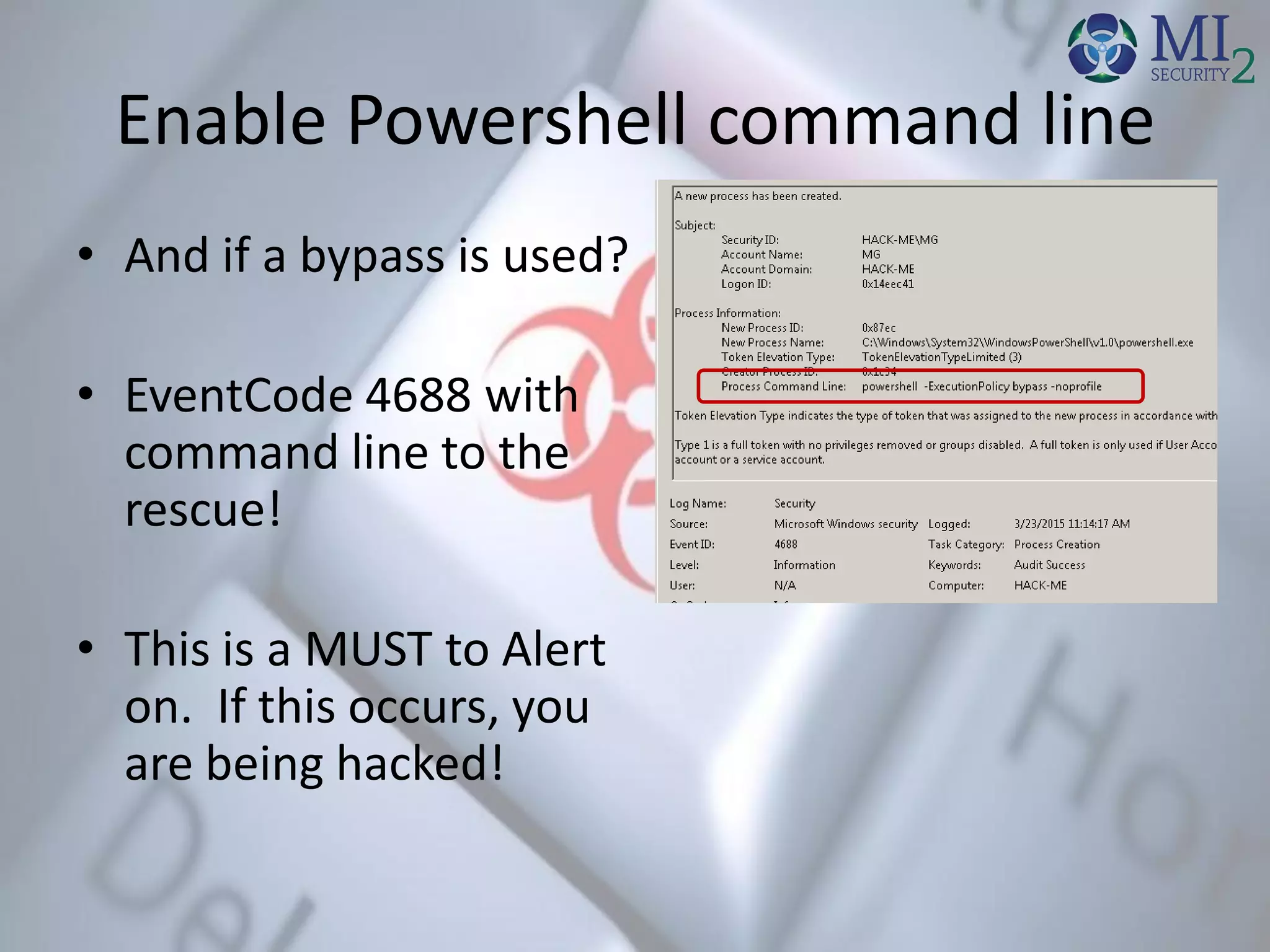
The document emphasizes the critical importance of logs in cybersecurity, particularly in detecting and analyzing malware incidents on Windows systems. The author, an expert in malware and log management, provides insights into enabling and configuring logs to effectively track malicious activities. It also outlines practical steps for auditing and monitoring key system activities to improve security postures against potential threats.












