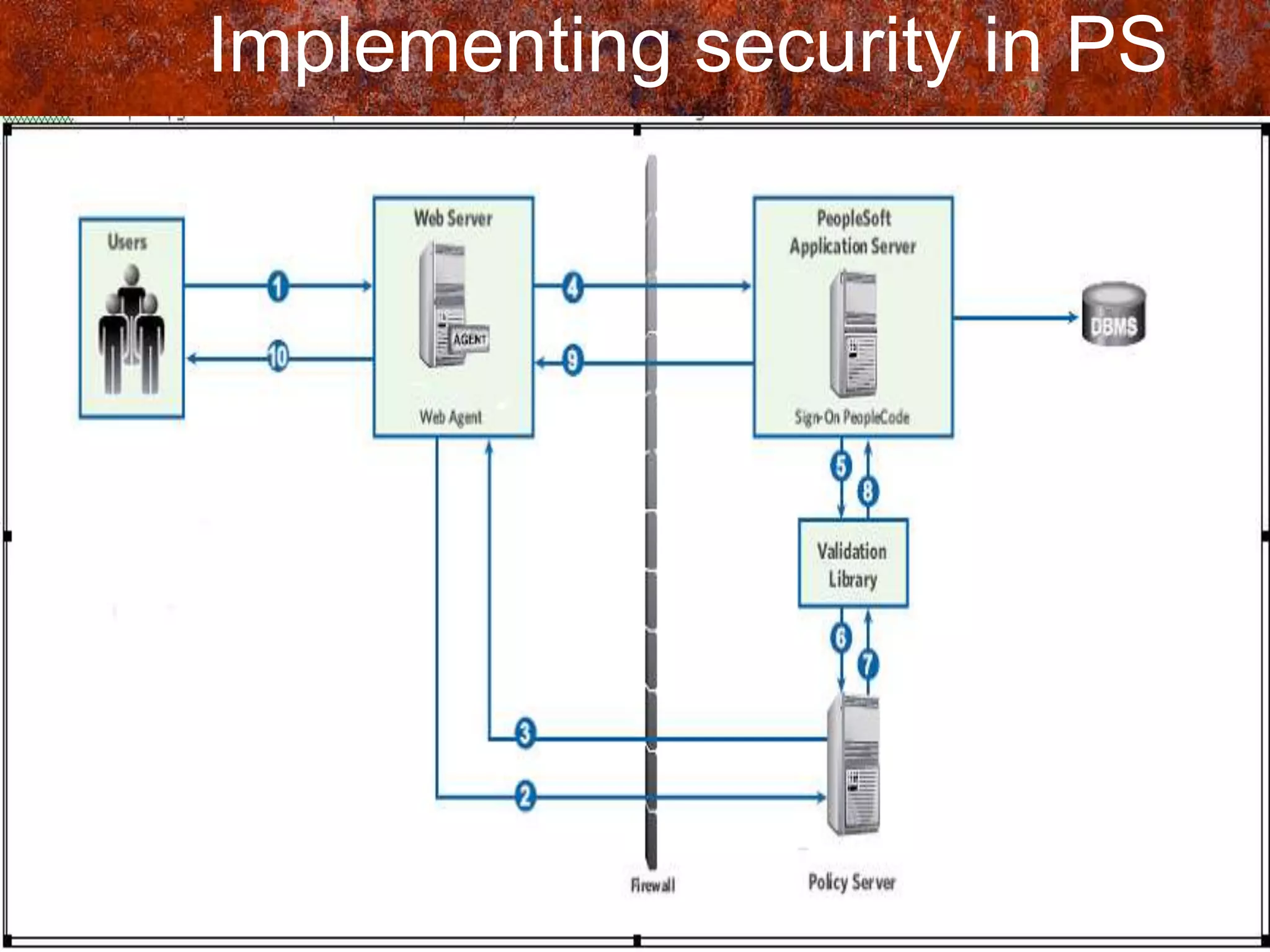
PS Security provides three main components for implementing security: permission lists, roles, and user profiles. Permission lists grant access to specific pages and tools. Roles are assigned to user profiles and link them to permission lists. User profiles define individual users. Security can be implemented through static or dynamic role assignments. Dynamic roles use business rules and technologies like PS/Query, LDAP, and PeopleCode to automatically assign roles based on changing user attributes. This provides a flexible security model in PeopleSoft.