b.e final year project in Trichy
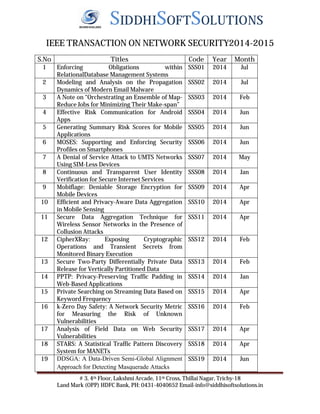
- 1. SIDDHISOFTSOLUTIONS IEEE TRANSACTION ON NETWORK SECURITY2014-2015 S.No Titles Code Year Month 1 Enforcing Obligations within RelationalDatabase Management Systems SSS01 2014 Jul 2 Modeling and Analysis on the Propagation Dynamics of Modern Email Malware SSS02 2014 Jul 3 A Note on “Orchestrating an Ensemble of Map- Reduce Jobs for Minimizing Their Make-span” SSS03 2014 Feb 4 Effective Risk Communication for Android SSS04 2014 Jun 5 Generating Summary Risk Scores for Mobile Applications SSS05 2014 Jun 6 MOSES: Supporting and Enforcing Security Profiles on Smartphones SSS06 2014 Jun 7 A Denial of Service Attack to UMTS Networks Using SIM-Less Devices SSS07 2014 May 8 Continuous and Transparent User Identity Verification for Secure Internet Services SSS08 2014 Jan 9 Mobiflage: Deniable Storage Encryption for Mobile Devices SSS09 2014 Apr 10 Efficient and Privacy-Aware Data Aggregation in Mobile Sensing SSS10 2014 Apr 11 Secure Data Aggregation Technique for Wireless Sensor Networks in the Presence of Collusion Attacks SSS11 2014 Apr 12 CipherXRay: Exposing Cryptographic Operations and Transient Secrets from Monitored Binary Execution SSS12 2014 Feb 13 Secure Two-Party Differentially Private Data Release for Vertically Partitioned Data SSS13 2014 Feb 14 PPTP: Privacy-Preserving Traffic Padding in Web-Based Applications SSS14 2014 Jan 15 Private Searching on Streaming Data Based on Keyword Frequency SSS15 2014 Apr 16 k-Zero Day Safety: A Network Security Metric for Measuring the Risk of Unknown Vulnerabilities SSS16 2014 Feb 17 Analysis of Field Data on Web Security Vulnerabilities SSS17 2014 Apr 18 STARS: A Statistical Traffic Pattern Discovery System for MANETs SSS18 2014 Apr 19 DDSGA: A Data-Driven Semi-Global Alignment Approach for Detecting Masquerade Attacks SSS19 2014 Jun # 3, 4th Floor, Lakshmi Arcade, 11th Cross, Thillai Nagar, Trichy-18 Apps Land Mark (OPP) HDFC Bank, PH: 0431-4040652 Email-info@siddhisoftsolutions.in
- 2. SIDDHISOFTSOLUTIONS 20 A Random Decision Tree Framework for Privacy-preserving Data Mining SSS20 2014 Jan 21 Risk Aware Query Replacement Approach For Secure Databases Performance Management. SSS21 2014 Apr 22 Abductive Analysis of Administrative Policies in Rule-based Access Control SSS22 2014 Jan 23 MFTS: A Multi-level Fault-tolerant Archiving Storage with Optimized Maintenance Bandwidth SSS23 2014 Feb 24 Security Analysis and Related Usability of Motion-based CAPTCHAs: Decoding Codewords in Motion SSS24 2014 Jan 25 A Lightweight Secure Scheme for Detecting Provenance Forgery and Packet Drop Attacks in Wireless Sensor Networks SSS25 2014 Jan 26 Low-Priced and Energy-Efficient Detection of Replicas for Wireless Sensor Networks SSS26 2014 Jun 27 Collusion-Tolerable Privacy-Preserving Sum and Product Calculation without Secure Channel SSS27 2014 Feb 28 hBFT: Speculative Byzantine Fault Tolerance With Minimum Cost SSS28 2014 Mar 29 A Computational Dynamic Trust Model for User Authorization SSS29 2014 Feb 30 Bandwidth Distributed Denial of Service: Attacks and Defenses SSS30 2014 Mar 31 Cost-Effective Authentic and Anonymous Data Sharing with Forward Security SSS31 2014 Apr 32 A Two-Stage De-anonymization Attack against Anonymized Social Networks SSS32 2014 Feb 33 E-MACs: Toward More Secure and More Efficient Constructions of Secure Channels SSS33 2014 Jan 34 Signature-Based Protection from Code Reuse SSS34 2014 Jan 35 Distributed Detection in Mobile Access Wireless Sensor Networks under Byzantine Attacks SSS35 2014 Apr 36 Certification Authorities Under Attack A Plea for Certificate Legitimation SSS36 2014 Feb 37 Secure De-duplication with Efficient and Reliable Convergent Key Management SSS37 2014 Jun 38 Secure and Efficient Data Transmission for Cluster-Based Wireless Sensor Networks SSS38 2014 Mar 39 Secure Continuous Aggregation in Wireless SSS39 2014 Mar # 3, 4th Floor, Lakshmi Arcade, 11th Cross, Thillai Nagar, Trichy-18 Attacks Land Mark (OPP) HDFC Bank, PH: 0431-4040652 Email-info@siddhisoftsolutions.in
- 3. SIDDHISOFTSOLUTIONS Sensor Networks 40 Securing Broker-Less Publish/Subscribe Systems Using Identity-Based Encryption SSS40 2014 Feb 41 A Probabilistic Misbehavior Detection Scheme toward Efficient Trust Establishment in Delay- Tolerant Networks SSS41 2014 Jan 42 Behavioral Malware Detection in Delay Tolerant Networks SSS42 2014 Jan 43 Hop-by-Hop Message Authentication and Source Privacy in Wireless Sensor Networks SSS43 2014 May # 3, 4th Floor, Lakshmi Arcade, 11th Cross, Thillai Nagar, Trichy-18 Land Mark (OPP) HDFC Bank, PH: 0431-4040652 Email-info@siddhisoftsolutions.in