![The Manual way - 4688
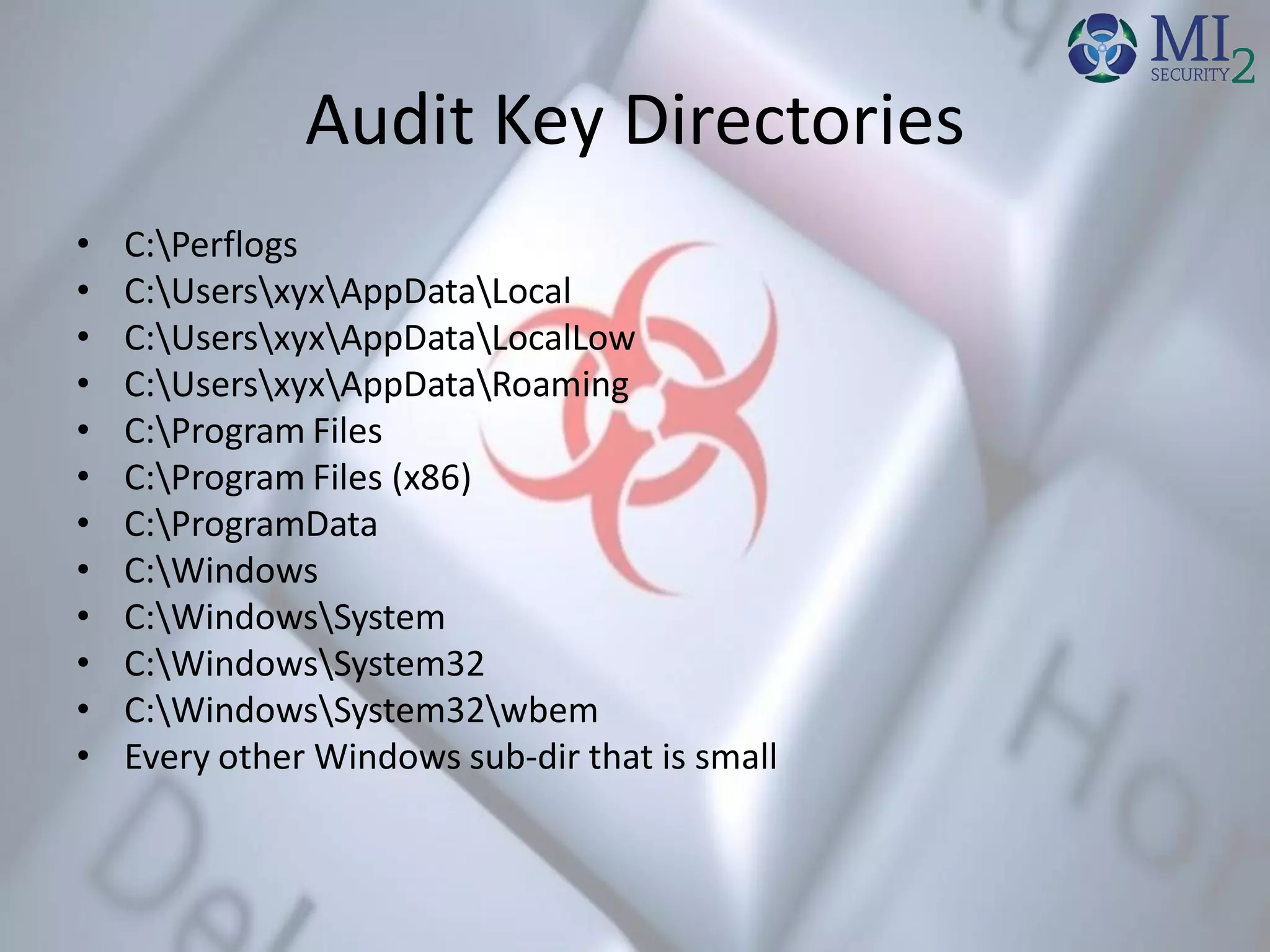
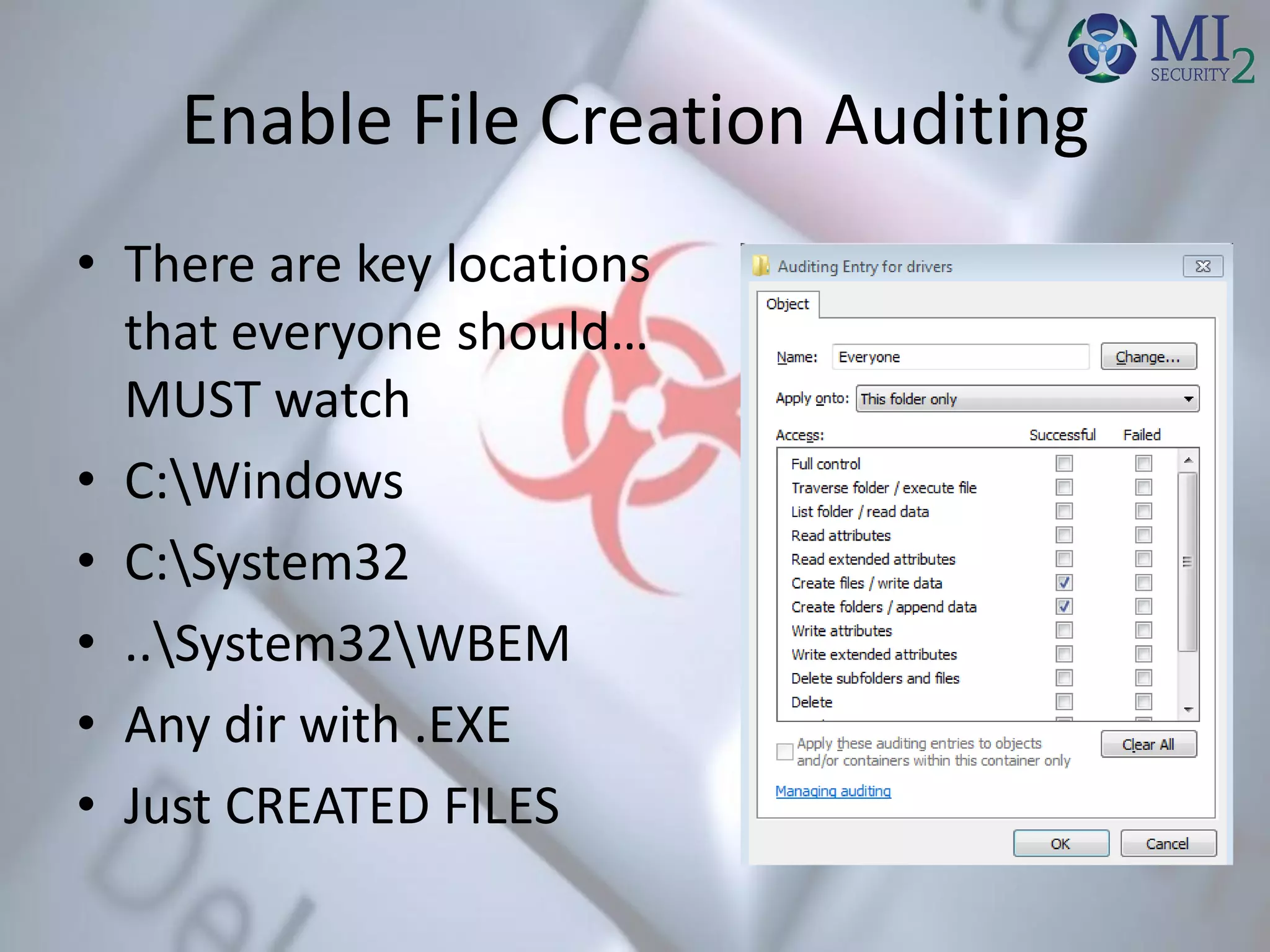
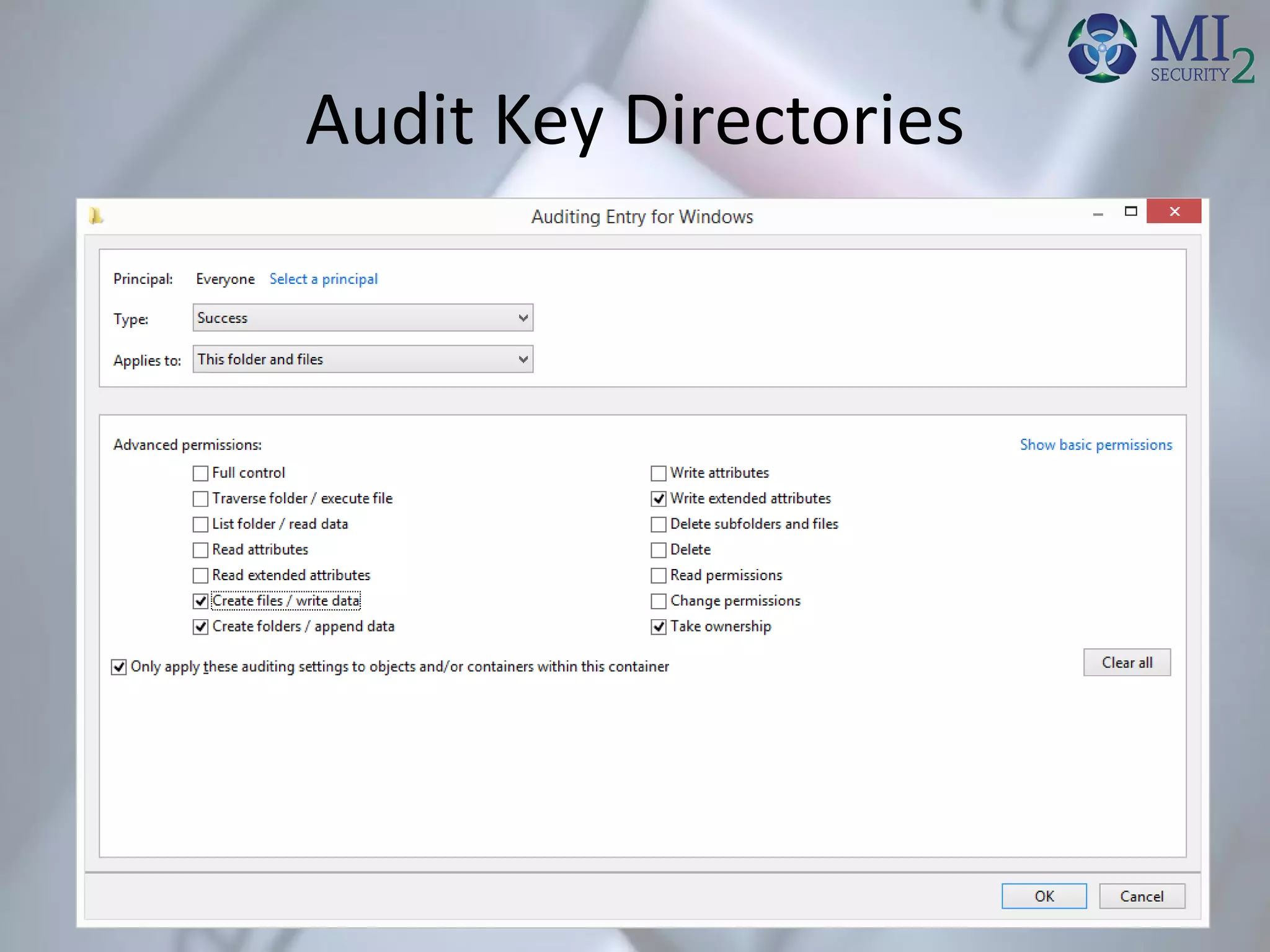
• Look for Executables in UsersAppData
WevtUtil qe Security /q:"*[System[(EventID=4688)]]" /c:50 /rd:true /f:text | find /i "AppData" | find /i "New Process Name"
Gives you this:
New Process Name: C:Users<username>AppDataLocalmalware.exe
New Process Name: C:Users<username>AppDataLocalCitrixGoToMeeting2185g2mvideoconference.exe
New Process Name: C:Users<username>AppDataLocalCitrixGoToMeeting2185g2mui.exe
New Process Name: C:Users<username> AppDataLocalCitrixGoToMeeting2185g2mlauncher.exe
New Process Name: C:Users<username>AppDataLocalCitrixGoToMeeting2185g2mcomm.exe
New Process Name: C:Users<username>AppDataLocalCitrixGoToMeeting2185g2mstart.exe
New Process Name: C:Users<username>AppDataLocalCitrixGoToMeeting2185G2MInstaller.exe
New Process Name: C:Users<username>AppDataLocalCitrixGoToMeeting2185G2MInstaller.exe
Filter out Citrix…
WevtUtil qe Security /q:"*[System[(EventID=4688)]]" /c:50 /rd:true /f:text | find /i "AppData" |
find /i "New Process Name" | find /I /v “CitrixGoTo”
Gives you…
