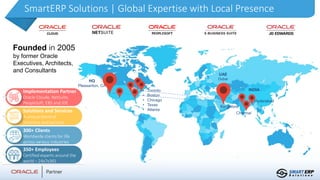
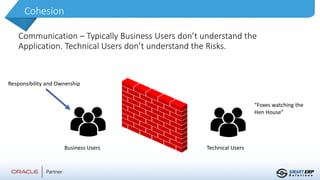
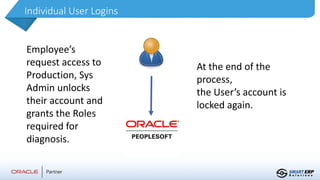
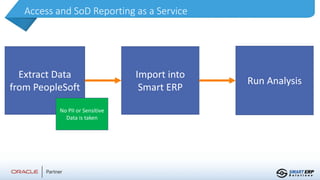
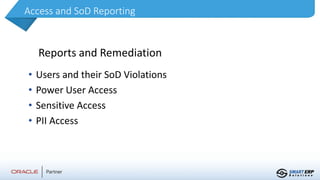
This document summarizes the services provided by SmartERP Solutions, an implementation partner for Oracle, NetSuite, PeopleSoft, and JDE solutions. They have over 300 clients worldwide across various industries and 350+ employees. They offer solutions and services around ERP implementations including PeopleSoft, security assessments, access reviews, segregation of duties analysis, and reporting on access and security as a subscription service. They aim to help organizations comply with various data security and privacy regulations.