New Process Name: C:Users<username>AppDataLocalmalware.exe](https://image.slidesharecdn.com/logslogslogsv2-150323220854-conversion-gate01/75/Logs-Logs-Logs-What-you-need-to-know-to-catch-a-thief-33-2048.jpg)
![The Manual way - 4688
Last 1000 records
WevtUtil qe Security /q:"*[System[(EventID=4688)]]" /c:1000 /rd:true /f:text | find /i "New Process Name" | find /i
"AppData“
New Process Name: C:Users<username>AppDataLocalTempbadstuffmalware.exe
New Process Name: C:Users<username>AppDataLocalTempbadstuffmalware.exe
New Process Name: C:Users<username>AppDataLocalTempmalware_users_Temp.exe
New Process Name: C:Users<username>AppDataLocalNVIDIANvBackendPackages00007063CoProc
update.19333411.exe
New Process Name: C:Users<username>AppDataRoamingDropboxbinDropbox.exe
New Process Name: C:Users<username>AppDataRoamingDropboxbinupdateDropbox.exe
New Process Name: C:Users<username>AppDataRoamingDropboxbinDropbox.exe
New Process Name:
C:Users<username>AppDataLocalApps2.0R9P169LK.0LAEA80CTLH.BZ3dell..tion_0f612f649c4a10af
_0005.000b_17ede8fa7a4e5cacDellSystemDetect.exe
New Process Name: C:Users<username>AppDataLocalAppleApple Software UpdateSetupAdmin.exe
New Process Name: C:Users<username>AppDataLocalTempi4jdel0.exe
New Process Name:
C:Users<username>AppDataLocalTempe4j9473.tmp_dir1424306522jrebinunpack200.exe
New Process Name:
C:Users<username>AppDataLocalTempe4j9473.tmp_dir1424306522jrebinunpack200.exe](https://image.slidesharecdn.com/logslogslogsv2-150323220854-conversion-gate01/75/Logs-Logs-Logs-What-you-need-to-know-to-catch-a-thief-34-2048.jpg)
![The Manual way - 4688
Last 1000 records
WevtUtil qe Security /q:"*[System[(EventID=4688)]]" /c:1000 /rd:true /f:text | find /i "Command" | find /i ".exe" | find
/i /v "windows" | find /i /v "Program files" | find /i /v "taskeng.exe" | find /i /v "taskhost.exe" | find /i /v
"logonUI.exe" | find /i /v “consent.exe" | find /i /v "programdata" | find /i /v "nvidianvbackendpackages" | find /i /v
"dropbox" | find /i /v "/i"
Gives you…
Process Command Line: malware.exe
Process Command Line: malware.exe 25.233.45.123
Process Command Line: malware_users_Temp.exe /u:hacker /p:yurfracked
Process Command Line: wmiadap.exe /F /T /R
Process Command Line: rundll32.exe NVCPL.DLL,NvStartupRunOnFirstSessionUserAccount
Process Command Line: "C:UsersMGAppDataLocalApps2.0R9P169LK.0LAEA80CTLH.BZ3
dell..tion_0f612f649c4a10af_0005.000b_17ede8fa7a4e5cacDellSystemDetect.exe"
Process Command Line: atbroker.exe
Process Command Line: C:PROGRA~1SUMOLO~1wrapper.exe -s
C:PROGRA~1SUMOLO~1c onfigwrapper.conf
Process Command Line: winlogon.exe
Process Command Line: "C:UsersMGAppDataLocalAppleApple Software UpdateSetupAdmin.exe"
What looks bad?](https://image.slidesharecdn.com/logslogslogsv2-150323220854-conversion-gate01/75/Logs-Logs-Logs-What-you-need-to-know-to-catch-a-thief-35-2048.jpg)

![Enable Powershell command line
• It’s nice to know Powershell executed, but we REALLY want to see what was executed
• Again, Windows SUCKS by default, Powershell
• Details on setting PowerShell Preference variables
– http://technet.microsoft.com/en-us/library/hh847796.aspx
• Set Execution Policy to allo .PS1 files to execute so default profile works
– powershell Set-ExecutionPolicy RemoteSigned
• Create a Default Profile for all users:
– C:WindowsSystem32WindowsPowershellv1.0
– Profile.ps1
• Add these to your default profile.ps1 file
– $LogCommandHealthEvent = $true
– $LogCommandLifecycleEvent = $true
• Splunk - Inputs.conf
– # Windows platform specific input processor
– [WinEventLog://Windows PowerShell]
– disabled = 0
• Upgrade to ver 3 or ver 4
• Investigating PowerShell Attacks (DefCon & Blackhat 2014)
– Ryan Kazanciyan TECHNICAL DIRECTOR, MANDIANT
– Matt Hastings CONSULTANT, MANDIANT](https://image.slidesharecdn.com/logslogslogsv2-150323220854-conversion-gate01/75/Logs-Logs-Logs-What-you-need-to-know-to-catch-a-thief-37-2048.jpg)